Integrating Blockchain with Artificial Intelligence to Secure IoT Networks: Future Trends
Abstract
1. Introduction
- RQ1: What are the need for integrating AI and Blockchain technologies with IoT to secure its network?
- RQ2: What are the recent approaches that handle the security concerns in the IoT environment by integrating AI algorithms and Blockchain?
- RQ3: What are the research gaps and future directions within the security of IoT networks based on AI and Blockchain technologies ?
1.1. Research Motivation
1.2. Research Contribution
- Propose a systematic review and analyze the existing defense models based on AI and Blockchain technologies.
- Highlight the benefits of employing Blockchain to empower the security of IoT networks.
- Explore the main limitations of the Blockchain-based defense models in IoT networks.
- Provide an assessment of the recent defense models using a set of metrics such as IoT network characteristics and requirements.
- Outline future directions that can enhance by integrating Blockchain and AI techniques for securing IoT networks against cybersecurity attacks.
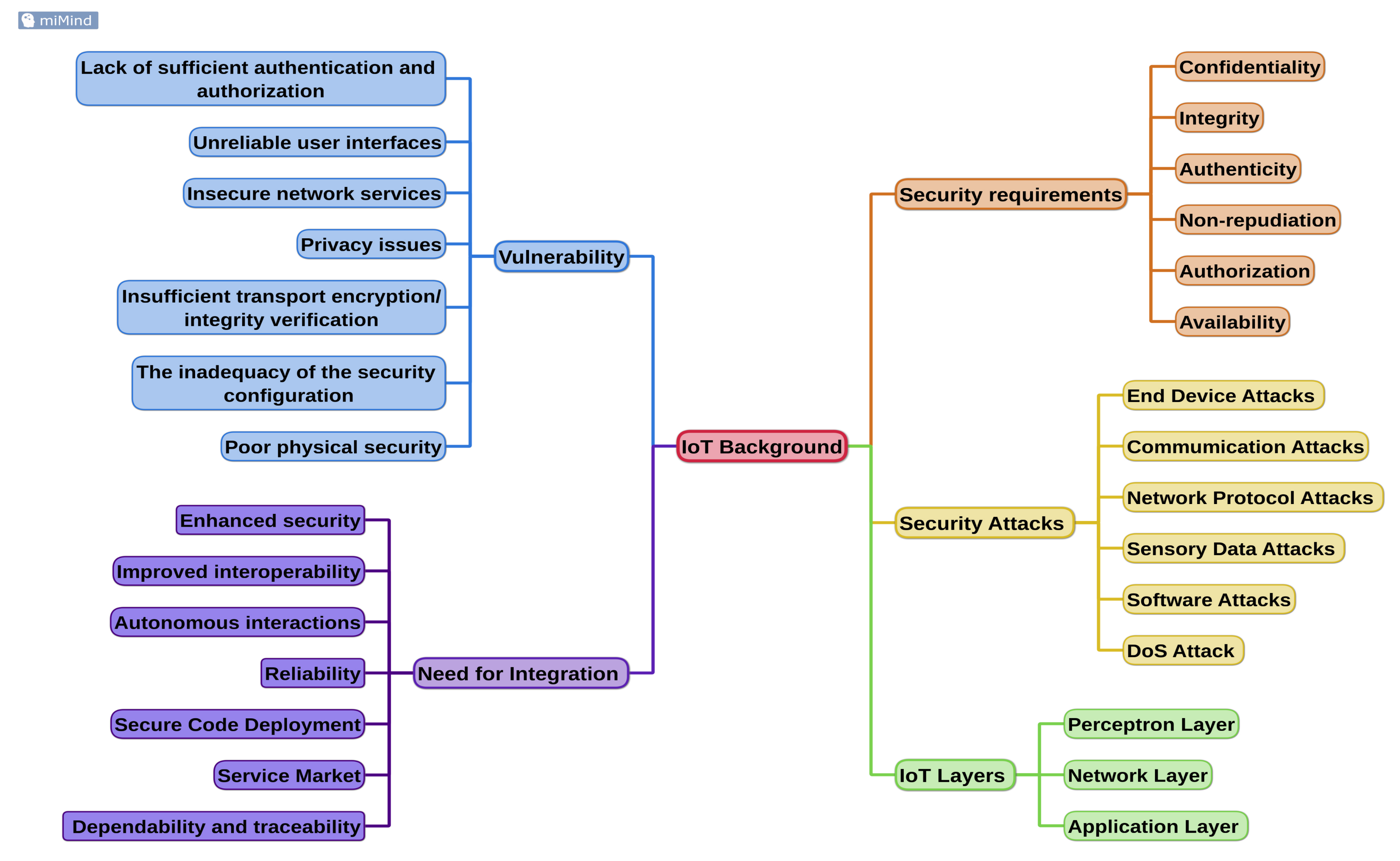
2. Background
2.1. IoT Overview
- Linked Feature: The IoT links a large amount of data from various sources to empower the community by delivering self-services at a low cost. Gathering big data from different sources involves different users and techniques. Therefore, the IoT network is complicated. The linked data can improve consumer trust with the ability of fraud detection. But the main risks related to linked data are shortage of skilled personnel, limited educational institutes, and structural issues.
- Big Feature: The IoT networks generate a large volume of data in which big data analytics play a vital role in enhancing information communication. The IoT can improve the planning operation and reactions to unexpected events that enhance the performance of industries. Additionally, the IoT network is being used in the monitoring process such as monitoring the quality of industrial assets. In contrast, the data leak is the main risk that affects privacy.
- Openness Feature: The data produced by IoT can be open for general use. The IoT makes data available for the public to provide transparency of the business processes. IoT allows other devices to access the public data on the IoT network to utilize them. Moreover, the IoT has improved data access to offer consumer self-services. But the risks of open data are scalability problems, security concerns especially providing fine-grained access control.
2.1.1. IoT Architecture
2.1.2. Security Requirements
- Confidentiality: The confidential data must be protected from unauthorized access by unauthorized users. Moreover, the protection of proprietary data and confidentiality should be guaranteed. Cryptographic encryption/decryption schemes are the best way to ensure data confidentiality.
- Integrity: Data integrity means that the data inside the node of IoT cannot be altered, manipulated, or consumed by uncertified entities or users. The most famous attack that can compromise data integrity is the man-in-the-middle attack. The attacker intercepts the data before it is delivered to the receiver node.
- Authenticity: The concept of this requirement is related to the assurance of the data and transactions’ authenticity. Particularly, the user must be the one who claims to be. The most famous technique that can preserve data authenticity is cryptographic digital signatures.
- Non-repudiation: It addresses the ability to prove all occurred events. In general terms, the sender and receiver cannot deny any sent or received data.
- Authorization: It means the provision of granting any user permission to own or perform some function.
- Availability: The concept of this requirement is to guarantee that the data, services, and network resources are available all time to authorized users.
- Energy efficiency: The low resources of IoT devices must be protected from energy consumption.
- Privacy: The individual information must not be exposed by other parties.
- Resilience to attacks: The concept of this requirement is avoiding the single points of failure.
2.1.3. Security Challenges and Vulnerability
- Lack of sufficient authentication and authorization approaches such as using the default weak passwords, having weak password retrieval systems, and a lack of fine-grained access control.
- Unreliable user interfaces such as weak login certificate and using plain-text credentials.
- Insecure network services.
- Privacy problems.
- Lack of sufficient transport encryption/integrity verification.
- The inadequacy of the security configuration.
- Poor physical security.
- Data Volume Challenges: IoT applications produce a large amount of confidential data that are a potential target to an attacker. Therefore, privacy protection is a critical concern especially in terms of linked data that are comprised of IoT nodes.
- The Scalability Challenges: The security scheme must be scaled throughout the IoT network to cover a large number of entities.
- Heterogeneity challenges: IoT links various identities in which every identity has different capabilities and complexity. Further, IoT devices differ from each other in their interfaces, versions, and function. Thus, IoT protocols should support all devices and must be able to connect heterogeneous networks and things.
- Interoperability Challenges: IoT security should be developed and utilized without restricting the operations of IoT nodes.
- Autonomous Control Challenges: IoT systems must provide automatic settings in the end devices without users’ configuration.
- Attack Resistant Challenges: End nodes of IoT systems are small devices having very little or no physical armor. Thus, the fixed devices can be destroyed easily by a natural disaster or cameras. Moreover, small mobile sensors can be stolen.
