Thermal Side-Channel Threats in Densely Integrated Microarchitectures: A Comprehensive Review for Cyber–Physical System Security
Abstract
1. Introduction
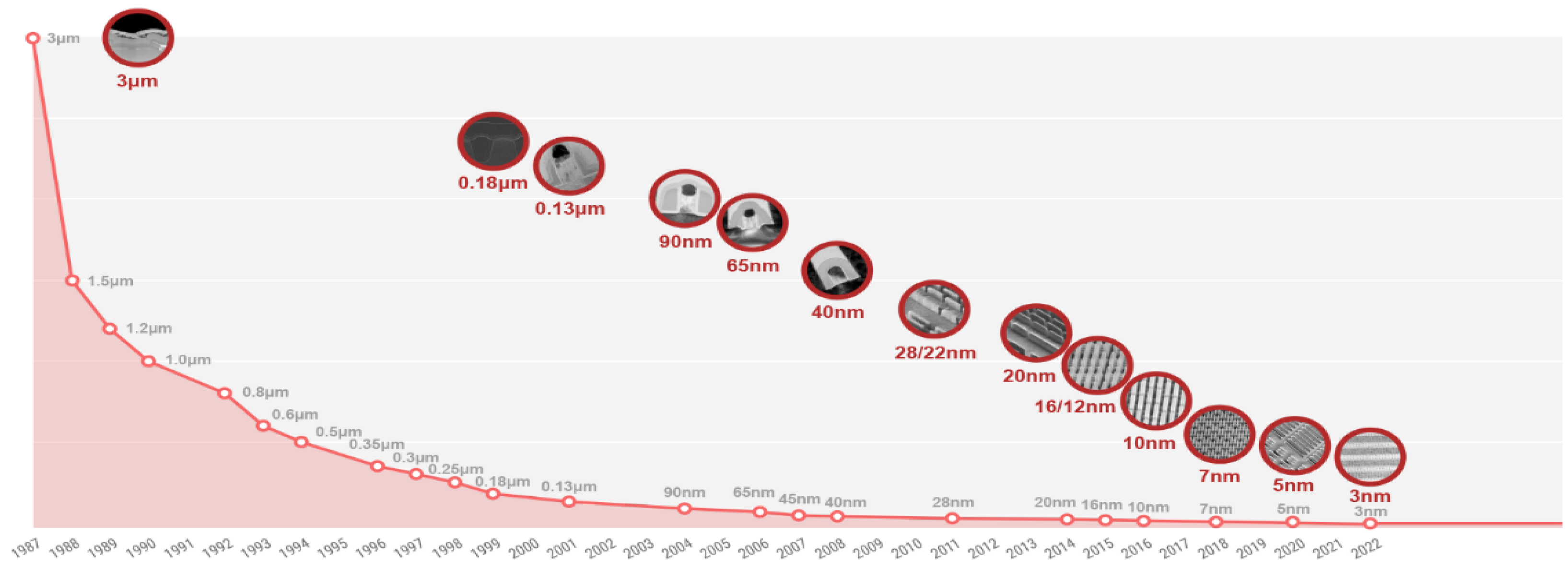
1.1. General Context of Miniaturization and Heterogeneous Integration
1.2. Persistent Thermal Management Challenges
1.3. Transition Toward Emerging Security Concerns: Thermal Side-Channel Attacks (TSCAs)
1.4. System-Level Impact of Thermal Side-Channel Vulnerabilities
1.5. Paper Objectives and Specific Contributions
2. Evolution of Microelectronics Integration: From One Chip to 3D and Heterogeneous Architectures
2.1. The Age of Monolithic (One-Chip) Integration
2.2. The Rise of Heterogeneous Integration
- System-in-Package (SiP): Multiple chips combined in a single package.
- Heterogeneous SoCs: Integration of diverse functions within a single die or closely coupled dies.
- Chiplets: Functional blocks separately manufactured and dynamically assembled on advanced interposers [32].
2.3. Three-Dimensional Integration: Leveraging the Vertical Dimension
2.4. Technical and Industrial Challenges in Microelectronics Integration: Long-Term Visions of Major Industry Players
- Cadence Design Systems: Their Integrity 3D-IC platform developed in collaboration with TSMC provides a holistic toolchain for co-designing, verifying, and optimizing complex 3D and chiplet-based architectures. By combining floorplanning, power and thermal integrity analysis, and multiphysics simulations in a single environment, such platforms allow for early detection of thermal hotspots and design rule violations, ultimately accelerating design cycles and enhancing reliability [39,40]. Cadence’s strategic vision, reflected in its alliance with TSMC 3DFabric technologies and the integration of AI-enhanced EDA tools like Celsius and Voltus, exemplifies how industrial ecosystems are responding with innovation-driven methodologies to overcome current integration bottlenecks
- Intel introduced Embedded Multi-die Interconnect Bridge (EMIB) and Foveros. EMIB facilitates high-bandwidth chiplet integration without a full silicon interposer, while Foveros enables true 3D logic-on-logic stacking. These platforms support flexible, high-performance assemblies critical for AI and data center applications [41].
- AMD led mainstream adoption of chiplet-based CPUs and GPUs using Infinity Fabric for high-bandwidth, coherent interconnects. Its 3D V-Cache, using direct copper-to-copper bonding, exemplifies how packaging can drive performance gains and better yield through small die architectures [42].
- Apple and TSMC partnered on commercializing highly integrated 2.5D/3D packaging with System-on-Integrated-Chip (SoIC) and Integrated Fan-Out (InFO). InFO packaging enables ultra-dense, low-profile, wafer-level integration pivotal for compact, power-efficient mobile processors, while SoIC brings fine-pitch heterogenous die stacking to mainstream consumer electronics [43].
- NVIDIA advanced High-Bandwidth Memory (HBM) integration with Chip on Wafer on Substrate (CoWoS), which bridges GPU logic and memory through silicon interposers. This design achieves the massive bandwidth and efficiency required by AI and machine learning workloads [44].
- Samsung developed X-Cube and H-Cube packaging, focusing on vertical stacking of memory and logic with fine-pitch TSVs. These platforms enable lower interconnect delays and dense logic memory integration, supporting demands of mobile, server, and AI applications [45].
2.5. Evolution of Integration Paradigms—A Summary and Insights
3. Thermal Challenges and Heat-Transfer Mechanisms in Densely Integrated Architecture
3.1. Heat-Transfer Mechanisms in Densely Integrated Architecture
3.1.1. Conduction
- k (W·m−1·K−1) is the thermal conductivity of the medium;
- (K·m−1) is the temperature gradient.
3.1.2. Convection
- Natural convection, where fluid motion arises from buoyancy forces due to temperature-dependent density differences.
- Forced convection, where an external device (fan, pump) imposes fluid motion.
- h (W·m−2·K−1) is the convective heat-transfer coefficient;
- A (m2) is the wetted surface area;
- (K) is the solid-surface temperature;
- (K) is the bulk fluid temperature.
3.1.3. Radiation
- is the surface emissivity (dimensionless);
- is the Stefan–Boltzmann constant;
- and (K) are the temperatures of the surface and surrounding environment, respectively;
- A (m2) is the radiating area.
3.2. Origin and Propagation of Thermal Stress in Monolithic and Heterogeneous IC Technologies
- Q: Thermal energy generated (in joules).
- I: Electric current flowing through the conductor (in amperes).
- R: Electrical resistance of the conductor (in ohms, ).
- t: Time during which the current flows (in seconds).
