Vulnerability and Sustainable Development Strategy of the Power Industry Under Carbon Market Based on Social Network Analysis Perspective
Abstract
1. Introduction
2. Literature Review
2.1. Critical Stakeholders of PICT
2.2. Vulnerabilities of PICT
2.3. Social Network Analysis
3. Materials and Methods
3.1. Research Framework
3.2. PICT Vulnerability Network Establishment
3.2.1. PICT Vulnerability Identification
3.2.2. PICT Vulnerability Network Relationship
3.3. SNA Key Metrics
3.3.1. Network-Level Metrics
3.3.2. Node-Level Metrics
3.3.3. Link-Level Metrics
4. Results
4.1. Overall Network Visualization
4.2. Node Visualization
4.3. Lines Visualization
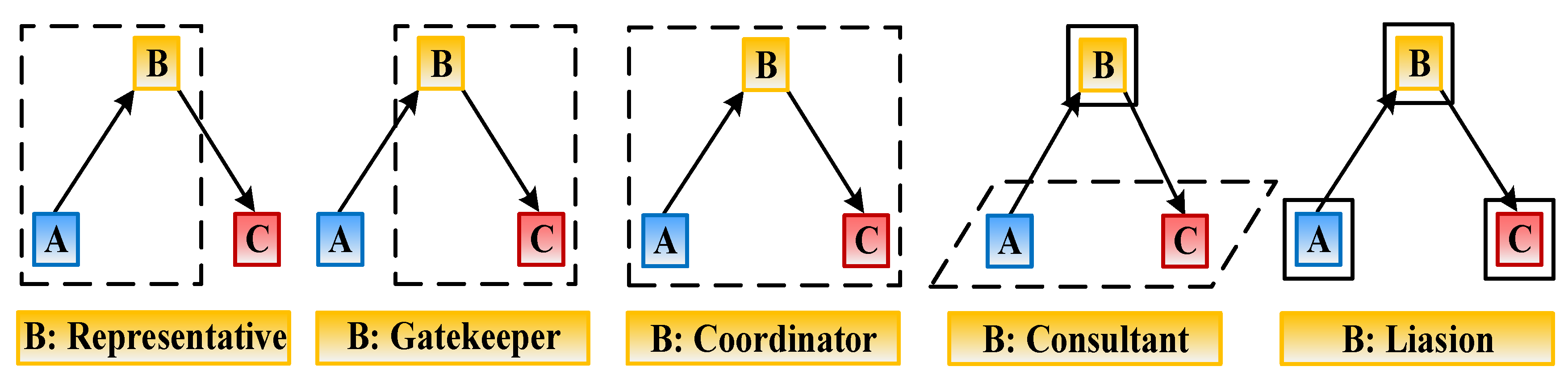
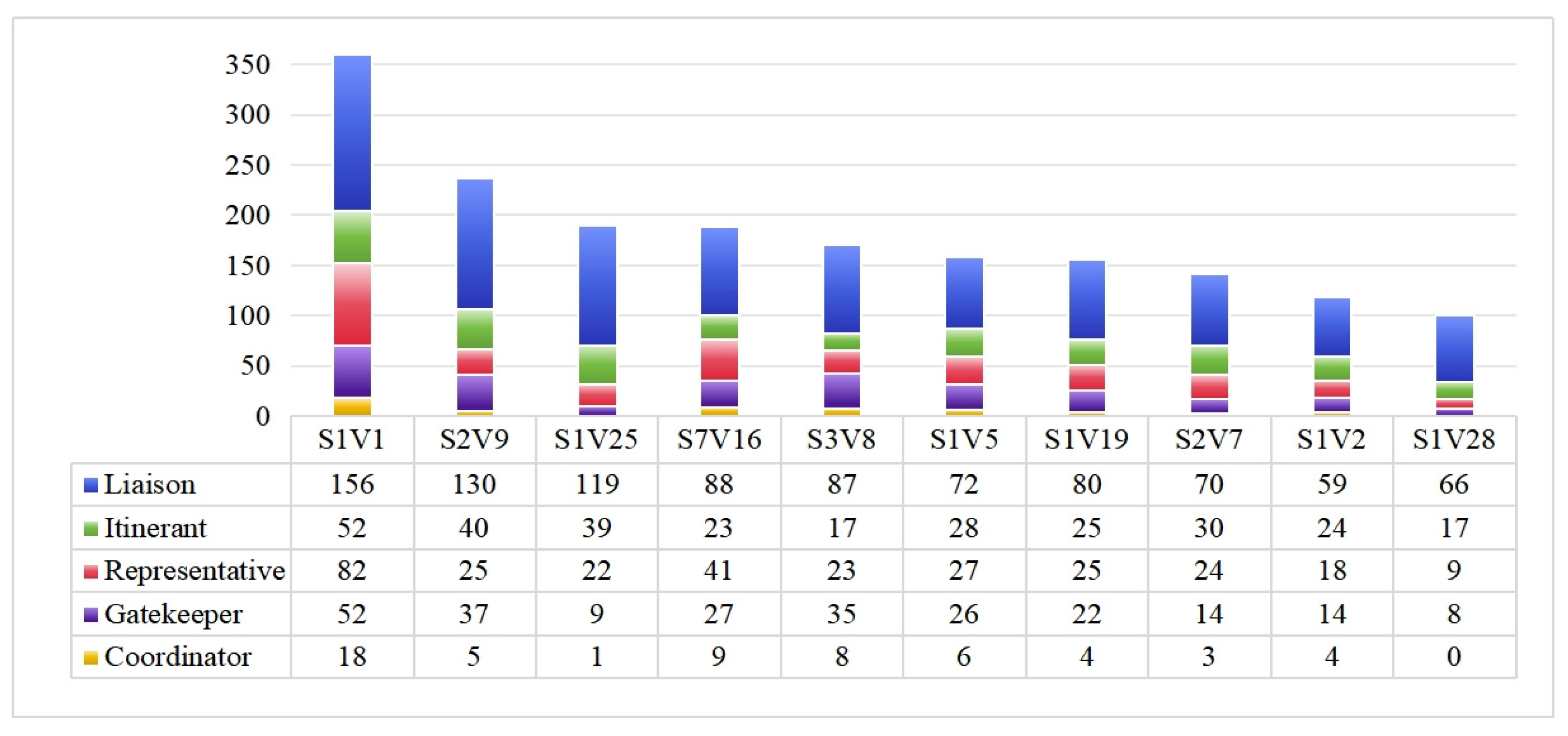
4.3.1. Brokerage Analysis
4.3.2. Betweenness Centrality
5. Discussion
5.1. Critical Challenges in PICT
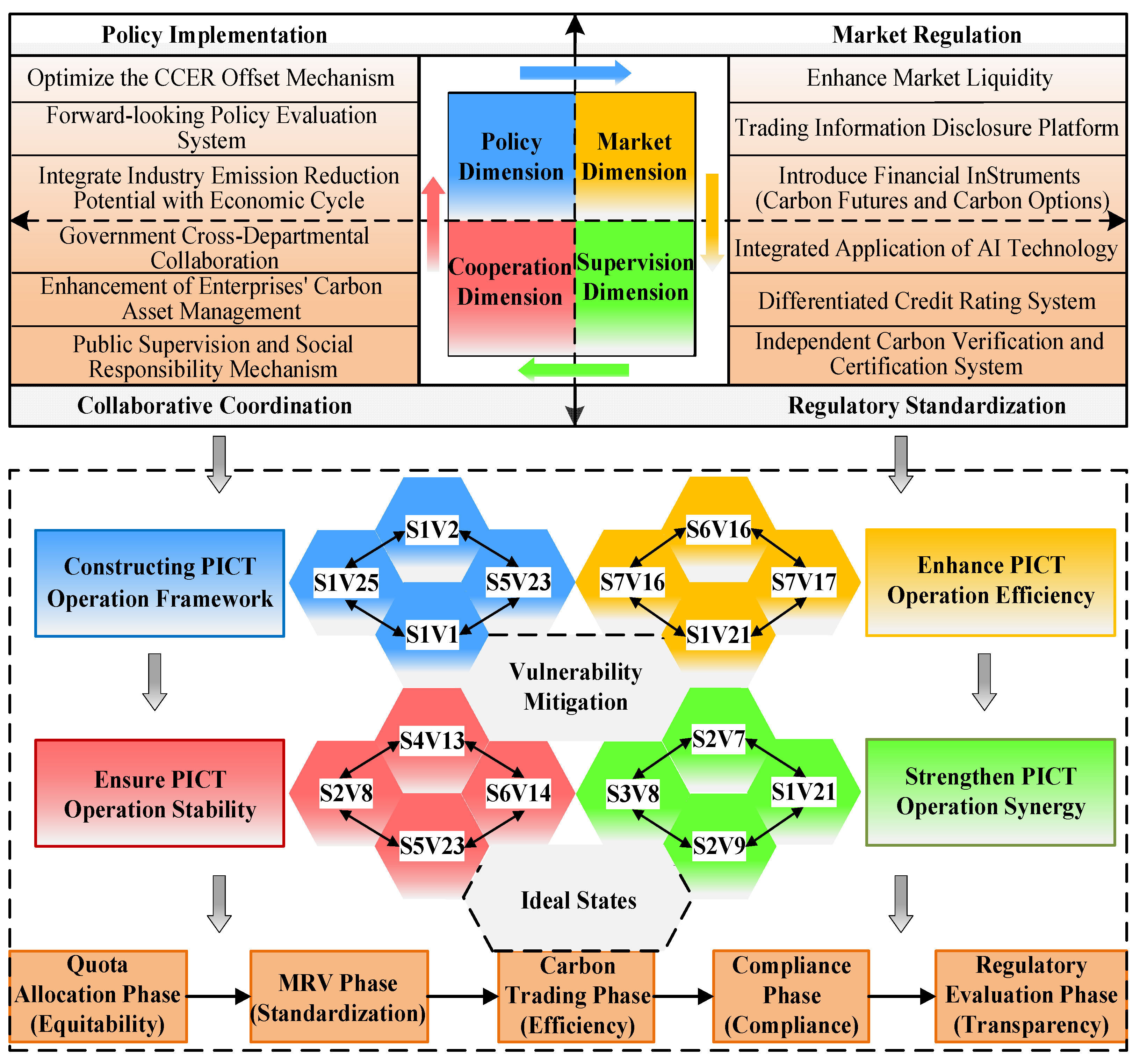
5.2. Vulnerabilities Mitigation Strategies
5.3. Effectiveness of Vulnerability Mitigation Strategies
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Cheng, X.M.; Ye, K.; Du, A.M.; Bao, Z.Z.; Chlomou, G. Dual carbon goals and renewable energy innovations. Res. Int. Bus. Financ. 2024, 70, 11. [Google Scholar] [CrossRef]
- Xu, Y.Y.; Ramanathan, V.; Victor, D.G. Global warming will happen faster than we think. Nature 2018, 564, 30–32. [Google Scholar] [CrossRef] [PubMed]
- Timilsina, G.R. Carbon Taxes. J. Econ. Lit. 2022, 60, 1456–1502. [Google Scholar] [CrossRef]
- Tang, B.J.; Ji, C.J.; Hu, Y.J.; Tan, J.X.; Wang, X.Y. Optimal carbon allowance price in China’s carbon emission trading system: Perspective from the multi-sectoral marginal abatement cost. J. Clean. Prod. 2020, 253, 12. [Google Scholar] [CrossRef]
- Su, C.; Zha, X.X.; Ma, J.Y.; Li, B.Y.; Wang, X.P. Dynamic Optimal Control Strategy of CCUS Technology Innovation in Coal Power Stations Under Environmental Protection Tax. Systems 2025, 13, 193. [Google Scholar] [CrossRef]
- Li, G.H.; Niu, M.M. How does the carbon trading scheme promote the decarbonization of China’s power sector? J. Environ. Plan. Manag. 2024, 28, 1969–1996. [Google Scholar] [CrossRef]
- Chen, X.H.; Zhang, C. A dynamic analysis of a green closed-loop supply chain with different on-line platform smart recycling and selling models. Comput. Ind. Eng. 2025, 200, 19. [Google Scholar] [CrossRef]
- Zhou, K.L.; Li, Y.W. Carbon finance and carbon market in China: Progress and challenges. J. Clean. Prod. 2019, 214, 536–549. [Google Scholar] [CrossRef]
