Elliptic Curve Cryptography-Based Scheme for Secure Signaling and Data Exchanges in Precision Agriculture
Abstract
1. Introduction
1.1. Contributions
- A lightweight authentication scheme based on elliptic curve cryptography is developed for secure message exchange among the communicating smart devices in precision agriculture.
- Formal security analysis is carried out using BAN logic to demonstrate that a session key is derived from enciphering the exchanged data between the farmers and the agricultural service providers.
- Extensive semantic analysis is executed to show that the proposed scheme can withstand side-channeling, physical capture, eavesdropping, password guessing, spoofing, forgery, replay, session hijacking, impersonation, de-synchronization, man-in-the-middle, privileged insider, denial of service, stolen smart device, and known session-specific temporary information attacks. In addition, this protocol is demonstrated to support user privacy, anonymity, unlinkability, untraceability, robust authentication, session key agreement, and key secrecy and does not require the deployment of verifier tables.
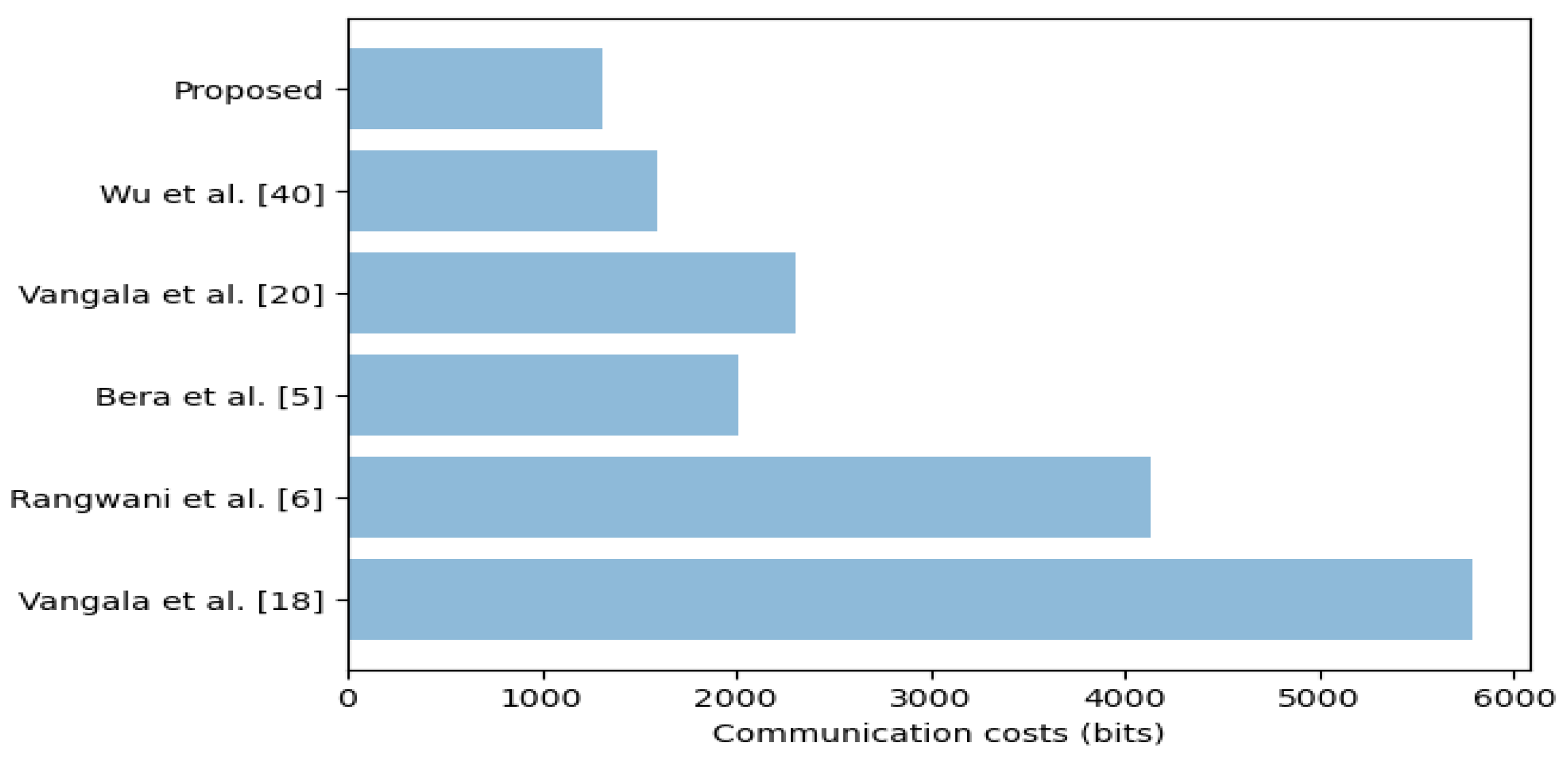
- An elaborate performance evaluation is carried out to show that our scheme yields 14.67% and 18% reductions in computation and communication costs, respectively, and a 35.29% improvement in supported security features.
