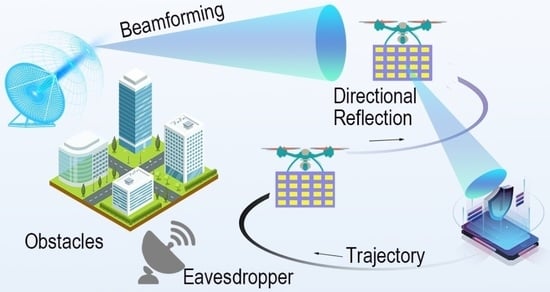
Passive Beamforming and Trajectory Optimization for Reconfigurable Intelligent Surface-Assisted UAV Secure Communication
Abstract
:1. Introduction
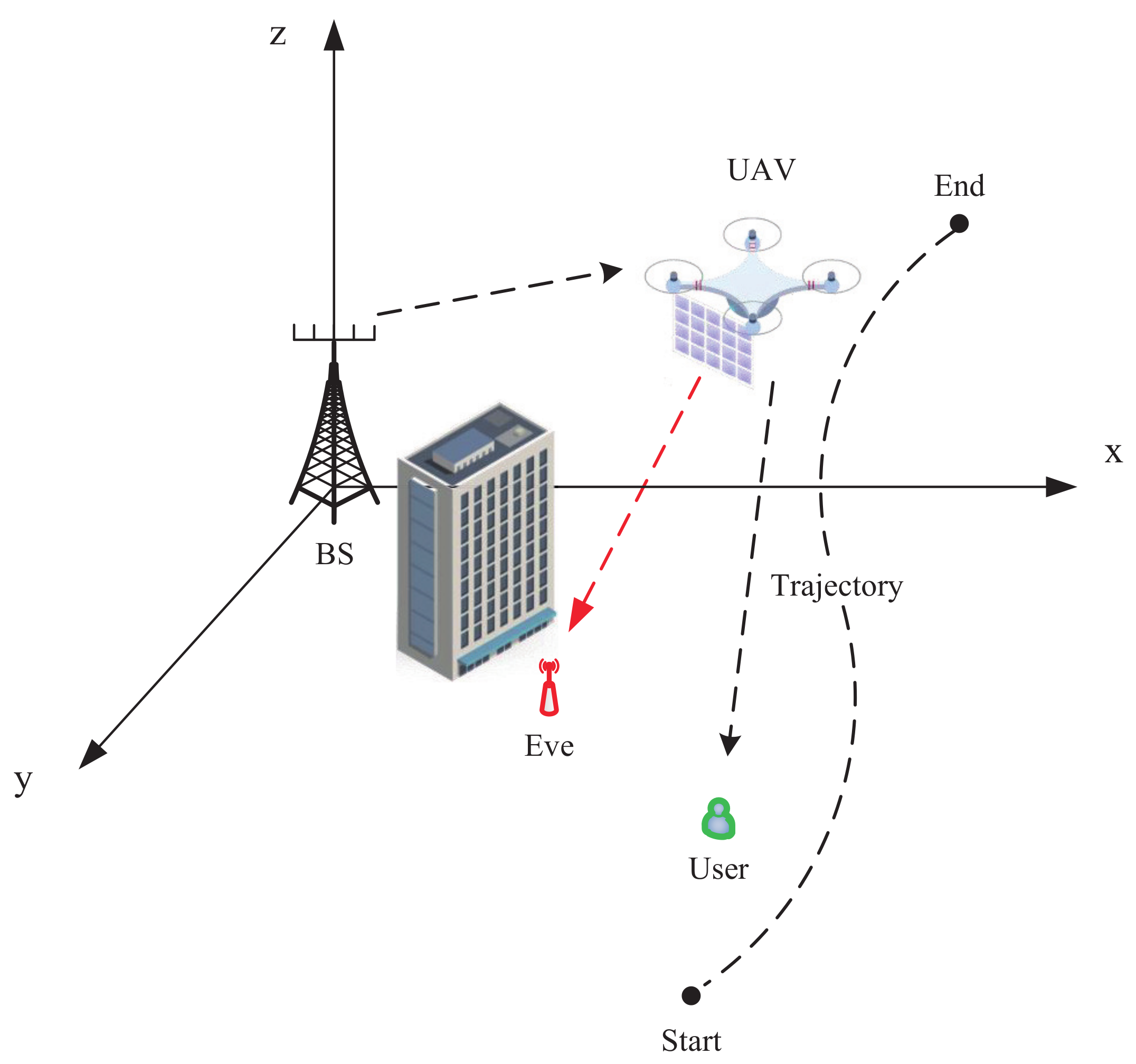
2. System Model
3. The RIS-Aided UAV Secure Transmission
| Algorithm 1: The AO Algorithm for the Power Allocation and Phase Shift and Trajectory Design |
 |
3.1. BS’s Beamforming Strategy
- (1)
- Eavesdropping elimination method
- (2)
- Destination aiming method
3.2. Phase Shift Optimization
- (1)
- Calculation of Riemannian gradient:Riemannianian gradient is the orthogonal projection of f of Euclidean gradient on the complex field as
- (2)
- Tangent vector of search direction:is the vector transfer function, which is defined as
- (3)
- The tangent vector is projected onto a complex circular manifold:is the size of the Armijo step [35] (We use the Armijo rule for descent in Riemannian manifolds, and provides a detailed description).
