Lightweight Mutual Authentication for Healthcare IoT
Abstract
1. Introduction
2. Preliminary Research
2.1. Cryptography
- Confidentiality: a third party should not obtain information content, only the sender and the receiver.
- Integrity: the information cannot be altered in storage or transit between sender and intended receiver without the alteration being detected.
- Non-repudiation: the sender of the information cannot later deny their intentions in the creation or transmission of the information.
2.2. Bilinear Pairing
2.3. Random Number
2.4. Public Key Infrastructure (PKI)
2.5. Attribute-Based Encryption
2.5.1. Key Policy Attribute-Based Encryption (KP-ABE)
2.5.2. Ciphertext Policy Attribute-Based Encryption (CP-ABE)
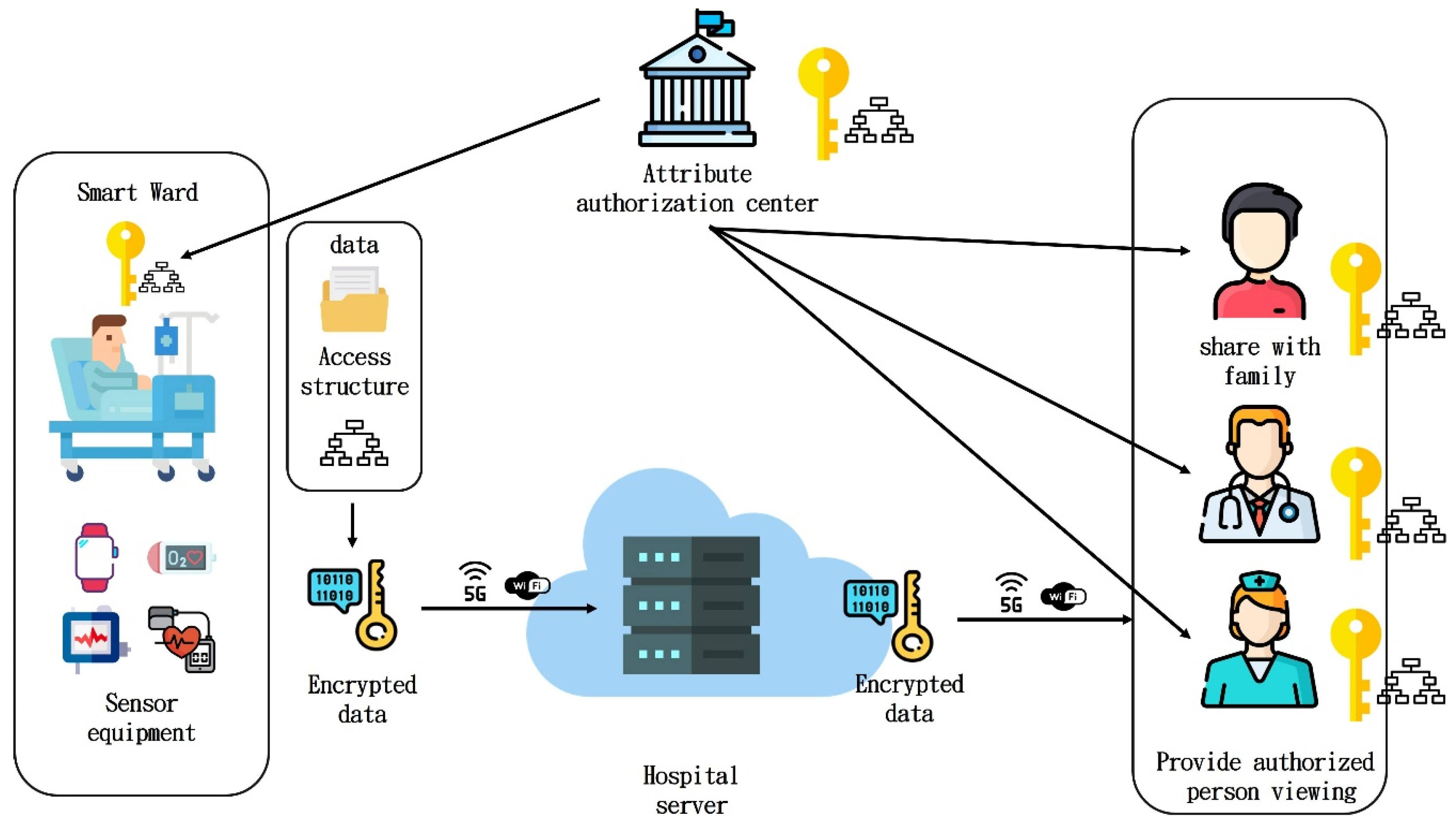
3. Proposed Scheme
3.1. Complete Authentication
- System initial stage:
- Patient registration stage:
- Key generation stage:
- Encryption stage:
- Decryption stage:
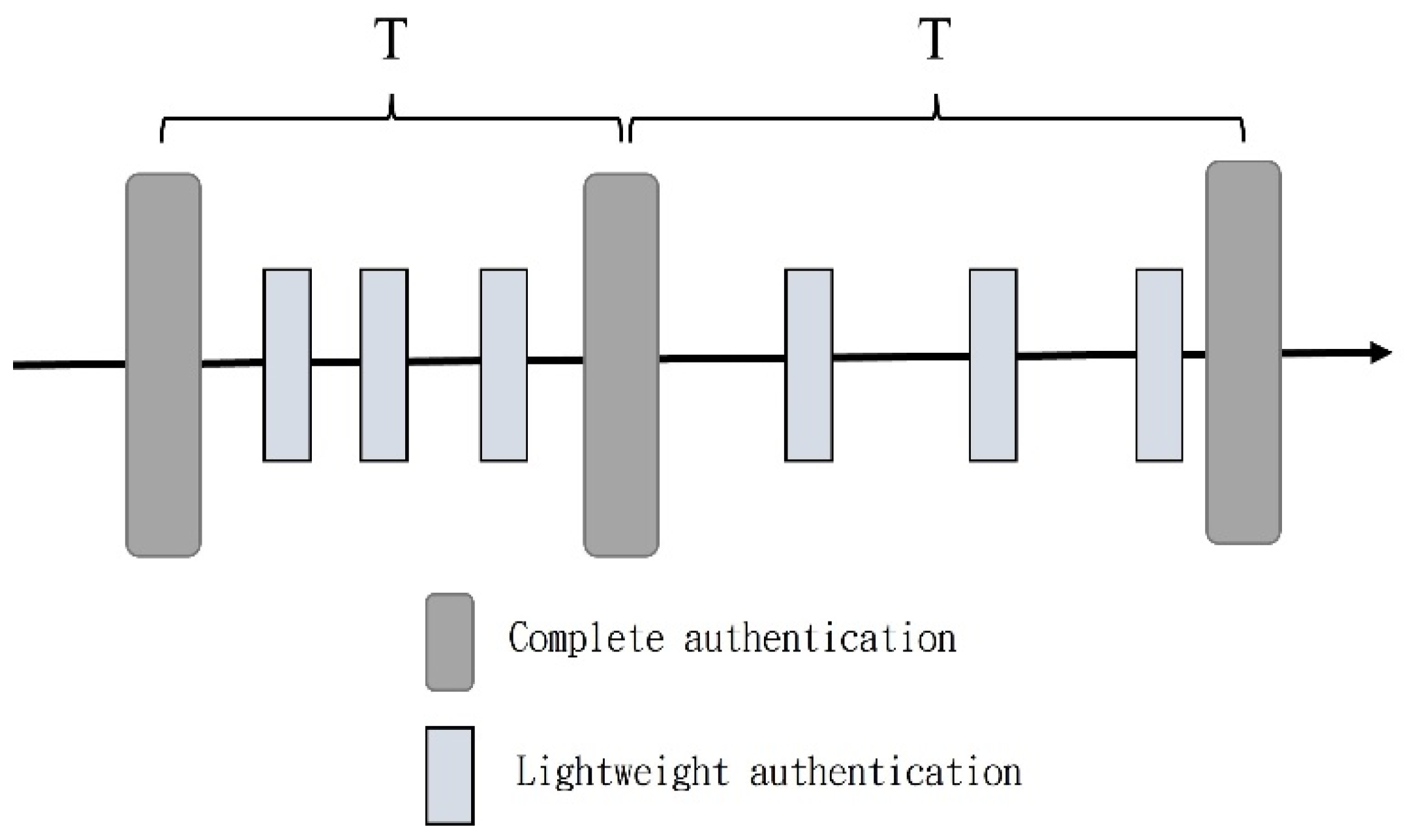
3.2. Lightweight Authentication
- Stage 1
- Stage 2
- Stage 3
- Stage 1
- Stage 2
- Stage 3
- Stage 4
- Stage 5
4. Results and Discussion
4.1. Performance Analysis
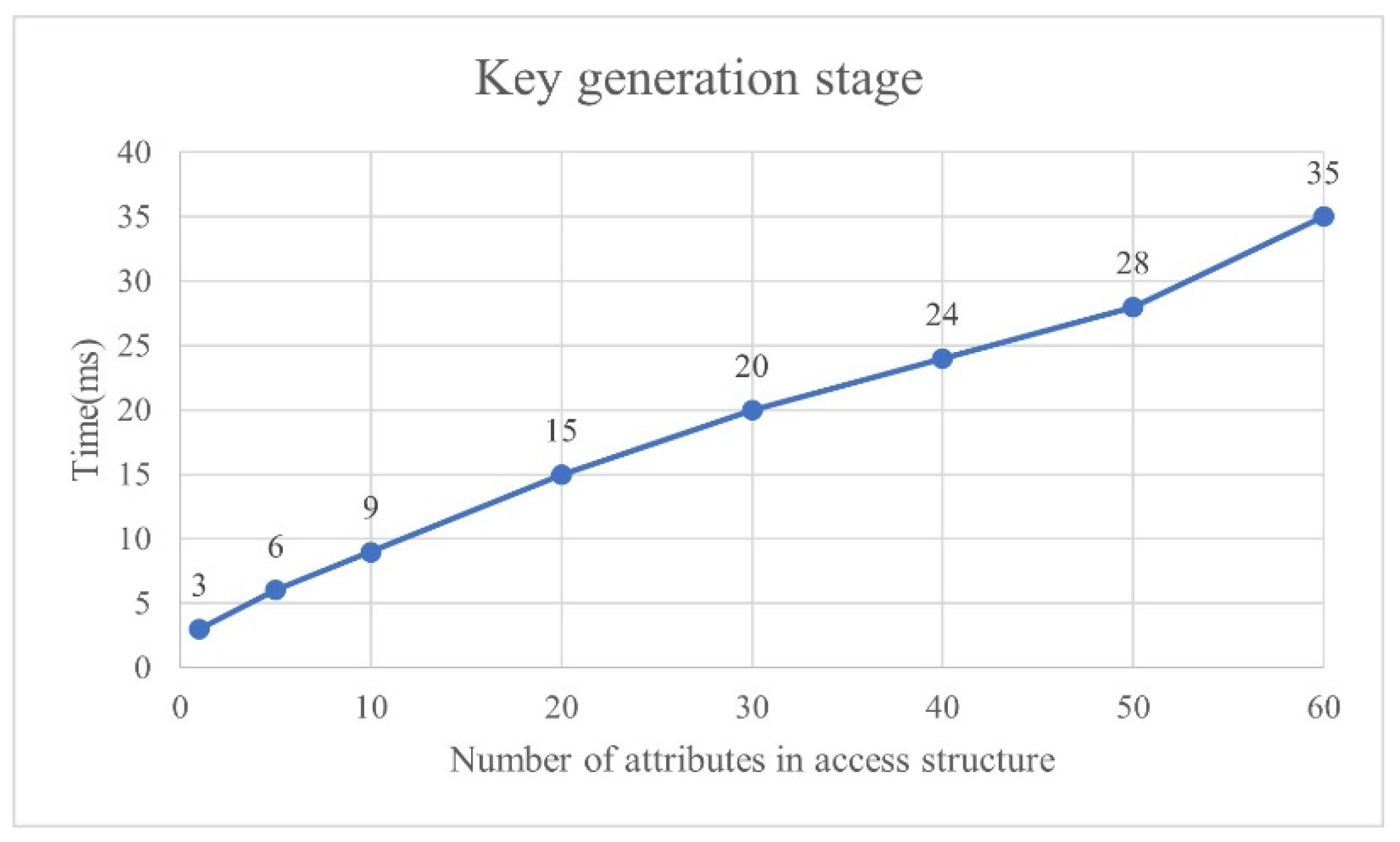
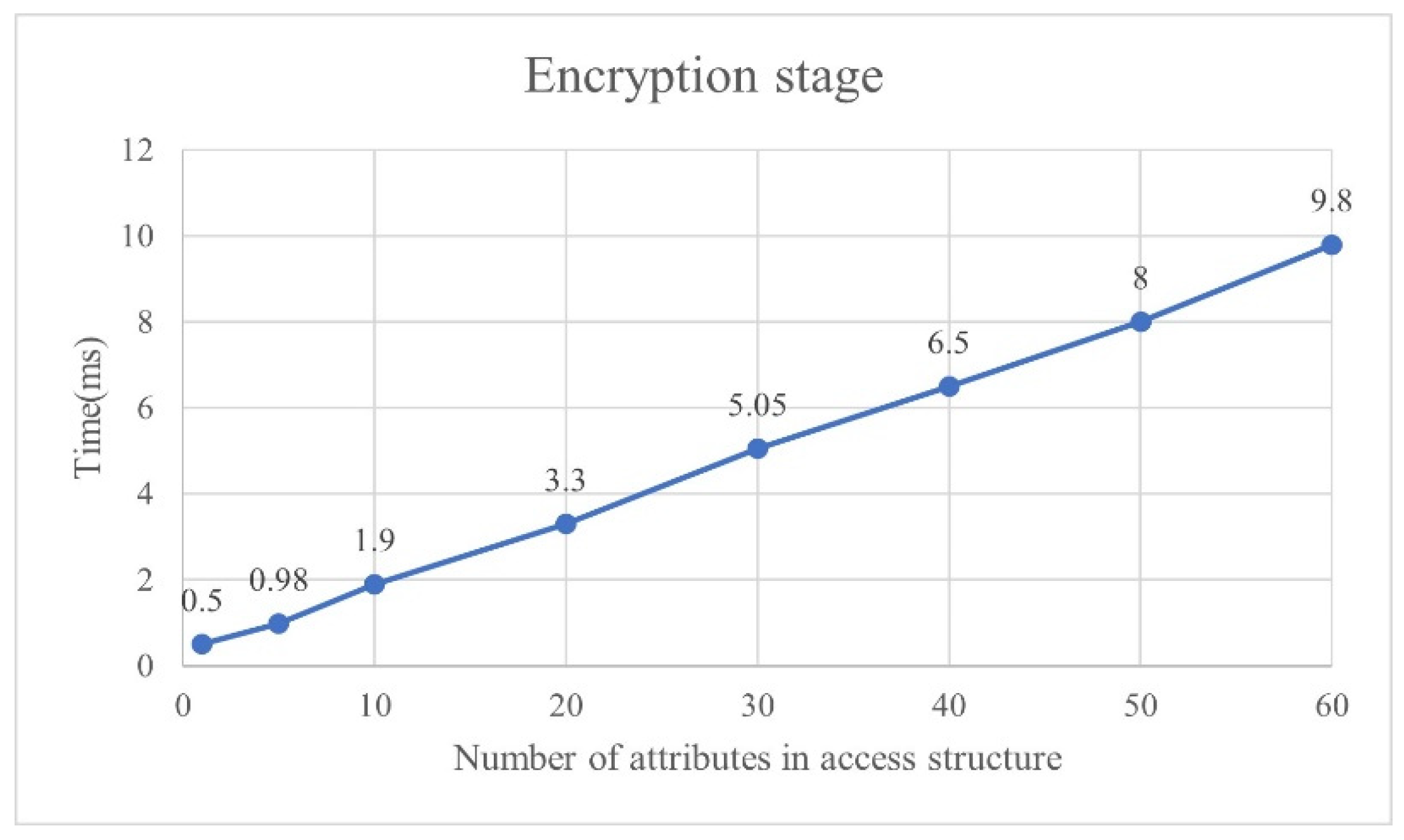
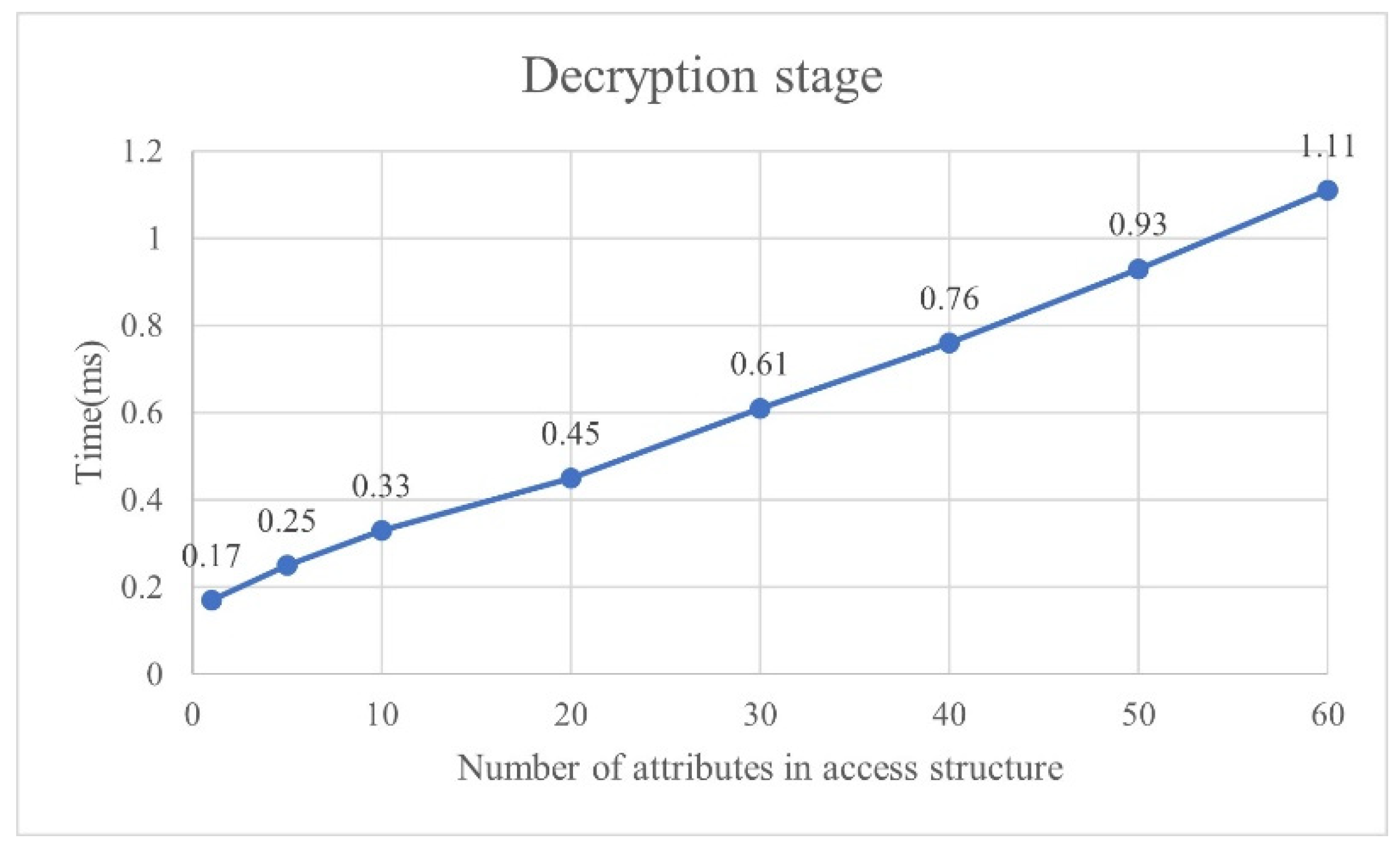
4.1.1. Complete Authentication Performance Analysis
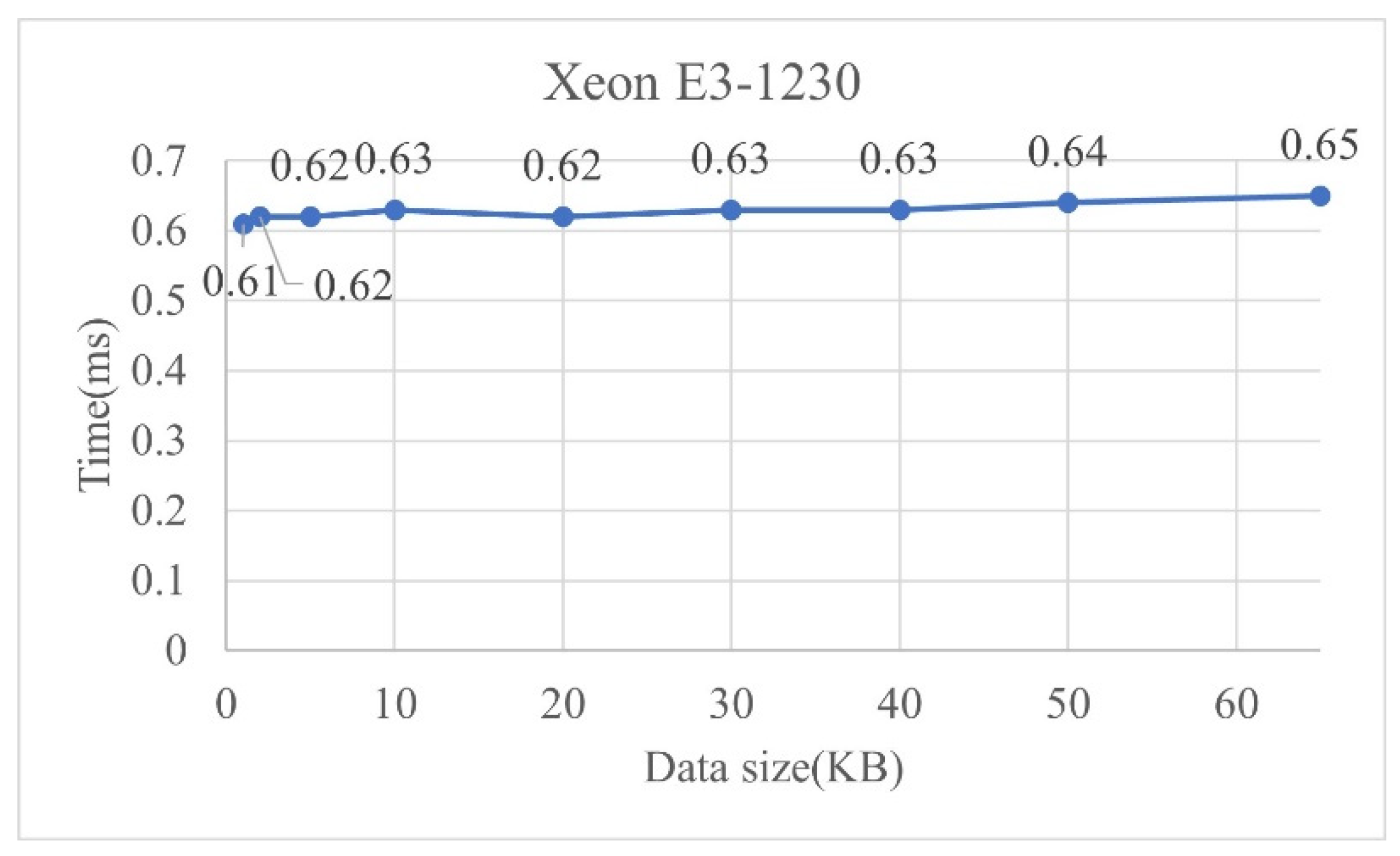
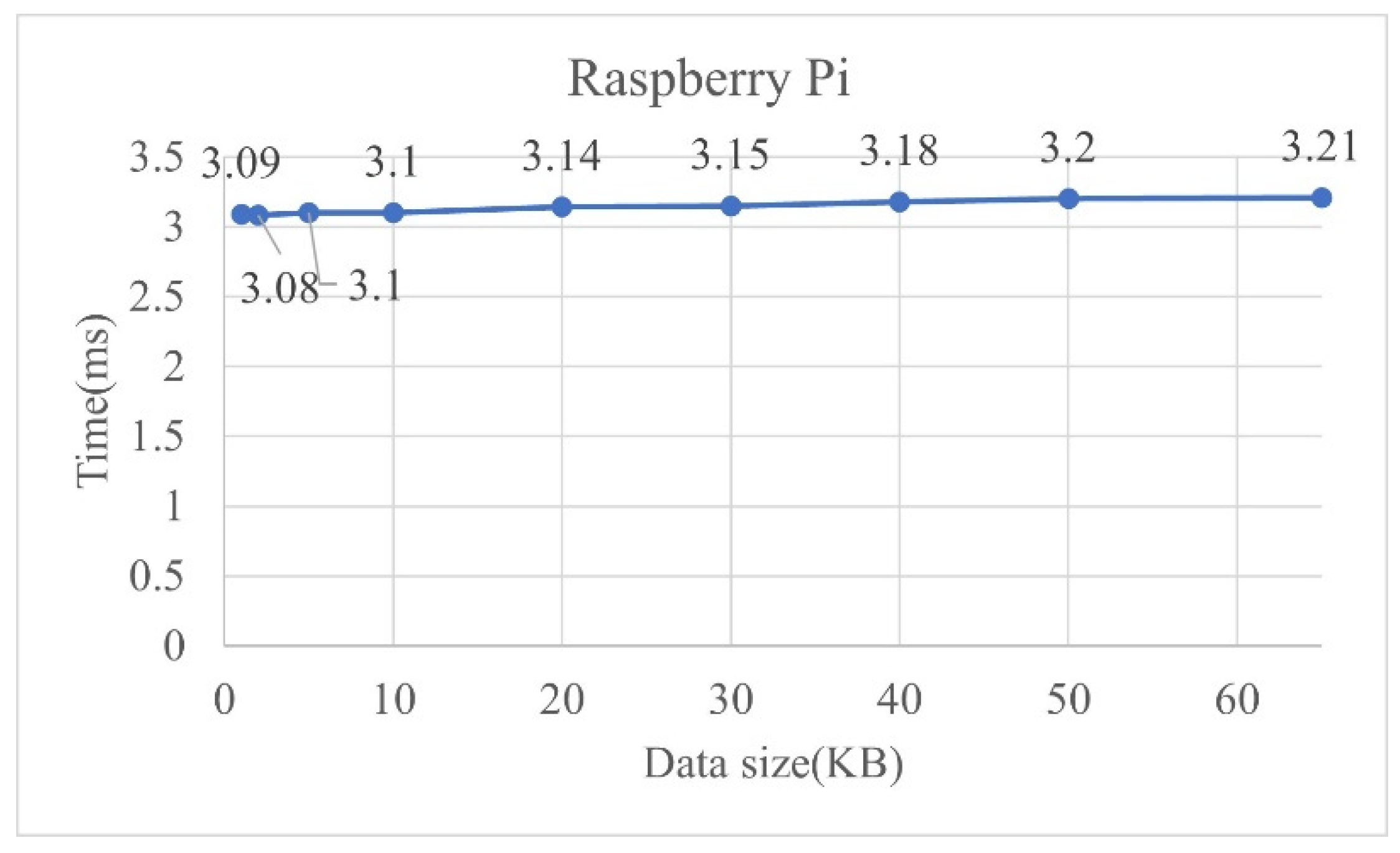
4.1.2. Lightweight Authentication Performance Analysis
5. Security Analysis
5.1. Resistance to Replay Attacks
5.2. Resistance to Man-in-the-Middle Attacks
5.3. Forward Secrecy
5.4. The Test Results of the Random Number
5.5. Security Analysis of Session Key