1.2. Problem Definition and Motivation
1.3. Security Requirements
1.4. Threat Modeling
2. Related Work
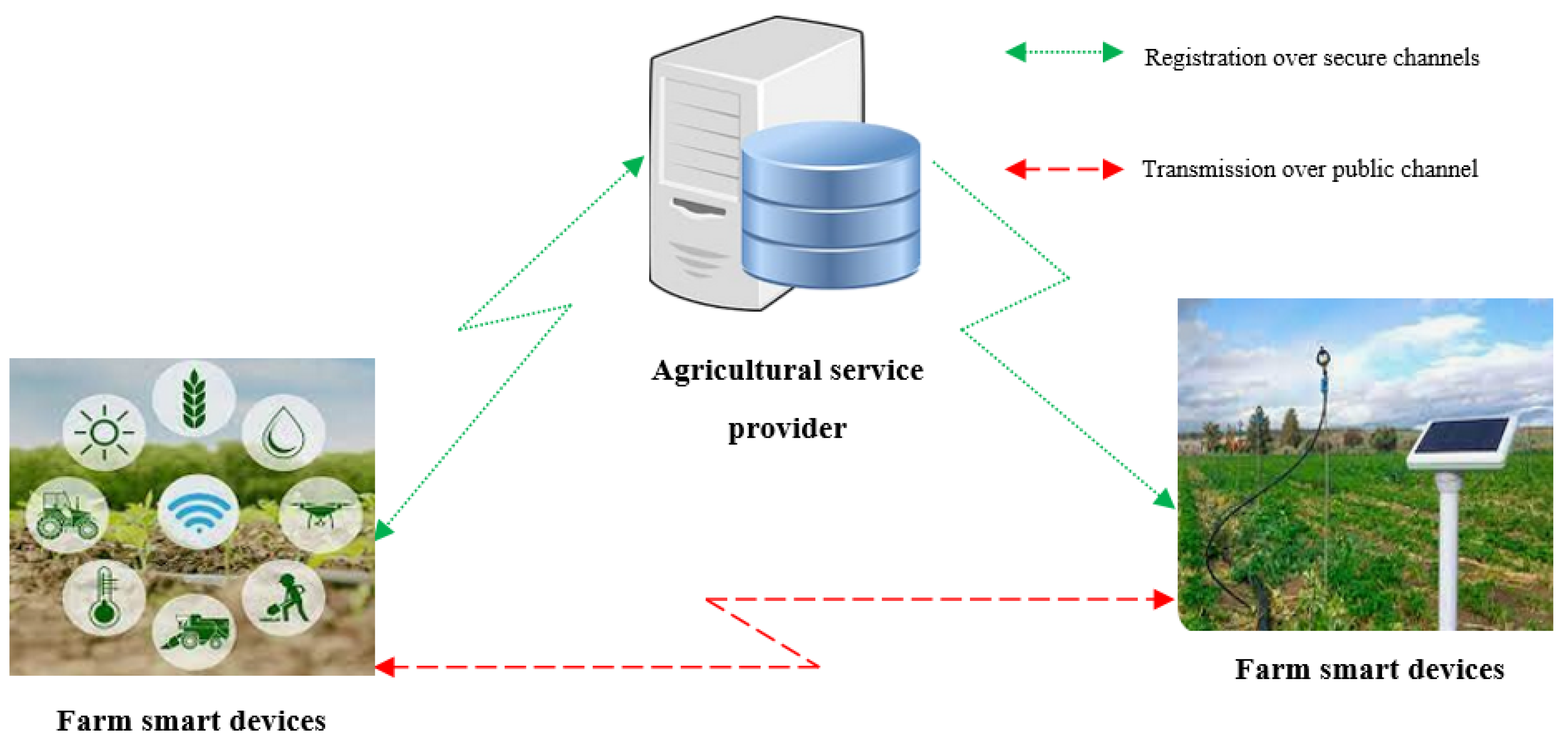
3. The Proposed Scheme
3.1. System Initialization
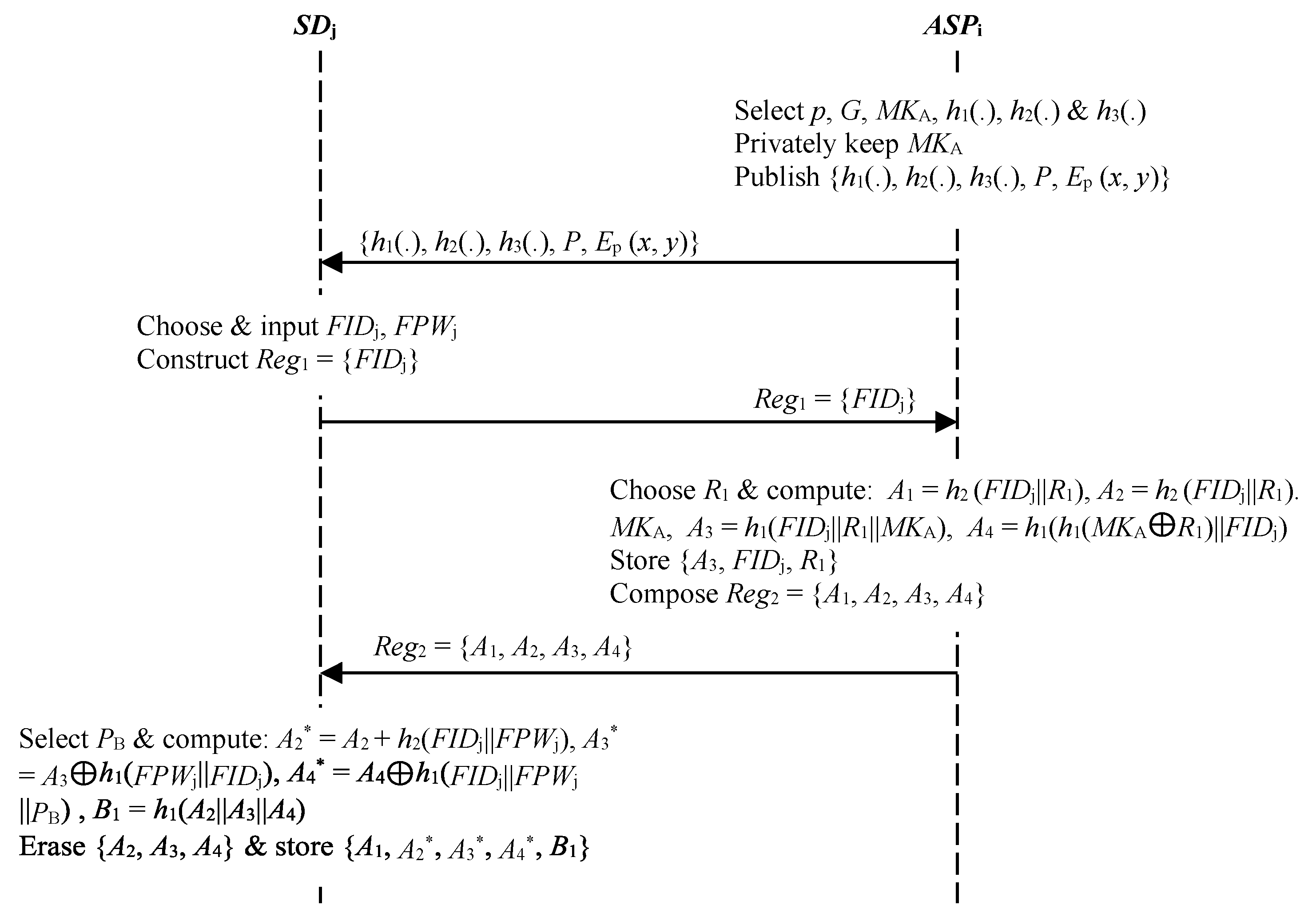
3.2. Registration Phase
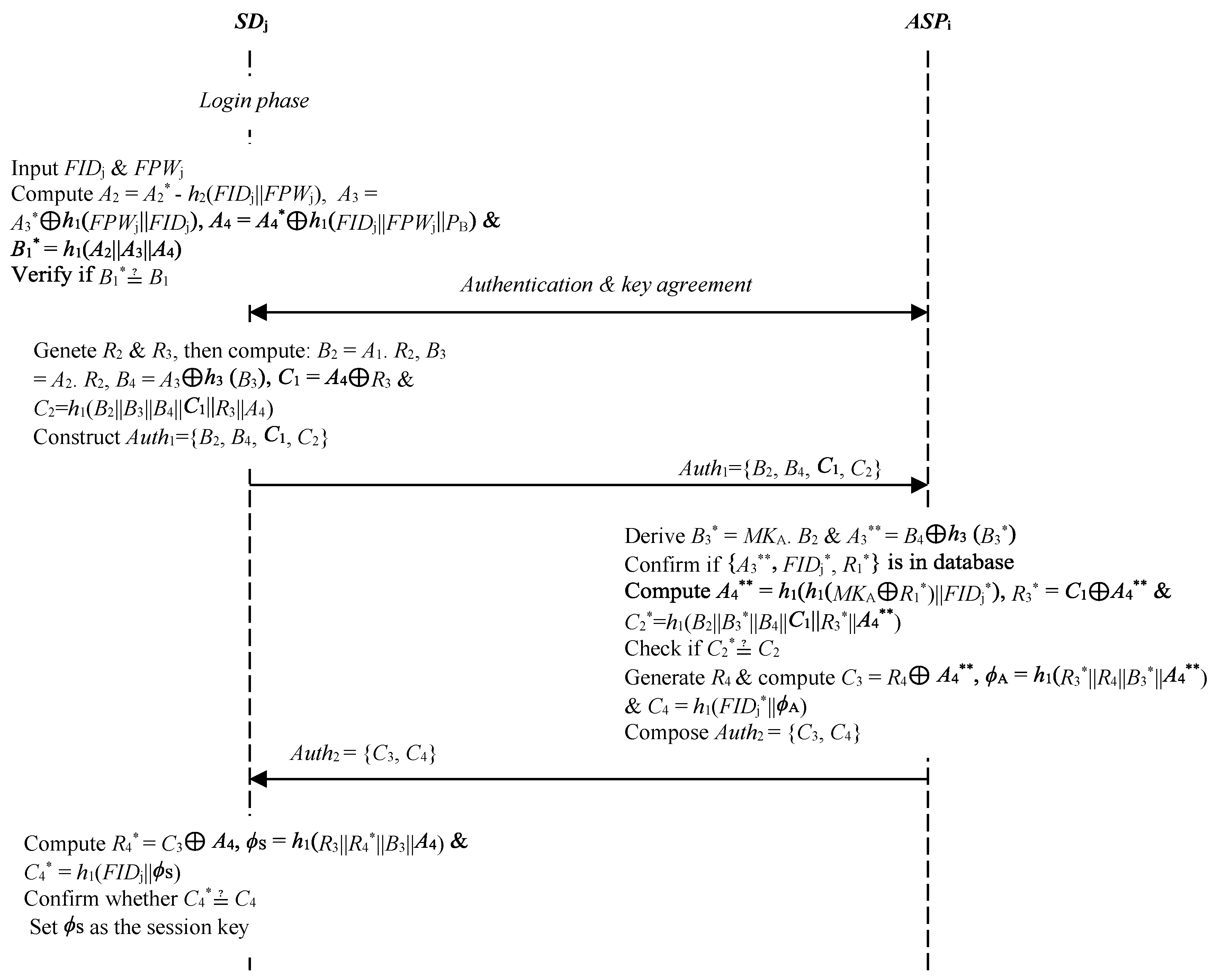
3.3. Login
3.4. Authentication and Key Agreement
3.5. Password Renewal Phase
4. Security Analysis
4.1. Formal Security Analysis
- IA1: Fj |≡ R2;
- IA2: Fj |≡ R3;
- IA3: Fj |≡ B2;
- IA4: Fj |≡ B3;
- IA5: Fj |≡ FjASPi;
- IA6: Fj |≡ ASPi(R4);
- IA7: ASPi |≡ B2;
- IA8: ASPi |≡ MKA;
- IA9: ASPi |≡ R4;
- IA10: ASPi |≡ FjASPi;
- IA11: ASPi |≡ Fj(R3, B2).
4.2. Semantic Security Analysis
5. Performance Evaluation
5.1. Computation Costs
5.2. Communication Costs
5.3. Security Characteristics
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Vangala, A.; Das, A.K.; Mitra, A.; Das, S.K.; Park, Y. Blockchain-Enabled Authenticated Key Agreement Scheme for Mobile Vehicles-Assisted Precision Agricultural IoT Networks. IEEE Trans. Inf. Forensics Secur. 2022, 18, 904–919. [Google Scholar] [CrossRef]
- Shafi, U.; Mumtaz, R.; García-Nieto, J.; Hassan, S.A.; Zaidi, S.A.R.; Iqbal, N. Precision Agriculture Techniques and Practices: From Considerations to Applications. Sensors 2019, 19, 3796. [Google Scholar] [CrossRef] [PubMed]
- Shi, X.; An, X.; Zhao, Q.; Liu, H.; Xia, L.; Sun, X.; Guo, Y. State-of-the-Art Internet of Things in Protected Agriculture. Sensors 2019, 19, 1833. [Google Scholar] [CrossRef]
- Vangala, A.; Das, A.K.; Chamola, V.; Korotaev, V.; Rodrigues, J.J. Security in IoT-enabled smart agriculture: Architecture, security solutions and challenges. Cluster Comput. 2022, 26, 879–902. [Google Scholar] [CrossRef]
- Bera, B.; Vangala, A.; Das, A.K.; Lorenz, P.; Khan, M.K. Private blockchain-envisioned drones-assisted authentication scheme in IoT-enabled agricultural environment. Comput. Stand. Interfaces 2022, 80, 103567. [Google Scholar] [CrossRef]
- Rangwani, D.; Sadhukhan, D.; Ray, S.; Khan, M.K.; Dasgupta, M. An improved privacy preserving remote user authentication scheme for agricultural wireless sensor network. Trans. Emerg. Telecommun. Technol. 2021, 32, e4218. [Google Scholar] [CrossRef]
- Lan, G.; Brewster, C.; Spek, J.; Smeenk, A.; Top, J. Blockchain for Agriculture and Food; Findings from the Pilot Study, Report; Wageningen Economic Research: Wageningen, The Netherlands, 2017; p. 34. [Google Scholar]
- Nyangaresi, V.O.; Ibrahim, A.; Abduljabbar, Z.A.; Hussain, M.A.; Al Sibahee, M.A.; Hussien, Z.A.; Ghrabat, M.J.J. Provably Secure Session Key Agreement Protocol for Unmanned Aerial Vehicles Packet Exchanges. In Proceedings of the 2021 International Conference on Electrical, Computer and Energy Technologies (ICECET), Cape Town, South Africa, 9–10 December 2021; pp. 1–6. [Google Scholar]
