Future Rail Signaling: Cyber and Energy Resilience Through AI Interoperability
Abstract
1. Introduction
- Integrated resilience model: The authors propose a unified AI model that has the functionality of simultaneously solving problems of forming technological resilience and detecting cyber-attacks in the signaling infrastructure. This synergistic approach provides a broader coverage than traditional studies, which study the problems of cyber and energy resilience in isolation.
- Modeling in an approximate operational environment: The effectiveness of the model is confirmed by validation under conditions that best demonstrate real operation—a double-track railway line with high intensity, variable traffic parameters and a simulated digital threat staged according to a predetermined schedule. AI demonstrates the potential to maintain functional compatibility with signaling processes and provide early warning of potential cyber-attacks.
- Functional conclusions: The authors formulate which initial parameters have the greatest impact on signaling resilience, and analyze the optimal balance between model complexity and performance. The obtained results provide practical guidance for railway infrastructure stakeholders (railway system operators) on how to implement AI to improve signaling resilience and security.
2. A Literature Review Regarding the Energy and Cybernetic Sustainability of Railway Signaling Systems
- The first stage: Selection of a railway line designated for technology implementation, collection of detailed information about the rolling stock intended for use, and preparation of a train control scheme based on AI technologies;
- The second stage: Implementation of the testing process and experiments on the operability, reliability and sustainability of the new technology, in experimental conditions, on the test section of the railway track;
- The third stage: Application of AI on an existing railway line [3].
- Resilience: This indicator analyses the ability to perform the conditioned function of the signaling without errors in the specified period and at a given position. The position is determined by the operating mode, load scale and environmental conditions.
- Reachability: A parameter that represents the option to provide a given functionality at a specified time and position. Reachability demonstrates the frequency of failures and the possible consequences of each error.
- Serviceability: A parameter that examines the ability to carry out maintenance on time and universally. The service complex includes inspection, analysis, detection of malfunctions and modification of devices.
- Safety: A criterion that gives an understanding of protection from harm to nature and humans. This category includes the analysis of possible emergency situations and associated dangers due to device errors [5].
- Internal safety of signaling devices refers to their inherent inability to be influenced by erroneous or non-standard computational conditions that could disrupt the execution sequence within strategies aimed at preventing transitions to critical states.
- External, fragmentary safety of signaling equipment is designated as the functionality of the equipment to parry certain disorganizing circumstances that can be detected by a machine.
- Network segmentation: This step involves counteracting possible non-standard situations. This concept is aimed at preventing the lateral movement of people who threaten the digital security of railways between multiple elements of the virtual infrastructure.
- The implementation of improved network security protocols, such as MQTT, which uses TLS encryption.
- The implementation of firewalls and intrusion detection technologies at key intersections of the digital security infrastructure.
- Modules for collecting and processing fault data (implemented on switching activity, and also cover several analog values for determining the relay starting current);
- A database coordination module (based on the functionality of storing fault data, information on transportation and processing operations);
- An expert module for error inspection (designed on Prolog software, the purpose of the module is to evaluate and diagnose damage indicators).
3. Aspects and Requirements for the Interoperability of Railway Signalization with AI, Taking into Account EU Standards
4. Methodology for Studying the Interoperability of AI in the Signaling Infrastructure of Railway Transport. Cyber- and Energy Resilience of Railway Signaling
- A comprehensively designed AI model can optimize and strengthen the energy resilience and cyber-resilience of railway signaling systems;
- Increasing the resilience of the signaling infrastructure by introducing AI will have an increasing effect on other components of the railway infrastructure (in accordance with the strategic guidelines for railway transport).
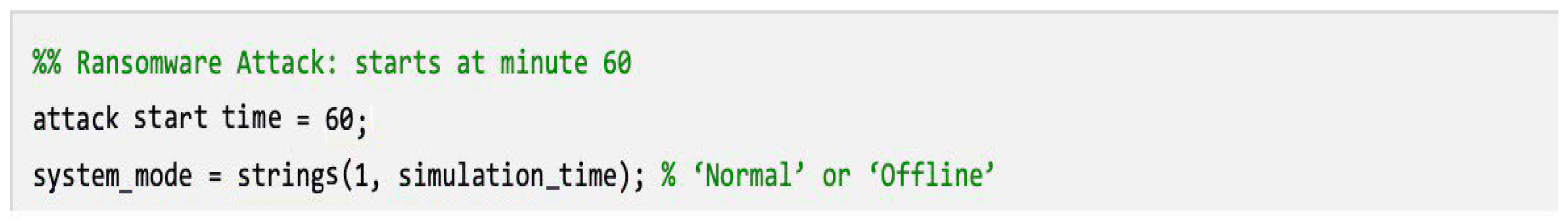
- Design of the threat identification algorithm: Initially, AI algorithms were proposed to facilitate the implementation of the detection of cyber threats (ransomware attacks) in the alarm infrastructure.