- Ren, Z.R.; Zhang, S.F.; Liu, H.J.; Huang, R.; Wang, H.Q.; Pu, L. The feasibility and policy engagements in achieving net zero emission in China’s power sector by 2050: A LEAP-REP model analysis. Energy Conv. Manag. 2024, 304, 19. [Google Scholar] [CrossRef]
- Liu, Q.; Zheng, X.Q.; Zhao, X.C.; Chen, Y.; Lugovoy, O. Carbon emission scenarios of China’s power sector: Impact of controlling measures and carbon pricing mechanism. Adv. Clim. Change Res. 2018, 9, 27–33. [Google Scholar] [CrossRef]
- Howie, P.; Atakhanova, Z. Assessing initial conditions and ETS outcomes in a fossil-fuel dependent economy. Energy Strateg. Rev. 2022, 40, 12. [Google Scholar] [CrossRef]
- Barragán-Beaud, C.; Pizarro-Alonso, A.; Xylia, M.; Syri, S.; Silveira, S. Carbon tax or emissions trading? An analysis of economic and political feasibility of policy mechanisms for greenhouse gas emissions reduction in the Mexican power sector. Energy Policy 2018, 122, 287–299. [Google Scholar] [CrossRef]
- Zhao, Y.H.; Li, H.; Xiao, Y.L.; Liu, Y.; Cao, Y.; Zhang, Z.H.; Wang, S.; Zhang, Y.F.; Ahmad, A. Scenario analysis of the carbon pricing policy in China’s power sector through 2050: Based on an improved CGE model. Ecol. Indic. 2018, 85, 352–366. [Google Scholar] [CrossRef]
- Xu, Y.Y.; Zhao, S.; Chu, B.X.; Zhu, Y.L. Emission Reduction Effects of China’s National Carbon Market: Evidence Based on the Power Sector. Energies 2024, 17, 16. [Google Scholar] [CrossRef]
- Meng, M.; Wang, L.X.; Chen, Q. Quota Allocation for Carbon Emissions in China’s Electric Power Industry Based Upon the Fairness Principle. Energies 2018, 11, 16. [Google Scholar] [CrossRef]
- Cui, X.Y.; Zhao, T.; Wang, J. Allocation of carbon emission quotas in China’s provincial power sector based on entropy method and ZSG-DEA. J. Clean. Prod. 2021, 284, 11. [Google Scholar] [CrossRef]
- Xiao, J.; Li, G.H.; Xie, L.; Wang, S.Y.; Yu, L.A. Decarbonizing China’s power sector by 2030 with consideration of technological progress and cross-regional power transmission. Energy Policy 2021, 150, 14. [Google Scholar] [CrossRef]
- Chen, H.D.; Wang, C.; Cai, W.J.; Wang, J.H. Simulating the impact of investment preference on low-carbon transition in power sector. Appl. Energy 2018, 217, 440–455. [Google Scholar] [CrossRef]
- Li, W.; Zhang, Y.W.; Lu, C. The impact on electric power industry under the implementation of national carbon trading market in China: A dynamic CGE analysis. J. Clean. Prod. 2018, 200, 511–523. [Google Scholar] [CrossRef]