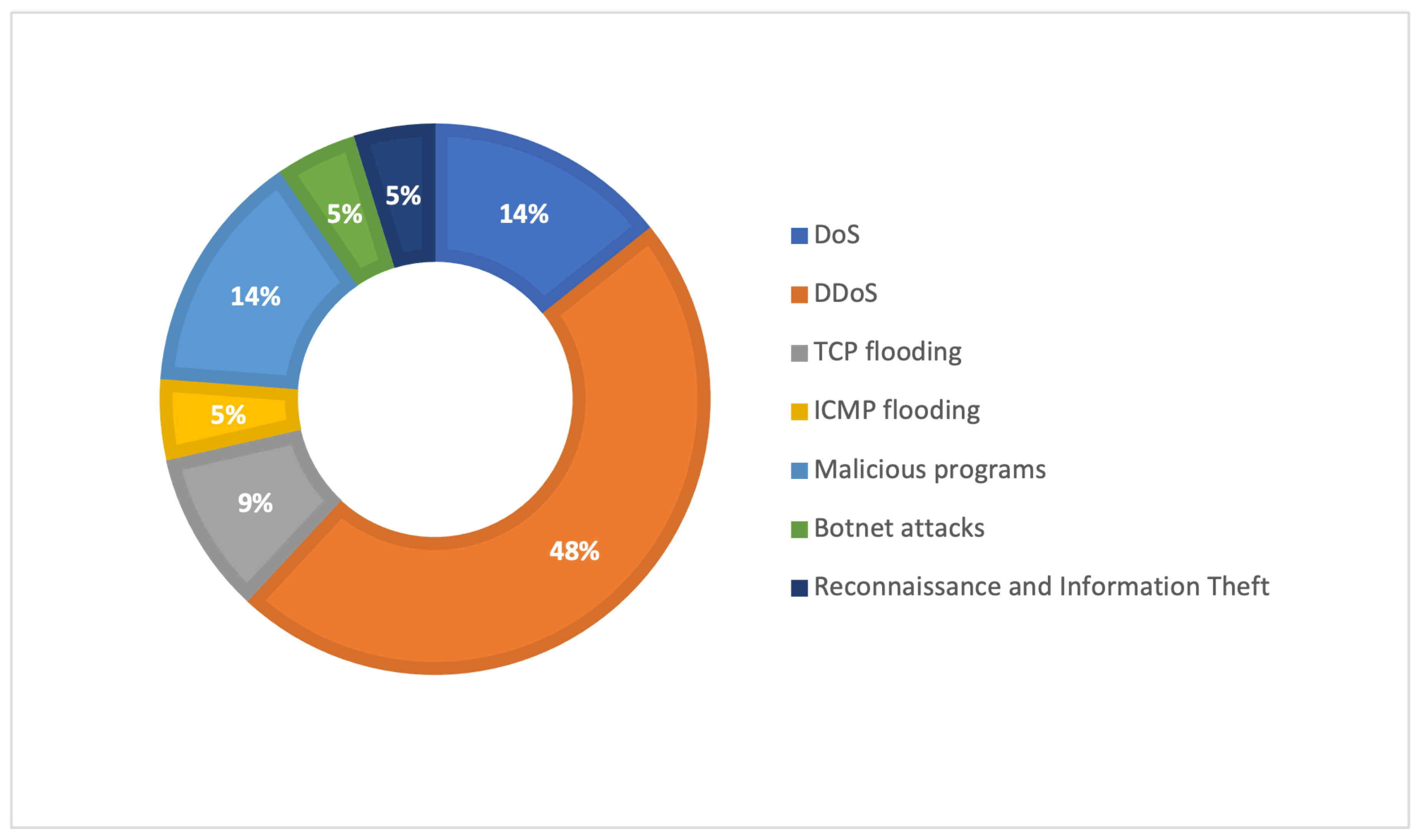
2.1.4. IoT Cybersecurity Attacks
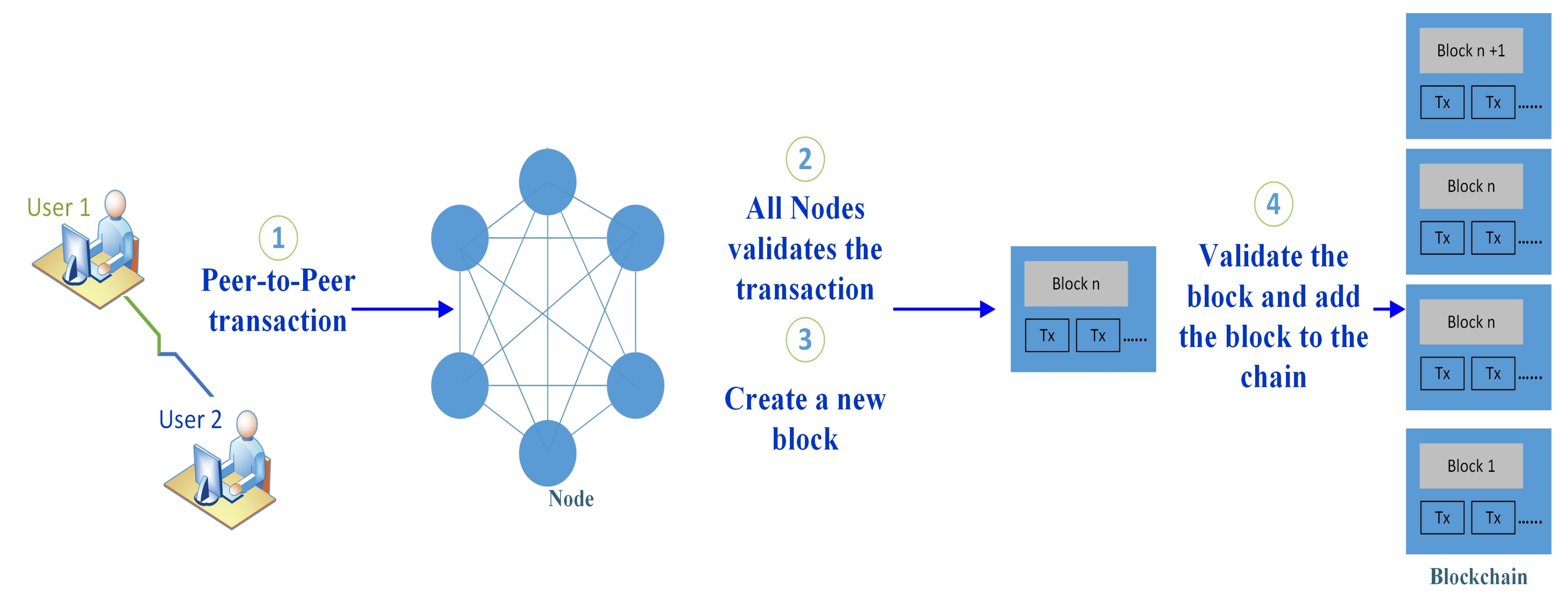
2.2. Blockchain Overview
- Miner nodes: These nodes are responsible for packing the transactions into blocks and running the consensus algorithms. Sometimes, they have the highest computational power in some Blockchain types like proof-of-work consensus.
- Full nodes: These nodes are responsible for downloading the entire Blockchain and verifying the integrity of all transactions.
- The thin clients: These nodes can download the block headers only. Thus, the Blockchain can be used with minimal storage and computing requirements.
- The server-trusting clients: These nodes have the public key of clients and can generate a transaction after making the client’s approval.
2.2.1. Blockchain Characteristics
- Transparency: The data is transparent to all users on the Blockchain that makes it credible. Specifically, in the public Blockchain, the full copy of all transactions in a network is available to all nodes. However, in the private and consortium Blockchain, restricted access to only permissions nodes [1,11,15].
- Autonomy: Each node can send and receive transactions without a trusted third party, using public/private key pairs [11].
- Programmable: Blockchain may include smart contracts that are made to support the negotiation and performance of the contract. A smart contract is a piece of code that can be executed, verified, or enforced by itself. Sometimes, smart contracts are employed to build IP addresses black-list and white-list. The Ethereum platform is the most famous open Blockchain that has smart contracts capabilities [16].
2.2.2. Types of Blockchain
- Public Blockchains are also called permissionless networks that allow all participants to use the main chain either as readers or writers. Thus, all transactions are open to all nodes, so each node can check and verify all transactions. Moreover, the transaction time and cost are more than other types. Examples of public Blockchain are Bitcoin, Ethereum, and Zerocash
- Private Blockchains are also called permissioned Blockchains that have restricted access. They identify the miner nodes that involve in all transactions. But each node has permission to access its linked data. These types protect data and user confidentiality more than public Blockchains because the number of involved nodes in each transaction is lesser. Examples of these types are Quorum and Multichain
- Consortium Blockchains are also called hybrid Blockchains which are semi-decentralized networks. They combine the public and private forms, but it is closer to private Blockchains. The Blockchain is under the supervision of a group of users. Mainly, they are controlled by unique predetermined nodes without monopoly. Examples of these types are Hyperledger Fabric and Ethermint.
