1. Introduction
With the rapid advancement of industrial information integration and the emergence of smart and micro-manufacturing paradigms, there is a critical need for scalable and robust supervisory control frameworks in automated manufacturing systems (AMSs). Modern AMSs increasingly require seamless integration between event-driven supervisory logic and industrial information systems, edge computing platforms, and smart devices to ensure safe, adaptive, and resilient operation under uncertainty. This requirement is particularly critical for micro-fabrication and MEMS production, where process outcomes are highly sensitive to dynamic conditions (e.g., surface roughness and feature/yield variability) [
1,
2]. While recent data-driven approaches can predict quality indicators or optimize yield, they do not provide a formal, verifiable supervisory logic to govern how the system should react under uncertainty [
1,
2]. Our work addresses this gap by proposing a distributed, automaton-based supervisory framework.
Supervisory control, originally proposed by Ramadge and Wonham [
3], has become a key method to restrict the behavior of discrete-event systems (DESs) by enabling or disabling controllable events to enforce desired specifications. Unlike traditional feedback control in continuous systems, supervisory control offers a formal, event-driven framework that has been widely applied to industrial scenarios such as manufacturing [
4], traffic management [
5], communication protocols [
6], and robotic coordination [
7].
The theoretical foundations of supervisory control are built upon the notions of controllability, observability, and nonblockingness. Over time, these foundations have been extended to support critical features such as fault diagnosis [
8,
9,
10], detectability [
11,
12,
13], opacity [
14,
15,
16], communication delays [
17,
18], and attack modeling and resilience [
19,
20,
21]. These extensions aim to enhance the observability, security, and robustness of DESs in uncertain environments, which is essential in domains such as smart manufacturing, cyber–physical systems, and critical infrastructure.
Such robustness concerns are especially critical in smart and micro-manufacturing systems, including MEMS-integrated production lines, where unreliable events and subsystem failures may lead to safety violations or task incompleteness, which motivates the development of robust and distributed supervisory control frameworks capable of handling such uncertainties. Among the various application domains, automated manufacturing systems (AMSs) represent one of the most representative real-world implementations of DES theory. In practice, AMSs frequently encounter uncertainties including event failures, communication latency, sensor faults, and external disturbances, which may cause system behaviors to deviate from their intended trajectories, potentially resulting in safety violations or degraded performance. To mitigate such risks, robust supervisory control in AMSs has attracted increasing research interest, with the objective of ensuring that core behaviors, task reachability, and nonblockingness are preserved even in the presence of local anomalies, structural perturbations, or environmental variations [
22,
23,
24,
25,
26,
27,
28,
29,
30].
Much of the existing literature on robustness in AMSs is based on Petri net modeling. For instance, [
25,
29] introduced the concept of maximal perfect resource-transition circuits (MPC) to characterize blocking states caused by resource failures. Other studies, such as [
26], proposed synthesis methods using strong covering structures or saturated siphon constructs to design robust supervisors. Reachability graph-based methods for robustness analysis have recently become mainstream [
24,
27,
28,
30].
Despite the progress achieved in Petri net-based AMS robustness, most of these studies rely on centralized control architectures. Few unified frameworks exist that adopt finite automata as the modeling basis while integrating unreliable event modeling, robustness classification, distributed detector synthesis, and local enforcement into a cohesive control strategy. Compared with Petri nets, automaton-based modeling offers a more direct semantic alignment with supervisory control logic, better supports modular composition, and simplifies detector construction and implementation, which is particularly important for MMSs that are highly sensitive to event failures and resource perturbations.
To address this gap, this paper proposes a distributed detector-based robust supervisory control framework specifically designed for AMSs subject to unreliable events and partial observation. The proposed method supports runtime robustness classification and localized control decision-making while preserving the global system’s safety and liveness properties.
Unlike previous studies that focus on Petri net-based robustness [
24,
27,
28,
30], this work builds a detector-based framework under automaton semantics, which simplifies classification logic and supports distributed enforcement without global synthesis. Compared with existing Petri net-based robustness control methods [
29,
30], the proposed automaton-based approach offers the following benefits:
Explicit state and transition structures better aligned with supervisory control logic;
Easier construction of local detectors via synchronous composition and projection;
Avoidance of state explosion during reachability graph enumeration.
Moreover, unlike traditional Petri net-based methods, the proposed automaton-based strategy offers not only formal clarity and modular implementation advantages but also better alignment with runtime deployment needs in intelligent MMS/MEMS platforms, and it simplifies the construction and deployment of detector automata, which is particularly important for AMSs that are highly sensitive to event failures and resource perturbations.
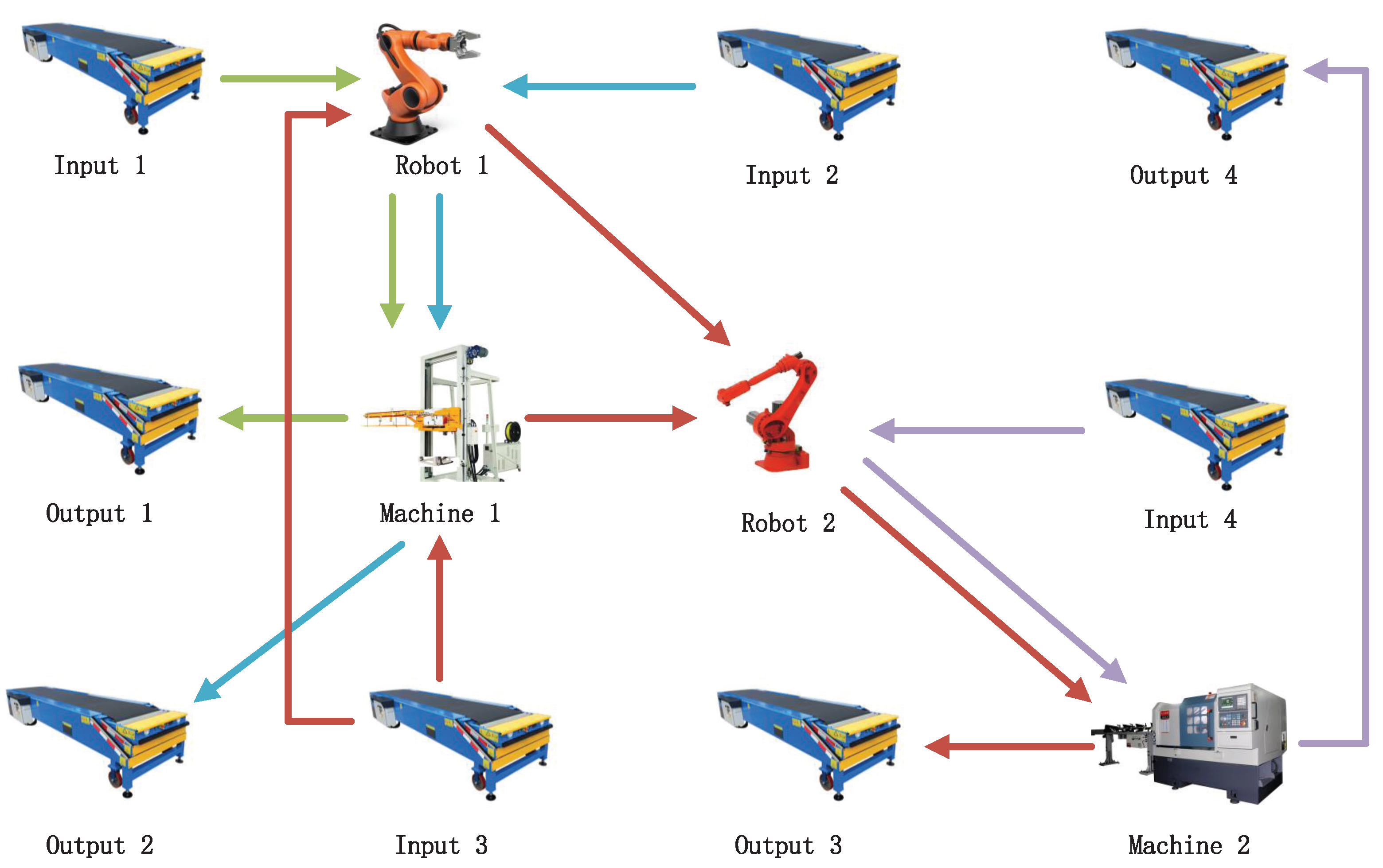
In the industrial context, modern micro-manufacturing cells (e.g., laser micromachining, micro-assembly/packaging, and micro-inspection) are organized as small DES subsystems that share resources such as vacuum pumps, precision stages, grippers, and inspection microscopes. Because parts and wafers are fragile and tolerances are tight, these cells are highly sensitive to event-level faults (loss of vacuum, misalignment, tool jam, vision rejection). Our framework fits this context for several reasons: (i) Event-level enforcement: robustness is decided at the event level, matching the granularity of the above faults. (ii) Local real-time decisions: supervisors inspect detector labels over the local event alphabet and a small set of enabled events, enabling millisecond-scale reactions on PLC/ROS without global search. (iii) Modularity in production cells: the detector-based design isolates faults locally and supports incremental cell integration across reconfigurable lines.
