1. Introduction
With the substantial growth of WiFi and 5G, digital images containing huge amounts of data are transferred frequently over multiple communication networks. In the meantime, tampering with and stealing digital images of high potential values are common [
1]. Thus, the security and privacy of such images must be preserved before transmission. Typical digital image protection techniques include image encryption, digital watermarking, secret-sharing, and information hiding. Among these techniques, image encryption is the most direct way [
2]. The diffusion and permutation stages are the two main steps of digital image encryption. The permutation stage alters the pixel positions of the original images arbitrarily, while the diffusion stage requires that all pixel values of the original images be altered [
3]. The main tools utilized in image encrypting contain frequency domain transformations, Chaos, evolutionary algorithms, neural networks (NNs), and DNA coding [
4]. Sensitivity and Chaos’s unpredictability in its primary state make it a widely used tool in image encrypting techniques [
5].
Recently, authors have modeled numerous digital image encryption techniques related to NNs [
6]. Cyber-attacks on automation on the Internet of Things (IoT) platform have far-reaching impacts. They can disturb manufacturing tasks, causing data loss and harming the quality and the standard of products [
7]. Current solutions for image encryption do not assist those smart industries in which the peers are decentralized. There are several prevailing methods of image encryption. However, none of them complies with industrial needs. Smart industrial units are decentralized networks of interconnected IIoT devices that can share sensitive information, which is at risk of exposure [
8]. The blockchain (BC) offers comprehensive solutions for decentralized devices, and its secure encrypted architecture is ideal for smart industrial units.
The history of BC technology (BCT) originates from Bitcoin or cryptocurrency. BC can act as a ledger that records every transferable transaction between individuals. This ledger can be decentralized; therefore, there are no centralized authorities [
9]. It can be cryptographically immutable and secure. This ledger cannot be changed or deleted once modified. BC is a consensus-related mechanism, which means that all nodes verify the incidence of the transaction and derive a consensus regarding every unit of data before it can be positioned into a BCT-related ledger. BCT solves security issues. Owing to its dynamic properties, businesses quickly understood that BCT had a serious role in the IIoT [
10]. This technology is implemented in industrial units to achieve security, regulatory complements, and transparency. BC can markedly transform the IIoT. It grants new functionality via smart contracts, security, and peer-to-peer device communications.
With the increased utilization of virtual reality and augmented reality in several industrial sectors, such as healthcare, education, and entertainment, the requirement of confidentiality in the context of sensitive images has become important. Encryption ensures that only authorized users have access to the images, defending the confidentiality of the data. It also ensures that the images remain unaltered during storage or transmission. This helps to maintain the data integrity of the images and ensures that they are reliable and trustworthy. Therefore, an image encryption technique with BC can be used to accomplish enhanced security.
With this motivation, this study develops blockchain-driven image encryption using arithmetic optimization with a fractional-order Lorenz system (BDIE-AOFOLS). The BDIE-AOFOLS procedure uses the FOLS technique, which is an integration of the Arnold map, tent map, and fractional Lorenz system. In addition, an arithmetic optimization algorithm (AOA) is carried out for the optimum key generation process, with the objective of achieving maximum PSNR value. The design of the AOA-based optimal generation of keys for the FOLS technique determines the novelty of the current work. Moreover, the cryptographical pixel values of the images can be stored securely in BC, guaranteeing image security. The experimental outcome investigation of the BDIE-AOFOLS technique was tested utilizing benchmark color images.
2. Related Works
Khayyat et al. [
11] examined a novelty BC-enabled shark smell model, optimized with Hopfield Chaotic NN (SSOHCNN), for securing encryption on the IIoT platform. The proposed SSOHCNN approach offers a merged chaotic map (CM), which is combined in the form of staged logistic and tent maps to complete the primary processing of the image and improve the variable required for Arnold mapping. Neelakandan et al. introduced a novel BC system with DL that enabled a secure medicinal data transmission and diagnosis (BDL-SMDTD) technique. Initially, the moth flame optimizer with ECC, known as the MFO-ECC approach, was utilized for the image encryption method, whereas better keys for ECC can be produced by utilizing the MFO system. In addition, BC technology has been employed for storing image encryption [
12].
