Blockchain-Based Solutions Supporting Reliable Healthcare for Fog Computing and Internet of Medical Things (IoMT) Integration
Abstract
1. Introduction
2. Background
2.1. IoT and IoMT
2.2. Types of IoMT Devices
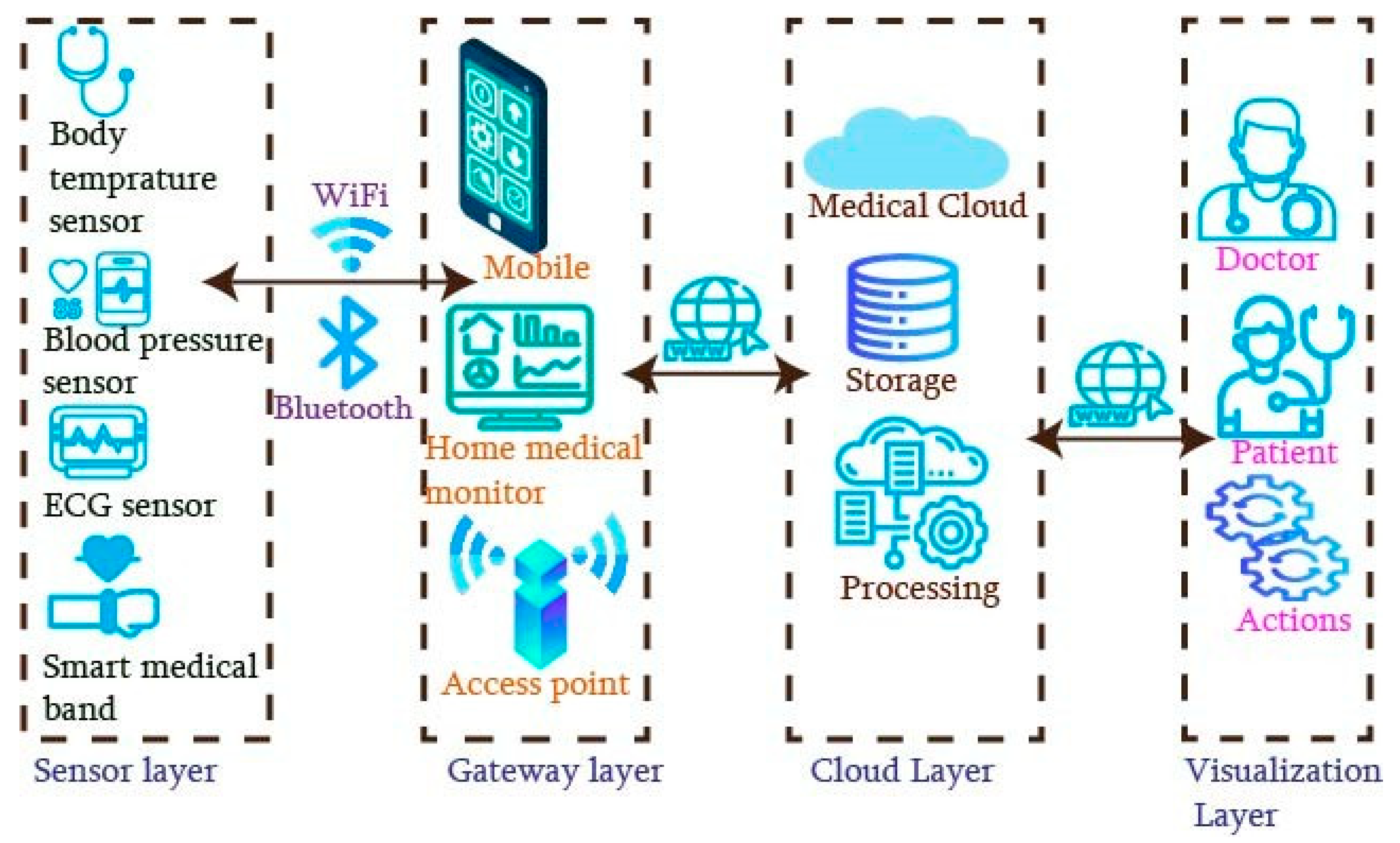
2.3. IoMT System Architecture
- Sensor/Perception layer: this consists of a collection of biometric sensors embedded or attached to the patient. The records are communicated to the succeeding layer using wireless protocols such as Wi-Fi [3].
- Gateway layer: unprocessed data are sent to the succeeding gateway layer owing to the memory and computing limitations of the IoMT devices. It can utilize the mobile phone or a devoted access point (AP), which are generally more potent than sensing nodes. These are capable of performing the basic pre-processing tasks, such as the validation and storage of data for a small duration, and elementary AI-based investigations. Additionally, these middleware devices use the internet to transmit the data collected from sensors to the cloud layer.
- Cloud layer: this is accountable for storing, analyzing, and providing secure access to data received from the gateway. Any fluctuations in the patient’s health may be detected by data processing and then presented for subsequent processing by healthcare professionals. The key generation server (KGS) generates IDs and keys for every node in the system. This layer enables remote sensor management and access control.
- Application layer: this presents the data to doctors and patients to monitor fitness. It also comprises the physician’s recommendations according to the patient’s medical situation. Instances of action comprise recommending or modifying the number of numerous drugs [15].
2.4. IoMT Security Requisites
- Confidentiality: The capacity to maintain the confidentiality of data during their gathering, transmission, or storage. Moreover, the data should be available only to authorized persons. Data encryption and access control mechanisms are the most prevalent methods for meeting these conditions [18].
- Integrity pertains to the data’s protection against unauthorized modification through the gathering, communicating, and storing phases.
- Availability is the capability to keep IoMT systems operational uninterruptedly. It can be achieved by keeping the structure current, observing any performance changes, supporting alternate storage or transmission routes in the event of DoS attacks, and promptly resolving any issues.
- Non-repudiation refers to the capacity to hold accountable every authorized user for their actions. This constraint ensures that no communication within the system can be denied. It is possible by employing digital signature techniques, which will be discussed in greater detail later in the article.
- Authentication refers to the competence to authenticate a user attempting to access a system. Conjoint authentication is the utmost secure practice in which both the server and the client endorse each other in advance to exchange secure data or keys.
2.5. Derived Security Requirements:
- Authorization: The capability to restrict to authentic users the authorization of command execution. Alike to confidentiality, authorization can be attained by employing cryptography and access control methods.
- Anonymity: When interacting with the system, the capacity to conceal the identities of patients and physicians from unauthorized users. By employing smart cards, the anonymity criterion can be satisfied.
- Forward/Backward Secrecy: Forward secrecy enables the protection of future-communicated data/keys, even if previously transmitted data/keys have been compromised. Backward secrecy safeguards that even if a successful attack compromises current data/keys, older data/keys remain secure.
