Drone Deployment Algorithms for Effective Communication Establishment in Disaster Affected Areas
Abstract
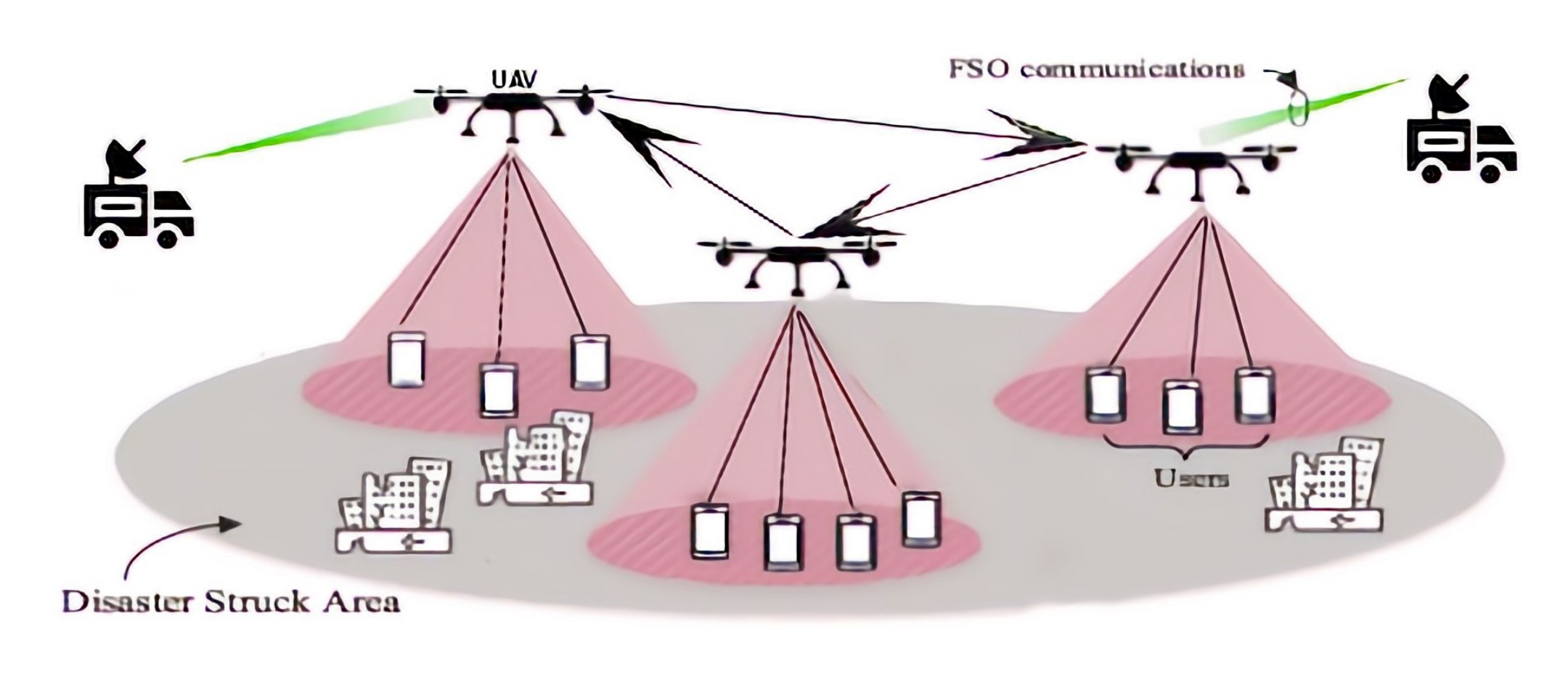
:1. Introduction
- Development of a terrain-aware region-filling algorithm that covers the entire disaster affected area under a cellular network.
- Minimization of the required number of drones while maximizing the average leftover energy of the system.
- A proof that our method uses the minimum number of drones possible.
- Application and evaluation of the above methods using the parameters of a real location in Pettimudi, India.
- A simulation of the region-filling algorithm for the terrain of Pettimudi.
2. Related Works
3. Proposed Methods
3.1. Problem Statement
- To develop a strategy for deploying drones to maintain the maximum possible average leftover energy and thereby increase the overall hovering time of all drones deployed.
- To develop a region-filling method that guarantees coverage over the whole region with the minimum possible number of drones.
- To deploy drones for communication establishment based on terrain and altitude analysis.
- To determine the number and positions of base stations required to facilitate the network.