3.3. UAV’s Trajectory Optimization
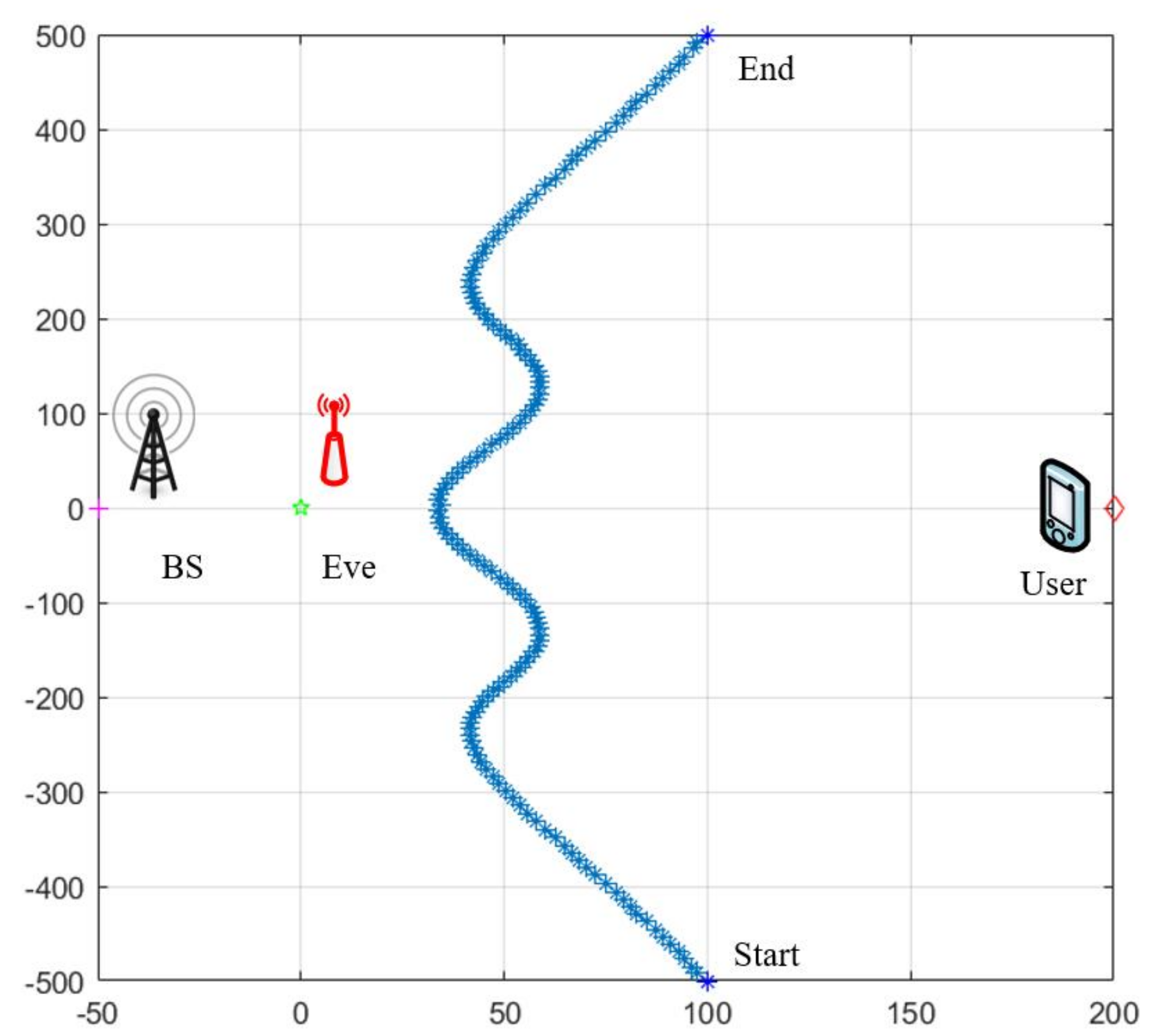
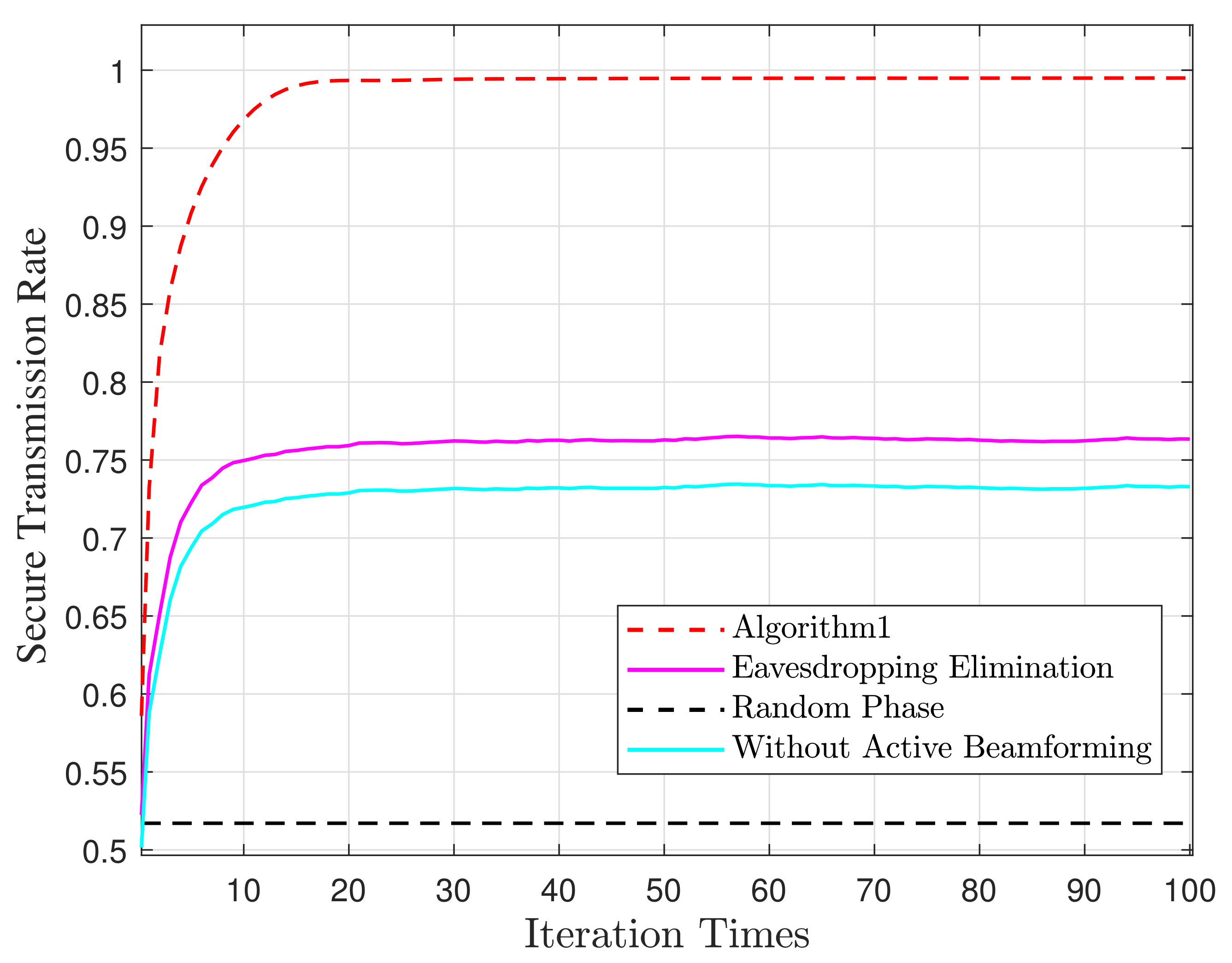
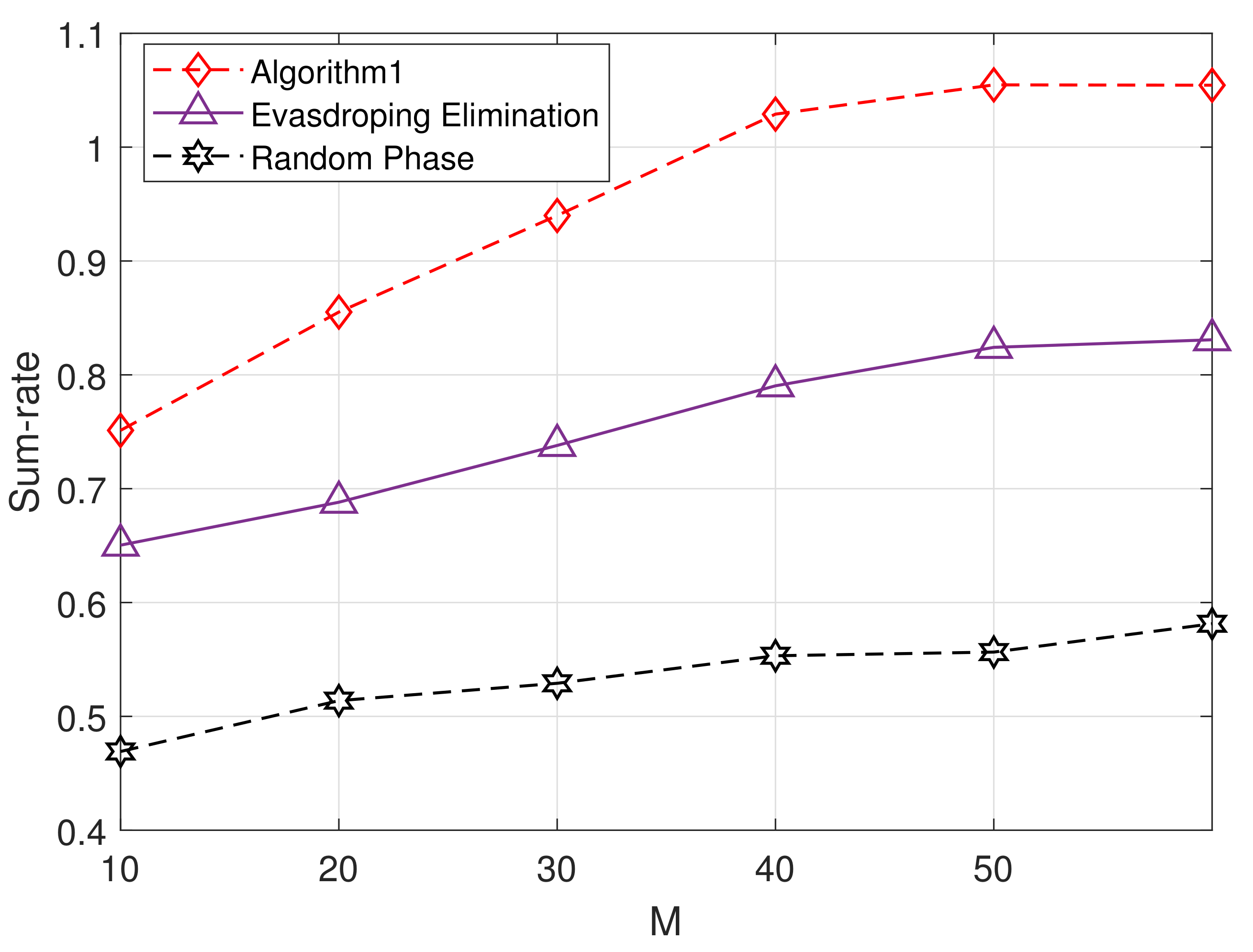
4. Simulation Results
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Ding, R.; Gao, F.; Shen, X.S. 3D UAV Trajectory Design and Frequency Band Allocation for Energy-Efficient and Fair Communication: A Deep Reinforcement Learning Approach. IEEE Trans. Wirel. Commun. 2020, 19, 7796–7809. [Google Scholar] [CrossRef]
- Wang, H.; Ding, G.; Gao, F.; Chen, J.; Wang, J.; Wang, L. Power Control in UAV-Supported Ultra Dense Networks: Communications, Caching, and Energy Transfer. IEEE Commun. Mag. 2018, 56, 28–34. [Google Scholar] [CrossRef] [Green Version]
- Zeng, Y.; Zhang, R.; Lim, T.J. Wireless communications with unmanned aerial vehicles: Opportunities and challenges. IEEE Commun. Mag. 2016, 54, 36–42. [Google Scholar] [CrossRef] [Green Version]
- Zhao, M.; Shi, Q.; Zhao, M. Efficiency Maximization for UAV-Enabled Mobile Relaying Systems With Laser Charging. IEEE Trans. Wirel. Commun. 2020, 19, 3257–3272. [Google Scholar] [CrossRef] [Green Version]
- Zhang, H.; Zhang, J.; Long, K. Energy Efficiency Optimization for NOMA UAV Network With Imperfect CSI. IEEE J. Sel. Areas Commun. 2020, 38, 2798–2809. [Google Scholar] [CrossRef]
- Wu, Q.; Zhang, R. Intelligent Reflecting Surface Enhanced Wireless Network via Joint Active and Passive Beamforming. IEEE Trans. Wirel. Commun. 2019, 18, 5394–5409. [Google Scholar] [CrossRef] [Green Version]
- Di, M.; Zappone, A.; Debbah, M.; Alouini, M.; Yuen, C.; Rosny, J.; Tretyakov, S. Smart Radio Environments Empowered by Reconfigurable Intelligent Surfaces: How It Works, State of Research, and The Road Ahead. IEEE J. Sel. Areas Commun. 2020, 38, 2450–2525. [Google Scholar]
