1. Introduction
The Internet of Things (IoT) tries to connect with all objects based on the communication network and provide people with the intellectual technologies and services that communicate between person and object, or object and object. For this purpose, IoT devices process various kinds of information at different service fields. At this time, the IoT environment is analyzed from various perspectives such as environment, economy, and infrastructure, among others, and the device is deployed depending on the analysis results. The deployed devices can sense and process simple ambient information such as temperature or humidity, or they can process personal information such as the position of an individual. In the case of handling simple ambient information, priority may be placed on service sustainability rather than security for energy efficiency. However, even when only simple ambient information is processed, it is hard for services such as smart energy or smart vehicles to place priority solely on energy efficiency, as they are closely related to the public and individual’s security.
Therefore, IoT devices shall provide people with a service environment in which both sustainability and security shall be achieved. Especially, the sensor that collects information at the front line shall be ensured of sustainability and security. This is because sustainability and security at the sensor ultimately leads to the service provided to the users. The characteristics of IoT service are as follows.
The IoT environment provides users context rich services based on user experience. At this time, user experience is based on the information collected from various objects that are available around users. Moreover, the most fundamental object among these diverse objects providing information is a sensor [
1,
2].
The quality of service to be provided to users through IoT shall be determined based on the quality of information to be collected and analyzed. That is to say, the quality of service to be provided through IoT shall be determined when it is possible to collect information from an authenticated sensor securely through a sensor network [
3,
4].
A sensor network infrastructure consists of the sensor nodes that synchronize or transmit the information detected through sensing to a server via other wireless network devices. Because of the characteristics of wireless communication, sensor nodes have been vulnerable to attacks such as relay attack, replay attack, and eavesdropping. The vulnerable authentication and management of the key may lead to infection by malicious codes such as Stuxnet, or an attack by malicious firmware updates, which in turn could develop into IoT device-based distributed denial-of-service (DDoS) by the second attack. Eavesdropping may expose the privacy of an individual who uses the IoT device to others, and an attack of retransmission may cause damages such as unfair penalty.
Thus, security protocols and schemes have been adapted. Even the sensor node supporting the encryption such as RC5 and public key was developed [
5,
6,
7].
However, those sensor nodes whose hardware computing power and energy resources are very limited compared to the other sensor nodes are not suitable for the use of encryption and secure communication requiring a high degree of computing power, which are used in the existing schemes and protocols. In addition, the studies to prevent relay attack have tried to detect transmission device location on wireless network topology using radio frequency signal analysis. On that account, it is not appropriate to utilize it in a sensor with mobility or a sensor whose energy is relatively limited compared to the other sensors [
8,
9,
10].
The quality of intelligent services in the IoT environment can be enhanced when the information is collected mainly from users on a continuous basis. That is to say, it is imperative to collect and transmit data continuously from a sensor [
1,
2]. The reason why sustainability is important is because an individual’s life and the company’s business are more closely dependent on IoT. After the development of the smart phone, many and various lives and businesses were re-conducted through the smart phone. As such, once an IoT environment is completely constructed, lives and business would continue based on IoT. It means that in this case, if there were even one disconnection in the continuity of information, there would be grave damage. In the smart factory environment, if even one piece of information does not arrive on time, the manufacturing process may be stopped or destroyed. In the smart automobile environment, if the sensor fails to collect the information even once, it could cause a traffic accident. Therefore, it is not optional but mandatory for IoT to provide sustainability.
The most adequate sensor network routing protocol for the continuous collection and transmission of data is the LEACH routing protocol [
11]. The LEACH protocol has a better efficiency of data transmission energy since it allocates cluster headers and sensor groups dynamically based on energy efficiency analysis. However, it is not adequate to utilize the LEACH protocol for the application of the existing group management technique because it allocates groups dynamically.
Therefore, in this paper, the goal is to develop the secure authentication protocol which has high energy efficiency and whose service is sustainable in the IoT environment. For this purpose, this paper designs and proposes a group sensor secure communication protocol that solves the security vulnerabilities to which the existing sensor nodes are threatened, by utilizing the four kinds of fundamental arithmetic operations such as ADD operator and logical operations such as AND operator. The proposed secure communication protocols are also secure to a relay attack by using the distance-bounding technique between sensor nodes during the proposed authentication process. Also, this paper proposes the scheme to authenticate simultaneously all the sensor nodes in the ever-changing sensor group and to allocate group keys dynamically.
3. Secure Dynamic Group Management Scheme
This section proposes a secure communication scheme that can conduct simultaneously mutual authentication between group sensor nodes and validate the distance between group sensor nodes by using the four kinds of fundamental arithmetic operations, substitution, logical operation, and challenge-response technique. The proposed scheme is made with four protocols that contain cluster header authentication and group authentication. During the authentication, the seed value which is required for generating and confirming the key is securely transmitted with the use of the multiplication, addition, and logistic XOR or || only.