- Secure Key Exchange: The capacity to share keys among nodes of a system in a secure manner.
- Resilience: The system administrator cannot assume a valid user’s identity; this requirement protects against internal threats. This requirement can be satisfied with asymmetric keys and a cryptographic hash function (CHF).
- Session Key Agreement: After the authentication procedure, the system’s nodes must use session keys. Similar to key escrow resilience, using a CHF satisfies this necessity.
2.6. IoMT Security Threats
3. Fog and Edge Computing
3.1. Blockchain
3.2. Blockchain Types:
- Public: A public BC, which is accessible to everyone on the planet, sends and verifies transactions. In this case, all nodes can participate in the consensus process.
- Private: Without authorization, no one can join this sort of BC; the consensus process is controlled by a few privileged nodes of a single business.
- Consortium: As this sort of BC is somewhat decentralized, access to data may be public or private; in other words, it is a hybrid. Similarly to a hyperledger, multiple actors govern the consensus process here rather than a single organization [51].
3.3. Blockchain Characteristics:
- Decentralization: No central authority exists for BC nodes. Each participant node in the BC undertakes network maintenance tasks to keep the network operational. Damage to one or a few nodes will not affect the system’s functionality [52].
- Trust: Nodes are not required to rely on verifiable third-party entities to establish pre-established trust connections between themselves. As long as they adhere to the BC protocol, distributed nodes are capable of dependable collaboration and interaction [53].
- Anonymity: In the BC, users are identified solely by their public key addresses. As a result, users can conduct transactions without disclosing their true identities.
- Tamper resistance: The related blocks in a BC system have a verification relationship. To alter the data in a block, the complete chain of blocks must be altered, and it must be altered within a certain period. Therefore, the more nodes in the system, the more secure the BC.
- Traceability: The BC stores data in a block structure, adding a time dimension. Each transaction on the block is cryptographically connected to two neighboring blocks, allowing for the traceability of each transaction.
- Programmability: The BC enables the construction of services at the application layer via on-chain scripts, and users can employ smart contracts to implement complex decentralized apps.
4. Blockchain Solution for IoMT-Fog Framework
- Reduce the data sent to the cloud: FC employs ingenious sensing and filtering techniques to send only the most valuable and essential data to the cloud; the remainder is stored locally on the network’s fog nodes.
- Low latency: Fog nodes can manage data, decision-making, and reporting without relying on distant cloud facilities. Particularly, these features save a great deal of time in an automated IoT context.
- Reduced bandwidth: In cloud computing, the transmission and processing of sensed data necessitate a significant bandwidth. In the case of FC, however, this problem does not exist because the majority of data are stored and processing is performed within the local network, thereby significantly reducing bandwidth consumption.
- Security enhancement: FC limits the exposure of the most sensitive and secret data to the most susceptible public network (the internet), thereby securing the data against attacks.
- Thus, FC reduces the strain on smart city components by enabling more dependable and rapid data exchange. Subsequently, fog (edge) computing smart cities have proliferated in a diversity of social sectors, including healthcare, manufacturing, education, transport, energy, and utilities.
- FC-based IoT is a theme of current interest. Previous publications omitted crucial security considerations, such as the fact that data transmitted from IoMT devices to cloud servers are naturally not encrypted, leaving them vulnerable to tampering and attack. This poses a risk of compromising patient confidentiality. There is an urgent need for IoMT node identification, leading to medical record authentication and validation. This objective can be easily attained by integrating BC technology into the IoT-FC system. Specifically, servers at the network’s edge should perform the authentication task in a decentralized manner [58]. BC technology is characterized by features such as decentralization, persistence, anonymity, and auditability. The BC persistency feature ensures the ability to evaluate trust and provides the means to demonstrate the authenticity of data. BC anonymity can aid in concealing the identity of producers and consumers [49]. BC’s decentralized connected registries can identify and thwart malicious actions. In addition, a BC compromises several fundamental technologies, such as digital signatures, cryptographic hash, and distributed consensus mechanisms. Smart contracts in a BC are effective authentication rules for IoT devices that protect data privacy [59]. A BC provides a secure communiqué between IoMT nodes, empowers the verification of device identity, and ensures the validation of transactions incorporating cryptographic means [60].
- BC can be a valuable technology for addressing the aforementioned security and privacy issues in FC-IoT systems due to the aforementioned characteristics. It is effortless, dependable, and secure [61]. A BC safeguards the security, authentication, and integrity of data communicated by IoT devices that have been cryptographically validated and assigned by the sender’s authentic identity. A BC facilitates the secure monitoring of IoT device transactions. BC technology can provide FC-enabled IoT systems with the means to construct and manage decentralized trust and security solutions due to FC’s distributed computing environment [62]. It provides self-healing capabilities to IoT systems enabled by the fog. The security system equipped with BC-based security satisfies the majority of the fog-enabled IoT system requirements by improving the independence of operations between all connected nodes [63].