In one study [
13], a novel fingerprint-related chaotic image encryption system was presented. The creation of key streams is influenced by the “fingerprints” of distributors instead of the plain-text form of images. Moreover, the BC infrastructure was implemented to ensure that the image encryption had been sent, following proper procedure, to the distributor. Furthermore, the distributor fingerprints embedded in the image encryption can be encoded by the anti-collusion code used for recording several fingerprints with a predetermined data length. Bhaskaran et al. [
14] introduce a novel BC-allowed secure optimum lightweight cryptography-based image encryption (BC-LWCIE) system for Industry 4.0 platforms. The BC-LWCIE system supplies the cryptographic pixel value of image encryption from the BCT for ensuring privacy on the IIoT platform.
In another study [
15], the authors established novel multiple share creation techniques with block technology for secure image management (MSCCBT-SIM) approaches. The MSCCBT-SIM technique permits the consumer to create a consensus without relying on central government input. In addition, the BC was utilized as a distributing data-storing process for generating a ledger intended to permit access to users and prevent third-party access to encrypted shares. Sammeta and Parthiban [
16] introduced a new data control and secure medicinal information broadcast method, utilizing optimal multiple key-based homomorphic encryptions (MHE) with a Hyperledger BC (OMHE-HBC). The optimum key generation procedure from the MHE systems works by utilizing a hosted cuckoo optimization (HCO) technique. Mahesh Kumar et al. [
17] presented a new multi-instance iris authentication model, BMIAE, for controlling malicious attacks on the broadcast channel and untrusted servers. BMIAE encrypted the iris template utilizing ElGamal to assure confidentiality, with a smart contract running on BC supports ensuring the integrity of templates and equivalent outcomes.
In a further study, Karim [
18] suggested how to secure V2V and V2I transmission in the context of the VANET against a large number of cyberattacks. A hybrid cryptography system incorporating ABS and IBS, known as AIBS (attribute identity-based signature), was constructed to provide effective message authentication and integrity while ensuring vehicle privacy and safeguarding vehicular transmission. A JPEG image encryption with the adaptive key and run consistency of MCUs was developed by the authors of [
19]. The chosen plain-text attack (CPA) was given here on this encryption system. First, the adaptive key can be reproduced from the encrypted image, such that the plain-text images with a similar adaptive key can be constructed. Second, the existence of the run consistency of MCUs (RCM) between the original image and the encrypted image facilitates rapid estimation. Sabir and Guleria [
20] developed a novel multiple-image encryption system using an affine Hill cipher (AHC), reality-preserving 2D discrete fractional Hartley transform (RP2DFrHT), and a generalized 2D Arnold map (AM). In this work, three indexed images are attained from three color images. Third, AHC performs a strong degree of confusion and diffusion operations and RP2DFrHT provides a real domain output image. Fourth, the 2D AM dislocates the image pixel position.
3. The Proposed Model
In this study, we have developed a novel BDIE-AOFOLS system for a color image encryption process. The BDIE-AOFOLS technique mainly relies on the FOLS technique, which is an integration of an Arnold map, tent map, and fractional Lorenz system. In addition, an AOA was executed for an optimum key generation process, with the objective of achieving the maximum PSNR value.
Figure 1 represents the workflow of the BDIE-AOFOLS approach.
3.1. Blockchain Technology in the BDIE-AOFOLS Technique
In the presented technique, the cryptographic pixel values of images can be stored on the BC, thereby assuring the privacy and security of images. BC is a beneficial ledger for assuring data quality. It has generated “controlling operations” for numerous decentralized industrial gadgets and has performed peer-to-peer interactions between globally decentralized gadgets. Moreover, BC offers amenability along with authority for all independent systems; simultaneously, it resolves security problems. In industrial fields, a private BC has been used for ensuring security. The phrase “Hyperledger fabric” refers to an environment that hinges on BC and satisfies the necessity for an IIoT platform. This is helpful in numerous fields, such as transportation, healthcare, large-scale IoT data, and the supply chain. Moreover, BC aids in accomplishing decentralization, privacy, and trust. BC also enables simple connections with numerous gadgets.
