About the New Methodology and XAI-Based Software Toolkit for Risk Assessment
Abstract
1. Introduction
2. Risk Approach
- Risk is the measure of probability and the weight of undesired consequences [4].
- Risk equals the triplet (si, pi, ci), where si is the set of scenarios, pi is the likelihood of that scenario, and ci is the consequence of the scenario, i = 1, 2, …, N [5].
- Risk equals the product of probability and severity [6].
- According to critics, risk means different things to different people [7].
- Risk is the likelihood of adverse effects predicting the possible consequences of exposure to a particular threat in a particular hazardous area over time [8].
- Risk is a combination of five primitives: outcome, likelihood, significance, causal scenario, and population affected [9].
- Risk is a situation or event where something of human value (including humans themselves) has been put at stake and where the outcome is uncertain [10].
- A “risk triangle” consists of three components: threat, openness, and vulnerability [11].
- Risk is the expression of influence and possibility of an accident in the sense of the severity of the potential accident and the probability of the event [12].
- Risk is a combination of the probability and scope of the consequences [13].
- Risk equals expected damage [14].
- The concept of risk is incorporated into so many different disciplines, starting with engineering and ending with portfolio theory, so it should come as no surprise that it is defined in different ways [15].
- Risk refers to uncertainty about and severity of the events and consequences (or outcomes) of an activity with respect to something that humans value [16].
- Risk is the effect of uncertainty on objectives [2].
- The simplest, most widely used definition of risk, used by many risk managers, is described by the equation: risk is the probability of an event occurring multiplied by the consequences of an event that has already occurred [17].
- Risk is an important concept in a number of scientific fields, yet there is no consensus on how it is to be defined and interpreted [18].
- The concept of risk is used in various fields of science. In each of them, the risk concept has topics, directions, and methods used [19].
- Risk is a word that causes the feeling of urgency, because it addresses detrimental, sometimes catastrophic, outcomes. If you asked ten different people what they imply by the word risk, you would probably get ten different answers [20].
- The risk concept indicates a complex state that, at least in modern society, is a normal aspect of life [21].
- The Oxford English Dictionary definition of risk is as follows: “a chance or possibility of danger, loss, injury or other adverse consequences”, and the definition of at risk is “exposed to danger”. In this context, risk is used to signify negative consequences. However, taking a risk can also result in a positive outcome. A third possibility is that risk is related to the uncertainty of an outcome [22].
- The community needs to take risks, all forms of human activity carry risks, and there is no such thing as “risk-free” [23].
- In general, there are two basic approaches to risk assessment: [24].
- a.
- Objective risk assessment, where all factors influencing its occurrence are measurable and can be identified and quantified.
- b.
- Subjective risk assessment, where the factors that lead to the occurrence of risk can be difficult to quantify and measure with exact mathematical methods.
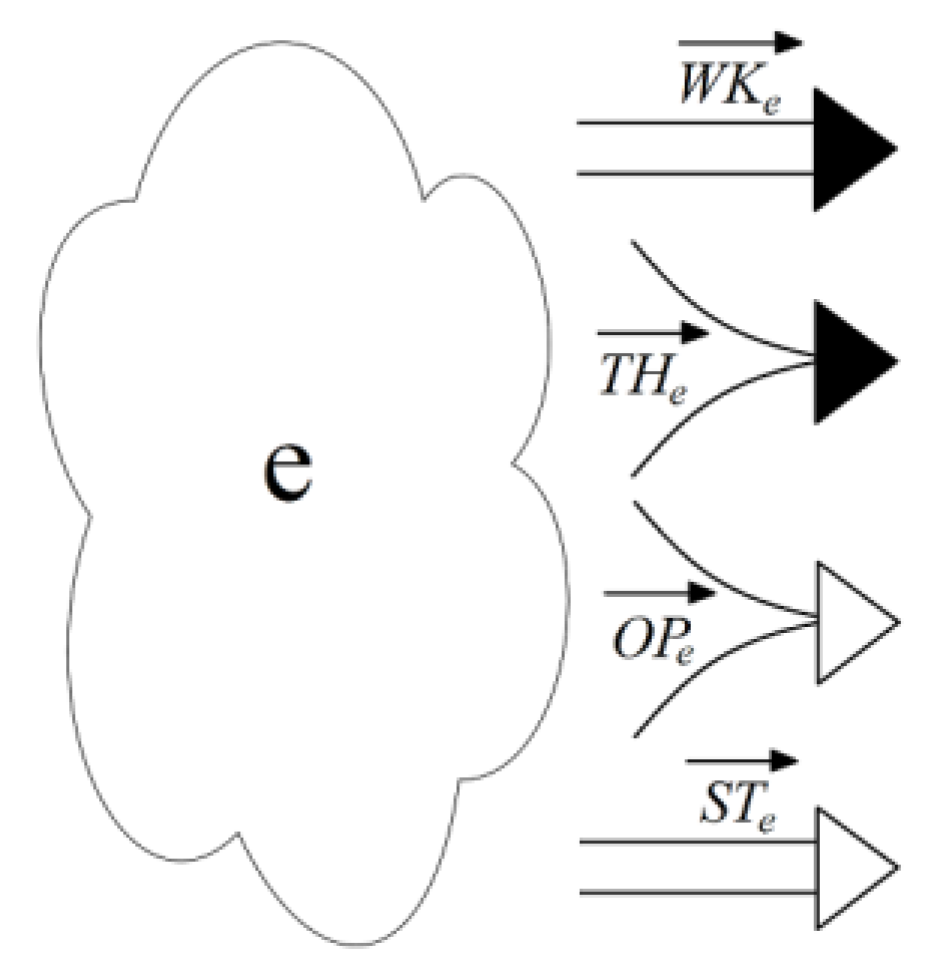
- Opportunities (OP)—profit, achievements, and positive results.
- Threats (TH)—losses, damage, and negative results.
- Efforts (EFF)—investment, labor cost, and contributions.
- Hesitancies (HES)—uncertainties, randomness, possibilities, probabilities, and level of doubts related to incomplete or inaccurate information or its probabilistic nature.
