DDoS Cyber-Incident Detection in Smart Grids
Abstract
:1. Introduction
1.1. Context and Motivation
1.2. Problem Statement
1.3. Our Contributions
- Analyze the dataset to predict and understand the behavior of DDoS reflective attacks.
- Enable not only the detection of possible DDoS attacks but also effectively classify different types of DDoS reflection-based attacks. This ability to classify DDoS attacks can help incident responders to generate the best and most relevant response strategy as quickly as possible.
- Develop a situational awareness tool to evaluate the effectiveness of our approach in detecting an attack, identifying IOCs and suggesting countermeasures.
2. Preliminaries and Related Works
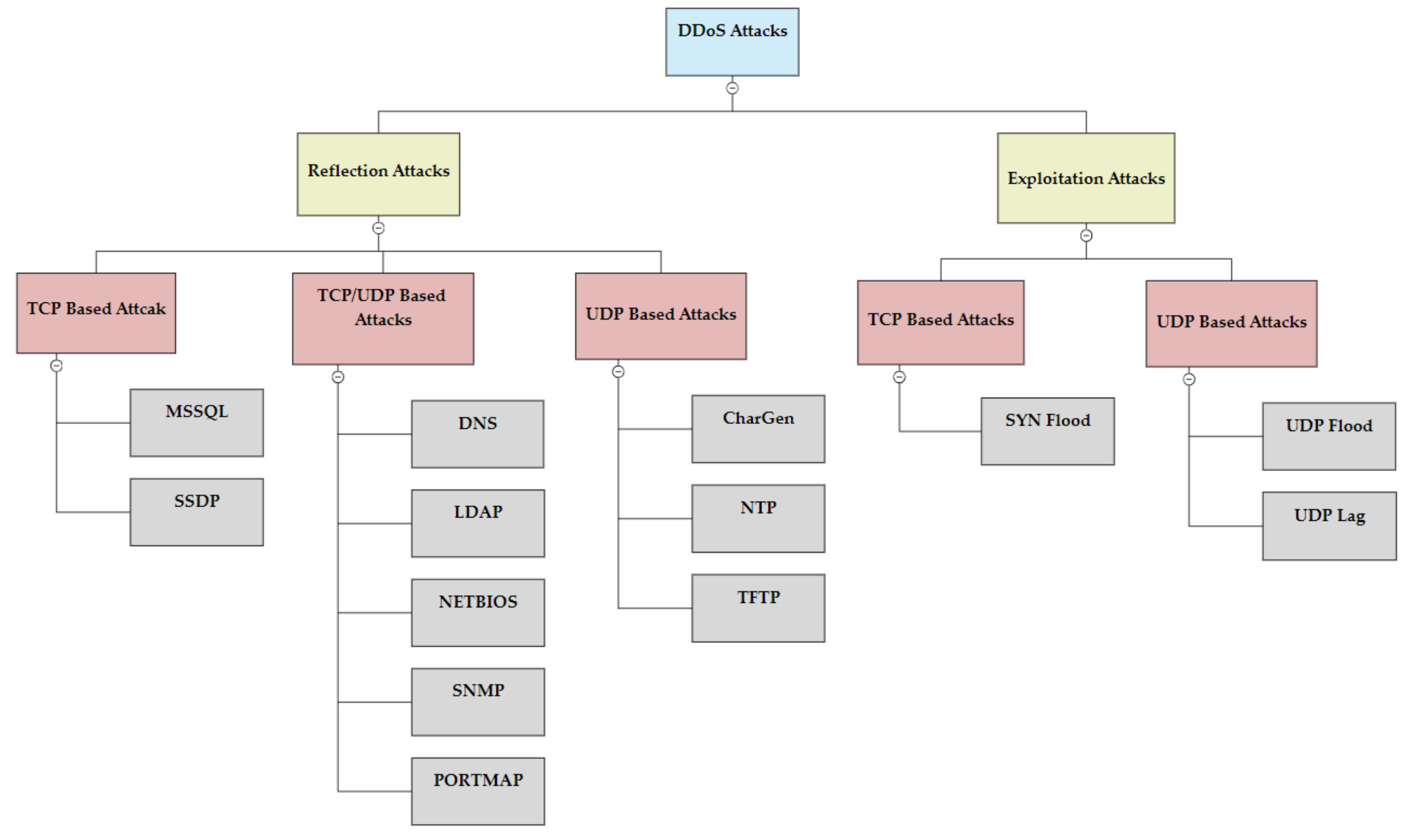
2.1. Preliminaries
2.2. Related Works and Existing Tools
3. System and Threat Models
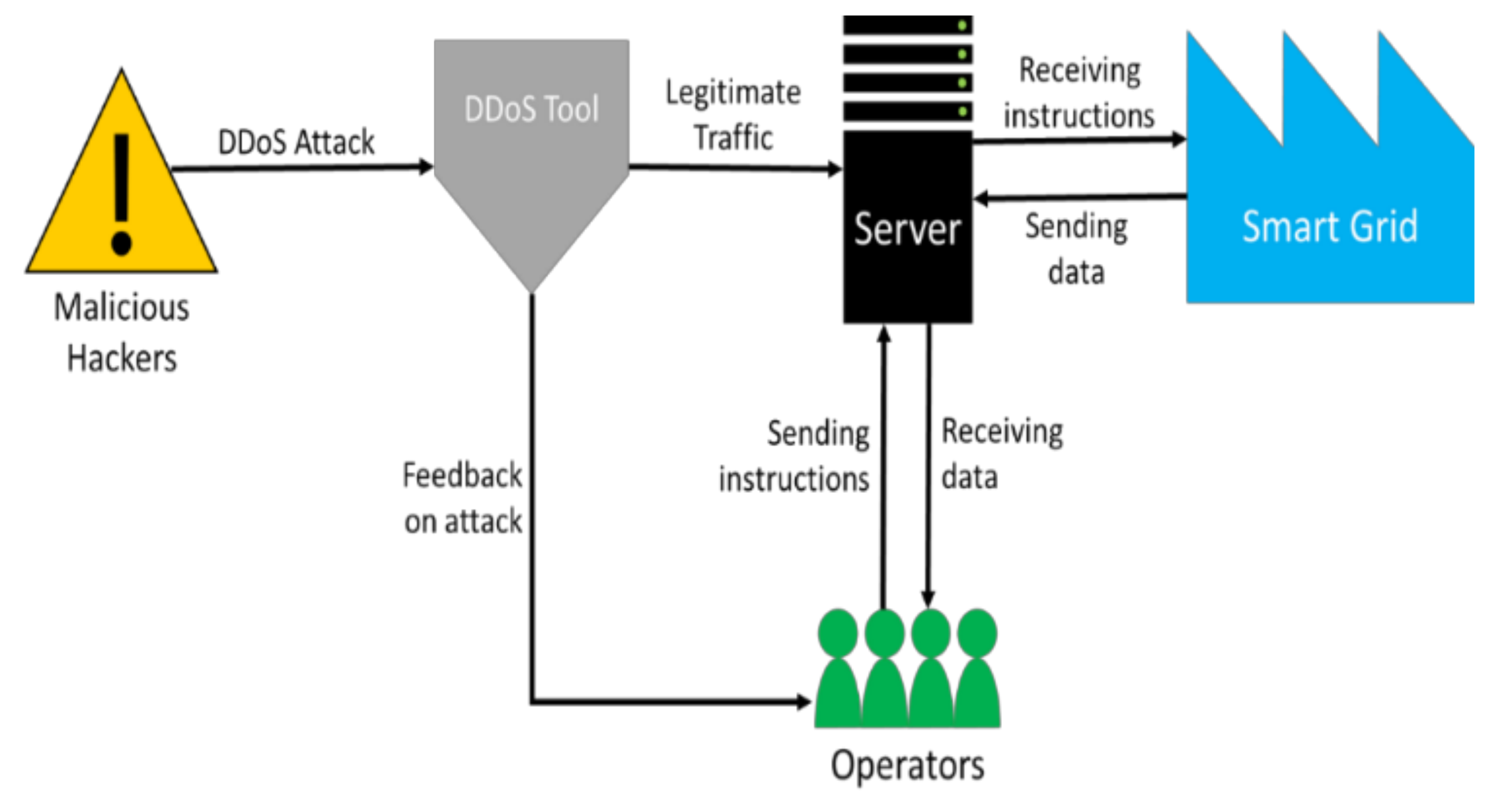
3.1. System Model
3.2. Threat Model
3.2.1. DNS Amplification Attack
3.2.2. NTP Amplification Attack
3.2.3. SNMP Amplification Attack
4. Our Approach
4.1. Experiment Design
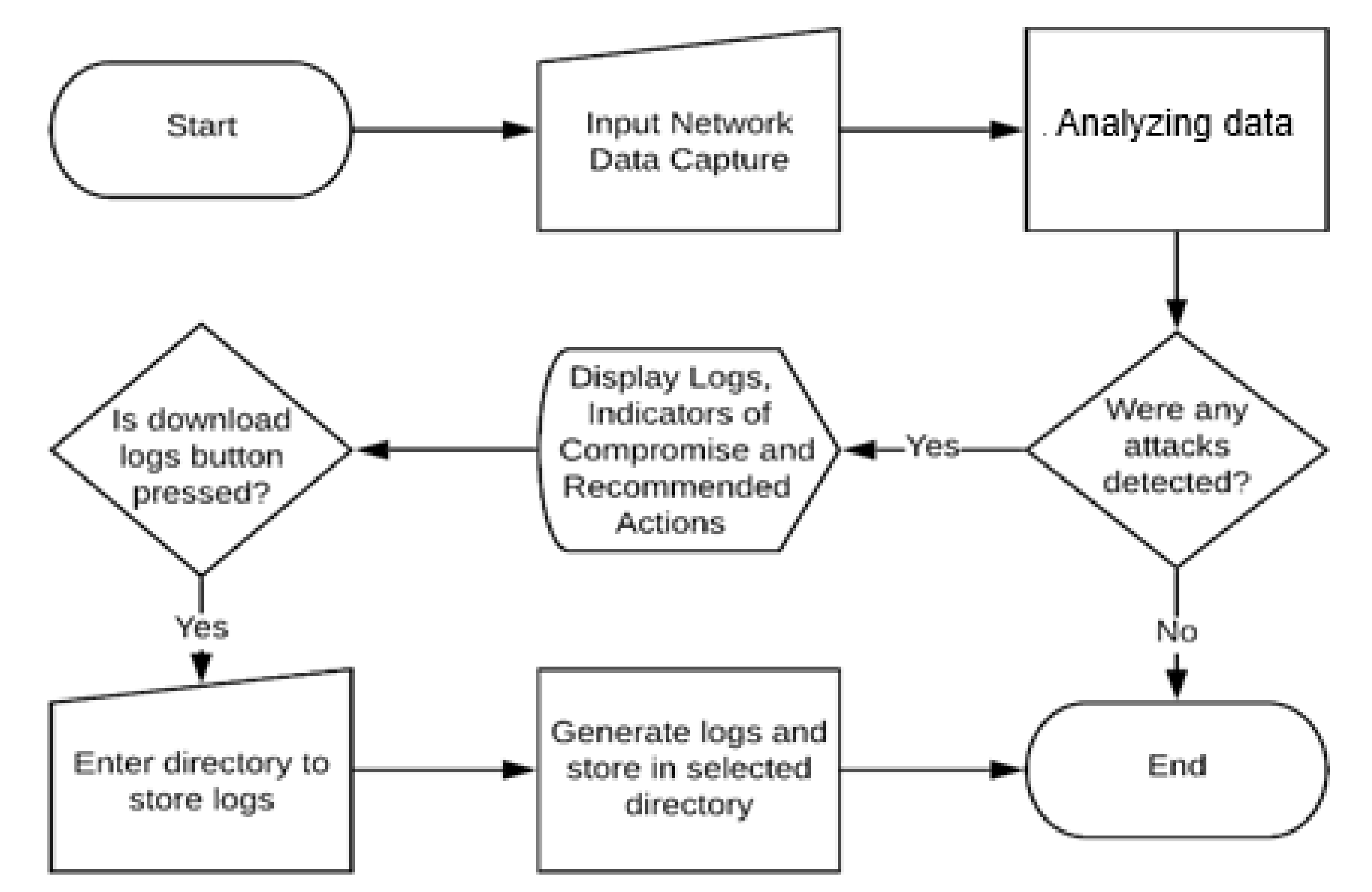
4.2. Overall Execution
4.3. Overall Functionality
4.3.1. Dataset Access and Processing
4.3.2. Analysing the Data
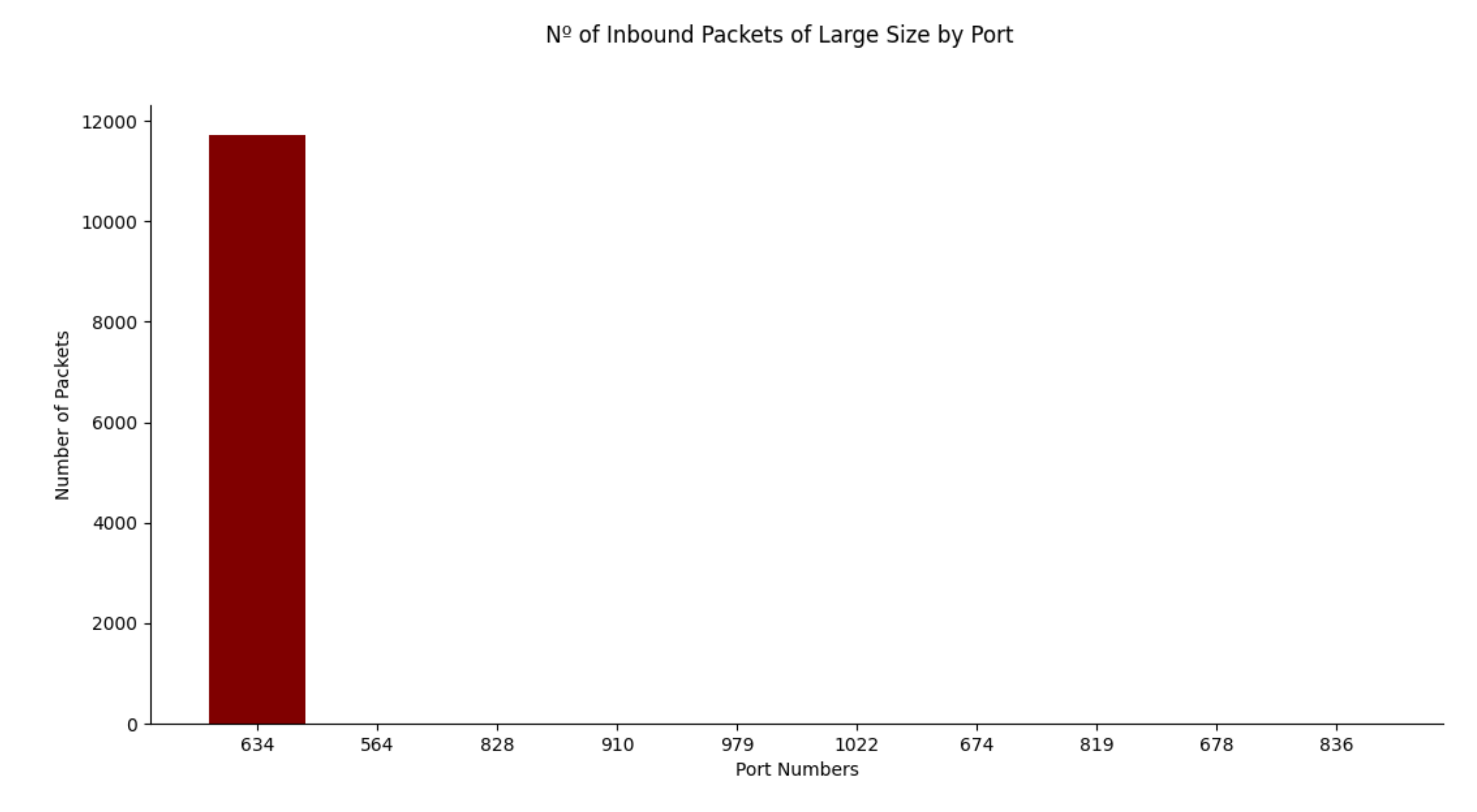
- Response Sizes. If response sizes are abnormally large, this could mean a DDoS attack is happening.
- Mismatch in Port-Application. If the data are being sent from unusual ports, a malicious attack could be occurring.
- DDoS Activity. An IP address sending multiple packets in a short amount of time could be an indicator of a DDoS attack.