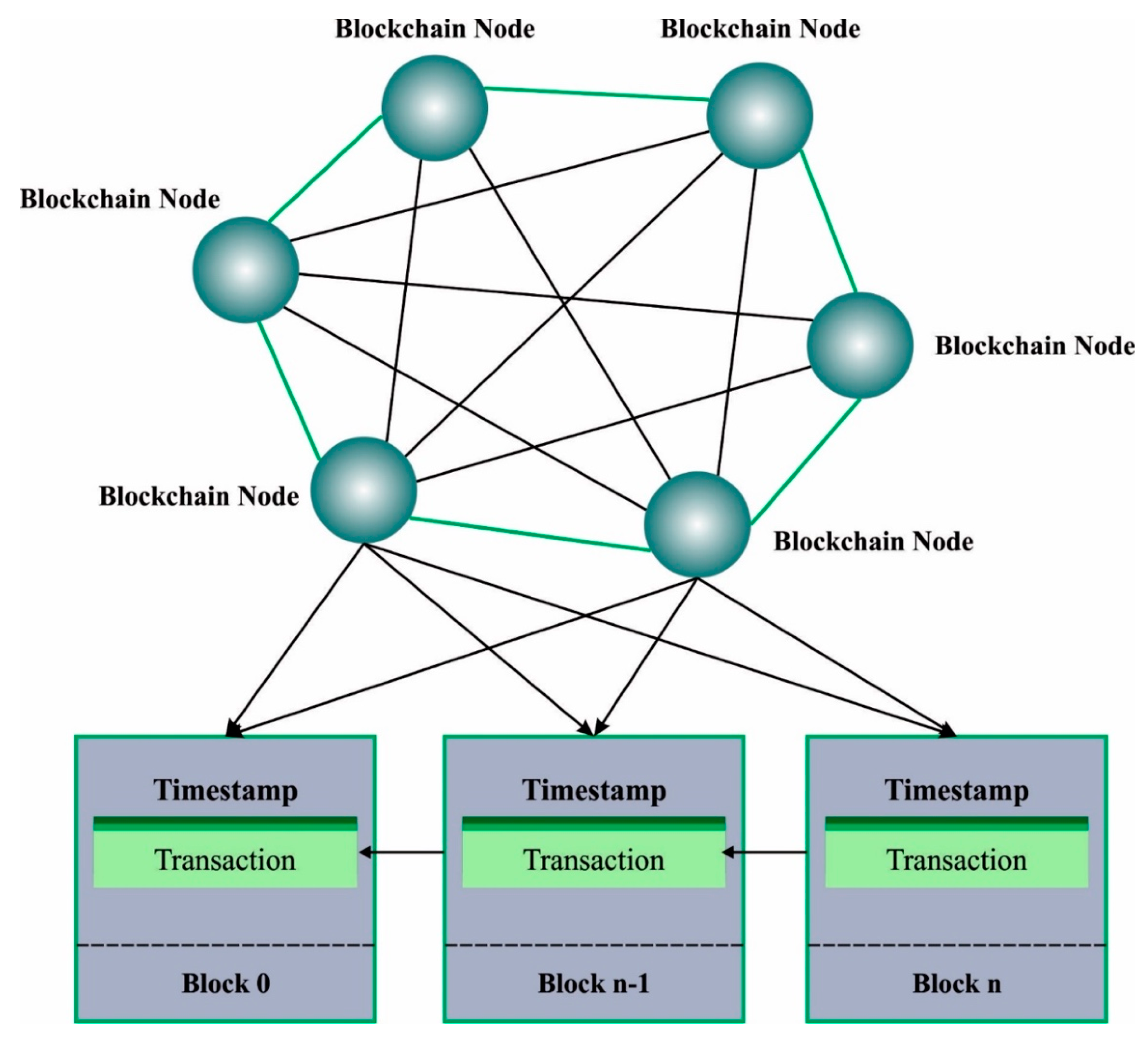
Figure 2 shows the basic framework of the BC. The client or server computer acts as a node and then commences making the connections.
The nodes exchange encrypted data with other peer nodes, without any invader being able to steal the information. They may transfer the information to a central location or distributed gadget, which can be connected to other gadgets. The hashing value specifies every transaction that happened in the block.
The transactions will be integrated together to generate a block, which will be added to the chain next to the confirmation from the endorsed node. The operation starts if the client begins to submit a proposal. The transaction procedures employ two types of peers: committer peers and endorsers. The certificate authority (CA) allows the credentials to the client as is compulsory for user applications for gaining permission to submit novel communications.
To start a novel transaction, the user application transfers the transaction proposals to a peer, thereby updating or reading the ledger. The peer could then read it and validate the authorization policy. Finally, the committer–peer makes an asynchronous announcement that is relevant to the transaction’s rank.
3.2. Image Encryption Using the FOLS Technique
To encrypt the color images, a FOLS technique is used in this work. In this study, a novel color image encryption technique dependent upon a fractional order chaotic system was introduced with the combination of three chaotic systems (a tent map (TM), an Arnold map (AM), and a fractional Lorenz system (FLS)) [
21]. Initially, the plain color images are separated into their
and
layers. In the scrambling phase, these three layers are scrambled with the AM, among which the first value of initial scrambling is the key, and the first values of the remaining two scrambles are the
and
layers.
