Abstract
Micro Aerial Vehicles (MAVs) are a type of UAV that are both small and fully autonomous, making them ideal for both civilian and military applications. Modern MAVs can hover and navigate while carrying several sensors, operate over long distances, and send data to a portable base station. Despite their many benefits, MAVs often encounter obstacles due to limitations in the embedded system (such as memory, processing power, energy, etc.). Due to these obstacles and the use of open wireless communication channels, MAVs are vulnerable to a variety of cyber-physical attacks. Consequently, MAVs cannot execute complex cryptographic algorithms due to their limited computing power. In light of these considerations, this article proposes a conditional privacy-preserving generalized ring signcryption scheme for MAVs using an identity-based cryptosystem. Elliptic Curve Cryptography (ECC), with a key size of 160 bits, is used in the proposed scheme. The proposed scheme’s security robustness has been analyzed using the Random Oracle Model (ROM), a formal security evaluation method. The proposed scheme is also compared in terms of computation cost, communication cost and memory overhead against relevant existing schemes. The total computation cost of the proposed scheme is 7.76 ms, which is 8.14%, 5.20%, and 11.40% schemes. The results show that the proposed scheme is both efficient and secure, proving its viability.
1. Introduction
Micro Aerial Vehicles (MAVs) are getting a lot of attention from research organizations and businesses around the world [1]. These flying machines have proven their worth in situations where humans cannot reach or work efficiently, such as last-minute package delivery during rush hours or base searches in inaccessible areas of the battlefield. Compared to conventional methods, MAVs can significantly lower the risk to human life, increase the system’s efficiency, and shorten the time of operations. The broad capabilities of MAVs range from surveillance MAVs with fixed wings to advanced MAVs capable of hovering, navigation, carrying several sensors, and carrying out their missions up to several kilometers in range [2]. MAVs can transmit data to a portable base station and can exchange data with one another. A general architecture of MAVs network is depicted in Figure 1. Despite these benefits, MAVs are not suitable for real-time or processor-intensive applications because to their limited memory and processing power [3].
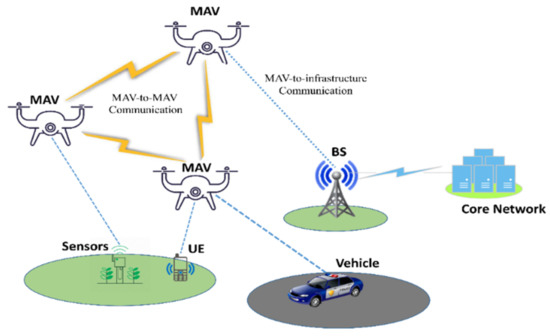
Figure 1.
General architecture of MAVs network.
Apart from the aforementioned constraints, the security measures to fight against cyber-attacks are rarely considered during the design of MAVs [4]. The security and privacy of the network could be severely compromised due to this vulnerability, which would have a devastating effect on data transmission and storage. There are a variety of ways a malicious attacker can compromise the MAVs system. The malicious attacker can, for instance, send several reservation requests, eavesdrop on control messages, or fake data. Wi-Fi-connected MAVs are more vulnerable to cyber-attacks than cellular-connected ones because of their less-reliable connections and weaker security measures [5]. Tracking MAV locations, tampering with onboard hardware, illegal data access, message modification, and fabrication are examples of common privacy and security concerns across the MAV system [6,7]. A major security concern that compromises the privacy of MAVs is a Global Positioning System (GPS) spoofing attack [8,9,10], in which an attacker exploits GPS signals. In this method, an adversary sends an MAV slightly stronger GPS signals in order to deviate it from its original mission. Therefore, given their extensive usage in current military and commercial applications, there is an urgent need for enhanced security measures for MAVs.