- Liu, Y.; Zhang, S.; Gao, F.; Tang, J.; Dobre, O.A. Cascaded Channel Estimation for RIS Assisted mmWave MIMO Transmissions. IEEE Wirel. Commun. Lett. 2021, 10, 2065–2069. [Google Scholar] [CrossRef]
- Wu, Q.; Zhang, R. Towards Smart and Reconfigurable Environment: Intelligent Reflecting Surface Aided Wireless Network. IEEE Commun. Mag. 2020, 58, 106–112. [Google Scholar] [CrossRef] [Green Version]
- Zhang, H.; Zhang, H.; Liu, W.; Long, K.; Dong, J.; Leung, V.C.M. Energy Efficient User Clustering, Hybrid Precoding and Power Optimization in Terahertz MIMO-NOMA Systems. IEEE J. Sel. Areas Commun. 2020, 38, 2074–2085. [Google Scholar] [CrossRef]
- Liang, Y.; Long, R.; Zhang, Q.; Chen, J.; Cheng, H.V.; Guo, H. Large Intelligent Surface/Antennas (LISA): Making Reflective Radios Smart. J. Commun. Inf. Netw. 2019, 4, 40–50. [Google Scholar]
- Yang, L.; Yang, J.; Xie, W.; Hasna, M.O.; Tsiftsis, T.; Renzo, M.D. Secrecy Performance Analysis of RIS-Aided Wireless Communication Systems. IEEE Trans. Veh. Technol. 2020, 69, 12296–12300. [Google Scholar] [CrossRef]
- He, Y.; Zhai, D.; Jiang, Y.; Zhang, R. Relay selection for UAV-assisted urban vehicular ad hoc networks. IEEE Wirel. Commun. Lett. 2020, 9, 1379–1383. [Google Scholar] [CrossRef]
- He, Y.; Zhai, D.; Huang, F.; Wang, D.; Tang, X.; Zhang, R. Joint task offloading, resource allocation, and security assurance for mobile edge computing-enabled UAV-assisted VANETs. Remote Sens. 2021, 13, 1547. [Google Scholar] [CrossRef]