| Algorithm 1. NTP detection |
| 1: Variable(s) 2: Suspicious IP list–counts how many times an IP is counted as suspicious 3: If the source IP is not known and the server is the target IP 4: NTP attack has been detected 5: If source IP is in suspicious IP list 6: Update counter by 1 7: Else 8: Add source IP to list and set counter to 1 |
| Algorithm 2. DNS detection |
| 1: Variable(s) 2: Suspicious IP list–counts how many times an IP is deemed suspicious 3: If the source IP is unknown and the server is the target IP 4: DNS attack has been detected 5: If the attack was not previously detected 6: In a suspicious IP list, update the counter for the source IP with the number of counts in the unidentified attack 7: Else 8: If source IP is in suspicious IP list 9: Update counter by 1 10: Else 11: Add source IP to list and set counter to 1 |
| Algorithm 3. SNMP detection |
| 1: Variable(s) 2: Suspicious IP list–Counts how many times an IP is counted suspicious 3: If the source IP is not known and the server is the target IP 4: SNMP attack has been detected 5: If the attack was not previously detected 6: In a suspicious IP list, update the counter for the source IP by the number of counts in the unidentified attack 7: Else 8: If source IP is in suspicious IP list 9: Update counter by 1 10: Else 11: Add source IP to list and set counter to 1 |
| Algorithm 4. Identifying the DDoS attack type |