The main contributions of this paper include the following:
A modular and distributed supervisory control integration framework is proposed for AMSs/MMSs, supporting robust execution under event failures and seamless integration into industrial information systems without requiring centralized coordination or global model construction.
Local detector automata are designed for each subsystem to classify operational states into Strictly robust, Recoverably robust, or Non-robust categories, thereby enabling real-time decision-making, enhanced information integration, and local control based on observed data streams.
The proposed control strategy offers a scalable and adaptable industrial solution that avoids unsafe trajectories, supports controller reusability and system extensibility, and is compatible with deployment on PLC-based, edge computing, and industrial information management platforms. It is also suitable for micro-manufacturing execution systems and MEMS-oriented production platforms.
The remainder of this paper is organized as follows.
Section 2 introduces the modeling framework and defines event unreliability.
Section 3 presents the problem formulation and robustness classification.
Section 4 details the construction of detectors and the distributed control strategy.
Section 5 provides simulation validation.
Section 6 concludes this paper.
3. Problem Formulation for Distributed Robust Supervision
3.1. Problem Formulation
Let
be the global plant defined in
Section 2, where
E is already partitioned into
Each local supervisor is defined over a partial alphabet and observes a subset and controls .
Define the local observation projection:
which erases events not in
.
The local supervisor is a map:
and the joint distributed supervisor is
Then the controlled behavior of the system is
Assumption 1. (Full controllability and observability): Although the global event set includes uncontrollable () and unobservable () events, we assume that all locally relevant events are controllable and observable, i.e., , . This assumption enables the focus to remain on robustness enforcement under unreliable events while avoiding complications due to uncontrollability or unobservability. The extension to partial observation and limited control authority will be pursued in future work.
Rationale: We adopt full controllability and observability locally to isolate the effect of unreliable events on robustness detection. This matches many PLC/ROS-based AMS cells where event execution and sensing at the cell level are fully actuated and instrumented; the treatment of limited control/partial observation is deferred to future work.
3.2. Distributed Robustness Criteria
We consider two types of robustness objectives:
Definition 2. The system is Strictly robust under S ifthat is, no string executed under control contains any unreliable event. Definition 3. The system is Recoverably robust under S if That is, for every prefix of the controlled behavior, there exists a continuation string without any unreliable events that drives the system into a terminal state.
Definition 4. Given a set of subsystems with individual detector automata , we say the system is distributedly robust with respect to event failures in if and only if the following hold: (i) the local robustness labels of are sound and complete with respect to the local behavior of ; and (ii) the composition of local robustness classifications under the merging rule ensures global nonblocking and task reachability.
These robustness criteria reflect different tolerance levels to resource failures and will guide the synthesis of distributed supervisors in subsequent sections.
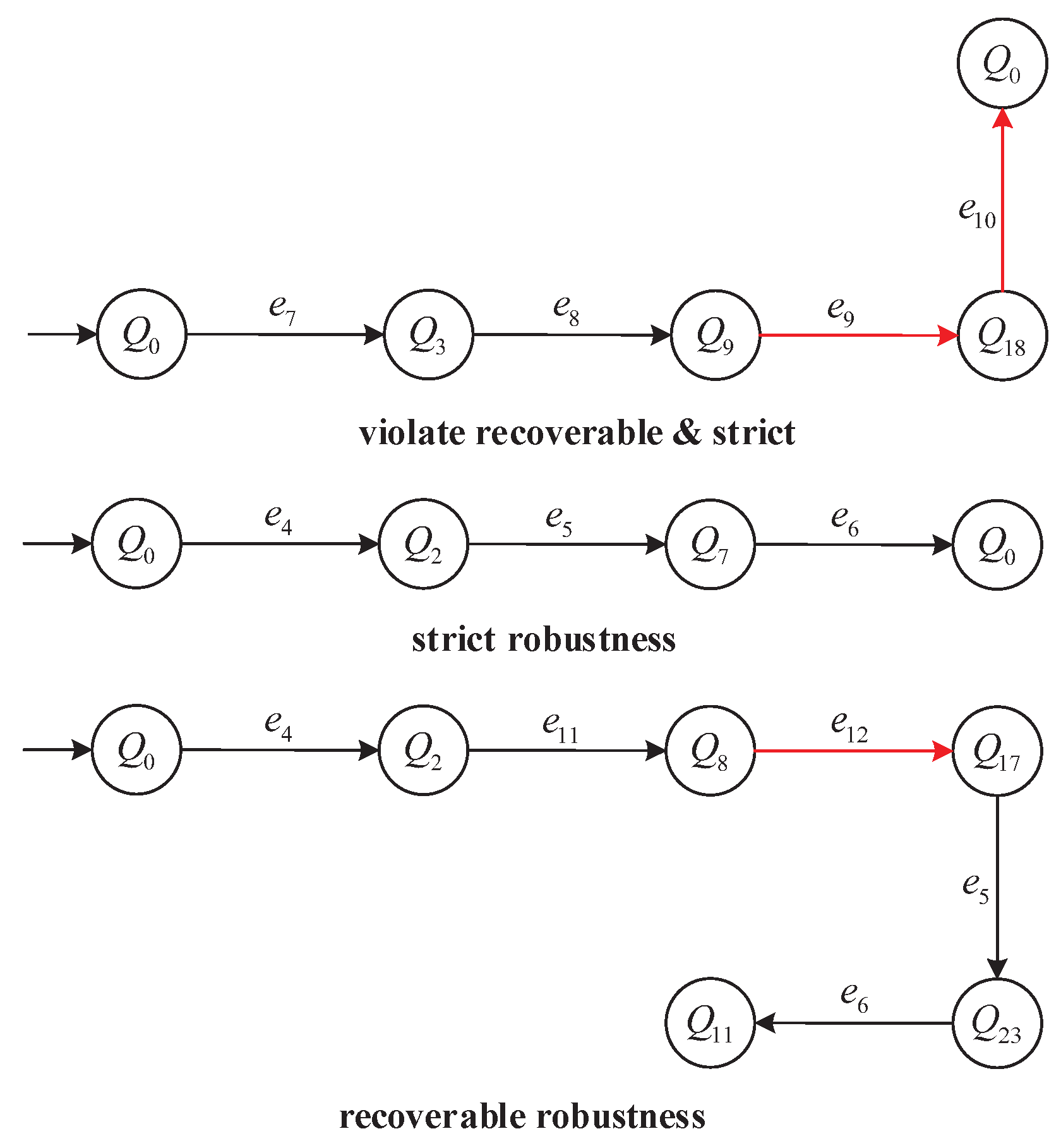
To further clarify these robustness definitions,
Figure 5 illustrates three representative execution paths from the AMS model
G:
(i) Top path: Violates both Strict and Recoverable robustness, as it executes and no further continuation reaches a terminal state.
