1. Introduction
The global transition to sustainable energy is driven by the urgent need to mitigate climate change, reduce greenhouse gas emissions, and enhance energy security amid depleting fossil fuel reserves. Wind power, valued for its low carbon footprint and scalability, is a cornerstone of this shift, advancing United Nations Sustainable Development Goals, notably SDG 7 (Affordable and Clean Energy) and SDG 13 (Climate Action). Variable-speed Wind Turbines (VSWTs), with advanced control systems and adaptability to fluctuating wind conditions, are integral to smart grids, optimizing energy efficiency and grid reliability. However, their integration into digital communication networks introduces significant cybersecurity risks, particularly from False Data Injection (FDI) attacks. These attacks manipulate critical operational data, such as wind speed or blade pitch angle, deceiving control systems and disrupting turbine performance, which can undermine energy efficiency and grid stability.
Such vulnerabilities threaten the reliability and environmental benefits of wind power. For instance, disruptions may increase reliance on fossil fuel backups, negating carbon reduction gains and raising costs. With wind power projected to supply over 20% of global electricity by 2030, per the International Energy Agency, safeguarding these systems is critical for attaining sustainable energy goals. FDI attacks, if unmitigated, could erode confidence in renewable energy and exacerbate environmental impacts through inefficiencies. Robust cybersecurity is thus essential to ensure operational resilience and minimize lifecycle emissions, reinforcing wind power’s role in a low-carbon future.
Despite wind power’s importance, the existing literature often overlooks VSWT-specific vulnerabilities to FDI attacks and their implications for energy efficiency and sustainability. While general cybersecurity strategies for renewable systems exist, they rarely address the sophisticated nature of FDI attacks or their impact on turbine performance and grid stability. This study proposes a novel approach to detect and mitigate FDI attacks in VSWTs, aiming to enhance cyber resilience and ensure reliable, sustainable energy production. By addressing this gap, this research contributes to securing renewable energy infrastructure, supporting global sustainability objectives in an interconnected energy landscape.
The novelty of this study lies in its comprehensive two-stage methodology that not only simulates FDI attacks on key control inputs of VSWTs but also evaluates the impact of these attacks through the lens of sustainability and grid resilience. Unlike existing studies that often examine FDI impacts in isolation or focus solely on detection, this research integrates control-loop-level analysis with sustainability metrics—such as energy efficiency, emission reduction, and grid stability—to form a holistic framework. This dual emphasis on operational resilience and sustainable development distinguishes our approach from earlier research and enhances its relevance for modern smart grid applications.
As such, the research question in this study is as follows: how can advanced detection and mitigation strategies be developed to protect VSWTs from FDI attacks, ensuring their operational reliability and performance while enhancing the sustainability of wind energy systems in the face of growing cybersecurity threats?
This study demonstrates that advanced detection and mitigation strategies can protect VSWTs from FDI attacks, enhancing their cyber resilience. A novel analytical framework, validated through MATLAB-based simulations of an induction generator VSWT, evaluates the impact of FDI attacks on operational parameters, including wind speed, blade pitch angle, and generator angular speed. The findings reveal that injecting false data about wind speed triggers significant power output deviations and decision-making errors, identifying it as a critical vulnerability. In contrast, pitch angle manipulations have negligible effects, guiding targeted defense prioritization.
To counter these threats, a robust strategy is proposed, integrating real-time monitoring and adaptive control to detect wind speed data anomalies and stabilize turbine performance. This approach mitigates operational disruptions, ensuring consistent power output and reducing risks of grid instability. By preventing reliance on fossil fuel backups during cyber-induced failures, the strategy preserves wind energy’s low-carbon benefits and supports energy security in smart grids. This research provides a practical framework to strengthen the cybersecurity of wind energy systems, addressing escalating threats in interconnected energy landscapes. By enhancing operational reliability and environmental sustainability, the proposed measures reinforce wind power’s role in achieving a secure, low-carbon energy future, offering actionable insights for policymakers and industry stakeholders to safeguard renewable energy infrastructure.
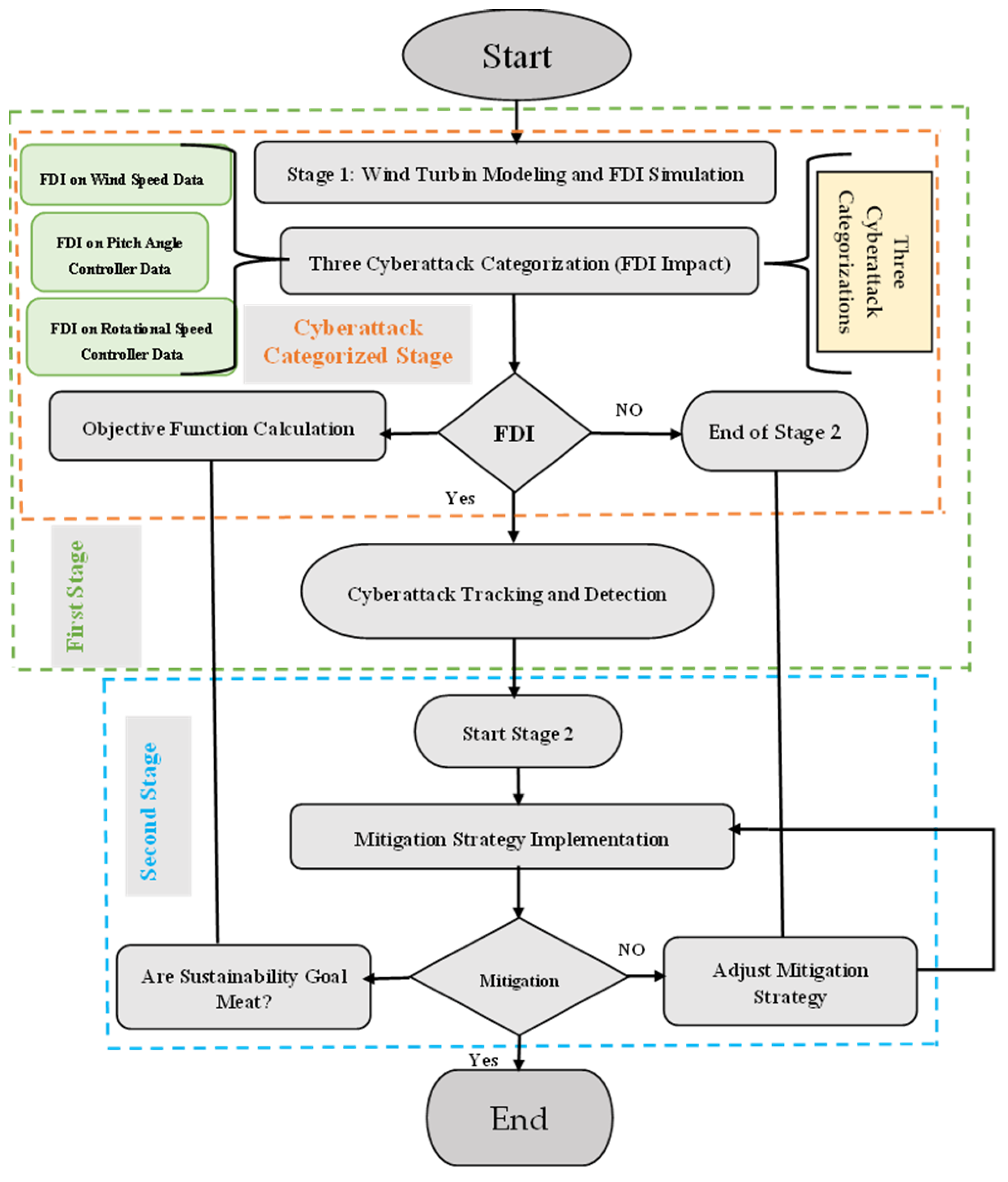
The flowchart in
Figure 1, entitled “Flowchart for Detection and Mitigation of FDI Attacks in Variable-Speed Wind Turbines”, delineates a comprehensive two-stage methodology to address FDI attacks in VSWTs, critical components of renewable energy systems, by integrating advanced detection techniques, adaptive mitigation strategies, and sustainability assessments to ensure operational reliability and environmental sustainability.
Based on the suggested flowchart, Stage 1 commenced with the development of a VSWT model using MATLAB, incorporating a variable-speed induction generator to simulate FDI attacks on wind speed, pitch angle, and rotational speed, as highlighted in the study’s abstract, followed by the categorization of these attacks, which identified wind speed as the most disruptive factor, causing significant output power deviations and decision-making errors. An objective function calculation quantified these impacts, leading to a decision point that, if significant, triggered real-time tracking and detection of wind speed anomalies, concluding Stage 1. Non-significant impacts led directly to result validation, aligning with the linear process in attachment ID 1 and the optimization steps in attachments ID 0 and ID 2. Stage 2 began with the implementation of adaptive control adjustments to mitigate FDI effects, stabilizing turbine performance as supported by resilient control, followed by an effectiveness evaluation with a feedback loop for iterative adjustments if ineffective, mirroring the iterative loops in attachments ID 0 and ID 2; if effective, a sustainability assessment evaluated energy efficiency, carbon emission avoidance, and grid stability contributions, ensuring alignment with sustainable development goals (SDGs) like SDG 7 and 13. This was a novel step that addressed the Introduction’s emphasis on environmental sustainability. After this, we validated results to confirm operational reliability and sustainability, with a final decision point looping back to refine mitigation if sustainability goals were unmet, thereby reinforcing wind energy’s role in a low-carbon future while addressing VSWT-specific vulnerabilities. Final validation confirms operational reliability and sustainability using a multi-criteria decision analysis to balance performance and sustainability, with a decision point looping back to refine mitigation strategies if sustainability goals are unmet, thereby reinforcing wind energy’s role in a low-carbon future while addressing VSWT-specific vulnerabilities through iterative optimization and advanced analytical techniques.