| 1: If the packet is UDP, is inbound, the source IP is unknown, and the target is the server IP 2: If packet size is 440 3: See Algorithm 5 4: Else if packet size is bigger than 1000 5: If attack is unidentified 6: See Algorithm 5 7: Else if attack is identified as DNS 8: See Algorithm 5 9: Else if attack is identified as SNMP 10: See Algorithm 5 |
| Algorithm 5. Attack detection |
| 1: Variable(s) 2: Suspicious IP list–Counts how many times an IP is counted suspicious 3: If the packet belongs to the ongoing attack 4: If five seconds have passed since the start 5: If the source IP was already in a suspicious IP list, add the number of packets in attack to list 6: Else 7: Add source IP to list with count set as the number of packets detected in the attack 8: Else 9: Set packet as the start of a new ongoing attack 10: Else 11: Set packet as the start of new ongoing attack |
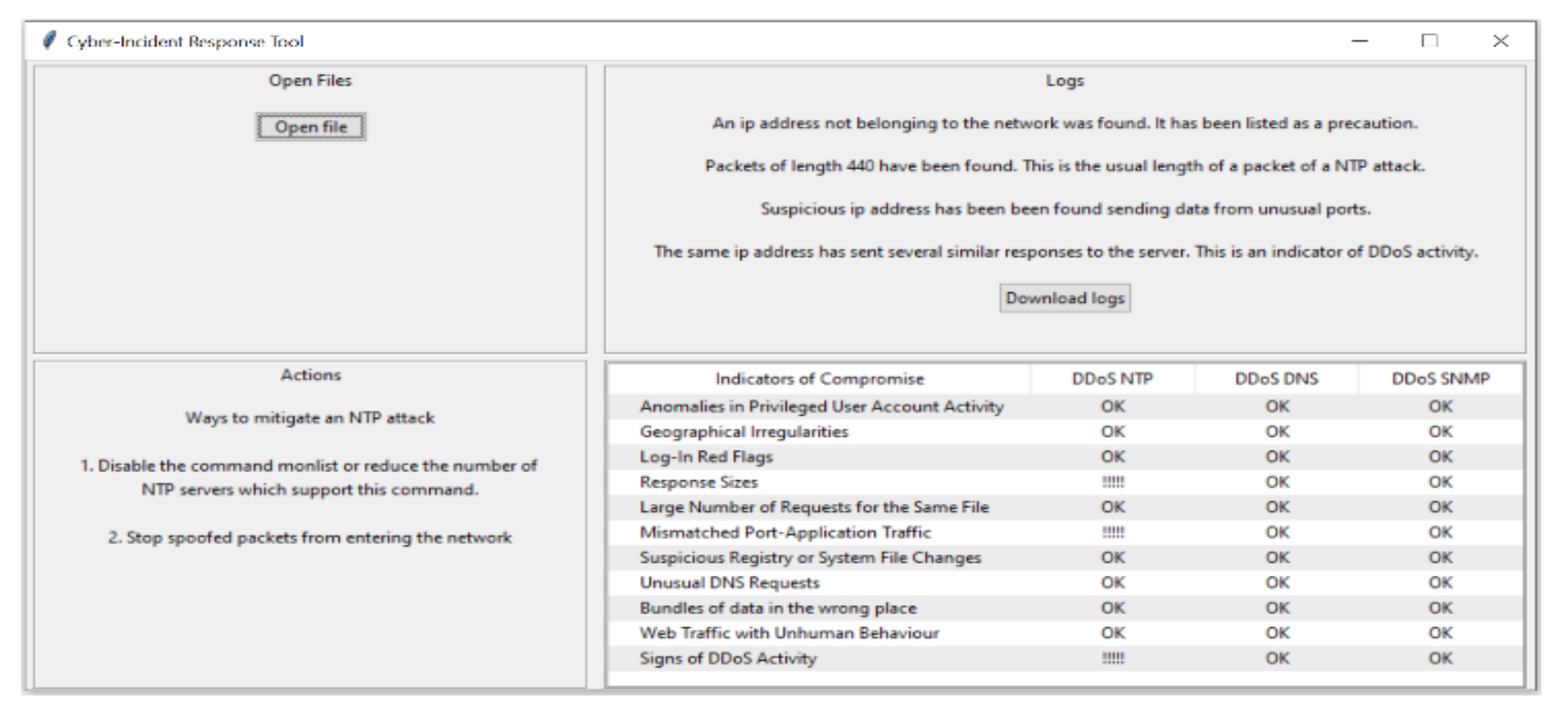
4.3.3. IOC and Recommended Actions
4.3.4. Logs Analysis
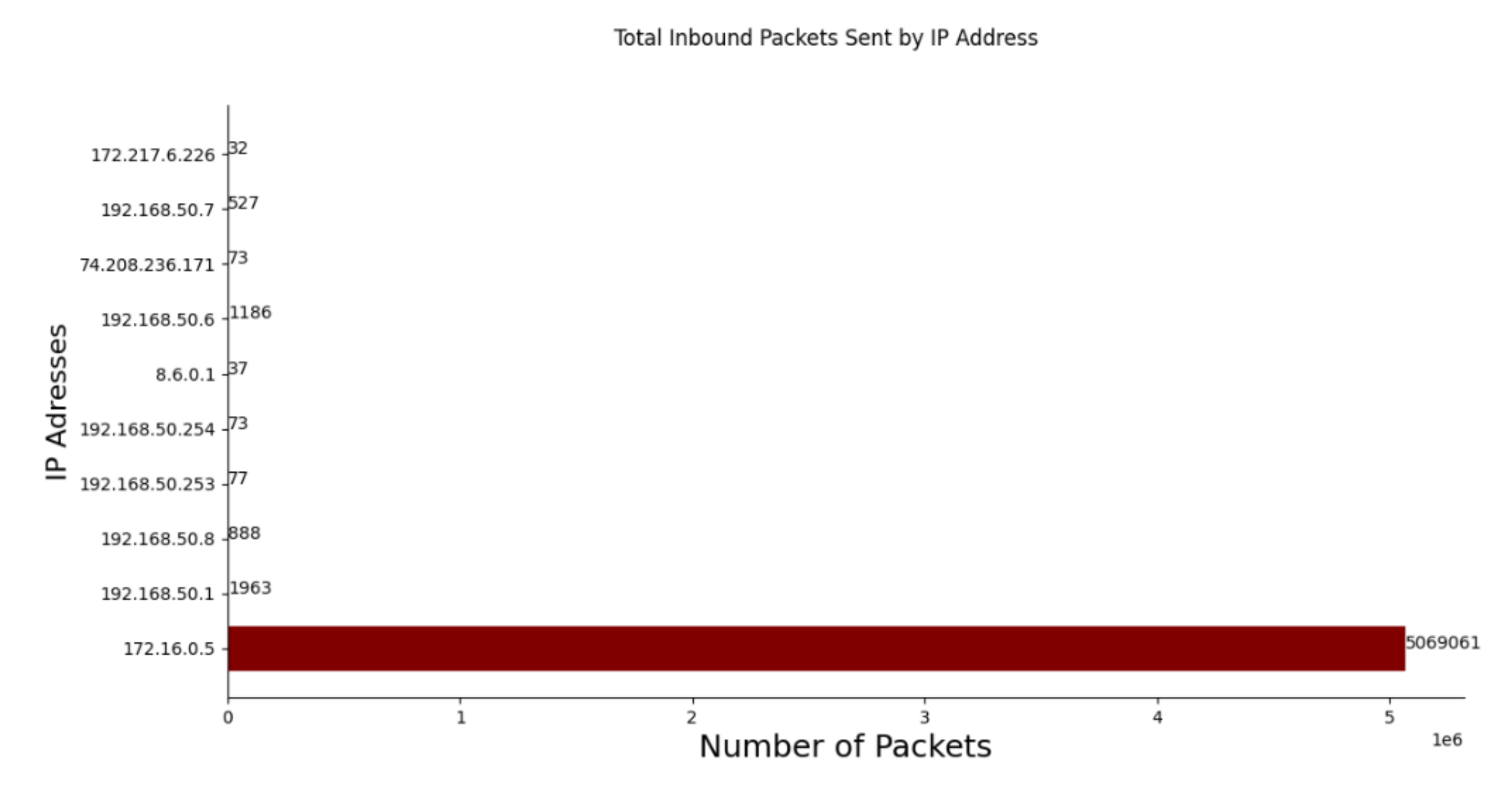
5. Results and Evaluation
5.1. Dataset
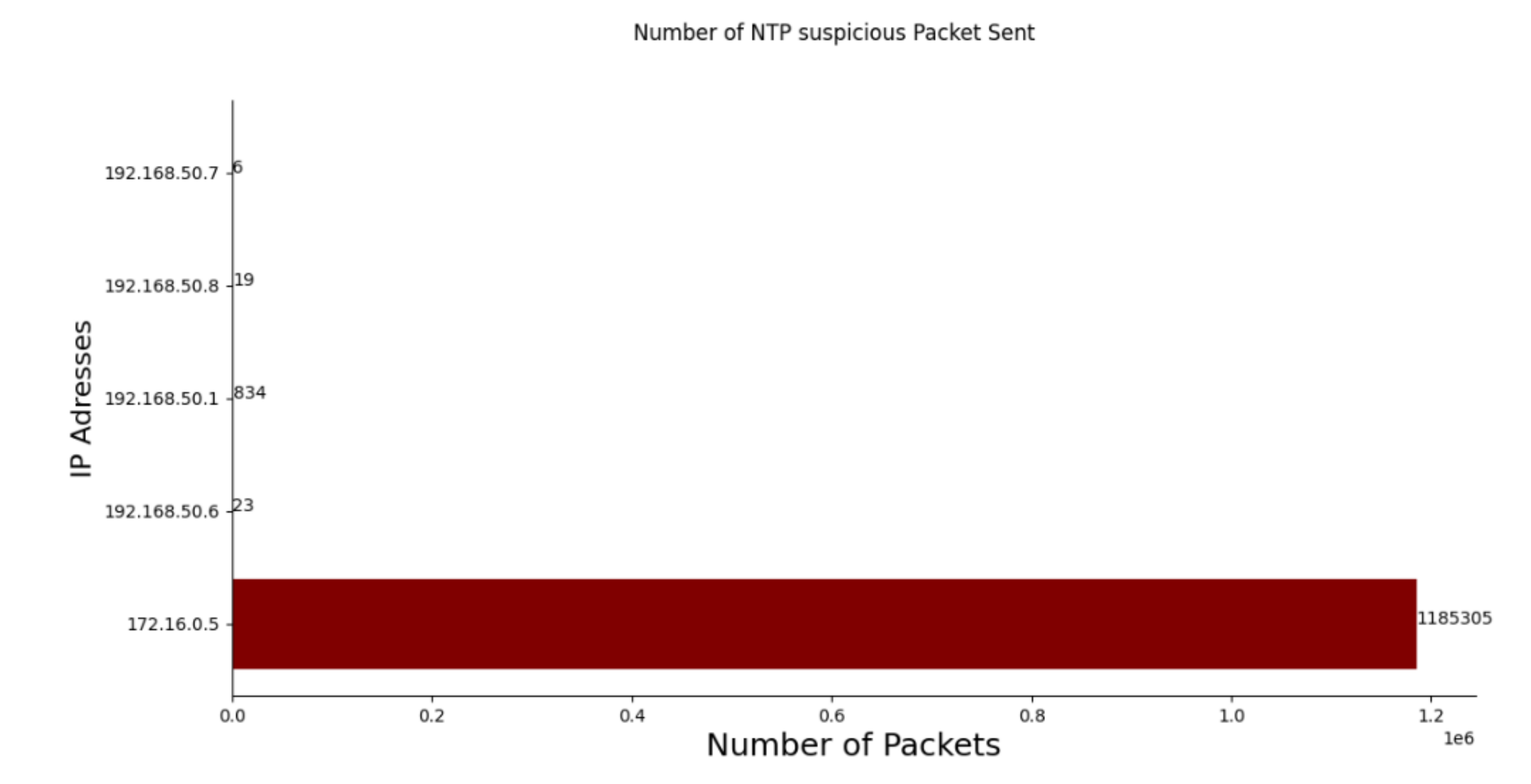
5.2. NTP Attack Evaluation
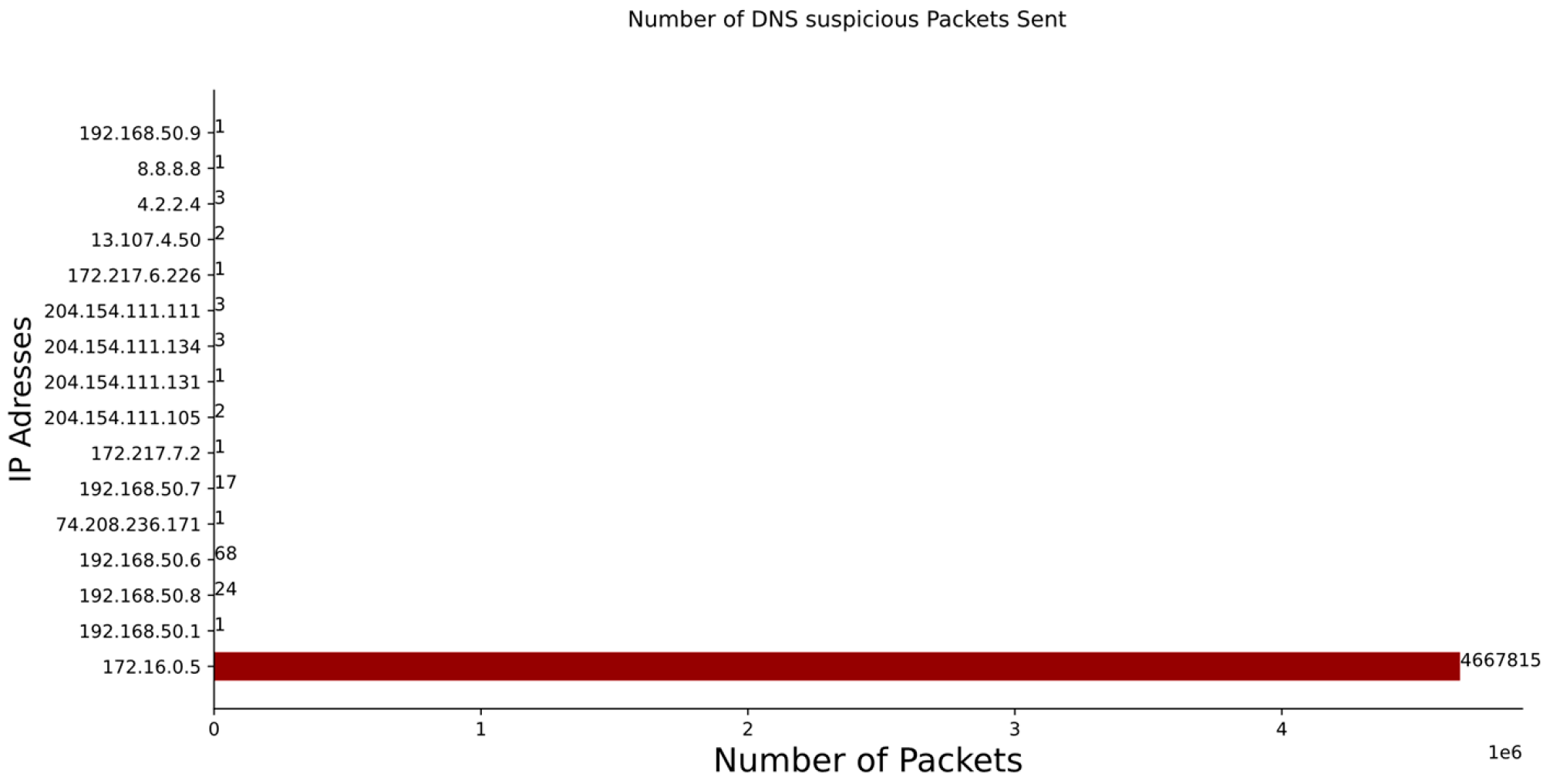
5.3. DNS Attack Evaluation
5.4. SNMP Attack Evaluation
5.5. Computing Complexity Analysis
5.6. Key Highlights and Discussion
6. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Rashid, A.; Gardiner, J.; Green, B.; Craggs, B. Everything is awesome! or is it? Cyber security risks in critical infrastructure. In Proceedings of the Critical Information Infrastructures Security-14th International Conference, CRITIS 2019, Linköping, Sweden, 23–25 September 2019; pp. 3–17. [Google Scholar]