(ii) Middle path: Satisfies Strict robustness by using only reliable events and reaching a designated terminal state.
(iii) Bottom path: Satisfies Recoverable robustness by continuing through reliable events after to reach a terminal state.
Lemma 1. If and s contains an event , then the supervisor S cannot satisfy Strict robustness.
Proof. By definition of Strict robustness, the set must be disjoint from . If s contains any , then , thus violating . Therefore, S fails to achieve Strict robustness. □
The robustness distinctions illustrated above motivate a clear analytical foundation. The following lemma formally highlights the inherent limitation imposed by Strict robustness, which completely forbids occurrences of unreliable events.
3.3. Problem Statement
Problem: Given the global plant , local alphabets , and event partitions , synthesize distributed supervisors such that the resulting behavior satisfies Strict or Recoverable robustness.
Key technical challenges: Each
only observes partial behaviors and controls local events. Ensuring that the global behavior
remains robust requires careful coordination under partial information.
Main conceptual challenges include the following:
Limited local knowledge: Although all events are assumed to be locally observable and controllable in this work, real-world systems may include unobservable or uncontrollable events, which complicate supervision.
Synchronization ambiguity: The execution of a shared event may depend on the state of another module that is not visible to the local supervisor.
Fault propagation risk: A single unreliable event can propagate failures through multiple modules unless proactively prevented.
4. Distributed Robust Supervisor Design
To enable robust supervision under partial observation and unreliable events, this section proposes a distributed synthesis strategy that decomposes global analysis into localized decisions.
Centralized robust supervisory synthesis typically requires the explicit construction of the global plant , which suffers from severe state explosion due to synchronous product operations. In the presence of unreliable events, the analysis of global robust reachability becomes even more intractable, as failure propagation must be tracked across all subsystems.
Centralized synthesis suffers from lack of modularity, as any subsystem update requires re-synthesizing the entire global model. This hinders scalability, adaptability, and practical implementation.
In contrast, the proposed distributed approach constructs local detectors and supervisors without requiring the global synchronous product, leveraging only local event structures and known unreliable events. This enables scalable synthesis, localized diagnosis, and runtime efficiency while still preserving global robustness guarantees through conservative decision fusion.
In systems composed of multiple interacting automata with local observations and possible event unreliability, centralized control methods often suffer from state explosion and lack of structural scalability. Specifically, the construction of the global plant and the corresponding monolithic supervisor becomes impractical as the number of subsystems increases or the event space becomes dense. (Throughout this paper, all events are observable and controllable; ‘local observations’ means each detector evolves on its own alphabet , not that some events are unobservable.)
To overcome these limitations, we propose a distributed robustness framework that decomposes the control synthesis problem into localized robustness detection and enforcement tasks. The core idea is to endow each subsystem with a local detector that classifies its states into Strictly robust, Recoverably robust, or Non-robust according to whether reliable paths to local terminal states exist. These detectors are constructed using only the state space of and the known unreliable event set .
Formally, for each local observation history
, the supervisor
determines the current state
of the detector and applies a conservative event-enablement rule:
Unlike traditional methods, our framework ensures that supervisors avoid unsafe behaviors without global coordination or fault observability. The distributed strategy guarantees that the global language
remains within the Strictly or Recoverably robust trajectories of the overall system, as proven in Theorem 1.
This design philosophy transforms the robustness problem from a centralized model-checking challenge into a modular, scalable synthesis approach, enabling large-scale implementation across fault-prone and information-constrained systems.
4.1. Distributed Robust State Detectors
The cornerstone of distributed robust supervision is the ability of local detectors to accurately classify the system states with respect to robustness. Distributed robust state detectors perform this function by analyzing local event sequences and predicting future execution outcomes.
Formal Definition and Construction
Formally, a local robust state detector associated with the local supervisor
is defined as
where
is the finite set of detector states;
is the locally observable event set;
is the transition function;
is the initial state of the detector;
is the robustness classification function.
Detectors evolve on the locally observable alphabet , while the robustness classification only needs the reliable/unreliable split inside the local alphabet inherited from the global partition (see Step 3 below).
The construction method: is as follows:
Define each local subsystem as a combination of a product automaton and its relevant resource automata.
Track reachable states in the local subsystem based solely on local observable events.
Event partition: Globally, the event set is partitioned as
into reliable and unreliable events. For a local subsystem
with alphabet
and locally observable subset
, we inherit the global partition by intersection:
Events not in do not occur in and are irrelevant for local reasoning. The detector transitions use locally observable labels , while robustness classification only needs the reliable/unreliable distinction inside as defined above. In Algorithm 1, we therefore operate on with two label sets: (i) when we compute forward reachability of arbitrary local prefixes, and (ii) when we require reliable prefixes or suffixes. Throughout the algorithm we write (resp. ) for (resp. ) to simplify notation.
Classify states as follows:
Strict robustness: A state is Strict if there exist a reliable prefix from to y, and there exists a reliable suffix from y to a terminal state in . Equivalently, y lies on a path that uses only reliable events up to y and can continue by reliable events to .
Recoverable robustness: A state is Recoverable if there exists a path from to y such that every prefix of s reaches a state that admits a reliable suffix to . Hence, Strict and Recoverable share the same ‘reliable-suffix-to-terminal’ property; furthermore, Strict requires a reliable prefix, while Recoverable allows unreliable prefixes whose every prefix remains Recoverable by some reliable suffix.