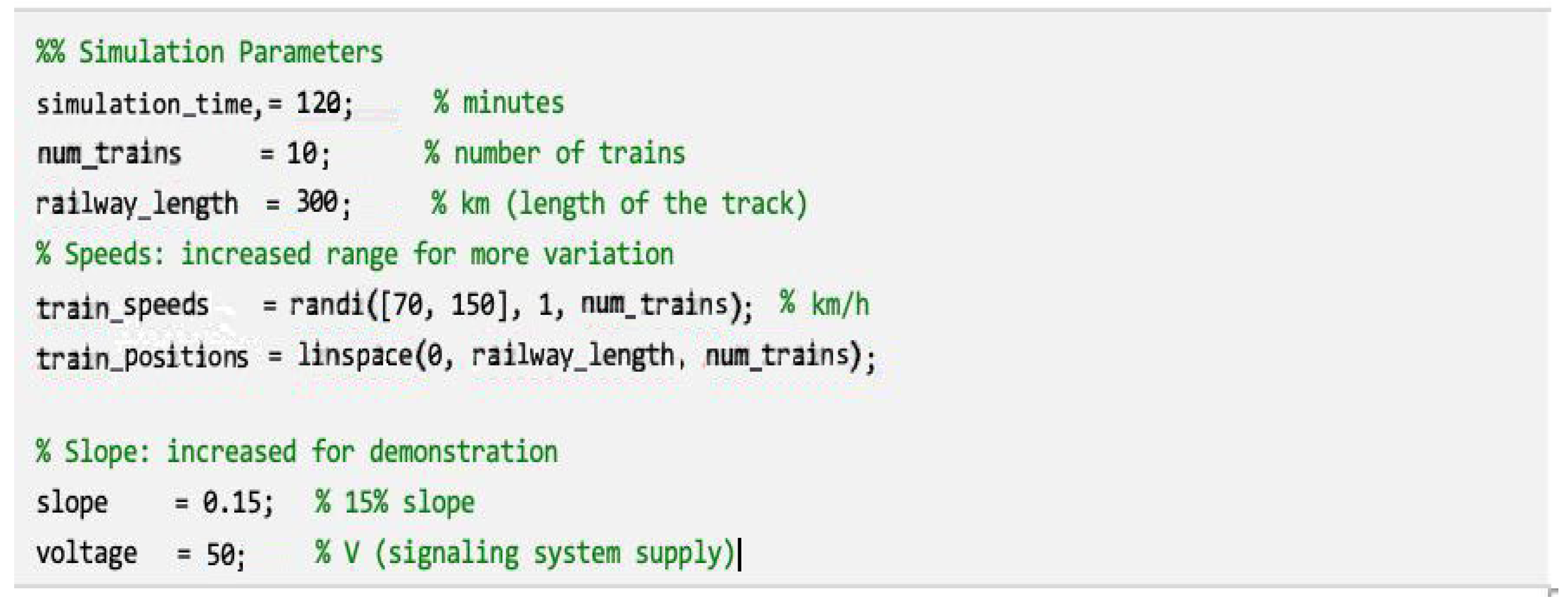
- Design of the simulation model: A simulation environment of the alarm system in the operating and offline mode provoked by the ransomware was implemented. The simulation was based on realistic characteristics, such as the supply voltage of the paths (50 V) and the cyber-attack scenario.
- Training the model with subsequent validation of the results: By applying the simulation data, the authors trained the neural network to generate predictive estimates of key parameters (energy stability and cyber-attack status) and performed its adaptation, comparing the output values of the model with the real simulation results.
- Scenario model of independent operation: The operation of the signaling equipment was tested in autonomous mode with an active AI model, in conditions of the presence of several trains on the line for scaling to operational traffic conditions.
- energy_consumption;
- cyber_threat_detected.