3.2. Methodology
3.3. Preprocessing
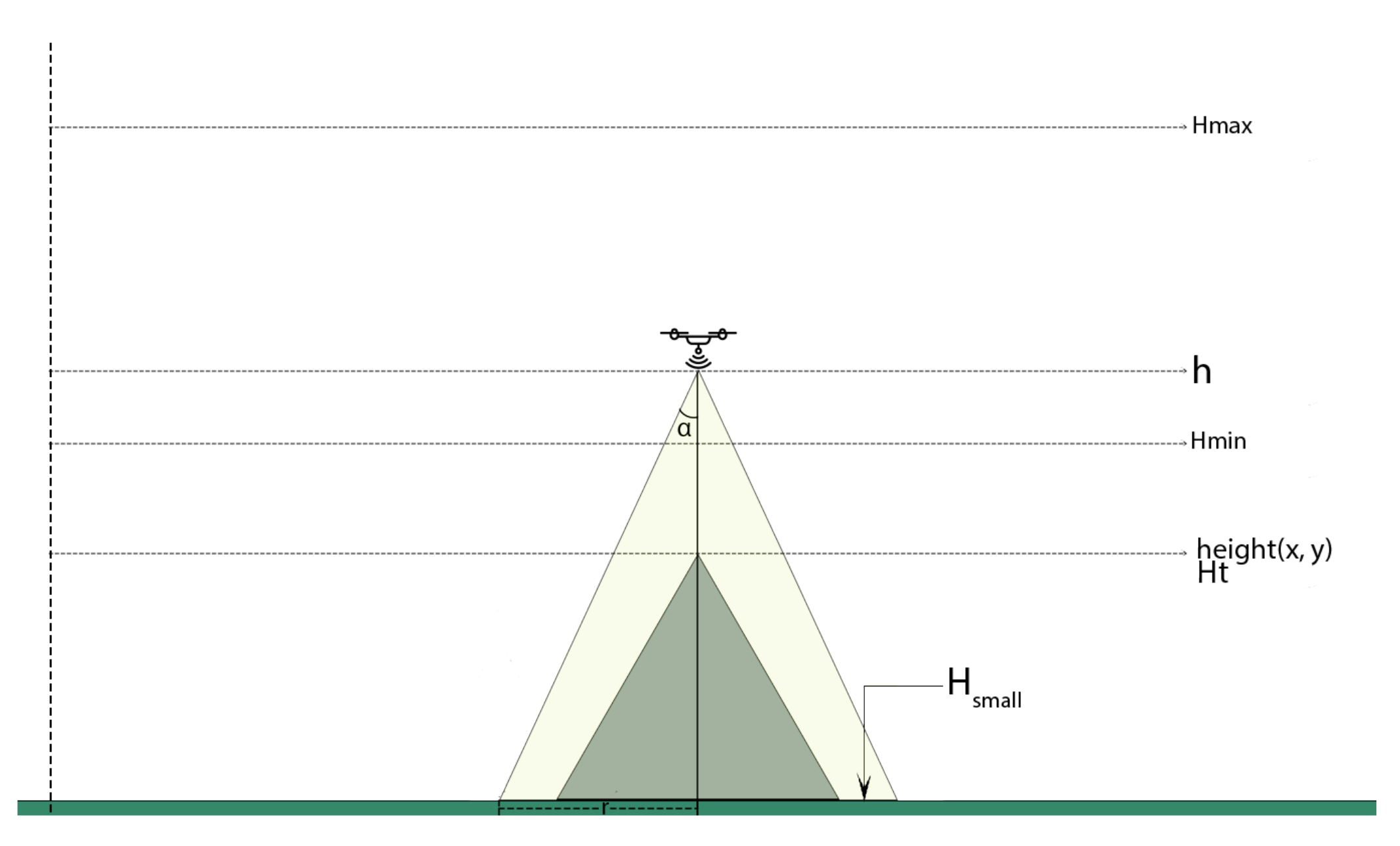
3.3.1. The Preprocessor Module
- Construction of the Height Matrix(H) data structure.
- Calculation of the environment parameters required by the region-filling algorithm.
Height Matrix Data Structure
Environmental Parameters
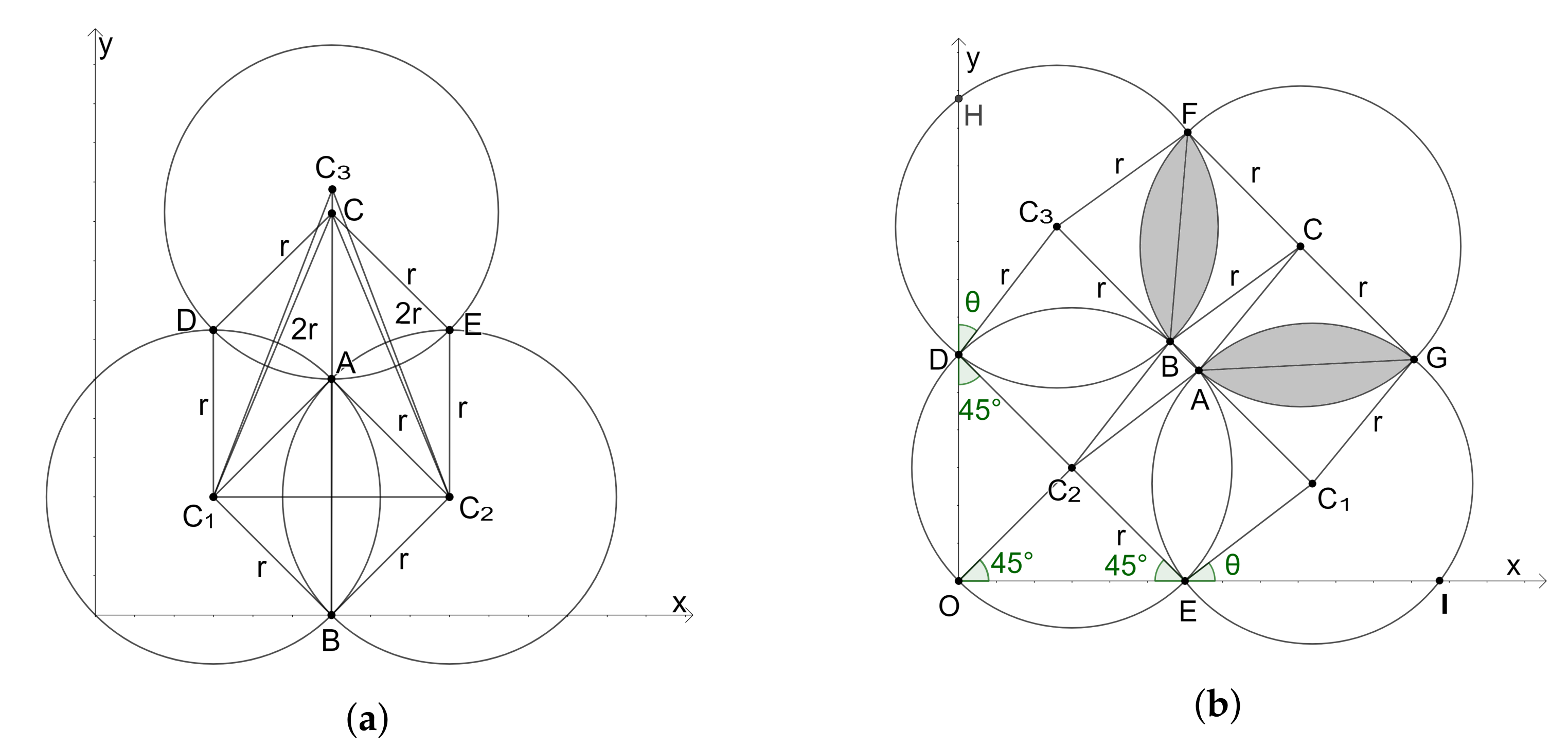
3.4. Region Filling
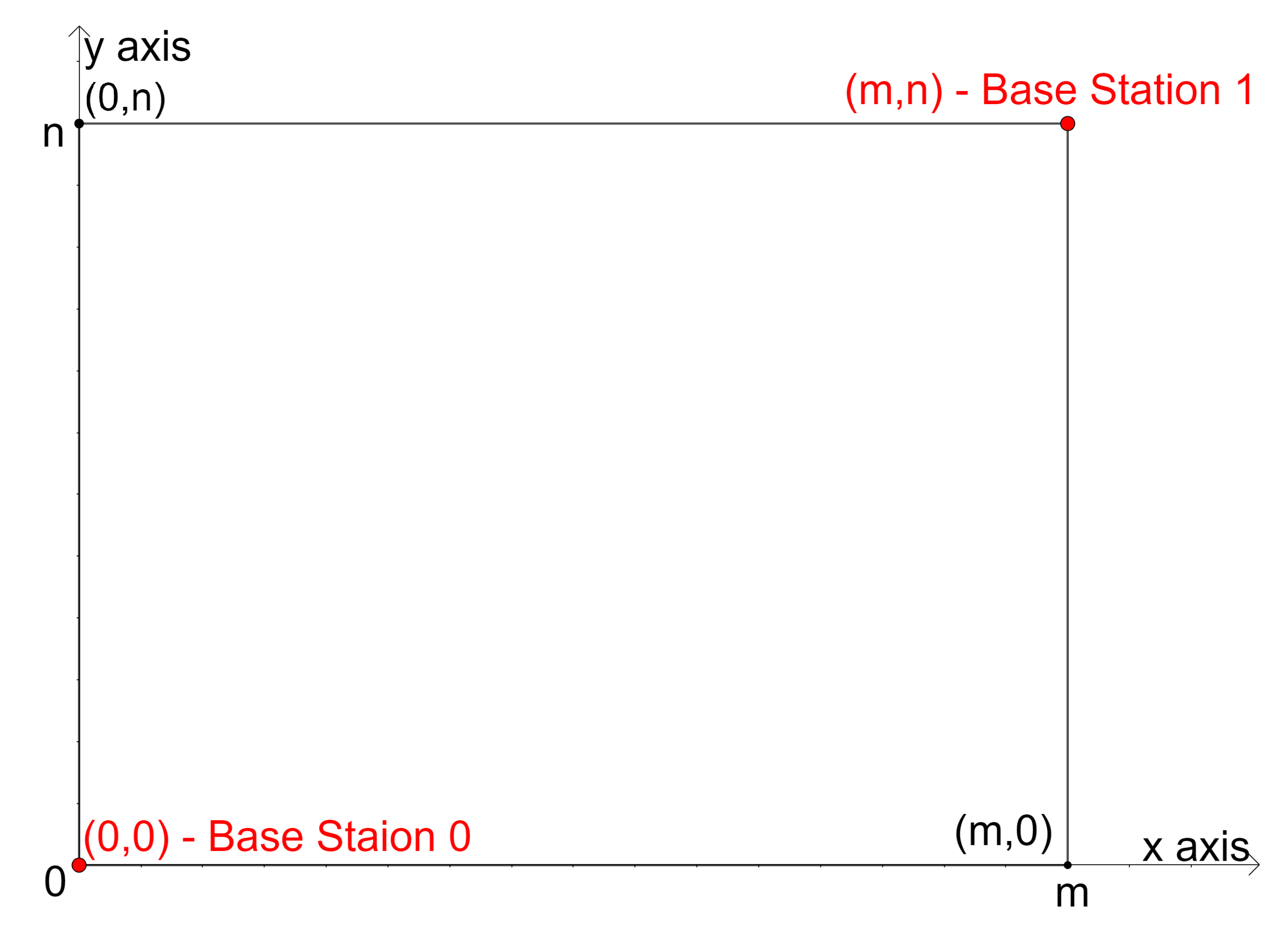
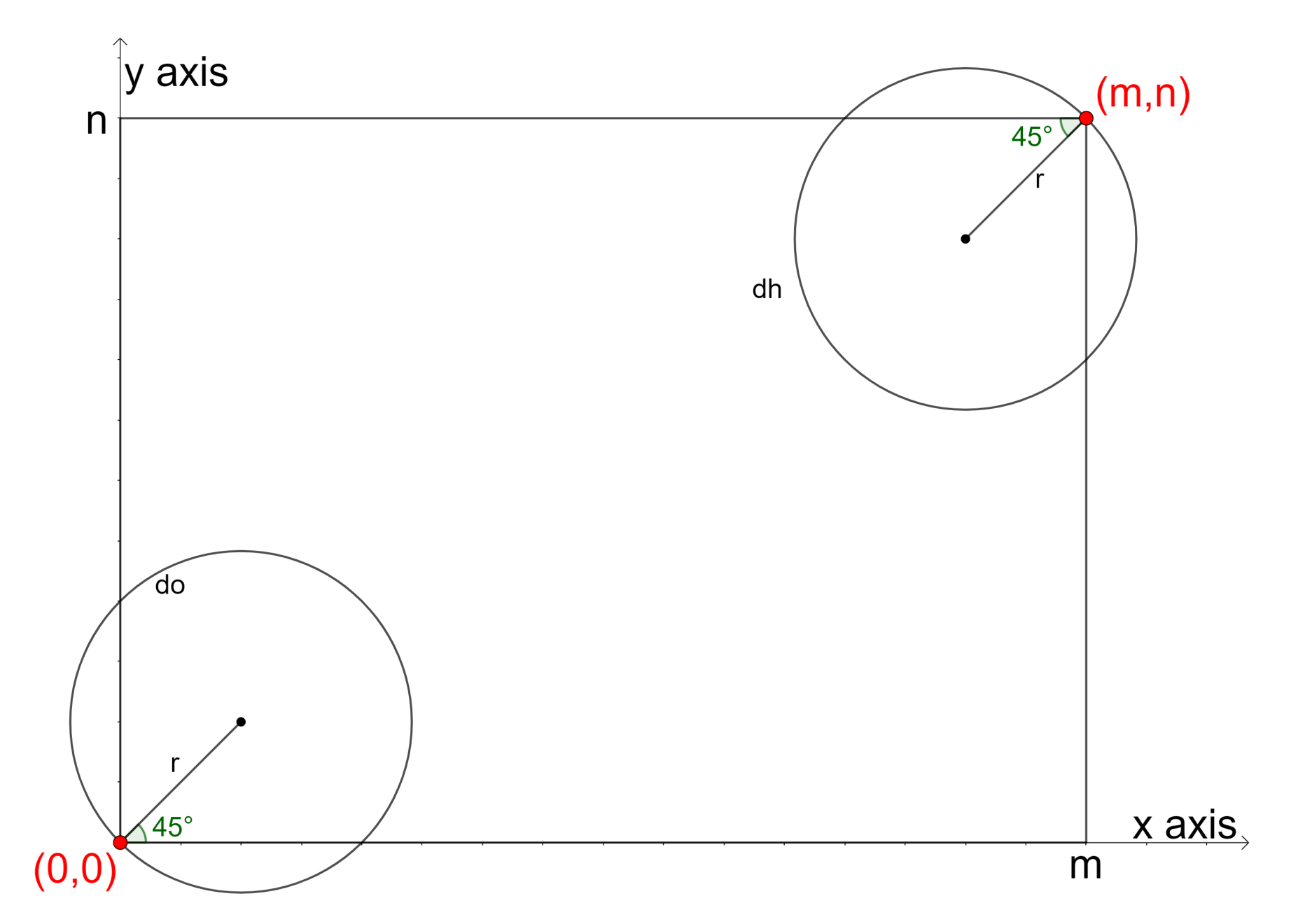
3.4.1. Determining the Number and Positions of Base Stations
3.4.2. Outline of the Region-Filling Algorithm
- —x and y coordinates of the position of a drone
- r—radius of the cone-shaped network coverage
- h—height of the cone-shaped network coverage
- b—an indication of the base station; a value of 0 means the base station of the drone is at (0, 0) and 1 means the base station of the drone is at (m, n)
- e—leftover energy of the drone when the drone reaches its assigned location starting from its base station
- —the maximum value among the heights of reference points associated with each drone, which is needed in order to cope with the terrain of the affected region
- , , , —the northern, southern, western, and eastern neighbouring drones of the network drone
- D—an ordered collection of drone objects (the output of the algorithm)
- —a reference x-coordinate for y-directional filling
- —a reference y-coordinate for x-directional filling
3.4.3. Calculating Various Drone Parameters
- —the height of the ith drone
- —the leftover energy of the ith drone
- —the height of the base station
- B—the initial energy of all drones
- C—the energy parameter (same for all drones)
- W—the ratio of horizontal lift to drag ratio to vertical lift to drag ratio
- —the horizontal distance travelled by the ith drone
| Algorithm 1 FindDroneParameters—Calculating the base station (b), height (h), radius of coverage (r), and leftover energy (e) of the drone |
Input: ()—position of the drone, —height of reference point, Output:
|
3.4.4. Filling the Coverage Circles along the X and Y Axes
| Algorithm 2 FillAlongXAxis—Filling drone coverage circles along x-axis |