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Stinson, D.R.; Paterson, M. Cryptography: Theory and Practice; Chapman and Hall/CRC: London, UK, 2005; pp. 1–583. [Google Scholar]
- Windley, P.J. Digital Identity: Unmasking Identity Management Architecture (IMA); O’Reilly Media, Inc.: Sebastopol, CA, USA, 2005. [Google Scholar]
- Delfs, H.; Knebl, H.; Knebl, H. Introduction to Cryptography; Springer: Berlin/Heidelberg, Germany, 2002. [Google Scholar]
- Goldwasser, S.; Micali, S. Probabilistic encryption & how to play mental poker keeping secret all partial information. In Proceedings of the 14th Annual ACM Symposium on Theory of Computing, San Francisco, CA, USA, 5–7 May 1982; pp. 365–377. [Google Scholar]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of things: A survey on enabling technologies, protocols, and applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Mahmoud, R.; Yousuf, T.; Aloul, F.; Zualkernan, I. Internet of things (IoT) security: Current status, challenges and prospective measures. In Proceedings of the 2015 10th International Conference for Internet Technology and Secured Transactions (ICITST), London, UK, 14–16 December 2015; pp. 336–341. [Google Scholar]
- Alaba, F.A.; Othman, M.; Hashem, I.A.T.; Alotaibi, F. Internet of Things security: A survey. J. Netw. Comput. Appl. 2017, 88, 10–28. [Google Scholar] [CrossRef]
- Liyanage, M.; Braeken, A.; Kumar, P.; Ylianttila, M. (Eds.) IoT Security: Advances in Authentication; John Wiley & Sons: Hoboken, NJ, USA, 2020. [Google Scholar]
- Roman, R.; Zhou, J.; Lopez, J. On the features and challenges of security and privacy in distributed internet of things. J. Comput. Netw. 2013, 57, 2266–2279. [Google Scholar] [CrossRef]