Authentication and confidentiality are two of the most important aspects of any security protocol design for ensuring secure communication, and the same is applicable for MAVs security. Encryption and digital signatures provide solutions for confidentiality and authenticity respectively. When both attributes are required simultaneously and in a single logical step for devices with limited resources, such as MAVs, signcryption [11] is preferred. In addition, generalized signcryption is an extension of the signcryption scheme that not only offers encryption and digital signature simultaneously, but also has the option to offer both independently, if desired. Such a characteristic is useful if one of the two essential characteristics, confidentiality or authenticity, is desired [12]. Generalized signcryption can be used in ring configurations, known as ring signcryption, which offers advantageous characteristics such as anonymity, spontaneity, flexibility, and equal membership [13]. A conditional privacy preserving property can be implemented in addition to generalized ring signcryption to guarantee recipient and sender identify anonymity. In this approach, each entity encrypts their real identity using a common secret key between entity and PKG in the key generation process rather than using the real identities of sender and receiver. PKG must first locate the secret key and real identity after obtaining the encrypted identity. The encrypted identities of each user for signcryption and unsigncryption are then published by PKG.
Zhou et al. [14] proposed a concrete scheme for generalized ring signcryption in an identity-based framework. The proposed technique is based on bilinear pairing, and a random oracle model (ROM) is used for the security analysis. Due to the fact that the scheme [14] is based on bilinear pairing, which involves computationally expensive cryptographic operations, it is not suited for resource-constrained devices with low processing capabilities, such as MAVs, to conduct such operations. In addition, the proposed scheme lacks conditional privacy-preserving characteristics. Caixue Zhou [15] proposed a certificate-based generalized ring signcryption method and a concrete methodology employing bilinear pairings for certificate-based cryptosystems. Using the ROM, the security hardness of the proposed system is evaluated. Again, this scheme [15] is not suitable for MAVs due to the high computation cost of bilinear pairing and the absence of conditional privacy-preserving attribute.
M. Luo and Y. Zhou [16] introduced an efficient conditional privacy-preserving authentication protocol based on generalized ring signcryption scheme. Generalized ring signcryption is proposed in this protocol to provide ring signature mode and ring signcryption mode inside a single algorithm in order to meet the diverse security needs of complicated application scenarios. A practical public verification technique is meant to make tracking results verifiable and more trustworthy. In addition, the protocol accomplishes secrecy, immutability, and Known Session-Specific Temporary Information Security (KSSTIS). However, the proposed protocol involves bilinear pairing-based multiplication, modular exponentials, and bilinear pairing in the combined ring signature and signcryption method, which is incompatible for MAVs. Khan et al. [17] presented an identity-based generalized signcryption with multi-access edge computing option to protect Flying Ad hoc Networks (FANETs). However, neither conditional privacy preservation nor ring signcryption are supported by the proposed scheme. Consequently, this scheme [17] does not ensure anonymity. Din et al. [18] presented an improved identity-based generalized signcryption scheme for secure multi-access edge computing-enabled FANETs. The proposed scheme supports neither conditional privacy preservation nor ring signcryption. Therefore, this approach [18] does not guarantee anonymity.
With the aforementioned facts and favorable features in mind, we provide a conditional privacy-preserving generalized ring signcryption scheme for MAVs in this work. Moreover, the proposed scheme is based on an Identity-based public key cryptosystem, which uses the user’s name, IP address, etc. as his/her public key, hence eliminating the requirement for a public key certificate. Then, a trusted third party known as the PKG produces all users’ private keys, which introduces a new issue known as the private key escrow problem. However, it is still quite beneficial in situations when the PKG is completely trusted. The following are the main contributions of the proposed scheme that distinguish it from existing schemes.
- We propose a conditional privacy-preserving generalized ring signcryption scheme for MAVs using the ECC operation.
- The proposed scheme is conditional privacy-preserving, meaning each entity encrypts its real identity using a common secret key between entity and PKG in the key generation process.
- The proposed scheme enables encryption and digital signature simultaneously as well as independently using generalized signcryption. In ring configurations mode, this scheme guarantees anonymity, spontaneity, flexibility, and equal membership.