Input: d—a drone object representing the starting circle of the outer layer Output: updated D—collection of drones, updated —reference y-coordinate for x direction filling.
|
3.4.5. Inner Layer Filling
| Algorithm 3 TwoNeighbours—Calculating the position of a third drone object based on the positions of its two neighbours |
Input: —two neighbouring drone objects Output: d—new drone object
|
| Algorithm 4 InnerXDirectionFilling—Filling inner layer along the x direction |
Input: d—a drone object that represents the starting circle of the inner layer Output: updated D—collection of drones, updated —reference y—coordinate for x direction filling.
|
3.4.6. The Region-Filling Algorithm
| Algorithm 5 Region Filling |
Input: Output:
|
3.5. Complexity Analysis of the Region Filling Algorithm
- is the coverage angle
- H is the maximum possible altitude
- H is the minimum possible altitude
3.6. Proof That Our Method Uses the Minimum Number of Drones
3.6.1. Deployment of the Initial Drone
3.6.2. Wastage of Coverage in FillAlongXAxis and FillAlongYAxis
3.6.3. Wastage of Coverage in TwoNeighbours
3.6.4. Wastage of Coverage in ThreeNeighbours
3.6.5. Wastage of Coverage in InnerXDirectionFilling and InnerYDirectionFilling
3.6.6. The Region Filling-Algorithm Minimizes the Number of Drones Required
4. Experiments and Results
4.1. Analysis of Results
4.1.1. Ratio of Horizontal Lift to Drag Ratio to Vertical Lift to Drag Ratio (W)
4.1.2. Area of the Region
4.1.3. Coverage Angle
4.1.4. Maximum Height ()
4.1.5. Number of Base Stations
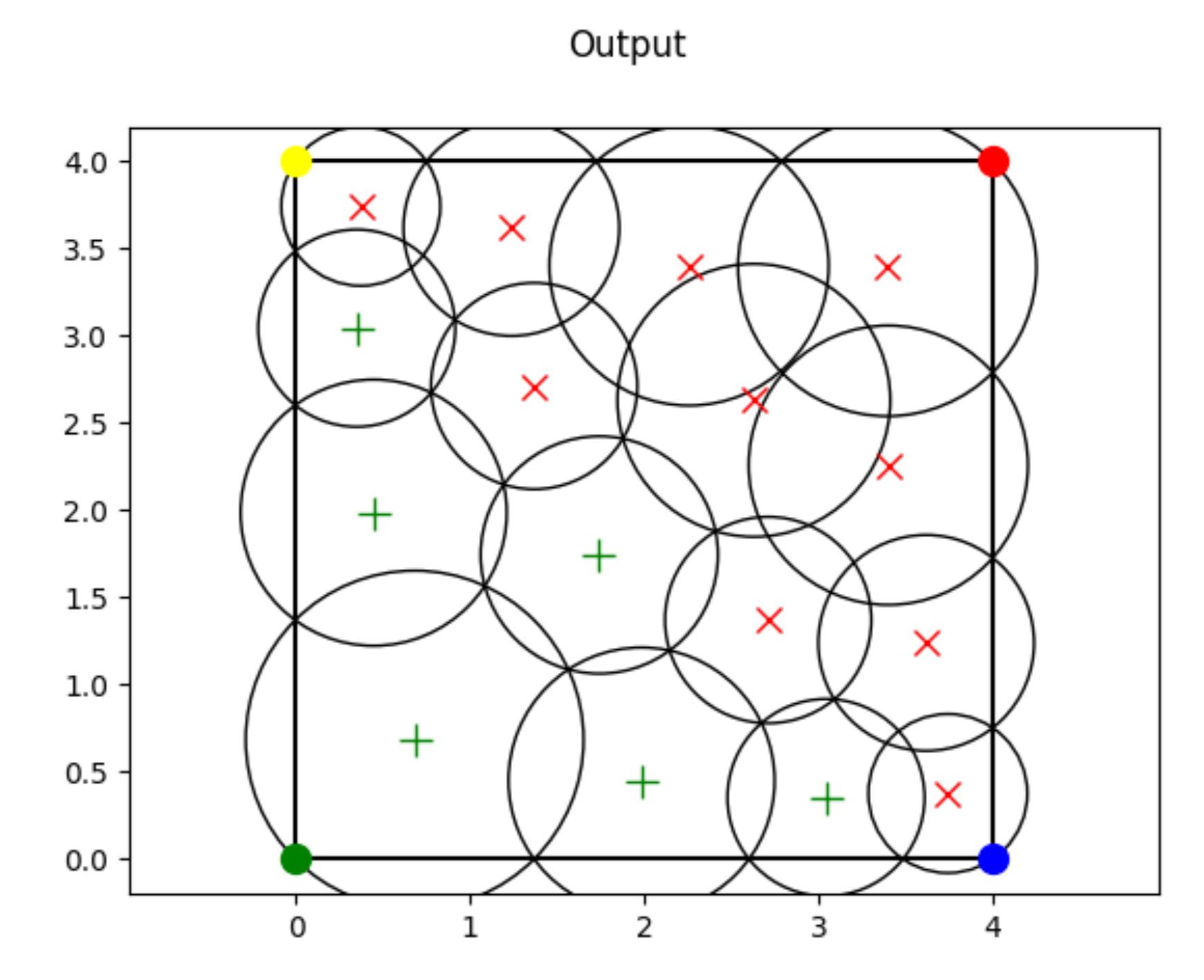
4.2. Simulation
5. Discussions
6. Conclusions
7. Future Work
- Here, we have considered only perfect circular-shaped coverage for drones; we intend to engage in a detailed exploration of other shapes as well.
- The present work concentrates on the algorithm used to fill the area without voids using stationary drones. We intend to study the effects of achieving the same using moving drones. In addition, we may explore different technologies available for establishing and maintaining communication between the drones and base stations.
- A detailed comparison between the region-filling algorithm and other network coverage management methods should be explored.