- Anwar, R.W.; Bakhtiari, M.; Zainal, A.; Qureshi, K.N. A Roadmap to Wireless Sensor Security Protocols Implementation in Health Care System. In Proceedings of the 2nd International Conference on Applied Information and Communications Technology (ICAICT), Muscat, Oman, 28–29 April 2014. [Google Scholar]
- Porambage, P.; Schmitt, C.; Kumar, P.; Gurtov, A.; Ylianttila, M. Two-phase authentication protocol for wireless sensor networks in distributed IoT applications. In Proceedings of the 2014 IEEE Wireless Communications and Networking Conference (WCNC), Istanbul, Turkey, 6–9 April 2014; pp. 2728–2733. [Google Scholar]
- Khemissa, H.; Tandjaoui, D. A Lightweight Authentication Scheme for E-health applications in the context of Internet of Things. In Proceedings of the 2015 9th International Conference on Next Generation Mobile Applications, Services and Technologies, Cambridge, UK, 9–11 September 2015; pp. 90–95. [Google Scholar]
- Yeh, K.H.; Su, C.; Choo, K.K.R.; Chiu, W. A novel certificateless signature scheme for smart objects in the Internet-of-Things. J. Sens. 2017, 17, 1001. [Google Scholar] [CrossRef] [PubMed]
- Bamasag, O.O.; Youcef-Toumi, K. Towards continuous authentication in internet of things based on secret sharing scheme. In Proceedings of the WESS’15: Workshop on Embedded Systems Security, Amsterdam, The Netherlands, 4–9 October 2015; pp. 1–8. [Google Scholar]
- Chuang, Y.H.; Lo, N.W.; Yang, C.Y.; Tang, S.W. A lightweight continuous authentication protocol for the Internet of Things. J. Sens. 2018, 18, 1104. [Google Scholar] [CrossRef]
- Atzori, L.; Iera, A.; Morabito, G. The internet of things: A survey. J. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Khemissa, H.; Tandjaoui, D. A novel lightweight authentication scheme for heterogeneous wireless sensor networks in the context of Internet of Things. In Proceedings of the 2016 Wireless Telecommunications Symposium (WTS), London, UK, 18–20 April 2016; pp. 1–6. [Google Scholar]