The paper is structured as follows:
Section 2 presents a comprehensive literature review, synthesizing existing research on wind turbine cybersecurity, sustainability, and resilience strategies to contextualize the study.
Section 3 introduces foundational modeling tools for wind turbines, including pitch angle and rotor speed dynamics, and thus establishing the technical framework for the analysis.
Section 4 validates the VSWTs model through rigorous simulations, confirming its reliability for real-world applications.
Section 5 details the proposed methodology, outlining a novel approach to detect and mitigate FDI attacks in VSWTs.
Section 6 evaluates the results, elucidating the effects of FDI on turbine performance and operational stability. Finally,
Section 7 concludes the paper, offering insights into the implications for enhancing the resilience and sustainability of wind energy systems within the broader vision of a secure, low-carbon energy future.
2. Literature Review
The rapid expansion of wind power, as a cornerstone of sustainable energy systems, catalyzed significant advancements in renewable energy generation, yet it also introduced complex challenges in cybersecurity, operational resilience, and long-term sustainability. This section synthesized key studies to situate current research within the domains of wind turbine technology, cyber–physical security, and environmental sustainability, emphasizing their implications for achieving Sustainable Development Goals (SDGs) such as SDG 7 (Affordable and Clean Energy) and SDG 13 (Climate Action). Mohanty et al. [
1] explored the role of photonics in offshore wind energy systems, demonstrating how high-capacity optical fibers improved data transmission reliability and photonics-based underwater sensors enhanced subsea component maintenance. These innovations reduced operational downtime, increased energy efficiency, and minimized environmental impacts, bolstering the sustainability of offshore wind farms. However, harsh marine conditions and high costs highlighted the need for durable, cost-effective solutions to ensure economic viability alongside ecological benefits.
Cybersecurity threats, particularly FDI attacks, posed a significant risk to wind turbine control systems. Mazare et al. [
2] developed a reinforcement learning-based control strategy that integrated adaptive neural networks and Lyapunov-based constraints to enhance resilience against FDI attacks. This approach stabilized rotor speed, ensured consistent power output, and reduced disruptions that could undermine wind energy’s low-carbon profile. Similarly, Zhao et al. [
3] proposed an adaptive resilient control method using rotor speed observers to detect cyber intrusions and adjust generator torque dynamically, mitigating FDI impacts and sustaining environmental advantages.
The integration of wind energy into modern power systems amplified cybersecurity vulnerabilities, especially in hybrid storage and electrified transport networks. Zhao et al. [
4] revealed that AI-driven cyberattacks disrupted up to 40% of hydrogen-power storage operations undetected, threatening renewable energy reliability and necessitating robust defenses for sustainability. Aljohani et al. [
5] surveyed cybersecurity risks in electric vehicles (EVs) as dynamic loads and mobile energy sources, identifying data breaches and grid instability as key threats, requiring fortified security to protect sustainable energy networks.
Wind power’s growing penetration introduced stability and cybersecurity challenges in cyber–physical systems. Gao et al. [
6] demonstrated that wind power uncertainty and communication delays triggered cascading failures, undermining grid reliability and sustainability. Ahmed et al. [
7] proposed a wireless network architecture based on IEC 61400-25, which enhanced data transmission reliability in remote wind farms and supported sustainable grid integration, reducing operational risks.
Accurate modeling proved essential for wind farm stability and sustainability. Ma et al. [
8] developed a cyber–physical modeling technique that improved wind farm aggregation by addressing Low-Voltage Ride-Through (LVRT) characteristics, reducing simulation errors and ensuring reliable power delivery. Cheng et al. [
9] introduced a federated learning-based approach for detecting turbine blade icing, achieving high accuracy while preserving data privacy, minimizing energy losses, and enhancing economic and environmental sustainability.
Resilience frameworks became critical as wind farms integrated with cyber systems. Zhao et al. [
10] designed a cyber-resilient torque control strategy that countered hybrid cyberattacks, such as denial of service and data manipulation, by stabilizing rotor speed, ensuring operational continuity and reducing environmental impacts. Jadidi et al. [
11] proposed a hybrid fault-tolerant and attack-resilient control method for offshore wind farms, using adaptive model predictive control and signal correction to maintain reliability under combined faults and cyber intrusions, supporting sustainable offshore energy production.
Advanced mitigation techniques strengthened wind farm cybersecurity and sustainability. Badihi et al. [
12] implemented a smart anomaly detection system that monitored network activity in real time and adjusted power controls, minimizing cyber risks and ensuring uninterrupted renewable energy generation. Liu et al. [
13] developed a grouping-based frequency regulation strategy that clustered wind turbines by wind profiles and used hierarchical control to enhance system response under conditions of cyber uncertainty, stabilizing grid frequency and advancing energy sustainability. Smacki et al. [
14] examined cybersecurity risks in offshore wind farms using autonomous ships, identifying vulnerabilities and developing rapid response strategies to enhance maritime and energy security, vital for sustainable offshore wind development.
Resilience strategies integrated economic and environmental sustainability. Pazouki et al. [
15] devised a remedial action framework that mitigated economic losses from cyberattacks on energy hubs by optimizing component connections, reducing costs by up to 76% and supporting the economic viability of sustainable energy infrastructure. Palanimuthu et al. [
16] formulated a reinforcement learning-based resilient control scheme for large-scale wind turbines to counter cyber actuator attacks, optimizing pitch and torque control to maximize power output while minimizing environmental impact through sustained efficiency.
Maintenance strategies proved pivotal for sustainable wind turbine operation. Khan et al. [
17] integrated diverse sensor data and AI models into a multimodal machine learning approach for predictive fault detection, enabling early fault classification and prognosis up to 48 h in advance, thus reducing downtime and lifecycle emissions. Al Lahham et al. [
18] evaluated online condition monitoring, signal processing, and failure diagnostics in a comprehensive review, underscoring their role in minimizing operational costs and ensuring continuous performance, essential for economic and environmental sustainability. Aranizadeh et al. [
19] employed frequency-domain analysis to detect early-stage failures in small-scale wind turbine blades, minimizing maintenance downtime and enhancing reliability, and thereby supporting the sustainability of small-scale wind energy systems. Aranizadeh et al. [
20] and Aranizadeh et al. [
21] extended this focus to failure diagnosis and maintenance planning across broader power grid components, reinforcing the systemic resilience necessary for sustainable energy networks.
Ref. [
22] proposes a risk-averse decentralized energy management strategy for integrated electricity and heat systems, considering vertical heating imbalances in buildings through a detailed thermal dynamic model. To avoid overly optimistic decisions, a CVaR-based approach is adopted, and a two-stage accelerated asynchronous decentralized ADMM algorithm is introduced to preserve privacy and reduce computational burden. Also, Ref. [
23] presents a stochastic bi-level optimal allocation approach for intelligent buildings (IBs) that incorporates energy storage sharing (ESS) services to reduce investment costs. By modeling the thermal dynamics of buildings with air conditioning and ESS stations, the proposed framework accounts for electricity price uncertainties. The upper level minimizes ESS planning costs, while the lower level minimizes the operational costs of IBs.
Despite these advancements, significant gaps persisted in addressing the specific vulnerabilities of VSWTs to FDI attacks and their broader implications for sustainability. Traditional cybersecurity methods often failed to detect sophisticated FDI attacks, leaving wind energy systems prone to disruptions that compromised efficiency, reliability, and environmental benefits. This literature collectively highlighted the critical intersection of cybersecurity and sustainability, where the failure to mitigate cyber threats not only jeopardized operational performance but also risked undermining wind power’s contributions to reducing carbon emissions and achieving a low-carbon energy future. The reliance on wind energy as a sustainable resource intensified the urgency to develop innovative strategies to safeguard its operational integrity while preserving its ecological and economic advantages. Such strategies are needed to ensure that wind farms continue to support global sustainability goals, including energy access, climate action, and resilient infrastructure, amidst escalating cyber risks. Consequently, this review underscored the necessity for a targeted approach that integrated advanced detection and mitigation techniques with sustainability principles, setting the stage for the subsequent section to define the research gap and articulate how this study addressed these pressing challenges in the context of sustainable wind energy systems.
