Addressing the Sustainability Challenges: Digital Economy Information Security Risk Assessment
Abstract
1. Introduction
2. Literature Review
2.1. Information Security Issues in the Digital Economy and Sustainable Development
2.2. Information Security Risks in the Digital Economy
2.3. Information Security Risk Analysis
3. Theoretical Analysis and Research Methods
3.1. Theoretical Analysis
3.2. Research Methods
3.2.1. Min–Max Normalization
3.2.2. CRITIC–EMW–GT Weighting
- The entropy weight method’s primary concept is to measure the amount of information entropy in order to determine the degree of dispersion of indicators. The degree of dispersion of the indicators and the influence on the evaluation outcomes increase with decreasing information entropy [48].
- The risk rating value Ri of the ith research subject is
3.2.3. Ward’s Method
3.2.4. Obstacle Degree Model
4. Results and Discussion
4.1. CRITIC–EWM–GT Weight
4.2. Spatio–Temporal Pattern Evolution of Information Security Risks in the Digital Economy
4.2.1. Time Evolution Pattern Analysis
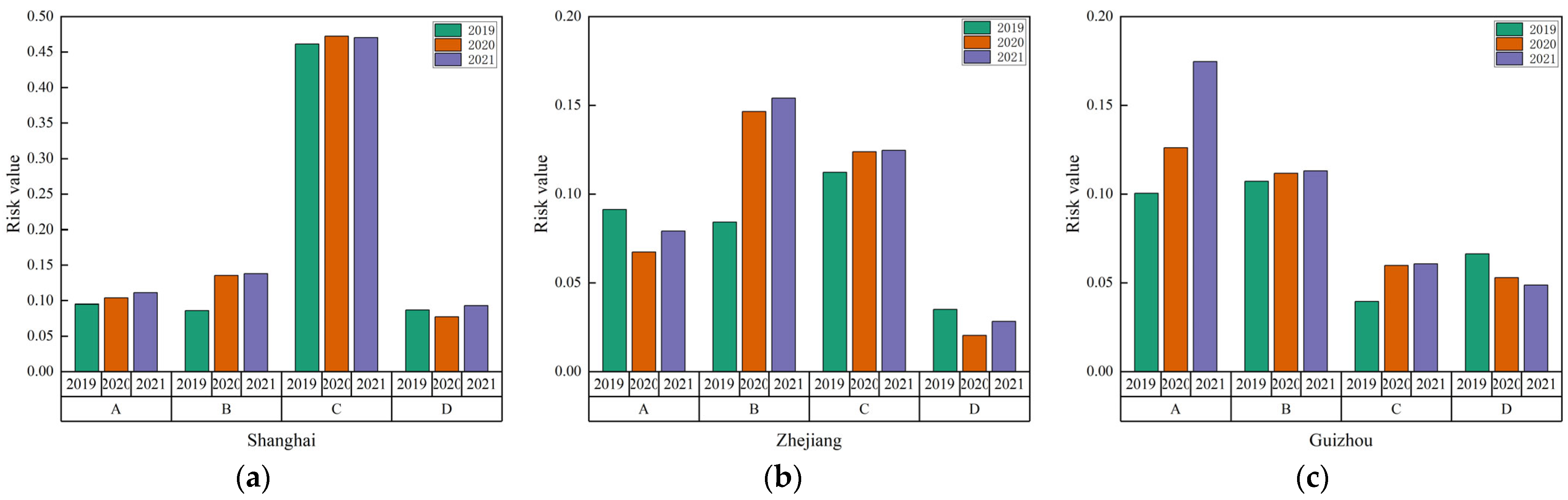
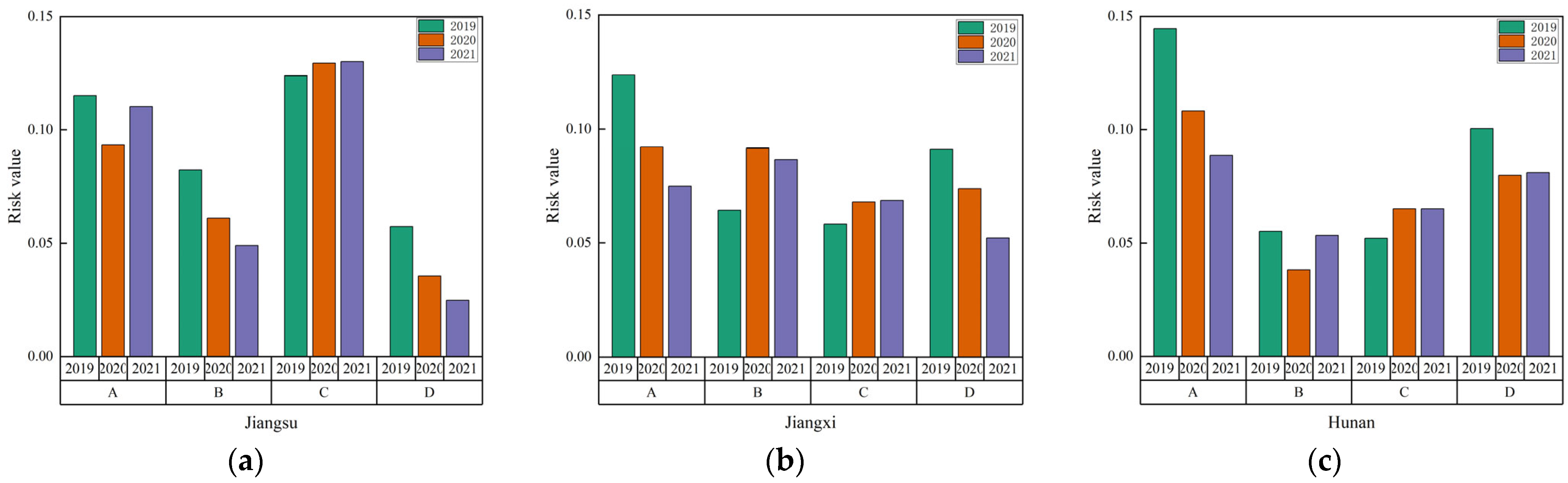
4.2.2. Spatial Evolution Pattern Analysis