- Zhang, Q.; Saad, W.; Bennis, M.; Lu, X.; Debbah, M. Predictive Deployment of UAV Base Stations in Wireless Networks: Machine Learning Meets Contract Theory. IEEE Trans. Wirel. Commun. 2021, 20, 637–652. [Google Scholar] [CrossRef]
- Wei, Z.; Cai, Y.; Sun, Z.; Ng, D.W.K.; Yuan, J. Sum-Rate Maximization for IRS-Assisted UAV OFDMA Communication Systems. IEEE Trans. Wirel. Commun. 2020, 20, 2530–2550. [Google Scholar] [CrossRef]
- Hua, M.; Yang, L.; Wu, Q.; Pan, C.; Li, C.; Swindlehurst, A.L. UAV-Assisted Intelligent Reflecting Surface Symbiotic Radio System. IEEE Trans. Wirel. Commun. 2021, 20, 5769–5785. [Google Scholar] [CrossRef]
- Fang, S.; Chen, G.; Li, Y. Joint Optimization for Secure Intelligent Reflecting Surface Assisted UAV Networks. IEEE Wirel. Commun. Lett. 2021, 10, 276–280. [Google Scholar] [CrossRef]
- Mu, X.; Liu, Y.; Guo, L.; Lin, J.; Poor, H.V. Intelligent Reflecting Surface Enhanced Multi-UAV NOMA Networks. IEEE J. Sel. Areas Commun. 2021, 39, 3051–3066. [Google Scholar] [CrossRef]
- Ji, B.; Li, Y.; Cao, D.; Li, C.; Mumtaz, S.; Wang, D. Secrecy Performance Analysis of UAV Assisted Relay Transmission for Cognitive Network With Energy Harvesting. IEEE Trans. Veh. Technol. 2020, 69, 7404–7415. [Google Scholar] [CrossRef]
- Wang, D.; He, Y.; Yu, K.; Srivastava, G.; Nie, L.; Zhang, R. Delay sensitive secure NOMA transmission for hierarchical HAP-LAP medical-care IoT networks. IEEE Trans. Ind. Informat. 2021. [Google Scholar] [CrossRef]
- Shafique, T.; Tabassum, H.; Hossain, E. Optimization of Wireless Relaying With Flexible UAV-Borne Reflecting Surfaces. IEEE Trans. Commun. 2021, 69, 309–325. [Google Scholar] [CrossRef]