- Bellare, M.; Namprempre, C. Authenticated Encryption: Relations among Notions and Analysis of the Generic Composition Paradigm; Springer: Berlin/Heidelberg, Germany, 2008; Volume 21, pp. 469–491. [Google Scholar]
- World Health Organization. National eHealth Strategy Toolkit; International Telecommunication Union: Geneva, Switzerland, 2012. [Google Scholar]
- Joux, A.; Nguyen, K. Separating decision Diffie–Hellman from computational Diffie—Hellman in cryptographic groups. J. Cryptol. 2003, 16, 239–247. [Google Scholar] [CrossRef]
- Cheon, J.H. Security analysis of the strong Diffie-Hellman problem. In Advances in Cryptology—EUROCRYPT 2006; Springer: Berlin/Heidelberg, Germany, 2006; pp. 1–11. [Google Scholar]
- Lee, K.; Lee, S.Y.; Seo, C.; Yim, K. TRNG (True Random Number Generator) method using visible spectrum for secure communication on 5G network. IEEE Access 2018, 6, 12838–12847. [Google Scholar] [CrossRef]
- Chen, I.T. Random numbers generated from audio and video sources. In Mathematical Problems in Engineering; Hindawi: London, UK, 2013. [Google Scholar]
- Blum, M.; Micali, S. How to generate cryptographically strong sequences of pseudorandom bits. In Providing Sound Foundations for Cryptography: On the Work of Shafi Goldwasser and Silvio Micali; Association for Computing Machinery: New York, NY, USA, 2019; p. 288. [Google Scholar]
- Rukhin, A.; Soto, J.; Nechvatal, J.; Smid, M.; Barker, E. A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Applications; Booz-Allen and Hamilton Inc.: McLean, VA, USA, 2001. [Google Scholar]