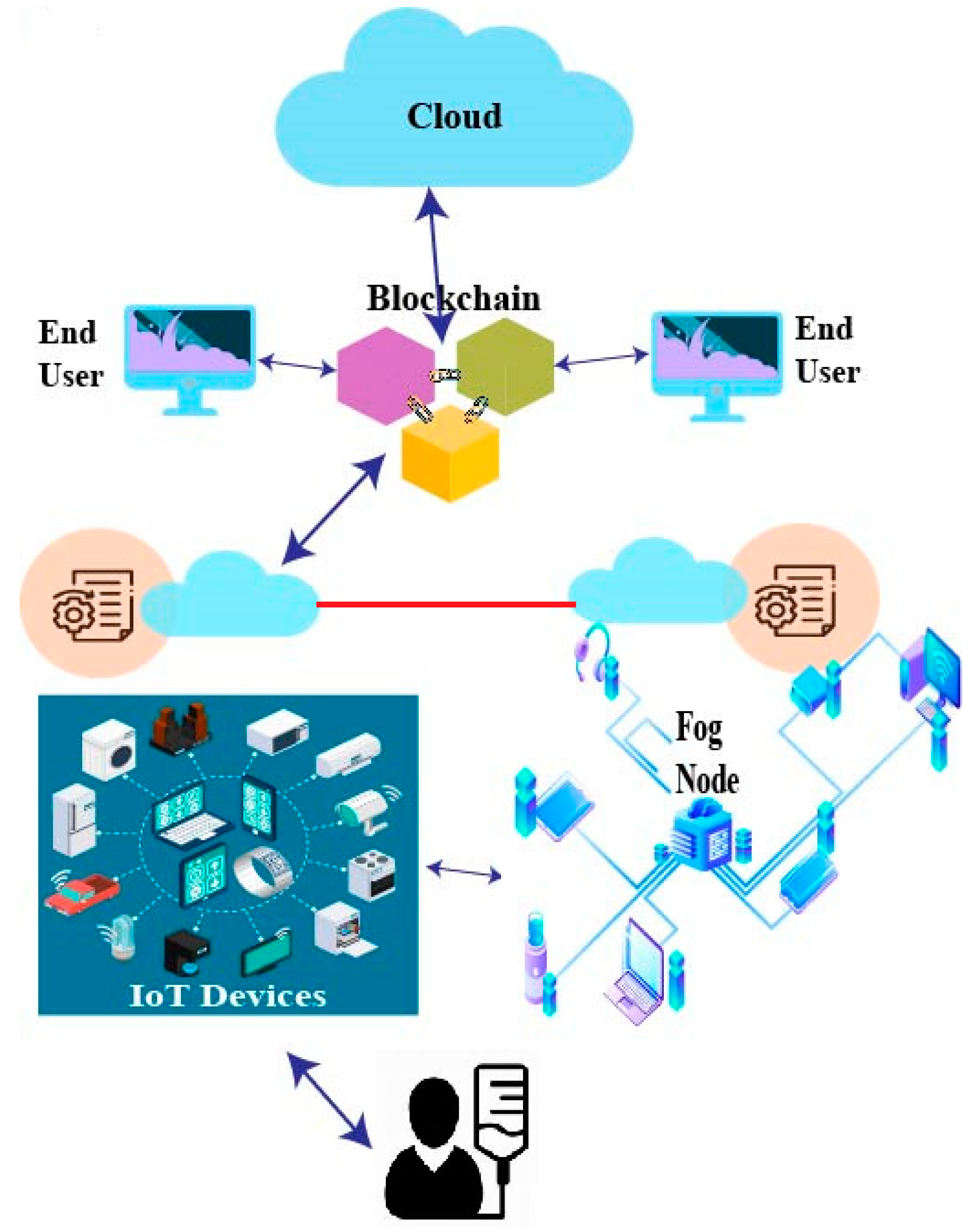
5. Fog and BC-Based Framework for IoMT
- Perception or sensor layer: The perception layer contains all the physical devices, sensors, and other monitoring devices that collect information from patients and, in some cases, from the environment and pass it to the fog layer for further transmission.
- Fog layer: In many cases, the transmission latency can be life-threatening and can result in bad medical care and support that is normally possible in a centralized or cloud-based architecture. The fog layer supports prompt responses and also tries to minimize the burden of encryption on IoMT sensors which have limited computational capabilities [66,67,68,69,70,71,72,73].
| Ref | Blockchain Application | BC Type | Benefits |
|---|---|---|---|
| [74] | Electronic health records (EHR) | Private and public | To minimize threats such as DOS, data modification, mining attacks, and storage attacks within the health sector |
| [75] | Patient monitoring and EHR | Public | The integration of BC and IoT solves the security issues healthcare applications face |
| [76] | Drug tracking | Enhance the system’s adaptability to resolve the problem of data privacy and authentication | |
| [77] | Drug tracking | Public | By tracking each drug through the supply chain, IoT and BC make the drug supply chain system more secure and dependable and prevent drug fraud |
| [78] | Drug tracking | Enhances the effectiveness of data transfer | |
| [79] | Drug tracking | Hybrid | Identifies falsified drugs in the supply chain |
| [80] | Patient monitoring and EHR | Private | The system safeguards the data and employs the patient’s information in a more pertinent format |
| [81] | EHR | Public | It guarantees that the patient cannot engage in any illegal activity. It emphasizes the openness of records and the safety of data |
| [82] | EHR | Public | Model of interoperability and trust for healthcare IoT |
| [83] | EHR | Private and public | A societal improvement through accurate and efficient healthcare |
| [84] | Patient monitoring and EHR | Private | Attempts to eliminate obstacles and provide a more secure network |
| [85] | EHR | Private | Concerning security-related issues of EHR |
| [66] | Patient monitoring and EHR | Public | Healthcare devices monitor patients’ vital signs and transmit these data to accredited physicians and hospitals via a secure BC |
- Data transportation layer: The data transportation layer works as a network layer for aggregating the information received from the fog layer and passing it to the cloud storage layer. This layer is the most vulnerable as it processes all the data flows from the fog layer to the storage layer.
- BC layer: The BC layer is responsible for authenticating the IoMT devices with the help of the fog layer, verifying the end users before providing access to the storage layer for a high level of data security with minimal delays and less of a burden on resource-constrained physical devices. It also supports the immutability of records by denying any record modification without proper authorization and authentication. The inclusion of a BC will further support interoperability and HIPAA compliance.
- Data storage or cloud layer: The data storage or cloud layer stores all the records and is responsible for providing services and data analytics to support healthcare facilities for the system’s users. The storage is perceived as a single unit. Still, it is generally a distributed architecture of different storage devices managed by the preceding BC layer while maintaining anonymity and security aspects [86,87,88].
6. Future Research Direction
- A detailed review of performance issues in FC and IoMT integration is required in healthcare. There are a few studies related to FC implementation and optimization in the IoT domain, but no such work has been performed explicitly for the IoMT frameworks.
- The review and design of scheduling algorithms should be studied for achieving highly optimized energy efficiency and ultra-low latency.
- Although a theoretical study about security challenges associated with the FC-IoMT framework has been discussed, and how a BC can resolve these challenges has been provided in this article, the practical implementation and demonstration of such security solutions can be performed to demonstrate their efficiency practically.