4.3. Classification of Provinces
4.4. Barriers to Digital Economy Information Security Risks
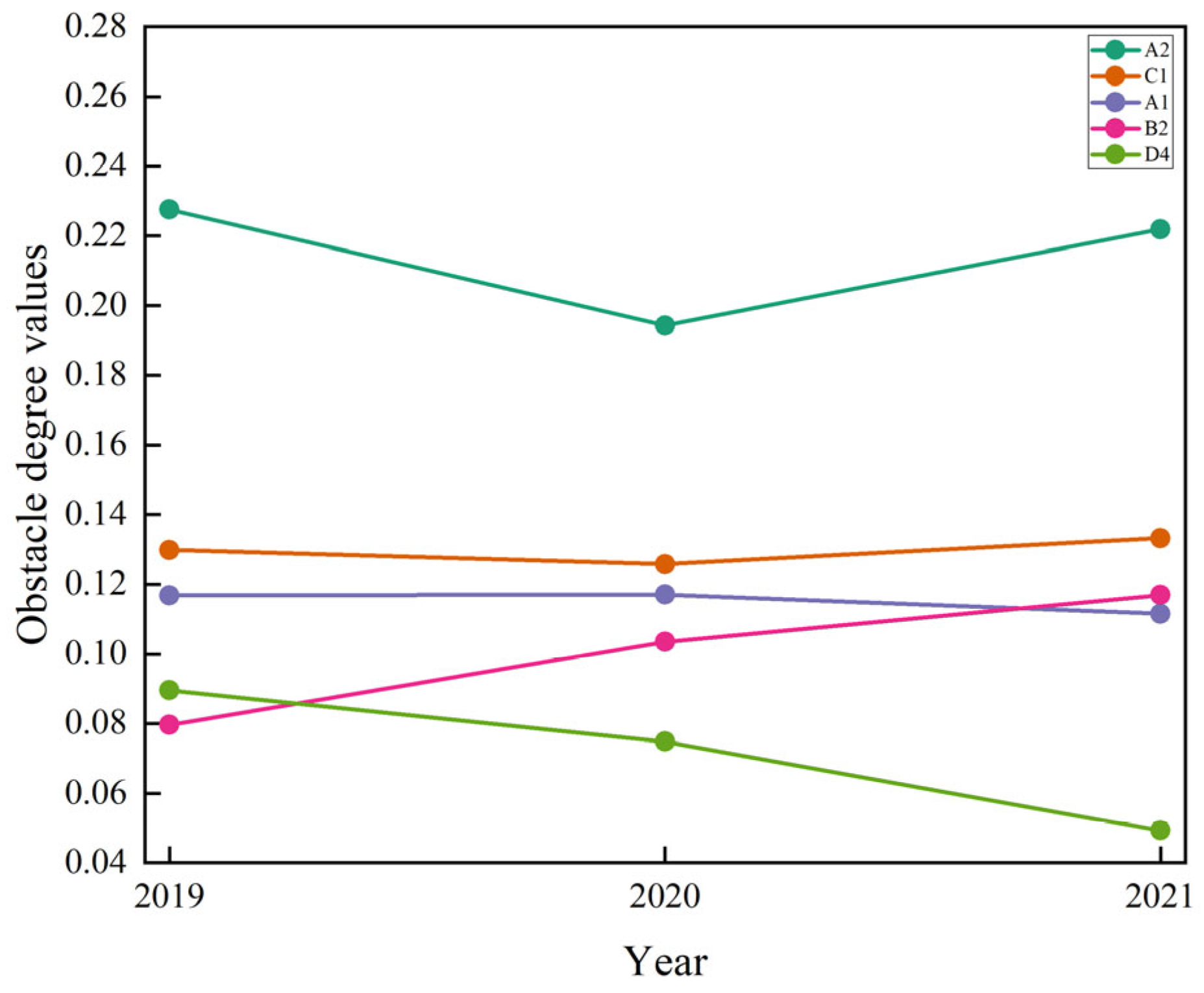
4.4.1. Overall Obstacle Factors
4.4.2. Obstacle Factors in Each Province
5. Conclusions and Policy Implications
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Ding, C.; Liu, C.; Zheng, C.; Li, F. Digital Economy, Technological Innovation and High-Quality Economic Development: Based on Spatial Effect and Mediation Effect. Sustainability 2022, 14, 216. [Google Scholar] [CrossRef]
- Xu, S.; Yang, C.Y.; Huang, Z.H.; Failler, P. Interaction between Digital Economy and Environmental Pollution: New Evidence from a Spatial Perspective. Int. J. Environ. Res. Public Health 2022, 19, 5074. [Google Scholar] [CrossRef] [PubMed]
- Ren, B.-p.; Zhang, C.-x. Security risk early warning and prevention mechanism construction of Digital economy development in China. J. Guizhou Univ. Financ. Econ. 2022, 1–13. [Google Scholar] [CrossRef]
- ISO/IEC 27002:2022; Information Security, Cybersecurity and Privacy Protection—Information Security Controls. International Organization for Standardization/International Electrotechnical Commission: Geneva, Switzerland, 2022.