- McCurley, K.S. The discrete logarithm problem. Proc. Symp. Appl. Math. 1990, 42, 49–74. [Google Scholar]
- Chokhani, S.; Ford, W.; Sabett, R.; Merrill, C.R.; Wu, S.S. Internet X. 509 Public Key Infrastructure Certificate Policy and Certification Practices Framework, RFC 3647; Internet Engineering Task Force (IETF): Fremont, CA, USA, 2003; pp. 1–94. [Google Scholar]
- Cooper, D.; Santesson, S.; Farrell, S.; Boeyen, S.; Housley, R.; Polk, W. Internet X. 509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile, RFC 5280; Internet Engineering Task Force (IETF): Fremont, CA, USA, 2008; pp. 1–151. [Google Scholar]
- Sahai, A.; Waters, B. Fuzzy identity-based encryption. In Advances in Cryptology—EUROCRYPT 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 457–473. [Google Scholar]
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute-based encryption for fine-grained access control of encrypted data. In Proceedings of the 13th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 30 October–3 November 2006; pp. 89–98. [Google Scholar]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-policy attribute-based encryption. In Proceedings of the 2007 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 20–23 May 2007; pp. 321–334. [Google Scholar]
- Shamir, A. Identity-based cryptosystems and signature schemes. In Workshop on the Theory and Application of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1984; pp. 47–53. [Google Scholar]
- Farrell, S.; Housley, R.; Turner, S. An Internet Attribute Certificate Profile for Authorization, RFC 3281; 2010; pp. 1–50. Available online: https://datatracker.ietf.org/doc/rfc3281/ (accessed on 8 October 2022).