- Sontowski, S.; Gupta, M.; Chukkapalli, S.S.L.; Abdelsalam, M.; Mittal, S.; Joshi, A.; Sandhu, R. Cyber attacks on smart farming infrastructure. In Proceedings of the 2020 IEEE 6th International Conference on Collaboration and Internet Computing (CIC), Atlanta, GA, USA, 1–3 December 2020; pp. 135–143. [Google Scholar]
- Khanna, A.; Kaur, S. Evolution of Internet of Things (IoT) and its significant impact in the field of Precision Agriculture. Comput. Electron. Agric. 2019, 157, 218–231. [Google Scholar] [CrossRef]
- Van der Merwe, D.; Burchfield, D.R.; Witt, T.D.; Price, K.P.; Sharda, A. Drones in agriculture. Adv. Agron. 2020, 162, 1–30. [Google Scholar]
- Dagar, R.; Som, S.; Khatri, S.K. Smart farming–IoT in agriculture. In Proceedings of the 2018 International Conference on Inventive Research in Computing Applications (ICIRCA), Coimbatore, India, 11–12 July 2018; pp. 1052–1056. [Google Scholar]
- Sanjeevi, P.; Prasanna, S.; Kumar, B.S.; Gunasekaran, G.; Alagiri, I.; Anand, R.V. Precision agriculture and farming using Internet of Things based on wireless sensor network. Trans. Emerg. Telecommun. Technol. 2020, 31, e3978. [Google Scholar] [CrossRef]
- Nyangaresi, V.O.; Abduljabbar, Z.A.; Refish, S.H.A.; Al Sibahee, M.A.; Abood, E.W.; Lu, S. Anonymous Key Agreement and Mutual Authentication Protocol for Smart Grids. In Cognitive Radio Oriented Wireless Networks and Wireless Internet, Proceedings of the 16th EAI International Conference, CROWNCOM 2021, Virtual Event, 11 December 2021, and 14th EAI International Conference, WiCON 2021, Virtual Event, 9 November 2021; Springer International Publishing: Cham, Switzerland, 2022; pp. 325–340. [Google Scholar]
- Wazid, M.; Das, A.K.; Bhat, V.; Vasilakos, A.V. LAM-CIoT: Lightweight authentication mechanism in cloud-based IoT environment. J. Netw. Comput. Appl. 2020, 150, 102496. [Google Scholar] [CrossRef]
- Wang, D.; Li, W.; Wang, P. Measuring Two-Factor Authentication Schemes for Real-Time Data Access in Industrial Wireless Sensor Networks. IEEE Trans. Ind. Inform. 2018, 14, 4081–4092. [Google Scholar] [CrossRef]
- Challa, S.; Das, A.K.; Gope, P.; Kumar, N.; Wu, F.; Vasilakos, A.V. Design and analysis of authenticated key agreement scheme in cloud-assisted cyber–physical systems. Futur. Gener. Comput. Syst. 2018, 108, 1267–1286. [Google Scholar] [CrossRef]
- Vangala, A.; Das, A.K.; Lee, J. Provably secure signature-based anonymous user authentication protocol in an Internet of Things-enabled intelligent precision agricultural environment. Concurr. Comput. Prac. Exp. 2021, 35, e6187. [Google Scholar] [CrossRef]