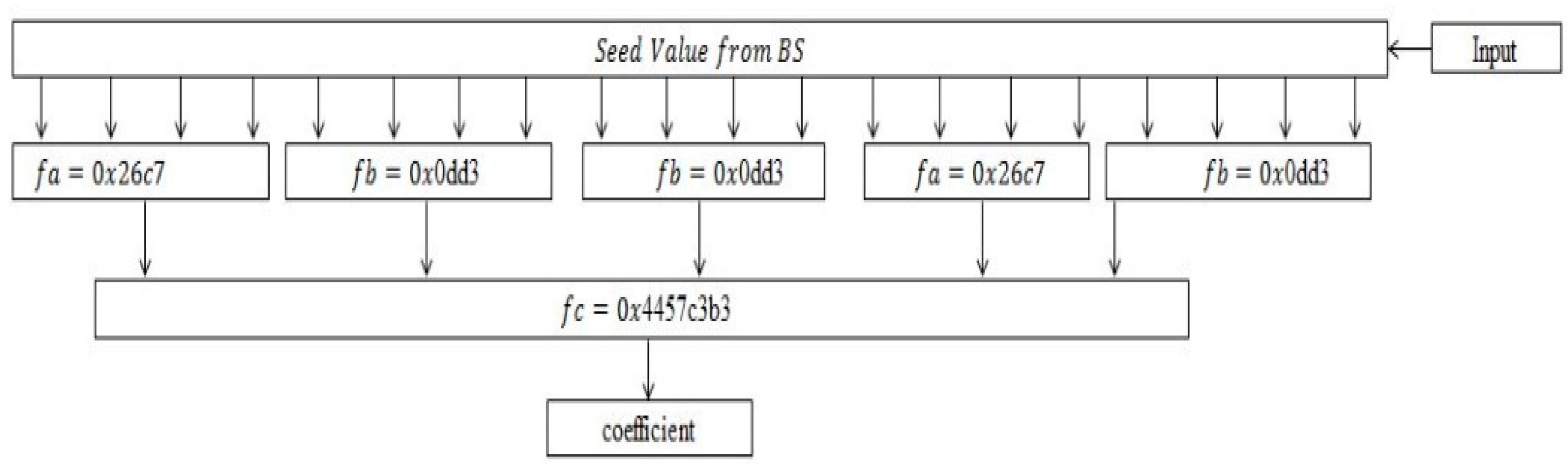
Figure 1 is a conceptual diagram of the secure dynamic group management scheme. Once the cluster header is selected, it will obtain a certain value for the group authentication from BS, and the sensor group will conduct the group authentication using that value. It is assumed that base station and secret key were shared when distributing sensor nodes. Also, it is assumed that the filter function was shared for the reduction of bit stream as shown in
Figure 2. The process of filter function action is as follows. If a series of bit streams is put in the function, the values of bits located in the specified position would be selected for first filtering. Then, the values of bits, which are located in the specification positions, are kept among those that are filtered in unit of block while others would be removed. Lastly, only one bit is selected which is located as a specified position. The filter function continues to act until it gets the bit steam of the specified size while the dual values are designed not to come out by changing the input values or the position of filtering. For example, assuming that the seed is x in the size of 48 bits, x undergoes the FA and FC filtering functions in the first layer and is then divided into 5-bit values. In addition, one output value is obtained through the FC filtering function in the second layer. In addition, if there is more than 1-bit value, the filtering shall be repeated from first layer to only 1-bit value is left. The used symbols are explained in
Table 1.