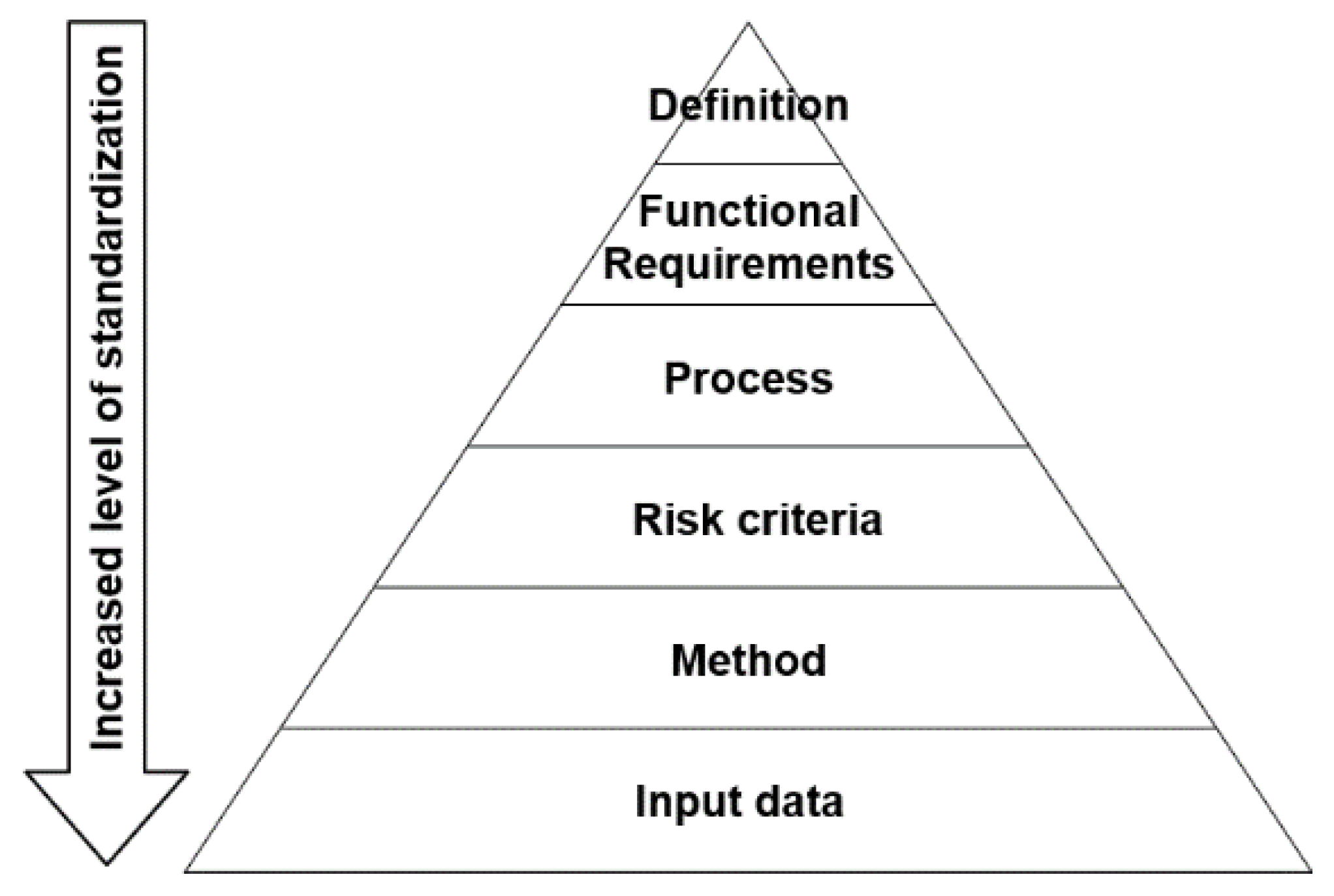
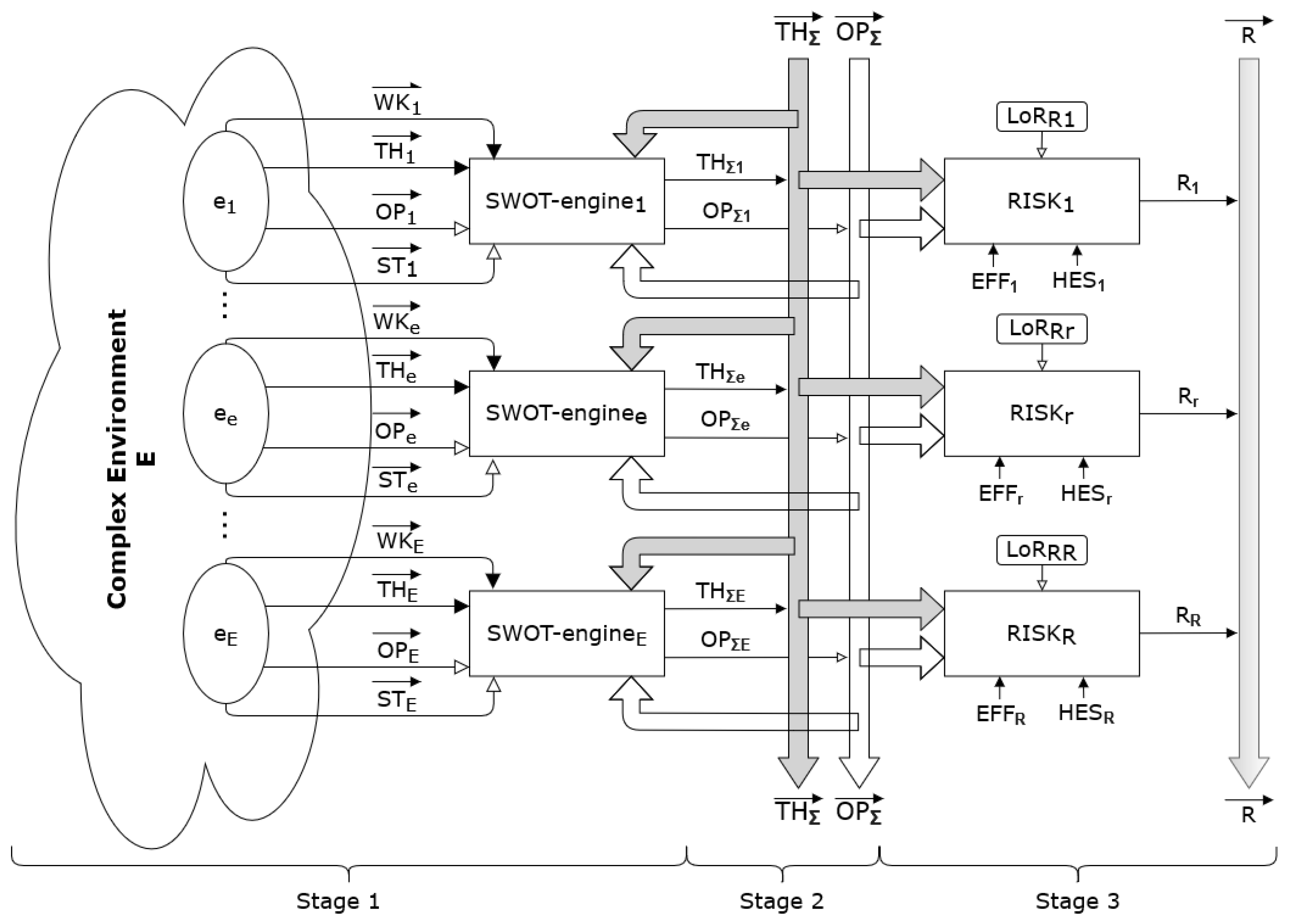
3. Functional Organization
4. Implementation of Risk Assessment System
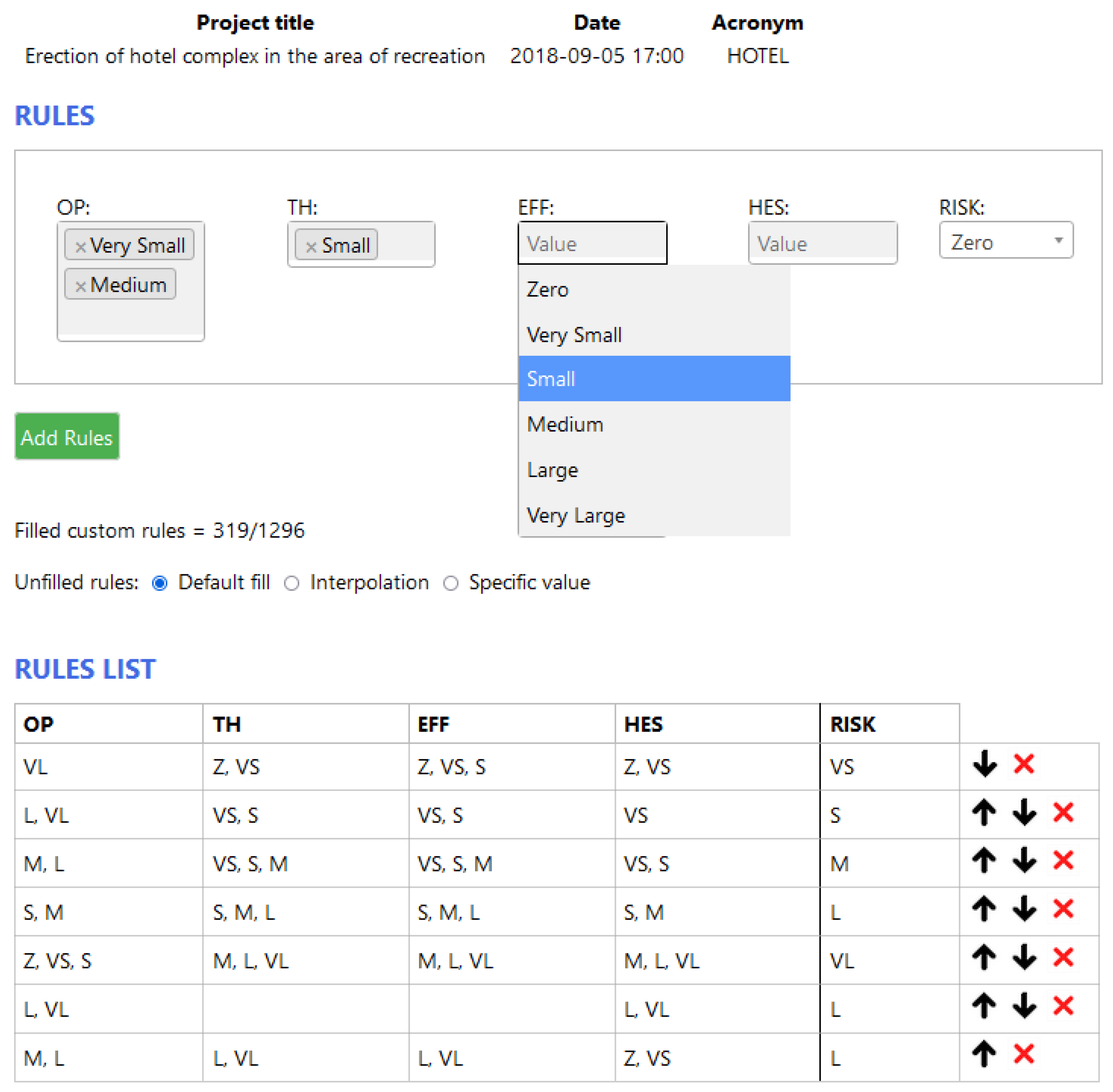
- Default fill—The entire rule block is already filled with default precalculated risk values, and only those that are specified will be overridden.
- Interpolation—Missing rules in the block are interpolated according to the entered values.
- Specific value—User enters a specific risk value for the undefined rules.
| Algorithmic 1. Risk estimation |
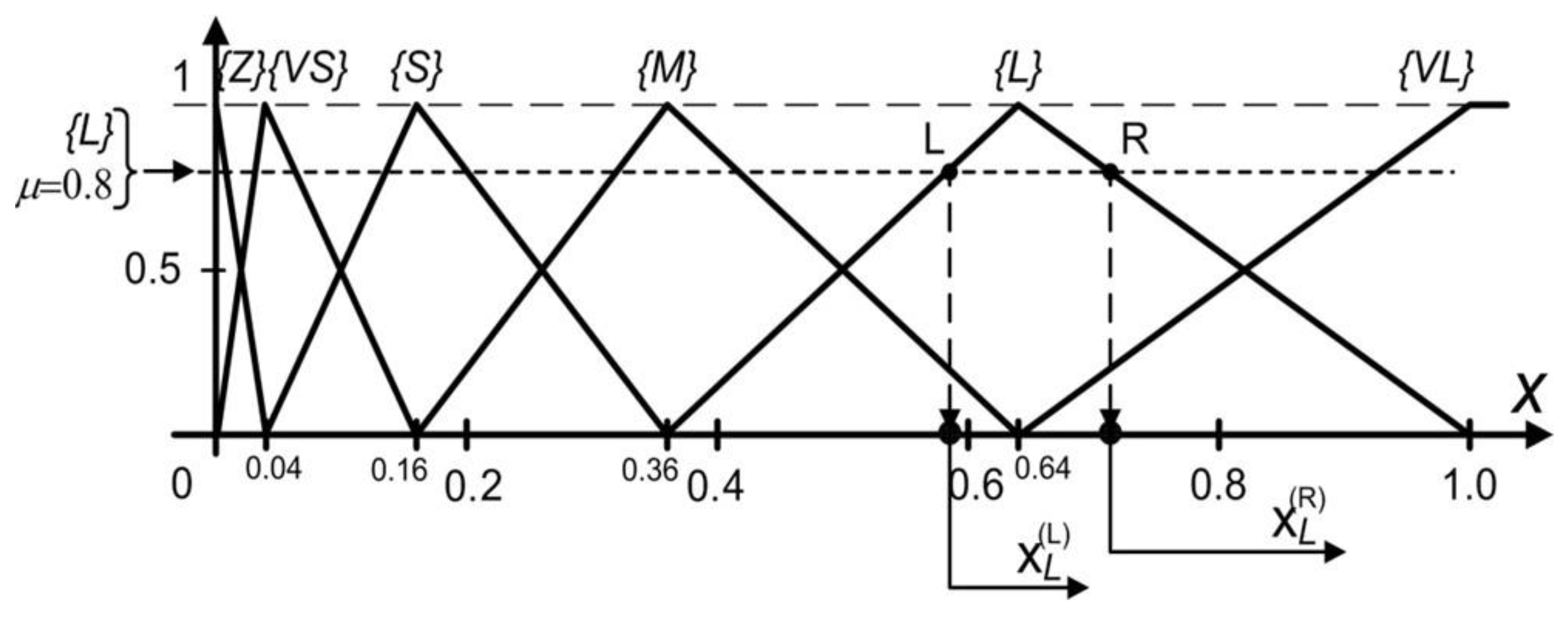