- Yang, M.; Wang, D.X.; Chen, X.F.; Lei, X.M.; Cao, L.X. Influence mechanism of technological innovation of electric power industry on carbon emission reduction in China. Int. J. Clim. Change Strateg. Manag. 2023, 15, 232–246. [Google Scholar] [CrossRef]
- Li, R.; Chen, Z.; Xiang, J.Y. A region-scale decoupling effort analysis of carbon dioxide emissions from the perspective of electric power industry: A case study of China. Environ. Dev. Sustain. 2023, 25, 4007–4032. [Google Scholar] [CrossRef]
- Liu, L.L.; Feng, T.T.; Kong, J.J. Can carbon trading policy and local public expenditures synergize to promote carbon emission reduction in the power industry? Resour. Conserv. Recycl. 2023, 188, 15. [Google Scholar] [CrossRef]
- Qi, C.; Choi, Y. A study on the CO2 marginal abatement cost of coal-fueled power plants: Is the current price of China pilot carbon emission trading market rational? Carbon Manag. 2020, 11, 303–314. [Google Scholar] [CrossRef]
- Xie, L.; Zhou, Z.C.; Hui, S.M. Does environmental regulation improve the structure of power generation technology? Evidence from China’s pilot policy on the carbon emissions trading market (CETM). Technol. Forecast. Soc. Change 2022, 176, 11. [Google Scholar] [CrossRef]
- Xian, Y.J.; Wang, K.; Wei, Y.M.; Huang, Z.M. Would China’s power industry benefit from nationwide carbon emission permit trading? An optimization model-based ex post analysis on abatement cost savings. Appl. Energy 2019, 235, 978–986. [Google Scholar] [CrossRef]
- Pietzcker, R.C.; Osorio, S.; Rodrigues, R. Tightening EU ETS targets in line with the European Green Deal: Impacts on the decarbonization of the EU power sector. Appl. Energy 2021, 293, 18. [Google Scholar] [CrossRef]
- Chen, W.Y.; Zhang, L.G.; Shi, L.J.; Shao, Y.Q.; Zhou, K.H. Carbon emissions trading system and investment efficiency: Evidence from China. J. Clean. Prod. 2022, 358, 12. [Google Scholar] [CrossRef]
- Ma, C.Q.; Ren, Y.S.; Zhang, Y.J.; Sharp, B. The allocation of carbon emission quotas to five major power generation corporations in China. J. Clean. Prod. 2018, 189, 1–12. [Google Scholar] [CrossRef]
- Han, Y.H.; Tan, S.T.; Zhu, C.W.; Liu, Y. Research on the emission reduction effects of carbon trading mechanism on power industry: Plant-level evidence from China. Int. J. Clim. Change Strateg. Manag. 2023, 15, 212–231. [Google Scholar] [CrossRef]