3. Research Methodology
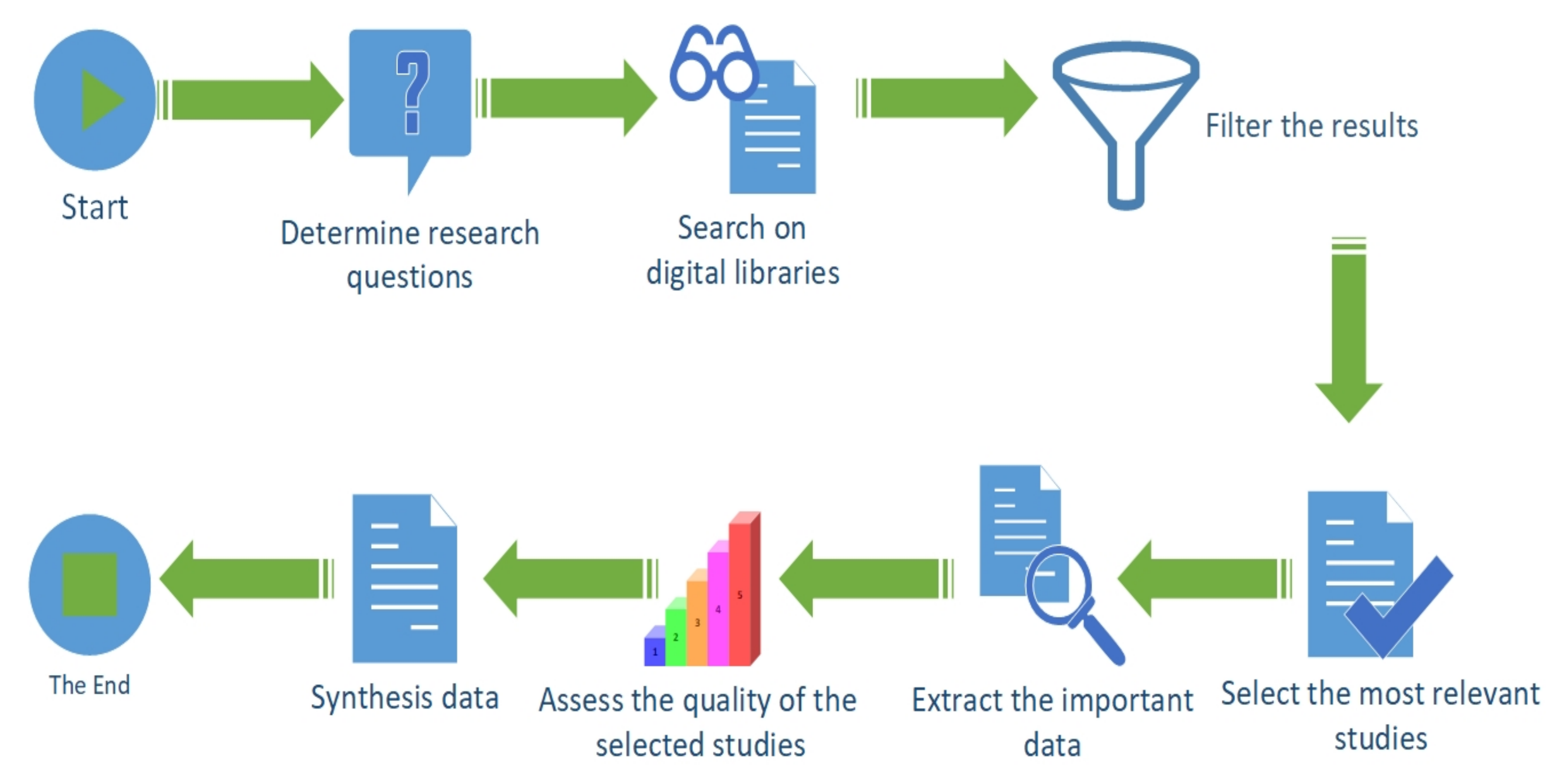
3.1. Planning Phase
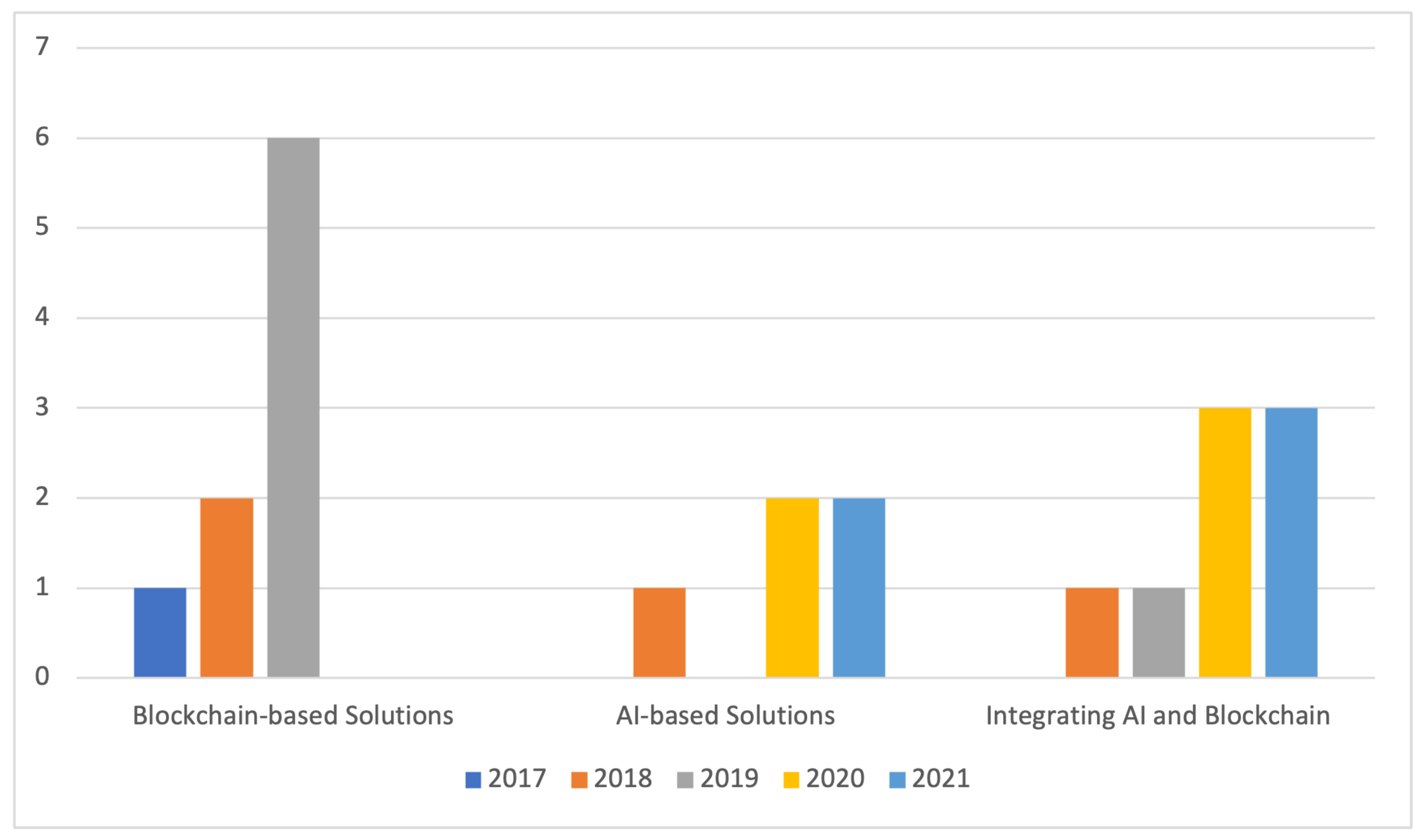
- Defining the Needs For SLR:From what we know, there has not been any systematic review of the literature on the empowerment of IoT network security by AI and Blockchain research together which led to the start of this work. Our paper discusses the recent studies during the period from 2017 to 2022. This SLR aims to discover how other researchers have remedied the security issues in the IoT network by AI and Blockchain. Then, explore the solutions and assess the studies to figure out how to secure IoT networks by integrating AI and Blockchain simultaneously.
- Indicating Research Questions:In accordance with our motivation, we set our research questions clearly to define the problems that our review aims to address (See Table 2).