The gray value of RGB is molded and is later applied as the initial value of FLS. Following this, add-mode diffusion is performed. Finally, an encrypted image is achieved. The plain image is represented as , the pixel matrix size was × × , and the encryption technique is determined by the following process:
Step 1: Enter the A plain image and the key,
, and assume that the size of
is
×
×
. Read the first value and parameter of the AM in
, then apply an AM for scrambling the plain image
layer. Choose the latter 2 pixels of the
layer after scrambling, obtaining the gray value as a parameter of AM while scrambling the
layer, and apply a similar function to scrambling the
layer for obtaining image
Step 2: Read the first value of TM
from the key,
. The TM is reiterated 800 times; the initial 300 transition conditions are abandoned and take the state value, which is defined by
.
Step 3: Use Equation (3) for turning into and coordinates for placing the pixel in .
The FLS is reiterated
and
times, respectively, with a small perturbation of the model every 3000 times, to obtain a size of
and
×
for the novel pseudo-random sequences
and
, which are transmuted by Equation (4) to password
and
Step 4: Utilize the password,
, to spread the data between the layers of images; this can be computed, as follows:
In Equation (6), denotes the pixel value after diffusing for the initial time. After pixel diffusion between the layers, the plain data of all the layers are diffused to the other 2 layers. This phase could improve the model’s capability for resisting a chosen-plain attack.
3.3. Optimal Key Generation Using AOA
The aim of key generation is to offer the secure encryption and decryption of data. An optimum key generation process ensures that the keys utilized for encryption and decryption are random, unique, and sufficiently complex, making it hard for attackers to decrypt the data. The system generates the keys rapidly and precisely, with no need for high computation resources. Therefore, in this work, an AOA was executed for the optimal key generation process, with the objective of achieving the maximum PSNR value [
22]. AOA operates following the distribution behavior of mathematical operations, such as multiplication (M), division (D), subtraction (S), and addition (A), which aims at finding the optimum solution covering a large number of search spaces.
The AOA operation depends on four major processes—inspiration, initialization, exploration, and exploitation. The steps that are adopted to establish an optimum solution by applying the AOA technique are given below.
Step 1: Inspiration is based on the operation of a simple arithmetical operator to determine better values when subjected to specific conditions from a large number of candidate solutions. The applicability of an arithmetic operator is used to find a solution for the arithmetical problem.
Step 2: Initialization, where the candidate solution can be determined as follows:
We then calculate the math optimizer acceleration
coefficient:
In Equation (8), and denote the maximal and minimal values of the accelerated function, shows the existing iteration, and indicates the maximal iteration.
Step 3: The exploration operators of AOA are the D and M operators. The exploration process recognizes the near-optimum solution that should be attained after various iterations. The and operators are used to support the exploitation phase via effective transmission. The higher dispersion possibility does not allow this exploration operator to approach the optimum solution.
In this phase, the division and multiplication search strategies implement the location update and are given by the following equation:
In Equation (9),
and
denote the smaller random integers; the
operator implements when
, while the
operators do not implement until the
operator finishes the existing process. The better solution that has been assessed so far is
’ characterizes the control parameter for altering the searching process,
denotes the small number,
and
indicate the lower and upper bounds of the existing location, and ‘
’ represents the math optimizer probability shown in the following equation:
In Equation (10), indicates the sensitivity parameter determining the exploration accuracy.
Step 4: Exploitation can be performed by the and operators that move through the searching space and attain a more highly dense solution. Owing to a lower dispersion, the above two operators are more effective in approaching the better t solution point than the higher dispersion operators, and
The addition and subtraction search strategies evolve the location of the near-optimum solution by moving through the deep dense region and are updated as follows:
If
then
The
and
operators assist in overcoming the existence of local minima; this exploitation process facilitates the exploration method to accomplish an optimum solution by retaining the diversity of candidate solutions. The hierarchical order of the
and
operators evaluate the location of the near-optimum solution and overcome the optimum stagnation occurrence toward the end of the final iterations. The AOA system was utilized in the initialization of the public as well as secret keys contained in the encryption procedure. This ensures that the method that PSNR obtained is improved. The fitness function of the AOA system for the FOLS approach is provided, as follows:
4. Performance Validation
In this section, the experimental validation of the BDIE-AOFOLS approach was tested utilizing benchmark color images.