- Guo, H.Y.; Davidson, M.R.; Chen, Q.X.; Zhang, D.; Jiang, N.; Xia, Q.; Kang, C.Q.; Zhang, X.L. Power market reform in China: Motivations, progress, and recommendations. Energy Policy 2020, 145, 14. [Google Scholar] [CrossRef]
- Wang, Z.H.; Li, J.Y.; Lu, B.; Wang, B.; Zhang, B.; Sun, K.N.; Fan, M. Effectiveness and risk of initial carbon quota allocation principle under the uncertainty of the Chinese electricity market. China Econ. Rev. 2023, 77, 15. [Google Scholar] [CrossRef]
- Liu, L.W.; Chen, C.X.; Zhao, Y.F.; Zhao, E.D. China’s carbon-emissions trading: Overview, challenges and future. Renew. Sust. Energ. Rev. 2015, 49, 254–266. [Google Scholar] [CrossRef]
- Chen, F.; Zhao, T.; Xia, H.M.; Cui, X.Y.; Li, Z.Y. Allocation of carbon emission quotas in Chinese provinces based on Super-SBM model and ZSG-DEA model. Clean Technol. Environ. Policy 2021, 23, 2285–2301. [Google Scholar] [CrossRef]
- Chi, Y.Y.; Zhao, H.; Hu, Y.; Yuan, Y.K.; Pang, Y.X. The impact of allocation methods on carbon emission trading under electricity marketization reform in China: A system dynamics analysis. Energy 2022, 259, 18. [Google Scholar] [CrossRef]
- Zhao, X.G.; Jiang, G.W.; Nie, D.; Chen, H. How to improve the market efficiency of carbon trading: A perspective of China. Renew. Sust. Energ. Rev. 2016, 59, 1229–1245. [Google Scholar] [CrossRef]
- Fan, J.H.; Todorova, N. Dynamics of China’s carbon prices in the pilot trading phase. Appl. Energy 2017, 208, 1452–1467. [Google Scholar] [CrossRef]
- Teng, F.; Jotzo, F.; Wang, X. Interactions between market reform and a carbon price in China’s power sector. Econ. Energy Environ. Policy 2017, 6, 39–54. [Google Scholar] [CrossRef]
- Qi, S.Z.; He, A.Q.; Zhang, J.H. The Effective Benchmark Selection Model and Simulation in the Power Sector of China’s ETS. Clim. Change Econ. 2020, 11, 39. [Google Scholar] [CrossRef]
- Zeng, Q.; Ma, F.; Lu, X.J.; Xu, W.J. Policy uncertainty and carbon neutrality: Evidence from China. Financ. Res. Lett. 2022, 47, 6. [Google Scholar] [CrossRef]
- Song, Y.Z.; Liu, T.S.; Li, Y.; Zhu, Y.; Ye, B. Paths and policy adjustments for improving carbon-market liquidity in China. Energy Econ. 2022, 115, 12. [Google Scholar] [CrossRef]
- Camacho, D.; Panizo-Lledot, A.; Bello-Orgaz, G.; Gonzalez-Pardo, A.; Cambria, E. The four dimensions of social network analysis: An overview of research methods, applications, and software tools. Inf. Fusion 2020, 63, 88–120. [Google Scholar] [CrossRef]