- Facebook’s Worst Outage Ever: Is It Time for Internet Companies to Rethink Their Architecture? Available online: https://mp.weixin.qq.com/s/qkUVPMHCE01JB2GB5_v2mQ (accessed on 21 April 2025).
- Abdiraman, A.; Goranin, N.; Balevicius, S.; Nurusheva, A.; Tumasoniene, I. Application of Multicriteria Methods for Improvement of Information Security Metrics. Sustainability 2023, 15, 8114. [Google Scholar] [CrossRef]
- Castro, G.D.R.; Fernandez, M.C.G.; Colsa, A.U. Unleashing the convergence amid digitalization and sustainability towards pursuing the Sustainable Development Goals (SDGs): A holistic review. J. Clean. Prod. 2021, 280, 122204. [Google Scholar] [CrossRef]
- Premaratna, S.; Padmasiri, H.; Rathnayaka, I.; Indeewari, G.; Arachchi, P.K. A Review of Literature on Sustainable Cities and Urban Ageing: Challenges and Opportunities for Developing Countries. Sri Lanka J. Soc. Sci. Humanit. 2023, 3, 63–70. [Google Scholar] [CrossRef]
- Transforming Our World: The 2030 Agenda for Sustainable Development. Available online: https://sdgs.un.org/2030agenda (accessed on 8 May 2025).
- Rosario, A.T.; Dias, J.C. The New Digital Economy and Sustainability: Challenges and Opportunities. Sustainability 2023, 15, 10902. [Google Scholar] [CrossRef]
- Duggineni, S. Data integrity and risk. Open J. Optim. 2023, 12, 25–33. [Google Scholar] [CrossRef]
- Leroy, I.; Zolotaryova, I.; Semenov, S. Impact of Critical Infrastructure Cyber Security on the Sustainable Development of Smart Cities: Insights from Internal Specialists and External Information Security Auditors. Sustainability 2025, 17, 1188. [Google Scholar] [CrossRef]
- ISO/IEC 27005:2022; Information Security, Cybersecurityand Privacy Protection—Guidance Onmanaging Information Security Risks. International Organization for Standardization/International Electrotechnical Commission: Geneva, Switzerland, 2022.
- Sadowski, J. When data is capital: Datafication, accumulation, and extraction. Big Data Soc. 2019, 6, 2053951718820549. [Google Scholar] [CrossRef]
- Evgenevna, F.E.; Anatolevna, P.T.; Nikolaevich, D.M.; Petrovna, R.E.; Aleksandrovich, K.P. Information Security of Russia in the Digital Economy: The Economic and Legal Aspects. J. Adv. Res. Law Econ. 2018, 9, 89. [Google Scholar]
- Sopilnyk, L.; Skrynkovskyy, R.; Kovaliv, M.; Zayats, R.; Malashko, O.; Yesimov, S.; Mykytiuk, M. Development of Digital Economy in the Context of Information Security in Ukraine. Path Sci. 2020, 6, 2023–2032. [Google Scholar] [CrossRef]
- Aliyev, A.G.; Shahverdiyeva, R.O. Scientific and methodological bases of complex assessment of threats and damage to information systems of the digital economy. Int. J. Inf. Eng. Electron. Bus. 2022, 15, 23. [Google Scholar]
- Que, T.; Wang, Z. Global Data Security Governance and Action Strategies for China’s Participation in the Era of Digital Economy. J. Int. Secur. Stud. 2022, 40, 130–154+158. [Google Scholar] [CrossRef]
- Sun, Y.; Zhuang, L.; Jia, T.; Cheng, D.; Zhao, X.; Guo, J. A risk assessment method for power internet of things information security based on multi-objective hierarchical optimisation. IET Smart Grid 2025, 8, e12208. [Google Scholar] [CrossRef]
- Yang, L.; Zou, K.; Gao, K.; Jiang, Z. A fuzzy DRBFNN-based information security risk assessment method in improving the efficiency of urban development. Math. Biosci. Eng. 2023, 19, 14232–14250. [Google Scholar] [CrossRef]
- Xu, W.; Lin, M. Information Security Evaluation of Industrial Control Systems Using Probabilistic Linguistic MCDM Method. CMC Comput. Mater. Contin. 2023, 77, 199–222. [Google Scholar] [CrossRef]
- Wang, D.; Lu, Y.; Gan, J. An information security evaluation method based on entropy theory and improved TOPSIS. In Proceedings of the 2017 IEEE Second International Conference on Data Science in Cyberspace (DSC), Shenzhen, China, 26–29 June 2017; IEEE: New York, NY, USA; pp. 595–600. [Google Scholar]