Non-robust: A state not reachable to under reliable events.
Robust State Classification Algorithm 1 follows below.
| Algorithm 1 Robust State Classification with Prefix–Suffix Semantics. |
| Require: Local automaton ; initial set ; terminal set ; reliable events ; unreliable events . |
| Ensure: Label . |
| 1: | ▹ states admitting a reliable suffix |
| 2: | ▹ prefix stays inside |
| 3: | ▹ reliable prefix inside |
| 4: | ▹ Recoverable but not Strict |
| 5: for all
do |
| 6: if then |
| 7: |
| 8: else if then |
| 9: |
| 10: else |
| 11: |
| 12: end if |
| 13: end for |
The graph primitives invoked by Algorithm 1 are specified in Algorithm 2.
The connection to Algorithm 1 is described below.
Using the localized sets above, we first compute the reliable-suffix basin
BackwardClosure, i.e., states that can reach
by
reliable events only. A state has an
arbitrary (possibly unreliable) prefix whose every prefix remains Recoverable iff it is forward-reachable from
within using labels in
. A state is
Strict iff, in addition, there exists a
reliable prefix inside
, obtained by forward closure from
with labels in
. Consequently, the classification realizes the logical intent: Strict states admit a reliable prefix and a reliable suffix; Recoverable states admit a path whose every prefix can be recovered by some reliable suffix; and
holds by construction.
| Algorithm 2 Graph primitives used in Algorithm 1. |
- 1:
function BackwardClosure() ▹ least fixpoint of - 2:
- 3:
repeat - 4:
- 5:
until R no longer changes - 6:
return R - 7:
end function - 8:
function ForwardClosureRestricted() ▹ BFS restricted to - 9:
; - 10:
while do - 11:
pop - 12:
for all with do - 13:
if and then - 14:
; push - 15:
end if - 16:
end for - 17:
end while - 18:
return R - 19:
end function
|
Complexity: Let be the number of states of the local automaton , the number of transitions, and the number of reliable-labeled transitions. All primitives used by Algorithm 1 are graph traversals (BFS/fixpoints) on finite graphs:
BackwardClosure: reverse-BFS/least-fixpoint over reliable edges; it runs in time and memory.
ForwardClosureRestricted: BFS restricted to ; it runs in time and memory.
ForwardClosureRestricted: BFS on the reliable subgraph inside ; it runs in time and memory.
The final labeling loop over is .
Hence, Algorithm 1 runs in overall time
i.e., linear in the size of the local graph. We compute all detector scales as
.
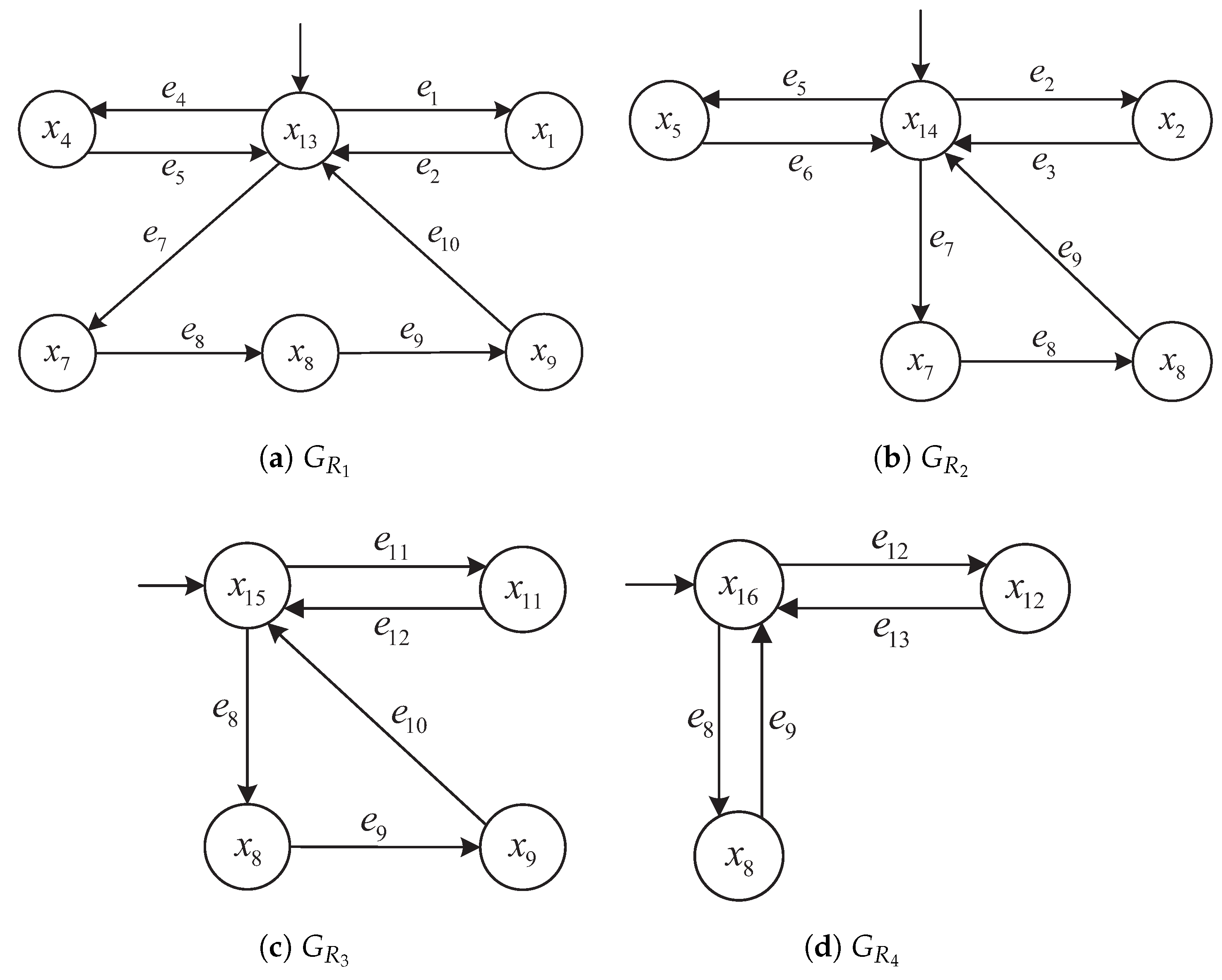
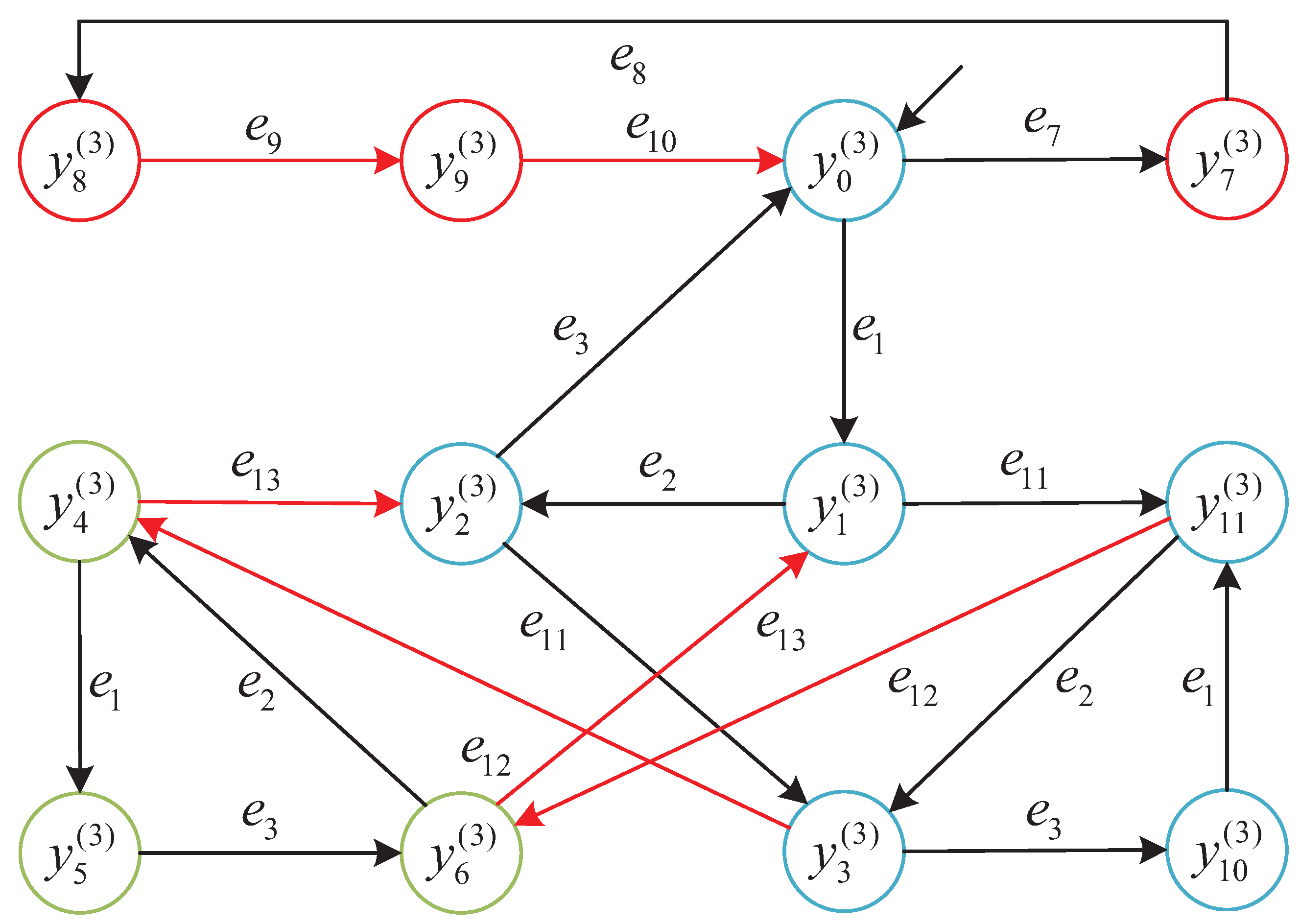
To enhance the interpretability of robustness classification under local observations, we visualize the reachable state space of the local detector for subsystem .
To further explain the interpretation of each detector state in subsystem
, we list below the component-wise markings in
Table 1 of
, which represent the synchronized configurations of product and resource automata.
The same modeling principle and robustness classification procedure are applied to the remaining subsystems –, but their detector state table is omitted for brevity.
To intuitively present the results of the local robust state classification, we provide the robustness-annotated state transition diagram for subsystem . Each state is colored according to its robustness label.
The states in
Figure 6 correspond to
.
This structure reveals how unreliable events (e.g.,
,
) impact recoverability. The same method is applied to other subsystems in the following
Figure 7,
Figure 8 and
Figure 9.
To improve clarity, we extract a representative fragment of the detector in subsystem , emphasizing robustness-relevant states and transitions. Unlike previous subsystems, contains intermediate states whose robustness classification depends on the presence of unreliable events in the prefix path.