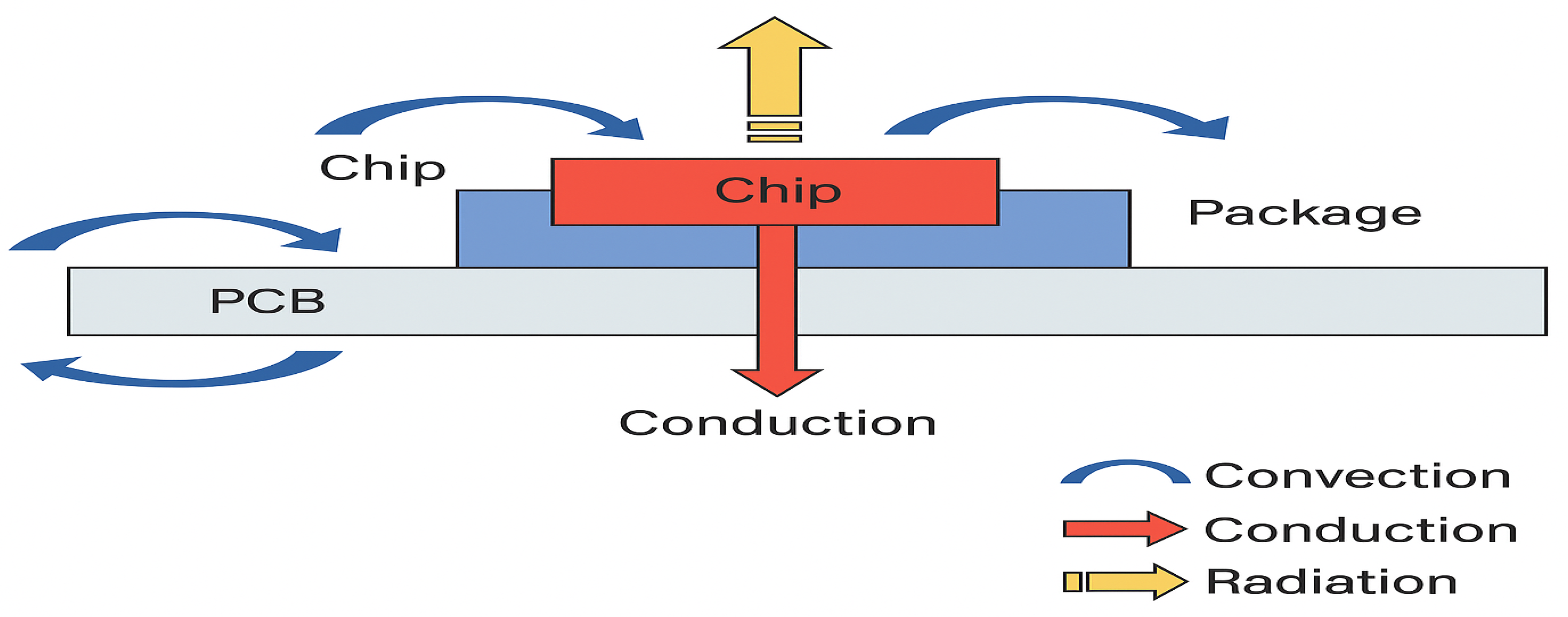
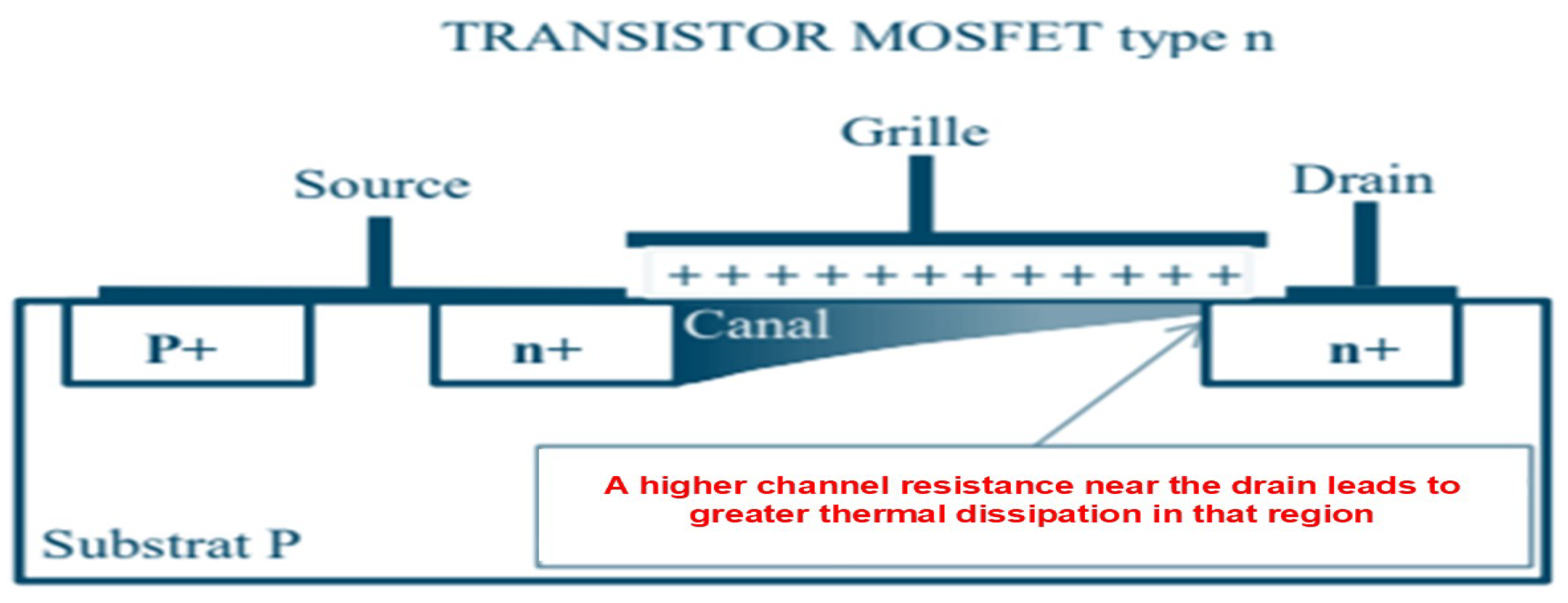
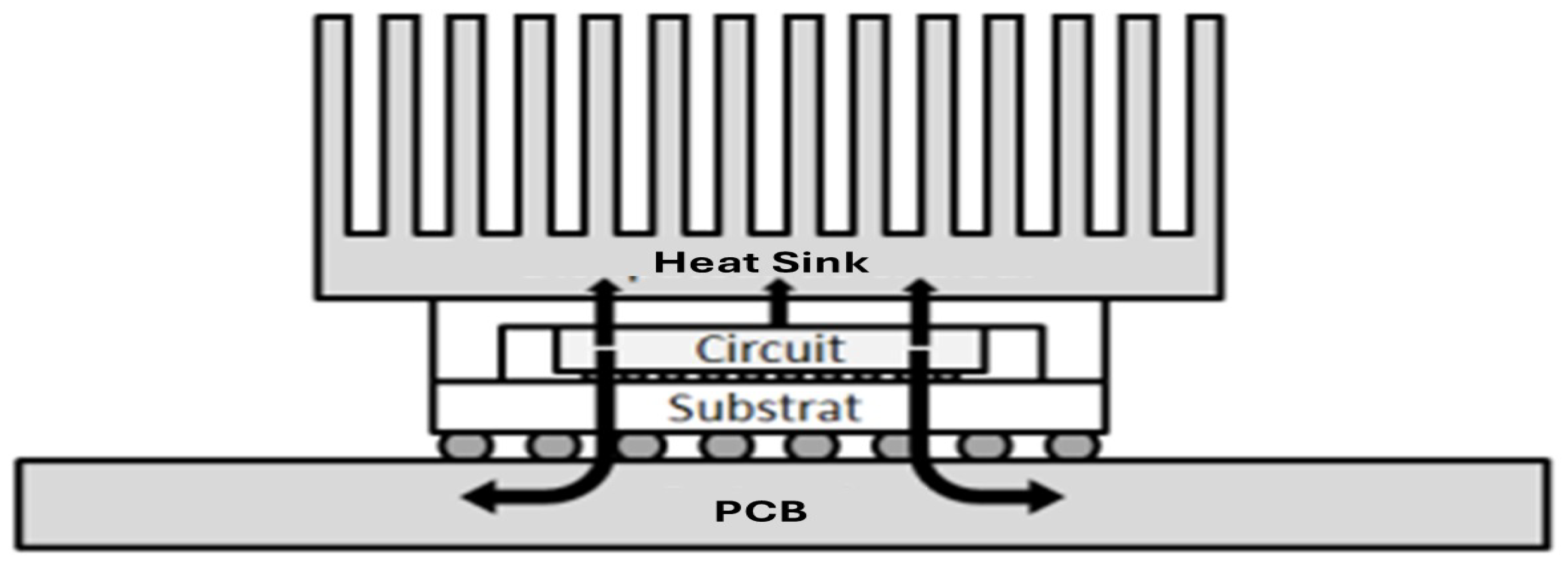
3.3. From Device Hotspots to Chip/Package Heat Flow
- An upward path from active regions through the interconnects to the passivation, package lid, and surrounding air;
- A lateral in-plane spreading within the silicon/metal layers toward neighboring blocks;
- A downward path into the silicon substrate and further to the PCB.