- Guo, Z.Y.; Qi, J.H.; Zuo, J.X.; Xie, W.X.; Lu, Y.M.; Tian, H.P.; Cao, R.H. A Security Evaluation Model for Edge Information Systems Based on Index Screening. IEEE Internet Things J. 2024, 11, 21585–21603. [Google Scholar] [CrossRef]
- Yang, Y.; Yuan, Q. Information Ecology and Its Application and Prospect in the Field of Information System Research. J. Mod. Inf. 2022, 42, 140–148. [Google Scholar]
- Pekkarinen, S.; Hasu, M.; Melkas, H.; Saari, E. Information ecology in digitalising welfare services: A multi-level analysis. Inf. Technol. People 2021, 34, 1697–1720. [Google Scholar] [CrossRef]
- Nardi, B.A.; O’Day, V. Information Ecologies: Using Technology with Heart; Mit Press: Cambridge, MA, USA, 1999. [Google Scholar]
- Wei, C.; Cai, Y.; Liu, J.; Guo, Y.; Wu, X.; He, X.; Hu, D. Factors influencing user’s health information discernment abilities in online health communities: Based on SEM and fsQCA. Front. Public Health 2024, 12, 1379094. [Google Scholar] [CrossRef] [PubMed]
- Yuan, X.; Wang, C. Research on the formation mechanism of information cocoon and individual differences among researchers based on information ecology theory. Front. Psychol. 2022, 13, 1055798. [Google Scholar] [CrossRef] [PubMed]
- Hughes-Lartey, K.; Li, M.; Botchey, F.E.; Qin, Z. Human factor, a critical weak point in the information security of an organization’s Internet of things. Heliyon 2021, 7, e06522. [Google Scholar] [CrossRef] [PubMed]
- Dolgieva, M.M. Digital crime object. Tomsk State Univ. J. 2022, 253–260. [Google Scholar] [CrossRef]
- Caramancion, K.M.; Li, Y.Q.; Dubois, E.; Jung, E.S. The Missing Case of Disinformation from the Cybersecurity Risk Continuum: A Comparative Assessment of Disinformation with Other Cyber Threats. Data 2022, 7, 49. [Google Scholar] [CrossRef]
- Yang, P.; Xiong, N.X.; Ren, J.L. Data Security and Privacy Protection for Cloud Storage: A Survey. IEEE Access 2020, 8, 131723–131740. [Google Scholar] [CrossRef]
- Zhu, L.; Ma, Z.; Huang, H.; Yan, M. Research on cybersecurity risk prevention and control of new infrastructure. In Proceedings of the 2021 International Conference on Computer Network Security and Software Engineering (CNSSE 2021), Zhuhai, China, 26–28 February 2021; p. 012034. [Google Scholar]
- Meleshko, Y.V. Business models digitalization of enterprises belarusian industrial complex: Directions, risks and tools. Econ. Sci. Today 2021, 61–74. Available online: https://cyberleninka.ru/article/n/tsifrovizatsiya-biznes-modeley-predpriyatiy-belorusskogo-promyshlennogo-kompleksa-napravleniya-riski-i-instrumenty (accessed on 8 May 2025). [CrossRef]
- Salayma, M. Risk and threat mitigation techniques in internet of things (IoT) environments: A survey. Front. Internet Things 2024, 2, 1306018. [Google Scholar] [CrossRef]
- Fu, M.; Tantithamthavorn, C.; Le, T.; Kume, Y.; Nguyen, V.; Phung, D.; Grundy, J. AIBugHunter: A Practical tool for predicting, classifying and repairing software vulnerabilities. Empir. Softw. Eng. 2024, 29, 4. [Google Scholar] [CrossRef]
- Naicker, V.; Mafaiti, M. The establishment of collaboration in managing information security through multisourcing. Comput. Secur. 2019, 80, 224–237. [Google Scholar] [CrossRef]
- Chen, B.; Liu, Y. Promotion and Advancement of Data Security Governance in China. Electronics 2024, 13, 1905. [Google Scholar] [CrossRef]
- He, X. Digital Economy, Business Environment and Foreign Trade Competitiveness. Front. Humanit. Soc. Sci. 2024, 4, 85–98. [Google Scholar] [CrossRef]
- Cheung, A.S.; Chen, Y. From datafication to data state: Making sense of China’s social credit system and its implications. Law Soc. Inq. 2022, 47, 1137–1171. [Google Scholar] [CrossRef]
- Bu, L.; Zhang, J. Quantitative Evaluation of Digital Economy Policy Based on PMC Index Model. Stat. Decis. 2023, 39, 22–27. [Google Scholar] [CrossRef]
- Tian, Z.; Jiang, C.C.; Yue, G.Y. Analysis of Digital Security Governance under the Objectives of Digital Ecology: A Three-Party Evolutionary Game Approach. Complexity 2024, 2024, 8849477. [Google Scholar] [CrossRef]