3.1. Cluster Header Authentication and Encryption Key’s Elements Transmission
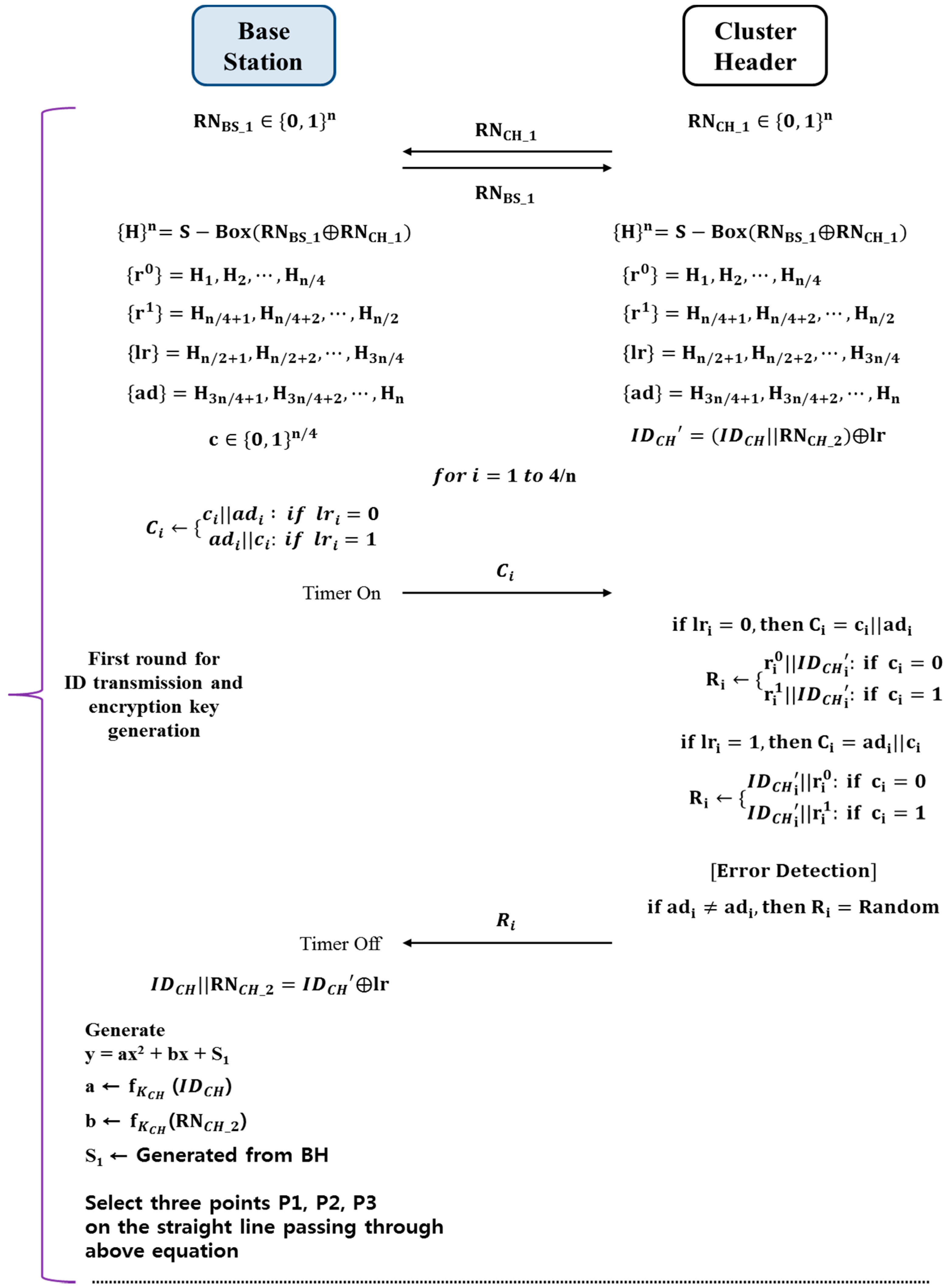
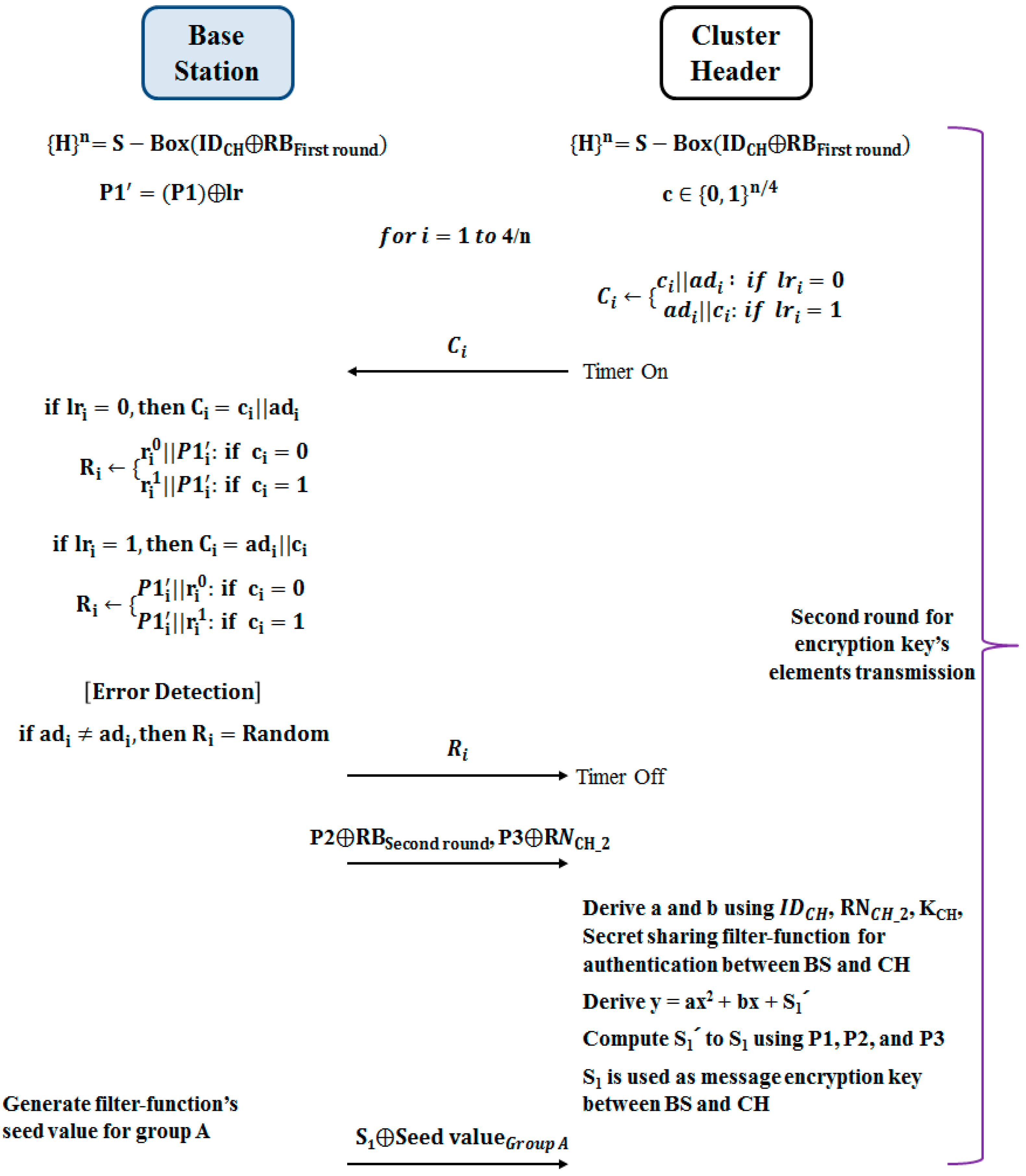
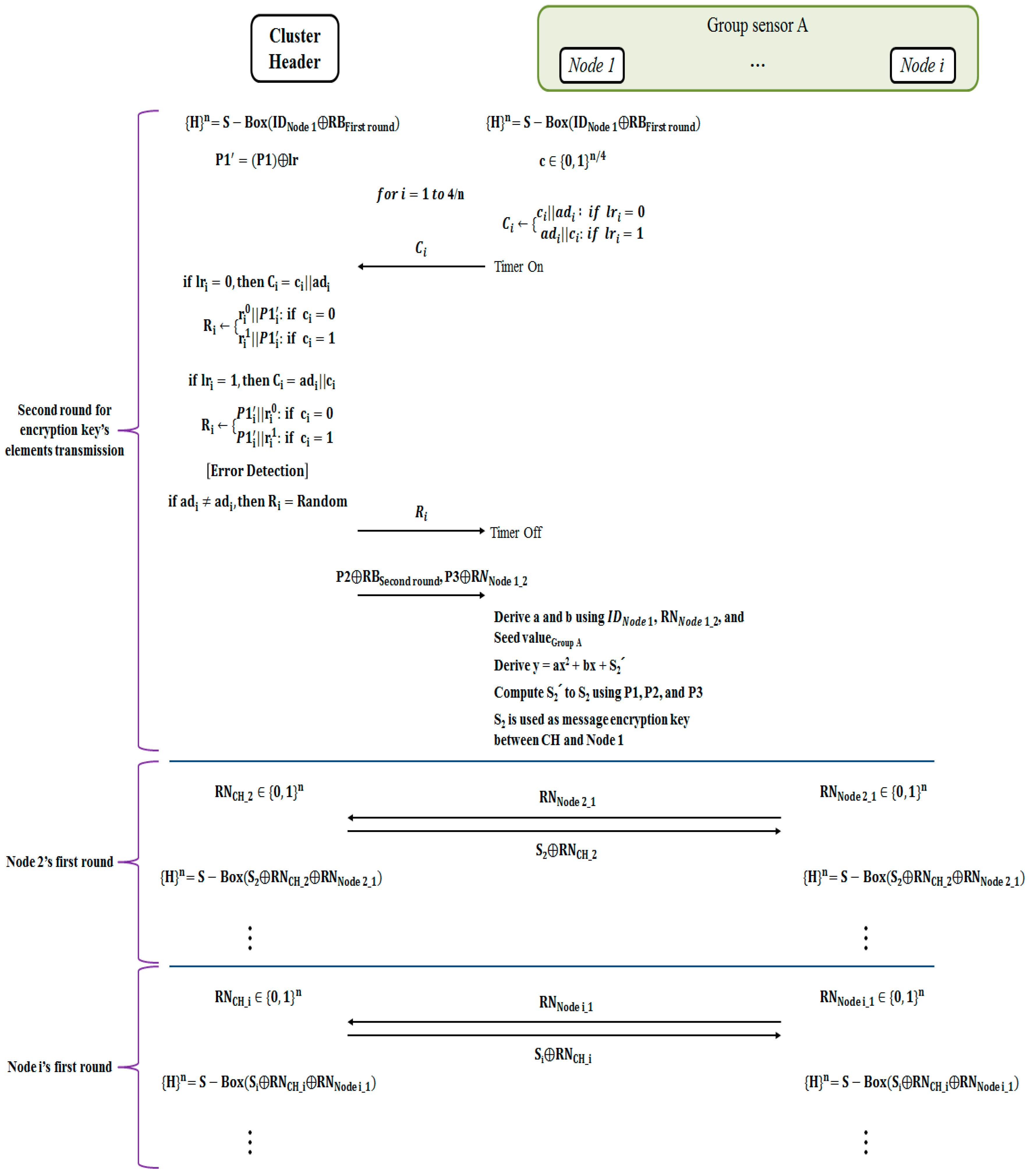
Figure 3 and
Figure 4 show the process of transmitting the filter function seed values, which the elected cluster headers (hereinafter referred to as CH) and the base station (hereinafter referred to as BS) will use for authentication and information transmission in mutual authentication and sensor group. The process thereof consists of the two rounds. The first round carries out the mutual authentication between BS and CH and the process of generating secret key. The second round is the process of transmitting filter function seed value for generating secret key and group sensor node secret key.
BS and CH exchange RNCH_1 and RNBS_1 and generate 4n bits stream {0, 1}n by utilizing the expansion substitution-box operator. The generated bits stream is separated into n bits stream, while the CH generates the second random number. The second random number and ID of CH are transmitted to BS using the challenge/response process. BS measures the time of the challenge/response process and verifies the distance between BS and CH.