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Dwivedi, R.; Mehrotra, D.; Chandra, S. Potential of Internet of Medical Things (IoMT) applications in building a smart healthcare system: A systematic review. J. Oral Biol. Craniofacial Res. 2021, 12, 302–318. [Google Scholar] [CrossRef] [PubMed]
- Khubrani, M.M.; Alam, S. A detailed review of blockchain-based applications for protection against pandemic like COVID-19. 2021, 19, 1185–1196. Telecommun. Comput. Electron. Control. 2021, 19, 1185–1196. [Google Scholar] [CrossRef]
- Ghubaish, A.; Salman, T.; Zolanvari, M.; Unal, D.; Al-Ali, A.; Jain, R. Recent advances in the internet-of-medical-things (IoMT) systems security. IEEE Internet Things J. 2020, 8, 8707–8718. [Google Scholar] [CrossRef]
- Khan, I.A.; Moustafa, N.; Razzak, I.; Tanveer, M.; Pi, D.; Pan, Y.; Ali, B.S. XSRU-IoMT: Explainable simple recurrent units for threat detection in Internet of Medical Things networks. Future Gener. Comput. Syst. 2022, 127, 181–193. [Google Scholar] [CrossRef]
- Shukla, S.; Thakur, S.; Hussain, S.; Breslin, J.G.; Jameel, S.M. Identification and Authentication in Healthcare Internet-of-Things Using Integrated Fog Computing Based Blockchain Model. Internet Things 2021, 15, 100422. [Google Scholar] [CrossRef]
- Uddin, M.A.; Stranieri, A.; Gondal, I.; Balasubramanian, V. A survey on the adoption of blockchain in iot: Challenges and solutions. Blockchain Res. Appl. 2021, 2, 100006. [Google Scholar] [CrossRef]
- Da Xu, L.; Lu, Y.; Li, L. Embedding blockchain technology into IoT for security: A survey. IEEE Internet Things J. 2021, 8, 10452–10473. [Google Scholar]
- Singh, S.K.; Rathore, S.; Park, J.H. BlockIoTIntelligence: A Blockchain-enabled Intelligent IoT Architecture with Artificial Intelligence. Future Gener. Comput. Syst. 2020, 110, 721–743. [Google Scholar] [CrossRef]
- Mohd Aman, A.H.; Hassan, W.H.; Sameen, S.; Attarbashi, Z.S.; Alizadeh, M.; Latiff, L.A. IoMT amid COVID-19 pandemic: Application, architecture, technology, and security. J. Netw. Comput. Appl. 2021, 174, 102886. [Google Scholar] [CrossRef]
- Wei, K.; Zhang, L.; Guo, Y.; Jiang, X. Health monitoring based on internet of medical things: Architecture, enabling technologies, and applications. IEEE Access 2020, 8, 27468–27478. [Google Scholar] [CrossRef]
- Sheng, T.J.; Islam, M.S.; Misran, N.; Baharuddin, M.H.; Arshad, H.; Islam, M.R.; Chowdhury, M.E.H.; Rmili, H.; Islam, M.T. An internet of things based smart waste management system using LoRa and tensorflow deep learning model. IEEE Access 2020, 8, 148793–148811. [Google Scholar] [CrossRef]
- Islam, S.M.R.; Kwak, D.; Kabir, M.D.H.; Hossain, M.; Kwak, K.-S. The internet of things for health care: A comprehensive survey. IEEE Access 2015, 3, 678–708. [Google Scholar] [CrossRef]
- Tseng, T.W.; Wu, C.T.; Lai, F. Threat analysis for wearable health devices and environment monitoring internet of things integration system. IEEE Access 2019, 7, 144983–144994. [Google Scholar] [CrossRef]
- Uddin, M.A.; Stranieri, A.; Gondal, I.; Balasubramanian, V. Continuous patient monitoring with a patient centric agent: A block architecture. IEEE Access 2018, 6, 32700–32726. [Google Scholar] [CrossRef]
- Nguyen, D.C.; Pathirana, P.N.; Ding, M.; Seneviratne, A. Bedgehealth: A decentralized architecture for edge-based iomt networks using blockchain. IEEE Internet Things J. 2021, 8, 11743–11757. [Google Scholar] [CrossRef]
- Kasyoka, P.; Kimwele, M.; Mbandu Angolo, S. Certificateless pairing-free authentication scheme for wireless body area network in healthcare management system. J. Med. Eng. Technol. 2020, 44, 12–19. [Google Scholar] [CrossRef]
- Belkhouja, T.; Sorour, S.; Hefeida, M.S. Role-based hierarchical medical data encryption for implantable medical devices. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–6. [Google Scholar]
- Bokhari, M.U.; Alam, S. BSF-128: A New Synchronous Stream Cipher Design. In Proceedings of the 4th International Conference on Emerging Trends on Engineering Science, Technology and Management, Jakarta, Indonesia, 26–27 December 2020. [Google Scholar]
- Zhang, Z.; Wang, F.; Zhong, C.; Ma, H. Grid Terminal Data Security Management Mechanism Based on Master-Slave Blockchain. In Proceedings of the 2020 5th International Conference on Computer and Communication Systems (ICCCS), Shanghai, China, 15–18 May 2020; pp. 67–70. [Google Scholar]
- Wazid, M.; Das, A.K.; Rodrigues, J.J.P.C.; Shetty, S.; Park, Y. IoMT malware detection approaches: Analysis and research challenges. IEEE Access 2019, 7, 182459–182476. [Google Scholar] [CrossRef]
- Fernández Maimó, L.; Huertas Celdrán, A.; Perales Gómez, Á.L.; Clemente, F.J.G.; Weimer, J.; Lee, I. Intelligent and Dynamic Ransomware Spread Detection and Mitigation in Integrated Clinical Environments. Sensors 2019, 19, 1114. [Google Scholar] [CrossRef]
- Gupta, R.; Tanwar, S.; Tyagi, S.; Kumar, N. Machine learning models for secure data analytics: A taxonomy and threat model. Comput. Commun. 2020, 153, 406–440. [Google Scholar] [CrossRef]
- Yaacoub, J.P.A.; Noura, M.; Noura, H.N.; Salman, O.; Yaacoub, E.; Couturier, R.; Chehab, A. Securing internet of medical things systems: Limitations, issues and recommendations. Future Gener. Comput. Syst. 2020, 105, 581–606. [Google Scholar] [CrossRef]