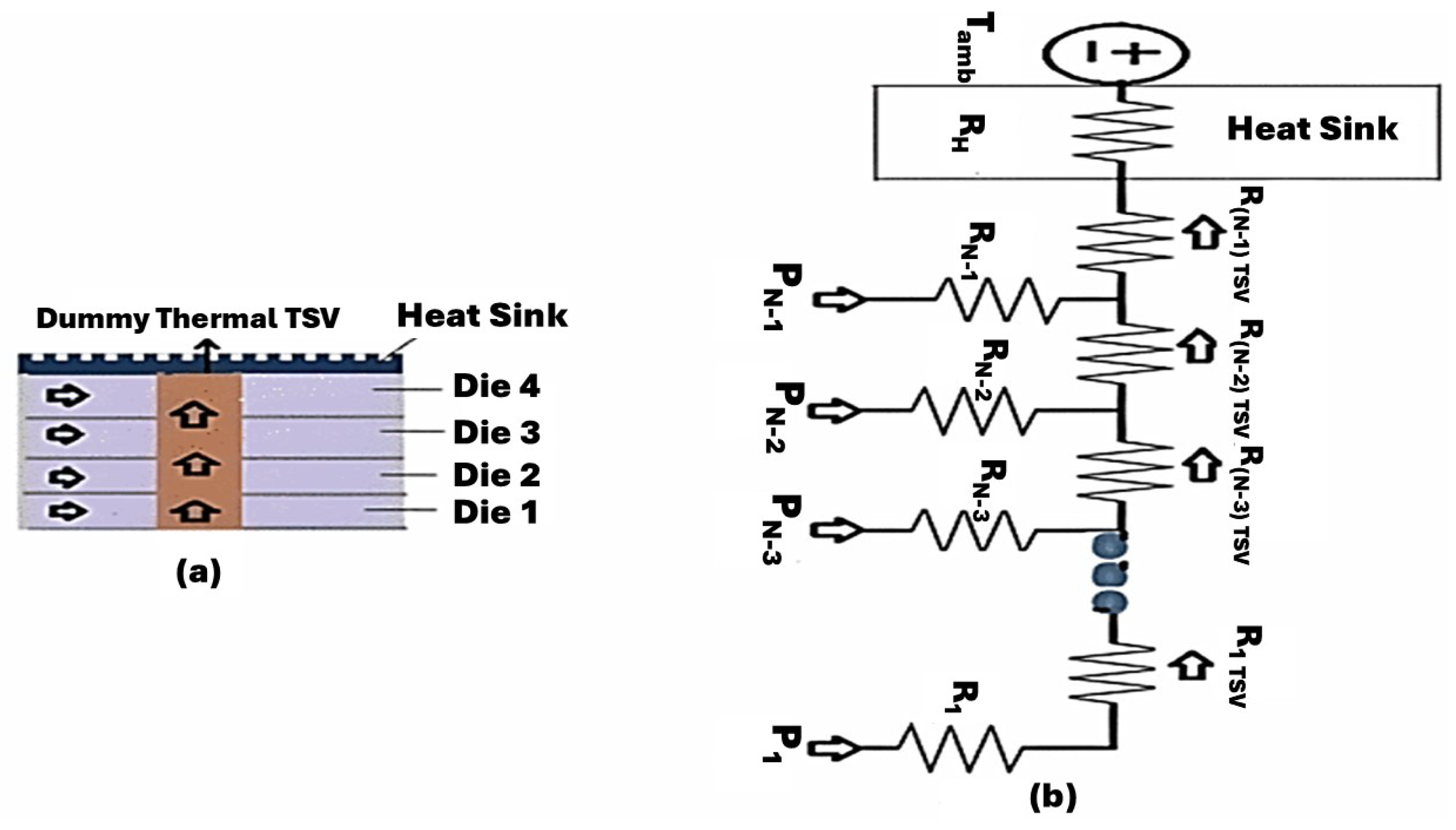
3.4. Thermal Impedance Representation of Dense Microarchitectures
3.5. Thermal Management Techniques for Densely Integrated Architectures
4. Thermal Side-Channel Attacks (TSCAs)
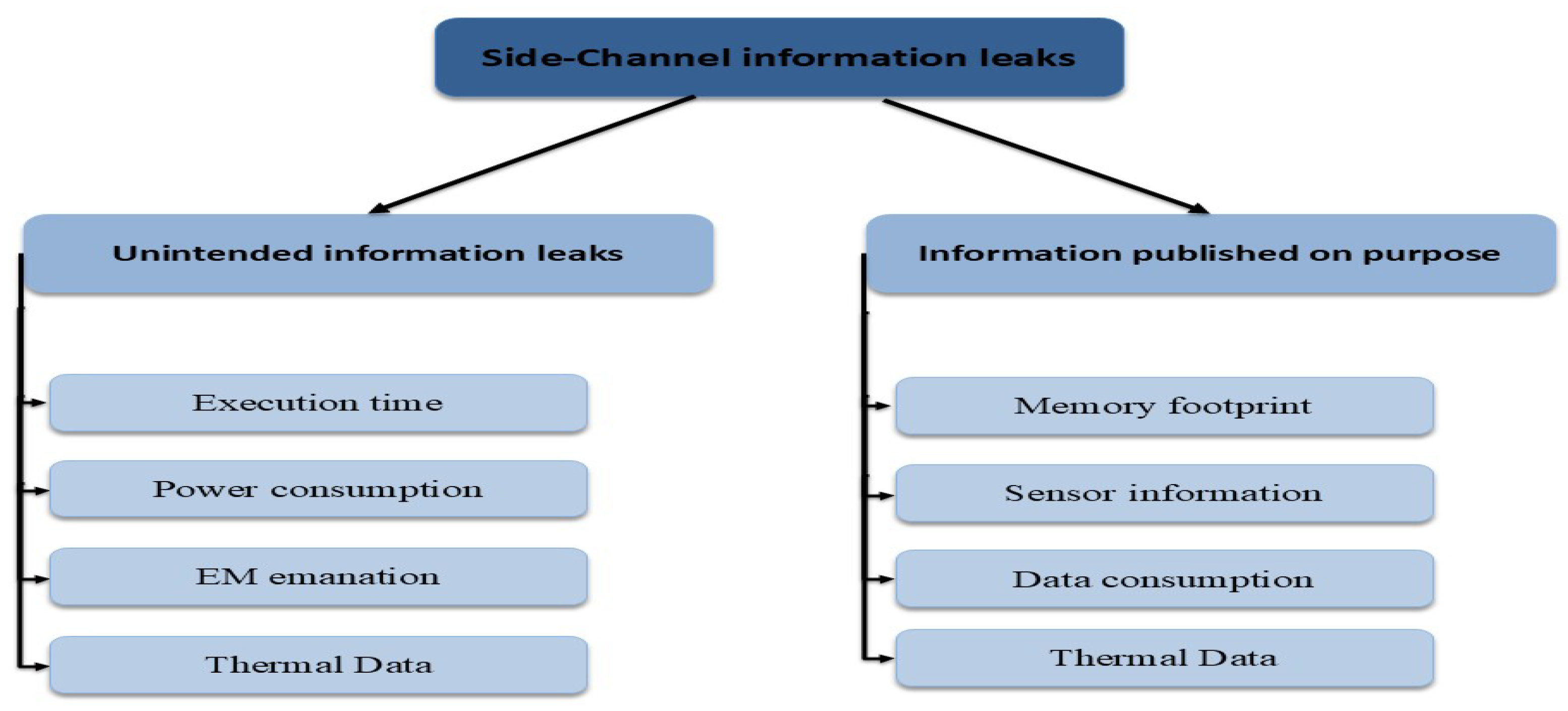
4.1. Background: Side-Channel Attacks (SCAs): Definitions, Taxonomy, and Scope
- Active (fault-induced) channels: the attacker injects faults (e.g., clock/voltage glitches, overheating) to force incorrect behavior that reveals secrets [75].