Supplementary Materials
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
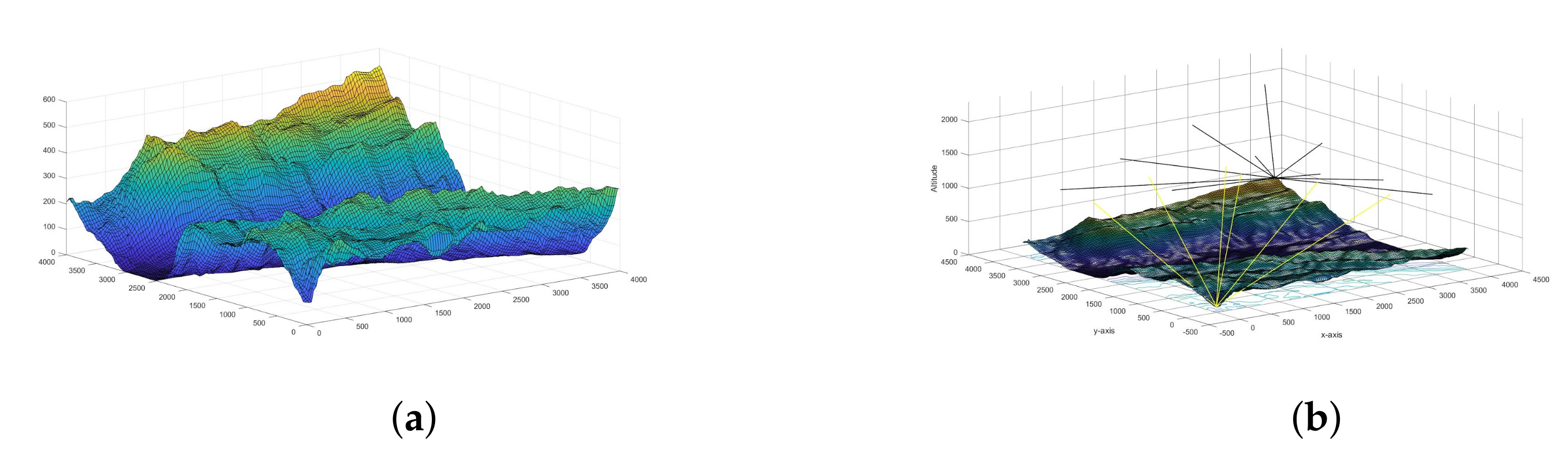
Appendix A. Data on Pettimudi
| Cartesian Coordinates () and Normalized Heights in km | Real World Coordinates () and Heights from the Sea Level in km | Radius of Coverage in km | Base Station | Leftover Energy in Wh | Hovering Time in Minutes |
|---|---|---|---|---|---|
| (0.6850012909668802, 0.6850012909668802, 1.9810872946905196) | (9.9975445782069, 76.93794986634965, 2.52708729469052) | 1.144338031 | 0 | 339.294 | 23.38707962 |
| (1.9863072120622192, 0.4500208730417653, 1.6521173291631104) | (9.99535120808547, 76.94980395247727, 2.1981173291631104) | 0.954314682 | 0 | 338.01825 | 23.13270969 |
| (3.0440939462526897, 0.35293290321067433, 1.3095049307901139) | (9.994416966351103, 76.9594446404037, 1.855504930790114) | 0.756411037 | 0 | 338.01825 | 23.13270969 |
| (3.742788025157351, 0.3762679343689235, 1.0910503229335835) | (9.994590335836122, 76.96581724258051, 1.6370503229335835) | 0.630224818 | 1 | 360.41475 | 27.59831517 |
| (0.4500208730417653, 1.9863072120622192, 1.5481173291631105) | (10.009320044652764, 76.93587672010516, 2.0941173291631108) | 0.894241027 | 0 | 342.93225 | 24.11250498 |
| (0.35293290321067433, 3.0440939462526897, 1.3035049307901139) | (10.01888693185655, 76.93504800175259, 1.849504930790114) | 0.752945249 | 0 | 338.30175 | 23.18923634 |
| (0.3762679343689235, 3.742788025157351, 1.1140503229335836) | (10.025201446811009, 76.93529828116637, 1.6600503229335837) | 0.643510337 | 1 | 359.328 | 27.38162967 |
| (1.7439562567843623, 1.7439562567843503, 1.481891136490049) | (10.007060435737923, 76.94766363480579, 2.027891136490049) | 0.855986705 | 0 | 339.294 | 23.38707962 |
| (2.7124246028936443, 1.3706564833549857, 1.355107375455865) | (10.003634231219198, 76.95647521198755, 1.901107375455865) | 0.782752436 | 1 | 359.0445 | 27.32510302 |
| (3.618532811839651, 1.2396785509335047, 1.146148156903163) | (10.00240158709933, 76.96473106479948, 1.6921481569031631) | 0.662051051 | 1 | 371.1405 | 29.73690682 |
| (1.37065648335483, 2.71242460289361, 1.2411073754558135) | (10.015834661655397, 76.94431150115088, 1.7871073754558136) | 0.716902468 | 1 | 364.431 | 28.3991094 |