3. Basic Tools
This section delineated the foundational tools and methodologies employed in the study to model and analyze VSWTs under FDI attacks, providing the technical groundwork for subsequent simulation and mitigation strategies. The primary tool utilized was MATLAB, which facilitated the development of a comprehensive VSWT model incorporating a variable-speed induction generator, enabling the precise simulation of FDI attacks on critical parameters such as wind speed, blade pitch angle, and rotational speed, as outlined in the abstract. MATLAB’s robust computational capabilities supported the implementation of aerodynamic models, control algorithms, and real-time monitoring systems, which were essential for tracking and detecting cyber intrusions, as described in the flowchart (
Section 5). Additionally, the study leveraged established aerodynamic power equations, as referenced in [
24,
25], to calculate the turbine’s power output, integrating sustainability metrics such as energy efficiency and carbon emission avoidance to align with SDGs like SDG 7 and SDG 13. The literature review further informed the selection of these tools, with studies such as those of Zhao et al. [
3] and Mazare et al. [
2] highlighting the importance of adaptive control and reinforcement learning in stabilizing turbine performance under cyber threats, ensuring both operational reliability and environmental sustainability. These tools collectively enabled a systematic approach to assess FDI impacts, develop mitigation strategies, and evaluate their sustainability outcomes, reinforcing wind energy’s role in a low-carbon energy future.
3.1. Wind Turbine Modeling
This subsection detailed the aerodynamic model of the WT, the dynamics of the blade pitch angle, and the procedure for achieving Maximum Power Point Tracking (MPPT) in VSWTs, establishing the foundation for simulating FDI attacks and their impacts on operational performance. The power output of the WT (Pt) was determined using the aerodynamic power equation presented in (1), derived from established models in [
24,
25]. This equation accounted for parameters such as wind speed, air density, rotor swept area, and the power coefficient influenced by the blade pitch angle and tip speed ratio, optimizing energy capture under varying wind conditions. The blade pitch angle dynamics were modeled to adjust the angle of attack, ensuring efficient power extraction while maintaining stability, a critical factor for MPPT, as supported by Zhao et al. [
3], whose work emphasized the role of rotor speed stabilization in achieving consistent output under cyber threats. The MPPT procedure employed a control strategy that dynamically adjusted the rotor speed to track the optimal operating point, maximizing energy efficiency and minimizing losses, and thereby enhancing the sustainability of wind energy systems in alignment with SDG 7. This modeling framework, implemented in MATLAB, facilitated the simulation of FDI attacks on wind speed, blade pitch angle, and rotational speed, as described in the flowchart (
Section 5), enabling the assessment of their effects on power output and the development of detection and mitigation strategies to ensure operational reliability and environmental sustainability.
In (1), ρ represents the air density in kg/m
3, A denotes the rotor-swept area in m
2, v is the wind speed in m/s, and C
P is the turbine’s power coefficient. It should be noted that the power coefficient depends on the blade tip speed ratio (TSR or λ) and the pitch angle (θ). The tip speed ratio (λ) is defined as shown in (2).
where ω
t represents the rotor speed of the turbine. Additionally, C
P is a nonlinear function influenced by the turbine components and the losses occurring during the energy conversion process. This value was approximated using (3).
3.2. Pitch Angle Modeling
The pitch angle controller operates using a closed-loop Proportional–Integral (PI) feedback mechanism that monitors the wind speed and adjusts blade angles to regulate aerodynamic torque. Under wind speeds exceeding the rated value, the controller increases the pitch angle to reduce power output and avoid overloading the generator. Conversely, at sub-rated wind speeds, the pitch angle is minimized to maximize energy capture. This feedback loop is sensitive to the manipulation of wind speed or power output data, which can trigger erroneous pitch adjustments and reduce operational efficiency.
For a pitch angle of 0 degrees, the maximum power coefficient is achieved, which corresponds to a blade TSR of
, yielding a
value of
. As the pitch angle increases, the range of the blade tip speed ratio widens, resulting in a decrease in the maximum value of
[
26,
27]. This relationship underscores the importance of optimizing the pitch angle to maximize energy capture efficiency in VSWTs, thereby enhancing the overall performance and sustainability of wind energy systems. Such optimization is critical for ensuring consistent power output under varying wind conditions, supporting the reliability of renewable energy generation.
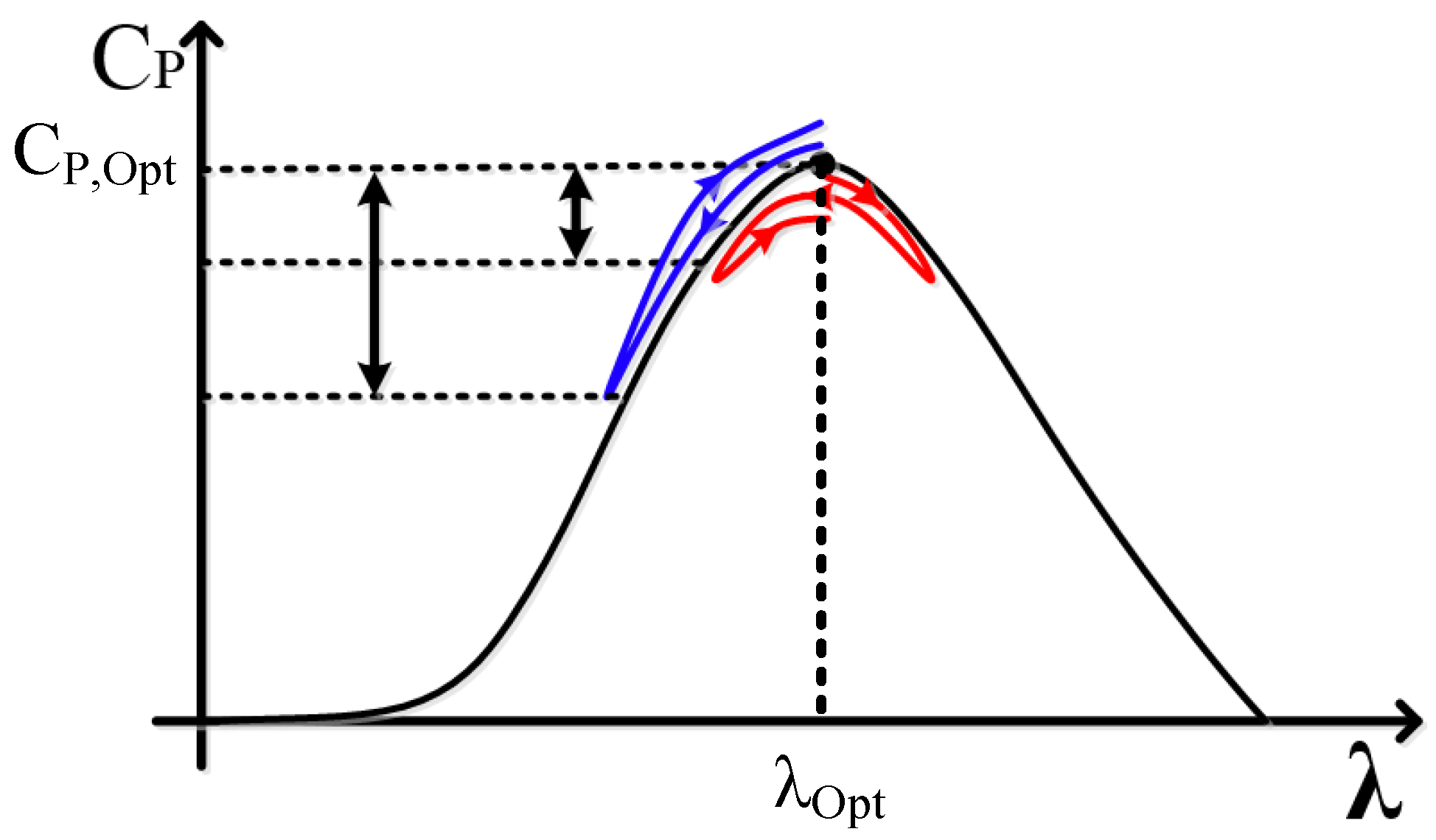
3.3. Rotor Speed Modeling
The rotor speed control system follows an MPPT strategy by dynamically adjusting generator torque to maintain the . A PI controller compares the measured rotor speed with the reference derived from wind speed and adjusts torque accordingly. Any FDI affecting wind speed or rotor speed sensor data can distort this comparison, misguide the torque control, and shift the operating point away from the CP,Opt, leading to suboptimal performance.
Thus, maximum
is achieved when the λ is at the optimal value (
). At a specific wind speed (v), to reach the highest efficiency (maximum
or C
P,Opt), the rotor’s speed needs to be kept at the ideal or optimal (
) point. When the wind speed changes, the rotor speed and the power captured by the WT will change. At a specific wind speed, the power output changes in relation to the rotor speed (ω), and there is a specific point where the power reaches its highest value, known as the optimal rotor speed (
). This procedure is shown in
Figure 2. Optimizing the rotor speed to achieve maximum
enhances the energy efficiency of VSWTs, thereby reducing energy losses and supporting the sustainability of wind energy systems. This approach minimizes the environmental footprint by maximizing renewable energy capture, contributing to a low-carbon energy future. Furthermore, maintaining optimal performance under varying wind conditions ensures grid stability, aligning with SDG 7 and SDG 13. Such efficiency improvements reduce the need for fossil fuel-based backup systems, reinforcing wind energy’s role in climate change mitigation. Consequently, this methodology underscores the critical link between operational optimization and environmental sustainability in renewable energy generation.