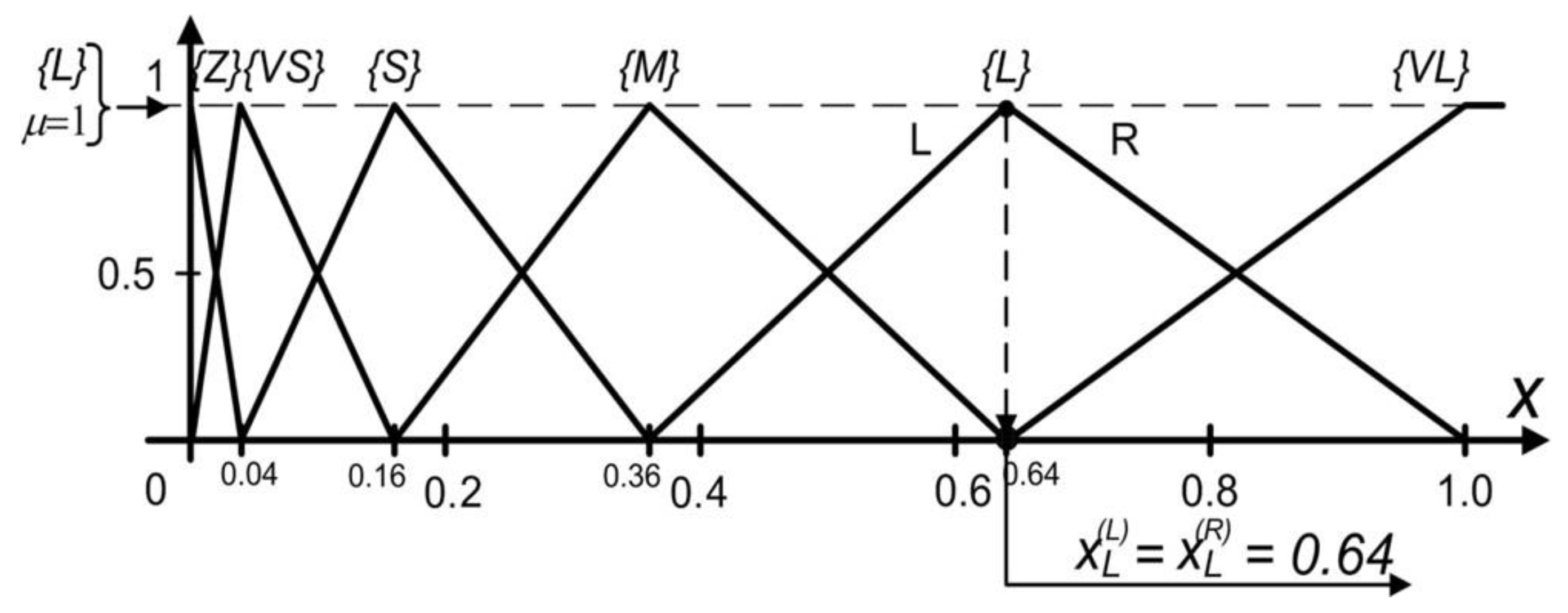
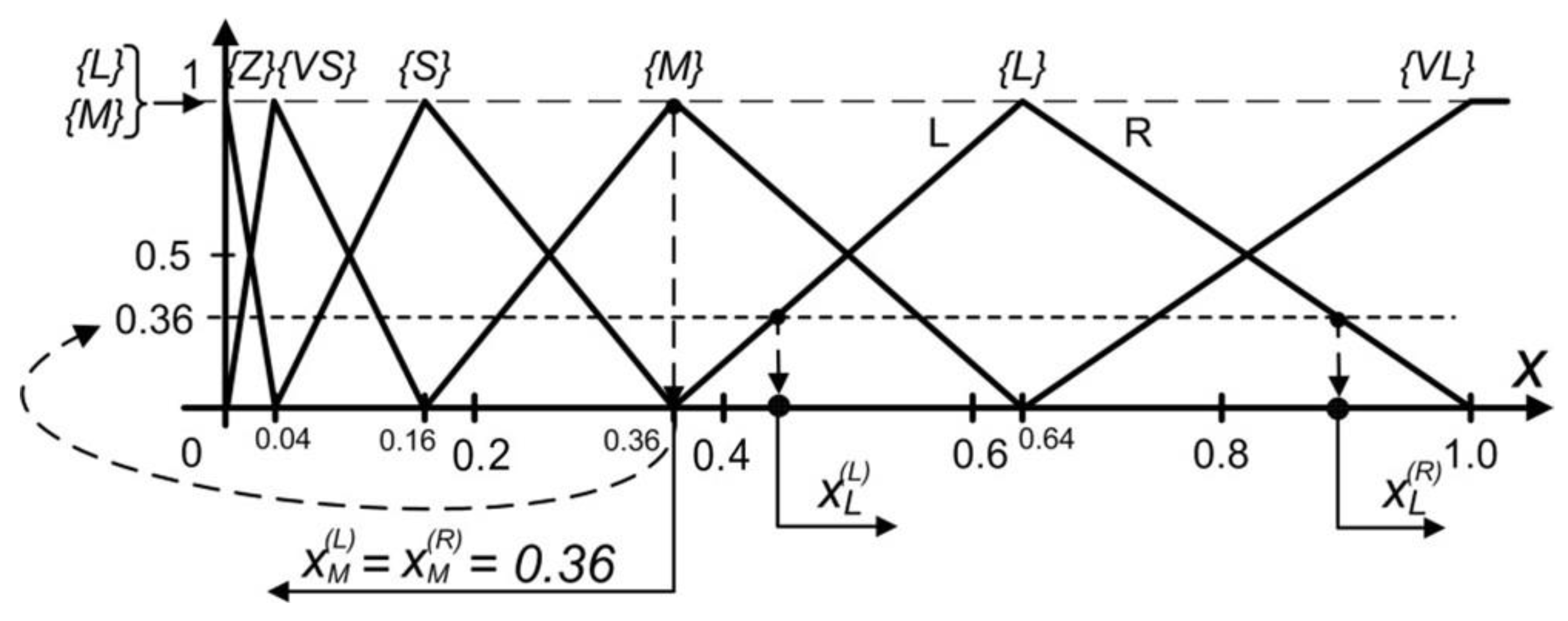
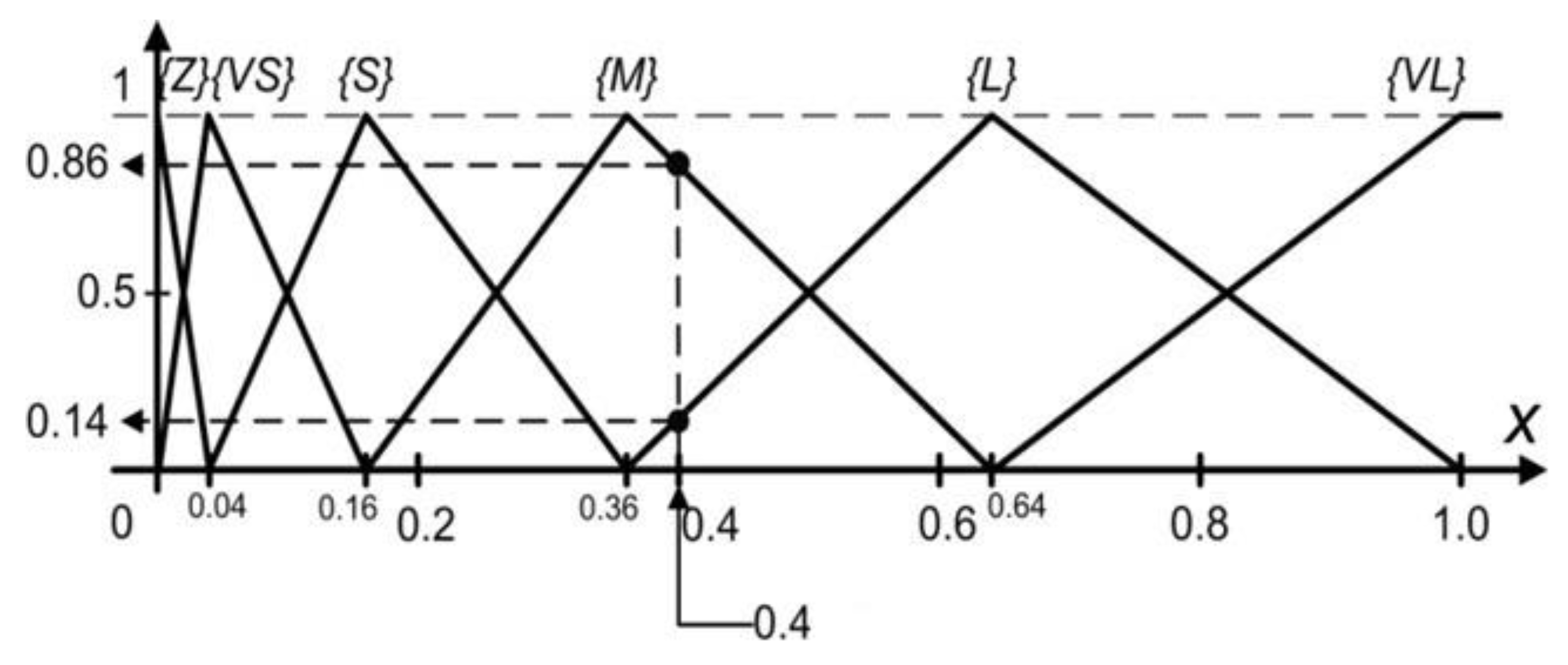
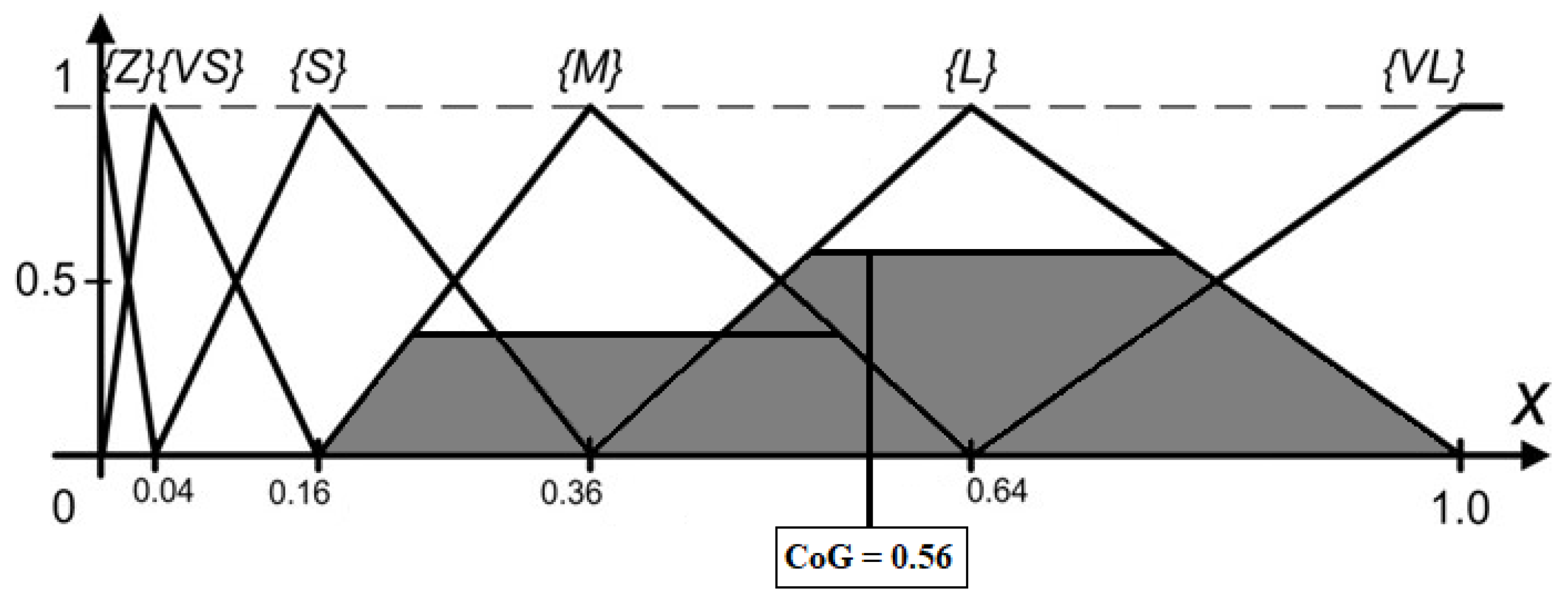
| Load OP∑, TH∑, HES, EFF and RulesBlock Calculate two times (pessimistic and optimistic): Get fuzzy terms and certainties for OP∑, TH∑, EFF, HES according to defined vocabulary (set OPTermsAndCert, ThTermsAndCert, EffTermsAndCert, HesTermsAndCert) Set leftSideRules to [] for each OPTermCert in OPTermsAndCert do for each THTermCert in THTermsAndCert do for each EFFTermCert in EFFTermsAndCert do for each HESTermCert in