| (1.239678550933715, 3.61853281183974, 1.3511481569032364) | (10.024032260677686, 76.94316581197926, 1.8971481569032365) | 0.780465468 | 1 | 361.45425 | 27.80557956 |
| (2.630328456811882, 2.630328456812093, 1.4423306425423421) | (10.015025145572809, 76.95579474007404, 1.9883306425423422) | 0.833135326 | 1 | 370.52625 | 29.61443241 |
| (3.4013205248344214, 2.2585005948062418, 1.63315625474712) | (10.011622647234047, 76.96280560529775, 2.17915625474712) | 0.943362172 | 1 | 363.0135 | 28.11647614 |
| (2.2585005948064087, 3.4013205248342473, 1.8341562547471535)) | (10.02201430185454, 76.95244553872685, 2.3801562547471535) | 1.059466064 | 1 | 353.51625 | 26.22283331 |
| (3.395089978241617, 3.395089978241617, 2.0140000000000002) | (10.021896870058129, 76.96281057227907, 2.5600000000000005) | 1.16334944 | 1 | 360.5490667 | 27.62509637 |

References
- Khaled, Z.E.; Mcheick, H. Case studies of communications systems during harsh environments: A review of approaches, weaknesses, and limitations to improve quality of service. Int. J. Distrib. Sens. Netw. 2019, 15, 9960. [Google Scholar] [CrossRef]
- Kamruzzaman, M.; Sarkar, N.I.; Gutierrez, J.; Ray, S.K. A study of IoT-based post-disaster management. In Proceedings of the 2017 International Conference on Information Networking (ICOIN), Da Nang, Vietnam, 11–13 January 2017; pp. 406–410. [Google Scholar] [CrossRef]
- Lefeuvre, F.; Tanzi, T. About radio science contribution to disaster management. In Proceedings of the 2014 XXXIth URSI General Assembly and Scientific Symposium (URSI GASS), Beijing, China, 16–23 August 2014; pp. 1–4. [Google Scholar] [CrossRef]
- Achu, A.L.; Joseph, S.; Aju, C.D.; Mathai, J. Preliminary analysis of a catastrophic landslide event on 6 August 2020 at Pettimudi, Kerala State, India. Landslides 2021, 18, 1459–1463. [Google Scholar] [CrossRef]
- Krishnakumar, G.; Raman, G.K. In Idukki, Living in Fear of Landslides. The Hindu Daily, August 29, 2020. Available online: https://www.thehindu.com/news/national/kerala/in-idukki-living-in-fear-of-landslides/article32468924.ece (accessed on 27 August 2021).