4. Simulation Validation
To evaluate the reliability and accuracy of the WT model under investigation, the power output curve was analyzed in relation to specific wind speeds, as depicted in
Figure 3a. In this figure, the power output remained at zero until the wind speed attained the cut-in speed threshold of 3 m/s. Beyond this threshold, the power output increased proportionally to the cube of the wind speed. To maximize power generation within this operational range, the turbine’s speed was meticulously controlled, ensuring that the rotor speed maintained a consistent relative blade tip speed, thereby consistently achieving the maximum
. This optimization not only enhanced the energy efficiency of the VSWT but also contributed significantly to the sustainability of wind energy systems by reducing energy losses. Such efficiency improvements minimized the environmental footprint of energy production, supporting a low-carbon energy framework. Additionally, consistent power output ensured grid stability, aligning with SDG 7 and SDG 13. By maximizing renewable energy capture, the approach reduced reliance on fossil fuel-based backup systems, mitigating greenhouse gas emissions. This operational reliability further bolstered the economic viability of wind energy, promoting its scalability in sustainable energy transitions. Consequently, the validated WT model underscored the critical role of precise control in achieving both environmental and operational sustainability in renewable energy generation.
Furthermore, it was observed that the power output remained constant at its nominal value once the wind speed exceeded the rated speed, a condition achieved through the precise regulation of the pitch angle. It is imperative to highlight that, although greater potential for power generation existed above the rated speed, the decision to maintain power at its rated value served two primary purposes: safeguarding electrical systems and preventing excessive rotor speed.
The variations in the pitch angle, illustrated in
Figure 3b, further demonstrated this mechanism, as the blade pitch angle increased proportionally with wind speeds surpassing the nominal value. Additionally, the analysis of rotor speed behavior revealed that, as the wind speed increased beyond the cut-in speed, the rotor speed initially rose in alignment with the increasing wind velocity; however, upon reaching the rated wind speed, the rotor speed stabilized to maintain the desired relative blade tip speed, ensuring the turbine operated at optimal efficiency. This regulation of rotor speed was crucial for maximizing energy capture while mitigating mechanical stress on the system, with the rotor speed remaining steady above the rated wind speed, underscoring the importance of controlling both the WT’s power output and rotor dynamics for system longevity and performance, as depicted in the rotor speed variations shown in
Figure 3c [
28,
29]. Such precise control mechanisms enhanced the sustainability of VSWTs by optimizing energy efficiency and reducing operational losses, thereby minimizing the environmental footprint of wind energy production. This approach supported a low-carbon energy framework by ensuring consistent renewable energy generation, aligning with SDG 7 and SDG 13. Moreover, maintaining system longevity through regulated rotor dynamics reduced the need for frequent maintenance, lowering lifecycle emissions. The stability in power output also contributed to grid reliability, facilitating the integration of wind energy into sustainable energy systems. Consequently, these strategies reinforced wind energy’s role in climate change mitigation by reducing reliance on fossil fuel-based alternatives, promoting a scalable and environmentally sustainable energy transition.
5. Methodology
The methodology will be outlined as follows. It is based on the following components:
WT modeling and simulation.
Identifying data vulnerable to FDI:
- ✓
Wind speed data → effect on WT controller.
- ✓
WT output power data → effect on pitch angle controller.
- ✓
Rotational speed data → effect on rotational speed of WT controller
- ✓
Other relevant data points
Cyberattack simulation and identification of its effect on WT.
Cyberattack tracking.
Cyberattack detection modeling by the operator.
Result validation.
The details of this algorithm are shown in
Figure 4. This structured methodology enabled a systematic evaluation of the impacts of FDI on VSWTs by first establishing a robust WT model to simulate real-world operating conditions. The identification of vulnerable data points ensured a targeted approach to understanding how FDI attacks disrupted critical control mechanisms, such as pitch angle and rotor speed regulation. Cyberattack simulation and tracking allowed for the precise isolation of malicious data injections, while the operator’s detection modeling facilitated the real-time identification of anomalies. The validation of results confirmed the effectiveness of the proposed strategies in maintaining WT performance under cyber threats. By addressing these vulnerabilities, the methodology enhanced the operational resilience of wind energy systems, ensuring consistent power generation. This approach significantly contributed to sustainability by optimizing energy efficiency and minimizing losses, reducing the environmental footprint of wind energy production. It supported a low-carbon energy framework, aligning with SDG 7 and SDG 13. Furthermore, reliable WT operation improved grid stability, facilitating the integration of renewable energy into sustainable systems. The methodology also reduced reliance on fossil fuel-based backups, mitigating greenhouse gas emissions. Ultimately, it reinforced wind energy’s role in advancing climate change mitigation through scalable and sustainable energy solutions.
The FDI procedure applied to the WT is introduced below. As shown in
Figure 4, cyberattacks on WTs can effectively target three critical inputs through FDI mechanisms:
Figure 5 illustrates that these cyberattacks exploit three key WT inputs—wind speed, pitch angle, and rotational speed controller data. By manipulating and distorting these inputs, the overall performance of the wind turbine is significantly compromised. Specifically, such disruptions reduce the WT’s power output, introduce errors into the power grid’s load flow calculations, and may ultimately destabilize grid operations.
Furthermore, to facilitate the comparative analysis of the obtained results, two parameters,
, and
are defined, as expressed in (5) and (6).
According to these equations, represents the steady-state power difference, while denotes the maximum power deviation. Additionally, |AA corresponds to the steady-state power after a cyberattack, whereas P|BA represents the power before the cyberattack. Moreover, |AA and |AA indicate the undershoot and overshoot after the cyberattack, respectively.
The methodology incorporates realistic control structures in the wind turbine simulation to assess the consequences of FDI. The pitch and rotor speed controllers operate based on real-time sensor data, forming interdependent feedback loops. When false data are injected, these control loops can react incorrectly—either by reducing power unnecessarily or failing to limit excessive output—thus highlighting the critical role of accurate sensor feedback in maintaining system stability. This control interaction is key to understanding the dynamics of turbine behavior under cyberattack scenarios.
6. Simulation Results and Discussion
For the analysis of simulation results, a 50-KW variable-speed wind turbine equipped with an induction generator is utilized. The detailed specifications of the wind turbine and the induction generator are provided in
Table 1 and
Table 2, respectively. The wind turbine model adopted in this study is a variable-speed Doubly Fed Induction Generator (DFIG), which is widely recognized for its efficiency in harnessing wind energy. The Perturb and Observe (P&O) algorithm is employed as the MPPT technique to optimize energy extraction. All simulations are performed using MATLAB/Simulink software (version 2016-B), ensuring accurate and reliable results. From a sustainability perspective, the use of a DFIG-based wind turbine enhances energy efficiency and reduces operational losses, thereby contributing to the broader goal of minimizing the environmental footprint of renewable energy systems.
In the subsequent sections, the impact of cyberattacks on wind turbine data and their consequent effects on the turbine’s output power are rigorously analyzed. Following this, a comparative assessment of various attack scenarios is conducted to evaluate their relative influence on system performance. This analysis also considers the broader implications for sustainability, as cyberattacks that compromise output power can undermine the reliability of renewable energy sources, potentially increasing dependence on less sustainable alternatives.
6.1. FDI on Wind Speed Data
In this section, the results pertaining to the case of FDI on wind speed data are presented, with the findings systematically analyzed under two distinct scenarios:
- i.
FDI with a value lower than the actual wind speed (Actual Data, AD), and
- ii.
FDI with a value higher than the actual wind speed (Actual Data, AD).
From a sustainability perspective, these scenarios highlight the potential for FDI attacks to disrupt the optimal operation of wind turbines, which may lead to inefficiencies in energy production and compromise the reliability of renewable energy contributions to the grid.