The n bits stream is conducted r0, r1, ad, and lr. Afterwards, IDCH’ is derivate. BS generates different n bits stream, called ‘c’. ‘c’ and ad are used to derivate challenge bits ‘C’. When ‘C’ is derivate, lr is used as reference point. If lri is zero, ‘C’ is conducted ci‖adi. Otherwise, if lri is one, ‘C’ is conducted adi‖adi.
After an initial process of challenge/response is run, BS sends challenge bits ‘C’ to CH. With that process started, BS also measures a time while the challenge/response process and verifies the distance between BS and CH against of relay attack.
For response, CH validates ‘C’ and operates ‘R’. CH also could generate 4n bits stream and derivate ‘C’. While BS derivates ‘C’, CH also derivates ‘C’. And while BS sends ‘C’, CH derivates ‘R’. ‘R’ is conducted r0, r1, and IDCH’. When ‘R’ is derivate, there are two rules. The first rule is about a position of IDCH’. If lri is zero, IDCH’ is positioned behind of r0 or r1. Otherwise, if lri is one, IDCH’ is positioned in front of r0 or r1. The second rule is about a value used. If ci is zero, ri0 is used. Otherwise, if ci is one, ri1 is used. Based on the two rules, ‘R’ is derivate and transmitted to BS.
After CH’s ID is transmitted, the process of generating a session key between BS and CH will begin. BS generates a second order polynomial with S (to be used as a session key) in the constant term. The coefficients of this polynomial will be derived by using ID of CH, which was transmitted in the challenge/response process, and the second random number. BS is the seed value of the filter function that was shared in advance. The resulting value of substituting ID and the random number in the filter function after substituting the secret key of CH is used as a coefficient of the polynomial. Lastly, BS selects the points (P1, P2 and P3) crossing the polynomial graph. In this process, only multiplication and addition is used to create P1, P2 and P3.
For the second round, BS and CH shall create a series of bit streams again. The ID and the result value obtained from the calculation of the remainder bit that is not used during the challenge/response in the first round becomes the bit stream of 4n bits, and the bit stream is separated into n bits. In the second challenge/response process, the response time is verified in CH and, through the challenge/response process, the point P1 in the polynomial is transmitted. Once the challenge/response process is finished, the remainder bit not used in the second challenge/response process and the random number, as well as P2 and P3, are XOR calculated and transmitted. Once the transmission of all seed values is finished, CH obtains the polynomial for the recovery of secret value S. As in the calculation at BS, CH uses the ID, random number, secret key and filter function to create the polynomial. Afterwards, the received P1, P2 and P3 are put into the polynomial to get the secret value S.