- Fatal Earthquake Hit the Chinese Province of Sichuan in May 2008 Disaster Management–How Satellite Communications and ND SatCom Technology Supported First Responders. Available online: https://www.ndsatcom.com/gfx/file/solutions/governmentCase_Study_Sichuan_earthquake_China_October_2008.pdf (accessed on 21 June 2021).
- Xu, J.; Zeng, F.; Liu, W.; Takahashi, T. Damage Detection and Level Classification of Roof Damage after Typhoon Faxai Based on Aerial Photos and Deep Learning. Appl. Sci. 2022, 12, 4912. [Google Scholar] [CrossRef]
- Ullah, F.; Khan, S.I.; Munawar, H.S.; Qadir, Z.; Qayyum, S. UAV Based Spatiotemporal Analysis of the 2019–2020 New South Wales Bushfires. Sustainability 2021, 13, 207. [Google Scholar] [CrossRef]
- Nikhil, N.; Shreyas, S.M.; Vyshnavi, G.; Yadav, S. Unmanned Aerial Vehicles (UAV) in Disaster Management Applications. In Proceedings of the 2020 Third International Conference on Smart Systems and Inventive Technology (ICSSIT), Tirunelveli, India, 20–22 August 2020; pp. 140–148. [Google Scholar] [CrossRef]
- Mototolea, D. A Study On The Actual And Upcoming Drone Communication Systems. In Proceedings of the 2019 International Symposium on Signals, Circuits and Systems (ISSCS), Iasi, Romania, 11–12 July 2019; pp. 1–4. [Google Scholar] [CrossRef]
- Liu, W.; Lis, K.; Salzmann, M.; Fua, P. Geometric and Physical Constraints for Drone-Based Head Plane Crowd Density Estimation. In Proceedings of the 2019 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS), Macau, China, 3–8 November 2019; pp. 244–249. [Google Scholar] [CrossRef]
- Morrison, K.T. Rapidly recovering from the catastrophic loss of a major telecommunications office. IEEE Commun. Mag. 2011, 49, 28–35. [Google Scholar] [CrossRef]
- Rabieekenari, L.; Sayrafian, K.; Baras, J.S. Autonomous relocation strategies for cells on wheels in public safety networks. In Proceedings of the 2017 14th IEEE Annual Consumer Communications Networking Conference (CCNC), IEEE, Las Vegas, NV, USA, 8–11 January 2017; pp. 41–44. [Google Scholar] [CrossRef]
- AT&T Network Disaster Recovery. Available online: https://www.business.att.com/solutions/family/network-services/network-disaster-recovery.html (accessed on 27 August 2021).