Figure 3 shows the sample images. In
Table 1, the encryption results of the BDIE-AOFOLS technique are clearly depicted. The results indicated that the input image is properly encrypted and reconstructed without any loss of information. It is evident that the BDIE-AOFOLS technique has obtained increasing values of PSNR and CC. At the same time, the BDIE-AOFOLS technique has obtained decreasing values of MSE under all images.
Table 2 and
Figure 4 illustrate the information entropy values (IEV) outcomes of the BDIE-AOFOLS with the existing models [
11]. The results indicated that the BDIE-AOFOLS approach has reached enhanced IEV values under all channels. For the sample, on the R channel, the BDIE-AOFOLS technique has reached a higher IEV of 7.9995, while the SSOHCNN, WOAHCNN, GWOHCNN, and HCNN models have obtained lower IEV levels of 7.9992, 7.9941, 7.9938, and 7.9931, respectively. Meanwhile, on the G channel, the BDIE-AOFOLS method has reached a higher IEV of 7.9998, while the SSOHCNN, WOAHCNN, GWOHCNN, and HCNN methods have gained lower IEV levels of 7.9990, 7.9935, 7.9921, and 7.9922, respectively. Furthermore, on the B channel, the BDIE-AOFOLS approach has reached a higher IEV of 7.9997, while the SSOHCNN, WOAHCNN, GWOHCNN, and HCNN methods have attained lower IEV levels of 7.9992, 7.9933, 7.9930, and 7.9915, respectively.
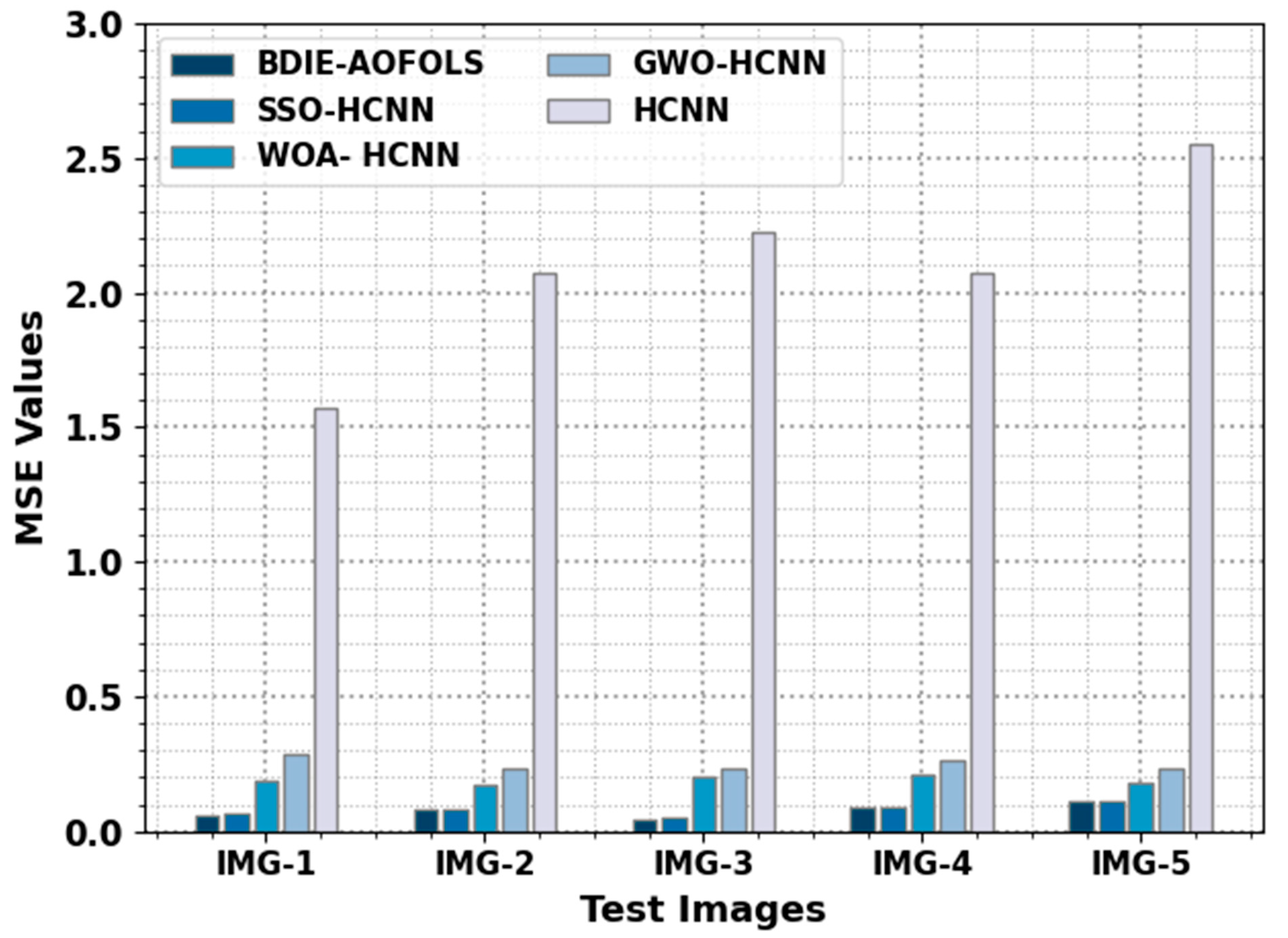
Table 3 reveals a comparative MSE and PSNR inspection of the BDIE-AOFOLS with recent models. A comparative analysis of the BDIE-AOFOLS with existing approaches in terms of MSE is reported in