- Albayrak, E.; Bağcı, H. Modelling the effects of personal factors on information security awareness. J. Inf. Sci. 2025, 51, 20–30. [Google Scholar] [CrossRef]
- Jie, C.; Yanjie, S.; Liang-hai, L. A Study on the Pathways for Improving the Efficiency of China’s Digital Economy Based on the fsQCA Method. Mod. Manag. Sci. 2024, 161–170. [Google Scholar]
- Zeng, G.H.; Wu, M.M.; Yuan, X.X. Digital economy and industrial agglomeration. Econ. Anal. Policy 2024, 84, 475–498. [Google Scholar] [CrossRef]
- Fang, X.B.; Liu, M.T. How does the digital transformation drive digital technology innovation of enterprises? Evidence from enterprise’s digital patents. Technol. Forecast. Soc. Change 2024, 204, 123428. [Google Scholar] [CrossRef]
- Gulishengmu, A.; Yang, G.; Tian, L.J.; Pan, Y.; Huang, Z.; Xu, X.G.; Gao, Y.L.; Li, Y. Analysis of Water Resource Carrying Capacity and Obstacle Factors Based on GRA-TOPSIS Evaluation Method in Manas River Basin. Water 2023, 15, 236. [Google Scholar] [CrossRef]
- Xu, D.Y.; Abbas, S.; Rafique, K.; Ali, N. The race to net-zero emissions: Can green technological innovation and environmental regulation be the potential pathway to net-zero emissions? Technol. Soc. 2023, 75, 102364. [Google Scholar] [CrossRef]
- Fu, L.; Lei, Y.L.; Zhu, L.; Lv, J.F. An evaluation and design method for Ming-style furniture integrating Kansei engineering with particle swarm optimization-support vector regression. Adv. Eng. Inform. 2024, 62, 102822. [Google Scholar] [CrossRef]
- Leng, Y.J.; Zhang, H. Comprehensive evaluation of renewable energy development level based on game theory and TOPSIS. Comput. Ind. Eng. 2023, 175, 108873. [Google Scholar] [CrossRef]
- Gheorghe, G.; Tudorache, P.; Rosca, I.M. The Contribution of Green Marketing in the Development of a Sustainable Destination through Advanced Clustering Methods. Sustainability 2023, 15, 13691. [Google Scholar] [CrossRef]
- Cui, X.L.; Shen, Z.; Li, Z.H.; Wu, J. Spatiotemporal evolutions and driving factors of green development performance of cities in the Yangtze River Economic Belt. Ecol. Inform. 2021, 66, 101476. [Google Scholar] [CrossRef]
- Bonai, F.; Zhonghua, S. Digital Risk Governance: Research Context, Theoretical Framework, and Future Outlook. J. Manag. World 2024, 40, 208–239. [Google Scholar]
- Tang, X. Measurement on the Chinese Digital Economic Development Level and Regional Heterogeneity. Jianghan Trib. 2025, 28–37. [Google Scholar] [CrossRef]
- Tang, L.; Lu, B.; Tian, T. Spatial Correlation Network and Regional Differences for the Development of Digital Economy in China. Entropy 2021, 23, 1575. [Google Scholar] [CrossRef]
- Amankwah-Amoah, J.; Khan, Z.; Wood, G.; Knight, G. COVID-19 and digitalization: The great acceleration. J. Bus. Res. 2021, 136, 602–611. [Google Scholar] [CrossRef]




| Primary Indicators | Secondary Indicators | Quantitative Indicators | Data Sources | Indicator Attributes |
|---|---|---|---|---|
| Information personnel A | Information security awareness A1 | Implementation rate of personal cybersecurity measures A11 | Survey report on Chinese netizens’ satisfaction with cybersecurity | Negative |
| The proportion of unsafe online behavior A12 | Positive | |||
| Digital crime A2 | Incidence rate of online fraud crimes A21 | Survey report on Chinese netizens’ satisfaction with cybersecurity | Positive | |
| Incidence of personal information infringement A22 | Positive | |||
| Information personnel A | Digital crime A2 | Network intrusion encounter rate A23 | Survey report on Chinese netizens’ satisfaction with cybersecurity | Positive |
| Network attack encounter rate A24 | Positive | |||
| Information B | False information B1 | Traffic fraud encounter rate B11 | Survey report on Chinese netizens’ satisfaction with cybersecurity | Positive |
| Data resource scale B2 | Data resource index B21 | China’s big data regional development level assessment white paper | Positive | |