3.2. Conducting Phase
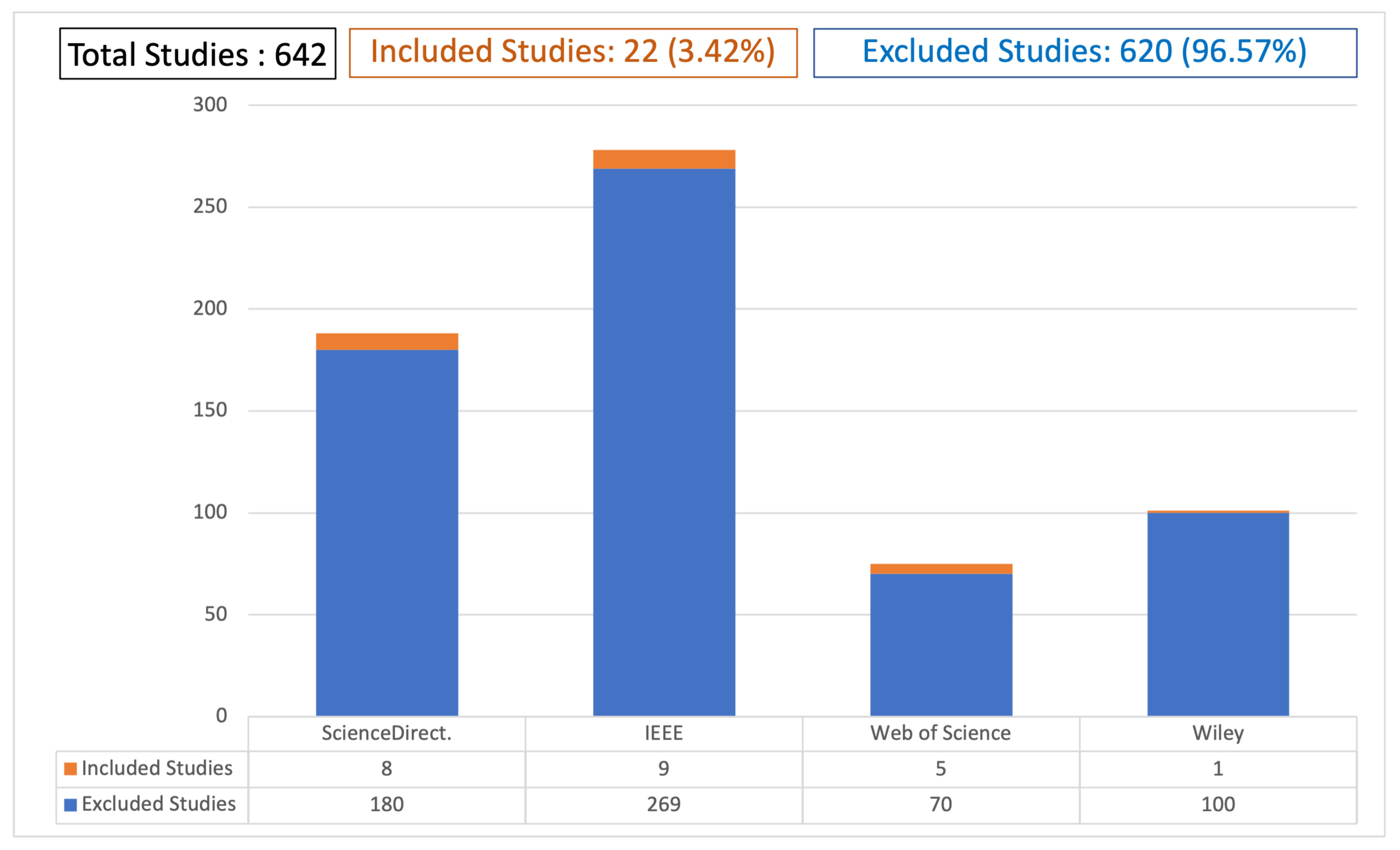
- Step 1: Studies Selection:In step one, we appiled a search strategy to find all relevant studies that fulfill the research objectives. Specifically, we performed two steps procedure that clarifies how to search for sources using search terms.
- First, we have determined the three groups of keywords considering the alternative spellings of the terms through the following strategy:
- -
- Defining the keywords related to the broad scope of the research as follows: Internet of Things, IoT security, network security, and cybersecurity.
- -
- Specifying the keywords related to enhancing IoT security by other technology as follows: Artificial Intelligence, Human Immune System, and Blockchain.
- -
- Narrowing down the research by selecting a set of terms related to the proposed solution type as follows: Intrusion detection system (IDS), Defense approach, Antivirus.
- Second, we have selected four digital libraries: IEEE, Web of Science, Wiley, and ScienceDirect. Then, we applied the keywords to these libraries using Boolean operators OR and AND. We have used OR between terms of each group and AND between keywords of different groups.
- Step 2: Filter the search results:In this step, we filtered down the papers from the search results to set the thematically relevant studies that can help us to answer the research questions of this SLR. We created a list of Inclusion and Exclusion Criteria (see Table 3). The following are the steps involved in this SLR’s selection and filtration:
- -
- Applying our criteria for inclusion and exclusion.
- -
- Removing any duplicate articles discovered in different libraries.
- -
- Searching on the article references to find additional related articles.
| Inclution Criteria | Exclution Criteria |
|---|---|
|
|
- Step 3: Data Extraction:In this step, we gathered the necessary data from each study to find the answer to our research questions. Table 5 presents the extracted data related to our search domain.In addition, Table 6 presents useful data related to Blockchain-based solutions, while Table 7 presents useful data related to AI-based solutions.Table 4. The most influential papers in the field of securing IoT networks ordered by year of publication.Table 4. The most influential papers in the field of securing IoT networks ordered by year of publication.
Studey No. Reference Year Title S1 [16] 2017 A Blockchain-Based Architecture for Collaborative DDoS Mitigation with Smart Contracts S2 [18] 2018 BlockSecIoTNet: Blockchain-Based Decentralized Security Architecture for IoT Network S3 [9] 2018 Towards decentralized IoT security enhancement: A Blockchain approach. S4 [7] 2018 Defense Scheme to Protect IoT from Cyber Attacks using AI Principles. S5 [19] 2018 SmartRetro: Blockchain-based Incentives for Distributed IoT Retrospective Detection. S6 [20] 2019 Autonomous and Malware-proof Blockchain-based Firmware Update Platform with Efficient Batch Verification for Internet of Things Devices. S7 [21] 2019 An Approach For An Distributed Anti-Malware System Based on Blockchain Technology. S8 [22] 2019 Secured Cyber-Attack Signatures Distribution using Blockchain Technology. S9 [23] 2019 Designing collaborative Blockchained signature-based intrusion detection in IoT environments. S10 [10] 2019 Privacy-Preserving Support Vector Machine Training Over Blockchain-Based Encrypted IoT Data in Smart Cities. S11 [24] 2019 Collaborative Blockchain-Based Detection of Distributed Denial of Service Attacks Based on Internet of Things Botnets. S12 [6] 2019 Designing a Blockchain- Based IoT With Ethereum, Swarm, and LoRa. S13 [25] 2020 Immune System Based Intrusion Detection System (IS-IDS): A Proposed Model. S14 [13] 2020 Biologically Inspired Smart Contract: A Blockchain-Based DDoS Detection System. S15 [26] 2020 Utilizing Blockchain for Distributed Machine Learning based Intrusion Detection in Internet of Things. S16 [12] 2020 BlockIoTIntelligence: A Blockchain-enabled Intelligent IoT Architecture with Artificial Intelligence. S17 [27] 2020 DeepDCA: Novel Network-Based Detection of IoT Attacks Using Artificial Immune System. S18 [5] 2021 Privacy-preserving in smart contracts using Blockchain and artificial intelligence for cyber risk measurements. S19 [28] 2021 A Bio-Inspired Reaction Against Cyberattacks: AIS-Powered Optimal Countermeasures Selection. S20 [29] 2021 IoTBoT-IDS: A novel statistical learning-enabled botnet detection framework for protecting networks of smart cities. S21 [30] 2021 A Framework for Mitigating DDoS and DOS Attacks in IoT Environment Using Hybrid Approach. S22 [31] 2021 A Distributed framework for detecting DDoS attacks in smart contract-based Blockchain-IoT Systems by leveraging Fog computing. Table 5. The Data extracted from selected studies.No. Year Solution Category IoT Attack Type S1 2017 DDoS mitigation solutions multiple domains. - DDoS attacks S2 2018 A decentralized security architecture ✓ TCP flooding, ICMP flooding, and DDoS Attacks. S3 2018 High-level security management scheme ✓ - S4 2018 Intrution Detection System ✓ DDoS S5 2018 Retrospective detection system ✓ - S6 2019 Firmware updating platform to enhance the process of updating firmware. (peer-to-peer file sharing system) ✓ DDoS and Malicious code S7 2019 Distributed Anti-Malware ✓ Malicious programs S8 2019 Architecture that securely stores and distribute attack signatures in real time for the purpose of prompt detection. - DoS attack S9 2019 Signature-based IDSs ✓ Worm attack and Flooding attack S10 2019 Privacy-Preserving Framework ✓ - S11 2019 Lightweight agents installed at multiple internet of things (IoT) installations. ✓ DDoS S12 2019 Standardized IoT infrastructure ✓ DDoS S13 2020 Intrution Detection System - - S14 2020 A DDoS Detection System - DDoS Attacks S15 2020 Intrution Detection System ✓ General S16 2020 IoT architecture with