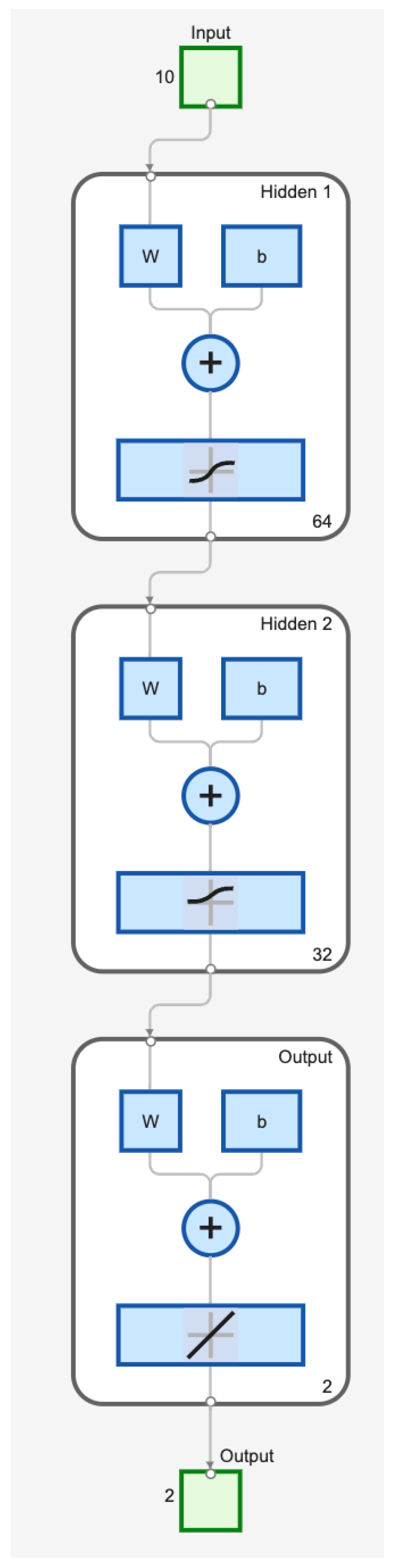
- The input layer consists of 10 features (train speed, their location, slope, voltage, energy consumption, anomalies, etc.).
- The hidden layers are represented by 64 and 32 neutrons, respectively. The structure under consideration initially provides a wide range of connections, and then filters out less significant ones.
- The output layer is presented by two neutrons—one predicts energy sustainability, and the second predicts cyber sustainability (anomaly monitoring).
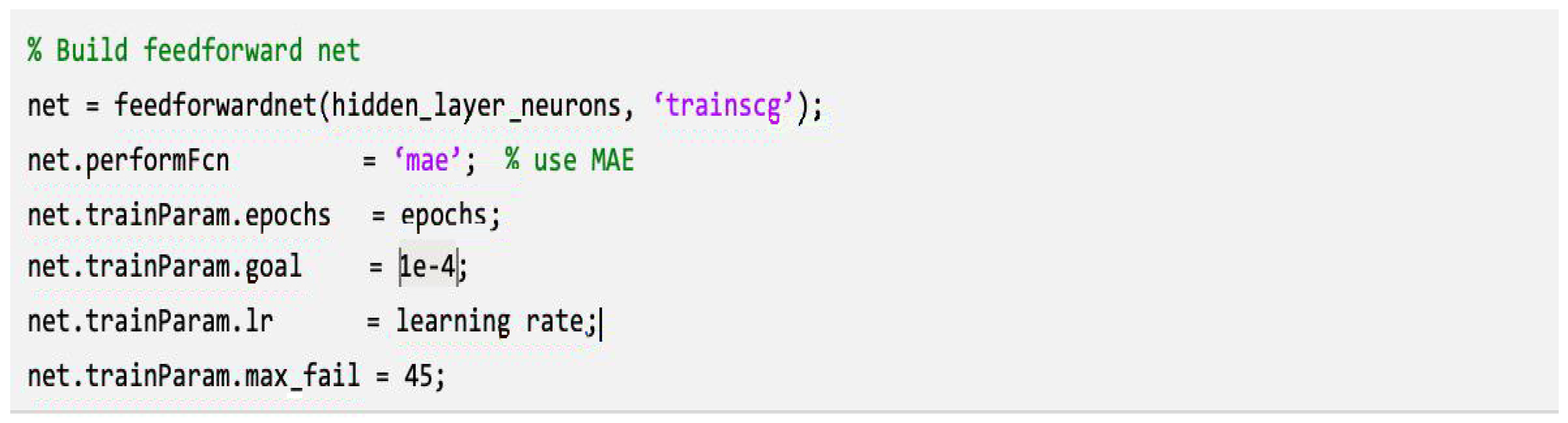
- Network training involved a maximum of 500 epochs, since this was a safe limit in the simulation. The hardware configuration on which the script was played was on an Intel Core i3-4160 processor (3.60 GHz, 2 cores/4 threads, 8 GB RAM (Random-access memory)). A series of runs from 100 to 1000 epochs revealed that starting from the 450th epoch, the validation MAE stabilized. After 550 epochs, the validation error began to increase, and therefore, 500 epochs was the upper limit, at which point the model demonstrated stable generalizing behavior and provided an optimal balance between the quality of the model and practical feasibility. Computing resources at 500 epochs reached 11 min of training; if the simulation was reproduced at 1000 epochs, then the training increased to 24 min and the RAM consumption increased from 2 GB to 4 GB. With a configuration with 8 GB of RAM with this number of cycles, “Out of memory” was recorded.