| Information security services B3 | Information security revenue B31 | China statistical yearbook | Negative | |
| Information technology C | Information infrastructure C1 | The ratio of optical cable line length to provincial area C11 | China statistical yearbook | Positive |
| The ratio of mobile phone base stations to provincial area C12 | Positive | |||
| Ratio of internet access ports to provincial area C13 | Positive | |||
| Digital innovation capabilities C2 | Number of digital economy patent authorizations C21 | Chinese research data services platform | Negative | |
| Safety protection capabilities C3 | Digital security capabilities C31 | Report on the innovative development of China’s big data | Negative | |
| Information environment D | Social credit system D1 | Number of social credit system policies D11 | Peking University Law Library | Negative |
| Digital economy system D2 | Number of digital economy policies D21 | Peking University Law Library | Negative | |
| Level of digital rule of law D3 | Digital rule of law index D31 | Report on the innovative development of China’s big data | Negative | |
| Information security promotion level D4 | Fraud prevention awareness campaign implementation rate D41 | Survey report on Chinese netizens’ satisfaction with cybersecurity | Negative |
| Quantitative Indicators | CRITIC Weight | Entropy Weight | Combined Weight |
|---|---|---|---|
| A11 | 0.0634 | 0.0430 | 0.0462 |
| A12 | 0.0614 | 0.0358 | 0.0398 |
| A21 | 0.0575 | 0.0468 | 0.0485 |
| A22 | 0.0550 | 0.0263 | 0.0308 |
| A23 | 0.0552 | 0.0239 | 0.0288 |
| A24 | 0.0659 | 0.0325 | 0.0377 |
| B11 | 0.0611 | 0.0286 | 0.0336 |
| B21 | 0.0699 | 0.1221 | 0.1140 |
| B31 | 0.0480 | 0.0099 | 0.0159 |
| C11 | 0.0417 | 0.1762 | 0.1552 |
| C12 | 0.0396 | 0.1358 | 0.1208 |
| C13 | 0.0398 | 0.1890 | 0.1657 |
| C21 | 0.0470 | 0.0112 | 0.0168 |
| C31 | 0.0644 | 0.0186 | 0.0258 |
| D11 | 0.0501 | 0.0111 | 0.0172 |
| D21 | 0.0574 | 0.0130 | 0.0199 |
| D31 | 0.0544 | 0.0294 | 0.0333 |
| D41 | 0.0680 | 0.0469 | 0.0502 |
| Province | 2019 | Ranking | 2020 | Ranking | 2021 | Ranking |
|---|---|---|---|---|---|---|
| Beijing | 0.3950 | 3 | 0.4786 | 3 | 0.4351 | 2 |
| Tianjin | 0.3639 | 6 | 0.5153 | 2 | 0.4100 | 3 |
| Hebei | 0.2977 | 21 | 0.3020 | 16 | 0.3243 | 13 |
| Shanxi | 0.3062 | 19 | 0.2924 | 19 | 0.2723 | 25 |
| Inner Mongolia | 0.2925 | 22 | 0.2850 | 23 | 0.2384 | 28 |
| Liaoning | 0.3207 | 14 | 0.3035 | 15 | 0.3017 | 18 |
| Jilin | 0.2909 | 24 | 0.2904 | 22 | 0.2950 | 19 |
| Heilongjiang | 0.3177 | 15 | 0.2765 | 25 | 0.2873 | 23 |
| Shanghai | 0.7292 | 1 | 0.7888 | 1 | 0.8127 | 1 |
| Jiangsu | 0.3787 | 4 | 0.3191 | 12 | 0.3142 | 16 |
| Zhejiang | 0.3229 | 13 | 0.3581 | 5 | 0.3863 | 5 |
| Anhui | 0.3451 | 9 | 0.2920 | 20 | 0.3236 | 14 |
| Fujian | 0.3049 | 20 | 0.3065 | 14 | 0.3336 | 12 |
| Jiangxi | 0.3375 | 10 | 0.3256 | 10 | 0.2823 | 24 |
| Shandong | 0.3752 | 5 | 0.3768 | 4 | 0.3796 | 6 |
| Henan | 0.2917 | 23 | 0.2953 | 18 | 0.2944 | 21 |
| Hubei | 0.2756 | 26 | 0.3369 | 7 | 0.2947 | 20 |
| Hunan | 0.3523 | 8 | 0.2913 | 21 | 0.2883 | 22 |
| Guangdong | 0.4024 | 2 | 0.3344 | 8 | 0.3376 | 11 |
| Guangxi | 0.3162 | 16 | 0.3296 | 9 | 0.3617 | 8 |
| Hainan | 0.3619 | 7 | 0.3256 | 10 | 0.3616 | 9 |
| Chongqing | 0.3269 | 12 | 0.3139 | 13 | 0.3674 | 7 |
| Sichuan | 0.3326 | 11 | 0.3207 | 11 | 0.3052 | 17 |
| Guizhou | 0.3135 | 18 | 0.3505 | 6 | 0.3971 | 4 |
| Yunnan | 0.2827 | 25 | 0.2987 | 17 | 0.2715 | 26 |
| Shaanxi | 0.3141 | 17 | 0.2836 | 24 | 0.3438 | 10 |
| Gansu | 0.2684 | 27 | 0.2448 | 27 | 0.2517 | 27 |
| Ningxia | 0.2532 | 28 | 0.2305 | 28 | 0.3197 | 15 |
| Xinjiang | 0.2446 | 29 | 0.2747 | 26 | 0.2291 | 29 |
| Type | Province | Mean | Mean of A | Mean of B | Mean of C | Mean of D |
|---|---|---|---|---|---|---|
| I | Inner Mongolia, Jilin, Hebei, Liaoning, Shanxi, Heilongjiang, Yunnan, Gansu, Xinjiang, Guangxi, Ningxia, Jiangxi, Henan, Anhui, Hubei, Chongqing, Hunan, Shaanxi, Hainan | 0.2998 | 0.1075 | 0.0505 | 0.0612 | 0.0806 |