Blockchain and AI ✓ - S17 2020 Intrution Detection System ✓ General but tested on DDoS/DoS attacks, Reconnaissance, and Information Theft S18 2021 Privacy-preserving framework - - S19 2021 Intrusion reaction systems - - S20 2021 Botnet detection framework (intrusion detection methods) ✓ Botnet attacks S21 2021 Framework for Mitigating DDoS and DOS Attacks in IoT ✓ DDoS and DoS attacks S22 2021 Distributed Intrution Detection System ✓ DDoS Table 6. Data Related to Blockchain-based Solutions.Paper Techniques Blockchain Usage Layers of Architecture Blockchain Nodes Tools S1 A Blockchain-based approach to mitigate DDoS attack using smart contracts. The Blockchain is used to advertise the whitelisted or blacklisted IP addresses in a fully automated and distributed manner. The proposed architecture consists of three components: The customers, autonomous systems, and Blockchain with smart contracts. The autonomous systems are connected to the Blockchain and work as collaborative nodes to publish the IP address list. Moreover, the customers are connected to the Blockchain to report the IP address list. Ethereum platform and Solidity smart contracts S2 A Blockchain based detection model copuled with SDN. Blockchain is used to provide a decentralized attack detection model. To mitigate the issue of a single point of failure through a dynamic approach that updates the detection model using Blockchain. The proposed approch is constructed from four layers: sensing, edge, fog, and cloud layers. The fog nodes are connected to the Blockchain, and they communicate with each other via peer-to-peer transactions using a smart contract. Ethereum and Mininet emulator S5 A Blockchain-based incentive platform The Blockchain is used to build a distributed incentive platform consisting of a group of detectors. In which these detectors cooperate to detect the vulnerabilities and share their results. The proposed framework includes three participators: IoT providers, IoT detectors, and IoT consumers. Distributed detectors Ethereum platform S6 A autonomous and Malware-proof firmware based on Blockchain. The proposed firmware employs the Blockchain to update system considering the integrity and enforce the scanning via smart contract. The proposed system contains four phases: phase one is the system setup and registration phase. The second phase is the manufacturer updates the firmware procedure. Thirdly, the device query and update procedure phase. Finally, the transaction and batch verification phase. There is four type of node: the Blockchain full node, client node, storing node, and manufacturer node. Ethereum Blockchain, VirusTotal, and distributed storage scheme swarm. S8 A Blockchain-based cooperative intrusion detection The Blockchain is e mployed to store and distribute the signatures of cyber attacks. The proposed architecture is constructed from three stages: Signature extraction, signature storage, and signature distribution. The IDS nodes are connected to the Blockchain, where they are divided into two groups: Authorized nodes and Unauthorized nodes. Ethereum platform and Ubuntu S9 A Collaborative Blockchained signature-based intrusion detection. The Blockchain is used to share the signatures between different nodes without a trusted intermediary. The proposed signature-based IDS model consists of three components: The Peer-to-peer communication component, the collaboration component, and the trust management component. A group of verified IDS nodes Snort and a proof-of-concept Blockchain. S10 A Blockchain-based data sharing approach. The Blockchain is utilized to create a secure and reliable data-sharing approach to train a classifier. The proposed approach is consist of four components: IoT devices, IoT data providers, IoT data sharing platform, and IoT data processing. Data providers and data analysts Java Development Kit 1.8. S11 A Blockchain-based DDoS detection approach The Blockchain is used to allow agents exchange the information about the outbound traffic by smart contracts. - The agents are connected to a private network, and they are installed on the gateway usually - S14 A DDoS detection approach based on a Blockchain-based collaborative using a biologically Inspired Smart Contract. A consortium chain structure to treat all participants as part of the private chain in the system. The proposed approach is constructed three layer: application layer, the contract layer, the network layer. All node are connected to Blockchain where every node is linked to its own private chain and can access the public chain in case abnormal behavior is detected. - S15 A Blockchain-based distributed intrusion detection. The Blockchain is used to share the attackers’ information (IP addresses) between the autonomous system border area nodes. The proposed system includes three phases: the first phase is the spectral partitioning technique. The second phase is the training of a machine learning model using a set of features to detect intrusions. The third phase is the Blockchain deployment phase. A set of AS border area nodes are selected to be connected to the Blockchain. Ethereum platform, MATLAB, Python-3, and web-3. S18 A privacy-preserving approach using a smart contracts. The Blockchain is used to verify whether the participant is legal or illegal to provide a secure data-sharing environment. The proposed approach is constructed from three layers: The system management layer, user layer, and cloud storage layer. - Hyperledger Fabric
- Step 4: Quality assessment:Following our comprehensive study, we defined a set of metrics of the ideal security model that can protect IoT networks considering the nature of the IoT environment. In particular, the goal of this step is that assess the selected studies based on the research questions.The following are the most desirable metrics:
- -