- A learning rate of 0.005 was selected based on the results of a series of tests. With smaller parameters, the model training did not meet the set accuracy threshold for 500 epochs; with larger values, error fluctuations and an increase in RAM consumption were recorded. Therefore, the specified value of 0.005 guaranteed stable convergence of the SCG algorithm and allowed the MAE to reach 0.033 in 11 min.
- -
- MAE calculates the mean absolute error between the forecast and the truth, and the scale of the results is interpreted directly (the same units as the goal);
- -
- MAE is less sensitive to rare outliers than MSE (mean squared error), which is advisable in the case of probable bursts in data (in our case, during cyber-attacks).
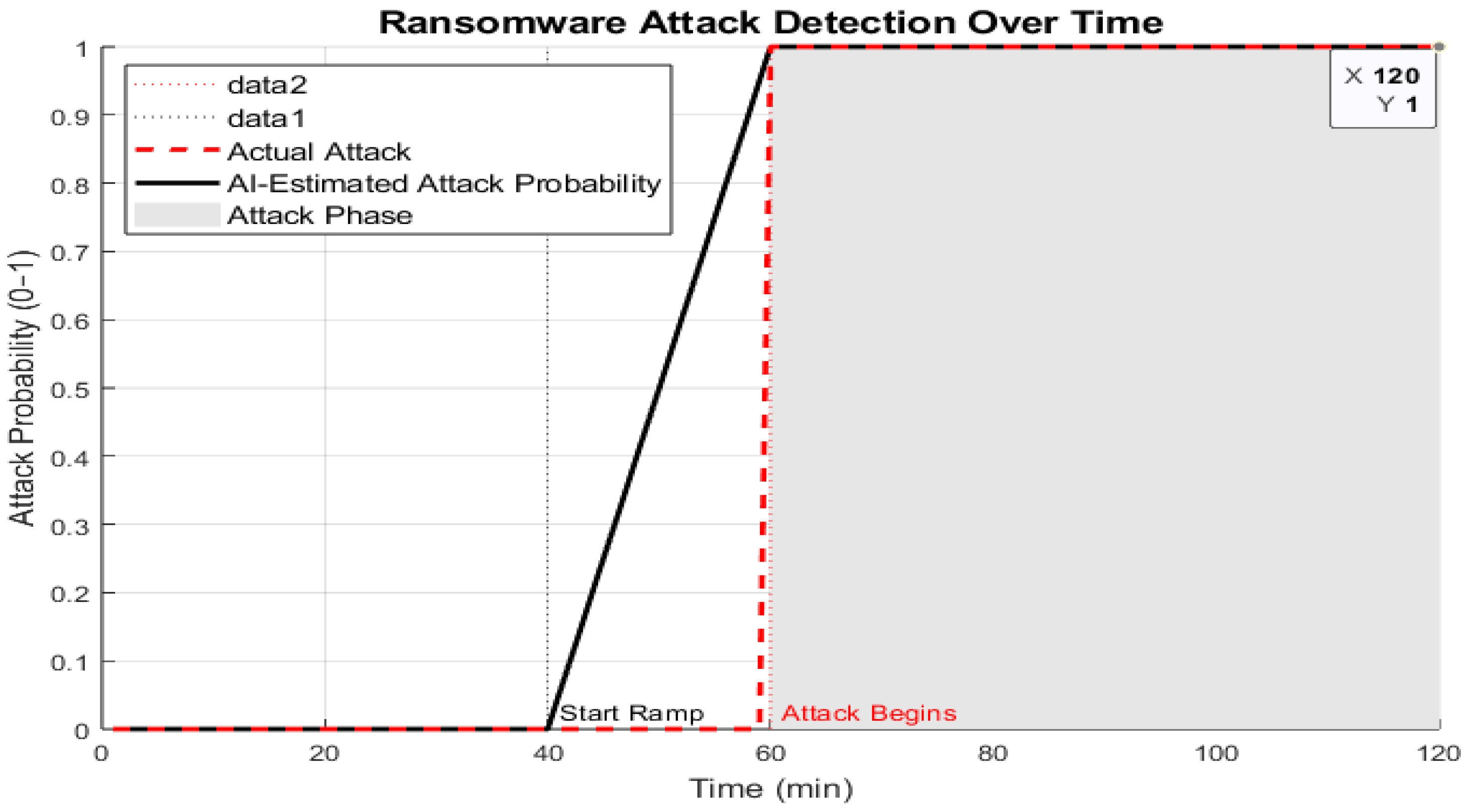
- A surge in port scanning;
- An increase in Heart-Beat packet delays in the service network;
- Single packets with an erroneous CRC (cyclic redundancy code).