- Degree of invasiveness: non-invasive (no opening/modification of the device), semi-invasive (limited exposure, e.g., delidding for closer sensing), invasive (direct silicon-level intervention) [79].
- Access vector: proximal hardware probing (contact or infrared (IR)), software-only observation (reading on-die (on-chip) sensors or thermal interrupts through the operating system (OS)), or co-resident processes on the same platform [69].
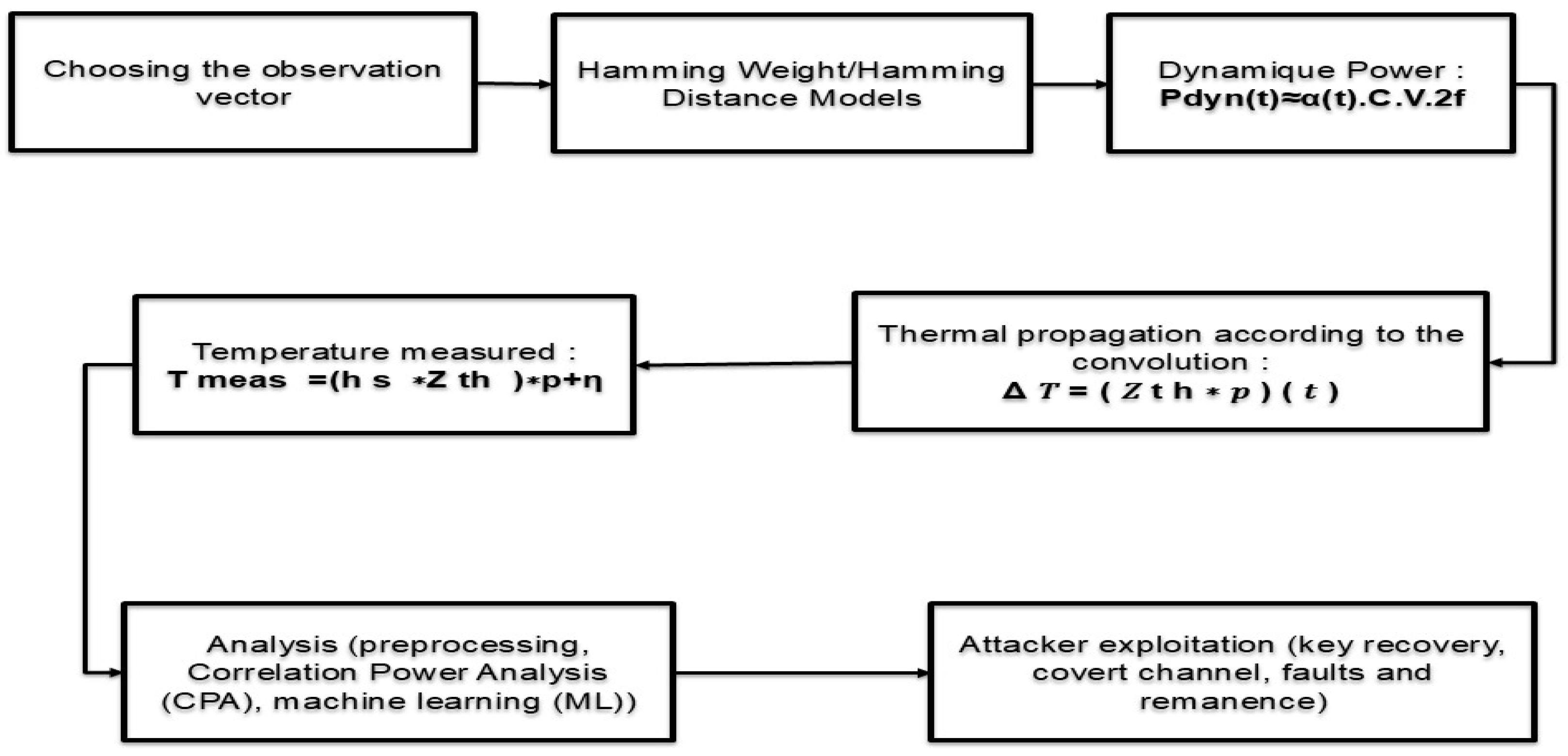
4.2. The Mechanistic View of Thermal Side Channels (TSCs): From Observation Vector to Exploitation
4.2.1. From the Observation Point to an Exploitable Signal
4.2.2. From Data-Dependent Activity to Power
4.2.3. From Power to Temperature Along the Thermal Chain
4.2.4. From Physical Temperature to What the Attacker Sees
4.2.5. From the Trace to Inference
4.2.6. From Inference to Exploitation
4.2.7. End-to-End Exploitation Chain of a Thermal Side-Channel Attack (TSCA)
4.3. Recent Thermal Side-Channel Attacks (2015–2025): Observation Vectors, Platforms, and Outcomes
4.3.1. Software TSCAs on CPUs via Operating System Exposed Temperature Sensors and Thermal Events
4.3.2. Co-Resident TSCAs on Densely Integrated Architectures and Accelerators
4.3.3. Mobile TSCAs and Android Thermal Telemetry
4.3.4. TSCAs for Cryptography and Machine Learning
5. CPS Security Implications of Thermal Side-Channel Attacks (TSCAs)
5.1. Understanding CPS and the Rising Priority of CPS Security
5.2. Nested Dependencies Between CPS Security and Thermal Side-Channel Defenses
5.3. Case Study—Industrial Control (PLC): Thermal Side-Channels and CPS Security
5.4. Institutional Roles and Strategic Investments Relevant to CPS Security
5.4.1. Department of Homeland Security (DHS)
5.4.2. National Science Foundation (NSF)
5.4.3. Regional Artificial Intelligence Initiative and Cyber–Physical Resilience Program (RAII)
5.4.4. Relevance to This Review
6. Future Directions
Open Research Directions: Digital Twins and Artificial Intelligence
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| 3D-IC | Three-Dimensional Integrated Circuit |
| AI | Artificial Intelligence |
| CNN | Convolutional Neural Network |
| CMOS | Complementary Metal–Oxide–Semiconductor |
| CPA | Correlation Power Analysis |
| CPS | Cyber–Physical System(s) |
| CPU | Central Processing Unit |
| CISA | Cybersecurity and Infrastructure Security Agency |
| DHS | Department of Homeland Security |
| DRAM | Dynamic Random-Access Memory |
| DT | Digital Twin |
| DTDF | Digital Twin Description Framework |
| DVFS | Dynamic Voltage and Frequency Scaling |
| EM | Electromagnetic |
| FPGA | Field-Programmable Gate Array |
| FET | Field-Effect Transistor |
| GPU | Graphics Processing Unit |
| IC | Integrated Circuit |
| IR | Infrared |
| IRT | Infrared Thermography |
| IT | Information Technology |
| JEDEC | Joint Electron Device Engineering Council |
| ML | Machine Learning |
| MPSoC | Multiprocessor System-on-Chip |
| NSF | National Science Foundation |
| OS | Operating System |
| OT | Operational Technology |
| PoP | Package-on-Package |
| RAII | Regional Artificial Intelligence Initiative program |
| RC | Resistance-Capacitance (thermal RC network) |
| SCA | Side-Channel Attack |
| SiP | System-in-Package |
| SoC | System-on-Chip |
| TSCA | Thermal Side-Channel Attack |
| TSV | Through-Silicon Via |
| TTSV | Thermal Through-Silicon Via |
References
- TSMC Technology Roadmap. Available online: https://www.tsmc.com/english/dedicatedFoundry/technology/logic/l_2nm (accessed on 19 August 2025).
- UniversityWafer, Inc. Moore’s Law and the Future of Semiconductor Scaling. Available online: https://www.universitywafer.com/moores-law.html (accessed on 19 August 2025).
- Intel 20A and 18A Roadmap. Available online: https://newsroom.intel.com/press-kit/intel-foundry-direct-connect-2025 (accessed on 19 August 2025).
- Samsung Electronics. Samsung Electronics to Provide Turnkey Semiconductor Solutions with 2nm GAA Process. Available online: https://news.samsung.com/global/samsung-electronics-to-provide-turnkey-semiconductor-solutions-with-2nm-gaa-process-and-2-5d-package-to-preferred-networks (accessed on 19 August 2025).