- Guo, L.; Zhang, C.; Sun, J.; Fang, Y. A privacy-preserving attribute-based authentication system for mobile health networks. IEEE Trans. Mob. Comput. 2013, 13, 1927–1941. [Google Scholar] [CrossRef]
- Guo, F.; Mu, Y.; Susilo, W.; Wong, D.S.; Varadharajan, V. CP-ABE with constant-size keys for lightweight devices. IEEE Trans. Inf. Forensics Secur. 2014, 9, 763–771. [Google Scholar]
- Ding, S.; Li, C.; Li, H. A novel efficient pairing-free CP-ABE based on elliptic curve cryptography for IoT. IEEE Access 2018, 6, 27336–27345. [Google Scholar] [CrossRef]
- Hwang, Y.W.; Lee, I.Y. A Study on CP-ABE-Based Medical Data Sharing System with Key Abuse Prevention and Verifiable Outsourcing in the IoMT Environment. J. Sens. 2020, 20, 4934. [Google Scholar] [CrossRef] [PubMed]
- Ambrosin, M.; Anzanpour, A.; Conti, M.; Dargahi, T.; Moosavi, S.R.; Rahmani, A.M.; Liljeberg, P. On the feasibility of attribute-based encryption on internet of things devices. IEEE Micro 2016, 36, 25–35. [Google Scholar] [CrossRef]
- Chow, S.S. A framework of multi-authority attribute-based encryption with outsourcing and revocation. In Proceedings of the 21st ACM on Symposium on access Control Models and Technologies, Shanghai, China, 6–8 June 2016; pp. 215–226. [Google Scholar]
- Li, Q.; Zhu, H.; Ying, Z.; Zhang, T. Traceable ciphertext-policy attribute-based encryption with verifiable outsourced decryption in ehealth cloud. Wirel. Commun. Mob. Comput. 2018, 2018, 1–12. [Google Scholar] [CrossRef]
- Li, J.; Yao, W.; Han, J.; Zhang, Y.; Shen, J. User collision avoidance CP-ABE with efficient attribute revocation for cloud storage. IEEE Syst. J. 2017, 12, 1767–1777. [Google Scholar] [CrossRef]
- Wang, C.; Li, W.; Li, Y.; Xu, X. A ciphertext-policy attribute-based encryption scheme supporting keyword search function. In International Symposium on Cyberspace Safety and Security; Springer: Cham, Switzerland, 2013; pp. 377–386. [Google Scholar]
- Wang, Q.; Peng, L.; Xiong, H.; Sun, J.; Qin, Z. Ciphertext-policy attribute-based encryption with delegated equality test in cloud computing. IEEE Access 2017, 6, 760–771. [Google Scholar] [CrossRef]
- Padhya, M.; Jinwala, D. A novel approach for searchable CP-ABE with hidden ciphertext-policy. In International Conference on Information Systems Security; Springer: Cham, Switzerland, 2014; pp. 167–184. [Google Scholar]
- Zhu, H.; Wang, L.; Ahmad, H.; Niu, X. Key-policy attribute-based encryption with equality test in cloud computing. IEEE Access 2017, 5, 20428–20439. [Google Scholar] [CrossRef]