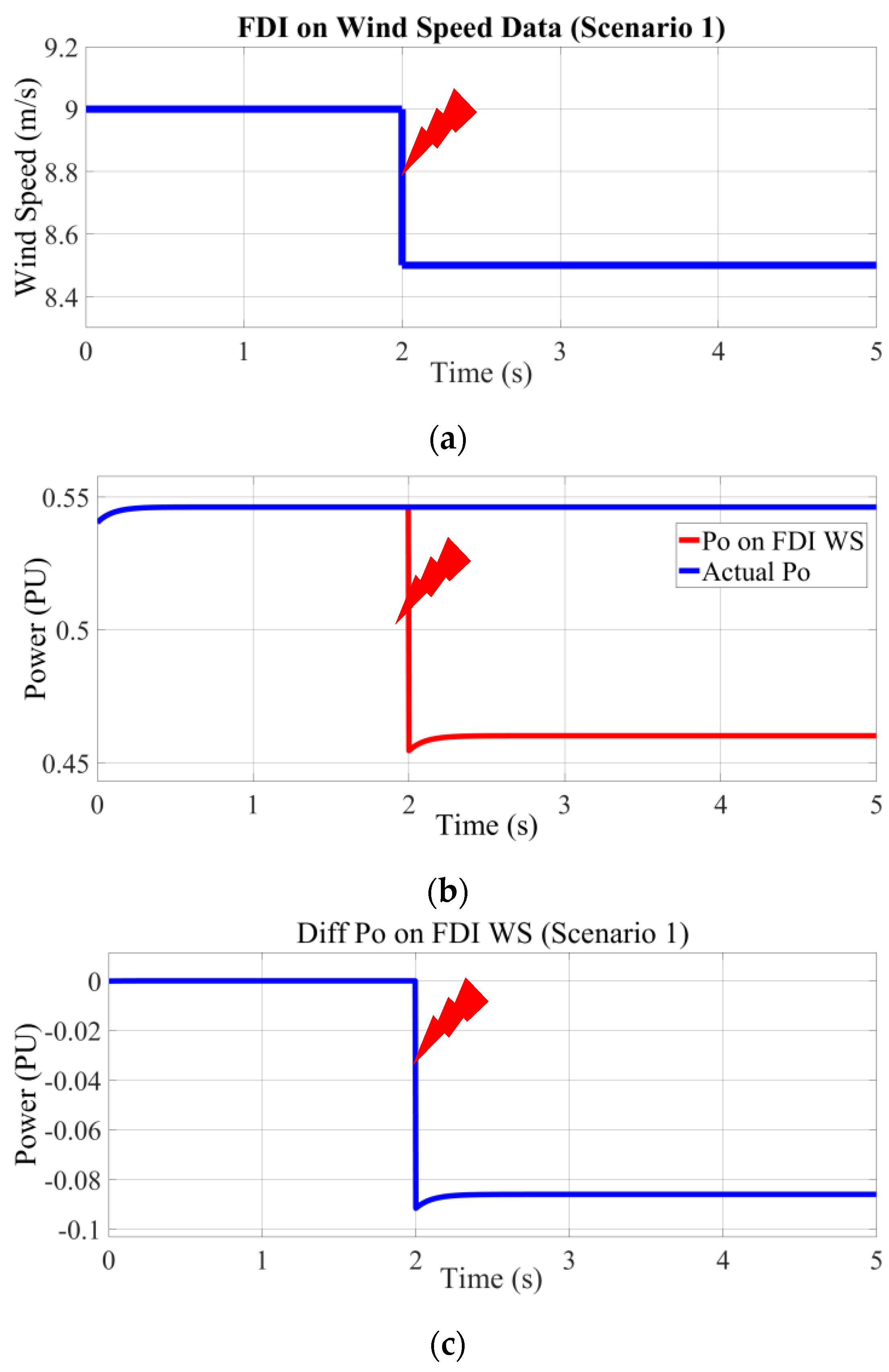
6.1.1. First Scenario (VFDI < VAD)
As demonstrated in this section, the initial wind speed applied to the wind turbine is 9 m/s (denoted as V
AD). However, following the injection of falsified data, the wind speed decreases to 8.5 m/s (denoted as V
FDI), reflecting a reduction of approximately 5.5%. This alteration in the wind speed data is illustrated in
Figure 6a. Consequently, the reduction in wind speed leads to a decline in the turbine’s power output below its expected value, as depicted in
Figure 6b. The resulting discrepancy in power output, which manifests as a notable deviation (less than 0.1 per unit), is further elucidated in
Figure 6c. From a sustainability perspective, such reductions in power output due to FDI attacks can undermine the efficiency of wind energy systems, potentially diminishing their contribution to sustainable energy goals and increasing reliance on less environmentally friendly energy sources.
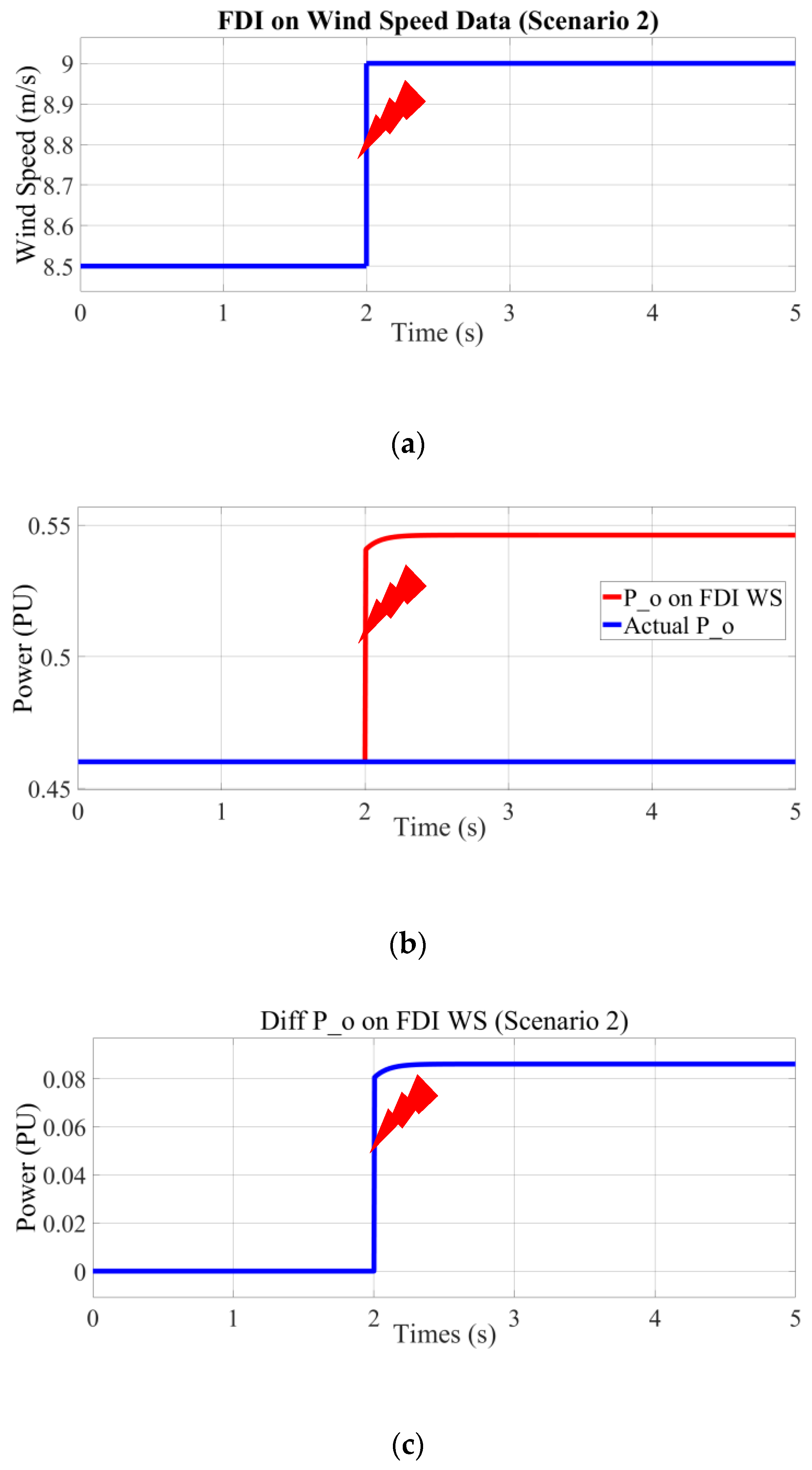
6.1.2. Second Scenario (VFDI > VAD)
As outlined in this section, the initial wind speed applied to the wind turbine is 8.5 m/s (denoted as V
AD). However, following the injection of falsified data, the wind speed increases to 9 m/s (denoted as V
FDI), corresponding to an approximate increase of 5.9%. This modification in the wind speed data is illustrated in
Figure 7a. Consequently, this increase causes the wind turbine’s power output to exceed its expected value, as shown in
Figure 7b. The resulting power discrepancy, which manifests as a significant deviation (less than 0.1 per unit), is further elucidated in
Figure 7c. From a sustainability perspective, such an overestimation of power output due to FDI attacks can lead to operational inefficiencies and potential grid instability, thereby jeopardizing the reliability of wind energy as a sustainable power source.
6.1.3. Discussion on Wind Speed Data Attacking
This section provides a comprehensive summary of the results derived from the cyberattack on wind speed data, as detailed in
Table 3. According to the table, a 5.5% reduction in wind speed results in a decrease of 0.086 in ΔP
SS and 0.092 in
. Conversely, a 5.9% increase in wind speed leads to an increase of 0.086 in both
and
. These variations indicate a substantial deviation in output power, which, given the observed discrepancies, could present significant challenges for power grid operation and planning. From a sustainability perspective, such fluctuations in wind turbine output due to cyberattacks may undermine the reliability of renewable energy’s integration into the grid, potentially necessitating greater reliance on less sustainable energy sources to maintain grid stability.
6.2. FDI on Pitch Angle Controller Data
Pitch control is a fundamental feature of wind turbines, facilitating precise adjustments to blade angles to optimize aerodynamic efficiency. By regulating the pitch angle, the turbine governs the interaction between the wind and the blades, directly affecting both power generation and aerodynamic forces. At wind speeds exceeding the rated limit, pitch angle adjustments are implemented to curtail power production and prevent mechanical overload, while at lower wind speeds, they are optimized to maximize power capture. This mechanism is essential for maintaining optimal blade angles to achieve the desired rotor speeds and power output, thereby ensuring efficient operation. However, the pitch angle is vulnerable to FDI attacks, which can compromise turbine performance. Two distinct scenarios are analyzed in this context:
- i.