- We conducted a formal security study using the Random Oracle Model (ROM) and found that the proposed scheme is secure against a wide range of cyber-attacks.
- Finally, the proposed scheme’s efficiency is compared to its counterparts, validating its low computation cost, communication cost and memory overhead.
The structure of the article is as follows: Section 2 provides preliminary information, the network model, and the syntax of the proposed scheme. In contrast, Section 3 includes a security analysis of the proposed scheme. In Section 4, performance analysis is discussed. The conclusion is contained in Section 5.
2. Preliminaries, Network Model and Syntax of the Proposed Scheme
This section includes preliminaries (elliptic curve cryptography, the elliptic curve decisional Diffie–Hellman problem, the elliptic curve discrete logarithm problem), syntax of the proposed scheme, network model and notations for the proposed scheme as shown in Table 1.

Table 1.
Notation table.
2.1. Preliminaries
2.1.1. Elliptic Curve Cryptography (ECC)
Suppose is a finite cyclic group on the elliptic curve (), is the finite field of with prime order , let , and is the generator of group ; the elliptic can be defined as follows: on . Suppose × based on the point, which is called infinity point on elliptic curve and congruence ≡ , where the values satisfying .
2.1.2. Elliptic Curve Decisional Diffie-Hellman Problem (ECDDHP)
Assume is the generator of group with prime order , and given (), extracting and from is called ECDDHP.
2.1.3. Elliptic Curve Discrete Logarithm Problem (ECDLP)
Assume ξ is the generator of group GECC with prime order q, and given (θ.ξ,ξ,K ∈ GECC), extracting θ from K = θ. ξ is called ECDLP.
2.2. Syntax
The syntax of the proposed scheme consists of the five sub-algorithms listed below.
- Initialization: The ground core network (GCN) can play the role private key generator (PKG), in which he/she can sets as his/her secret key, as his/her public key, and generates a public parameter set .
- Key Generation: The device that participates in a network as a legal user will send () to GCN by using open channel. Based on (), GCN first compute and recover the real identity . Then, GCN computes and send () to the legitimate user by using secure channel.
- Generalized Ring Signcryption: This algorithm will run by Micro Aerial Vehicle (MAV), in which the MAV take input that are () and produce the tuple ().
- Generalized Ring Signcryption Verifications: Given the tuple (), a user can verify ().
2.3. Network Model
Figure 2 depicts the network model of the proposed scheme, which includes entities such as MAVs and Base Station (BS) deployed to provide monitoring of a certain region. The proposed network model relies heavily on MAVs, which are outfitted with a camera, IMU, sensors, and GPS devices capable of handling a wide range of use cases. It allows for interaction between many MAVs and also between MAVs and fixed facilities. To establish a connection with the BS, the MAV makes use of 5G and Wi-Fi wireless technologies. The MAVs are able to talk to one another over Wi-Fi. The primary goal of a hybridised approach is to capitalise on the strengths of both technologies.
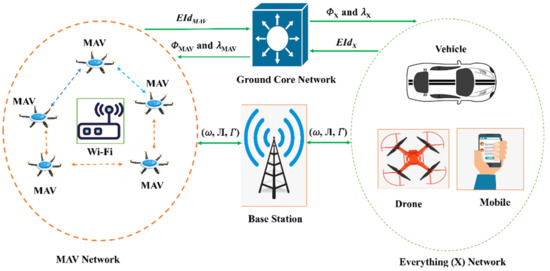
Figure 2.
Network model of the proposed scheme.
3. Proposed Scheme Construction
The construction of the proposed scheme includes the following steps.
Initialization: In this sub algorithm, a ground core network (GCN) can play the role private key generator (PKG) that can first choose his own secret key and compute a master public key as . then, GCN chooses three hash functions (, ) that are irreversible and collision resistant. At the end, GCN produces a public param , ).