Unlike the detectors for and , the robustness structure of is dominated by Non-robust states. This is due to the fact that many transitions in involve unreliable events, forming unrecoverable cycles or branches. Thus, local supervisory control in this subsystem must Strictly avoid enabling transitions such as , , , and .
4.2. Global Robustness Classification and Guarantee
To enable distributed robustness enforcement, each local supervisor must make control decisions based on its current detector state . The robustness classification determines which controllable events are allowed, depending on whether the state is Strict, Recoverable, or Non-robust.
Notation. For and , define . A shared event is globally enabled at a joint state iff it is enabled by every local supervisor that synchronizes on it (conjunctive fusion).
Below, Algorithm 3 summarizes the local decision-making rule.
| Algorithm 3 Local supervisor enabling rule based on robustness. |
| Require: Local observation |
| Ensure: Enabled set (here and are the offline partitions precomputed by Algorithm 1). |
| 1: | ▹ current detector state |
| 2: | ▹ robustness label |
| 3: if r = Strict then |
| 4: |
| 5: else if r = Recoverable then |
| 6: |
| 7: else |
| 8: |
| 9: end if |
Label order and global aggregation:
Let the label set be
endowed with the total order
. For a joint detector state
, the global robustness label is
where
denotes the minimum with respect to the above total order (i.e., the weakest label dominates). Equivalently,
Lemma 2. (Global robustness consistency.) If any local detector classifies a state as Non-robust, then the global system state is Non-robust.
Proof. By definition, global robustness classification is determined by the least robust local detector classification. Hence, a Non-robust local classification directly yields a global Non-robust state. □
Lemma 3. (Robustness propagation.) If all local detectors classify their current state as either Strict or Recoverable, then the global state is at least Recoverable.
Proof. By definition of the global classification rule , where , the absence of any Non-robust local state ensures that . □
Theorem 1 (Global robustness under reliable-event enforcement). Let be the synchronous product of local automata. For each i, Algorithm 1 computes a partition with , where (resp. ) is the set of states that admit a reliable prefix (resp. a prefix whose every prefix remains Recoverable by some reliable suffix) to the terminal set .
Each local supervisor applies the following reliable-state rule at its current detector state : A shared event is globally enabled at a global state iff it is enabled by every local supervisor that synchronizes on it (conjunctive fusion).
Then along every closed-loop execution, each visited global state y satisfies for all . Equivalently, the global robustness labelalways belongs to . Moreover, Proof. We show that is an invariant of the closed loop.
By Algorithm 1, we first compute the reliable-suffix basin and then ; hence, collects exactly the states that are forward-reachable from while staying inside . In particular, , so the initial global state belongs to .
Let and suppose a global event e occurs to . Because all events are controllable and the global enabling is conjunctive, e can occur only if each involved supervisor enables e at . If , the rule enables only transitions with , where , thus . If , the rule enables only transitions with , hence . If for some i we had , no event would be enabled contradicting the occurrence of e at y. Therefore, and the invariant holds.