FDI with a value lower than the actual pitch angle (Actual Data, AD);
- ii.
FDI with a value higher than the actual pitch angle (Actual Data, AD).
These scenarios will be explored in detail in the subsequent subsection.
Figure 8 illustrates the wind speed profile applied to the wind turbine in this section. As depicted in the figure, the initial wind speed is 10.5 m/s, which subsequently rises to 11.5 m/s. Given that the nominal wind speed is 11 m/s, the wind speed exceeds this threshold after 2 s. Consequently, the turbine’s pitch control mechanism is activated at this point to regulate power output and maintain operational stability. From a sustainability perspective, the integrity of pitch control is critical for ensuring consistent renewable energy production; FDI attacks that disrupt this mechanism can lead to inefficiencies, reducing the turbine’s contribution to sustainable energy goals and potentially increasing reliance on less environmentally friendly energy sources. The vulnerability of pitch control to FDI attacks underscores the need for robust cybersecurity measures in wind turbine systems. Such attacks not only disrupt the turbine’s ability to maintain optimal power output but also pose a risk to the structural integrity of the blades due to improper aerodynamic loading. This can result in increased maintenance costs and downtime, further diminishing the turbine’s operational efficiency. From a sustainability standpoint, ensuring the resilience of pitch control mechanisms against cyber threats is paramount, as any reduction in wind turbine reliability can hinder the transition to a low-carbon energy future, potentially delaying progress toward meeting global renewable energy targets and climate change mitigation goals.
6.2.1. First Scenario (θFDI < θAD)
As established in this section, at t = 2 s, the wind speed increases, necessitating a real-time adjustment in the wind turbine’s pitch angle to maintain operational stability. However, at t = 4 s, a cyberattack is initiated, targeting the pitch angle data and reducing its value by 20%. This modification in the blade angle data is depicted in
Figure 9a. Consequently, this reduction causes the wind turbine’s output power to deviate from its expected value at specific intervals, as shown in
Figure 9b. The resulting power deviation, which manifests as a significant discrepancy (less than 0.04 per unit), is further elucidated in
Figure 9c.
The cyberattack on the pitch angle data not only affects the turbine’s power output but also introduces aerodynamic imbalances that can lead to increased mechanical stress on the blades. As the pitch angle is reduced below its optimal value, the blades experience excessive lift forces, potentially causing vibrations and fatigue in the turbine’s structural components. This is particularly concerning for long-term operation, as prolonged exposure to such conditions may accelerate wear and tear, necessitating more frequent maintenance and repairs. From a sustainability perspective, the increased maintenance demands and potential for unexpected downtime can reduce the overall lifecycle efficiency of the wind turbine, thereby diminishing its contribution to sustainable energy production and increasing the environmental footprint associated with repair activities.
Furthermore, the deviation in power output caused by the FDI attack has broader implications for grid integration and stability. Wind turbines are often critical components of renewable energy grids, where their output must be carefully balanced with demand to ensure reliable power delivery. A 0.04 per unit deviation, though seemingly small, can accumulate across multiple turbines in a wind farm, leading to significant mismatches in power supply and demand. This can strain grid operations, potentially requiring compensatory measures such as activating reserve power from fossil fuel-based plants. Such reliance on non-renewable energy sources to mitigate the effects of cyberattacks undermines the sustainability goals of transitioning to a cleaner energy mix, highlighting the urgent need for enhanced cybersecurity protocols in renewable energy systems.
To address these challenges, future research should focus on developing advanced detection and mitigation strategies for FDI attacks on wind turbine pitch control systems. Machine learning-based anomaly detection algorithms, for instance, could be employed to identify deviations in pitch angle data in real time, enabling rapid responses to potential cyberattacks. Additionally, integrating redundant control systems or fallback mechanisms could help maintain turbine stability during an attack, minimizing disruptions to power output. From a sustainability standpoint, bolstering the resilience of wind turbines against cyber threats not only ensures consistent renewable energy production but also supports the long-term viability of wind energy as a cornerstone of global efforts to achieve carbon neutrality and combat climate change.
6.2.2. Second Scenario (θFDI > θAD)
As demonstrated in this section, at t = 2 s, an increase in wind speed necessitates a real-time adjustment in the wind turbine’s blade angle to optimize aerodynamic performance. However, at t = 4 s, a cyberattack is initiated, targeting the blade angle data and artificially increasing its value by 20%. This alteration in the blade angle data is depicted in
Figure 10a. This increase causes the wind turbine’s output power to deviate from its expected value at specific intervals, as shown in
Figure 10b. The resulting deviation in output power, which manifests as a significant discrepancy (less than 0.04 per unit), is further elucidated in
Figure 10c. From a sustainability perspective, such deviations in power output due to FDI attacks can compromise the reliability of wind energy systems, potentially reducing their contribution to sustainable energy production and necessitating greater reliance on less environmentally sustainable energy sources to meet grid demands.
6.2.3. Discussion on Pitch Angle Controller Data Attacking
This section provides a detailed summary of the results derived from the cyberattack targeting the pitch angle data, as presented in
Table 4. According to the table, a 20% decrease in the blade angle, which corresponded to a reduction in the pitch angle below its optimal value, did not impact the steady-state power output P
SS but resulted in a 0.039 increase in
, representing the deviation in the maximum power output from its expected value. Conversely, a 20% increase in the pitch angle, which indicates an over-adjustment of the blade angle, similarly had no effect on the P
SS value but led to a 0.034 decrease in
, reflecting a reduction in the maximum power output deviation. These changes signify a relatively minor deviation in the wind turbine’s overall output power, suggesting that while the cyberattack affects the turbine’s performance, the impact on steady-state operation remains limited. However, even small deviations can accumulate over time, potentially affecting grid reliability. From a sustainability perspective, such fluctuations in power output due to FDI attacks on pitch angle data can undermine the consistency of renewable energy generation, posing challenges to the reliability of wind energy as a sustainable power source and potentially increasing dependence on less environmentally friendly energy alternatives to stabilize the grid.
6.3. FDI on Rotational Speed Controller Data
The rotational speed of a wind turbine is susceptible to FDI attacks, which can disrupt the turbine’s ability to maintain optimal performance. In this context, two distinct scenarios are analyzed:
- i.
FDI with a value lower than the actual rotational speed (Actual Data, AD), which may cause the turbine to operate below its optimal efficiency, and
- ii.
FDI with a value higher than the actual rotational speed (Actual Data, AD), potentially leading to excessive mechanical stress on the rotor.
These scenarios will be explored in detail in the subsequent subsection, providing a comprehensive understanding of their impacts on turbine operation.
Figure 11 depicts the wind speed profile applied to the wind turbine in this section. As indicated in the figure, the wind speed remains constant at 9 m/s, serving as the baseline condition for evaluating the effects of the FDI attacks on rotational speed. From a sustainability perspective, FDI attacks targeting rotational speed can compromise the efficiency and reliability of wind energy generation, potentially reducing turbines’ contribution to renewable energy production and necessitating increased reliance on less sustainable energy sources to meet grid demands.
The susceptibility of rotational speed to FDI attacks highlights the critical need for robust monitoring systems to detect and mitigate such cyber threats in real time. An FDI attack that manipulates rotational speed data can lead to improper control actions, such as the over-speeding or under-speeding of the rotor, which may not only reduce power generation efficiency but also cause long-term damage to the turbine’s mechanical components, including the gearbox and bearings. This could result in increased operational costs and unplanned downtime, further exacerbating the economic and environmental challenges associated with wind energy production. From a sustainability perspective, ensuring the integrity of rotational speed data is vital for maintaining the reliability of wind turbines as a renewable energy source, as any disruption can hinder their role in reducing carbon emissions and supporting global efforts toward a more sustainable energy future.