- Distributed: As the IoT network is a distributed environment the security model must defeat cybersecurity attacks using a distributed manner.
- -
- Adaptive: Can learn and develop its behaviors over time as the attacker develop an advanced approach day by day.
- -
- Privacy preserving: Able to avoid the data breaches and exchange the important information securely.
- -
- Collaborative: Promote collaboration among organizations through sharing the attacks’ signature response to threats.
- -
- Defeat IoT Botnet: Can protect IoT devices as the attacker can exploit unsecured IoT devices to launch an attack.
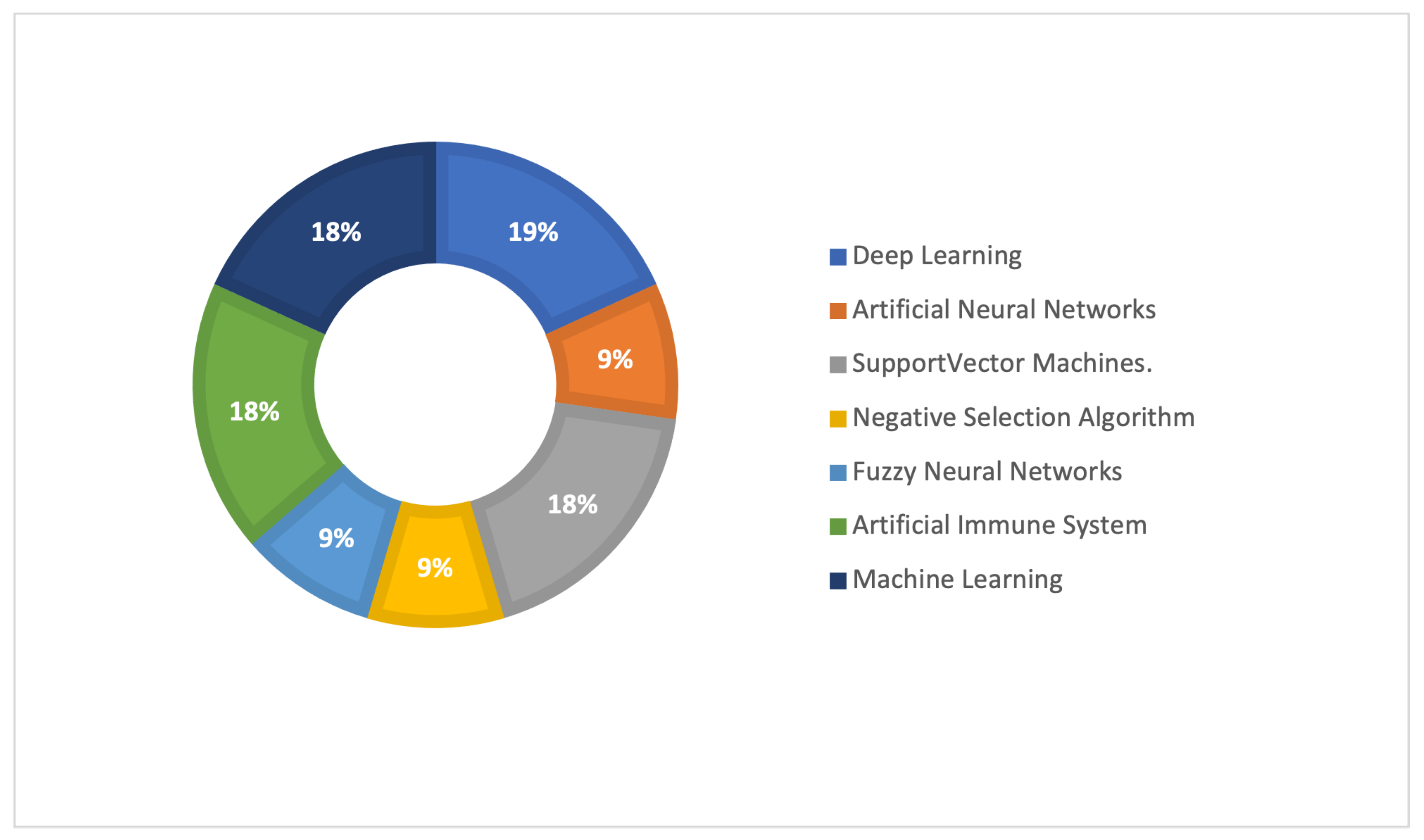
| Studey No. | AI Type | Dataset | Source |
|---|---|---|---|
| S2 | Deep Learning | NSL-KDD dataset | [32] |
| S4 | Artificial Neural Networks | - | |
| S10 | Support Vector Machines. | Breast Cancer Wisconsin Data Set (BCWD) and Heart Disease Data Set (HDD) | [33,34] |
| S13 | Negative Selection Algorithm | KDD 99 standard dataset and UNSW-NB15 dataset | [35,36] |
| S14 | Fuzzy Neural Networks. | CICDDoS2019 dataset | [37] |
| S15 | Support Vector Machines. | NSL-KDD and UNSW-NB15 | [36,38] |
| S17 | Deep Learning and Artificial Immune System | BoT-IoT dataset | [39] |
| S18 | Machine Learning (Decision-tree, nearest neighbor, and Naïve Bayes). | - | |
| S19 | Artificial Immune System | - | |
| S22 | Machine Learning (Random forest (RF) and XGBoost) | BoT-IoT dataset | [39] |
| Study ID | Distributed | Adaptive | Privacy Preserving | Collaborative | Defeats IoT Botnet | Total |
|---|---|---|---|---|---|---|
| S1 | 1 | 0 | 1 | 1 | 1 | 4 |
| S2 | 1 | 1 | 1 | 1 | 1 | 5 |
| S3 | 1 | 0 | 1 | 1 | 1 | 4 |
| S4 | 0 | 1 | 0 | 0 | 0 | 1 |
| S5 | 1 | 0 | 1 | 1 | 1 | 4 |
| S6 | 1 | 0 | 1 | 1 | 0 | 3 |
| S7 | 1 | 0 | 1 | 1 | 0 | 3 |
| S8 | 1 | 0 | 1 | 1 | 0 | 3 |
| S9 | 1 | 0 | 1 | 1 | 0 | 3 |
| S10 | 1 | 1 | 1 | 1 | 0 | 4 |
| S11 | 1 | 0 | 1 | 1 | 1 | 4 |
| S12 | 1 | 0 | 1 | 1 | 1 | 4 |
| S13 | 0 | 1 | 0 | 0 | 0 | 1 |
| S14 | 1 | 1 | 1 | 1 | 1 | 5 |
| S15 | 1 | 1 | 1 | 1 | 0 | 4 |
| S16 | 1 | 1 | 1 | 1 | 0 | 4 |
| S17 | 0 | 1 | 0 | 0 | 1 | 2 |
| S18 | 1 | 1 | 1 | 1 | 0 | 4 |
| S19 | 0 | 1 | 0 | 0 | 0 | 1 |
| S20 | 0 | 1 | 0 | 0 | 1 | 2 |
| S21 | 0 | 1 | 1 | 0 | 0 | 2 |
| S22 | 1 | 1 | 1 | 1 | 1 | 5 |
| Total | 16 | 13 | 17 | 16 | 10 | Avg = 3.27 |
3.3. Reporting Phase
- -
- The dissemination strategy identification.
- -
- The report formatting.
- -
- The report evaluation.
4. Analysis
4.1. What Are the Needs for Integrating AI and Blockchain Technologies with IoT to Secure Its Network?
4.2. What Are the Recent Approaches That Handle the Security Concerns in the IoT Environment by Integrating AI Algorithms and Blockchain?
4.2.1. AI-Based Approaches
4.2.2. Blockchain-Based Approaches
4.2.3. The Integration of IoT, Blockchain, AI
4.3. What Are the Research Gaps and Future Directions within the Security of IoT Networks Based on AI and Blockchain Technologies
4.3.1. The Research Gaps
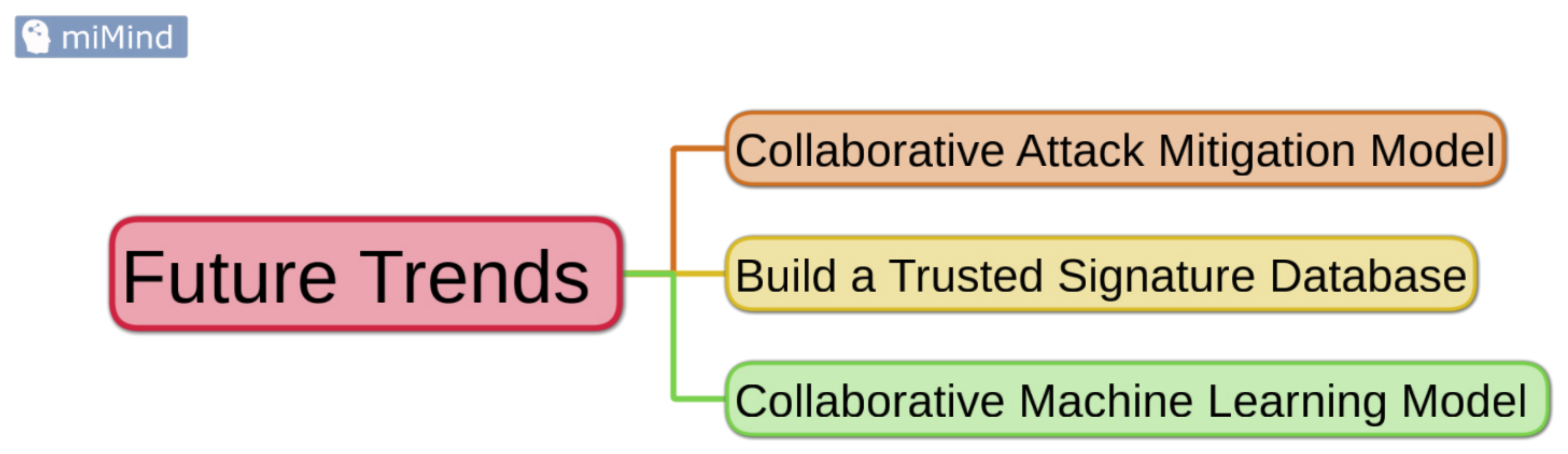
4.3.2. Future Directions
- Collaborative Machine Learning (ML) Model:Although the ML-based IDS has the power to extract and process IoT data in real-time to analyze the data to detect intrusions, it suffers from a single-point-failure problem as it usually builds on a centralized-single server to train ML model. And many studies have proposed distributed ML solutions to carry out this issue. However, the distributed ML-based approaches involve a group of collaborative participants, which makes the data-sharing process a critical concern.To deal with these issues, recent studies have tended to link AI with Blockchain as it encourages participants to share information between IDS participants in a secure and decentralized manner. But this strategy is still in a formative phase and under investigation, and it has several obstacles due to the cost of computation, storage constraints, and the dynamic nature of the IoT network. Nevertheless, it needs more attention to provide a lightweight solution. More experiments using this approach would lead to the next wave of revolution in IoT network security.
- Collaborative Attack Mitigation Model:Some existing defense approaches lack the resources to cope with cybersecurity attacks alone. And utilizing other companies’ resources might be an efficient way to share the burden and mitigate attacks. The IP address is one of the most valuable pieces of information that could be shared among companies to mitigate the attacks. Recently the researchers employed the Blockchain to advertise black or whitelisted IP addresses, especially to defeat DDoS attacks. Though there is a benefit in employing Blockchain to advertise black- or whitelisted IP addresses, this approach works as an additional method. Therefore, it needs more investigation to be combined with the existing AI-based solutions without changing existing ones. Furthermore, such integrations need further research to deal with a dynamic IP address.Moreover, updating the list is a critical issue and must be performed professionally and in a timely manner. For example, when the attacker launches the attack using a victim’s device, the IP address of the victim device should be unblocked after the recovery process using antivirus. Further, its behavior must remain under observation for a while to avoid another violation. Thus, more research is needed to get deep into real-world scenarios.
- Build a Trusted Signature Database:Researchers recently employed Blockchain to build a trusted database that contains attack signatures where a group of IoT nodes is connected to a Blockchain. These nodes cooperate to create this database where every node signs a signature using its private key. Each node monitors the traffic to define signatures periodically using an analytical algorithm. However, these studies faced several limitations and are still in early research and need more investigation as they do not consider the insider attack.