- Takahashi, T.; Jeong, B.; Okawa, M.; Akaishi, A.; Asai, T.; Katayama, N.; Akioka, M.; Yoshimura, N.; Toyoshima, M.; Miura, R.; et al. Disaster satellite communication experiments using WINDS and wireless mesh network. In Proceedings of the 2013 16th International Symposium on Wireless Personal Multimedia Communications (WPMC), Atlantic City, NJ, USA, 24–27 June 2013; pp. 1–4. [Google Scholar]
- Fotouhi, A.; Ding, M.; Hassan, M. Service on Demand: Drone Base Stations Cruising in the Cellular Network. In Proceedings of the 2017 IEEE Globecom Workshops (GC Wkshps), Singapore, 4–8 December 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Park, S.; Kim, K.; Kim, H.; Kim, H. Formation control algorithm of multi-UAV-based network infrastructure. Appl. Sci. 2018, 8, 1740. [Google Scholar] [CrossRef]
- Zhang, X.; Duan, L. Energy-Saving Deployment Algorithms of UAV Swarm for Sustainable Wireless Coverage. IEEE Trans. Veh. Technol. 2020, 69, 10320–10335. [Google Scholar] [CrossRef]
- Ruan, L.; Wang, J.; Chen, J.; Xu, Y.; Yang, Y.; Jiang, H.; Zhang, Y.; Xu, Y. Energy-efficient multi-UAV coverage deployment in UAV networks: A game-theoretic framework. China Commun. 2018, 15, 194–209. [Google Scholar] [CrossRef]
- Kumar, P.; Singh, P.; Darshi, S.; Shailendra, S. Analysis of Drone Assisted Network Coded Cooperation for Next Generation Wireless Network. IEEE Trans. Mob. Comput. 2021, 20, 93–103. [Google Scholar] [CrossRef]
- Mozaffari, M.; Saad, W.; Bennis, M.; Debbah, M. Drone-Based Antenna Array for Service Time Minimization in Wireless Networks. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Namvar, N.; Homaifar, A.; Karimoddini, A.; Maham, B. Heterogeneous UAV Cells: An Effective Resource Allocation Scheme for Maximum Coverage Performance. IEEE Access 2019, 7, 164708–164719. [Google Scholar] [CrossRef]
- Thibbotuwawa, A.; Nielsen, P.; Zbigniew, Z.; Bocewicz, G. Energy Consumption in Unmanned Aerial Vehicles: A Review of Energy Consumption Models and Their Relation to the UAV Routing. In Proceedings of the 39th International Conference on Information Systems Architecture and Technology–ISAT 2018; Springer: Berlin/Heidelberg, Germany, 2018; Volume 853. [Google Scholar]
- Theys, B.; Schutter, J.D. Forward flight tests of a quadcopter unmanned aerial vehicle with various spherical body diameters. Int. J. Micro Air Veh. 2020, 12. [Google Scholar] [CrossRef]
- Sundaresan, K.; Chai, E.; Chakraborty, A.; Rangarajan, S. SkyLiTE:End-to-end design of low-altitude UAV networks for providing LTE connectivity. arXiv 2018, arXiv:1802.06042. [Google Scholar]
- Panda, K.G.; Das, S.; Sen, D.; Arif, W. Design and Deployment of UAV-Aided Post-Disaster Emergency Network. IEEE Access 2019, 7, 102985–102999. [Google Scholar] [CrossRef]
- Li, J.; Lu, D.; Zhang, G.; Tian, J.; Pang, Y. Post-Disaster Unmanned Aerial Vehicle Base Station Deployment Method Based on Artificial Bee Colony Algorithm. IEEE Access 2019, 7, 168327–168336. [Google Scholar] [CrossRef]
- Ishigami, M.; Sugiyama, T. A Novel Drone’s Height Control Algorithm for Throughput Optimization in Disaster Resilient Network. IEEE Trans. Veh. Technol. 2020, 69, 16188–16190. [Google Scholar] [CrossRef]
- Shakhatreh, H.; Khreishah, A.; Ji, B. UAVs to the Rescue: Prolonging the Lifetime of Wireless Devices Under Disaster Situations. IEEE Trans. Green Commun. Netw. 2019, 3, 942–954. [Google Scholar] [CrossRef]
- Lyu, J.; Zeng, Y.; Zhang, R.; Lim, T.J. Placement Optimization of UAV-Mounted Mobile Base Stations. IEEE Commun. Lett. 2017, 21, 604–607. [Google Scholar] [CrossRef]
- Plachy, J.; Becvar, Z.; Mach, P.; Marik, R.; Vondra, M. Joint Positioning of Flying Base Stations and Association of Users: Evolutionary-Based Approach. IEEE Access 2019, 7, 11454–11463. [Google Scholar] [CrossRef]
- Ruzicka, M.; Volosin, M.; Gazda, J.; Maksymyuk, T.; Han, L.; Dohler, M. Fast and computationally efficient generative adversarial network algorithm for unmanned aerial vehicle–based network coverage optimization. Int. J. Distrib. Sens. Netw. 2022, 18. [Google Scholar] [CrossRef]
- Furutani, T.; Minami, M. Drones for Disaster Risk Reduction and Crisis Response. In Emerging Technologies for Disaster Resilience: Practical Cases and Theories; Sakurai, M., Shaw, R., Eds.; Springer: Singapore, 2021; pp. 51–62. [Google Scholar] [CrossRef]
- Chen, Y.; Cheng, W. Performance Analysis of RIS-equipped-UAV Based Emergency Wireless Communications. In Proceedings of the ICC 2022—IEEE International Conference on Communications, Seoul, Korea, 16–20 May 2022; pp. 255–260. [Google Scholar] [CrossRef]
- Mohamed, E.M.; Hashima, S.; Hatano, K. Energy Aware Multiarmed Bandit for Millimeter Wave-Based UAV Mounted RIS Networks. IEEE Wirel. Commun. Lett. 2022, 11, 1293–1297. [Google Scholar] [CrossRef]