Figure 5. The results represent the improvised outcomes of the BDIE-AOFOLS model using minimal values of MSE. For instance, on IMG-1, the BDIE-AOFOLS technique attains a reduced MSE value of 0.0590, while the SSOHCNN, WOAHCNN, GWOHCNN, and HCNN models have resulted in improved MSE values of 0.0636, 0.1850, 0.2875, and 1.5733, respectively.
Along with these findings, for IMG-3, the BDIE-AOFOLS method achieved a reduced MSE of 0.0430, while the SSOHCNN, WOAHCNN, GWOHCNN, and HCNN methods resulted in increased MSE values of 0.0487, 0.2027, 0.2352, and 2.2278, respectively. Finally, for IMG-5, the BDIE-AOFOLS algorithm attained a reduced MSE of 0.1100, while the SSOHCNN, WOAHCNN, GWOHCNN, and HCNN approaches resulted in increased MSE values of 0.1117, 0.1798, 0.2318, and 2.5501, respectively.
In
Figure 6, a comprehensive PSNR analysis of the BDIE-AOFOLS with recent algorithms is reported. The obtained values show the superior performance of the BDIE-AOFOLS technique, with improved PSNR values. For instance, for IMG-1, the BDIE-AOFOLS technique accomplished an enhanced PSNR value of 60.42 dB, while the SSOHCNN, WOAHCNN, GWOHCNN, and HCNN models obtained decreased PSNR values of 60.10 dB, 55.46 dB, 53.54 dB, and 46.16 dB, respectively. Meanwhile, for IMG-3, the BDIE-AOFOLS method accomplished an enhanced PSNR value of 61.80 dB, while the SSOHCNN, WOAHCNN, GWOHCNN, and HCNN methods achieved decreased PSNR values of 61.26 dB, 55.06 dB, 54.42 dB, and 44.65 dB, respectively. Eventually, for IMG-5, the BDIE-AOFOLS technique achieved an enhanced PSNR value of 57.72 dB, while the SSOHCNN, WOAHCNN, GWOHCNN, and HCNN methods attained decreased PSNR values of 57.65 dB, 55.58 dB, 54.48 dB, and 44.07 dB, respectively.