- TechHQ. The Semiconductor Industry Is “Near Its Limit,” Says Nvidia CEO. Available online: https://techhq.com/news/the-semiconductor-industry-is-near-its-limit-says-nvidia-ceo/#:~:text=The%20semiconductor%20industry%20is%20at%20a%20point%20where,to%20find%20limits%20and%20we%E2%80%99re%20at%20atomic%20scales.%E2%80%9D (accessed on 19 August 2025).
- The Chip Letter. Huang’s Law. Available online: https://thechipletter.substack.com/p/huangs-law?img=https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F248192af-2b47-4fb1-add1-74ada6f133fb_2400x1350.jpeg&open=false (accessed on 19 August 2025).
- Cirstea, M.; Benkrid, K.; Dinu, A.; Ghiriti, R.; Petreus, D. Digital Electronic System-on-Chip Design: Methodologies, Tools, Evolution, and Trends. Micromachines 2024, 15, 247. [Google Scholar] [CrossRef]
- Zhao, Y.; Zou, L.; Yu, B. Invited: Physical Design for Advanced 3D ICs: Challenges and Solutions. In Proceedings of the 2025 International Symposium on Physical Design, Austin, TX, USA, 16–19 March 2025; pp. 209–216. [Google Scholar]
- Lau, J.H. Recent advances and trends in chiplet design and heterogeneous integration packaging. J. Electron. Packag. 2024, 146, 010801. [Google Scholar] [CrossRef]
- Wang, H.; Ma, J.; Yang, Y.; Gong, M.; Wang, Q. A Review of System-in-Package Technologies: Application and Reliability of Advanced Packaging. Micromachines 2023, 14, 1149. [Google Scholar] [CrossRef] [PubMed]
- Rosenfeld, V.; Breß, S.; Markl, V. Query Processing on Heterogeneous CPU/GPU Systems. ACM Comput. Surv. 2022, 55, 1–38. [Google Scholar] [CrossRef]
- Dang, K.N.; Ben Ahmed, A.; Ben Abdallah, A.; Tran, X.-T. Thermal Distribution and Reliability Prediction for 3D Networks-on-Chip. VNU J. Sci. Comput. Sci. Commun. Eng. 2020, 36, 1. [Google Scholar] [CrossRef]
- Lu, L.; Zhu, J.; Li, Y.; Nagarajan, A.; Liu, J.; Shiau, S.Y.; Ai, X. 3D-IC In-Design Thermal Analysis and Optimization. In Proceedings of the 2024 23rd IEEE Intersociety Conference on Thermal and Thermomechanical Phenomena in Electronic Systems (ITherm), Aurora, CO, USA, 28–31 May 2024; pp. 1–5. [Google Scholar]
- Wang, C.; Huang, X.-J.; Vafai, K. Analysis of Hotspots and Cooling Strategy for Multilayer Three-Dimensional Integrated Circuits. Appl. Therm. Eng. 2021, 186, 116336. [Google Scholar] [CrossRef]
- Sanipini, V.K.; Rakesh, B.; Chamanthula, A.J.; Santoshi, N.; Gudivada, A.A.; Panigrahy, A.K. Thermal Management in TSV Based 3D IC Integration: A Survey. Mater. Today Proc. 2021, 45, 1742–1746. [Google Scholar] [CrossRef]
- Chaudhuri, D.; Nandi Das, D.; Rahaman, H.; Ghosh, T. Heat Mitigation in 3D ICs by Improvised TTSV Structure. In Proceedings of the International Symposium on Devices, Circuits and Systems (ISDCS), Howrah, India, 4–6 March 2020; pp. 1–4. [Google Scholar]
- Guo, F.; Suo, Z.-J.; Xi, X.; Bi, Y.; Li, T.; Wang, C.; Su, K.; Zou, X.; Li, R. Recent Developments in Thermal Management of 3D ICs: A Review. IEEE Access 2025, 13, 94286–94301. [Google Scholar] [CrossRef]
- Abdullah, M.F.; Lee, H.W. Technology review of CNTs TSV in 3D IC and 2.5 D packaging: Progress and challenges from an electrical viewpoint. Microelectron. Eng. 2024, 290, 112189. [Google Scholar] [CrossRef]
- Dai, W.; Wang, Y.; Li, M.; Chen, L.; Yan, Q.; Yu, J.; Jiang, N.; Lin, C. 2D Materials-Based Thermal Interface Materials: Structure, Properties, and Applications. Adv. Mater. 2024, 36, 37. [Google Scholar] [CrossRef]
- Benelhaouare, A.Z.; Oumlaz, M.; Oukaira, A.; Lakhssassi, A. Analytical and Numerical Modeling of the Thermal Performance of 3D System-in-Package (SiP). In Proceedings of the International Conference on Electrical, Computer and Energy Technologies (ICECET), Cape Town, South Africa, 16–17 November 2023; pp. 1–5. [Google Scholar]
- Salvi, S.S.; Jain, A. A Review of Recent Research on Heat Transfer in Three-Dimensional Integrated Circuits (3-D ICs). IEEE Trans. Compon. Packag. Manuf. Technol. 2021, 11, 2246–2296. [Google Scholar] [CrossRef]
- Singh, N.; Srivastava, K.; Kumar, A.; Yadav, N.; Yadav, A.; Dubey, S.; Singh, R.; Gehlot, A.; Verma, A.S.; Gupta, N.; et al. Challenges and opportunities in engineering next-generation 3D microelectronic devices: Improved performance and higher integration density. Nanoscale Adv. 2024, 6, 6044–6060. [Google Scholar] [CrossRef]
- Vasilas, T.; Bacila, C.; Brad, R. Contre la chaleur: Détection des attaques d’appels système via un canal latéral thermique. Future Internet 2024, 16, 301. [Google Scholar] [CrossRef]
- Benelhaouare, A.Z.; Mellal, I.; Oumlaz, M.; Lakhssassi, A. Mitigating Thermal Side-Channel Vulnerabilities in FPGA-Based SiP Systems Through Advanced Thermal Management and Security Integration Using Thermal Digital Twin (TDT) Technology. Electronics 2024, 13, 4176. [Google Scholar] [CrossRef]
- Wurm, J.; Jin, Y.; Liu, Y.; Hu, S.; Heffner, K.; Rahman, F.; Tehranipoor, M. Introduction to Cyber-Physical System Security: A Cross-Layer Perspective. IEEE Trans. Multi-Scale Comput. Syst. 2017, 3, 215–227. [Google Scholar] [CrossRef]
- Baird, A.; Panda, A.; Pearce, H.; Pinisetty, S.; Roop, P. Scalable Security Enforcement for Cyber-Physical Systems. IEEE Access 2024, 12, 14385–14410. [Google Scholar] [CrossRef]
- Lu, L.C. Semiconductor Evolution for Chip and System Design—From 2D Scaling to 3D Heterogeneous Integration. In Proceedings of the International Symposium on VLSI Design, Automation and Test (VLSI-DAT), Hsinchu, Taiwan, 18–21 April 2022; p. 1. [Google Scholar]
- Wang, A.; Chen, Q.; Li, C.; Lu, F.; Wang, C.; Zhang, F.; Wang, X.S.; Ng, J.; Xie, Y.H.; Ma, R. More-Than-Moore: 3D Heterogeneous Integration into CMOS Technologies. In Proceedings of the IEEE 12th International Conference on Nano/Micro Engineered and Molecular Systems (NEMS), Los Angeles, CA, USA, 9–12 April 2017; pp. 1–4. [Google Scholar]
- The Advantages and Disadvantages of Integrated Circuit Technology. Available online: https://www.dhgate.com/blog/the-advantages-and-disadvantages-of-integrated-circuit-technology-c/?msockid=184d8da8432665051f4a984b42e76433 (accessed on 19 August 2025).
- imec. CMOS 2.0: Bringing Heterogeneity Inside the System-on-Chip. Available online: https://www.imec-int.com/en/articles/cmos-20-bringing-heterogeneity-inside-system-chip (accessed on 19 August 2025).