- Surya, V.; Mayan, J.A. A Secure Data Sharing Mechanism In Dynamic Cloud By Using KP-ABE. Res. J. Pharm. Technol. 2017, 10, 83–86. [Google Scholar] [CrossRef]
- Attrapadung, N.; Libert, B.; de Panafieu, E. Expressive key-policy attribute-based encryption with constant-size ciphertexts. In International Workshop on Public Key Cryptography; Springer: Berlin/Heidelberg, Germany, 2011; pp. 90–108. [Google Scholar]
- Touati, L.; Challal, Y. Collaborative kp-abe for cloud-based internet of things applications. In Proceedings of the 2016 IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 22–27 May 2016; pp. 1–7. [Google Scholar]
- NIST. Advanced Encryption Standard(AES). Available online: https://www.nist.gov/publications/advanced-encryption-standard-aes (accessed on 8 October 2022).
- Xian, Y.; Wang, X.; Teng, L. Double Parameters Fractal Sorting Matrix and Its Application in Image Encryption. IEEE TCSVT 2022, 32, 4028–4037. [Google Scholar] [CrossRef]
- Xian, Y.; Wang, X.; Wang, X.; Li, Q.; Yan, X. Spiral-Transform-Based Fractal Sorting Matrix for Chaotic Image Encryption. IEEE TCS I 2022, 69, 3320–3327. [Google Scholar] [CrossRef]
- Xian, Y.; Wang, X.; Teng, L.; Yan, X.; Li, Q.; Wang, X. Cryptographic system based on double parameters fractal sorting vector and new spatiotemporal chaotic system. Inf. Sci. 2022, 596, 304–320. [Google Scholar] [CrossRef]
- Top500. Fugaku Holds Top Spot, Exascale Remains Elusive. Available online: https://www.top500.org/lists/top500/2022/06 (accessed on 28 July 2022).
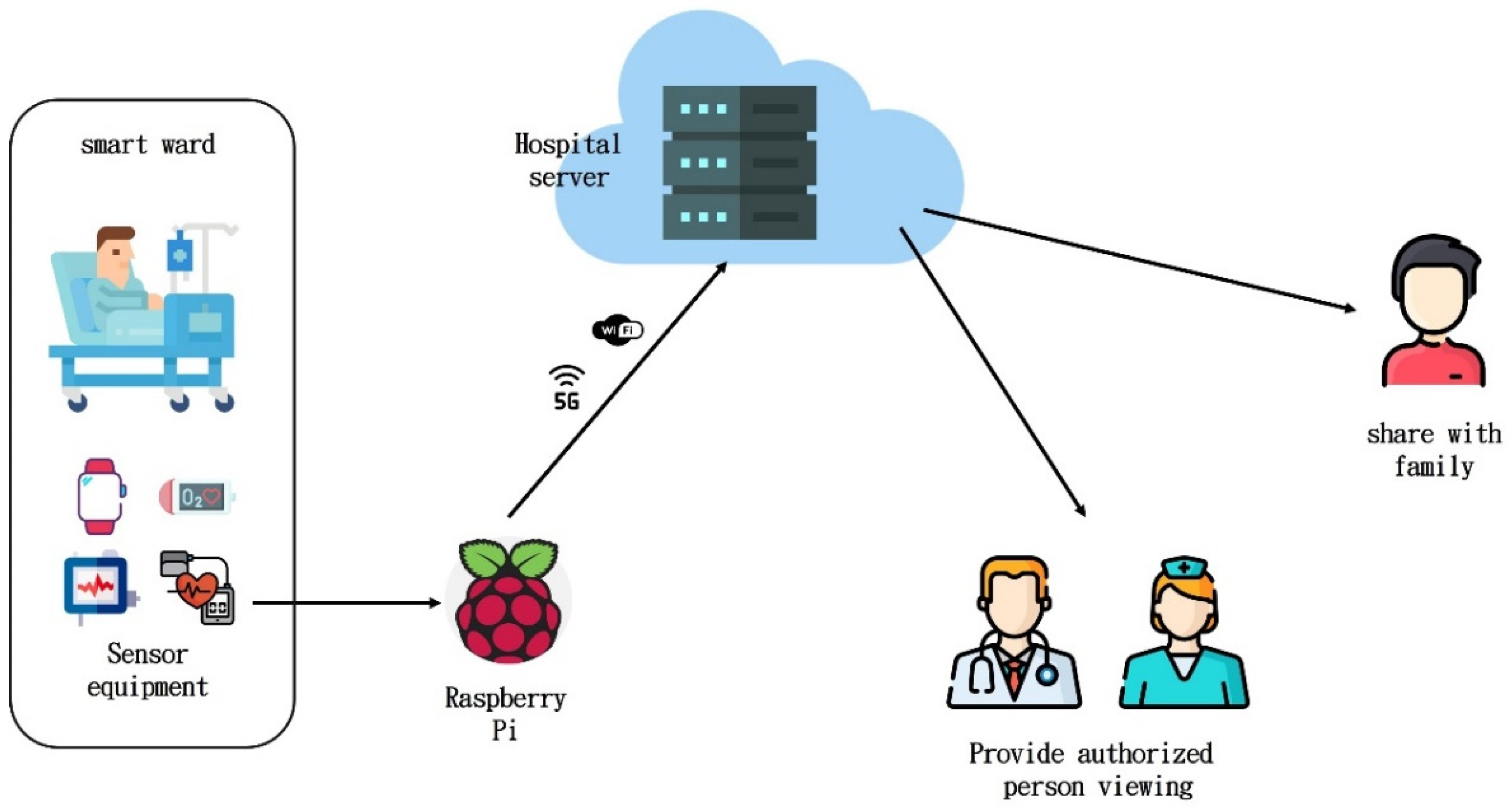
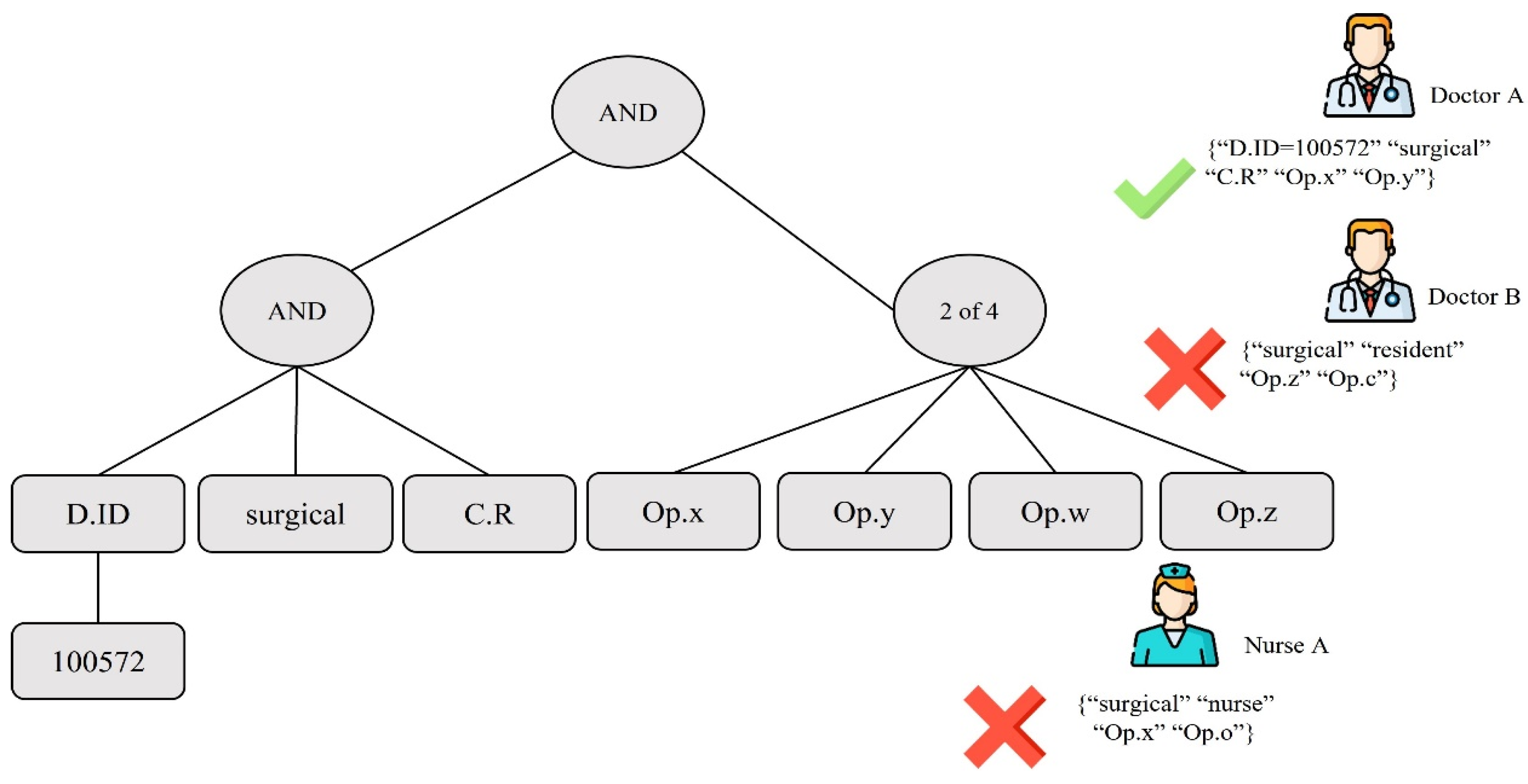
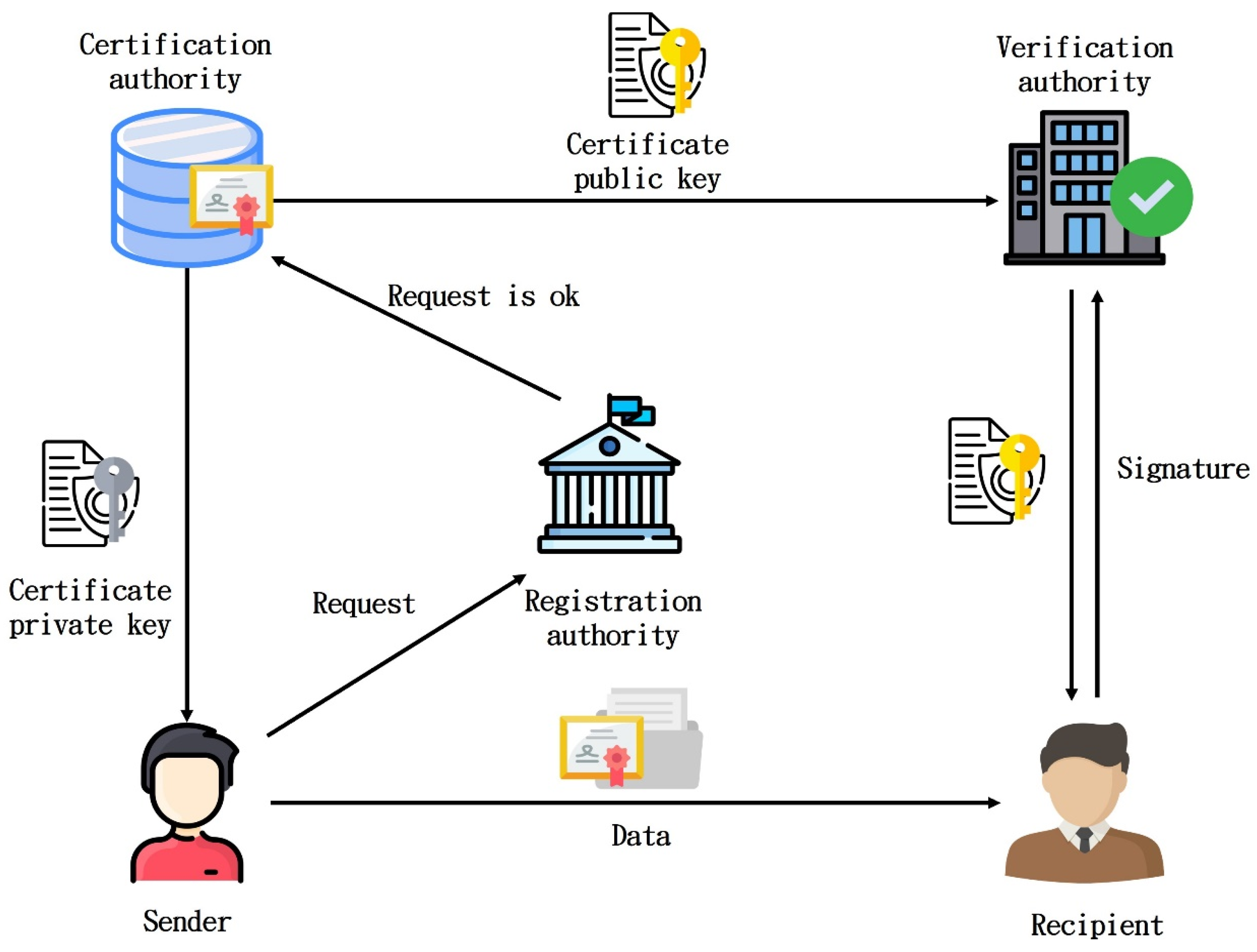

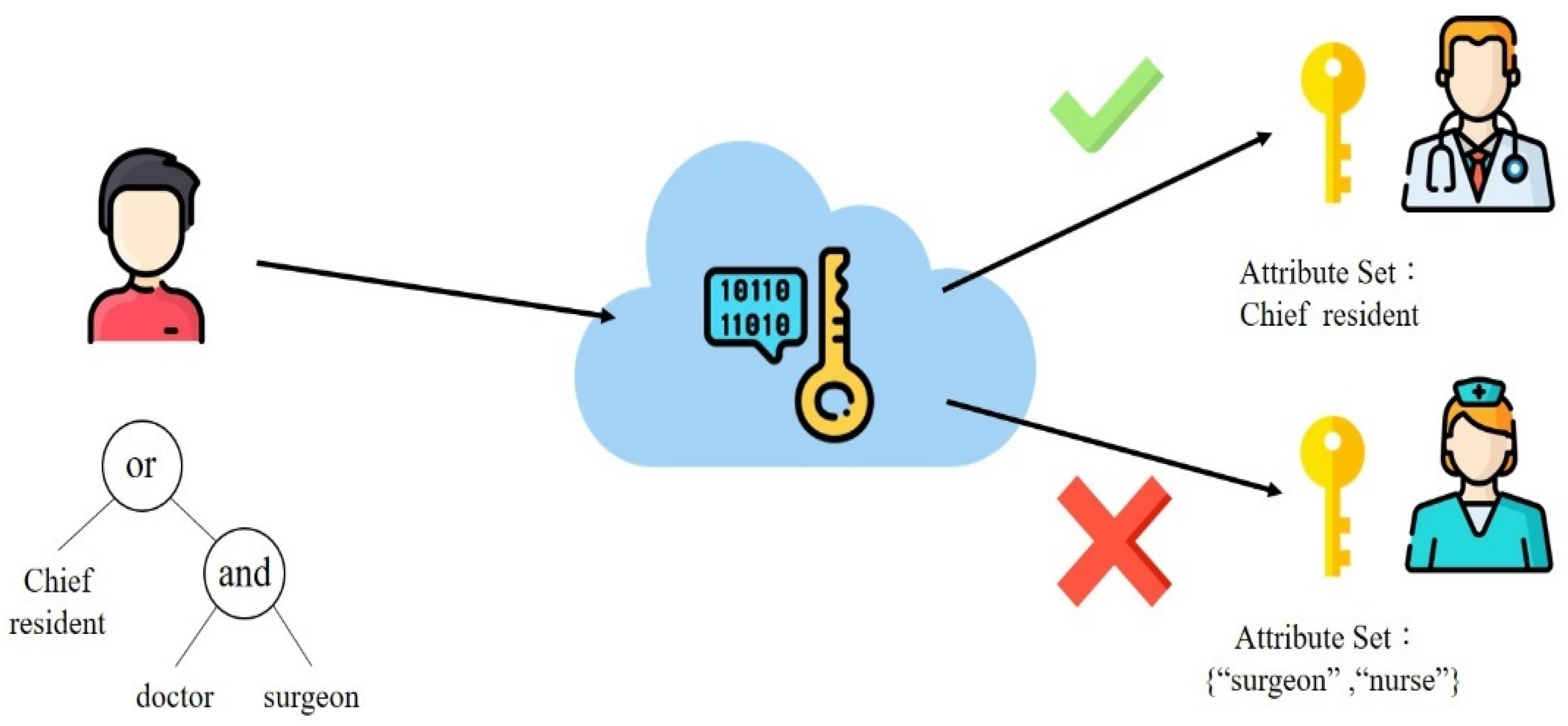






| Server-Level CPU | IoT Devices | |
|---|---|---|
| CPU | Intel(R) Xeon(R) CPU E3-1230 v3 | ARM Cortex-A53 |
| GPU | NVIDIA GT 630 | Broadcom Video Core IV |
| RAM | 12 GB | 1 GB |
| HD | 500 GB | 32 GB |
| OS | Ubuntu 18.04.5LTS | Raspbian OS |
| Name | Explanation |
|---|---|
| Attribute authorization center | Manage the attribute set of the authorized person and assigns the attribute to the authorized person. |
| Authorizer | Patient, encrypt data and send it to the hospital server store |
| Authorized person | Doctor or nurse can access physiological data as the authorized person |
| Hospital server | Store data and provide access to doctors and nurses |