HESTermsAndCert do set minCert to Min(OPTermCert.cert, THTermCert.cert, EFFTermCert.cert, HESTermCert.cert) leftSideRules add minCert and rulesRow from RulesBlock according to OPTermCert.term, THTermCert.term, EFFTermCert.term and HESTermCert.term Set riskTermsAndCertainties to [] for each rule in leftSideRules do if riskTermsAndCertainties contains term from rule then set index = index of riskTermsAndCertainties.term is equal to rule.term if rule.cert > riskTermsAndCertainties[index].cert then riskTermsAndCertainties[index].cert = rule.cert else riskTermsAndCertainties add rule end if set dividentSum to 0 set divisorSum to 0 for each riskTermCert in riskTermsAndCertainties do set area to riskTermCert polygon area set midpointX to riskTermCert polygon upper hizontal midpoint on X axis dividentSum = dividentSum + midpointX * area divisorSum = divisorSum + area set CoG = dividentSum/divisorSum set Risk[pes] to smaller CoM value set Risk[opt] to greater CoM value set Risk[med] to (Risk[pes]+Risk[opt])/2 Additionally, convert the risk results to verbal values. |
5. Experimental Simulation
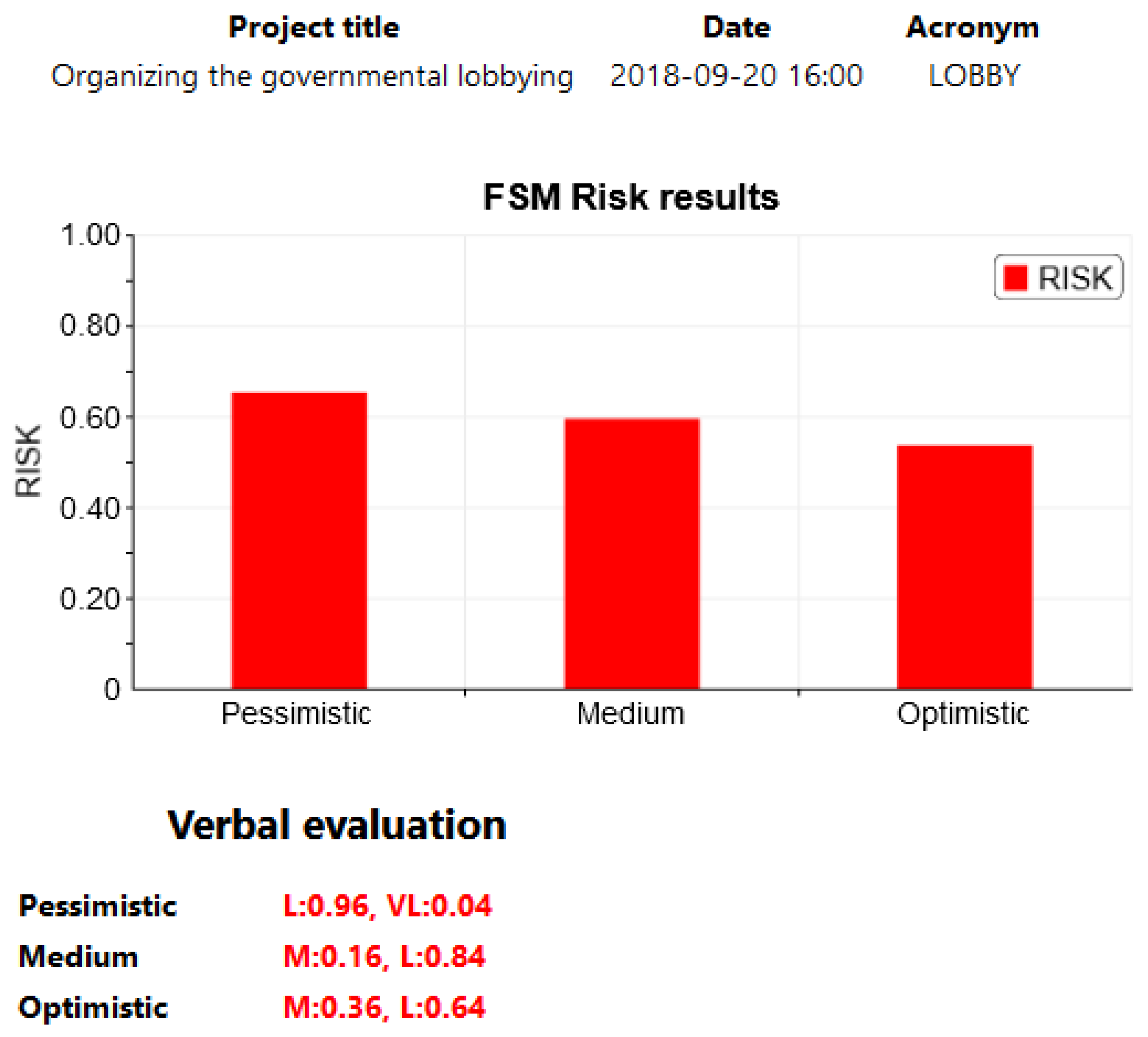