- Oughton, E.J.; Ralph, D.; Pant, R.; Leverett, E.; Copic, J.; Thacker, S.; Dada, R.; Ruffle, S.; Tuveson, M.; Hall, J.W. Stochastic Counterfactual Risk Analysis for the Vulnerability Assessment of Cyber-Physical Attacks on Electricity Distribution Infrastructure Networks. Risk Anal. 2019, 39, 2012–2031. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Gellings, C.W. The Smart Grid: Enabling Energy Efficiency and Demand Response; CRC Press: Boca Raton, FL, USA, 2020. [Google Scholar]
- Mohammadi, F. Emerging Challenges in Smart Grid Cybersecurity Enhancement: A Review. Energies 2021, 14, 1380. [Google Scholar] [CrossRef]
- Saxena, N.; Chukwuka, V.; Xiong, L.; Grijalva, S. CPSA: A Cyber-Physical Security Assessment Tool for Situational Awareness in Smart Grid. In Proceedings of the CCS ’17: 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 30 October–3 November 2017; pp. 69–79. [Google Scholar]
- Diovu, R.C.; Agee, J.T. Quantitative analysis of firewall security under DDoS attacks in smart grid AMI networks. In Proceedings of the IEEE 3rd International Conference on Electro-Technology for National Development (NIGERCON), Owerri, Nigeria, 7–10 November 2017; pp. 696–701. [Google Scholar]
- Asiri, M.; Saxena, N.; Burnap, P. Investigating Usable Indicators against Cyber-Attacks in Industrial Control Systems. In Proceedings of the Seventeenth Symposium on Usable Privacy and Security (SOUPS) 2021, Vancouver, BC, Canada, 8–10 August 2021; pp. 1–5. [Google Scholar]