- Li, C.; Pan, Z.; Li, X.; Hao, W.; Miao, R.; Wang, A. Selective Overview of 3D Heterogeneity in CMOS. Nanomaterials 2022, 12, 2340. [Google Scholar] [CrossRef]
- Li, T.; Hou, J.; Yan, J.; Liu, R.; Yang, H.; Sun, Z. Chiplet Heterogeneous Integration Technology—Status and Challenges. Electronics 2020, 9, 670. [Google Scholar] [CrossRef]
- Fischer, A.C.; Forsberg, F.; Lapisa, M.; Bleiker, S.J.; Stemme, G.; Roxhed, N.; Niklaus, F. Integrating MEMS and ICs. Microsyst. Nanoeng. 2015, 1, 1. [Google Scholar] [CrossRef]
- Jeong, J.; Geum, D.-M.; Kim, S. Heterogeneous and Monolithic 3D Integration Technology for Mixed-Signal ICs. Electronics 2022, 11, 3013. [Google Scholar] [CrossRef]
- Zhang, S.; Li, Z.; Zhou, H.; Li, R.; Wang, S.; Paik, K.W.; He, P. Challenges and Recent Prospectives of 3D Heterogeneous Integration. e-Prime-Adv. Electr. Eng. Electron. Energy 2022, 2, 100052. [Google Scholar] [CrossRef]
- Lee, K.-W. 3-D Hetero-Integration Technologies for Multifunctional Convergence Systems. J. Microelectron. Packag. Soc. 2015, 22, 11–19. [Google Scholar] [CrossRef]
- Wang, C.; Xu, Q.; Nie, C.; Cao, H.; Liu, J.; Li, Z. An Efficient Thermal Model of Chiplet Heterogeneous Integration System for Steady-State Temperature Prediction. Microelectron. Reliab. 2023, 146, 115006. [Google Scholar] [CrossRef]
- Lau, J.H. State-of-the-Art and Outlooks of Chiplets Heterogeneous Integration and Hybrid Bonding. Int. Symp. Microelectron. 2021, 2021, 49–59. [Google Scholar] [CrossRef]
- Cadence Design Systems. Integrity 3D-IC Platform (Datasheet). Available online: https://www.cadence.com/en_US/home/resources/datasheets/integrity-3d-ic-platform-ds.html (accessed on 19 August 2025).
- Cadence Design Systems. 3D IC: Chip-Centric Power & Thermal Integrity (Webinar). Available online: https://www.cadence.com/en_US/home/resources/on-demand-webinars/3d-ic-chip-centric-power-thermal-integrity.html (accessed on 19 August 2025).
- Intel. Intel Advanced Packaging Technology Ensures High Quality & Reliability. Available online: https://www.intel.com/content/www/us/en/content-details/826148/quality-reliability-vol-6-intel-advanced-packaging-technology-ensures-high-quality-reliability.html (accessed on 19 August 2025).
- AMD. Blogs. Available online: https://www.amd.com/en/search/blogs.html (accessed on 19 August 2025).
- TSMC-SoIC. Available online: https://3dfabric.tsmc.com/english/dedicatedFoundry/technology/SoIC.htm (accessed on 19 August 2025).
- TrendForce. Press Center. Available online: https://www.trendforce.com/presscenter/news/20240416-12119.html (accessed on 19 August 2025).
- Samsung Semiconductor. Samsung Advanced Packaging Helps Customers Bring Their Own Architecture. Available online: https://semiconductor.samsung.com/news-events/tech-blog/samsung-advanced-packaging-helps-customers-bring-their-own-architecture/ (accessed on 19 August 2025).
- He, Z.; Yan, Y.; Zhang, Z. Thermal Management and Temperature Uniformity Enhancement of Electronic Devices by Micro Heat Sinks: A Review. Energy 2021, 216, 119223. [Google Scholar] [CrossRef]
- Yeh, L.T. Review of heat transfer technologies in electronic equipment. J. Electron. Packag. 1995, 117, 333–339. [Google Scholar] [CrossRef]
- Saydé, M. Caractérisations Thermiques par Thermographie IR et Méthode de Stabilisation Thermique Cellulaire par Impact de Jets d’air Pour les Détecteurs de Tomographie par émission de Positrons à Base de Photodiodes à Avalanche. Ph.D. Dissertation, Université du Québec en Outaouais, Gatineau, QC, Canada, 2020. [Google Scholar]
- Lienhard, J.I.; Lienhard, J. DOE Fundamentals Handbook: Thermodynamics, Heat Transfer, and Fluid Flow; US Department of Energy: Washington, DC, USA, 2008. [Google Scholar]
- Bar-Cohen, A. Encyclopedia Of Thermal Packaging, Set 2: Thermal Packaging Tools (A 4-volume Set); World Scientific: Hackensack, NJ, USA, 2014. [Google Scholar]
- Norazlina, M.S.; Chakravarthii, M.D.; Shanmugan, S.; Mutharasu, D.; Shahrom, M. Heat Transfer Enhancement in MOSFET Mounted on Different FR4 Substrates by Thermal Transient Measurement. Chin. Phys. B 2017, 26, 098901. [Google Scholar] [CrossRef]
- KKoizumi, H. Ohm’s Law, Joule Heat, and Planckian Dissipation. arXiv 2025, arXiv:2501.01797. [Google Scholar]
- Uyemura, J.P. Introduction to VLSI Circuits and Systems; Georgia Institut of Technology: Atlanta, GA, USA, 2002. [Google Scholar]
- Tap, H.; Tan, R.P.; Bernal, O.; Calmon, P.F.; Rouabhi, C.; Capello, C.; d’Aguerre, P.B.; Gessinn, F.; Respaud, M. De la conception à la fabrication de circuits intégrés en technologie CMOS. J3eA 2019, 18, 1019. [Google Scholar] [CrossRef]
- Oukaira, A.; Oumlaz, M.; Zbitou, J.; Lakhssassi, A. Integrated thermal management strategies for 3D chip stacking with through-silicon vias (TSV). In Proceedings of the IEEE 4th International Conference on Innovative Research in Applied Science, Engineering and Technology (IRASET), Fez, Morocco, 16–17 May 2024; pp. 1–4. [Google Scholar]
- Köroğlu, Ç.; Pop, E. High Thermal Conductivity Insulators for Thermal Management in 3D Integrated Circuits. IEEE Electron. Device Lett. 2023, 44, 496–499. [Google Scholar] [CrossRef]
- Sun, X.; Peng, D.; Cang, J.; Zhao, J.; Liu, Y.; Fang, J. Chiplet Multi-Objective Optimization Algorithm Based on Communication Consumption and Temperature. Electronics 2023, 12, 1604. [Google Scholar] [CrossRef]
- Wang, X.; Su, J.; Chen, D.; Li, D.; Li, G.; Yang, Y. Efficient Thermal-Stress Coupling Design of Chiplet-Based System with Coaxial TSV Array. Micromachines 2023, 14, 1493. [Google Scholar] [CrossRef]
- Feng, J.; Zhou, M.; Chen, C.; Wang, Q.; Cao, L. Thermal Interaction and Cooling of Electronic Device with Chiplet 2.5D Integration. Appl. Sci. 2024, 14, 8114. [Google Scholar] [CrossRef]
- Ju, L.; Jiang, P.; Ren, Y.; Liu, R.; Kong, Y.; Yun, S.; Ye, Y.; Jiao, B.; Hao, Q.; Sun, H. Overview of Research Progress and Application Prospects of Thermal Test Chips. Micromachines 2025, 16, 669. [Google Scholar] [CrossRef]
- Pfromm, L.; Kanani, A.; Sharma, H.; Solanki, P.; Tervo, E.; Park, J.; Doppa, J.R.; Pande, P.P.; Ogras, U.Y. MFIT: Multi-Fidelity Thermal Modeling for 2.5D and 3D Multi-Chiplet Architectures. arXiv, 2025; arXiv:2410.09188. [Google Scholar]
- Liu, Z.; Li, Y.; Hu, J.; Yu, X.; Shiau, S.; Ai, X.; Zeng, Z.; Zhang, Z. DeepOHeat: Operator Learning-based Ultra-fast Thermal Simulation in 3D-IC Design. In Proceedings of the 60th ACM/IEEE Design Automation Conference (DAC), San Francisco, CA, USA, 9–13 July 2023; pp. 1–6. [Google Scholar]
- Liao, S.; Huang, C.; Zhang, H.; Liu, S. Thermal Stress Study of 3D IC Based on TSV and Verification of Thermal Dissipation of STI. In Proceedings of the 22nd International Conference on Electronic Packaging Technology (ICEPT), Xiamen, China, 14–17 September 2021; pp. 1–5. [Google Scholar]
- Wang, Z.; Ye, G.; Li, X.; Xue, S.; Gong, L. Thermal–Mechanical Performance Analysis and Structure Optimization of the TSV in 3-D IC. IEEE Trans. Compon. Packag. Manuf. Technol. 2021, 11, 822–831. [Google Scholar] [CrossRef]
- Benelhaouare, A.Z.; Oukaira, A.; Oumlaz, M.; Lakhssassi, A. Efficient Thermal Management Strategies for 3D-SiP Architectures. In Proceedings of the 18th International Conference on Ubiquitous Information Management and Communication (IMCOM), Kuala Lumpur, Malaysia, 3–5 January 2024; pp. 1–5. [Google Scholar]
- MDPI. Statistical Data from the Journal Micromachines. Available online: https://www.mdpi.com/journal/micromachines/stats (accessed on 19 August 2025).