- Mahmoud, A.; Muhaidat, S.; Sofotasios, P.; Abualhaol, I.; Dobre, O.A.; Yanikomeroglu, H. Intelligent Reflecting Surfaces Assisted UAV Communications for IoT Networks: Performance Analysis. IEEE Trans. Green Commun. Netw. 2021, 5, 1029–1040. [Google Scholar] [CrossRef]
- Wang, D.; Ren, P.; Cheng, J. Cooperative Secure Communication in Two-Hop Buffer-Aided Networks. IEEE Trans. Commun. 2018, 66, 972–985. [Google Scholar] [CrossRef]
- Zhou, G.; Pan, C.; Ren, H.; Wang, K.; Peng, Z. Secure Wireless Communication in RIS-Aided MISO System With Hardware Impairments. IEEE Wirel. Commun. Lett. 2021, 10, 1309–1313. [Google Scholar] [CrossRef]
- Tang, X.; Lan, X.; Zhai, D.; Zhang, R.; Han, Z. Securing Wireless Transmissions with RIS-Receiver Coordination: Passive Beamforming and Active Jamming. IEEE Trans. Veh. Technol. 2021, 70, 6260–6265. [Google Scholar] [CrossRef]
- Trigui, I.; Ajib, W.; Zhu, W.-P. Secrecy Outage Probability and Average Rate of RIS-Aided Communications Using Quantized Phases. IEEE Commun. Lett. 2021, 25, 1820–1824. [Google Scholar] [CrossRef]
- Wu, Q.; Zhang, R. Intelligent Reflecting Surface Enhanced Wireless Network: Joint Active and Passive Beamforming Design. In Proceedings of the IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar]
- Han, Y.; Tang, W.; Jin, S.; Wen, C.-K.; Ma, X. Large Intelligent Surface-Assisted Wireless Communication Exploiting Statistical CSI. IEEE Trans. Veh. Technol. 2019, 68, 8238–8242. [Google Scholar] [CrossRef] [Green Version]
- Tse, D.; Viswanath, P. Fundamentals of Wireless Communication; Cambridge University, Press: Cambridge, UK, 2005. [Google Scholar]