- The estimated risk for project LOBBY is relatively high, but the decision-maker may accept the risk due to the dynamics of the field.
- In the case of the HOTEL project, the risk varies between pessimistic and optimistic perspectives. The decision-maker must assess whether such an outcome is more indicative of the potential value through risk or whether the project is too risky to implement.
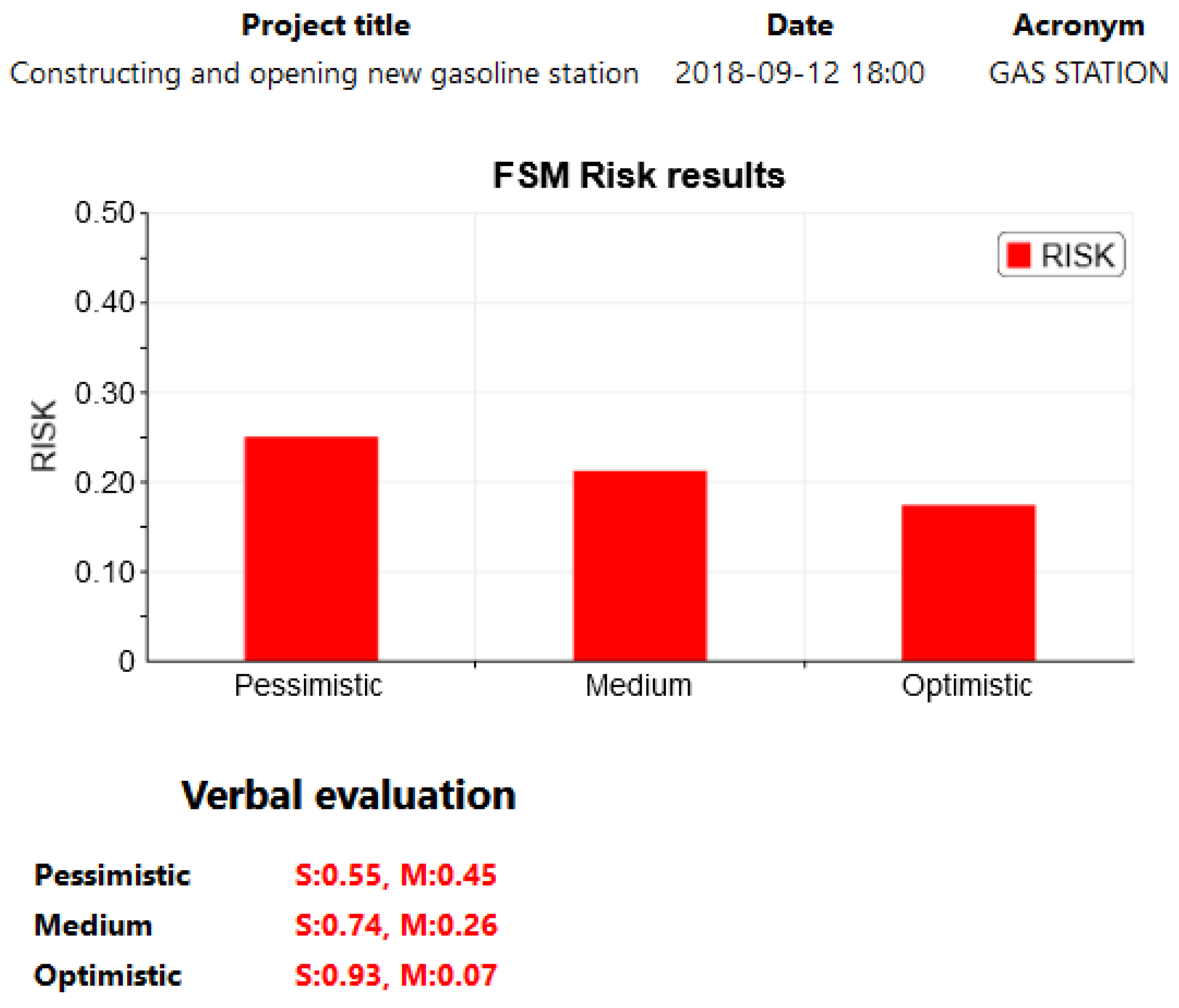
- In the case of GAS STATION, the risk is relatively low in all three perspectives, so it is likely that the decision-maker will be more inclined to implement the project based on this result.