Key Generation: In this sub algorithm, a device which participated in a network as a legal user will send his encrypted real identity , and to GCN by using open channel, where and . Based on (), GCN firs compute and recover the real identity as . Then, GCN choose , compute , , calculate , and send () to the legitimate user by using secure channel.
Generalized Ring Signcryption: This algorithm will run by MAV, in which the MAV first select his identity () from , and perform the following steps.
- MDN choose and compute .
- Compute and
- Compute and .
- MAV send () to everything (X).
Generalized Ring Signcryption Verifications: With the encrypted identity (), a user upon reception of () can perform the following steps.
- Compare if is holds, where .
- Compute and .
Correctness Analysis
The device at receiving end (X) can verify the signature as follows.
hence proved.
Furthermore, a device at receiving end (X) can made the decryption key as follows.
hence proved.
4. Security Analysis
In this section, we first show that the proposed scheme is secure against breaches of confidentiality and forgeability under the Random Oracle Model (ROM). Then, using an informal security analysis, we show that the proposed scheme is secure against an adversary attempting to violate sender and recipient anonymity. The subsequent theorems demonstrate that the proposed scheme provides security properties such as confidentiality, unforgeability, sender anonymity, and recipient anonymity, respectively.
Theorem 1.
Confidentiality: The proposed generalized ring signcryption is indistinguishable against intruder INT under the ROM, if ECDDHP is hard.
Proof.
Suppose the instances of elliptic curve is given to . To find and from , will play the following Game with .
Initialization: can first choose the secret key , public key , public parameter set . Then, sends to .
Phase 1: Here, can made the following queries with
- Query: send a request for Query with identity check for a tuple in the list , if is found, returns to . Otherwise, choose the value for randomly and returns it to .
- Query: send a request for Query with identity check for a tuple in the list , if is found, returns to . Otherwise, choose the value for randomly and returns it to .
- Query: send a request for Query with identity check for a tuple in the list , if is found, returns to . Otherwise, choose the value for randomly and returns it to .
User Public Key Query: send a request for User Public Key Query with check for a tuple in the list , if is found, returns to . Otherwise, perform the following two steps.
- At query, if , set .
- Else, compute , where it selects randomly.
- At the end, returns to
User Private Key Query: send a request for User Private Key Query with check for a tuple in the list , if stop further processing, otherwise he found the tuple and returns to .
Generalized Ring Signcryption Query: send a request for Generalized Ring Signcryption with and , where , and perform the following steps.
- If , It choose and compute .
- Compute and
- Compute and , where is randomly selected now here.
- send () to .
Generalized Ring Signcryption Verification Query: If , shows the tuple () is invalid. Otherwise, it normally Generalized Ring Signcryption Verification algorithm.
Challenge: send the tuple (, ) to , where , are the two plaintexts with same size but contains different contents. If , pick and perform the following computations.
- It computes .
- Compute and
- Compute and , where is randomly selected now here.
- returns ().
Phase 2: In this phase, INT executes Query, Query, Query, User Public Key Query, Generalized Ring Signcryption Query, and Generalized Ring Signcryption Verification Query, respectively. Note that at this stage INT should not perform User Private Key Query on encrypted identity and requested message corresponding to the Generalized ring signcrypted text.
Guess: INT return , if , outputs 1. Otherwise, outputs 0.
Probability Analysis: Suppose , and represent Query, Query, Query, User Public Key Query, and User Private Key Query, respectively. So, we express the following events.
- 1.
- succeeded in User Private Key Query.
- 2.
- succeeded in Generalized Ring Signcryption Verification Query.
- 3.
- succeeded in in challenge phase.
After denoting the above events, we can easily receive the following outcomes.
and , then ≈ ≈ , where represent the advantage of INT. □
Theorem 2.
Unforgeability. Our proposed generalized ring signcryption is indistinguishable against intruder INT under the random oracle model, if ECDLP is hard.
Proof.