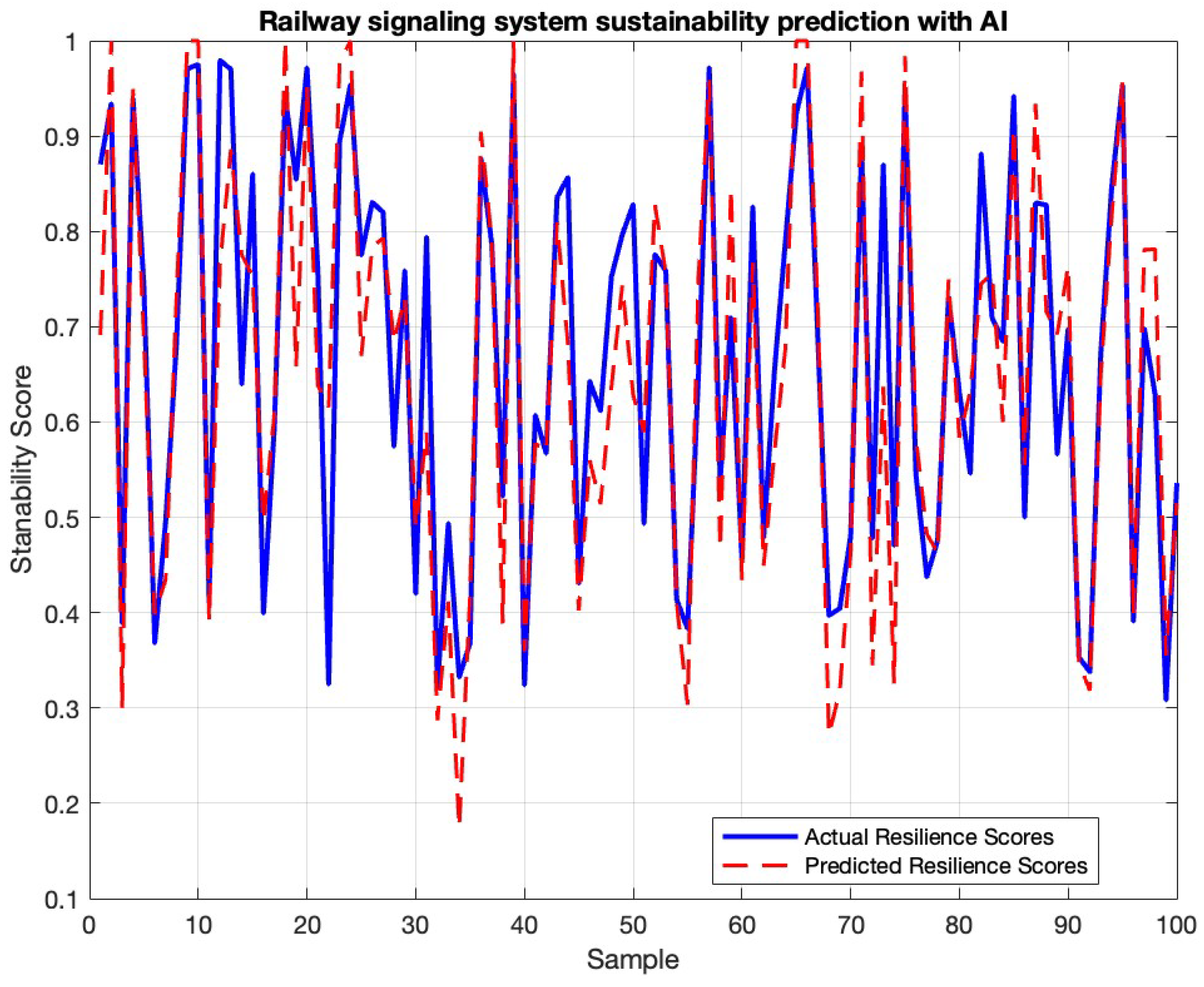
- A high trend coincidence rate: For almost every peak and trough, the red dotted line follows the blue solid line, with minimal fluctuations. This is confirmed by the indicators MAE = 0.0331 and R2 ≈ 0.94 (the determination coefficient, indicating that the neural network explains about 94% of the spread of real stability values, and confirming that the model correctly tracks the dynamics of the system).