| II | Tianjin, Jiangsu, Beijing, Fujian, Sichuan, Guizhou, Shandong, Guangdong, Zhejiang | 0.3647 | 0.1052 | 0.1016 | 0.1044 | 0.0535 |
| III | Shanghai | 0.7768 | 0.1033 | 0.1198 | 0.4678 | 0.0859 |
| A2 | C1 | A1 | B2 | D4 |
|---|---|---|---|---|
| 21.46% | 12.96% | 11.52% | 10.00% | 7.12% |
| Province | Year | Index Ranking | ||||
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | ||
| Beijing | 2019 | C1(42.97%) | D4(12.05%) | A1(10.46%) | B2(8.27%) | A2(6.32%) |
| 2020 | C1(35.09%) | A2(16.62%) | B2(14.85%) | A1(13.99%) | D4(6.05%) | |
| 2021 | C1(38.12%) | B2(19.97%) | A1(11.07%) | A2(10.79%) | D4(5.48%) | |
| Tianjin | 2019 | C1(35.89%) | A2(13.71%) | A1(11.43%) | B2(7.61%) | D2(5.47%) |
| 2020 | C1(25.84%) | A2(24.49%) | B2(13.76%) | A1(13.55%) | C3(4.64%) | |
| 2021 | C1(32.08%) | B2(14.05%) | A1(13.49%) | A2(12.91%) | C3(5.93%) | |
| Hebei | 2019 | D4(15.75%) | A1(14.49%) | A2(13.49%) | C1(11.58%) | D3(8.19%) |
| 2020 | A2(19.72%) | A1(17.11%) | D4(11.80%) | C1(11.28%) | C3(8.39%) | |
| 2021 | A2(21.45%) | A1(14.78%) | C1(10.52%) | D3(8.14%) | C3(7.78%) | |
| Shanxi | 2019 | A2(30.20%) | A1(13.27%) | D3(8.46%) | D4(8.02%) | C3(7.92%) |
| 2020 | A2(23.14%) | A1(14.03%) | D4(11.22%) | C3(8.73%) | D3(8.28%) | |
| 2021 | A2(27.73%) | D3(11.76%) | A1(10.40%) | C3(9.42%) | C1(8.65%) | |
| Inner Mongolia | 2019 | A2(23.74%) | A1(13.52%) | D4(13.07%) | C3(8.82%) | D3(8.69%) |
| 2020 | A1(18.76%) | A2(16.41%) | D4(16.02%) | C3(8.88%) | B1(8.55%) | |
| 2021 | A2(29.77%) | C3(10.73%) | A1(9.83%) | D3(8.86%) | D2(7.91%) | |
| Liaoning | 2019 | A2(19.22%) | A1(16.37%) | D4(13.91%) | C1(9.98%) | B1(7.58%) |
| 2020 | A2(16.97%) | D4(16.54%) | A1(12.90%) | C1(10.27%) | C3(8.39%) | |
| 2021 | A2(23.80%) | A1(17.81%) | C1(10.16%) | C3(8.39%) | D3(7.00%) | |
| Jilin | 2019 | A2(18.36%) | D4(17.08%) | A1(13.48%) | D3(8.78%) | C3(8.22%) |
| 2020 | A2(18.38%) | A1(16.92%) | D4(16.04%) | C3(8.71%) | B1(6.87%) | |
| 2021 | A2(30.85%) | A1(14.43%) | C3(8.56%) | D4(7.43%) | D2(6.66%) | |
| Heilongjiang | 2019 | A2(21.46%) | A1(13.44%) | D4(12.59%) | D3(9.68%) | B2(9.05%) |
| 2020 | A1(20.24%) | A2(17.85%) | D4(11.80%) | D3(9.55%) | C3(9.04%) | |
| 2021 | A1(20.84%) | A2(20.69%) | D4(10.01%) | C3(8.70%) | D3(7.90%) | |
| Shanghai | 2019 | C1(60.57%) | A1(7.99%) | B2(5.39%) | D4(5.09%) | A2(5.03%) |
| 2020 | C1(56.01%) | B2(11.80%) | A2(7.18%) | A1(5.97%) | D4(3.46%) | |
| 2021 | C1(54.35%) | B2(12.41%) | A2(8.08%) | D4(6.18%) | A1(5.60%) | |
| Jiangsu | 2019 | C1(26.93%) | A2(22.04%) | B2(14.85%) | A1(8.36%) | D4(5.61%) |
| 2020 | C1(31.68%) | A2(22.46%) | B2(11.97%) | C3(7.06%) | A1(6.76%) | |
| 2021 | C1(32.32%) | A2(25.22%) | A1(9.87%) | B2(7.65%) | C3(7.21%) | |
| Zhejiang | 2019 | C1(29.29%) | A2(17.22%) | B2(14.28%) | A1(11.05%) | B1(7.12%) |
| 2020 | B2(31.83%) | C1(25.54%) | A2(12.90%) | C3(5.96%) | A1(5.93%) | |
| 2021 | B2(29.51%) | C1(23.71%) | A2(12.71%) | A1(7.82%) | B1(6.43%) | |
| Anhui | 2019 | A2(22.25%) | A1(13.53%) | C1(11.87%) | B2(11.22%) | D4(8.11%) |
| 2020 | A2(18.43%) | A1(14.21%) | C1(13.64%) | D4(9.22%) | C3(8.40%) | |
| 2021 | A2(27.01%) | C1(12.69%) | A1(8.53%) | D4(7.82%) | C3(7.49%) | |
| Fujian | 2019 | A2(24.22%) | B2(14.28%) | A1(10.93%) | C1(9.08%) | B1(8.56%) |
| 2020 | B2(24.70%) | C1(12.39%) | A2(11.73%) | A1(10.20%) | C3(7.98%) | |
| 2021 | B2(23.40%) | A2(15.02%) | A1(13.56%) | C1(11.57%) | B1(7.96%) | |
| Jiangxi | 2019 | A1(18.43%) | A2(18.23%) | D4(10.78%) | C1(7.83%) | B1(7.60%) |
| 2020 | B2(16.72%) | A2(15.28%) | A1(13.02%) | C1(8.35%) | C3(7.72%) | |
| 2021 | A2(20.10%) | B2(15.30%) | C1(9.88%) | B1(9.74%) | C3(8.88%) | |
| Shandong | 2019 | B2(28.05%) | C1(15.93%) | A2(15.56%) | A1(7.45%) | D4(7.04%) |
| 2020 | B2(27.66%) | C1(14.97%) | A2(14.18%) | D4(8.68%) | C3(6.16%) | |
| 2021 | B2(29.66%) | A2(17.26%) | C1(14.78%) | D4(6.55%) | A1(6.40%) | |
| Henan | 2019 | A2(27.44%) | C1(13.62%) | A1(10.42%) | B2(8.10%) | D3(7.14%) |
