Decision Support System Based on Indoor Location for Personnel Management
Abstract
1. Introduction
2. Discovering the Location
- The employee’s receiver is continuously searching for beacons placed as reference points.
- At least one beacon should be detected in each iteration, and a minimum of three beacons is recommended, for allowing to the receiver to perform the necessary calculations to determine the location.
- The RSSI associated to the discovered beacons must be converted to distance using [16].
- With that set of distances and the beacons identifiers, whenever possible, the receiver performs a triangulation to resolve its own position.
- The computed location is sent to the system in order to report the employee’s position. Section 3 will show that the location is not sent in plain mode.
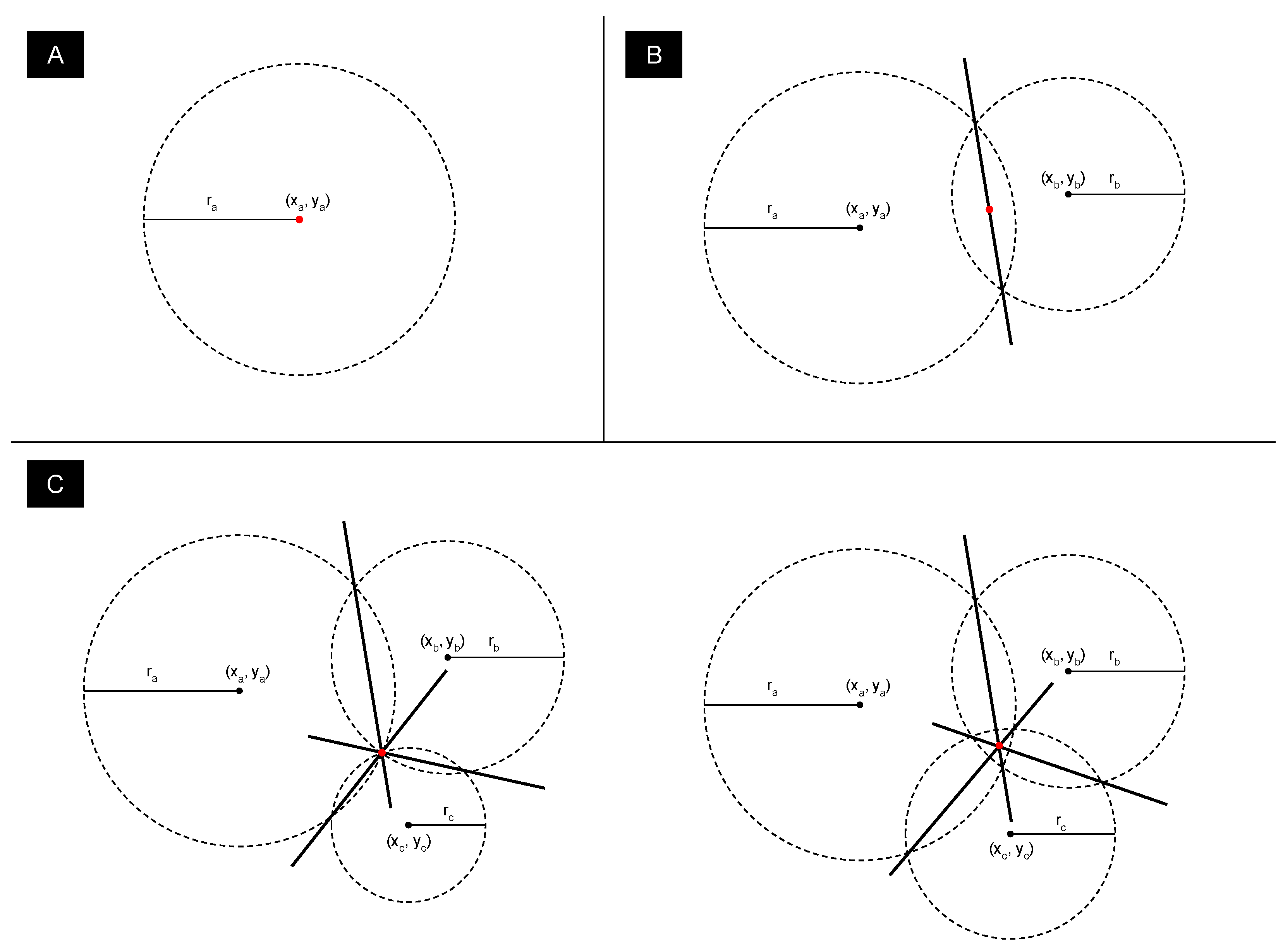
3. Preservation of the Privacy
- Completeness. With a true statement, an honest V will be convinced with high probability by an honest P. Honesty implies that the scheme is followed correctly by both parties.