The procedure of obtaining the secret value S is as follows. The coefficients in the polynomial of the cluster header are known but not the constants. The polynomial is a second-degree polynomial. So, if the three coordinates passing by are known, one can find out the constants. For this, P1, P2 and P3 are put into the cluster header to get the S, which can jointly meet the requirements.
Lastly, BS transmits CH the filter function seed value to be used in the group sensor nodes belonging to CH.
3.2. Group Sensor Authentication and Secure Sensor Information Transmission
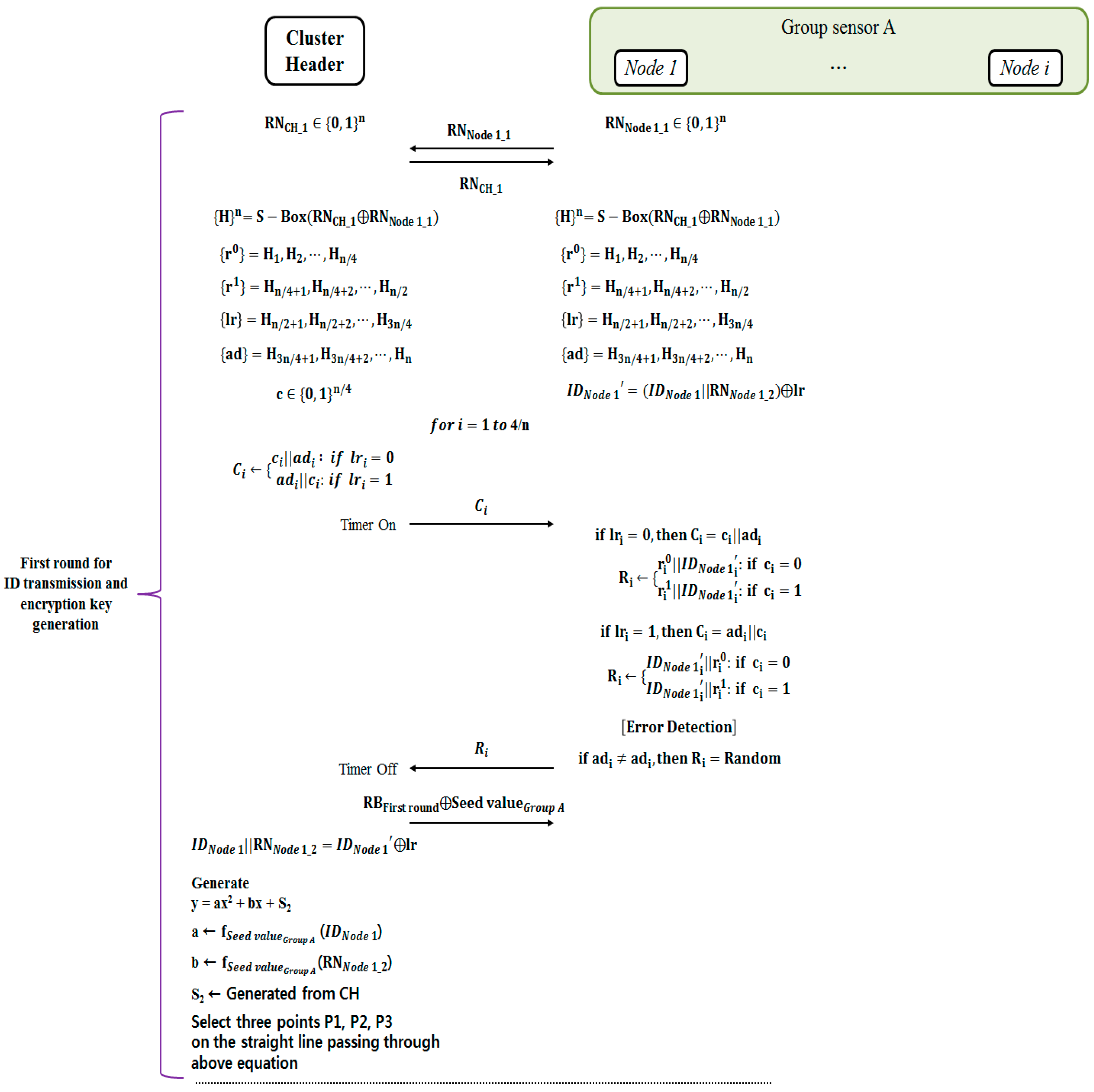
Figure 5 and
Figure 6 show the process in which an elected cluster header conducts mutual authentication for all the sensor nodes simultaneously belonging to a group, and also derives a session key value to be used for transmitting sensor information. A process for each sensor node consists of the two rounds.
The first round consists of the mutual authentication between CH and sensor node, the transmission of filter function seed value and the process of generating a session key. The second round is the polynomial transmission process to generate a session key to be used in a group sensor node.