Suppose the instance of elliptic curve () is given to so, to find from , will play the following Game with .
Initialization: can first choose the secret key , public key , public parameter set . Then, send to .
Queries: All the queries are processed is same as executed in Theorem 1-Confidentiality.
Forgery: wants to generate and verify combined ring signature and signcryption, in which he needs the private key of MAV and X (). can generate the forge signature as follows.
- choose and compute .
- Compute and
- Compute and .
- Returns ().
In the above process for forging a signature, INT can solve two-time ECDLP such as finding the values ().
Probability Analysis: Suppose , and represent Query, Query, Query, User Public Key Query, and User Private Key Query, respectively. So, we express the following events.
- 4.
- succeeded in User Private Key Query.
- 5.
- succeeded in Generalized Ring Signcryption Verification Query.
- 6.
- succeeded in in challenge phase.
After denoting the above events, we can easily receive the following outcomes.
and , then ≈ ≈ , where represents the advantage of INT. □
Theorem 3.
Sender Anonymity. In the key generation phase, the sender device called MAV will send his encrypted real identity, andto GCN by using open channel, where and. Based on (), GCN firs compute and recover the real identityas. Here, if INT wants the real identityof MAV, he will pass the following two cases.
- INT first struggle to access from to made .
- Secondly INT can access from to made .
In both the above cases, INT can solve ECDLP which will be infeasible for him/her.
Theorem 4.
Receiver Anonymity. In the key generation phase, the receiver device called will send his encrypted real identity, andto GCN by using open channel, where and. Based on (), GCN firs computeand recover the real identityas. Here, if INT wants the real identity of, he will pass the following two cases.
- INT first struggle to access from to made .
- Secondly INT can access from to made .
In both the above cases, INT can solve ECDLP, which will be infeasible for him/her.
5. Performance Comparison
This section compares the performance of the proposed scheme with the relevant existing counterparts proposed by Zhou et al. [14], Zhou et al. [15], and Luo and Zhou [16].
5.1. Computation Cost
The computation cost represents the operational expenses spent by each user during the proposed generalized ring signcryption process and existing comparable schemes proposed by Zhou et al. [14], Zhou et al. [15], and Luo and Zhou [16]. In Table 2, we list the key operations of the proposed scheme, including Elliptic Curve Point Multiplication (), Bilinear Pairing Based Multiplication (), Modular Exponentials (), and Bilinear Pairing (). Table 3 contains the operating expenses, measured in milliseconds (ms), for the proposed scheme, as well as those of Zhou et al. [14], Zhou et al. [15], and Luo and Zhou [16]. The time requires for a single takes 0.97 ms, and [19]. The Multi-Precision Integer and Rational Arithmetic C Library (MIRACL) [20] is used to assess the performance of the proposed scheme by testing the runtime of the core cryptographic operations up to 1000 times. Observations are made on a workstation with the following specifications: 8 GB RAM and the Windows 7 Home Basic 64-bit operating system [21]. As seen in Figure 3, the proposed scheme has a lower computation cost than the schemes proposed by Zhou et al. [14], Zhou et al. [15], and Luo and Zhou [16].

Table 2.
Comparison of computation cost with major operations.

Table 3.
Comparison of computation cost (in ms).
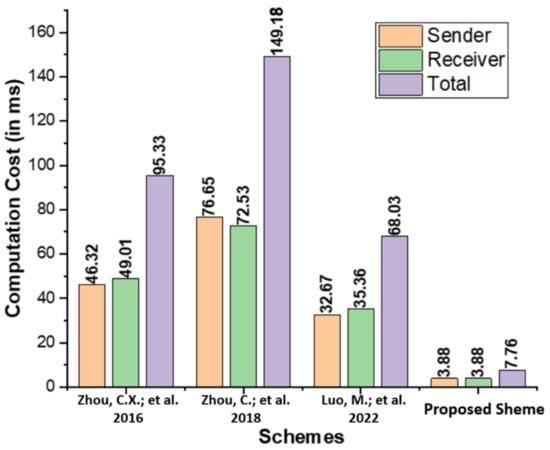
Figure 3.