- Arends, R.; Austein, R.; Larson, M.; Massey, D.; Rose, S. DNS Security Introduction and Requirements; RFC 4033, Proposed Standard; The Internet Society: Reston, VA, USA, 2005. [Google Scholar]
- Malhotra, A.; Cohen, I.E.; Brakke, E.; Goldberg, S. Attacking the network time protocol. Cryptol. Eprint Arch. 2015. [Google Scholar] [CrossRef]
- Crossley, P.A.; Guo, H.; Ma, Z. Time synchronization for transmission substations using GPS and IEEE 1588. CSEE J. Power Energy Syst. 2016, 2, 91–99. [Google Scholar] [CrossRef]
- Barbosa, R.R.R.; Sadre, R.; Pras, A. A first look into SCADA network traffic. In Proceedings of the IEEE Network Operations and Management Symposium, Maui, HI, USA, 16–20 April 2012; pp. 518–521. [Google Scholar]
- Vormayr, G.; Zseby, T.; Fabini, J. Botnet communication patterns. IEEE Commun. Surv. Tutor. 2017, 19, 2768–2796. [Google Scholar] [CrossRef]
- Fonseca, O.; Cunha, Í.; Fazzion, E.; Meira, W.; da Silva, B.A.; Ferreira, R.A.; Katz-Bassett, E. Identifying Networks Vulnerable to IP Spoofing. IEEE Trans. Netw. Serv. Manag. 2021, 18, 3170–3183. [Google Scholar] [CrossRef]
- Kolias, C.; Kambourakis, G.; Stavrou, A.; Voas, J. DDoS in the IoT: Mirai and other botnets. Computer 2017, 50, 80–84. [Google Scholar] [CrossRef]
- NGFW Enterprise Firewall. Forcepoint. 2021. Available online: https://www.forcepoint.com/product/ngfw-next-generation-firewall (accessed on 26 December 2021).
- Tenable.ot. Tenable®. 2020. Available online: https://www.tenable.com/products/tenable-ot (accessed on 26 December 2021).