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Saxena, S.; Bhushan, B.; Ahad, M.A. Blockchain based solutions to secure IoT: Background, integration trends and a way forward. J. Netw. Comput. Appl. 2021, 181, 103050. [Google Scholar] [CrossRef]
- Aldhaheri, S.; Alghazzawi, D.; Cheng, L.; Barnawi, A.; Alzahrani, B.A. Artificial Immune Systems approaches to secure the internet of things: A systematic review of the literature and recommendations for future research. J. Netw. Comput. Appl. 2020, 157, 102537. [Google Scholar] [CrossRef]
- Vishwakarma, R.; Jain, A.K. A survey of DDoS attacking techniques and defence mechanisms in the IoT network. Telecommun. Syst. 2020, 73, 3–25. [Google Scholar] [CrossRef]
- Singh, S.; Sharma, P.K.; Yoon, B.; Shojafar, M.; Cho, G.H.; Ra, I.H. Convergence of blockchain and artificial intelligence in IoT network for the sustainable smart city. Sustain. Cities Soc. 2020, 63, 102364. [Google Scholar] [CrossRef]
- Deebak, B.D.; Fadi, A.T. Privacy-preserving in smart contracts using blockchain and artificial intelligence for cyber risk measurements. J. Inf. Secur. Appl. 2021, 58, 102749. [Google Scholar] [CrossRef]
- Ozyilmaz, K.R.; Yurdakul, A. Designing a Blockchain-based IoT with Ethereum, swarm, and LoRa: The software solution to create high availability with minimal security risks. IEEE Consum. Electron. Mag. 2019, 8, 28–34. [Google Scholar] [CrossRef]
- Ahanger, T.A. Defense scheme to protect IoT from cyber attacks using AI principles. Int. J. Comput. Commun. Control. 2018, 13, 915–926. [Google Scholar] [CrossRef]
- Atlam, H.F.; Walters, R.J.; Wills, G.B. Intelligence of things: Opportunities & challenges. In Proceedings of the 2018 3rd Cloudification of the Internet of Things (CIoT), Paris, France, 2–4 July 2018; pp. 1–6. [Google Scholar]
- Qian, Y.; Jiang, Y.; Chen, J.; Zhang, Y.; Song, J.; Zhou, M.; Pustišek, M. Towards decentralized IoT security enhancement: A blockchain approach. Comput. Electr. Eng. 2018, 72, 266–273. [Google Scholar] [CrossRef]
- Shen, M.; Tang, X.; Zhu, L.; Du, X.; Guizani, M. Privacy-preserving support vector machine training over blockchain-based encrypted IoT data in smart cities. IEEE Internet Things J. 2019, 6, 7702–7712. [Google Scholar] [CrossRef]
- Liu, Y.; Yu, F.R.; Li, X.; Ji, H.; Leung, V.C. Blockchain and machine learning for communications and networking systems. IEEE Commun. Surv. Tutor. 2020, 22, 1392–1431. [Google Scholar] [CrossRef]
- Singh, S.K.; Rathore, S.; Park, J.H. Blockiotintelligence: A blockchain-enabled intelligent IoT architecture with artificial intelligence. Future Gener. Comput. Syst. 2020, 110, 721–743. [Google Scholar] [CrossRef]
- Han, X.; Zhang, R.; Liu, X.; Jiang, F. Biologically Inspired Smart Contract: A Blockchain-Based DDoS Detection System. In Proceedings of the 2020 IEEE International Conference on Networking, Sensing and Control (ICNSC), Nanjing, China, 30 October–2 November 2020; pp. 1–6. [Google Scholar]
- Kowalski, M.; Lee, Z.W.; Chan, T.K. Blockchain technology and trust relationships in trade finance. Technol. Forecast. Soc. Chang. 2021, 166, 120641. [Google Scholar] [CrossRef]
- Sandner, P.; Gross, J.; Richter, R. Convergence of Blockchain, IoT, and AI. Front. Blockchain 2020, 3, 522600. [Google Scholar] [CrossRef]
- Rodrigues, B.; Bocek, T.; Lareida, A.; Hausheer, D.; Rafati, S.; Stiller, B. A blockchain-based architecture for collaborative DDoS mitigation with smart contracts. In Proceedings of the IFIP International Conference on Autonomous Infrastructure, Management and Security, Zurich, Switzerland, 10–13 July 2017; Springer: Cham, Switzerland, 2017; pp. 16–29. [Google Scholar]
- Kitchenham, B.; Charters, S. Guidelines for Performing Systematic Literature Reviews in Software Engineering. Volume 5. Technical Report, Ver. 2.3 ebse Technical Report. ebse. 2007. Available online: https://www.elsevier.com/__data/promis_misc/525444systematicreviewsguide.pdf (accessed on 18 November 2022).
- Rathore, S.; Kwon, B.W.; Park, J.H. BlockSecIoTNet: Blockchain-based decentralized security architecture for IoT network. J. Netw. Comput. Appl. 2019, 143, 167–177. [Google Scholar] [CrossRef]
- Wu, B.; Li, Q.; Xu, K.; Li, R.; Liu, Z. Smartretro: Blockchain-based incentives for distributed iot retrospective detection. In Proceedings of the 2018 IEEE 15th International Conference on Mobile Ad Hoc and Sensor Systems (MASS), Chengdu, China, 9–12 October 2018; pp. 308–316. [Google Scholar]
- Hu, J.W.; Yeh, L.Y.; Liao, S.W.; Yang, C.S. Autonomous and malware-proof blockchain-based firmware update platform with efficient batch verification for Internet of Things devices. Comput. Secur. 2019, 86, 238–252. [Google Scholar] [CrossRef]
- Talukder, S.; Roy, S.; Al Mahmud, T. An approach for an distributed anti-malware system based on blockchain technology. In Proceedings of the 2019 11th International Conference on Communication Systems & Networks (COMSNETS), Bengaluru, India, 7–11 January 2019; pp. 1–6. [Google Scholar]
- Ajayi, O.; Cherian, M.; Saadawi, T. Secured cyber-attack signatures distribution using blockchain technology. In Proceedings of the 2019 IEEE International Conference on Computational Science and Engineering (CSE) and IEEE International Conference on Embedded and Ubiquitous Computing (EUC), New York, NY, USA, 1–3 August 2019; pp. 482–488. [Google Scholar]
- Li, W.; Tug, S.; Meng, W.; Wang, Y. Designing collaborative blockchained signature-based intrusion detection in IoT environments. Future Gener. Comput. Syst. 2019, 96, 481–489. [Google Scholar] [CrossRef]
- Spathoulas, G.; Giachoudis, N.; Damiris, G.P.; Theodoridis, G. Collaborative blockchain-based detection of distributed denial of service attacks based on internet of things botnets. Future Internet 2019, 11, 226. [Google Scholar] [CrossRef]
- Dutt, I.; Borah, S.; Maitra, I.K. Immune system based intrusion detection system (IS-IDS): A proposed model. IEEE Access 2020, 8, 34929–34941. [Google Scholar] [CrossRef]
- Cheema, M.A.; Qureshi, H.K.; Chrysostomou, C.; Lestas, M. Utilizing blockchain for distributed machine learning based intrusion detection in internet of things. In Proceedings of the 2020 16th International Conference on Distributed Computing in Sensor Systems (DCOSS), Marina del Rey, CA, USA, 25–27 May 2020; pp. 429–435. [Google Scholar]
- Aldhaheri, S.; Alghazzawi, D.; Cheng, L.; Alzahrani, B.; Al-Barakati, A. DeepDCA: Novel network-based detection of IoT attacks using artificial immune system. Appl. Sci. 2020, 10, 1909. [Google Scholar] [CrossRef]
- Nespoli, P.; Mármol, F.G.; Vidal, J.M. A Bio-Inspired Reaction Against Cyberattacks: AIS-Powered Optimal Countermeasures Selection. IEEE Access 2021, 9, 60971–60996. [Google Scholar] [CrossRef]
- Ashraf, J.; Keshk, M.; Moustafa, N.; Abdel-Basset, M.; Khurshid, H.; Bakhshi, A.D.; Mostafa, R.R. IoTBoT-IDS: A Novel Statistical Learning-enabled Botnet Detection Framework for Protecting Networks of Smart Cities. Sustain. Cities Soc. 2021, 72, 103041. [Google Scholar] [CrossRef]
- Ghali, A.A.; Ahmad, R.; Alhussian, H. A Framework for Mitigating DDoS and DOS Attacks in IoT Environment Using Hybrid Approach. Electronics 2021, 10, 1282. [Google Scholar] [CrossRef]
- Kumar, P.; Kumar, R.; Gupta, G.P.; Tripathi, R. A Distributed framework for detecting DDoS attacks in smart contract-based Blockchain-IoT Systems by leveraging Fog computing. Trans. Emerg. Telecommun. Technol. 2021, 32, e4112. [Google Scholar] [CrossRef]
- Tavallaee, M.; Bagheri, E.; Lu, W.; Ghorbani, A.A. A detailed analysis of the KDD CUP 99 data set. In Proceedings of the 2009 IEEE Symposium on Computational Intelligence for Security and Defense Applications, Ottawa, ON, Canada, 8–10 July 2009; pp. 1–6. [Google Scholar]
- Dua, D.; Graff, C. Machine Learning Repository. University of California, Irvine, School of Information and Computer Sciences. 2017. Available online: http://archive.ics.uci.edu/ml (accessed on 16 January 2022).