Comparison of computation cost (in ms) [14,15,16].
5.2. Communication Cost
In this subsection, the proposed scheme is compared to existing schemes, namely those proposed by Zhou et al. [14], Zhou et al. [15], and Luo and Zhou [16], in terms of communication cost. We list the communication cost incurred based on the Elliptic Curve Parameter Size (|ECC q|), Bilinear Pairing Parameter Size (|BP G|), and a message size (|m|) for the proposed and those of Zhou et al. [14], Zhou et al. [15], and Luo and Zhou [16]. We have selected the bit values 160, 1024, and 1024 bits for (|ECC q|), (|m|), and (|BP G|) from [19]. In addition, the communication cost analysis between Zhou et al. [14], Zhou et al. [15], and Luo and Zhou [16] and the proposed scheme are provided in Table 4. As seen in Figure 4, the proposed scheme has a lower communication cost than the schemes proposed by Zhou et al. [14], Zhou et al. [15], and Luo and Zhou [16].

Table 4.
Comparison of communication cost (in bits).
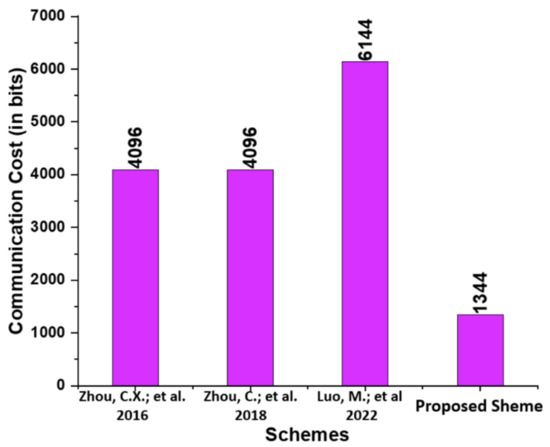
Figure 4.
Comparison of communication cost (in bits) [14,15,16].
5.3. Memory Overhead
The proposed scheme is compared in terms of memory overhead to existing schemes proposed by by Zhou et al. [14], Zhou et al. [15], and Luo and Zhou [16]. Table 5 describes the primary operations, and Table 6 compares the memory overhead in bits of the proposed scheme to that of relevant existing schemes. A significant reduction in memory space is achieved, as shown in Figure 5.

Table 5.
Memory Overhead Analysis.

Table 6.
Memory Overhead Analysis in Bits.
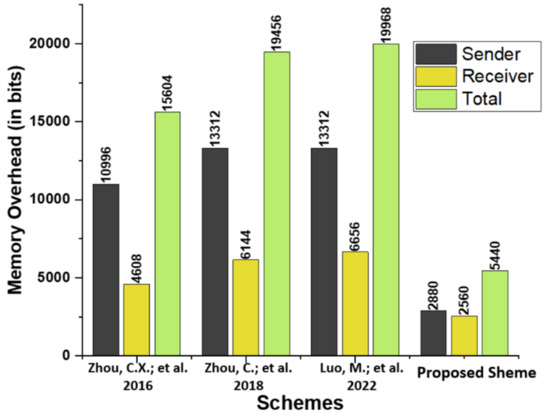
Figure 5.
Comparison of memory overhead (in bits) [14,15,16].
6. Conclusions
In this article, we proposed a conditional privacy-preserving generalized ring signcryption scheme for MAVs using an identity-based cryptosystem. The proposed scheme is developed using the Elliptic Curve Cryptography concept (ECC). A comprehensive security analysis of ROM indicates that the proposed method is robust to a number of attacks. Comparing the proposed scheme to similar schemes presented by Zhou et al. [14], Zhou et al. [15], and Luo and Zhou [16] with regard to commutation and communication costs. The results reveal that the proposed scheme is more cost-effective in terms of computation and communication costs than its current alternatives. In addition, the results demonstrate that the proposed method is suitable for MAV systems due to the algorithm’s functionality and reduced computation cost, communication cost and memory overhead.