Consequently, no closed-loop execution can reach a local Non-robust state, i.e., for all i, so . The two characterizations of follow directly from the order and the invariance . □
We construct a robust event enablement, see
Table 2, mapping local detector states to enabled events.
Table 2, which shows robust events, assists the local supervisors in making rapid and precise decisions.
The next chapter provides experimental validation of the distributed robust supervisory strategy, verifying its efficacy under practical scenarios.
4.3. Structural Characterization of Local Robustness
The robustness of each subsystem is structurally influenced by its topological configuration and its interaction with unreliable events. In particular, the existence of cycles or interleaving paths involving events in directly affects the classification of states in .
We formally observe the following:
Lemma 4 (Structural strictness via reliable closures)
. For subsystem with reliable alphabet , defineThen a state is Strictly robust iff .
Lemma 5 (Cycle-induced Non-robustness (sufficient)). If a state y lies on a cycle that contains some event in and , then y is classified as Non-robust.
To summarize the overall distributed control flow,
Figure 10 illustrates the high-level architecture of the proposed framework, where each subsystem constructs a local detector, and the global classification is obtained through the merging rule
.
5. Experimental Validation
To evaluate the applicability of the proposed framework in automated and micro-manufacturing contexts, simulation studies are conducted on representative system models. All subsystem automata and detector structures were constructed based on the modular modeling approach proposed in
Section 3. The robustness classification Algorithms 1 and 3 were implemented using a Java-based simulation framework developed by the authors. All simulations were executed on a Windows 10 workstation with an Intel Core i7 processor and 16 GB RAM.
To visualize the local detectors and robustness propagation structures, we manually generated state transition graphs using Microsoft Visio. Each diagram reflects the formal construction of detectors based on synchronous composition and robustness labeling, as defined in
Section 4.
5.1. Experimental Setup
Each local plant
is modeled as the synchronous composition of a product automaton
and its corresponding resource automata
:
where
denotes the index set of resources used by subsystem
i. Four distributed subsystems are constructed as follows:
;
;
;
.
Unreliable events are defined as , corresponding to typical faults:
: tool jam or axis over-current on a precision stage;
: part/wafers misalignment detected by the vision system;
: loss of vacuum or gripping failure during pick-place;
: vision reject after micro-inspection.
A compact mapping is summarized in
Table 3. These faults occur at the event granularity and directly impact shared resources, which is consistent with our robustness classification and local supervision.
5.2. Robustness Structure Analysis of Subsystems
We summarize the robustness classification across subsystems based on the constructed detector automata, as visualized in
Figure 6,
Figure 7,
Figure 8 and
Figure 9. Each figure highlights state robustness categories under local observation:
and contain mostly Strictly robust states, with only a few Non-robust configurations.
exhibits a mixed structure, including ambiguous and Recoverable states due to its complex resource interactions.
is entirely Non-robust, as every reachable state involves unreliable transitions.
These results validate the effectiveness of local detectors in classifying robustness-critical regions, which directly influence supervisory control strategies. A summary of robustness distribution is given in
Table 4.
5.3. Supervisor Response to Event Sequences
Each local supervisor applies the robust event-enablement rule using its detector to classify states and selectively disable risky transitions.
In and , only Strictly robust paths are allowed. In , the supervisor permits Recoverable trajectories while blocking transitions to Non-robust regions. In , all controllable transitions are disabled to avoid Non-robust cycles.
5.4. Structural Sensitivity and Scalability
Robustness is structurally influenced by the interaction between subsystems and unreliable events. As interleaving increases, detectors grow in size and more states become ambiguous or Non-robust. In , complex resource sharing induces a significant number of states requiring Recoverable supervision. In contrast, demonstrates the fragility of subsystems lacking redundant safe paths.
5.5. Robustness Enforcement Consistency
The consistency between local supervisory decisions and global robustness outcomes is confirmed through representative simulations. The following is shown in
Figure 6,
Figure 7,
Figure 8 and
Figure 9 and
Section 5.2:
Supervisors in and enable only Strictly robust trajectories, which are also a subset of Recoverably robust behaviors.
Supervisors in permit Recoverable but not Strictly robust trajectories while preventing unsafe transitions.
Supervisors in disable all controllable events due to inherent Non-robustness.
These results confirm that the distributed supervisory strategy achieves global robustness through local enforcement without requiring centralized coordination.
5.6. Evaluation of Structural Performance Metrics
To complement the robustness enforcement results presented in
Section 5.2,
Section 5.3,
Section 5.4 and
Section 5.5, this section focuses on architectural-level performance indicators that reflect the practical value of the proposed distributed framework. Instead of measuring time-based performance—often dependent on platform-specific implementation—we evaluate structural properties that are stable across platforms and scale with system complexity. Specifically, we compare centralized and distributed designs in terms of reachable states, modularity, and extensibility.
We consider a partial plant composed of subsystems
and
, defined as
The centralized plant is constructed as
while the distributed approach constructs independent local detectors
and
over
and
, respectively. These subsystems and their corresponding structures are consistent with the plant models illustrated in
Figure 2 and
Figure 3 and the detector graphs in
Figure 6,
Figure 7,
Figure 8 and
Figure 9.
Table 5 summarizes the structural performance differences between the centralized and distributed architectures in terms of reachability, design reusability, and scalability.
Note: ‘Reachable States’ counts the reachable states of the detector(s)—a single monolithic detector for the centralized case or the sum of local detectors for the distributed case—not the size of the plant’s global synchronous product.
Scalability: The complexity of each local detector scales with the size of its local graph only. Algorithm 1 runs in time and uses memory, where and are the reachable states and edges of the detector built on the local alphabet (product automaton of with its adjacent resources). Thus, growth is driven by the local interaction degree (number of shared resources/events), not by the total number of subsystems N. In our case study, the most connected subsystem yields detector states, while and each have 11, showing that ‘hub’ modules can dominate the footprint, whereas other modules remain small. Practical mitigations include resource partitioning/decoupling, clustering or hierarchical detectors for hubs, and event abstraction to shrink . Here are some examples:
The centralized model has fewer reachable states due to full synchronization and global pruning.
The distributed approach constructs reusable local detectors that enable modular expansion.
Adding new modules (e.g., , ) in the centralized case requires reconstructing the full plant, while distributed controllers support incremental composition.
These metrics collectively confirm that although centralized synthesis produces compact models for small configurations, the distributed approach offers substantial structural advantages. It supports subsystem-level reuse, incremental integration, and scalable extension to larger system configurations—all without requiring full plant redesign.
5.7. Language-Level Comparison of Centralized and Distributed Control
To complement the structural evaluation presented in
Section 5.6, we now compare the behavioral correctness of the proposed distributed supervisory scheme against a centralized baseline. The objective is to verify whether the distributed controllers can achieve equivalent robustness enforcement in terms of permissible event sequences and rejection of unsafe trajectories.
We consider the same partial plant
and its centralized composition
, as defined in
Section 5.6. The centralized supervisor is synthesized over
using robustness enforcement based on Recoverably robust trajectories. The distributed control scheme uses two detectors
and
to determine local robustness and enable event decisions based on the distributed rule:
where
denotes the projection of string
s onto the event set of
.