| 2020 | A2(15.85%) | B2(15.20%) | C1(13.16%) | A1(12.44%) | D3(8.89%) | |
| 2021 | B2(16.54%) | A2(16.37%) | C1(13.96%) | A1(13.70%) | C3(8.14%) | |
| Hubei | 2019 | A2(23.58%) | A1(11.62%) | C1(9.71%) | D4(8.88%) | D2(6.80%) |
| 2020 | A2(23.46%) | B2(12.43%) | D4(9.60%) | A1(8.91%) | C1(7.93%) | |
| 2021 | A2(18.11%) | D4(11.68%) | A1(10.75%) | C1(9.59%) | C3(7.64%) | |
| Hunan | 2019 | A2(25.53%) | A1(15.50%) | D4(11.12%) | D3(7.55%) | C1(7.11%) |
| 2020 | A2(24.69%) | A1(12.48%) | C1(8.62%) | C3(8.35%) | D3(7.98%) | |
| 2021 | A2(21.83%) | A1(8.95%) | C1(8.95%) | C3(8.20%) | D3(8.07%) | |
| Guangdong | 2019 | B2(28.33%) | A2(23.03%) | C1(16.41%) | A1(8.61%) | D4(5.05%) |
| 2020 | B2(25.92%) | A2(22.39%) | C1(19.43%) | A1(10.85%) | C3(5.01%) | |
| 2021 | B2(26.80%) | A2(22.96%) | C1(19.74%) | A1(10.48%) | C3(4.46%) | |
| Guangxi | 2019 | A2(32.64%) | A1(12.38%) | D3(9.64%) | B1(8.57%) | D4(8.18%) |
| 2020 | A2(21.49%) | B2(18.30%) | A1(8.61%) | D3(8.56%) | C3(7.72%) | |
| 2021 | A2(33.35%) | B2(17.68%) | A1(9.19%) | C3(7.00%) | C1(5.89%) | |
| Hainan | 2019 | A2(28.50%) | D4(10.70%) | A1(10.04%) | C1(8.61%) | B2(7.74%) |
| 2020 | A2(15.96%) | B2(15.00%) | D4(11.81%) | C1(9.60%) | C3(7.85%) | |
| 2021 | C1(26.56%) | A2(13.36%) | B2(9.64%) | D4(8.39%) | C3(6.99%) | |
| Chongqing | 2019 | A2(25.18%) | C1(13.66%) | D4(11.86%) | A1(11.77%) | B1(8.15%) |
| 2020 | A2(26.49%) | C1(14.05%) | A1(9.67%) | C3(7.96%) | D4(7.96%) | |
| 2021 | A2(26.01%) | B2(15.46%) | C1(12.39%) | A1(8.22%) | C3(6.80%) | |
| Sichuan | 2019 | A2(24.42%) | A1(14.31%) | B2(13.37%) | D4(9.90%) | B1(7.58%) |
| 2020 | B2(23.30%) | A2(15.92%) | A1(12.32%) | C3(7.56%) | D3(6.53%) | |
| 2021 | A2(20.04%) | B2(19.33%) | A1(9.65%) | B1(9.40%) | C3(8.00%) | |
| Guizhou | 2019 | B2(20.37%) | A1(16.90%) | A2(15.15%) | B1(8.79%) | D4(8.44%) |
| 2020 | B2(24.32%) | A1(20.59%) | A2(15.34%) | C3(7.15%) | C1(5.23%) | |
| 2021 | A2(30.34%) | B2(18.41%) | A1(13.61%) | C3(6.29%) | B1(6.11%) | |
| Yunnan | 2019 | A2(42.53%) | D3(7.82%) | A1(7.58%) | C3(7.19%) | D2(6.83%) |
| 2020 | A2(30.70%) | A1(10.70%) | D4(9.65%) | D3(9.28%) | C3(8.43%) | |
| 2021 | A2(27.75%) | A1(14.69%) | D3(10.01%) | C3(9.25%) | B1(7.16%) | |
| Shananxi | 2019 | A2(21.28%) | D4(15.98%) | A1(11.61%) | B1(7.84%) | D3(6.65%) |
| 2020 | A2(18.02%) | D4(14.65%) | A1(12.45%) | B1(9.42%) | C3(8.94%) | |
| 2021 | A2(30.26%) | B1(9.77%) | D4(9.65%) | C3(7.34%) | D3(7.30%) | |
| Gansu | 2019 | A2(34.42%) | A1(10.14%) | C3(8.51%) | D3(8.50%) | B1(7.69%) |
| 2020 | A2(30.05%) | D3(10.91%) | C3(10.48%) | B1(7.88%) | D2(7.84%) | |
| 2021 | A2(28.75%) | C3(10.20%) | B2(9.26%) | A1(8.59%) | D3(7.26%) | |
| Ningxia | 2019 | A2(33.51%) | B2(12.94%) | D3(12.54%) | D2(7.63%) | C2(6.62%) |
| 2020 | A1(16.14%) | B1(12.57%) | D3(12.31%) | C3(11.19%) | A2(9.33%) | |
| 2021 | A2(25.72%) | A1(16.54%) | B2(12.97%) | C3(8.07%) | D3(8.06%) | |
| Xinjiang | 2019 | A2(31.53%) | D3(13.61%) | A1(12.15%) | D2(8.14%) | B1(7.00%) |
| 2020 | A2(38.02%) | B1(12.23%) | D3(12.12%) | C3(9.12%) | D2(6.99%) | |
| 2021 | A2(25.18%) | A1(16.45%) | D3(14.53%) | C3(11.02%) | D2(8.46%) | |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, F.; Zhang, Z. Addressing the Sustainability Challenges: Digital Economy Information Security Risk Assessment. Sustainability 2025, 17, 6428. https://doi.org/10.3390/su17146428
Li F, Zhang Z. Addressing the Sustainability Challenges: Digital Economy Information Security Risk Assessment. Sustainability. 2025; 17(14):6428. https://doi.org/10.3390/su17146428
Chicago/Turabian StyleLi, Fanke, and Zhongqingyang Zhang. 2025. "Addressing the Sustainability Challenges: Digital Economy Information Security Risk Assessment" Sustainability 17, no. 14: 6428. https://doi.org/10.3390/su17146428
APA StyleLi, F., & Zhang, Z. (2025). Addressing the Sustainability Challenges: Digital Economy Information Security Risk Assessment. Sustainability, 17(14), 6428. https://doi.org/10.3390/su17146428


_Li.png)