- Mishra, D.; Johansson, H. Channel Estimation and Low-complexity Beamforming Design for Passive Intelligent Surface Assisted MISO Wireless Energy Transfer. In Proceedings of the ICASSP 2019–2019 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Brighton, UK, 12–17 May 2019; pp. 4659–4663. [Google Scholar]
- Basilevsky, A. Applied Matrix Algebra in the Statistical Sciences; Courier Corporation: New York, NY, USA, 2013. [Google Scholar]
- Friedlander, B.; Porat, B. Performance analysis of a null-steering algorithm based on direction-of-arrival estimation. IEEE Trans. Acoust. Speech Signal Process. 1989, 37, 461–466. [Google Scholar] [CrossRef]
- Guo, H.; Liang, Y.; Chen, J.; Larsson, E.G. Weighted Sum-Rate Maximization for Reconfigurable Intelligent Surface Aided Wireless Networks. IEEE Trans. Wirel. Commun. 2020, 19, 3064–3076. [Google Scholar] [CrossRef] [Green Version]
- Absil, P.A.; Mahony, R.; Sepulchre, R. Optimization Algorithms on Matrix Manifolds; Princeton University Press: Princeton, NJ, USA, 2008. [Google Scholar]
- Wang, T.; Vandendorpe, L. Successive convex approximation based methods for dynamic spectrum management. In Proceedings of the IEEE International Conference on Communications, Ottawa, ON, Canada, 10–15 June 2012; pp. 4061–4065. [Google Scholar]
- Huang, C.; Zappone, A.; Alexandropoulos, G.C.; Debbah, M.; Yuen, C. Reconfigurable Intelligent Surfaces for Energy Efficiency in Wireless Communication. IEEE Trans. Wirel. Commun. 2019, 18, 4157–4170. [Google Scholar] [CrossRef] [Green Version]
- Björnson, E.; Sanguinetti, L.; Hoydis, J.; Debbah, M. Optimal Design of Energy-Efficient Multi-User MIMO Systems: Is Massive MIMO the Answer? IEEE Trans. Wirel. Commun. 2015, 14, 3059–3075. [Google Scholar] [CrossRef] [Green Version]