- The boundaries of level 0–1 are identically recreated: Within the range close to 1.0 according to actual data, the forecast also approaches 1. In the range where empirical “failure” occurs, 0.25–0.30, the model goes down to almost the same depth.
- Local discrepancies ≤ 0.10: Large inconsistencies are noted in the zones of sharp jumps in the real metric. Here, the red line reacts with a delay of 1–2 samples, and does not reach the most extreme values, which is typical for one-step predictors without a self-adaptive filter.
- Absence of systematic bias: An equal number of “overflows” of the red curve above/below the blue curve is detected—the system does not systematically overestimate or underestimate stability.
- Stable distribution of “expressiveness/resources”: The use of 64 and 32 hidden neurons provides sufficient nonlinearity, but does not overload the CPU (central processing unit) and RAM.
- Model transparency: The result is only two clearly defined indicators (energy resilience score and cyber-attack), and threshold values (0.5, 0.8) can be set without difficulty and for automatic actions.
- Compliance with legal aspects (EU AI Act): The authors’ model is compact and transparently logged (MAE, weights), which facilitates the audit process of “high-risk” AI.
- Modularity: When new devices appear in the alarm system, it is enough to scale the input layer and retrain the models, since the internal layers are already adapted for feature aggregation.
5. Scientific Discussion Evaluating the Effectiveness, Architecture, and Limitations of the Developed Model
6. Conclusions
- Phased implementation of AI monitoring: It is advisable, from a practical point of view, to introduce the system in the “shadow” mode initially, which will allow for configuration of the model and reduce the likelihood of false positives.
- Investments in sensor upgrades and data integration: The accuracy of the model’s forecasting is associated with a linear dependence on sensors and telemetry. It seems reasonable to equip the infrastructure with additional sensors (voltage, intrusion detection) and combine data from different subsystems into a unified information space.
- Preservation of traditional security components: Given the obvious advantages of AI, it is advisable to preserve established security tools (emergency locks, “red on failure” signals) and use them in interaction with AI.
- Strengthening basic cyber defense: Simultaneously with the implementation of AI, it is envisaged to implement supporting cybersecurity measures: network segmentation, encryption of coordination commands, regular updates and professional training of personnel in cybersecurity.
- Formation of professional competencies and algorithms for personnel actions: Dispatchers must have confirmed competence to interpret the results of AI work and make prompt decisions. The created model must be integrated into current dispatch procedures, taking into account clear algorithms for actions when warnings occur.
- Scalability and additional training of the model: It is recommended to assess the likelihood of scaling and regular retraining of the model with an increase in the volume of data on actual incidents and situations close to emergency situations, and, in addition, to implement continuous validation procedures.
- Digital processing of multiple and highly organized attacks: Designing multi-output and recurrent architectures to classify complex cyber threat and failure patterns;
- Incorporating AI into the digital twin: Designing digital models of signaling infrastructure to safely test complex and abnormal scenarios;
- Formation of standards and regulation: Coordinated actions with rail network regulators to develop industry standards and regulations, including legal liability for decisions made by AI;
- Expanding the functional coverage of application: Reorganization from individual sections to the entire rail network using federated learning to share data and experience between lines without violating privacy.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| AI | Artificial intelligence |
| MATLAB | MATrix LABoratory (proprietary multi-paradigm programming language and numeric computing environment developed by MathWorks) |
| MQTT | Message Queuing Telemetry Transport |
| TLS | Transport Layers Security |
| CPS | Cyber-Physical System |
| CSM | Common Safety Methods |
| TGV | Train à Grande Vitesse (high-speed train) |
| SNCF | Société Nationale des Chemins de fer Français (National Company of French Railways) |
| IoT | Internet of Things |
| MAE | Mean absolute error |
| SCG | Scaled conjugate gradient |
References
- PolsatNews.pl. Nieuprawnione Użycie Sygnału Radio-Stop. Doszło do Kolejnych Incydentów. PolsatNews.pl. Available online: https://www.polsatnews.pl/wiadomosc/2023-08-27/nieuprawnione-uzycie-sygnalu-radio-stop-w-dwoch-wojewodztwach/?ref=aside_najnowsze (accessed on 27 August 2023).