- Soundness. With an invalid statement, V is convinced of the contrary with very small probability.
- Zero-Knowledge. For a valid statement, V learns no information except that the statement is valid.
- Non-Interactivity due to the need to reduce communications between P and V as well as to allow V to verify the suitability of a set of candidates by itself.
- Proof of Range due to the fact that the desired location cannot be compared to an exact point. This range is used to determine if a person is within a range of the desired location.
Non-Interactive Zero-Knowledge Range Proof Scheme
4. Decision Support System
- Define the boundaries and the identifiers of each floor plan.
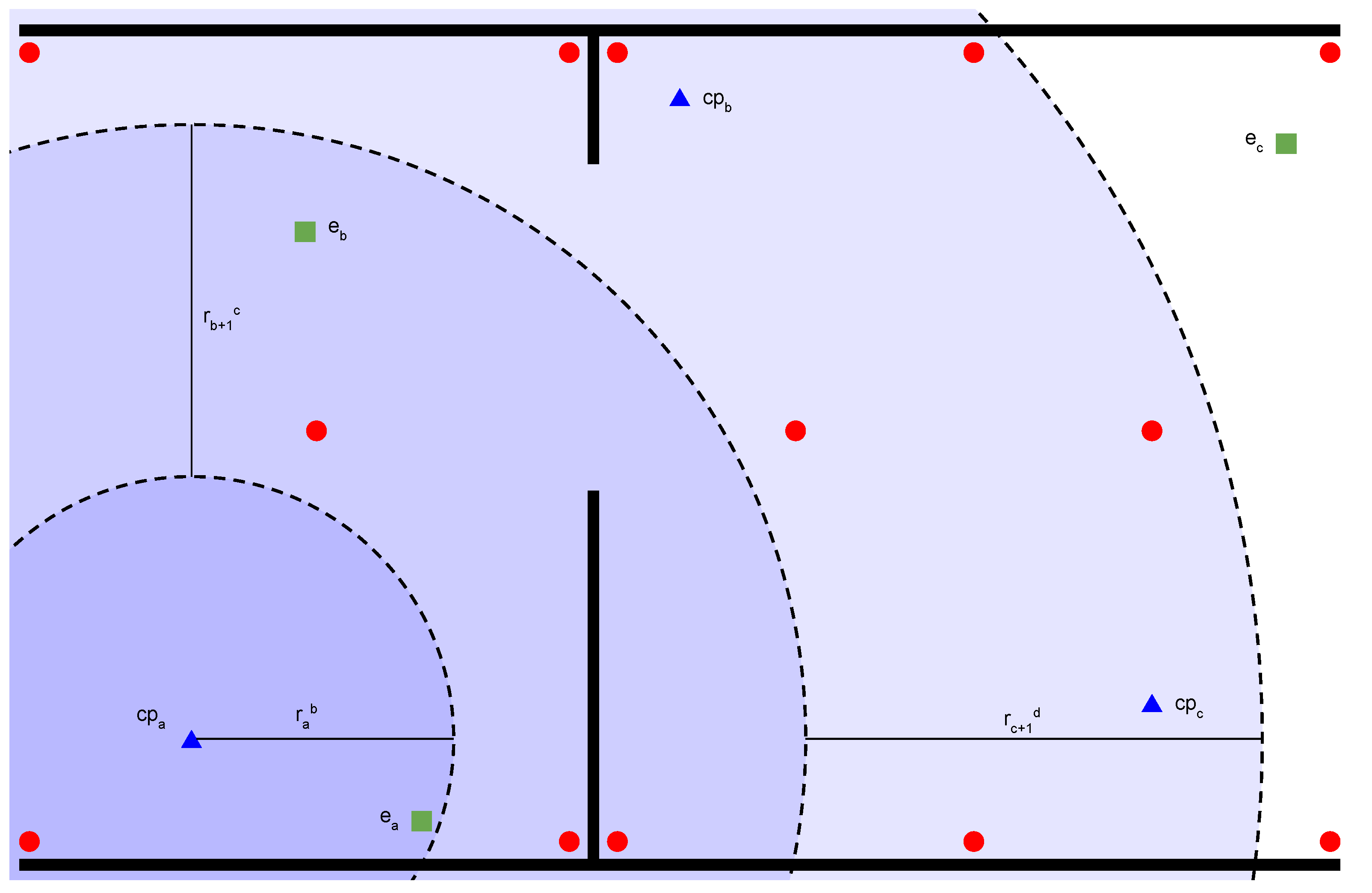
- Place and configure beacons correctly, as shown with red dots in Figure 3. This means that each beacon will be registered with a unique identifier and the coordinates where it will be located, allowing the DSS to determine the relative location through triangulation. They should be placed trying to cover the floor in such a way that the receiver detects at least three signals at the same time to minimize the number cases where it only finds one or two beacons.