- Kocher, P.; Jaffe, J.; Jun, B. Differential Power Analysis. In Proceedings of the Annual International Cryptology Conference, Barbara, CA, USA, 15–19 August 1999; pp. 388–397. [Google Scholar]
- Mangard, S.; Oswald, E.; Popp, T. Power Analysis Attacks: Revealing the Secrets of Smart Cards; Springer: Boston, MA, USA, 2007. [Google Scholar]
- Lou, X.; Zhang, T.; Jiang, J.; Zhang, Y. A Survey of Microarchitectural Side-Channel Vulnerabilities, Attacks, and Defenses in Cryptography. ACM Comput. Surv. 2021, 54, 1–37. [Google Scholar] [CrossRef]
- Socha, P.; Miškovský, V.; Novotný, M. A Comprehensive Survey on the Non-Invasive Passive Side-Channel Analysis. Sensors 2022, 22, 8096. [Google Scholar] [CrossRef]
- Spreitzer, R.; Moonsamy, V.; Korak, T.; Mangard, S. Systematic Classification of Side-Channel Attacks: A Case Study for Mobile Devices. IEEE Commun. Surv. Tutorials 2017, 20, 465–488. [Google Scholar] [CrossRef]
- Kocher, P.C. Timing Attacks on Implementations of Diffie-Hellman, RSA, DSS, and Other Systems. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 18–22 August 1996; pp. 104–113. [Google Scholar]
- Peeters, E.; Standaert, F.X.; Quisquater, J.J. Power and Electromagnetic Analysis: Improved Model, Consequences and Comparisons. Integration 2007, 40, 52–60. [Google Scholar] [CrossRef]
- Hutter, M.; Schmidt, J.M. The Temperature Side Channel and Heating Fault Attacks. In Smart Card Research and Advanced Applications; Springer International Publishing: Cham, Switzerland, 2013; pp. 219–235. [Google Scholar]
- Yuce, B.; Schaumont, P.; Witteman, M. Fault Attacks on Secure Embedded Software: Threats, Design, and Evaluation. J. Hardw. Syst. Secur. 2018, 2, 111–130. [Google Scholar] [CrossRef]
- Ristenpart, T.; Tromer, E.; Shacham, H.; Savage, S. Hey, You, Get off of My Cloud: Exploring Information Leakage in Third-Party Compute Clouds. In Proceedings of the 16th ACM Conference on Computer and Communications Security (CCS), Chicago, IL, USA, 9–13 November 2009; pp. 199–212. [Google Scholar]
- Chen, S.; Xiong, W.; Xu, Y.; Li, B.; Szefer, J. Thermal Covert Channels Leveraging Package-on-Package DRAM. In Proceedings of the 18th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/13th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE), Rotorua, New Zealand, 5–8 August 2019; pp. 319–326. [Google Scholar]
- Tian, J.; Xiong, G.; Li, Z.; Gou, G. A survey of key technologies for constructing network covert channel. Secur. Commun. Netw. 2020, 1, 8892896. [Google Scholar] [CrossRef]
- Skorobogatov, S.P. Semi-Invasive Attacks–A New Approach to Hardware Security Analysis (No. UCAM-CL-TR-630). Ph.D. Thesis, Computer Laboratory, University of Cambridge, Cambridge, UK, 2005. [Google Scholar]
- Brier, E.; Clavier, C.; Olivier, F. Correlation Power Analysis with a Leakage Model. In Proceedings of the International Workshop on Cryptographic Hardware and Embedded Systems (CHES), Cambridge, MA, USA, 11–13 August 2004; pp. 16–29. [Google Scholar]
- Skadron, K.; Stan, M.R.; Huang, W.; Velusamy, S.; Sankaranarayanan, K.; Tarjan, D. Temperature-Aware Microarchitecture. ACM SIGARCH Comput. Archit. News 2003, 31, 2–13. [Google Scholar] [CrossRef]
- JEDEC Standard JESD51-4A; JESD51 Standard: Transient Dual Interface Test Method for the Measurement of the Thermal Resistance Junction-To-Case of Semiconductor Devices with Heat Flow Through a Single Path. JEDEC: Arlington, VA, USA, 2010.
- Ma, X.; Wang, Y.; Wang, Y.; Cai, X.; Han, Y. Survey on Chiplets: Interface, Interconnect and Integration Methodology. CCF Trans. High Perform. Comput. 2022, 4, 43–52. [Google Scholar] [CrossRef]
- Masti, R.J.; Rai, D.; Ranganathan, A.; Müller, C.; Thiele, L.; Capkun, S. Thermal Covert Channels on Multi-Core Platforms. In Proceedings of the 24th USENIX Security Symposium (USENIX Security’15), Washington, DC, USA, 12–14 August 2015; pp. 865–880. [Google Scholar]
- Bartolini, D.B.; Miedl, P.; Thiele, L. On the Capacity of Thermal Covert Channels in Multicores. In Proceedings of the Eleventh European Conference on Computer Systems (EuroSys), London, UK, 18–21 April 2016; pp. 1–16. [Google Scholar]
- Kim, T.; Shin, Y. ThermalBleed: A Practical Thermal Side-Channel Attack. IEEE Access 2022, 10, 25718–25731. [Google Scholar] [CrossRef]
- Zhang, X.; Zhang, Z.; Shen, Q.; Wang, W.; Gao, Y.; Yang, Z.; Wu, Z. Thermalscope: A Practical Interrupt Side Channel Attack Based on Thermal Event Interrupts. In Proceedings of the 61st ACM/IEEE Design Automation Conference (DAC), San Francisco, CA, USA, 23–27 June 2024; pp. 1–6. [Google Scholar]
- Mishra, N.; Dutta, T.L.; Shukla, S.; Chakraborty, A.; Mukhopadhyay, D. Too Hot to Handle: Novel Thermal Side-Channel in Power Attack-Protected Intel Processors. In Proceedings of the 2024 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), Tysons Corner, VA, USA, 6–9 May 2024; pp. 378–382. [Google Scholar]
- Tian, S.; Szefer, J. Temporal Thermal Covert Channels in Cloud FPGAs. In Proceedings of the 2019 ACM/SIGDA International Symposium on Field-Programmable Gate Arrays (FPGA), Seaside, CA, USA, 24–26 February 2019; pp. 298–303. [Google Scholar]
- González-Gómez, J.; Cordero-Zuñiga, K.; Bauer, L.; Henkel, J. The First Concept and Real-World Deployment of a GPU-Based Thermal Covert Channel: Attack and Countermeasures. In Proceedings of the Design, Automation & Test in Europe Conference (DATE), Antwerp, Belgium, 17–19 April 2023; pp. 1–6. [Google Scholar]
- Miedl, P.; Ahmed, R.; Thiele, L. We Know What You’re Doing! Application Detection Using Thermal Data. Leibniz Trans. Embedded Syst. 2021, 7. [Google Scholar]
- Aljuffri, A.; Zwalua, M.; Reinbrecht, C.R.W.; Hamdioui, S.; Taouil, M. Applying Thermal Side-Channel Attacks on Asymmetric Cryptography. IEEE Trans. Very Large Scale Integr. VLSI Syst. 2021, 29, 1930–1942. [Google Scholar] [CrossRef]
- Dey, S.; Singh, A.K.; McDonald-Maier, K. ThermalAttackNet: Are CNNs Making It Easy to Perform Temperature Side-Channel Attack in Mobile Edge Devices? Future Internet 2021, 13, 146. [Google Scholar] [CrossRef]
- Lee, E.A. Cyber-Physical Systems: Design Challenges. In Proceedings of the 2008 11th IEEE International Symposium on Object and Component-Oriented Real-Time Distributed Computing (ISORC), Orlando, FL, USA, 5–7 May 2008; pp. 363–369. [Google Scholar]
- Rajkumar, R.; Lee, I.; Sha, L.; Stankovic, J. Cyber-Physical Systems: The Next Computing Revolution. In Proceedings of the 47th Design Automation Conference (DAC), Anaheim, CA, USA, 13–18 June 2010; pp. 731–736. [Google Scholar]
- Griffor, E.R.; Greer, C.; Wollman, D.A.; Burns, M.J. Framework for Cyber-Physical Systems: Volume 2, Working Group Reports; US Government Publication; NIST: Gaithersburg, MD, USA, 2017. [Google Scholar]
- Rehman, S.U.; Gruhn, V. An Effective Security Requirements Engineering Framework for Cyber-Physical Systems. Technologies 2018, 6, 65. [Google Scholar] [CrossRef]
- DHS. Science and Technology: CPS Security. Available online: https://www.dhs.gov/archive/science-and-technology/cpssec (accessed on 19 August 2025).