Author Contributions
Conceptualization, I.U. and M.A.K.; Methodology, I.U., M.A.K., S.A.H.M. and A.M.A.; Software, A.M.A., S.A.H.M. and F.N.; Validation, M.A.K., F.N. and I.U.; Formal analysis, I.U. and M.A.K.; Investigation, I.U. and M.A.K.; Resources, M.A.K., F.A., N.I., S.A.H.M. and A.M.A.; Data curation, M.A.K., A.M.A., F.A., N.I. and S.A.H.M.; Writing—original draft preparation, M.A.K., S.A.H.M. and A.M.A.; Writing—review and editing, M.A.K., S.A.H.M. and A.M.A.; Visualization, A.M.A.; Funds Acquisitions, N.I.; Supervision, F.N. and M.A.K. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by AlMaarefa University, Riyadh, Saudi Arabia (TUMA-2021-57).
Data Availability Statement
Not applicable.
Acknowledgments
Nisreen Innab would like to express her gratitude to AlMaarefa University, Riyadh, Saudi Arabia, for providing funding (TUMA-2021-57) to do this research.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Mohsan, S.A.H.; Othman, N.Q.H.; Khan, M.A.; Amjad, H.; Żywiołek, J. A Comprehensive Review of Micro UAV Charging Techniques. Micromachines 2022, 13, 977. [Google Scholar] [CrossRef] [PubMed]
- Liu, X.; Chen, S.W.; Nardari, G.V.; Qu, C.; Ojeda, F.C.; Taylor, C.J.; Kumar, V. Challenges and Opportunities for Autonomous Micro-UAVs in Precision Agriculture. IEEE Micro 2022, 42, 61–68. [Google Scholar] [CrossRef]
- Ahmed, F.; Mohanta, J.C.; Keshari, A.; Yadav, P.S. Recent Advances in Unmanned Aerial Vehicles: A Review. Arab. J. Sci. Eng. 2022, 47, 7963–7984. [Google Scholar] [CrossRef] [PubMed]
- Noor, F.; Khan, M.A.; Al-Zahrani, A.; Ullah, I.; Al-Dhlan, K.A. A Review on Communications Perspective of Flying Ad-Hoc Networks: Key Enabling Wireless Technologies, Applications, Challenges and Open Research Topics. Drones 2020, 4, 65. [Google Scholar] [CrossRef]
- Khan, M.A.; Kumar, N.; Mohsan, S.A.H.; Khan, W.U.; Nasralla, M.M.; Alsharif, M.H.; Zywiolek, J.; Ullah, I. Swarm of UAVs for Network Management in 6G: A Technical Review. IEEE Trans. Netw. Serv. Manag. 2022. [Google Scholar] [CrossRef]
- Khan, M.A.; Ullah, I.; Alkhalifah, A.; Rehman, S.U.; Shah, J.A.; Uddin, I.I.; Alsharif, M.H.; Algarni, F. A Provable and Privacy-Preserving Authentication Scheme for UAV-Enabled Intelligent Transportation Systems. IEEE Trans. Ind. Inform. 2021, 18, 3416–3425. [Google Scholar] [CrossRef]
- Krishna, C.G.L.; Murphy, R.R. A review on cybersecurity vulnerabilities for unmanned aerial vehicles. In Proceedings of the 2017 IEEE International Symposium on Safety, Security and Rescue Robotics (SSRR), Shanghai, China, 11–13 October 2017; pp. 194–199. [Google Scholar]
- Guo, Y.; Wu, M.; Tang, K.; Tie, J.; Li, X. Covert Spoofing Algorithm of UAV Based on GPS/INS-Integrated Navigation. IEEE Trans. Veh. Technol. 2019, 68, 6557–6564. [Google Scholar] [CrossRef]
- Eldosouky, A.R.; Ferdowsi, A.; Saad, W. Drones in Distress: A Game-Theoretic Countermeasure for Protecting UAVs Against GPS Spoofing. IEEE Internet Things J. 2019, 7, 2840–2854. [Google Scholar] [CrossRef]