- Define all control points within the boundaries of the floor plan, as shown with blue triangles in Figure 3. These points are used to calculate the distances to the receiver. The activities will be defined with some details and one of them is its location which will be located in one of those control points. In addition, a maximum distance is defined here to rule out people who are too far from the control point where the activity is required.
- Enroll all employees in the system. They should be able to communicate with the system, preferably in a secure way, in order to publish the commitments of their location as well as be able to receive assignments.
- Define factors and their weight to make decisions based on them, so that is the score associated to a particular employee, where f is a factor and w is its weight. The employee with the highest score will be selected to perform the activity.
- Agree on the distance ranges as well as the common cryptographic parameters for the calculation of the NIZKR commitment and secure communications. As mentioned above, ranges should be an integer range such that where a is the lower bound and b is the upper bound. For example, the range is represented by the range where and . More than one range could be defined and would be treated as independent factors. In Figure 3, the ranges , , and have been illustrated in order to define a possible scenario where the weight of being in the range is greater than the weight of being in the range . For example, the system can be configured to consider the ranges , and . In this situation, the employee will be selected before the employee if all other factors are considered equal.
- Presumably, a set of beacons has been detected. With those signals, the receiver are able to compute its location using triangulation methods described above.
- With the location computed, the receiver calculates its distance to nearby control points. For example, the employee shown in Figure 3 should compute the distance to control points and but not with the control point if its distance is greater than the maximum distance defined in the system configuration.
- In order to preserve privacy, the calculated distances will not be shared even in encrypted form. Instead, knowing distances to control points, the receiver calculates a NIZKR commitment for each nearby control point.
- Each of the computed NIZKR commitment is sent to the DSS properly tagged. Figure 3 where red dots are beacons, blue triangles are control points and green squares are employees shows a possible scenario. There, the employee will send the tuple where is the unique identifier of the employee, is the control point at which the proof was computed, and is the NIZKR commitment. Also, this employee must submit all tuples calculated with the other nearby control points. These proofs allow the system to know that a particular employee is within a distance range of a certain control point, but without knowing the exact location of the employee.
5. Conclusions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Harris, H.; Brewster, C.; Sparrow, P. International Human Resource Management; CIPD Publishing: London, UK, 2003. [Google Scholar]
- Legato, P.; Monaco, M.F. Human resources management at a marine container terminal. Eur. J. Oper. Res. 2004, 156, 769–781. [Google Scholar] [CrossRef]
- Schneider, A.M.; Oppel, E.M.; Winter, V. Explaining variations in hospitals’ use of strategic human resource management: How environmental and organizational factors matter. Health Care Manag. Rev. 2021, 46, 2–11. [Google Scholar] [CrossRef] [PubMed]
- He, W.; Tan, E.L.; Lee, E.W.; Li, T.Y. A solution for integrated track and trace in supply chain based on RFID & GPS. In Proceedings of the IEEE Conference on Emerging Technologies & Factory Automation, Mallorca, Spain, 22–25 September 2009; pp. 1–6. [Google Scholar] [CrossRef]
- Chumkamon, S.; Tuvaphanthaphiphat, P.; Keeratiwintakorn, P. A Blind Navigation System Using RFID for Indoor Environments. In Proceedings of the 5th International Conference on Electrical Engineering/Electronics, Computer, Telecommunications and Information Technology, Krabi, Thailand, 14–17 May 2008; pp. 765–768. [Google Scholar] [CrossRef]
- Cantón Paterna, V.; Calveras Augé, A.; Paradells Aspas, J.; Pérez Bullones, M.A. A Bluetooth Low Energy Indoor Positioning System with Channel Diversity, Weighted Trilateration and Kalman Filtering. Sensors 2017, 17, 2927. [Google Scholar] [CrossRef] [PubMed]