| Parameters | Values |
|---|---|
| Time slot | 1s |
| Maximum speed of UAV | 10m/s |
| Horizontal height of UAV | 100m |
| Starting position of UAV | (100, −500) |
| Ending position of UAV | (100, 500) |
| Position of BS | (−50, 0) |
| Position of EVE | (0, 0) |
| Position of User | (200, 0) |
| Path-loss for LoS channel | |
| Path-loss for NLoS channel | |
| Transmission bandwidth | 180 kHz |
| Noise power spectral density | −170 dBm/Hz |
| Maximum transmission power | 10 dBm |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, D.; Zhao, Y.; He, Y.; Tang, X.; Li, L.; Zhang, R.; Zhai, D. Passive Beamforming and Trajectory Optimization for Reconfigurable Intelligent Surface-Assisted UAV Secure Communication. Remote Sens. 2021, 13, 4286. https://doi.org/10.3390/rs13214286
Wang D, Zhao Y, He Y, Tang X, Li L, Zhang R, Zhai D. Passive Beamforming and Trajectory Optimization for Reconfigurable Intelligent Surface-Assisted UAV Secure Communication. Remote Sensing. 2021; 13(21):4286. https://doi.org/10.3390/rs13214286
Chicago/Turabian StyleWang, Dawei, Yang Zhao, Yixin He, Xiao Tang, Lixin Li, Ruonan Zhang, and Daosen Zhai. 2021. "Passive Beamforming and Trajectory Optimization for Reconfigurable Intelligent Surface-Assisted UAV Secure Communication" Remote Sensing 13, no. 21: 4286. https://doi.org/10.3390/rs13214286
APA StyleWang, D., Zhao, Y., He, Y., Tang, X., Li, L., Zhang, R., & Zhai, D. (2021). Passive Beamforming and Trajectory Optimization for Reconfigurable Intelligent Surface-Assisted UAV Secure Communication. Remote Sensing, 13(21), 4286. https://doi.org/10.3390/rs13214286