- Arteaga, S.P.; Hernandez, L.A.M.; Perez, G.S.; Orozco, A.L.S.; Villalba, L.J.G. Analysis of the GPS Spoofing Vulnerability in the Drone 3DR Solo. IEEE Access 2019, 7, 51782–51789. [Google Scholar] [CrossRef]
- Zheng, Y. Digital signcryption or how to achieve cost (signature & encryption) << cost (signature) + cost (encryption). In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 17–21 August 1997; Springer: Berlin/Heidelberg, Germany, 1997; pp. 165–179. [Google Scholar]
- Han, Y.; Yang, X.; Wei, P.; Wang, Y.; Hu, Y. ECGSC: Elliptic curve based generalized signcryption. In Proceedings of the Third International Conference Ubiquitous Intelligence and Computing of Lecture Notes in Computer Science, Wuhan, China, 3–6 September 2006; Springer: Berlin/Heidelberg, Germany, 2006; Volume 4159, pp. 956–965. [Google Scholar]
- Wang, L.; Zhang, G.; Ma, C. A Secure Ring Signcryption Scheme for Private and Anonymous Communication. In Proceedings of the 2007 IFIP International Conference on Network and Parallel Computing Workshops (NPC 2007), Dalian, China, 18–21 September 2007; Springer: Berlin/Heidelberg, Germany, 1997; pp. 107–111. [Google Scholar]
- Zhou, C.X.; Cui, Z.M.; Gao, G.Y. Efficient identity-based generalized ring signcryption scheme. KSII Trans. Internet Inf. Syst. 2016, 10, 5553–5571. [Google Scholar]
- Zhou, C.; Gao, G.; Cui, Z.; Zhao, Z. Certificate-based generalized ring signcryption scheme. Int. J. Found. Comput. Sci. 2018, 29, 1063–1088. [Google Scholar] [CrossRef]
- Luo, M.; Zhou, Y. An Efficient Conditional Privacy-preserving Authentication Protocol Based on Generalized Ring Signcryption for VANETs. IEEE Trans. Veh. Technol. 2022, 71, 10001–10015. [Google Scholar] [CrossRef]
- Khan, M.A.; Ullah, I.; Nisar, S.; Noor, F.; Qureshi, I.M.; Khanzada, F.; Khattak, H.; Aziz, M.A. Multi-access Edge Computing (MEC) Enabled Flying Ad-hoc Networks with Secure Deployment Using Identity Based Generalized Signcryption. Mob. Inf. Syst. 2020, 2020, 8861947. [Google Scholar]
- Din, N.; Waheed, A.; Zareei, M.; Alanazi, F. An Improved Identity-Based Generalized Signcryption Scheme for Secure Multi-Access Edge Computing Empowered Flying Ad Hoc Networks. IEEE Access 2021, 9, 120704–120714. [Google Scholar] [CrossRef]
- Khan, M.A.; Ullah, I.; Alsharif, M.H.; Alghtani, A.H.; Aly, A.A.; Chen, C.M. An Efficient Certificate-Based Aggregate Signature Scheme for Internet of Drones. Secur. Commun. Netw. 2022, 2022, 9718580. [Google Scholar] [CrossRef]
- Shamus Sofware Ltd. Miracl Library. Available online: http://github.com/miracl/MIRACL (accessed on 2 August 2022).
- Zhou, C.; Zhao, Z.; Zhou, W.; Mei, Y. Certificateless Key-Insulated Generalized Signcryption Scheme without Bilinear Pairings. Secur. Commun. Netw. 2017, 2017, 8405879. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).