- Alsamhi, S.H.; Shvetsov, A.V.; Kumar, S.; Shvetsova, S.V.; Alhartomi, M.A.; Hawbani, A.; Rajput, N.S.; Srivastava, S.; Saif, A.; Nyangaresi, V.O. UAV Computing-Assisted Search and Rescue Mission Framework for Disaster and Harsh Environment Mitigation. Drones 2022, 6, 154. [Google Scholar] [CrossRef]
- Vangala, A.; Sutrala, A.K.; Das, A.K.; Jo, M. Smart Contract-Based Blockchain-Envisioned Authentication Scheme for Smart Farming. IEEE Internet Things J. 2021, 8, 10792–10806. [Google Scholar] [CrossRef]
- Akram, S.V.; Malik, P.K.; Singh, R.; Anita, G.; Tanwar, S. Adoption of blockchain technology in various realms: Opportunities and challenges. Secur. Priv. 2020, 3, e109. [Google Scholar] [CrossRef]
- Lin, Y.-P.; Petway, J.R.; Anthony, J.; Mukhtar, H.; Liao, S.-W.; Chou, C.-F.; Ho, Y.-F. Blockchain: The Evolutionary Next Step for ICT E-Agriculture. Environments 2017, 4, 50. [Google Scholar] [CrossRef]
- Almadhoun, R.; Kadadha, M.; Alhemeiri, M.; Alshehhi, M.; Salah, K. A user authentication scheme of IoT devices using blockchain-enabled fog nodes. In Proceedings of the 2018 IEEE/ACS 15th international conference on computer systems and applications (AICCSA), Aqaba, Jordan, 28 October–1 November 2018; pp. 1–8. [Google Scholar]
- Wang, L.; Xu, L.; Zheng, Z.; Liu, S.; Li, X.; Cao, L.; Li, J.; Sun, C. Smart Contract-Based Agricultural Food Supply Chain Traceability. IEEE Access 2021, 9, 9296–9307. [Google Scholar] [CrossRef]
- Al Sibahee, M.A.; Nyangaresi, V.O.; Ma, J.; Abduljabbar, Z.A. Stochastic Security Ephemeral Generation Protocol for 5G Enabled Internet of Things. In IoT as a Service, Proceedings of the 7th EAI International Conference, IoTaaS 2021, Sydney, Australia, 13–14 December 2021; Springer International Publishing: Cham, Switzerland, 2022; pp. 3–18. [Google Scholar]
- Turkanović, M.; Brumen, B.; Hölbl, M. A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the Internet of Things notion. Ad Hoc Netw. 2014, 20, 96–112. [Google Scholar] [CrossRef]
- Chang, C.-C.; Le, H.-D. A Provably Secure, Efficient, and Flexible Authentication Scheme for Ad hoc Wireless Sensor Networks. IEEE Trans. Wirel. Commun. 2015, 15, 357–366. [Google Scholar] [CrossRef]
- Das, A.K.; Kumari, S.; Odelu, V.; Li, X.; Wu, F.; Huang, X. Provably secure user authentication and key agreement scheme for wireless sensor networks. Secur. Commun. Netw. 2016, 9, 3670–3687. [Google Scholar] [CrossRef]
- Shuai, M.; Xiong, L.; Wang, C.; Yu, N. A secure authentication scheme with forward secrecy for industrial internet of things using Rabin cryptosystem. Comput. Commun. 2020, 160, 215–227. [Google Scholar] [CrossRef]