- Claroty. Claroty: The Industrial Cybersecurity Company. Available online: https://www.claroty.com/comprehensive-platform-overview/ (accessed on 26 December 2021).
- Thomas, D.R.; Clayton, R.; Beresford, A.R. 1000 days of UDP amplification DDoS attacks. In Proceedings of the APWG Symposium on Electronic Crime Research (eCrime), Phoenix, AZ, USA, 25–27 April 2017; pp. 79–84. [Google Scholar]
- Özer, E.; Iskefiyeli, M. Detection of DDoS attack via deep packet analysis in real time systems. In Proceedings of the International Conference on Computer Science and Engineering (UBMK), Antalya, Turkey, 5–8 October 2017; pp. 1137–1140. [Google Scholar]
- Maheshwari, V.; Bhatia, A.; Kumar, K. Faster detection and prediction of DDoS attacks using MapReduce and time series analysis. In Proceedings of the International Conference on Information Networking (ICOIN), Chiang Mai, Thailand, 10–12 January 2018; pp. 556–561. [Google Scholar]
- Yang, Y.; McLaughlin, K.; Sezer, S.; Littler, T.; Pranggono, B.; Brogan, P.; Wang, H.F. Intrusion detection system for network security in synchrophasor systems. In Proceedings of the IET International Conference on Information and Communications Technologies (IETICT 2013), Beijing, China, 27–29 April 2013; pp. 246–252. [Google Scholar] [CrossRef]
- Hussain, Y.S. Network Intrusion Detection for Distributed Denial-of-Service (DDoS) Attacks Using Machine Learning Classification Techniques. Master’s Thesis, University of Victoria, Victoria, BC, Canada, 2020. Available online: https://dspace.library.uvic.ca/handle/1828/11679 (accessed on 26 December 2021).