- Otte, E.; Rousseau, R. Social network analysis: A powerful strategy, also for the information sciences. J. Inf. Sci. 2002, 28, 441–453. [Google Scholar] [CrossRef]
- Lee, C.Y.; Chong, H.Y.; Liao, P.C.; Wang, X.Y. Critical Review of Social Network Analysis Applications in Complex Project Management. J. Manag. Eng. 2018, 34, 15. [Google Scholar] [CrossRef]
- Xian, Z.; Yun, L.; Chan, A.P.C.; Yi, H.; Yongkui, L. Review of the application of social network analysis (SNA) in construction project management research. Int. J. Proj. Manag. 2016, 34, 1214–1225. [Google Scholar] [CrossRef]
- Yuan, M.Q.; Li, Z.F.; Li, X.D.; Luo, X.W. Managing stakeholder-associated risks and their interactions in the life cycle of prefabricated building projects: A social network analysis approach. J. Clean. Prod. 2021, 323, 18. [Google Scholar] [CrossRef]
- Yang, Y.R.; Zuo, J.; Pan, M.; Chang, R.D.; Zou, Z.J.; Webber, R.J.; Dong, N. Analysis of stakeholder-associated factors and their interactions in energy conservation behaviour of occupants: Evidence from network analysis. Environ. Dev. Sustain. 2024, 36. [Google Scholar] [CrossRef]
- Luo, L.Z.; Li, Y.K.; Wang, X.; Jin, X.; Qin, Z.Y. Supply Chain Vulnerability in Prefabricated Building Projects and Digital Mitigation Technologies. IEEE Trans. Eng. Manag. 2024, 71, 10686–10698. [Google Scholar] [CrossRef]
- Hu, X.; Chong, H.Y.; Wang, X.Y.; London, K. Understanding Stakeholders in Off-Site Manufacturing: A Literature Review. J. Constr. Eng. Manag. 2019, 145, 15. [Google Scholar] [CrossRef]
- Luo, L.Z.; Shen, G.Q.; Xu, G.Y.; Liu, Y.L.; Wang, Y.J. Stakeholder-Associated Supply Chain Risks and Their Interactions in a Prefabricated Building Project in Hong Kong. J. Manag. Eng. 2019, 35, 14. [Google Scholar] [CrossRef]
- Lin, B.Q.; Jia, Z.J. Why do we suggest small sectoral coverage in China’s carbon trading market? J. Clean. Prod. 2020, 257, 14. [Google Scholar] [CrossRef]
- Cong, R.G.; Wei, Y.M. Potential impact of (CET) carbon emissions trading on China’s power sector: A perspective from different allowance allocation options. Energy 2010, 35, 3921–3931. [Google Scholar] [CrossRef]
- Chen, S.; Shi, A.N.; Wang, X. Carbon emission curbing effects and influencing mechanisms of China’s Emission Trading Scheme: The mediating roles of technique effect, composition effect and allocation effect. J. Clean. Prod. 2020, 264, 15. [Google Scholar] [CrossRef]