- Tian, Y.; Yuan, J.; Song, H. Efficient privacy-preserving authentication framework for edge-assisted Internet of Drones. J. Inf. Secur. Appl. 2019, 48, 102354. [Google Scholar] [CrossRef]
- Chae, C.-J.; Cho, H.-J. Enhanced secure device authentication algorithm in P2P-based smart farm system. Peer-to-Peer Netw. Appl. 2018, 11, 1230–1239. [Google Scholar] [CrossRef]
- Nyangaresi, V.O.; Abduljabbar, Z.A.; Mutlaq, K.A.-A.; Ma, J.; Honi, D.G.; Aldarwish, A.J.Y.; Abduljaleel, I.Q. Energy Efficient Dynamic Symmetric Key Based Protocol for Secure Traffic Exchanges in Smart Homes. Appl. Sci. 2022, 12, 12688. [Google Scholar] [CrossRef]
- Wu, F.; Xu, L.; Kumari, S.; Li, X. A new and secure authentication scheme for wireless sensor networks with formal proof. Peer-to-Peer Netw. Appl. 2015, 10, 16–30. [Google Scholar] [CrossRef]
- Srinivas, J.; Mukhopadhyay, S.; Mishra, D. Secure and efficient user authentication scheme for multi-gateway wireless sensor networks. Ad Hoc Netw. 2017, 54, 147–169. [Google Scholar] [CrossRef]
- Zeng, X.; Xu, G.; Zheng, X.; Xiang, Y.; Zhou, W. E-AUA: An Efficient Anonymous User Authentication Protocol for Mobile IoT. IEEE Internet Things J. 2018, 6, 1506–1519. [Google Scholar] [CrossRef]
- Liu, C.-H.; Chung, Y.-F. Secure user authentication scheme for wireless healthcare sensor networks. Comput. Electr. Eng. 2017, 59, 250–261. [Google Scholar] [CrossRef]
- Nyangaresi, V.O.; Abduljabbar, Z.A.; Ma, J.; Al Sibahee, M.A. Verifiable Security and Privacy Provisioning Protocol for High Reliability in Smart Healthcare Communication Environment. In Proceedings of the 2022 4th Global Power, Energy and Communication Conference (GPECOM), Cappadocia, Turkey, 14–17 June 2022; pp. 569–574. [Google Scholar]
- Challa, S.; Das, A.K.; Odelu, V.; Kumar, N.; Kumari, S.; Khan, M.K.; Vasilakos, A.V. An efficient ECC-based provably secure three-factor user authentication and key agreement protocol for wireless healthcare sensor networks. Comput. Electr. Eng. 2018, 69, 534–554. [Google Scholar] [CrossRef]
- Ali, Z.; Ghani, A.; Khan, I.; Chaudhry, S.A.; Islam, S.H.; Giri, D. A robust authentication and access control protocol for securing wireless healthcare sensor networks. J. Inf. Secur. Appl. 2020, 52, 102502. [Google Scholar] [CrossRef]
- Wu, H.-T.; Tsai, C.-W. An intelligent agriculture network security system based on private blockchains. J. Commun. Netw. 2019, 21, 503–508. [Google Scholar] [CrossRef]
- Abduljaleel, I.Q.; Abduljabbar, Z.A.; Al Sibahee, M.A.; Ghrabat, M.J.J.; Ma, J.; Nyangaresi, V.O. A Lightweight Hybrid Scheme for Hiding Text Messages in Colour Images Using LSB, Lah Transform and Chaotic Techniques. J. Sens. Actuator Netw. 2022, 11, 66. [Google Scholar] [CrossRef]