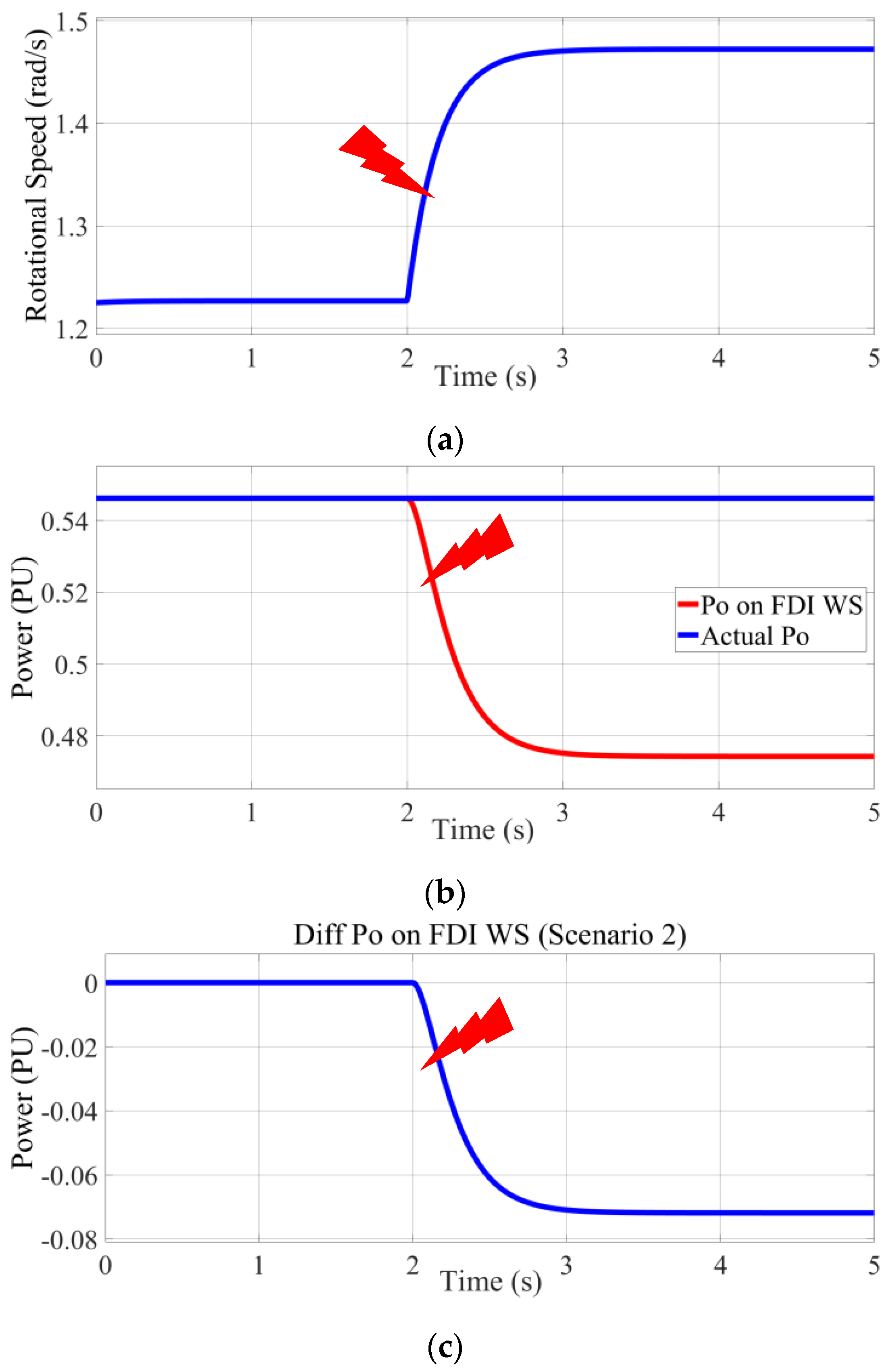
6.3.1. First Scenarios (ωFDI < ωAD)
As detailed in this section, at t = 2 s, a cyberattack is initiated, targeting the rotational speed data and reducing its value by 20%. This manipulation of the rotational speed data, which disrupts the turbine’s ability to maintain optimal rotor performance, is depicted in
Figure 12a. As a result of this decrease, the wind turbine’s output power deviates from its expected value, leading to a noticeable reduction at specific intervals due to the diminished rotor speed’s impact on power generation, as shown in
Figure 12b. The resulting discrepancy in output power, which manifests as a significant deviation (less than 0.08 per unit) and indicates a substantial impact on the turbine’s performance, is further elucidated in
Figure 12c. From a sustainability perspective, such reductions in output power due to FDI attacks on rotational speed can undermine the reliability of wind energy systems, potentially decreasing their contribution to renewable energy production and necessitating greater reliance on less sustainable energy sources to fulfill grid requirements.
The reduction in rotational speed due to the FDI attack not only impacts the wind turbine’s power output but also introduces potential risks to its mechanical integrity. A 20% decrease in rotational speed can lead to suboptimal operation of the rotor, causing the turbine to operate outside its designed efficiency range. This may result in increased mechanical torque fluctuations, which can place additional stress on the drivetrain components, such as the gearbox and shaft, potentially leading to accelerated wear and a higher likelihood of mechanical failure over time. Such mechanical issues can necessitate costly repairs and extended downtime, which in turn reduce the turbine’s availability for power generation. From a sustainability perspective, the increased maintenance requirements and downtime associated with these mechanical stresses can diminish the overall environmental benefits of wind energy, as the energy and resources required for repairs may offset the turbine’s contribution to reducing carbon emissions.
Moreover, the deviation in output power caused by the FDI attack on rotational speed data has significant implications for grid stability and energy management. A deviation of less than 0.08 per unit, while seemingly minor, can have a cumulative effect when multiple turbines in a wind farm are affected, leading to a mismatch between the expected and actual power supplied to the grid. This mismatch can challenge grid operators, who may need to compensate by activating backup power sources, often from non-renewable origins such as coal or gas plants, to maintain grid reliability. Such compensatory measures undermine the sustainability goals of relying on renewable energy sources like wind power to reduce greenhouse gas emissions. Consequently, this highlights the critical need for advanced cybersecurity measures, such as real-time intrusion detection systems, to protect wind turbine control systems from FDI attacks and ensure the consistent delivery of clean energy to the grid.
6.3.2. Second Scenarios (ωFDI > ωAD)
As elucidated in this section, at t = 2 s, a cyberattack is initiated, targeting the rotational speed data and inducing an artificial increase of 20%. This manipulation of the rotational speed data, which disrupts the turbine’s ability to maintain its designed operational parameters, is depicted in
Figure 13a. Consequently, this increases in rotational speed leads to a reduction in the wind turbine’s output power at specific intervals, primarily because the elevated speed causes the turbine to operate beyond its optimal efficiency range, resulting in aerodynamic inefficiencies and a subsequent drop in power generation, as shown in
Figure 13b. The resulting power discrepancy, which manifests as a significant deviation (less than 0.08 per unit) and indicates a notable impact on the turbine’s performance under these conditions, is further illustrated in
Figure 13c. From a sustainability perspective, such reductions in output power due to FDI attacks on rotational speed can jeopardize the reliability of wind energy systems, potentially diminishing their role in sustainable energy production and necessitating increased reliance on less environmentally sustainable energy sources to meet grid demands, thereby undermining efforts to reduce carbon emissions.
6.3.3. Discussion on Rotational Speed Controller Data Attacking
This section provides a comprehensive summary of the results derived from the cyberattack targeting the rotational speed data, as detailed in
Table 5. As indicated in the table, a 20% decrease in rotational speed, which simulates an FDI attack that underestimates the rotor’s actual speed, leads to a 0.077 decrease per unit in the steady-state power output
, reflecting a reduction in the turbine’s ability to generate power consistently, as well as a 0.077 decrease in
, indicating a corresponding reduction in the maximum power output deviation from its expected value. Similarly, a 20% increase in rotational speed, representing an FDI attack that overestimates the rotor’s speed and potentially causes the turbine to operate beyond its optimal range, results in a 0.072 per unit decrease in the
value, signifying a loss in steady-state power generation, and a 0.072 decrease in
, highlighting a consistent reduction in the maximum power output deviation. These changes signify a relatively significant deviation in the wind turbine’s overall output power, which can disrupt the expected power delivery to the grid and, consequently, present substantial challenges for network planners and operators in maintaining grid stability and reliability. From a sustainability perspective, such deviations in power output due to FDI attacks on rotational speed can undermine the reliability of wind energy as a renewable resource, potentially reducing its contribution to sustainable energy production and necessitating increased reliance on less environmentally sustainable energy sources to ensure grid stability, thereby hindering progress toward carbon emission reduction goals.