- BBC News. Russian Service. French Railways Sabotaged Hours Before Olympics. Arson Devices Found. (Russian Service. French Railways Sabotaged Hours Before Olympics. Arson Devices Found). Available online: https://www.bbc.com/russian/articles/cx72xpqpqz7o (accessed on 12 February 2025).
- Zhang, M.; Zhang, Q.; Lv, Y.; Sun, W.; Wang, H. An AI based High-speed Railway Automatic Train Operation System Analysis and Design. In Proceedings of the 2018 International Conference on Intelligent Rail Transportation (ICIRT), Singapore, 12–14 December 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Vatakov, V.; Pencheva, E.; Dimitrova, E. Recent Advances in Artificial Intelligence for Improving Railway Operations. In Proceedings of the 30th National Conference with International Participation (TELECOM), Sofia, Bulgaria, 27–28 October 2022; pp. 1–4. [Google Scholar] [CrossRef]
- Wu, C.K.; He, Y.; Tsang, K.F.; Mozar, S. The IDex Case Study on the Safety Measures of AIoT-based Railway Infrastructures. In Proceedings of the 2020 IEEE International Symposium on Product Compliance Engineering-Asia (ISPCE-CN), Chongqing, China, 6–8 November 2020; pp. 1–4. [Google Scholar] [CrossRef]
- Tang, R.; De Donato, L.; Besinović, N.; Flammini, F.; Goverde, R.M.P.; Lin, Z.; Liu, R.; Tang, T.; Vittorini, V.; Wang, Z. A literature review of Artificial Intelligence applications in railway systems. Transp. Res. Part C Emerg. Techn. 2022, 140, 103679. [Google Scholar] [CrossRef]
- Fu, Y. Applications of Artificial Intelligence-Based Communication Systems in Rail Transit. In Proceedings of the 6th International Conference on Internet of Things, Automation and Artificial Intelligence (IoTAAI), Guangzhou, China, 26–28 July 2024; pp. 347–350. [Google Scholar] [CrossRef]
- Efanov, D.V.; Khóroshev, V.V.; Osadchy, G.V. Principles of Safety Signalling and Traffic Control Systems Synthesis on Railways. In Proceedings of the International Conference on Industrial Engineering, Applications and Manufacturing (ICIEAM), Sochi, Russia, 15–19 May 2023; pp. 634–638. [Google Scholar] [CrossRef]
- Hu, J.; Yang, X.; Yang, L. A Novel Diagnosis Scheme against Collusive False Data Injection Attack. Sensors 2023, 23, 5943. [Google Scholar] [CrossRef] [PubMed]
- Cao, L.; Zhao, Y. Research on the Application of AI Technology in Railway Signal Fault Identification System. In Proceedings of the IEEE Interna-tional Conference on Electrical, Automation and Computer Engineering (ICEACE), Changchun, China, 29–31 December 2023; pp. 1332–1336. [Google Scholar] [CrossRef]
- Liu, Z.; Jin, C.; Jin, W.; Lee, J.; Zhang, Z.; Peng, C. Industrial AI Enabled Prognostics for High-speed Railway Systems. In Proceedings of the IEEE International Conference on Prognostics and Health Management (ICPHM), Seattle, WA, USA, 11–13 June 2018; pp. 1–8. [Google Scholar] [CrossRef]
- Skalozub, V.; Zhukovytskyi, I.; Bosyi, D.; Lakhno, V. Usage of Specialized Intellectual and Artificial Intelligence Systems to Improve Railway Transport Technologies. In Using Artificial Intelligence to Solve Transportation Problems. Studies in Systems, Decision and Control; Sładkowski, A., Ed.; Springer: Cham, Switzerland, 2024; pp. 27–122. [Google Scholar] [CrossRef]
- European Parliament. Regulation (EU) 2024/1689 of the European Parliament and of the Council of 13 June 2024 Laying Down Har-Monised Rules on Artificial Intelligence and Amending Regulations (EC) No 300/2008, (EU) No 167/2013, (EU) No 168/2013, (EU) 2018/858, (EU) 2018/1139. EUR-Lex. Available online: https://eur-lex.europa.eu/eli/reg/2024/1689/oj/eng#ntr28-L_202401689EN.000101-E0028 (accessed on 13 June 2024).