CH and sensor node exchange RNCH_1 and RNNode_1_i and generate 4n bits stream {0, 1}n by utilizing the expansion substitution box operator. The generated bits stream is separated into n bits stream, while the sensor node generates the second random number. The second random number and ID of sensor node are transmitted to CH using the challenge/response process. CH measures a time while the challenge/response process and verifies the distance between CH and sensor node.
The n bits stream is conducted r0, r1, ad, and lr. Afterwards, IDNode_1’ is derivate. CH generates different n bits stream. And it’s called ‘c’. ‘c’ and ad are used to derivate challenge bits ‘C’. When ‘C’ is derivate, lr is used as reference point. If lri is zero, ‘C’ is conducted ci‖adi. Else if lri is one, ‘C’ is conducted adi‖adi.
After initial process of challenge/response is run, CH sends challenge bits ‘C’ to sensor node. At that process started, CH also measures the time of the challenge/response process and verifies the distance between CH and sensor node against relay attack.
For the response, sensor node validates ‘C’ and operates ‘R’. Sensor node also could generate 4n bits stream and derivate ‘C’. While CH derivates ‘C’, sensor node also derivates ‘C’. And while CH sends ‘C’, sensor node derivates ‘R’. ‘R’ is conducted r0, r1, and IDNode_1’. When ‘R’ is derivate, there are two rules. The first rule is about a position of IDNode_1’. If lri is zero, IDNode_1’ is positioned behind of r0 or r1. Otherwise, if lri is one, IDNode_1’ is positioned in front of r0 or r1. The second rule is about a value used. If ci is zero, ri0 is used. Otherwise, if ci is one, ri1 is used. Based on the two rules, ‘R’ is derivate and transmitted to CH.
After sensor node’s ID is transmitted, the process of generating a session key between BS and CH will begin. At this time, CH executes an operation on the filter function seed value received from BS with the remainder bit occurred in the first challenge/response process and then transmits the result of this operation to a sensor node. After then, CH generates a second order polynomial with S (to be used as a session key) in the constant term. The coefficients of this polynomial are derived through the ID of a sensor node transmitted in the challenge/response process and the second random number. CH substitutes the seed value of the filter function transmitted to a sensor node. The result value of substituting ID and the random number in the filter function is utilized as a coefficient of the polynomial. Lastly, CH selects the points (P1, P2 and P3) crossing the polynomial graph.
For the second round, CH and a sensor node generate a series of bit streams again. The resulting value of calculating ID and the remainder bit stream not used as seed of transmitted value in the challenge/response process of the first round becomes a n bit stream. This bit stream is again sub-divided into a bit stream of each n bits. The second challenge/response process verifies the response time in a sensor node. The point P1 above the polynomial is transmitted via challenge/response process. After the challenge/response process is completed, P2 and P3 undergo an XOR operation with the remainder bit and random number not used in the second challenge/response process and then they are transmitted. After transmitting all the seed values, a sensor node derives a polynomial for restoring the secret value S. As shown in the operation process in CH, a sensor node generates a polynomial by using the ID, random number, secret key and filter function. After this, it derives the secret value S by substituting the received P1, P2 and P3 in the polynomial. The derived S will be utilized as the encryption key to transmit sensor information.
After the first sensor node authentication and key derivation process are completed, the second sensor node will be processed. At this time, the value used in the first sensor node is transmitted to the second sensor node as though it is a random number, in order to guarantee that all the authentication and key derivation processes are continuous.
5. Conclusions
This paper provides the measurements to manage the dynamically allocated cluster headers and group securely by utilizing the four kinds of fundamental arithmetic operator, substitution operator, and logical operator. The proposed scheme supports mutual authentication and confidential information transmission in the dynamically allocated cluster headers and groups through authenticating group sensor nodes simultaneously and allocating the keys. Moreover, it can verify the distance between the sensor nodes by utilizing the distance bounding. It is secure to the various vulnerabilities resulting from the nature of wireless sensor network environment.
The security provided by the proposed scheme not only provides logical security, but also physical security. The mutual authentication and e2e encryption communication offers confidentiality in communication in a logical way. If the proposed scheme is applied, actions can be taken against access by malicious users, infections by malicious codes, malicious updates of firmware and eavesdropping.
The dynamic group authentication and the distance-bounding technique contained in the proposed scheme also provide people with physical security. If even one sensor does not participate in authentication, the dynamic group authentication would fail. This kind of security leads to the sensor’s function, which detects theft or damage. The distance-bounding technique allows the sensor implementing the authentication to sense the geological existence, thereby providing similar physical security as in a dynamic group authentication.