- Tai, W.-L.; Chang, Y.-F.; Li, W.-H. An IoT notion–based authentication and key agreement scheme ensuring user anonymity for heterogeneous ad hoc wireless sensor networks. J. Inf. Secur. Appl. 2017, 34, 133–141. [Google Scholar] [CrossRef]
- Ali, R.; Pal, A.K.; Kumari, S.; Karuppiah, M.; Conti, M. A secure user authentication and key-agreement scheme using wireless sensor networks for agriculture monitoring. Futur. Gener. Comput. Syst. 2018, 84, 200–215. [Google Scholar] [CrossRef]
- He, D.; Zhang, Y.; Wang, D.; Choo, K.-K.R. Secure and Efficient Two-Party Signing Protocol for the Identity-Based Signature Scheme in the IEEE P1363 Standard for Public Key Cryptography. IEEE Trans. Dependable Secur. Comput. 2018, 17, 1124–1132. [Google Scholar] [CrossRef]
- Feng, Q.; He, D.; Liu, Z.; Wang, D.; Choo, K.K.R. Multi-party signing protocol for the identity-based signature scheme in IEEE P1363 standard. IET Inf. Secur. 2020, 1, 1–10. [Google Scholar]
- Nyangaresi, V.O. Terminal independent security token derivation scheme for ultra-dense IoT networks. Array 2022, 15, 100210. [Google Scholar] [CrossRef]
- Sadhukhan, D.; Ray, S.; Biswas, G.P.; Khan, M.K.; Dasgupta, M. A lightweight remote user authentication scheme for IoT communication using elliptic curve cryptography. J. Supercomput. 2020, 77, 1114–1151. [Google Scholar] [CrossRef]
- Dhillon, P.K.; Kalra, S. A lightweight biometrics based remote user authentication scheme for IoT services. J. Inf. Secur. Appl. 2017, 34, 255–270. [Google Scholar] [CrossRef]
- Chang, C.-C.; Nguyen, N.-T. An Untraceable Biometric-Based Multi-server Authenticated Key Agreement Protocol with Revocation. Wirel. Pers. Commun. 2016, 90, 1695–1715. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.H.; Kumar, N.; Choo, K.-K.R. An untraceable and anonymous password authentication protocol for heterogeneous wireless sensor networks. J. Netw. Comput. Appl. 2018, 104, 133–144. [Google Scholar] [CrossRef]
- Li, X.; Niu, J.; Alam Bhuiyan, Z.; Wu, F.; Karuppiah, M.; Kumari, S. A Robust ECC-Based Provable Secure Authentication Protocol With Privacy Preserving for Industrial Internet of Things. IEEE Trans. Ind. Inform. 2017, 14, 3599–3609. [Google Scholar] [CrossRef]
- Alotaibi, M. An Enhanced Symmetric Cryptosystem and Biometric-Based Anonymous User Authentication and Session Key Establishment Scheme for WSN. IEEE Access 2018, 6, 70072–70087. [Google Scholar] [CrossRef]
- Moghadam, M.F.; Nikooghadam, M.; Al Jabban, M.A.B.; Alishahi, M.; Mortazavi, L.; Mohajerzadeh, A. An Efficient Authentication and Key Agreement Scheme Based on ECDH for Wireless Sensor Network. IEEE Access 2020, 8, 73182–73192. [Google Scholar] [CrossRef]