- Ji, C.J.; Hu, Y.J.; Tang, B.J.; Qu, S. Price drivers in the carbon emissions trading scheme: Evidence from Chinese emissions trading scheme pilots. J. Clean. Prod. 2021, 278, 12. [Google Scholar] [CrossRef]
- Hu, Y.J.; Li, X.Y.; Tang, B.J. Assessing the operational performance and maturity of the carbon trading pilot program: The case study of Beijing’s carbon market. J. Clean. Prod. 2017, 161, 1263–1274. [Google Scholar] [CrossRef]
- Maosheng, D.; Tao, P.; Xiliang, Z. Review of carbon emissions trading pilots in China. Energy Environ. 2014, 25, 527–549. [Google Scholar] [CrossRef]
- Yang, Y.; Cheng, L.W. Operational efficiency evaluation and system design improvements for carbon emissions trading pilots in China. Carbon Manag. 2017, 8, 399–415. [Google Scholar] [CrossRef]
- Wang, J.Q.; Dai, P.F.; Chen, X.H.; Nguyen, D.K. Examining the linkage between economic policy uncertainty, coal price, and carbon pricing in China: Evidence from pilot carbon markets. J. Environ. Manag. 2024, 352, 16. [Google Scholar] [CrossRef]
- Morris, J.; Paltsev, S.; Ku, A.Y. Impacts of China’s emissions trading schemes on deployment of power generation with carbon capture and storage. Energy Econ. 2019, 81, 848–858. [Google Scholar] [CrossRef]
- Chang, K.; Ge, F.P.; Zhang, C.; Wang, W.H. The dynamic linkage effect between energy and emissions allowances price for regional emissions trading scheme pilots in China. Renew. Sust. Energ. Rev. 2018, 98, 415–425. [Google Scholar] [CrossRef]
- Zha, D.S.; Feng, T.T.; Kong, J.J. Effects of enterprise carbon trading mechanism design on willingness to participate-Evidence from China. Front. Environ. Sci. 2022, 10, 22. [Google Scholar] [CrossRef]
- Wang, X.Q.; Su, C.W.; Lobont, O.R.; Li, H.; Nicoleta-Claudia, M. Is China’s carbon trading market efficient? Evidence from emissions trading scheme pilots. Energy 2022, 245, 9. [Google Scholar] [CrossRef]
- Zhang, S.Y.; Jiang, K.; Wang, L.; Bongers, G.; Hu, G.P.; Li, J. Do the performance and efficiency of China’s carbon emission trading market change over time? Environ. Sci. Pollut. Res. 2020, 27, 33140–33160. [Google Scholar] [CrossRef] [PubMed]
- Kai, C.; Rongda, C.; Chevallier, J. Market fragmentation, liquidity measures and improvement perspectives from China’s emissions trading scheme pilots. Energy Econ. 2018, 75, 249–260. [Google Scholar] [CrossRef]
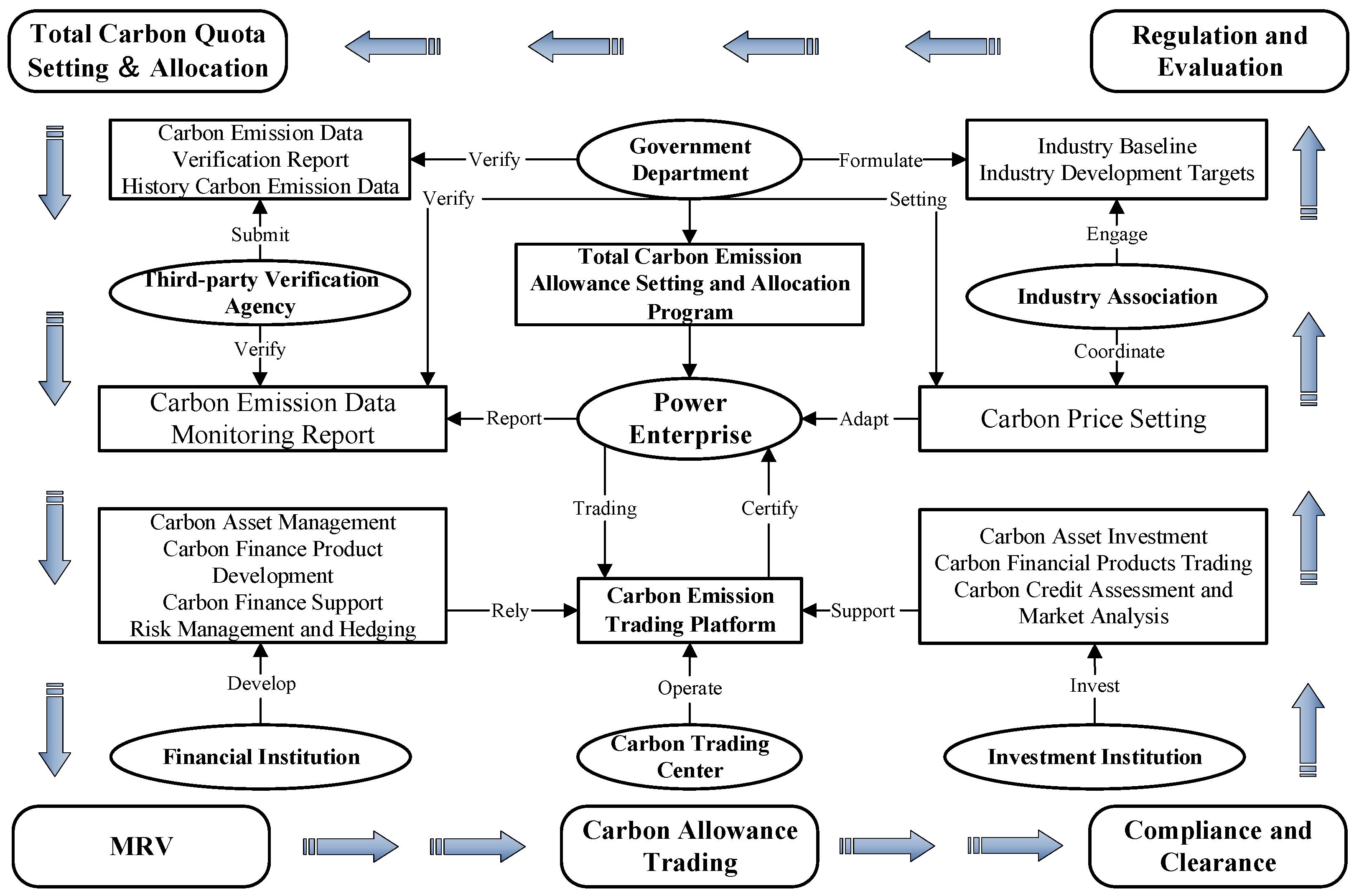


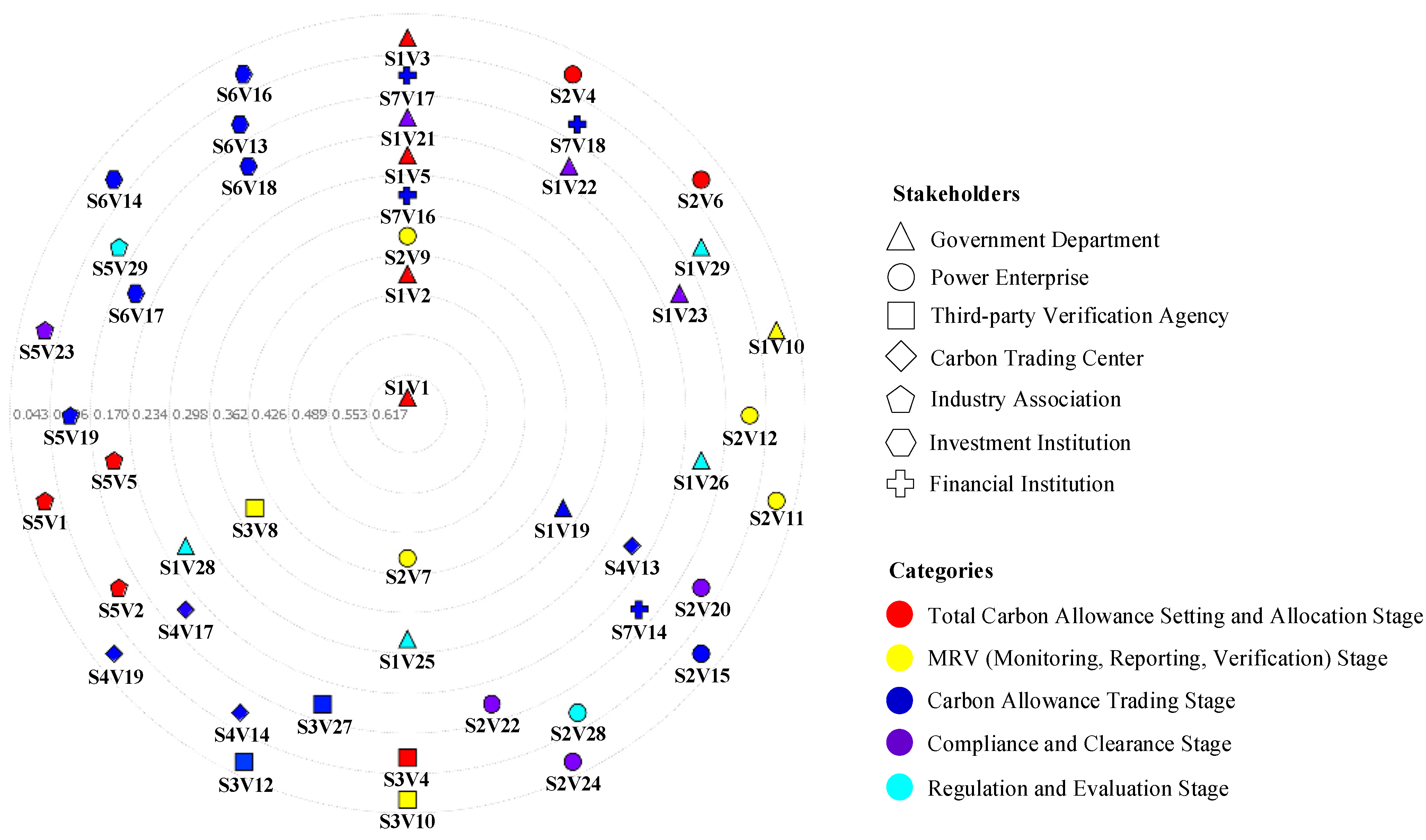


| Stage | Description | Stakeholders | References |
|---|---|---|---|