- Yang, C.; Shao, H. WiFi-based indoor positioning. IEEE Commun. Mag. 2015, 53, 150–157. [Google Scholar] [CrossRef]
- Kriz, P.; Maly, F.; Kozel, T. Improving indoor localization using bluetooth low energy beacons. Mob. Inf. Syst. 2016, 2016, 2083094. [Google Scholar] [CrossRef]
- Yoon, P.K.; Zihajehzadeh, S.; Kang, B.S.; Park, E.J. Adaptive Kalman filter for indoor localization using Bluetooth Low Energy and inertial measurement unit. In Proceedings of the 2015 37th Annual International Conference of the IEEE Engineering in Medicine and Biology Society (EMBC), Milan, Italy, 25–29 August 2015. [Google Scholar]
- Iqbal, Z.; Luo, D.; Henry, P.; Kazemifar, S.; Rozario, T.; Yan, Y.; Westover, K.; Lu, W.; Nguyen, D.; Long, T.; et al. Accurate real time localization tracking in a clinical environment using Bluetooth Low Energy and deep learning. PLoS ONE 2018, 13, e0205392. [Google Scholar] [CrossRef] [PubMed]
- Giuliano, R.; Cardarilli, G.C.; Cesarini, C.; Di Nunzio, L.; Fallucchi, F.; Fazzolari, R.; Mazzenga, F.; Re, M.; Vizzarri, A. Indoor localization system based on bluetooth low energy for museum applications. Electronics 2020, 9, 1055. [Google Scholar] [CrossRef]
- Shen, H.; Bai, G.; Yang, M.; Wang, Z. Protecting trajectory privacy: A user-centric analysis. J. Netw. Comput. Appl. 2017, 82, 128–139. [Google Scholar] [CrossRef]
- Michael, K.; McNamee, A.; Michael, M.G. The emerging ethics of humancentric GPS tracking and monitoring. In Proceedings of the IEEE International Conference on Mobile Business, Copenhagen, Denmark, 25–27 July 2006; p. 34. [Google Scholar] [CrossRef]
- Álvarez-Díaz, N.; Caballero-Gil, P.; Reboso-Morales, H.; Martín-Fernández, F. Optimizing Resource Allocation and Indoor Location Using Bluetooth Low Energy. World Academy of Science, Engineering and Technology, Open Science Index 110. Int. J. Comput. Inf. Eng. 2016, 10, 333–336. [Google Scholar]
- Scheerens, D. Practical indoor localization using Bluetooth. Master’s Thesis, University of Twente, Enschede, The Netherlands, 2012. [Google Scholar]
- Parameswaran, A.T.; Husain, M.I.; Upadhyaya, S. Is rssi a reliable parameter in sensor localization algorithms: An experimental study. In Proceedings of the Field Failure Data Analysis Workshop, New York, NY, USA, January 2009; Volume 5. [Google Scholar]
- Bourke, P. Calculating the Area and Centroid of a Polygon. 1997. Available online: http://paulbourke.net/geometry/polygonmesh/ (accessed on 12 January 2021).
- Goldwasser, S.; Micali, S.; Rackoff, C. The knowledge complexity of interactive proof systems. In Proceedings of the Seventeenth Annual ACM Symposium on Theory of Computing, Providence, RI, USA, 6–8 May 1985; pp. 291–304. [Google Scholar]
- Blum, M.; Feldman, P.; Micali, S. Non-interactive zero-knowledge and its applications. In Proceedings of the 20th annual ACM Symposium on Theory of Computing, Chicago, IL, USA, 2–4 May 1988; pp. 103–112. [Google Scholar]
- Peng, K.; Bao, F. An Efficient Range Proof Scheme. In Proceedings of the 2010 IEEE Second International Conference on Social Computing, Minneapolis, MN, USA, 20–22 August 2010; pp. 826–833. [Google Scholar] [CrossRef]
- Koens, T.; Ramaekers, C.; Van Wijk, C. Efficient Zero-Knowledge Range Proofs in Ethereum; Technical Report; ING: Amsterdam, The Netherlands, 2018. [Google Scholar]
- Morais, E.; van Wijk, C.; Koens, T. Zero Knowledge Set Membership; Technical Report; ING Bank: Amsterdam, The Netherlands, 2018. [Google Scholar]

| Employees | |||
|---|---|---|---|
| Number of assigned activities () | 3 | 2 | 3 |
| Time spent in completed activities () | 5 h | 4.5 h | 4 h |
| Is in range () | 1 | 0 | 0 |
| Is in range () | 0 | 1 | 0 |
| Is in range () | 0 | 0 | 0 |
| Score |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Álvarez-Díaz, N.; Caballero-Gil, P. Decision Support System Based on Indoor Location for Personnel Management. Remote Sens. 2021, 13, 248. https://doi.org/10.3390/rs13020248
Álvarez-Díaz N, Caballero-Gil P. Decision Support System Based on Indoor Location for Personnel Management. Remote Sensing. 2021; 13(2):248. https://doi.org/10.3390/rs13020248
Chicago/Turabian StyleÁlvarez-Díaz, Néstor, and Pino Caballero-Gil. 2021. "Decision Support System Based on Indoor Location for Personnel Management" Remote Sensing 13, no. 2: 248. https://doi.org/10.3390/rs13020248
APA StyleÁlvarez-Díaz, N., & Caballero-Gil, P. (2021). Decision Support System Based on Indoor Location for Personnel Management. Remote Sensing, 13(2), 248. https://doi.org/10.3390/rs13020248