- Fadi, A.T.; Deebak, B.D. Seamless authentication: For IoT-big data technologies in smart industrial application systems. IEEE Trans. Ind. Inform. 2020, 17, 2919–2927. [Google Scholar]
| Symbol | Description |
|---|---|
| ASPi | Agricultural service provider i |
| MKA | Master key for ASPi |
| Fj | Farmer j |
| SDj | Smart device for Fj |
| FIDj | Unique identity for Fj |
| FPWj | Login password for Fj |
| Ri | Random nonce i |
| || | Concatenation operation |
| PB | Padding bits |
| ⊕ | XOR operation |
| ϕA | Session key computed at ASPi |
| ϕS | Session key computed at SDj |
| Feature | Description |
|---|---|
| Operating system | Ubuntu 22.04 LTS |
| RAM | 8 GB |
| Processor | Intel Core i7-8565U |
| Operating system type | 64-bit |
| Clock frequency | 3.2 GHz |
| Feature | Description |
|---|---|
| Operating system | Ubuntu 20.04 LTS |
| RAM | 1 GB |
| Processor | Quad-core |
| Operating system type | 64 bit |
| Clock frequency | 1.4 GHz |
| Cryptographic Operation | Time (ms) | |
|---|---|---|
| SDj | ASPi | |
| Hashing operation (TH) | 0.314 | 0.056 |
| Bilinear pairing (TBP) | 33.051 | 4.715 |
| Elliptic curve scalar multiplications (TSM) | 2.256 | 0.654 |
| Symmetric encryption/Decryption (TED) | 0.019 | 0.002 |
| Elliptic curve point subtraction (TPS) | 0.0115 | 0.003 |
| Modular exponentiation (TME) | 0.325 | 0.083 |
| Modular multiplication (TMM) | 0.015 | 0.002 |
| Modular addition (TMA) | 0.012 | 0.001 |
| Fuzzy extraction (TFE) | 2.253 | 0.674 |
| t-degree univariate polynomial evaluation (TPL) | 13.3 | 0.3 |
| Map-to-point hashing (TMTP) | 5.264 | 2.853 |
| Elliptic curve point addition (TPA) | 0.017 | 0.004 |
| Scheme | Derivations | Total (ms) | |
|---|---|---|---|
| User/Smart Device/Sensor | Server/Gateway Node | ||
| Vangala et al. [18] | 22 TH +8 TSM+ 2 TPA+ TFE = 27.243 | 12 TH +6 TSM+ 2 TPA = 4.604 | 31.847 |
| Rangwani et al. [6] | 8 TH +5 TSM = 13.792 | 7 TH +TSM = 1.046 | 14.838 |
| Bera et al. [5] | 7 TH + 6 TSM + 2 TPA + TPL = 29.068 | 7 TH + 6 TSM + 2 TPA + TPL = 4.624 | 33.692 |
| Vangala et al. [20] | 9 TH + 4 TSM = 11.85 | 9 TH + 4 TSM = 3.12 | 14.970 |
| Wu et al. [40] | 2 TBP + 2 TME + 2 TED + TH = 67.446 | 2 TBP + 2 TME + 2 TED + TH = 9.656 | 77.102 |
| Proposed | TMTP + 6 TH + 2 TSM + TPS = 11.672 | TSM + 6 TH = 0.99 | 12.662 |
| Operation | Size (bits) |
|---|---|
| Real identity | 160 |
| Random nonce | 160 |
| Hashing output | 256 |
| Points in finite group | 512 |
| Timestamp | 32 |
| Password | 160 |
| Message | Size (bits) |
|---|---|
| SDj → ASPi Auth1:{B2, B4, C1, C2} B4 = C1 = C2 = 160; B2 = 512 | 992 |