- European Parliament. Directive (EU) 2016/797 of the European Parliament and of the Council of 11 May 2016 on the Interoperability of the Rail System Within the European Union (Recast) (Text with EEA Relevance). EUR-Lex. Available online: https://eur-lex.europa.eu/eli/dir/2016/797/oj/eng (accessed on 11 May 2016).
- European Parliament. Directive (EU) 2016/798 of the European Parliament and of the Council of 11 May 2016 on Railway Safety (Recast) (Text with EEA Relevance). R EUR-Lex. Available online: https://eur-lex.europa.eu/eli/dir/2016/798/oj/eng (accessed on 11 May 2016).
- Ren, Q.; Du, J. Harmonizing innovation and regulation: The EU Artificial Intelligence Act in the international trade context. Comp. Comput. Law Secur. Rev. 2024, 54, 106028. [Google Scholar] [CrossRef]
- Liza, F. Challenges of Enforcing Regulations in Artificial Intelligence Act: Analyzing Quantity Requirement in Data and Data Governance. In Proceedings of the 1st International Workshop on Imagining the AI Landscape After the AI Act (In conjunction with the first International Conference on Hybrid Human-Artificial Intelligence), Vrije Universiteit Amsterdam, Amsterdam, The Netherlands, 13 June 2022; pp. 1–10. Available online: https://ceur-ws.org/Vol-3221/IAIL_paper9.pdf (accessed on 9 January 2025).
- Gesmann-Nuissl, D.; Kunitz, S. Auditing of AI in Railway Technology—A European Legal Approach. Digit. Soc. Ethics Socio-Leg. Gov. Digit. Technol. 2022, 1, 17. [Google Scholar] [CrossRef]
- National Institute of Standards and Technology—Cybersecurity Framework Manufacturing Profile (NIST IR 8183). Available online: https://nvlpubs.nist.gov/nistpubs/ir/2017/NIST.IR.8183.pdf (accessed on 20 May 2019).
- Layman, L.; Roden, W. A Controlled Experiment on the Impact of Intrusion Detection False Alarm Rate on Analyst Performance. Impact of IDS False Alarm Rate 2023. Available online: https://repository.uncw.edu/server/api/core/bitstreams/1e6e647a-6785-4e9a-936b-a84479b71f7b/content (accessed on 25 October 2023).
- Gupta, N.; Srivastava, K.; Sharma, A. Reducing False Positive in Intrusion Detection System: A Survey. Int. J. Comput. Sci. Inf. Technol. 2016, 7, 1600–1603. Available online: https://www.ijcsit.com/docs/Volume%207/vol7issue3/ijcsit20160703120.pdf (accessed on 14 May 2025).
- Novikova, E.S.; Golubev, S.A. An Approach to Intrusion Detection Based on Federated Learning; St. Petersburg Federal Research Center of the Russian Academy of Sciences: St. Petersburg, Russia, 2023; Available online: https://cts.etu.ru/assets/files/2023/sbornik/200-203.pdf (accessed on 15 November 2024).

Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Holoborodko, P.; Bazaras, D.; Batarlienė, N. Future Rail Signaling: Cyber and Energy Resilience Through AI Interoperability. Sustainability 2025, 17, 4643. https://doi.org/10.3390/su17104643
Holoborodko P, Bazaras D, Batarlienė N. Future Rail Signaling: Cyber and Energy Resilience Through AI Interoperability. Sustainability. 2025; 17(10):4643. https://doi.org/10.3390/su17104643
Chicago/Turabian StyleHoloborodko, Pavlo, Darius Bazaras, and Nijolė Batarlienė. 2025. "Future Rail Signaling: Cyber and Energy Resilience Through AI Interoperability" Sustainability 17, no. 10: 4643. https://doi.org/10.3390/su17104643
APA StyleHoloborodko, P., Bazaras, D., & Batarlienė, N. (2025). Future Rail Signaling: Cyber and Energy Resilience Through AI Interoperability. Sustainability, 17(10), 4643. https://doi.org/10.3390/su17104643