Let denote the language generated by the centralized supervisor and denote the language generated by the distributed scheme under detector-based coordination.
We now state a formal result that characterizes the behavioral soundness of the distributed supervisor.
Proposition 2. Let and let , be the robust state detectors constructed for and , respectively. Let be the language of the centralized robust supervisor synthesized over , and let be the language permitted by the distributed strategy.
Then, the following holds:
- 1.
;
- 2.
.
Proof. Consider any string . By definition of the distributed strategy, and . According to the detector design (see Algorithm 1), this means that leads to a state in and leads to a state in , both of which are either Strictly robust or Recoverably robust.
Since the centralized supervisor is synthesized over , which contains the full behavior of G, and robustness pruning only removes strings violating Definition 3, any s that passes all local robustness detectors also satisfies the global robustness condition. Thus, and .
Now consider any string . Then there exists some i such that , meaning leads to a Non-robust state in . Since the global supervisor enforces robustness over all components, such a string must also be removed from during centralized pruning. Therefore, and , implying . □
5.8. Trajectory-Level Validation of Recoverable Robustness
While the structural and language-level analyses in
Section 5.6 and
Section 5.7 demonstrate that the distributed control framework enforces robustness consistently, it remains essential to validate that the detectors allow appropriate runtime execution for strings that meet the Recoverable robustness condition. In this section, we evaluate a specific trajectory under the distributed supervisory scheme to illustrate the runtime behavior and semantic interpretation of Recoverable robustness.
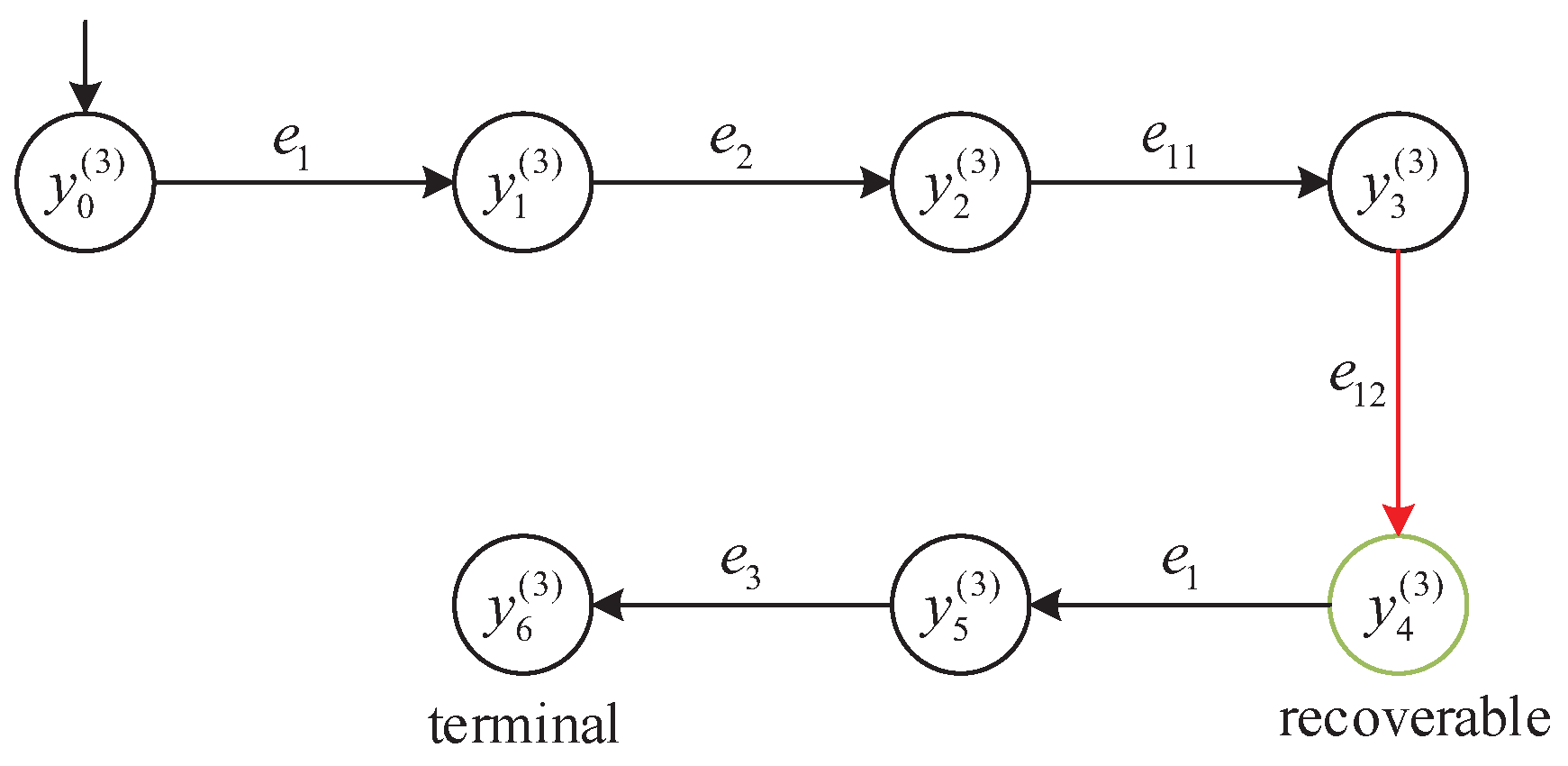
We consider the subsystem
with its detector
illustrated in
Figure 8. The following event sequence is analyzed:
This path contains the unreliable event and tests the distributed supervisor’s ability to accept partially unreliable behavior while preserving the ability to reach a terminal configuration.
Let y denote the state reached after executing the prefix . According to the detector classification in , the state is labeled as Recoverably robust. This classification is justified because, although is an unreliable event, there exists a valid recovery sequence from y that leads to the terminal state . Thus, the Recoverably robust label permits continuation beyond an unreliable event provided a complete recovery path is guaranteed.
At the detector state , the supervisor evaluates whether to allow the event to continue execution. Since the detector classification is Recoverable and a valid recovery trajectory exists via , the system permits to occur.
After executing
and then
, the system reaches the terminal configuration
. According to the terminal state definition introduced in
Section 2.4,
lies in the local terminal state set
of subsystem
. This demonstrates that the recovery path exists and is operational, validating the runtime semantics of the Recoverably robust label and confirming that the execution leads to a semantically complete production cycle.
Figure 11 visualizes the state transitions along the trajectory
s, highlighting the transitions involving unreliable events and the eventual recovery via
. The states along the path are as follows:
(initial);
;
;
(Recoverable robustness);
(terminal).
This example confirms that the distributed supervisor correctly interprets the Recoverably robust classification and allows execution of unreliable events only when a valid recovery path exists. Such behavior illustrates the semantic soundness of the detector-based control strategy in runtime decision-making.
These structural properties confirm the feasibility of implementing the proposed detector-based supervisors in real-world industrial environments. In particular, the modular architecture is well-suited for deployment on edge controllers or Programmable Logic Controllers (PLCs) within smart factories, enabling real-time detection and mitigation of failures without centralized coordination.