- Khooi, X.Z.; Csikor, L.; Divakaran, D.M.; Kang, M.S. DIDA: Distributed In-Network Defense Architecture Against Amplified Reflection DDoS Attacks. In Proceedings of the 2020 6th IEEE Conference on Network Softwarization (NetSoft), Ghent, Belgium, 29 June–3 July 2020; pp. 277–281. [Google Scholar]
- Erez, N. How threat actors abuse ICS-specific file types. Netw. Secur. 2020, 2020, 10–13. [Google Scholar] [CrossRef]
- MacFarland, D.C.; Shue, C.A.; Kalafut, A.J. Characterizing optimal DNS amplification attacks and effective mitigation. In Passive and Active Measurement; Springer: Cham, Switzerland, 2015; Volume 8995, pp. 15–27. [Google Scholar]
- Rudman, L.; Irwin, B. Characterization and analysis of NTP amplification based DDoS attacks. In Proceedings of the Information Security for South Africa (ISSA), Johannesburg, South Africa, 12–13 August 2015; pp. 1–5. [Google Scholar]
- Borenius, S.; Costa-Requena, J.; Lehtonen, M.; Kantola, R. Providing network time protocol based timing for smart grid measurement and control devices in 5G networks. In Proceedings of the IEEE International Conference on Communications, Control, and Computing Technologies for Smart Grids (SmartGridComm), Beijing, China, 21–23 October 2019; pp. 1–6. [Google Scholar]
- Wright, J.; Wolthusen, S. Time Accuracy De-Synchronisation Attacks Against IEC 60870-5-104 and IEC 61850 Protocols. In Proceedings of the IEEE Power & Energy Society Innovative Smart Grid Technologies Conference (ISGT), Washington, DC, USA, 18–21 February 2019; pp. 1–5. [Google Scholar]
- Stouffer, K.; Falco, J.; Scarfone, K. Guide to Industrial Control Systems (ICS) Security; National Institute of Standards and Technology: Gaithersburg, MA, USA, 2008. [Google Scholar]
- What is SNMP Reflection and Amplification, Imperva. Available online: https://www.imperva.com/learn/ddos/snmp-reflection/#:~:text=SNMP%20reflection%20is%20a%20volumetric,infrastructure%20to%20withstand%20the%20attack.&text=Learn%20more%20about%20Imperva%20DDoS%20Protection%20services (accessed on 26 December 2021).
- Sharafaldin, I.; Lashkari, A.H.; Hakak, S.; Ghorbani, A.A. Developing Realistic Distributed Denial of Service (DDoS) Attack Dataset and Taxonomy. In Proceedings of the 2019 International Carnahan Conference on Security Technology (ICCST), Chennai, India, 1–3 October 2019; pp. 1–8. [Google Scholar]




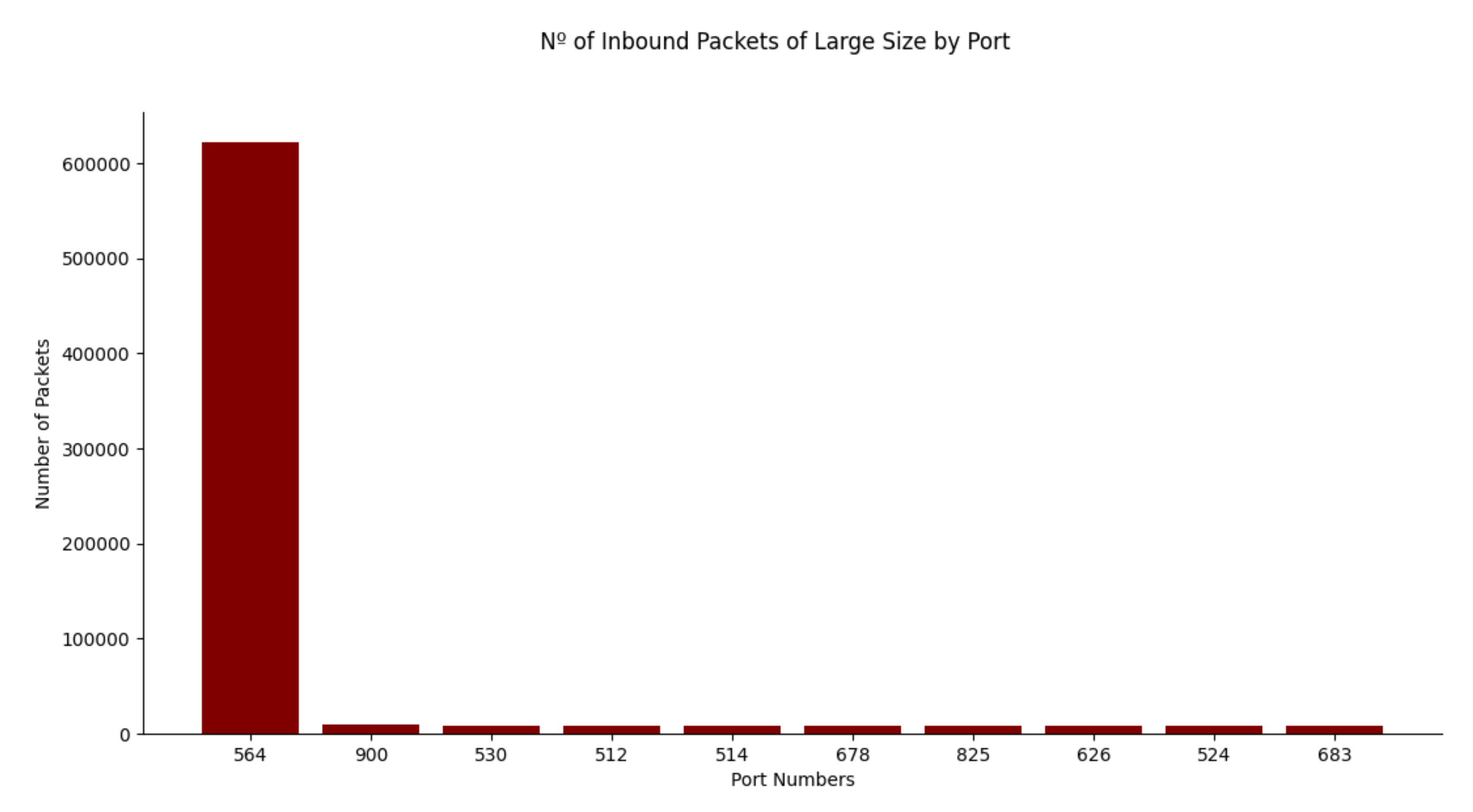
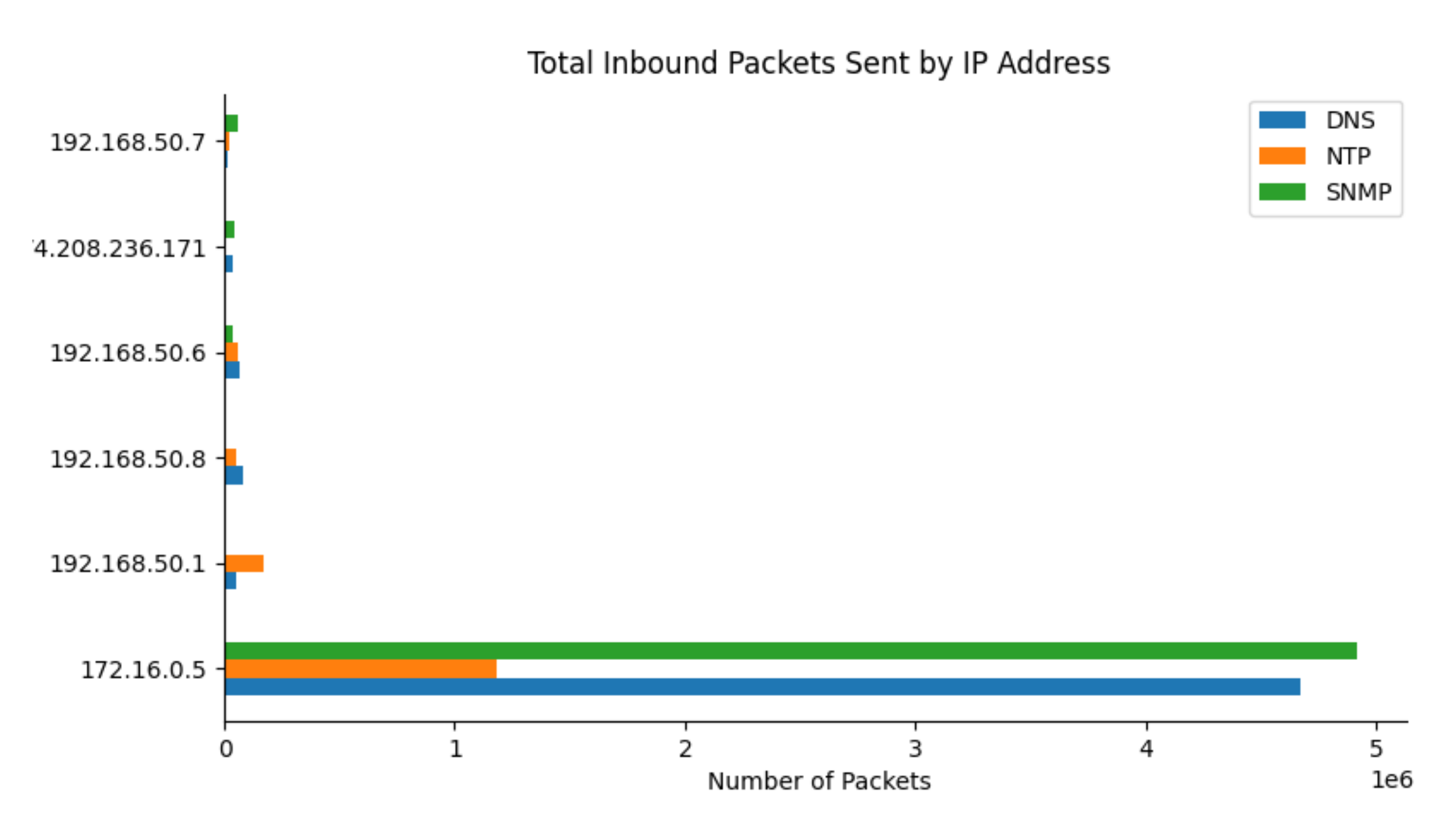
| Tool Name | Company | Pros–Idea | Cons–Limitations | Impact on a System |
|---|---|---|---|---|
| Next-Generation Firewall [15] | Forcepoint | Provides good control over the network and helps with cyberattacks | DDoS protection does not cover amplification attacks | High |