- Stiawan, D.; Yazid Idris, M.; Malik, R.F.; Nurmaini, S.; Alsharif, N.; Budiarto, R. Investigating Brute Force Attack Patterns in IoT Network. J. Electr. Comput. Eng. 2019, 2019, 4568368. [Google Scholar] [CrossRef]
- Ibitoye, O.; Shafiq, O.; Matrawy, A. Analyzing adversarial attacks against deep learning for intrusion detection in IoT networks. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–6. [Google Scholar]
- Bahşi, H.; Nõmm, S.; La Torre, F.B. Dimensionality reduction for machine learning based iot botnet detection. In Proceedings of the 2018 15th International Conference on Control, Automation, Robotics and Vision (ICARCV), Singapore, 18–21 November 2021; IEEE: Piscataway, NJ, USA, 2018; pp. 1857–1862. [Google Scholar]
- Sun, Y.; Lo, P.-W.; Lo, B. Security and Privacy for the Internet of Medical Things Enabled Healthcare Systems: A Survey. IEEE Access 2019, 7, 183339–183355. [Google Scholar] [CrossRef]
- Kumar, S.; Pundir, A.K. Blockchain—Internet of things (IoT) Enabled Pharmaceutical Supply Chain for COVID-19. In Proceedings of the NA International Conference on Industrial Engineering and Operations Management Detroit, Detroit, MI, USA, 10–14 August 2020. [Google Scholar]
- Xing, K.; Srinivasan, S.S.R.; Rivera, M.J.; Li, J.; Cheng, X. Attacks and countermeasures in sensor networks: A survey. In Network Security; Springer: Berlin/Heidelberg, Germany, 2010; pp. 251–272. [Google Scholar]
- Bostami, B.; Ahmed, M.; Choudhury, S. False data injection attacks in internet of things. In Performability in Internet of Things; Springer: Berlin/Heidelberg, Germany, 2019; pp. 47–58. [Google Scholar]
- Newaz, A.K.M.I.; Sikder, A.K.; Rahman, M.A.; Uluagac, A.S. A survey on security and privacy issues in modern healthcare systems: Attacks and defenses. ACM Trans. Comput. Healthc. 2021, 2, 1–44. [Google Scholar] [CrossRef]
- Lv, Z. Security of internet of things edge devices. Softw. Pract. Exp. 2021, 51, 2446–2456. [Google Scholar] [CrossRef]
- Rizvi, S.; Kurtz, A.; Pfeffer, J.; Rizvi, M. Securing the Internet of Things (IoT): A security taxonomy for IoT. In Proceedings of the 2018 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 163–168. [Google Scholar]
- Gadekallu, T.R.; Pham, Q.-V.; Nguyen, D.C.; Maddikunta, P.K.R.; Deepa, N.; Prabadevi, B.; Pathirana, P.N.; Zhao, J.; Hwang, W.-J. Blockchain for edge of things: Applications, opportunities, and challenges. IEEE Internet Things J. 2021, 9, 964–988. [Google Scholar] [CrossRef]
- Wang, X.; Li, Y. Fog-assisted content-centric healthcare IoT. IEEE Internet Things Mag. 2020, 3, 90–93. [Google Scholar] [CrossRef]
- Jain, R.; Gupta, M.; Nayyar, A.; Sharma, N. Adoption of Fog Computing in Healthcare 4.0 BT. In Fog Computing for Healthcare 4.0 Environments: Technical, Societal, and Future Implications; Tanwar, S., Ed.; Springer International Publishing: Cham, Switzerland, 2021; pp. 3–36. ISBN 978-3-030-46197-3. [Google Scholar]
- Sood, S.K.; Mahajan, I. IoT-fog-based healthcare framework to identify and control hypertension attack. IEEE Internet Things J. 2018, 6, 1920–1927. [Google Scholar] [CrossRef]
- Saha, R.; Kumar, G.; Rai, M.K.; Thomas, R.; Lim, S.-J. Privacy Ensured ${e} $-healthcare for fog-enhanced IoT based applications. IEEE Access 2019, 7, 44536–44543. [Google Scholar] [CrossRef]
- Awaisi, K.S.; Hussain, S.; Ahmed, M.; Khan, A.A.; Ahmed, G. Leveraging IoT and fog computing in healthcare systems. IEEE Internet Things Mag. 2020, 3, 52–56. [Google Scholar] [CrossRef]
- Isa, I.S.B.M.; El-Gorashi, T.E.H.; Musa, M.O.I.; Elmirghani, J.M.H. Energy efficient fog-based healthcare monitoring infrastructure. IEEE Access 2020, 8, 197828–197852. [Google Scholar] [CrossRef]
- Tuli, S.; Basumatary, N.; Gill, S.S.; Kahani, M.; Arya, R.C.; Wander, G.S.; Buyya, R. HealthFog: An ensemble deep learning based Smart Healthcare System for Automatic Diagnosis of Heart Diseases in integrated IoT and fog computing environments. Future Gener. Comput. Syst. 2020, 104, 187–200. [Google Scholar] [CrossRef]
- Zhang, L.; Cao, B.; Li, Y.; Peng, M.; Feng, G. A multi-stage stochastic programming-based offloading policy for fog enabled IoT-eHealth. IEEE J. Sel. Areas Commun. 2020, 39, 411–425. [Google Scholar] [CrossRef]
- Shynu, P.G.; Menon, V.G.; Kumar, R.L.; Kadry, S.; Nam, Y. Blockchain-based secure healthcare application for diabetic-cardio disease prediction in fog computing. IEEE Access 2021, 9, 45706–45720. [Google Scholar] [CrossRef]
- Qiu, Y.; Zhang, H.; Long, K. Computation Offloading and Wireless Resource Management for Healthcare Monitoring in Fog-Computing-Based Internet of Medical Things. IEEE Internet Things J. 2021, 8, 15875–15883. [Google Scholar] [CrossRef]
- Hussain, A.; Zafar, K.; Baig, A.R. Fog-centric IoT based framework for healthcare monitoring, management and early warning system. IEEE Access 2021, 9, 74168–74179. [Google Scholar] [CrossRef]
- Asghar, A.; Abbas, A.; Khattak, H.A.; Khan, S.U. Fog Based Architecture and Load Balancing Methodology for Health Monitoring Systems. IEEE Access 2021, 9, 96189–96200. [Google Scholar] [CrossRef]