| Total Carbon Allowance Setting and Allocation Stage | Unreasonable setting of total carbon allowances V1 | Government Department, Power Enterprise, Third Party Verification Agency, Industry Association | [50,51,52,53] |
| Inequity in the way carbon allowances allocated V2 | |||
| Local government intervention leads to market fragmentation V3 | |||
| Inaccurate historical carbon emission data V4 | |||
| Unscientific industry baseline setting V5 | |||
| Game of interests in high-emission and high-energy-consumption industries V6 | |||
| MRV Stage | Data falsification in carbon emission reports V7 | [54,55,56] | |
| Lack of independence in third-party verification agencies V8 | |||
| Lack of uniformity in monitoring methods and standards V9 | |||
| Lack of coordination in the regulatory system V10 | |||
| Insufficient transparency in carbon emission data V11 | |||
| High costs of MRV V12 | |||
| Carbon Allowance Trading Stage | Volatility in carbon prices V13 | Government Department, Power Enterprise, Carbon Trading Center, Industry Association, Investment Institution, Financial Institution | [36,53,57,58,59] |
| Insufficient market liquidity V14 | |||
| Carbon allowance hoarding V15 | |||
| Immaturity of the carbon financial derivatives market V16 | |||
| Lack of transparency in carbon allowance trading V17 | |||
| Excessive financial speculation V18 | |||
| Poor connection between regional carbon markets V19 | |||
| Compliance and Clearance Stage | Low compliance willingness V20 | Government Department, Power Enterprise, Industry Association | [58,60,61] |
| Insufficient regulatory penalties V21 | |||
| Unreasonable deadlines for compliance V22 | |||
| Irrational CCER offset ratio V23 | |||
| Insufficient carbon asset management capacity V24 | |||
| Regulation and Evaluation Stage | Delayed adjustment of carbon market policies V25 | Government Department, Power Enterprise, Third Party Verification Agency, Industry Association | [54,56,62,63] |
| Unclear responsibilities and authorities of regulatory agencies V26 | |||
| Lack of independence in third-party verification agency V27 | |||
| Conflict between carbon market goals and economic development goals V28 | |||
| Inadequate carbon credit evaluation system V29 |
| No. | S1V1 | S1V2 | … | S7V17 | S7V18 |
|---|---|---|---|---|---|
| S1V1 | (2, 3) | ||||
| S1V2 | (3, 2) | (3, 4) | (4, 4) | ||
| … | (likelihood, level) | ||||
| S7V17 | (4, 3) | ||||
| S7V18 | (3, 2) |