| ASPi → SDj Auth2: {C3, C4} C3 = C4 = 160 | 320 |
| Total | 1312 |
| Scheme | Number of Exchanged Messages | Size (bits) |
|---|---|---|
| Vangala et al. [18] | 4 | 5792 |
| Rangwani et al. [6] | 5 | 4128 |
| Bera et al. [5] | 2 | 2016 |
| Vangala et al. [20] | 3 | 2305 |
| Wu et al. [40] | 10 | 1600 |
| Proposed | 2 | 1312 |
| [18] | [6] | [5] | [20] | [40] | Proposed | |
|---|---|---|---|---|---|---|
| Security features | ||||||
| User privacy | √ | √ | - | √ | √ | √ |
| Anonymity | √ | √ | - | √ | √ | √ |
| Unlinkability | - | - | - | - | - | √ |
| Untraceability | √ | √ | - | √ | √ | √ |
| Robust authentication | √ | √ | √ | √ | √ | √ |
| No verifier tables | × | √ | √ | × | - | √ |
| Session key agreement | √ | √ | √ | √ | √ | √ |
| Key secrecy | √ | √ | √ | - | - | √ |
| Robust against: | ||||||
| Side-channeling | √ | √ | √ | √ | × | √ |
| Physical capture | √ | √ | √ | √ | × | √ |
| Eavesdropping | × | × | √ | × | × | √ |
| Password guessing | √ | √ | × | × | √ | √ |
| Spoofing | × | × | × | × | × | √ |
| Forgery | × | × | √ | × | × | √ |
| Replay | √ | √ | √ | √ | √ | √ |
| Session hijacking | × | × | × | × | × | √ |
| Impersonation | √ | √ | √ | √ | × | √ |
| De-synchronization | × | × | × | × | × | √ |
| MitM | √ | √ | √ | √ | √ | √ |
| Privileged insider | √ | √ | √ | √ | √ | √ |
| KSSTI | × | √ | √ | √ | × | √ |
| DoS | √ | √ | - | √ | √ | √ |
| Stolen smart device | √ | √ | √ | √ | × | √ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Abduljabbar, Z.A.; Nyangaresi, V.O.; Jasim, H.M.; Ma, J.; Hussain, M.A.; Hussien, Z.A.; Aldarwish, A.J.Y. Elliptic Curve Cryptography-Based Scheme for Secure Signaling and Data Exchanges in Precision Agriculture. Sustainability 2023, 15, 10264. https://doi.org/10.3390/su151310264
Abduljabbar ZA, Nyangaresi VO, Jasim HM, Ma J, Hussain MA, Hussien ZA, Aldarwish AJY. Elliptic Curve Cryptography-Based Scheme for Secure Signaling and Data Exchanges in Precision Agriculture. Sustainability. 2023; 15(13):10264. https://doi.org/10.3390/su151310264
Chicago/Turabian StyleAbduljabbar, Zaid Ameen, Vincent Omollo Nyangaresi, Hend Muslim Jasim, Junchao Ma, Mohammed Abdulridha Hussain, Zaid Alaa Hussien, and Abdulla J. Y. Aldarwish. 2023. "Elliptic Curve Cryptography-Based Scheme for Secure Signaling and Data Exchanges in Precision Agriculture" Sustainability 15, no. 13: 10264. https://doi.org/10.3390/su151310264
APA StyleAbduljabbar, Z. A., Nyangaresi, V. O., Jasim, H. M., Ma, J., Hussain, M. A., Hussien, Z. A., & Aldarwish, A. J. Y. (2023). Elliptic Curve Cryptography-Based Scheme for Secure Signaling and Data Exchanges in Precision Agriculture. Sustainability, 15(13), 10264. https://doi.org/10.3390/su151310264