- Guo, C.; Tian, P.; Raymond Choo, K.-K.; Member, S. Enabling Privacy-Assured Fog-Based Data Aggregation in E-Healthcare Systems. IEEE Trans. Ind. Inform. 2021, 17, 1948–1957. [Google Scholar] [CrossRef]
- Ramzanpoor, Y.; Shirvani, M.H.; Golsorkhtabaramiri, M. Multi-objective fault-tolerant optimization algorithm for deployment of IoT applications on fog computing infrastructure. Complex Intell. Syst. 2022, 8, 361–392. [Google Scholar] [CrossRef]
- Aslam, T.; Maqbool, A.; Akhtar, M.; Mirza, A.; Khan, M.A.; Khan, W.Z.; Alam, S. Blockchain based enhanced ERP transaction integrity architecture and PoET consensus. Comput. Mater. Contin. 2021, 70, 1089–1108. [Google Scholar] [CrossRef]
- Huang, L.; Zhen, L.; Wang, J.; Zhang, X. Blockchain implementation for circular supply chain management: Evaluating critical success factors. Ind. Mark. Manag. 2022, 102, 451–464. [Google Scholar] [CrossRef]
- Shen, B.; Dong, C.; Minner, S. Combating copycats in the supply chain with permissioned blockchain technology. Prod. Oper. Manag. 2022, 31, 138–154. [Google Scholar] [CrossRef]
- Shuaib, M.; Hafizah Hassan, N.; Usman, S.; Alam, S.; Bhatia, S.; Koundal, D.; Mashat, A.; Belay, A. Identity Model for Blockchain-Based Land Registry System: A Comparison. Wirel. Commun. Mob. Comput. 2022, 2022, 5670714. [Google Scholar] [CrossRef]
- Shuaib, M.; Hassan, N.H.; Usman, S.; Alam, S.; Bhatia, S.; Mashat, A.; Kumar, A.; Kumar, M. Self-Sovereign Identity Solution for Blockchain-Based Land Registry System: A Comparison. Mob. Inf. Syst. 2022, 2022, 8930472. [Google Scholar] [CrossRef]
- Schinckus, C. A Nuanced perspective on blockchain technology and healthcare. Technol. Soc. 2022, 71, 102082. [Google Scholar] [CrossRef]
- Hassan, M.U.; Rehmani, M.H.; Chen, J. Privacy preservation in blockchain based IoT systems: Integration issues, prospects, challenges, and future research directions. Future Gener. Comput. Syst. 2019, 97, 512–529. [Google Scholar] [CrossRef]
- Alsaeed, N.; Nadeem, F. A Framework for Blockchain and Fogging-based Efficient Authentication in Internet of Things. In Proceedings of the 2022 2nd International Conference on Computing and Information Technology (ICCIT), Tabuk, Saudi Arabia, 25–27 January 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 409–417. [Google Scholar]
- Venkadeshan, R.; Jegatha, M. Blockchain-Based Fog Computing Model (BFCM) for IoT Smart Cities. In Convergence of Internet of Things and Blockchain Technologies; Springer: Berlin/Heidelberg, Germany, 2022; pp. 77–92. [Google Scholar]
- She, W.; Liu, Q.; Tian, Z.; Chen, J.-S.; Wang, B.; Liu, W. Blockchain trust model for malicious node detection in wireless sensor networks. IEEE Access 2019, 7, 38947–38956. [Google Scholar] [CrossRef]
- Fitwi, A.; Chen, Y.; Zhu, S. A Lightweight Blockchain-Based Privacy Protection for Smart Surveillance at the Edge. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 552–555. [Google Scholar]
- Muthanna, A.; Ateya, A.A.; Khakimov, A.; Gudkova, I.; Abuarqoub, A.; Samouylov, K.; Koucheryavy, A. Secure and Re-liable IoT Networks Using Fog Computing with Software-Defined Networking and Blockchain. J. Sens. Actuator Netw. 2019, 8, 15. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Derdour, M.; Mukherjee, M.; Derhab, A.; Maglaras, L.; Janicke, H. Blockchain technologies for the internet of things: Research issues and challenges. IEEE Internet Things J. 2018, 6, 2188–2204. [Google Scholar] [CrossRef]
- Tariq, N.; Asim, M.; Al-Obeidat, F.; Zubair Farooqi, M.; Baker, T.; Hammoudeh, M.; Ghafir, I. The security of big data in fog-enabled IoT applications including blockchain: A survey. Sensors 2019, 19, 1788. [Google Scholar] [CrossRef]
- Alzoubi, Y.I.; Al-Ahmad, A.; Jaradat, A. Fog computing security and privacy issues, open challenges, and blockchain solution: An overview. Int. J. Electr. Comput. Eng. 2021, 11, 5081–5088. [Google Scholar] [CrossRef]
- Zhou, L.; Wang, L.; Sun, Y.; Lv, P. Beekeeper: A blockchain-based iot system with secure storage and homomorphic computation. IEEE Access 2018, 6, 43472–43488. [Google Scholar] [CrossRef]
- Rahmani, M.K.I.; Shuaib, M.; Alam, S.; Siddiqui, S.T.; Ahmad, S.; Bhatia, S.; Mashat, A. Blockchain-Based Trust Management Framework for Cloud Computing-Based Internet of Medical Things (IoMT): A Systematic Review. Comput. Intell. Neurosci. 2022, 2022, 9766844. [Google Scholar] [CrossRef] [PubMed]
- Jamil, F.; Ahmad, S.; Iqbal, N.; Kim, D.H. Towards a remote monitoring of patient vital signs based on iot-based blockchain integrity management platforms in smart hospitals. Sensors 2020, 20, 2195. [Google Scholar] [CrossRef] [PubMed]
- Bharany, S.; Badotra, S.; Sharma, S.; Rani, S.; Alazab, M.; Jhaveri, R.H.; Reddy Gadekallu, T. Energy efficient fault tolerance techniques in green cloud computing: A systematic survey and taxonomy. Sustain. Energy Technol. Assess. 2022, 53, 102613. [Google Scholar] [CrossRef]
- Chen, Y.; Lu, Y.; Bulysheva, L.; Kataev, M.Y. Applications of Blockchain in Industry 4.0: A Review. Inf. Syst. Front. 2022, 24, 1–15. [Google Scholar] [CrossRef]
- Zile, K.; Strazdina, R. Blockchain Use Cases and Their Feasibility. Appl. Comput. Syst. 2018, 23, 12–20. [Google Scholar] [CrossRef]