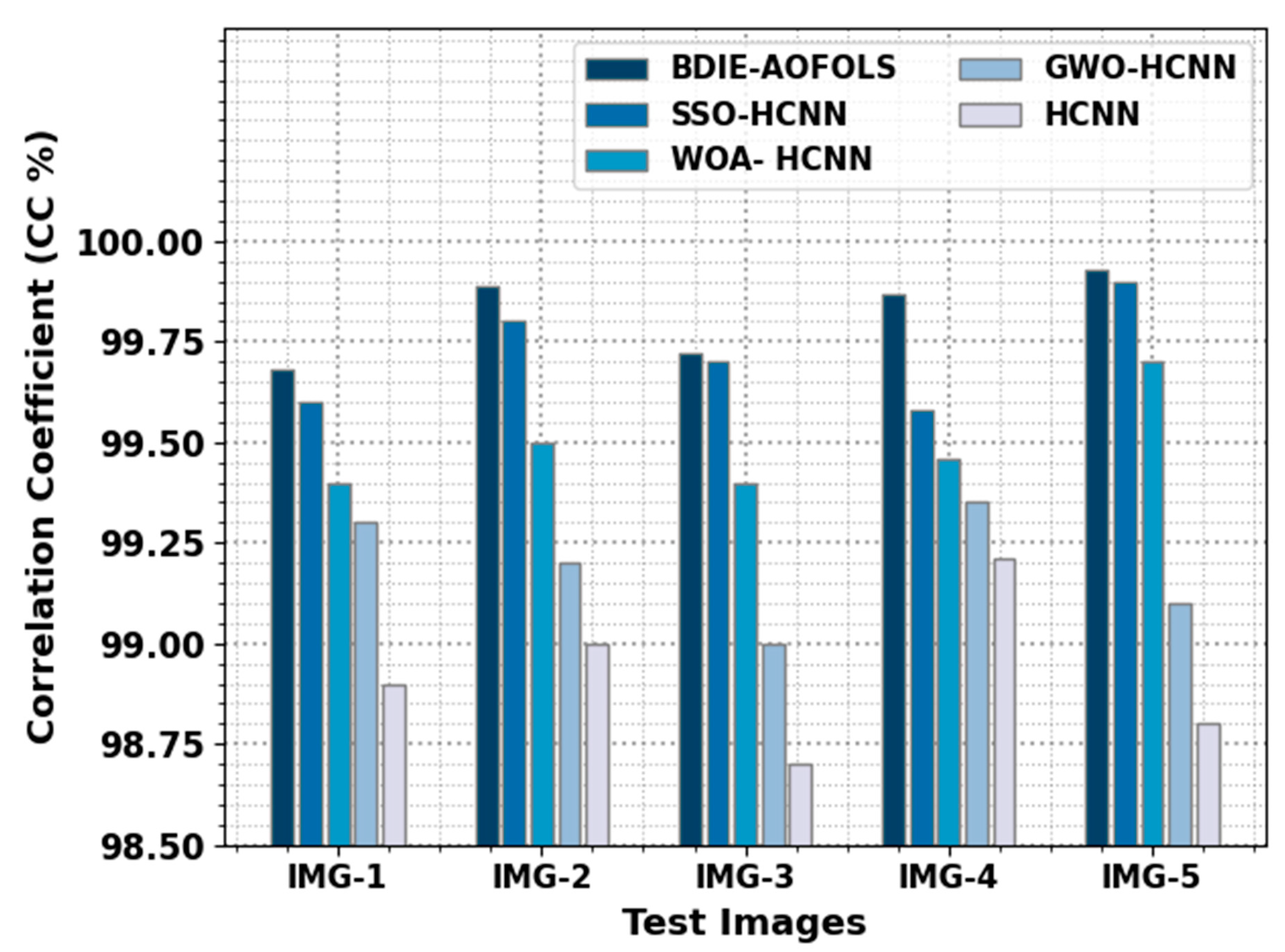
In
Table 4 and
Figure 7, a detailed CC comparison of the BDIE-AOFOLS approach with recent methods is given. The obtained values show the superior performance of the BDIE-AOFOLS method, with improved CC values. For example, for IMG-1, the BDIE-AOFOLS technique accomplished an enhanced CC value of 99.68%, while the SSOHCNN, WOAHCNN, GWOHCNN, and HCNN methods obtained decreased CC values of 99.60%, 99.40%, 99.30%, and 98.90%, respectively. Meanwhile, for IMG-3, the BDIE-AOFOLS approach achieved an enhanced CC value of 99.72%, while the SSOHCNN, WOAHCNN, GWOHCNN, and HCNN methods showed decreased CC values of 99.58%, 99.46%, 99.35%, and 99.21%, accordingly. Eventually, for IMG-5, the BDIE-AOFOLS method accomplished an enhanced CC value of 99.93%, while the SSOHCNN, WOAHCNN, GWOHCNN, and HCNN methods obtained decreased CC values of 99.90%, 99.70%, 99.10%, and 98.80%, respectively.