| Tenable.ot [16] | Tenable powered by Indegy | Good visibility of all incidents as they happen | Does not specify if it handles DDoS attacks | Medium |
| Claroty Platform [17] | Claroty | A comprehensive tool that covers many security aspects | Does not specify if it handles DDoS attacks | Medium |
| Author, Year | Research Idea for Detecting DDoS Attacks | Pros | Cons | Impact | Gap |
|---|---|---|---|---|---|
| Thomas et al., 2017 [18] | Monitor scanners before attacks to predict and prevent them | Research focuses on amplification attacks, has a very good detection rate | – | High | – |
| Özer and İskefiyeli, 2017 [19] | Set the average number of packets for real-time detection | Many different types of DDoS can be detected | No data on the type of DDoS attack | Medium | Lack of attack identification |
| Maheshwari et al., 2018 [20] | Use MapReduce to detect DDoS attacks | Fast detection and most DDoS attacks are detected | No data on the type of DDoS attack | Medium | Lack of attack identification |
| Yang et al.,2013 [21] | Use an IDS framework to detect man-in-the-middle (MITM) and denial-of-service (DoS) attacks against a practical synchrophasor system | Ability to detect zero-day attacks | Inability to detect certain types of attacks, such as packet drop and injection and GPS spoofing | High | Detection evaluation against other DDoS attacks is not discussed |
| Hussain,2020 [22] | Use deep learning for DDOS mitigation in 5G | Effective detection process | - | Medium | - |
| Khooi et al. [23] | Distribute mitigation mechanism against amplified reflection DDoS attacks | Very good detection rate | The adoption of such a system is cumbersome and expensive | Medium | Lack of evaluation on real traces |
| Attack | No. of Total Packets Sent/Sec | No. of Malicious Packets Sent | Streak Duration/Sec | Attack Duration/Sec |
|---|---|---|---|---|
| NTP | 1300 | ≈1.2 million | 19 | 932 |
| DNS | 4700 | ≈4.7 millions | 70 | 994 |
| SNMP | 8200 | ≈5 millions | 495 | 594 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Merlino, J.C.; Asiri, M.; Saxena, N. DDoS Cyber-Incident Detection in Smart Grids. Sustainability 2022, 14, 2730. https://doi.org/10.3390/su14052730
Merlino JC, Asiri M, Saxena N. DDoS Cyber-Incident Detection in Smart Grids. Sustainability. 2022; 14(5):2730. https://doi.org/10.3390/su14052730
Chicago/Turabian StyleMerlino, Jorge C., Mohammed Asiri, and Neetesh Saxena. 2022. "DDoS Cyber-Incident Detection in Smart Grids" Sustainability 14, no. 5: 2730. https://doi.org/10.3390/su14052730
APA StyleMerlino, J. C., Asiri, M., & Saxena, N. (2022). DDoS Cyber-Incident Detection in Smart Grids. Sustainability, 14(5), 2730. https://doi.org/10.3390/su14052730