6.4. Discussion on FDI
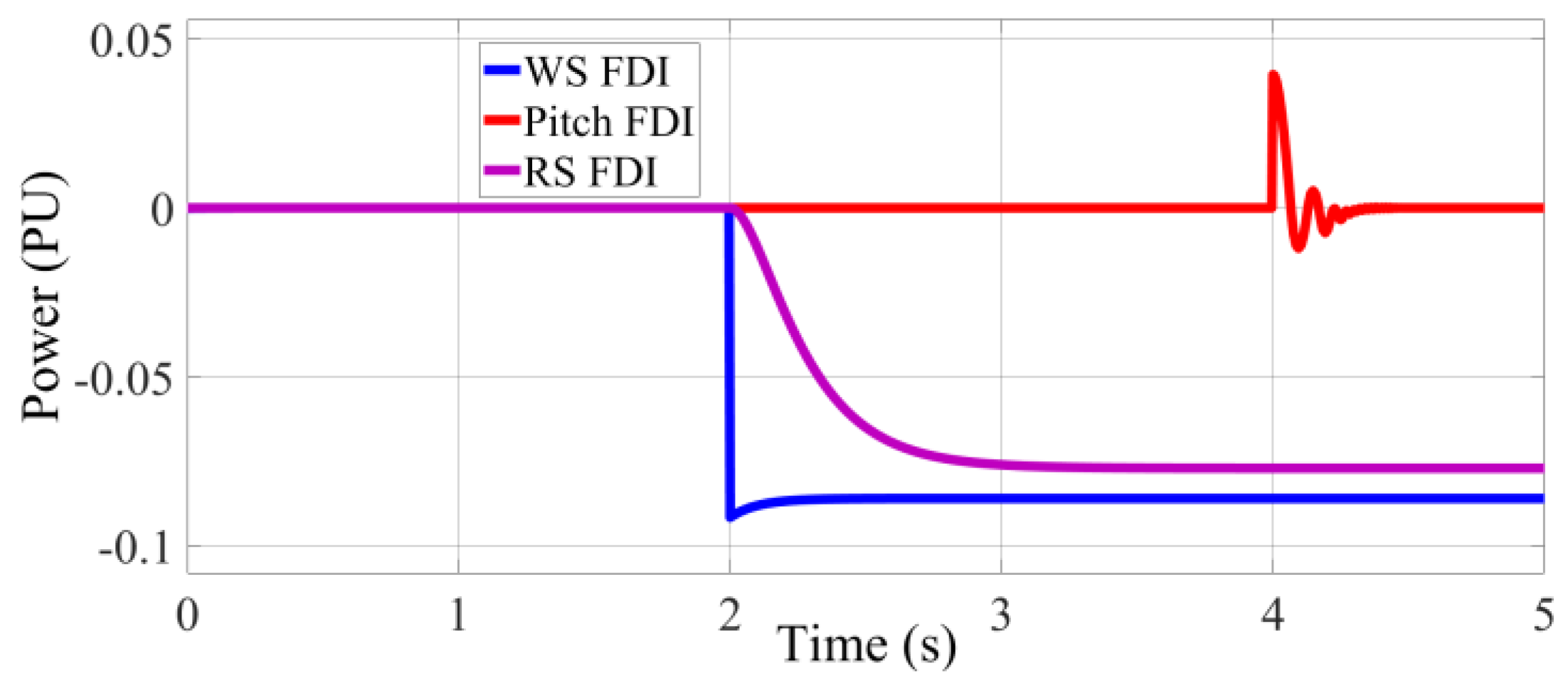
The comprehensive investigation into FDI attacks on wind turbine systems, targeting Wind Speed (WS), Rotational Speed (RS), and pitch angle (Pitch), reveals their varying impacts on power output, as summarized by a comparative analysis and temporal dynamics in
Figure 14 over a 5 s timeframe. WS FDI, with manipulations of 5% to 6%, exerts the most significant effect, causing a sustained power deviation of up to −0.1 PU from t = 2 s to t = 4 s, resulting in up to a 9% output reduction due to its direct influence on aerodynamic torque; RS FDI, with a 20% change, induces a consistent −0.05 PU deviation (~7.5% impact), reflecting a steady-state error that affects turbine dynamics and grid reliability; and Pitch FDI, also at 20%, shows the least significant impact with deviations under 4%, exhibiting a transient −0.05 PU spike at t = 4 s before rapid recovery, highlighting the pitch control system’s resilience despite instantaneous modeling.
This impact hierarchy—WS FDI > RS FDI > Pitch FDI—stems from WS’s foundational role in power generation, RS’s effect on operational efficiency, and Pitch’s fine-tuning function, with
Figure 13 illustrating prolonged disruptions from WS FDI, steady errors from RS FDI, and transient effects from Pitch FDI, each challenging turbine performance and grid integration. Research gaps persist, including topics such as the effects of combined FDI attacks, long-term consequences like mechanical fatigue and energy losses, the influence of attack timing, and generalizability across turbine designs, necessitating future studies on adaptive controls, advanced detection, and environmental interactions to bolster resilience. From a sustainability perspective, FDI attacks threaten wind energy reliability, with WS FDI’s sustained reductions risking significant energy shortfalls, RS FDI’s errors increasing maintenance needs, and Pitch FDI’s transient disruptions potentially destabilizing grids at scale, all of which may lead to increased fossil fuel reliance, undermining carbon reduction goals; this underscores the critical need for robust cybersecurity measures, such as real-time anomaly detection and secure data protocols, to safeguard wind turbine operations, ensure consistent renewable energy production, and support the global transition to a sustainable, low-carbon energy future while maintaining public trust in clean energy technologies.
Several state-of-the-art strategies have been proposed for detecting and mitigating FDI attacks on renewable energy systems. For instance, Mazare et al. [
2] employed a reinforcement learning-based control strategy with adaptive neural networks to enhance resilience, while Zhao et al. [
3] introduced an observer-based adaptive resilient control method to detect intrusions in rotor speed. Compared to these approaches, our method uniquely integrates real-time cyberattack detection within the control loops of pitch angle and rotational speed, offering a simulation-driven analysis that aligns closely with turbine dynamics.
Moreover, unlike previous techniques that primarily focus on stability restoration, our framework incorporates sustainability-oriented metrics such as carbon emission reduction and energy efficiency, offering a multi-dimensional evaluation of impact and mitigation. While our model does not currently provide a quantitative performance comparison with these strategies due to different system configurations and implementation tools (e.g., MATLAB vs. Python-based reinforcement learning), future studies will aim to integrate standard benchmarks and datasets to quantitatively evaluate detection accuracy, false positive rates, and computational efficiency.
This comparative perspective highlights the practical relevance of our approach, particularly in scenarios where sustainability and cyber resilience are jointly prioritized.
7. Conclusions
This investigation into FDI attacks on variable-speed wind turbines underscores the susceptibility of renewable energy infrastructure to cyber threats, offering critical insights for system operators and engineers. The research reveals that a modest 5–6% manipulation of wind speed data triggers a substantial shift in turbine output power, with a deviation of around 0.092, highlighting wind speed as the most sensitive parameter in this context. In comparison, a more significant 20% alteration in pitch angle yields a smaller power output change of 0.039, while a 20% tweak in generator rotational speed results in a 0.077 deviation. These disparities suggest that attackers targeting wind speed inputs can disproportionately disrupt turbine performance, potentially destabilizing grid reliability. The findings stress the urgency of implementing advanced cybersecurity protocols, such as anomaly detection and data validation mechanisms, to safeguard wind energy systems. By prioritizing protection against wind speed manipulation, operators can enhance resilience, ensuring consistent power delivery and reinforcing the integrity of renewable energy contributions to the grid. This is particularly vital for sustainability, as wind power remains a cornerstone of efforts to reduce carbon emissions globally. A breach that harmed in turbine efficiency could undermine trust in renewable solutions, slowing the transition from fossil fuels. Sustainable energy systems demand not just physical durability but also digital fortitude to maintain their environmental promise. Strengthening cybersecurity in wind turbines thus supports long-term ecological goals, preserving the planet for future generations while meeting current energy needs.
It is also worth noting that while our analysis demonstrates the impact of FDI attacks on wind turbine power output, the assessment of their consequences on power grid stability remains qualitative in this study. In actual power systems, grid stability is measured through key indicators such as frequency deviation, voltage fluctuation, and load-generation imbalance. Such an analysis would enable a more comprehensive understanding of the cascading impacts of cyberattacks on renewable-integrated smart grids and offer valuable insights for designing coordinated mitigation strategies at both local (turbine) and global (grid) levels.
Looking ahead, future studies should expand on these results by exploring a broader range of attack scenarios and turbine configurations to better understand the full scope of FDI vulnerabilities. Investigating hybrid attack strategies—combining wind speed, pitch angle, and rotational speed manipulations—could reveal compounding effects not captured in this study. Future work should incorporate random wind speed profiles to evaluate the resilience of detection and mitigation strategies under turbulent and unpredictable atmospheric conditions, thereby enhancing the real-world relevance of the proposed framework. To enhance the cybersecurity of VSWTs, this study suggests exploring mitigation strategies such as machine learning-based intrusion detection and blockchain-secured data streams, which offer practical solutions for real-world deployment. However, limitations exist. The analysis focuses on a single-turbine model, potentially overlooking the diversity of operational wind energy systems. It also assumes ideal conditions, neglecting environmental factors like turbulence or equipment wear, which may influence the impact of FDI attacks. Future research should address these gaps by expanding the sample size, incorporating real-time field data, and simulating long-term attack scenarios to develop a more robust framework for securing wind turbines against evolving cyber threats. From a sustainability perspective, this research underscores the importance of resilient cybersecurity to maintain wind power’s role in reducing greenhouse gas emissions. Unaddressed cyber vulnerabilities could undermine the economic and environmental benefits of wind energy, hindering progress toward net-zero targets. Future work should investigate how advanced safeguards improve resource efficiency, minimizing waste in energy production. By aligning technological protections with sustainable outcomes, such efforts can strengthen wind power’s contribution to a low-carbon future, ensuring operational reliability and environmental integrity in increasingly interconnected energy systems. These advancements will guide policymakers and industry in fortifying renewable energy infrastructure.
In future studies, it is recommended to utilize high-fidelity aeroelastic simulators such as Open FAST to more accurately replicate real-world wind turbine behavior and validate FDI mitigation strategies for realistic operational dynamics. Also, future studies are encouraged to incorporate region-specific meteorological data and terrain-dependent wind modeling to enhance the environmental realism of the simulation framework and evaluate the performance of FDI detection strategies under more diverse and complex operating conditions. In Addition, future research should explore the integration of hybrid detection frameworks that differentiate between parameter deviations caused by FDI attacks and those originating from internal faults such as sensor drift or actuator malfunction. Statistical residual analysis, machine learning classifiers, and model-based diagnostic approaches can be leveraged to enhance the reliability and interpretability of anomaly detection in networked wind energy systems.