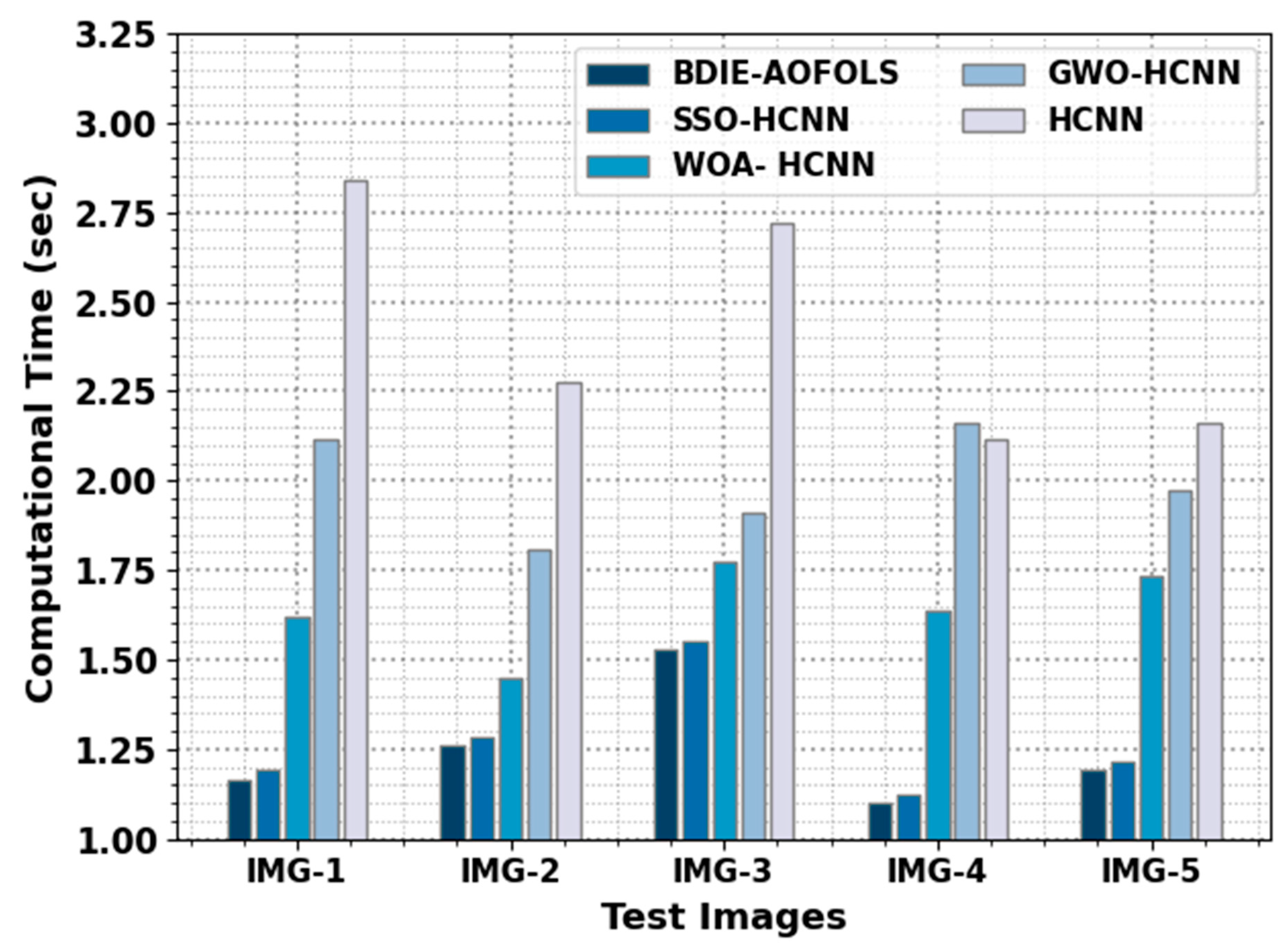
A comparative analysis of the BDIE-AOFOLS with existing methods in terms of CT is reported in
Table 5 and
Figure 8. The results represent the improvised outcomes of the BDIE-AOFOLS approach, with minimal values of MSE. For example, for IMG-1, the BDIE-AOFOLS method reached a reduced CT value of 1.164 s, while the SSOHCNN, WOAHCNN, GWOHCNN, and HCNN methods resulted in increased CT values of 1.192 s, 1.619 s, 2.117 s, and 2.837 s, respectively. In addition, for IMG-3, the BDIE-AOFOLS method attained a reduced CT value of 1.528 s, while the SSOHCNN, WOAHCNN, GWOHCNN, and HCNN methods resulted in increased CT values of 1.549 s, 1.774 s, 1.910 s, and 2.718 s, respectively.
Finally, for IMG-5, the BDIE-AOFOLS method attains a reduced CT value of 1.190 s, while the SSOHCNN, WOAHCNN, GWOHCNN, and HCNN methods have resulted in increased CT values of 1.214 s, 1.736 s, 1.973 s, and 2.161 s, respectively. These results emphasized the improvement offered by the suggested technique over other existing models. The proposed image encryption with BC offers several benefits, including enhanced security, transparency, and tamper-proof storage. It is particularly useful for protecting sensitive images in virtual environments where the confidentiality and integrity of data are critical.