- Detrano, R.; Janosi, A.; Steinbrunn, W.; Pfisterer, M.; Schmid, J.J.; Sandhu, S.; Guppy, K.H.; Lee, S.; Froelicher, V. International application of a new probability algorithm for the diagnosis of coronary artery disease. Am. J. Cardiol. 1989, 64, 304–310. [Google Scholar] [CrossRef]
- Cup, K. 2007. KDD Cup 1999 Data. Available online: http://kdd.ics.uci.edu/databases/kddcup99/kddcup99.html (accessed on 16 January 2022).
- Moustafa, N.; Slay, J. UNSW-NB15: A comprehensive data set for network intrusion detection systems (UNSW-NB15 network data set). In Proceedings of the 2015 Military Communications and Information Systems Conference (MilCIS), Canberra, Australia, 10–12 November 2015; pp. 1–6. [Google Scholar]
- Qu, X.; Yang, L.; Guo, K.; Ma, L.; Sun, M.; Ke, M.; Li, M. A survey on the development of self-organizing maps for unsupervised intrusion detection. Mob. Netw. Appl. 2021, 26, 808–829. [Google Scholar] [CrossRef]
- Revathi, S.; Malathi, A. A detailed analysis on NSL-KDD dataset using various machine learning techniques for intrusion detection. Int. J. Eng. Res. Technol. (IJERT) 2013, 2, 1848–1853. [Google Scholar]
- Koroniotis, N.; Moustafa, N.; Sitnikova, E.; Turnbull, B. Towards the development of realistic botnet dataset in the internet of things for network forensic analytics: Bot-iot dataset. Future Gener. Comput. Syst. 2019, 100, 779–796. [Google Scholar] [CrossRef]
- Mehra, M.; Paranjape, J.N.; Ribeiro, V.J. Improving ML Detection of IoT Botnets using Comprehensive Data and Feature Sets. In Proceedings of the 2021 International Conference on COMmunication Systems & NETworkS (COMSNETS), Bangalore, India, 5–9 January 2021; pp. 438–446. [Google Scholar]
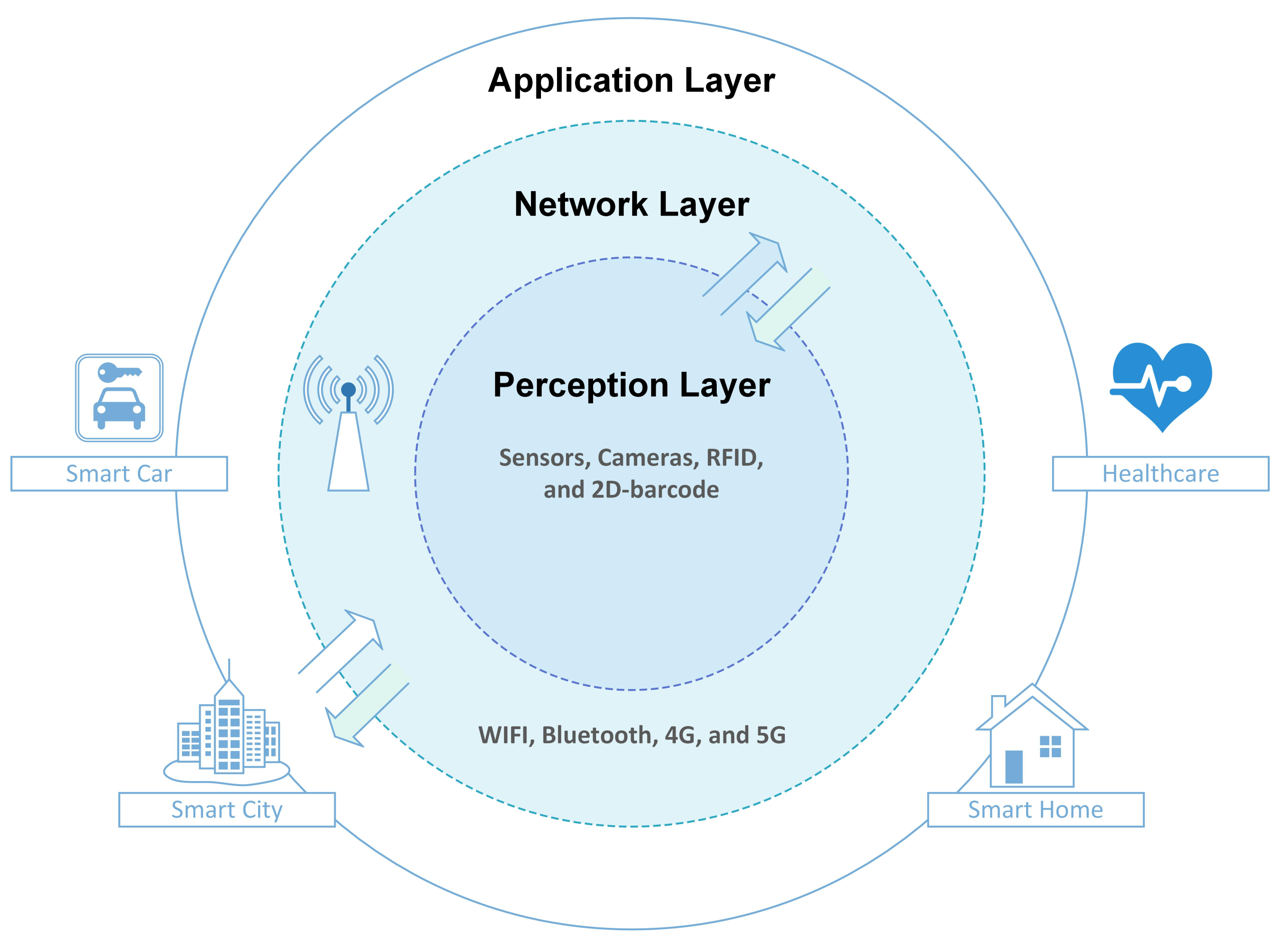
| Type | Action | IoT Layer | Effect |
|---|---|---|---|
| End Device Attacks | The attacker owns the physical control of IoT devices. | Perception Layer | The attacker can access confidential data such as keys and certificates. Further, the attacker may use the stolen confidential data to pretend to be an authentic node. |
| Communication Channel Attacks | The attacker intercepts the communication of the unencrypted channels to gain access to the confidential data. | Network layer | Disclosure of IoT data. |
| Network Protocol Attacks | The attacker exploits the vulnerabilities of the used network protocol to launch different attacks such as blackhole attacks, reply attacks, DDoS attacks. | Network layer & Application layer | The efficiency and precision of the IoT network would be degraded by this type of attack. |
| Sensory Data Attacks | The attacker alters and tampers the data before they reach the destination. | Network layer & Application layer | Corrupted data will be spread across the IoT network. |
| DoS Attack | The attacker depletes the IoT resources by sending a huge number of fake requests to make IoT services unavailable to authorized users. | Network layer & Application layer | The IoT resources will be completely consumed, and the whole network will be overwhelmed. |
| Software Attacks | The attacker exploits the software vulnerabilities to own full control of software using malicious scripts, viruses, and worms. | Application layer | The attacker uses these types of attacks to perform advanced attacks such as the DoS attack. |
| Research Question | Motivations |
|---|---|
| What are the need for integrating AI and Blockchain technologies with IoT to secure its network? | To get insight into recent IoT security solutions that integrate IoT with other emerging technology for improving its security and addressing their effectiveness in a secure manner. |
| What are the recent approaches that handle the security concerns in the IoT environment by integrating AI algorithms and Blockchain? | Determine, contrast, and categorize the IoT security techniques currently in use. |
| What are the research gaps and future directions within the security of IoT networks based on AI and Blockchain technologies? | Realize the research gaps and future directions in IoT security. |
| Strength-Points | Limitations |
|---|---|
|
|
| Strength-Points | Limitations |
|---|---|
|
|
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alharbi, S.; Attiah, A.; Alghazzawi, D. Integrating Blockchain with Artificial Intelligence to Secure IoT Networks: Future Trends. Sustainability 2022, 14, 16002. https://doi.org/10.3390/su142316002
Alharbi S, Attiah A, Alghazzawi D. Integrating Blockchain with Artificial Intelligence to Secure IoT Networks: Future Trends. Sustainability. 2022; 14(23):16002. https://doi.org/10.3390/su142316002
Chicago/Turabian StyleAlharbi, Shatha, Afraa Attiah, and Daniyal Alghazzawi. 2022. "Integrating Blockchain with Artificial Intelligence to Secure IoT Networks: Future Trends" Sustainability 14, no. 23: 16002. https://doi.org/10.3390/su142316002
APA StyleAlharbi, S., Attiah, A., & Alghazzawi, D. (2022). Integrating Blockchain with Artificial Intelligence to Secure IoT Networks: Future Trends. Sustainability, 14(23), 16002. https://doi.org/10.3390/su142316002