6. Concluding Remarks
Author Contributions
Funding
Conflicts of Interest
References
- Survila, A. Nepaprastųjų Situacijų Valdymas; Mykolas Romeris University: Vilnius, Lithuania, 2015. [Google Scholar]
- ISO 31000. Risk Management-Principles and Guidelines; International Organization for Standardization: Geneva, Switzerland, 2009; pp. 15–21. [Google Scholar]
- Jaeger, C.C.; Webler, T.; Rosa, E.A.; Renn, O. Risk, Uncertainty and Rational Action; Routledge: London, UK, 2001. [Google Scholar]
- Lowrance, W.W. Of Acceptable Risk: Science and the Determination of Safety; William Kaufman Inc.: Los Altos, CA, USA, 1976. [Google Scholar]
- Kaplan, S.; Garrick, B.J. On the quantitative definition of risk. Risk Anal. 1981, 1, 11–27. [Google Scholar] [CrossRef]
- Crouch, E.A.; Wilson, R. Risk/Benefit Analysis; Harvard University Press: Cambridge, MA, USA, 1982. [Google Scholar]
- Moore, P.G.; Moore, P.G. The Business of Risk; Cambridge University Press: Cambridge, MA, USA, 1983. [Google Scholar]
- Dolce, M.; Kappos, A.; Zuccaro, G.; Coburn, A.W. Report of the EAEE Working Group 3: Vulnerability and risk analysis. In Proceedings of the 10th European Conference on Earthquake Engineering, Vienna, Austria, 28 August–2 September 1994. [Google Scholar]
- Henley, E.J.; Kumamoto, H. Probabilistic Risk Assessment and Management for Engineers and Scientists, 2nd ed.; IEEE Press: Piscataway, NJ, USA, 1996. [Google Scholar]
- Rosa, E.A. Metatheoretical foundations for post-normal risk. J. Risk Res. 1998, 1, 15–44. [Google Scholar] [CrossRef]
- Crichton, D. The risk triangle. Nat. Disaster Manag. 1999, 102–103. [Google Scholar]
- Clemens, P.L. Comments on the MIL-STD-882D example risk assessment matrix. J. Syst. Saf. 2000, 36, 20–24. [Google Scholar]
- International Electrotechnical Commission. Risk Management-Vocabulary-Guidelines for Use in Standards; International Organization for Standardization (ISO): Geneva, Switzerland, 2002. [Google Scholar]
- Campbell, J.Y.; Viceira, L.M. The term structure of the risk-return trade-off. Financ. Anal. J. 2005, 61, 34–44. [Google Scholar] [CrossRef]
- Damodaran, A. Equity risk premiums (ERP): Determinants, estimation and implications. Financ. Mark. Inst. Instrum. 2009, 18, 1–82. [Google Scholar] [CrossRef]
- Aven, T.; Renn, O. On risk defined as an event where the outcome is uncertain. J. Risk Res. 2009, 12, 1–11. [Google Scholar] [CrossRef]
- Marchand, M.; Buurman, J.; Pribadi, A.; Kurniawan, A. Damage and casualties modelling as part of a vulnerability assessment for tsunami hazards: A case study from Aceh, Indonesia. J. Flood Risk Manag. 2009, 2, 120–131. [Google Scholar] [CrossRef]
- Aven, T. On some recent definitions and analysis frameworks for risk, vulnerability, and resilience. Risk Anal. Int. J. 2011, 31, 515–522. [Google Scholar] [CrossRef] [PubMed]
- Miheyeva, N. Dynamics of the Development of ’Risk’ Notion in the Psychological Science and its Interdisciplinary Discourse. Soc. Nat. Sci. J. 2012, 5, 1–6. [Google Scholar] [CrossRef][Green Version]
- Johansen, I.L.; Rausand, M. Foundations and choice of risk metrics. Saf. Sci. 2014, 62, 386–399. [Google Scholar] [CrossRef]
- Luhmann, N.; Barrell, R.; Stehr, N.; Bechmann, G. Risk: A Sociological Theory; Routledge: Boca Raton, FL, USA, 2017. [Google Scholar]
- Hopkin, P. Fundamentals of Risk Management: Understanding, Evaluating and Implementing Effective Risk Management; Kogan Page Publishers: London, UK, 2018. [Google Scholar]
- Abu-Alrop, J.H. Risk Definition in Banks. In Proceedings of the Сoвременная мирoвая экoнoмика: прoблемы и перспективы в эпoху развития цифрoвых технoлoгий и биoтехнoлoгии, Moscow, Russia, 15–16 May 2020. [Google Scholar]
- Babić, B. Identification and Definition of Risk, Threats and Disasters. In Risk Management in the Western Balkans; University of Novi Sad, Faculty of Technical Sciences: Novi Sad, Serbia, 2020; pp. 2–10. [Google Scholar]
- Zadeh, L.A. Fuzzy logic = computing with words. In Computing with Words in Information/Intelligent Systems 1; Physica: Heidelberg, Germany, 1999; pp. 3–23. [Google Scholar]
- Atkinson, J.; Jourdan, C. A Practical Guide to Risk Assessment: How Principles-Based Risk Assessment Enables Organizations to Take the Right Risks; PriceWaterHouseCoopers, LLC: London, UK, 2008. [Google Scholar]
- Segudovic, H. Qualitative Risk Analysis Method Comparison; Infigo IS doo: Zagreb, Croatia, 2006. [Google Scholar]