5.9. Comparison with Existing Methods
To further assess the efficacy of the proposed distributed framework, we qualitatively compare it with several representative supervisory-control approaches: centralized robust synthesis, static fault-tolerant control (FTC), modular supervision, and our distributed robust scheme (see
Table 6). The comparison focuses on unreliable-event handling, Recoverable robustness, state-space scalability, supervisor reusability, and incremental integration.
The centralized strategy provides strong guarantees but suffers from state explosion and poor scalability. Static FTC approaches enable some resilience, yet they typically rely on predefined failure models and cannot adapt at runtime. Modular architectures support structural reuse but lack explicit robustness enforcement against event uncertainty.
Compared with a centralized robust supervisor, the proposed distributed scheme achieves the same safety guarantees (see Proposition 2 and
Section 5.7) while avoiding global runtime search. At runtime, decisions are made locally by inspecting the label of the current detector state and a small set of enabled events; therefore, the decision cost depends on the local event alphabet and the detector size rather than the size of the monolithic product automaton (
Table 6). In practice, this reduces decision latency and improves controller reuse and scalability (cf.
Section 5.6 and
Table 5). Because timing strongly depends on platform and implementation (PLC vs. ROS, CPU load, I/O latency, etc.), we deliberately do not report a fixed percentage improvement and leave a cross-platform timing benchmark as future work.
The detector-based control structure is amenable to modular implementation, since each local subsystem requires only partial event monitoring and local classification. The architecture is compatible with PLC-based or ROS-based deployments and supports incremental system expansion and fault isolation, and it is therefore a strong candidate for practical cyber–physical manufacturing environments.
Practical implementation for micro-manufacturing: Each detector can be deployed as local logic on PLCs (IEC 61131-3 [
31]) or ROS edge controllers. Because only partial events are monitored and the detector automaton is small, runtime checks are constant-time with negligible memory footprint compared to a monolithic product automaton. This enables short-cycle reactions, fault isolation at the cell level, and incremental expansion of production lines—key properties for micro-manufacturing and MEMS-based execution platforms (see also
Section 5.1/
Table 3).
Network latency and deployment: Our enabling rule is conjunctive and event-driven without a global clock. Latency mainly affects throughput (waiting for all involved local supervisors to enable a shared event) but not the correctness of the robustness guarantee. For time-critical shared operations, we recommend co-locating the relevant supervisors with the shared resource (e.g., on the same PLC rack or ROS edge) or using industrial fieldbuses with bounded jitter. A quantitative latency budget and its impact on cycle time are part of our planned hardware testbed.
5.10. Cost and Scalability Micro-Study
Setup: We use the running example with product automata and 4 resource automata. For each local composition , we run Algorithm 1 once and record the following platform-agnostic counters: (i) graph sizes , , and ; (ii) the intermediate sets of Algorithm 1: , , ; and (iii) the final label counts , , .
Unless otherwise stated, the terminal set
used by Algorithm 1 is obtained by the product–events semantics: let
be the union of terminal events declared by the product automata. Whenever a shared event
fires in the synchronous product that defines
, the successor global state is inserted into
. Multiple successors reached by the same terminal event at the
same global state are
deduplicated. Reliable events are
as in
Section 4, and all events are controllable/observable (Assumption 1 in
Section 3).
Centralized structural baseline: As a baseline, we build once the synchronous product of the eight base automata are reached and report the reachable sizes
and
.
Table 7 compares the centralized reachable graph with the sum of locals. We also report the (purely structural) explosion factors
These ratios quantify how much larger the centralized model is than the aggregate of local models, independent of execution platforms.
Workload of Algorithm 1 (platform-agnostic): For each we also accumulate the edge visits of the three graph primitives used by Algorithm 1 (Algorithm 2):
: number of reliable edges inspected by BackwardClosure;
: number of edges scanned by ForwardClosureRestricted;
: number of reliable edges scanned by ForwardClosureRestricted.
And we also accumulate the peak queue length
among these BFS/fixpoint procedures, which serves as a proxy for memory usage.
Table 8 summarizes the counts. In all cases, the total work
empirically matches the linear-time bound
on
.
Label distributions (Strict ⊆ Rec): To avoid ambiguity and to respect
, we report
,
, their sum
, and
. We also list
(after deduplicating multiple successors produced by the same terminal event at the same global state). For instance, in
, all paths to the single terminal state are via unreliable events; hence,
and
. The results in
Table 9 are consistent with this semantics.
Optional, sensitivity to unreliable events: We vary the fraction p of events marked as unreliable and recompute the labels using the same product–events terminals. A simple trend plot can show how increasing unreliability reduces and increases .
Takeaway. The centralized reachable graph is an order of magnitude larger than the sum of locals (
Table 7), whereas our detection cost scales linearly in
on each
(
Table 8). The proposed distributed scheme therefore avoids constructing the global synchronous product at runtime and scales structurally with the sum of local sizes. This substantiates the claims on modularity and scalability without relying on platform-dependent wall-clock timing.
6. Conclusions
In conclusion, the proposed modular and distributed supervisory control integration framework provides a scalable and robust solution for automated and micro-manufacturing systems experiencing event-level failures. The method’s compatibility with industrial information integration standards, micro-fabrication platforms, MEMS-oriented production environments, and edge control infrastructures makes it highly suitable for deployment in real-world smart and micro-manufacturing applications. Simulation studies confirm its effectiveness in maintaining system robustness and adaptability while avoiding unsafe trajectories. Future work will focus on practical deployment and integration within industrial and micro-manufacturing execution systems, as well as experimental validation on MEMS-based devices, industrial edge controllers, and cloud-based control infrastructures. To facilitate deployment, we also distill two practice-oriented points clarified in this revision-online update of unreliable events and the applicability beyond full local controllability/observability.
Online update of unreliable events: The detector graph does not depend on the reliable/unreliable split; only the labels produced by Algorithm 1 do. Therefore, if the set changes at runtime, each affected subsystem can recompute labels locally in linear time or hot-swap one of a few precomputed label tables for anticipated modes (e.g., a ‘resource-unreliable’ flag). The update is safety-monotone: declaring more events as unreliable can only shrink the enabled set and thus preserves safety while possibly becoming more conservative until a reliable suffix exists.
Finally, we note that the above study is carried out under a simplifying assumption of full local controllability and observability; the paragraph below outlines how the framework can be relaxed when this assumption is violated.
Limitations and extensions beyond full controllability/observability: The results above rely on full local controllability and observability. When some events are uncontrollable or unobservable, Algorithm 1 can be adapted as follows:
Limited control: Replace the reliable label set by the enforceable set . Then, in Step 3 (ForwardClosureRestricted on reliable labels), use instead of . This ensures that Strict states admit a reliable and controllable prefix inside .
Partial observation: Build an observer (or belief-state) automaton over the observable alphabet (or equivalently run Algorithm 1 on the fly over observed state sets using the projection ). This yields labels consistent with what supervisors can infer from observations.
Mixed case: Combine the two by running Algorithm 1 on the observer with enforceable labels .
A rigorous development, together with complexity/approximation techniques to mitigate observer blow-up, is left as future work.