| Ranking | Nodes | Out-Status Centrality | Nodes | Out-Degree | Nodes | Degree Difference | Nodes | Ego Size |
|---|---|---|---|---|---|---|---|---|
| 1 | S1V1 | 2.951710 | S1V1 | 32 | S1V1 | 17 | S1V1 | 32 |
| 2 | S1V2 | 2.244449 | S1V2 | 22 | S1V2 | 14 | S2V9 | 27 |
| 3 | S2V7 | 2.002302 | S2V7 | 21 | S2V7 | 11 | S1V5 | 26 |
| 4 | S3V8 | 1.832926 | S3V8 | 20 | S3V8 | 8 | S2V7 | 25 |
| 5 | S2V9 | 1.727897 | S2V9 | 18 | S1V19 | 6 | S1V19 | 25 |
| 6 | S1V19 | 1.630182 | S1V19 | 18 | S6V17 | 5 | S7V16 | 24 |
| 7 | S7V16 | 1.407323 | S7V16 | 15 | S6V18 | 5 | S3V8 | 23 |
| 8 | S3V27 | 1.266567 | S1V25 | 15 | S4V17 | 4 | S1V2 | 23 |
| 9 | S1V21 | 1.252348 | S1V5 | 14 | S1V26 | 3 | S3V27 | 21 |
| 10 | S1V25 | 1.208533 | S4V13 | 13 | S1V23 | 3 | S4V13 | 21 |
| Ranking | Risk Nodes | Node Betweenness Centrality | Risk Interactions | Link Betweenness Centrality |
|---|---|---|---|---|
| 1 | S1V1 | 0.122319 | S2V4→S1V1 | 43.756 |
| 2 | S2V9 | 0.098750 | S2V11→S2V9 | 43.384 |
| 3 | S1V25 | 0.077409 | S2V15→S1V21 | 30.659 |
| 4 | S7V16 | 0.056601 | S1V21→S1V1 | 28.864 |
| 5 | S1V19 | 0.049295 | S6V14→S2V9 | 28.095 |
| 6 | S3V8 | 0.046392 | S2V12→S1V19 | 25.201 |
| 7 | S1V5 | 0.046113 | S5V23→S1V2 | 24.965 |
| 8 | S2V7 | 0.042557 | S7V17→S1V2 | 23.974 |
| 9 | S3V27 | 0.039767 | S1V25→S1V1 | 22.876 |
| 10 | S1V2 | 0.036953 | S6V16→S1V25 | 21.983 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, L.; Xiu, C.; Liu, B.; Yu, X.; Zhu, R. Vulnerability and Sustainable Development Strategy of the Power Industry Under Carbon Market Based on Social Network Analysis Perspective. Sustainability 2025, 17, 4398. https://doi.org/10.3390/su17104398
Li L, Xiu C, Liu B, Yu X, Zhu R. Vulnerability and Sustainable Development Strategy of the Power Industry Under Carbon Market Based on Social Network Analysis Perspective. Sustainability. 2025; 17(10):4398. https://doi.org/10.3390/su17104398
Chicago/Turabian StyleLi, Lihong, Ce Xiu, Bing Liu, Xingcheng Yu, and Rui Zhu. 2025. "Vulnerability and Sustainable Development Strategy of the Power Industry Under Carbon Market Based on Social Network Analysis Perspective" Sustainability 17, no. 10: 4398. https://doi.org/10.3390/su17104398
APA StyleLi, L., Xiu, C., Liu, B., Yu, X., & Zhu, R. (2025). Vulnerability and Sustainable Development Strategy of the Power Industry Under Carbon Market Based on Social Network Analysis Perspective. Sustainability, 17(10), 4398. https://doi.org/10.3390/su17104398