- Petrauskas, V.; Jasinevičius, R.; Kazanavičius, E.; Meškauskas, Ž. CWW elements to enrich SWOT analysis. J. Intell. Fuzzy Syst. 2018, 34, 307–320. [Google Scholar] [CrossRef]
- Jasinevičius, R.; Petrauskas, V. Dynamic SWOT Analysis as a Tool for Environmentalists. Environ. Res. Eng. Manag. 2008, 43, 14–20. [Google Scholar]
- Miller, G.A. The magical number seven, plus or minus two: Some limits on our capacity for processing information. Psychol. Rev. 1956, 63, 81–97. [Google Scholar] [CrossRef]
- Meškauskas, Ž.; Jasinevičius, R.; Kazanavičius, E.; Petrauskas, V. XAI-Based Fuzzy SWOT Maps for Analysis of Complex Systems. In Proceedings of the 2020 IEEE International Conference on Fuzzy Systems (FUZZ-IEEE), Glasgow, UK, 19–24 July 2020. [Google Scholar]
- Jasinevičius, R.; Petrauskas, V. Fuzzy expert maps for risk management systems. In Proceedings of the 2008 IEEE/OES US/EU-Baltic International Symposium, Tallin, Estonia, 27–29 May 2008. [Google Scholar]
- Jasinevičius, R.; Petrauskas, V. Sprendimų Pagrindimo Kompiuterizavimas (Computerization of Decision Making); Technologija: Kaunas, Lithuania, 2011; p. 152. [Google Scholar]
- Petrauskas, V.; Damulevičienė, G.; Dobrovolskis, A.; Dovydaitis, J.; Janavičiūtė, A.; Jasinevičius, R.; Kazanavičius, E.; Knašienė, J.; Lesauskaitė, V.; Liutkevičius, A. XAI-Based Medical Decision Support System Model. Int. J. Sci. Res. Publ. 2020, 10, 598–607. [Google Scholar] [CrossRef]
- Liao, H.; Mi, X.; Xu, Z.; Xu, J.; Herrera, F. Intuitionistic fuzzy analytic network process. IEEE Trans. Fuzzy Syst. 2018, 26, 2578–2590. [Google Scholar] [CrossRef]


| OP | TH | EFF | HES | RISK |
|---|---|---|---|---|
| αOP1 | αTH1 | αEFF1 | αHES1 | αR1 |
| … | … | … | … | … |
| αOPn | αTHn | αEFFn | αHESn | αRn |
| Project Acronym | Efforts | Hesitancies | ||
|---|---|---|---|---|
| Verbal Evaluation | Degree of Certainty | Verbal Evaluation | Degree of Certainty | |
| GAS STATION | Medium | Large | Small | 0.8 |
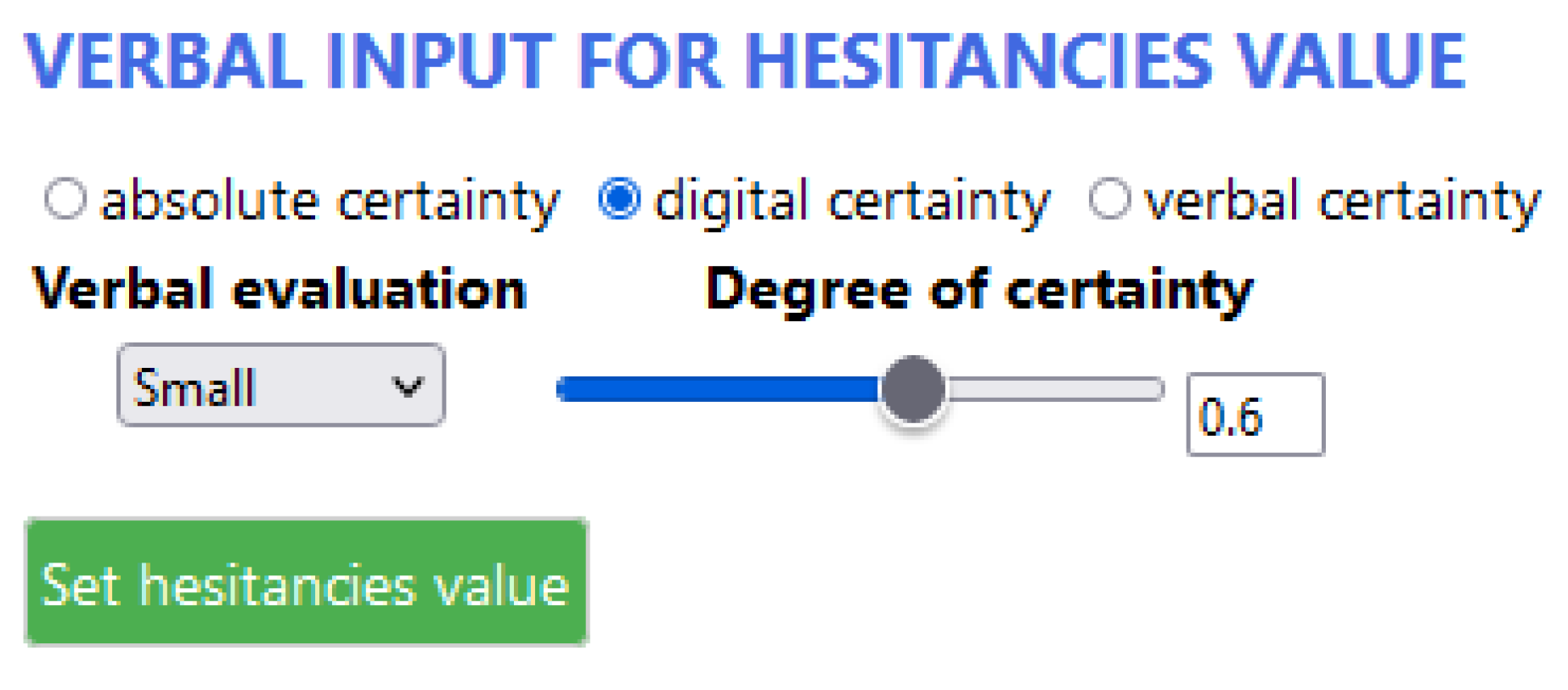
| HOTEL | Large | Very Large | Small | 0.6 |
| LOBBY | Large | Very Large | Medium | Large |
| OP | TH | EFF | HES | RISK |
|---|---|---|---|---|
| VL | Z, VS | Z, VS | Z | Z |
| L, VL | Z, VS | Z, VS, S | Z, VS | VS |
| M, L, VL | VS, S | VS, S, M | Z, VS, S | S |
| M, L | S, M | S, M | VS, S | M |
| VS, S, M | S, M, L | S, M, L | S, M | L |
| Z, VS, S | M, L, VL | M, L, VL | M, L, VL | VL |
| L, VL | L, VL | M | ||
| M, L, VL | L, VL | L, VL | Z, VS | L |
| OP | TH | EFF | HES | RISK |
|---|---|---|---|---|
| VL | Z, VS | Z, VS, S | Z, VS | VS |
| L, VL | VS, S | VS, S | VS | S |
| M, L | VS, S, M | VS, S, M | VS, S | M |
| S, M | S, M, L | S, M, L | S, M | L |
| Z, VS, S | M, L, VL | M, L, VL | M, L, VL | VL |
| L, VL | L, VL | L | ||
| M, L | L, VL | L, VL | Z, VS | L |
| OP | TH | EFF | HES | RISK |
|---|---|---|---|---|
| VL | Z, VS | Z, VS, S | Z | Z |
| L, VL | Z, VS, S | VS, S | Z, VS | VS |
| M, L, VL | VS, S, M | S, M | Z, VS | S |
| M, L | S, M, L | S, M, L | VS, S | M |
| VS, S, M | M, L | M, L | VS, S, M | L |
| Z, VS | L, VL | L, VL | M, L, VL | VL |
| M, L, VL | M, L, VL | L | ||
| M, L, VL | M, L, VL | L, VL | Z, VS | L |
| M, L | Z, VS | M, L, VL | Z, VS | L |
| GAS STATION | HOTEL | LOBBY | |
|---|---|---|---|
| Pessimistic | |||
| Numerical | 0.251 | 0.419 | 0.654 |
| Verbal | S:0.55,M:0.45 | M:0.79,L:0.21 | L:0.96,VL:0.04 |
| Medium | |||
| Numerical | 0.213 | 0.338 | 0.596 |
| Verbal | S:0.74,M:0.26 | S:0.11,M:0.89 | M:0.16,L:0.84 |
| Optimistic | |||
| Numerical | 0.174 | 0.257 | 0.538 |
| Verbal | S:0.93,M:0.07 | S:0.52,M:0.48 | M:0.36,L:0.64 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Meskauskas, Z.; Kazanavicius, E. About the New Methodology and XAI-Based Software Toolkit for Risk Assessment. Sustainability 2022, 14, 5496. https://doi.org/10.3390/su14095496
Meskauskas Z, Kazanavicius E. About the New Methodology and XAI-Based Software Toolkit for Risk Assessment. Sustainability. 2022; 14(9):5496. https://doi.org/10.3390/su14095496
Chicago/Turabian StyleMeskauskas, Zygimantas, and Egidijus Kazanavicius. 2022. "About the New Methodology and XAI-Based Software Toolkit for Risk Assessment" Sustainability 14, no. 9: 5496. https://doi.org/10.3390/su14095496
APA StyleMeskauskas, Z., & Kazanavicius, E. (2022). About the New Methodology and XAI-Based Software Toolkit for Risk Assessment. Sustainability, 14(9), 5496. https://doi.org/10.3390/su14095496