- Hashima, S.; Hatano, K.; Mohamed, E.M. Multiagent Multi-Armed Bandit Schemes for Gateway Selection in UAV Networks. In Proceedings of the 2020 IEEE Globecom Workshops (GC Wkshps), IEEE, Taipei, Taiwan, 7–11 December 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Belkadi1, A.; Ciarletta, L.; Theilliol, D. Particle swarm optimization method for the control of a fleet of Unmanned Aerial Vehicles. J. Phys. Conf. Ser. 2015, 659, 012015. [Google Scholar] [CrossRef]
- Mesquita, R.; Gaspar, P.D. A Path Planning Optimization Algorithm Based on Particle Swarm Optimization for UAVs for Bird Monitoring and Repelling–Simulation Results. In Proceedings of the 2020 International Conference on Decision Aid Sciences and Application (DASA), Sakheer, Bahrain, 8–9 November 2020; pp. 1144–1148. [Google Scholar] [CrossRef]
- Li, M.; Du, W.; Nian, F. An Adaptive Particle Swarm Optimization Algorithm Based on Directed Weighted Complex Network. Math. Probl. Eng. 2014, 9, 2232. [Google Scholar] [CrossRef]
- Sewak, M.; Sahay, S.K.; Rathore, H. Comparison of Deep Learning and the Classical Machine Learning Algorithm for the Malware Detection. In Proceedings of the 2018 19th IEEE/ACIS International Conference on Software Engineering, Artificial Intelligence, Networking and Parallel/Distributed Computing (SNPD), Busan, Korea, 27–29 June 2018; pp. 293–296. [Google Scholar] [CrossRef]
- Latitude, Longitude and Coordinate System Grids. Available online: https://gisgeography.com/latitude-longitude-coordinates/ (accessed on 20 June 2021).
- Janssen, V. Understanding coordinate reference systems, datums and transformations. Int. J. Geoinformatics 2009, 5, 41–53. [Google Scholar]
- Ostrovsky, R.; Rabani, Y.; Schulman, L.J.; Swamy, C. The Effectiveness of Lloyd-Type Methods for the k-Means Problem. In Proceedings of the 2006 47th Annual IEEE Symposium on Foundations of Computer Science (FOCS’06), IEEE, Berkeley, CA, USA, 21–24 October 2006; pp. 165–176. [Google Scholar] [CrossRef]
- Varga, A.; Horning, A. An overview of the OMNeT++ simulation environment. In Proceedings of the Simutools’08–1st International Conference on Simulation Tools and Techniques for Communications, Networks and Systems & Workshops, ICST (Institute for Computer Sciences, Social-Informatics and Telecommunications Engineering), Brussels, Belgium, 3–7 March 2008; Volume 60, pp. 1–10. [Google Scholar]
- Kurt, A.; Saputro, N.; Akkaya, K.; Uluagac, A.S. Distributed Connectivity Maintenance in Swarm of Drones During Post-Disaster Transportation Applications. IEEE Trans. Intell. Transp. Syst. 2021, 22, 6061–6073. [Google Scholar] [CrossRef]














| Parameter | Description |
|---|---|
| m | Length of the region |
| n | Breadth of the region |
| Minimum altitude of a drone | |
| Maximum permissible height of a drone | |
| Threshold height for drone deployment | |
| Height of the lowest point in a circular region with left at and radius r ( is a sub Height Matrix, a subset of H) | |
| B | Initial energy of a drone |
| W | Ratio of horizontal lift to drag ratio to vertical lift to drag ratio |
| C | Energy dissipation rate per kilometer |
| Coverage angle of network drone in degrees |
| Parameter | Value |
|---|---|
| Length | 4 km |
| Width | 4 km |
| Normalized | 0.185 km |
| Height threshold | 0.05 km |
| Air density | 1.293 kg/m |
| Parameter | Value |
|---|---|
| Coverage angle | |
| Weight | 5 kg |
| Diameter (distance between two opposite rotors) | 0.4 m |
| Battery Capacity | 20,000 mAh |
| Battery voltage | 22.2 V |
| Battery energy | 444 Wh |
| Battery efficiency | 0.9 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Varghese, B.V.; Kannan, P.S.; Jayanth, R.S.; Thomas, J.; Shibu Kumar, K.M.B. Drone Deployment Algorithms for Effective Communication Establishment in Disaster Affected Areas. Computers 2022, 11, 139. https://doi.org/10.3390/computers11090139
Varghese BV, Kannan PS, Jayanth RS, Thomas J, Shibu Kumar KMB. Drone Deployment Algorithms for Effective Communication Establishment in Disaster Affected Areas. Computers. 2022; 11(9):139. https://doi.org/10.3390/computers11090139
Chicago/Turabian StyleVarghese, Bivin Varkey, Paravurumbel Sreedharan Kannan, Ravilal Soni Jayanth, Johns Thomas, and Kavum Muriyil Balachandran Shibu Kumar. 2022. "Drone Deployment Algorithms for Effective Communication Establishment in Disaster Affected Areas" Computers 11, no. 9: 139. https://doi.org/10.3390/computers11090139
APA StyleVarghese, B. V., Kannan, P. S., Jayanth, R. S., Thomas, J., & Shibu Kumar, K. M. B. (2022). Drone Deployment Algorithms for Effective Communication Establishment in Disaster Affected Areas. Computers, 11(9), 139. https://doi.org/10.3390/computers11090139