| Notation | Definition | Notation | Definition |
|---|---|---|---|
| The identity of patient | The secret value of patient | ||
| The identity of doctor | |||
| Master key | >> | A right shift operation | |
| Public key | A bitwise exclusive-or operation | ||
| Secret key | || | A concatenation operation | |
| bilinear pairing | timestamp | ||
| plaintext | ciphertext |
| Notation | Definition | Notation | Definition |
|---|---|---|---|
| The identity of patient | Hmac value | ||
| The identity of doctor | A bitwise exclusive-or operation | ||
| Intermediate variables by patient | || | A concatenation operation | |
| Intermediate variables by doctor | timestamp | ||
| Intermediate variables by hospital server | Hash-based message authentication code function | ||
| The secret value | Hash function | ||
| Authentication parameters | Random number by PRNG | ||
| ciphertext | Session key | Session key |
| Explanation | Xeon E3-1230 | Raspberry Pi 3 B+ | |
|---|---|---|---|
| hash operation | 16 ms | 41 ms | |
| Hash-based message authentication | 3.6 ms | 8 ms | |
| 0.9 ms | 7.52 ms | ||
| Encrypt with session key | 2.2 ms | 6.4 ms | |
| random number generator | 1.6 ms | 11 ms |
| Result | Result | ||
|---|---|---|---|
| Frequency | PASS | Overlapping Template | PASS |
| Block Frequency | PASS | Universal Statistical | PASS |
| Cumulative Sums | PASS | Approximate Entropy | PASS |
| Runs | PASS | Serial | FAIL |
| Longest-Run-of-Ones | PASS | Linear Complexity | PASS |
| Binary Matrix Rank | PASS | Random Excursions | Insufficient number of cycles |
| FFT | FAIL | Random Excursions Varian | Insufficient number of cycles |
| Non-overlapping Template | PASS |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, I.-T.; Tsai, J.-M.; Chen, Y.-T.; Lee, C.-H. Lightweight Mutual Authentication for Healthcare IoT. Sustainability 2022, 14, 13411. https://doi.org/10.3390/su142013411
Chen I-T, Tsai J-M, Chen Y-T, Lee C-H. Lightweight Mutual Authentication for Healthcare IoT. Sustainability. 2022; 14(20):13411. https://doi.org/10.3390/su142013411
Chicago/Turabian StyleChen, I-Te, Jer-Min Tsai, Yin-Tung Chen, and Chung-Hong Lee. 2022. "Lightweight Mutual Authentication for Healthcare IoT" Sustainability 14, no. 20: 13411. https://doi.org/10.3390/su142013411
APA StyleChen, I.-T., Tsai, J.-M., Chen, Y.-T., & Lee, C.-H. (2022). Lightweight Mutual Authentication for Healthcare IoT. Sustainability, 14(20), 13411. https://doi.org/10.3390/su142013411