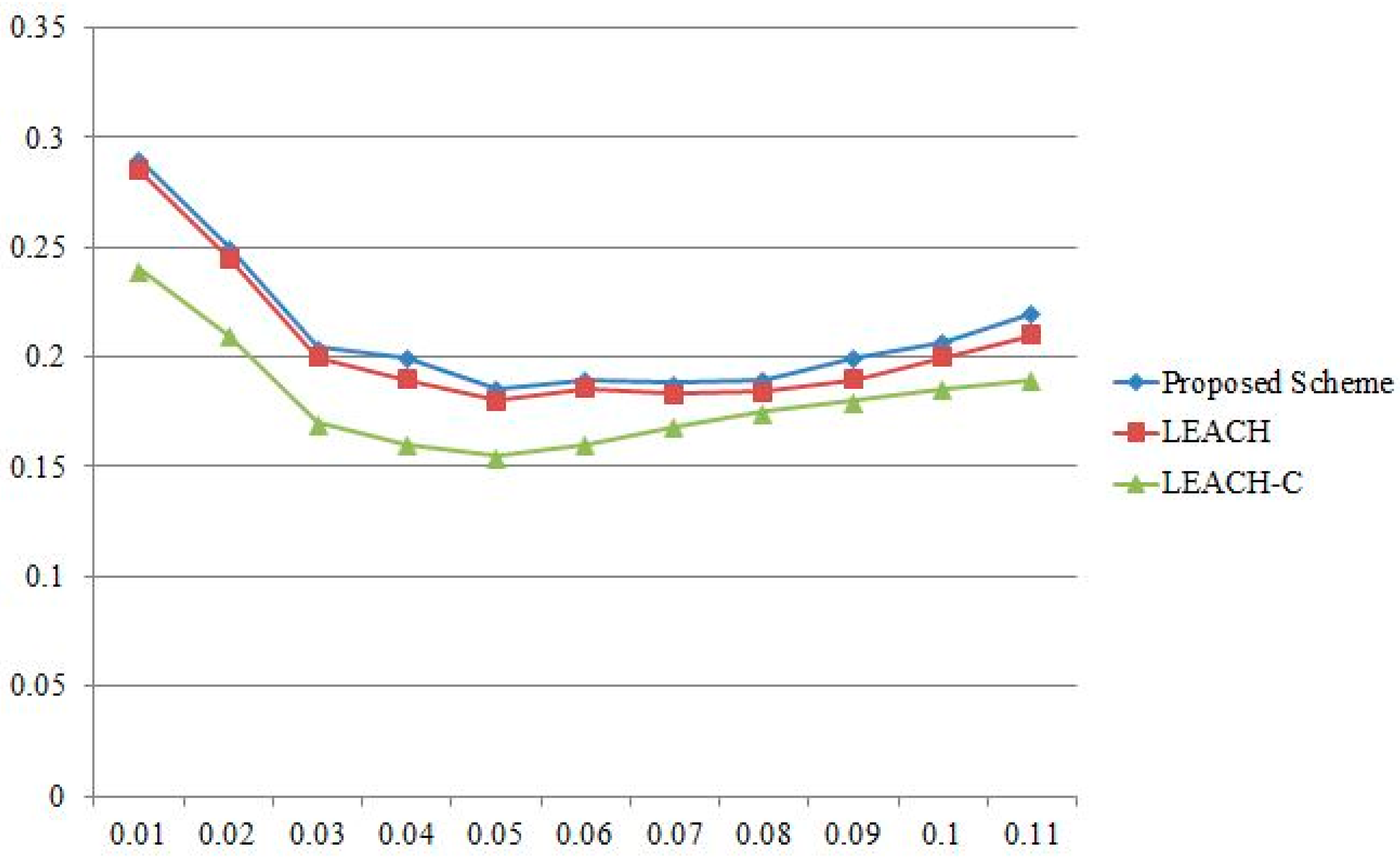
Also, it was confirmed that the proposed scheme had an insignificant difference in the energy consumption as compared with the existing routing protocols. The IoT environment will be the mesh network environment and the transfer of various kinds of information would happen on a sporadic basis. In addition, the cluster header will continue to transfer the information to servers for the analysis of information based on the cloud computing environment. Therefore, this could ultimately lead to service sustainability since both the demand for calculation at the cluster header and energy consumption is reduced. However, the calculation cannot be reduced for the quality in service. What is necessary is not reduction in energy consumption, but the efficient use of energy. The best routing protocol in terms of efficient energy use is the LEACH protocol. It can be said that the proposed scheme is more efficient than the LEACH protocol, which is the most efficient in energy consumption.
From the abovementioned analysis results, it is believed that the proposed dynamic group management scheme can be utilized as a sustainable and secure sensor node management scheme for providing high-quality intelligent services in the IoT environment [
18].