- Mittal, M.; Iwendi, C.; Khan, S.; Rehman Javed, A. Analysis of security and energy efficiency for shortest route discovery in low-energy adaptive clustering hierarchy protocol using Levenberg-Marquardt neural network and gated recurrent unit for intrusion detection system. Trans. Emerg. Telecommun. Technol. 2021, 32, e3997. [Google Scholar] [CrossRef]
- Bharany, S.; Sharma, S.; Bhatia, S.; Rahmani, M.K.I.; Shuaib, M.; Lashari, S.A. Energy Efficient Clustering Protocol for FANETS Using Moth Flame Optimization. Sustainability 2022, 14, 6159. [Google Scholar] [CrossRef]
- Burer, M.J.; de Lapparent, M.; Pallotta, V.; Capezzali, M.; Carpita, M. Use cases for Blockchain in the Energy Industry Opportunities of emerging business models and related risks. Comput. Ind. Eng. 2019, 137, 106002. [Google Scholar] [CrossRef]
- Bharany, S.; Sharma, S.; Khalaf, O.I.; Abdulsahib, G.M.; Al Humaimeedy, A.S.; Aldhyani, T.H.H.; Maashi, M.; Alkahtani, H. A Systematic Survey on Energy-Efficient Techniques in Sustainable Cloud Computing. Sustainability 2022, 14, 6256. [Google Scholar] [CrossRef]
- Dwivedi, A.; Srivastava, G.; Dhar, S.; Singh, R. A Decentralized Privacy-Preserving Healthcare Blockchain for IoT. Sensors 2019, 19, 326. [Google Scholar] [CrossRef] [PubMed]
- McGhin, T.; Choo, K.K.R.; Liu, C.Z.; He, D. Blockchain in healthcare applications: Research challenges and opportunities. J. Netw. Comput. Appl. 2019, 135, 62–75. [Google Scholar] [CrossRef]
- Huang, Y.; Wu, J.; Long, C. Drugledger: A practical blockchain system for drug traceability and regulation. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July 2018–3 August 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1137–1144. [Google Scholar]
- Ahmadi, V.; Benjelloun, S.; El Kik, M.; Sharma, T.; Chi, H.; Zhou, W. Drug governance: IoT-based blockchain implementation in the pharmaceutical supply chain. In Proceedings of the 2020 Sixth International Conference on Mobile and Secure Services (MobiSecServ), Miami Beach, FL, USA, 22–23 February 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–8. [Google Scholar]
- Tseng, J.-H.; Liao, Y.-C.; Chong, B.; Liao, S.-W. Governance on the Drug Supply Chain via Gcoin Blockchain. Int. J. Environ. Res. Public Health 2018, 15, 1055. [Google Scholar] [CrossRef] [PubMed]
- Pandey, P.; Litoriya, R. Securing e-health networks from counterfeit medicine penetration using blockchain. Wirel. Pers. Commun. 2020, 117, 7–25. [Google Scholar] [CrossRef]
- Griggs, K.N.; Ossipova, O.; Kohlios, C.P.; Baccarini, A.N.; Howson, E.A.; Hayajneh, T. Healthcare Blockchain System Using Smart Contracts for Secure Automated Remote Patient Monitoring. J. Med. Syst. 2018, 42, 130. [Google Scholar] [CrossRef]
- Rathee, P. Introduction to blockchain and IoT. In Advanced Applications of Blockchain Technology; Springer: Berlin/Heidelberg, Germany, 2020; pp. 1–14. [Google Scholar]
- Abou-Nassar, E.M.; Iliyasu, A.M.; El-Kafrawy, P.M.; Song, O.-Y.; Kashif Bashir, A.; El-Latif, A.A.A.; Abd El-Latif, A.A. Special Section on Blockchain Technology: Principles and Applications DITrust Chain: Towards Blockchain-Based Trust Models for Sustainable Healthcare IoT Systems. IEEE Access 2020, 8, 111223–111238. [Google Scholar] [CrossRef]
- Chakraborty, S.; Aich, S.; Kim, H.-C. A secure healthcare system design framework using blockchain technology. In Proceedings of the 2019 21st International Conference on Advanced Communication Technology (ICACT), Pyeongchang, Korea, 17–20 February 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 260–264. [Google Scholar]
- Dwivedi, A.D.; Malina, L.; Dzurenda, P.; Srivastava, G. Optimized blockchain model for internet of things based healthcare applications. In Proceedings of the 2019 42nd International Conference on Telecommunications and Signal Processing (TSP), Budapest, Hungary, 1–3 July 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 135–139. [Google Scholar]
- Attia, O.; Khoufi, I.; Laouiti, A.; Adjih, C. An IoT-Blockchain Architecture Based on Hyperledger Framework for Healthcare Monitoring Application. In Proceedings of the 2019 10th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Canary Islands, Spain, 24–26 June 2019; pp. 1–5. [Google Scholar]
- Le, T.; Hsu, C.; Chen, W. A Hybrid Blockchain-Based Log Management Scheme with Non-Repudiation for Smart Grids. IEEE Trans. Ind. Inform. 2021, 18, 5771–5782. [Google Scholar] [CrossRef]
- Bharany, S.; Kaur, K.; Badotra, S.; Rani, S.; Kavita; Wozniak, M.; Shafi, J.; Ijaz, M.F. Efficient Middleware for the Portability of PaaS Services Consuming Applications among Heterogeneous Clouds. Sensors 2022, 22, 5013. [Google Scholar] [CrossRef]
- Choi, T.; Siqin, T. Blockchain in logistics and production from Blockchain 1.0 to Blockchain 5.0: An intra-inter-organizational framework. Transp. Res. Part E 2022, 160, 102653. [Google Scholar] [CrossRef]
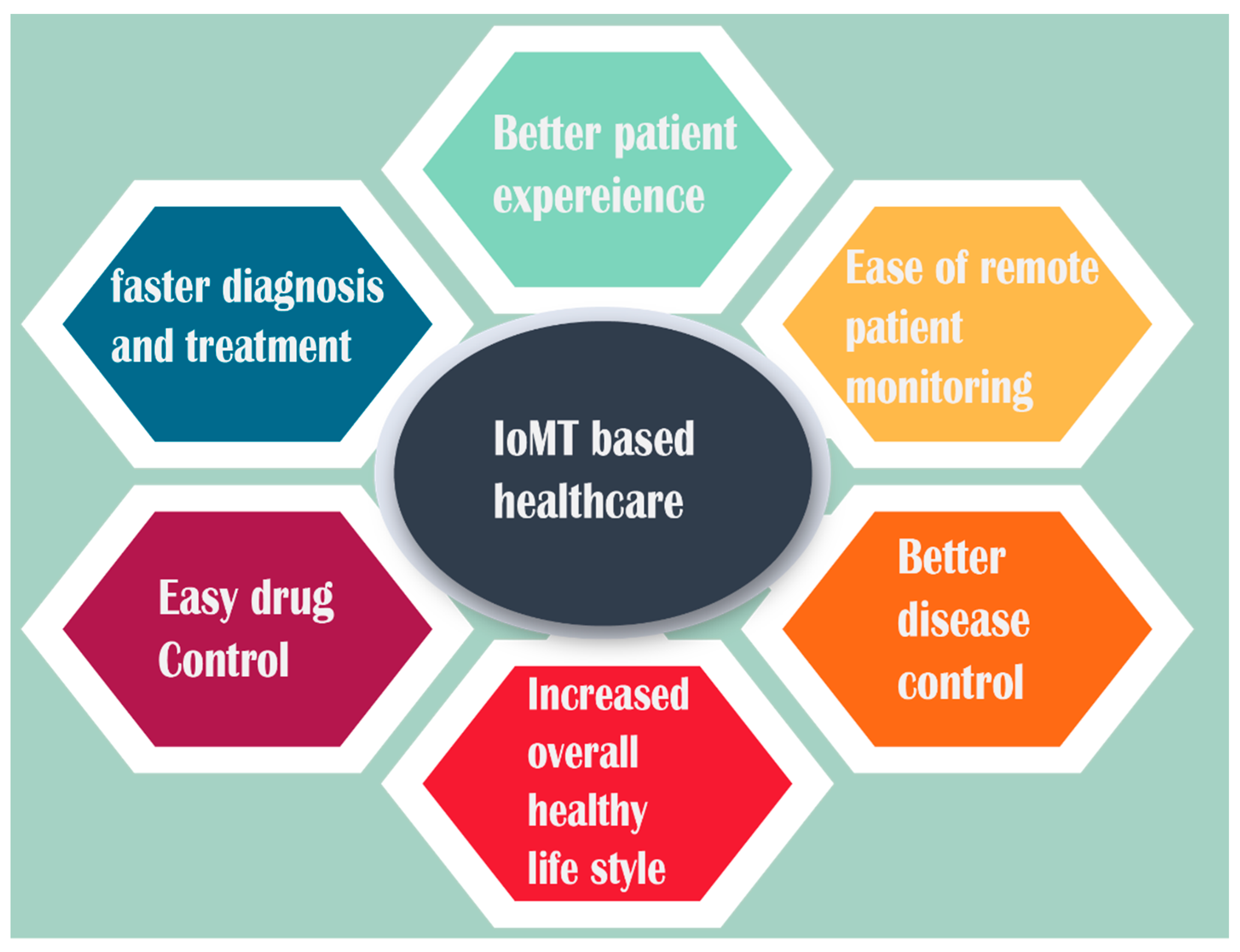

| Category of Devices | Location | Examples |
|---|---|---|
| Wearable devices | Attached to the human body | Fitness trackers, smart watches, hearing aids, body-mounted sensors, smart glasses, patient bracelets |
| Implantable devices | Inside the human body | Cardiac pacemakers, implantable insulin pumps, coronary stents, implantable cardioverter defibrillators (ICDs), artificial knees, ear tubes |