- CISA. CISA and Partners Release Asset Inventory Guidance to Strengthen Operational Technology Security. Available online: https://www.cisa.gov/news-events/news/cisa-and-partners-release-asset-inventory-guidance-strengthen-operational-technology-security (accessed on 19 August 2025).
- National Science Foundation. CPS: Cyber-Physical Systems Funding Opportunities. Available online: https://www.nsf.gov/funding/opportunities/cps-cyberphysical-systems/503286/nsf24-581/solicitation (accessed on 19 August 2025).
- National Science Foundation. CPS Foundations and Connected Communities. Available online: https://www.nsf.gov/funding/opportunities/cps-cyber-physical-system-foundations-connected-communities (accessed on 19 August 2025).
- Government of Canada. Regional Artificial Intelligence Initiative (RAII)—Program Applicant Guide. Available online: https://www.canada.ca/en/prairies-economic-development/services/funding/regional-artificial-intelligence-initiative/program-applicant-guide.html (accessed on 19 August 2025).
- Benelhaouare, A.Z.; Oukaira, A.; Oumlaz, M.; Lakhssassi, A. Enhancing Thermal Security of 3D-SiP Systems through Thermal Digital Twin (TDT). In Proceedings of the IEEE Canadian Conference on Electrical and Computer Engineering (CCECE), Kingston, ON, Canada, 6–9 August 2024; pp. 20–24. [Google Scholar]
- Fiter, K.; Malassigné-Onfroy, L.; and Oakes, B. DTInsight: A tool for explicit, interactive, and continuous digital twin reporting. arXiv 2025, arXiv:2508.18431. [Google Scholar] [CrossRef]




| Integration Paradigm | Description | Key Benifits | Main Challenges |
|---|---|---|---|
| Monolithic SoC | All functions on single silicon die | Mature, cost-effective, high-yield | Scaling, heat, flexibility |
| Heterogeneous Integration | Different device/processes combined in one system | Optimized functions, design modularity, flexibility | Fabrication, cost, thermal |
| 3D-Stacked Integration | Multiple dies/layers stacked, interconnected vertically | Ultra-high density, reduced latency, BW boost | Heat management, complexity |
| Chiplets | Modular small dies integrated via interposer | Reusability, scalability, improved yield | Interface standardization, Heat |
| 2D/3D Hybrid Materials | Atomically thin layers on 3D platforms | New electronic/optical properties, miniaturization | Reliability, integration, heat dissipation |
| Subject | Publications |
|---|---|
| Microfluidic Devices & Surface Engineering | 2029 |
| Microelectromechanical Systems | 1722 |
| Semiconductor Physics | 1098 |
| Manufacturing | 654 |
| Wireless Technology | 577 |
| Organic Semiconductors | 461 |
| Electronic Packaging and Interconnection | 421 |
| Biosensors | 402 |
| Electrical Energy Management | 386 |
| Optoelectronics & Optical Engineering | 373 |
| Year | Ref | Platform | Observation Vector | Access | Signal/Cadence | Objective | Outcome and Caveats |
|---|---|---|---|---|---|---|---|
| 2015 | Masti et al. [84] | ×86 multicore CPUs | Software, co-resident | User OS | On-die temperature, Hz–tens of Hz | Covert, side | Low-rate covert side |
| 2016 | Bartolini et al. [85] | Multicore CPU | Software, co-resident | User OS | Quantized temperature | Covert | Capacity, coding gains |
| 2019 | Tian et al. [89] | Cloud FPGA | Co-resident (temporal) | Cloud tenant | Fabric temperature | Covert inter-tenant | Inter-tenant temporal channel |
| 2019 | Chen et al. [77] | SoC with PoP DRAM | Co-resident, cross-block | User OS | SoC/DRAM thermal coupling | Covert | Intra-package thermal coupling |
| 2021 | Aljuffri et al. [92] | MPSoC | Software/embedded | Varies | Windowed thermal traces | Crypto via ML | Crypto leakage ML |
| 2021 | Miedl et al. [91] | Android smartphone | Software | User OS | Linux thermal zones | Fingerprinting | App fingerprinting mobile |
| 2021 | Dey et al. [93] | Mobile edge MPSoC | Software | User OS | Thermal series to CNN | ML leakage | Workload classification ML |
| 2023 | González-Gómez et al. [90] | embedded GPU | Co-resident | User OS/driver | Temperature/frequency telemetry | Covert | GPU-based covert channel |
| 2024 | Zhang et al. [87] | x86 client | Software (event-driven) | User OS | Thermal interrupts | Side/covert | Event-driven side/covert |
| 2024 | Mishra et al. [88] | Intel CPUs (power defenses present) | Software | User OS | Thermal telemetry | Fingerprinting | Bypass power defenses |
| Element | Content |
|---|---|
| System | Industrial controller (PLC) with a SoC/FPGA regulating a thermal process (e.g., an oven). |
| Exposed surface | On-chip temperature sensors, power/frequency logs, and automatic frequency scaling (DVFS). |
| Attack vector | Directed heating (e.g., IR/lamps) or crafted software load that raises local temperature. |
| Observable signal | Measured temperature changes and heat-driven shifts in frequency/power. |
| Technical effect | Processor/GPU throttling; control tasks execute later than planned. |
| Safety impact | Higher control-loop latency → setpoints may be overshot; triggers unsafe or unplanned shutdowns. |
| Reliability impact | Repeated thermal cycling accelerates component wear. |
| Practical mitigations | Restrict access to thermal/telemetry data; thermally isolate critical zones, alarms on fast temperature rise (rate-of-change), watchdogs that monitor control-loop latency. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Benelhaouare, A.Z.; Mellal, I.; Saydé, M.; Nicolescu, G.; Lakhssassi, A. Thermal Side-Channel Threats in Densely Integrated Microarchitectures: A Comprehensive Review for Cyber–Physical System Security. Micromachines 2025, 16, 1152. https://doi.org/10.3390/mi16101152
Benelhaouare AZ, Mellal I, Saydé M, Nicolescu G, Lakhssassi A. Thermal Side-Channel Threats in Densely Integrated Microarchitectures: A Comprehensive Review for Cyber–Physical System Security. Micromachines. 2025; 16(10):1152. https://doi.org/10.3390/mi16101152
Chicago/Turabian StyleBenelhaouare, Amrou Zyad, Idir Mellal, Michel Saydé, Gabriela Nicolescu, and Ahmed Lakhssassi. 2025. "Thermal Side-Channel Threats in Densely Integrated Microarchitectures: A Comprehensive Review for Cyber–Physical System Security" Micromachines 16, no. 10: 1152. https://doi.org/10.3390/mi16101152
APA StyleBenelhaouare, A. Z., Mellal, I., Saydé, M., Nicolescu, G., & Lakhssassi, A. (2025). Thermal Side-Channel Threats in Densely Integrated Microarchitectures: A Comprehensive Review for Cyber–Physical System Security. Micromachines, 16(10), 1152. https://doi.org/10.3390/mi16101152