| Remote monitoring devices | Outside the human body | ECG devices, pulse oximeters, BP monitors, telemonitoring devices, smart pill containers, personal emergency response systems (PERS) |
| Point-of-care devices and kiosks | Fixed locations | Body temperature monitors, smart scales, BMI monitors |
| Hospital devices | Within hospital premises | Medical image processing devices such as MRIs, CT scans, etc., ECG machines |
| Ref | Attacks | Target Layer | C | P | I | A | NR |
|---|---|---|---|---|---|---|---|
| [20] | Malware attack | Cloud/Database layer | ✓ | ✓ | |||
| [21] | Ransomware attack | Cloud/Database layer | ✓ | ✓ | |||
| [22] | SQL injection | Cloud/Database layer | ✓ | ✓ | ✓ | ✓ | ✓ |
| [23] | Social engineering | Cloud/Database layer | ✓ | ✓ | ✓ | ✓ | ✓ |
| [24] | Brute force | Cloud/Database layer | ✓ | ✓ | |||
| [25] | Poisoning and evasion attacks | Cloud/Database layer | ✓ | ✓ | |||
| [22] | DoS and DDoS | Network layer | ✓ | ✓ | ✓ | ✓ | ✓ |
| [23] | Man-in-the-middle | Network layer | ✓ | ✓ | |||
| [22] | Eavesdropping | Network layer | ✓ | ✓ | ✓ | ||
| [23] | Replay | Network layer | ✓ | ✓ | |||
| [26] | Botnet | Network layer | ✓ | ✓ | |||
| [27] | Jamming | Network layer | ✓ | ||||
| [23] | Flooding | Network layer | ✓ | ||||
| [28] | Packet analysis | Network layer | ✓ | ✓ | ✓ | ✓ | |
| [29] | Node tampering | Sensor/Perception layer | ✓ | ✓ | ✓ | ✓ | ✓ |
| [30] | False data injection | Sensor/Perception layer | ✓ | ✓ | ✓ | ✓ | |
| [22] | Buffer overflow | Sensor/Perception layer | ✓ | ||||
| [31] | Side-channel | Sensor/Perception layer | ✓ | ✓ | ✓ | ||
| [32] | Trojan | Sensor/Perception layer | ✓ | ✓ | ✓ | ✓ | ✓ |
| [22] | Eavesdropping | Sensor/Perception layer | ✓ | ✓ | ✓ | ||
| [33] | Cross-site scripting | Application layer | |||||
| [20] | Malicious code | Application layer | ✓ | ✓ | |||
| [23] | Social engineering | Application layer | ✓ | ✓ | ✓ | ✓ | ✓ |
| Parameter | Cloud Computing | FC |
|---|---|---|
| Service continuum | Difficult to provide uninterrupted connectivity | Easy to provide uninterrupted connectivity |
| Response time | High | High to moderate |
| Device coupling | Tightly coupled | Loosely coupled |
| Connectivity | Distributed | Fully distributed |
| Deployment | Centralized | Distributed |
| Ref | Issues Discussed |
|---|---|
| [37] | IoT-fog-based architecture for monitoring and diagnosing the hypertension |
| [38] | To ensure the privacy of an e-healthcare framework to protect the patient data |
| [39] | Fog-IoMT to improve efficiency and security |
| [35] | Fog-IoMT to reduce patient data access time |
| [40] | Fog-IoMT architecture to save and optimize energy consumption |
| [41] | Fog-IoMT framework that automatically analyzes and identifies heart disease issues |
| [42] | Fog-IoMT offloading schema to optimal offload plan |
| [43] | BC-fog-IoMT for better privacy, safety, and better diagnosis accuracy in diabetic and heart ailments |
| [44] | Fog-IoT to improve the diagnosis accuracy and better treatment of infected patients with COVID-19 |
| [45] | Fog-IoMT to monitor the physical position of sportspersons |
| [46] | Fog-IoMT to improve the adaptability for large-scale healthcare applications |
| [47] | Fog-IoMT is based on symmetric homomorphic encryption for secure patient information |
| [48] | Fog-IoMT to decrease the transaction delay, reduce bandwidth and energy consumption, and further augment the consistency of the system |
| Parameters | Blockchain | IoT |
|---|---|---|
| Resource | Resource consuming | Most devices have a limited resource |
| Time consumption | Block mining is time-intensive | Requires low latency |
| Scalability | Blockchain scales poorly with large networks | IoT is expected to contain a large number of nodes |
| Bandwidth | High bandwidth consumption | Limited bandwidth |
| Big data | Source | Means to manage |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alam, S.; Shuaib, M.; Ahmad, S.; Jayakody, D.N.K.; Muthanna, A.; Bharany, S.; Elgendy, I.A. Blockchain-Based Solutions Supporting Reliable Healthcare for Fog Computing and Internet of Medical Things (IoMT) Integration. Sustainability 2022, 14, 15312. https://doi.org/10.3390/su142215312
Alam S, Shuaib M, Ahmad S, Jayakody DNK, Muthanna A, Bharany S, Elgendy IA. Blockchain-Based Solutions Supporting Reliable Healthcare for Fog Computing and Internet of Medical Things (IoMT) Integration. Sustainability. 2022; 14(22):15312. https://doi.org/10.3390/su142215312
Chicago/Turabian StyleAlam, Shadab, Mohammed Shuaib, Sadaf Ahmad, Dushantha Nalin K. Jayakody, Ammar Muthanna, Salil Bharany, and Ibrahim A. Elgendy. 2022. "Blockchain-Based Solutions Supporting Reliable Healthcare for Fog Computing and Internet of Medical Things (IoMT) Integration" Sustainability 14, no. 22: 15312. https://doi.org/10.3390/su142215312
APA StyleAlam, S., Shuaib, M., Ahmad, S., Jayakody, D. N. K., Muthanna, A., Bharany, S., & Elgendy, I. A. (2022). Blockchain-Based Solutions Supporting Reliable Healthcare for Fog Computing and Internet of Medical Things (IoMT) Integration. Sustainability, 14(22), 15312. https://doi.org/10.3390/su142215312















