Blockchain-Based Anti-Counterfeiting Management System for Traceable Luxury Products
Abstract
1. Introduction
1.1. Background
1.2. Related Works
- Anti-counterfeiting systems based on QR codes and databases: QR codes can be copied, and since their contents are fixed, unscrupulous parties can achieve counterfeiting effects in this way; lawless parties can forge or copy the database of genuine products according to the contents of each column of the genuine serial number; lawless parties can forge and create a pirated website similar to the genuine one and pretend to be genuine merchants to deceive consumers; merchants have the right to change the database, so merchants can manipulate the database themselves, making online verification no longer credible [9,10,11,12,13];
- RFID-based anti-counterfeiting systems: Since the data inside the chip can be read and written, there are many forged tags, which do not have their unique attributes. In the verification process of anti-counterfeiting, the information is transmitted through the Internet channel. Once the encryption measures of the commodity information are not in place, since the data management system tends to be centrally managed, there is a risk of the information being cracked and stolen, leading to the leakage and exposure of the commodity information [14].
- In terms of security, this system adopts the Elliptic Curve Digital Signature Algorithm (ECDSA) in cryptography to protect the integrity, traceability, and non-repudiation of data, thus further ensuring the security of information related to luxury products in the process of transmission;
- In terms of anti-counterfeiting and traceability, the system incorporates the Internet of Things (IoT), thereby enabling consumers to query specific information on the production and sales process of luxury products and the flow of products in real-time, and uses smart contracts to prevent human intervention in the process and ensure the accuracy of the data;
- In terms of logistics and distribution, when the logistics delivery is made, both parties must confirm the integrity of the luxury products. If their integrity is confirmed, both parties will scan a code to confirm, which will trigger the smart contract and upload the logistics information, a timestamp, and the identity information of both parties to the blockchain center. The corresponding responsible unit can then be contacted for that information if needed, for instance, if the products are damaged or swapped;
- In terms of its framework, this system uses Hyperledger Fabric, which combines the supply chain with the blockchain to further ensure the correct transmission of data.
2. Preliminary
2.1. Elliptic Curve Digital Signature Algorithm (ECDSA)
- When the sender needs to send a message, they first choose a random value in , calculate it , and then send the ECDSA signature pair together with the original message to the receiver (where h is the hash function);
- Once the receiver has received the signature pair and the original message , it verifies the validity of the ECDSA signature. First, it calculates , and second, it calculates and . Then, it determines the equality of and . If the values are equal, the receiver confirms that the ECDSA signature and message sent by the sender are valid.
2.2. Smart Contract
2.3. Blockchain
2.4. Hyperledger Fabric
3. Proposed Scheme
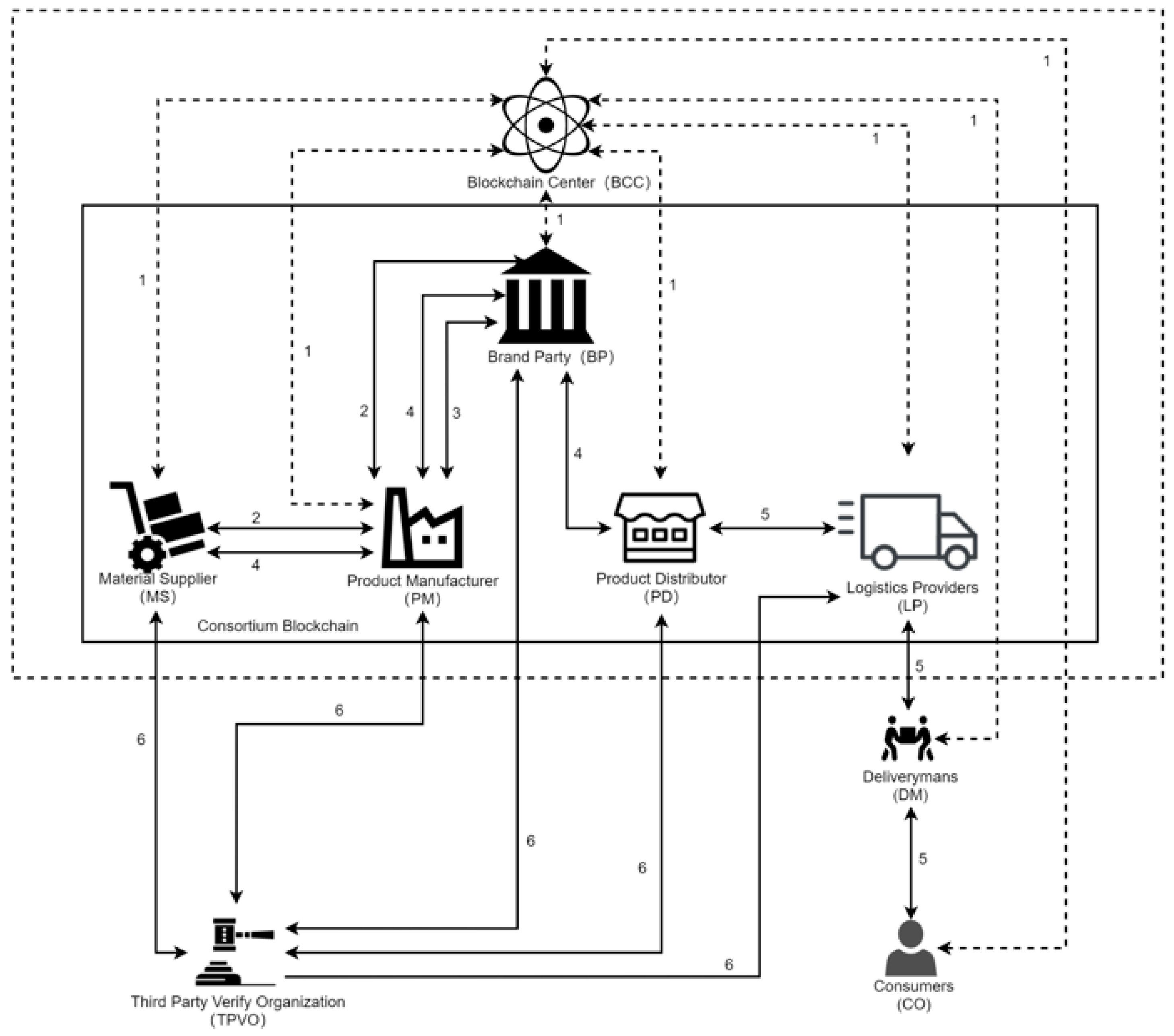
3.1. System Structure
- Blockchain Center (BCC): the BCC accepts registrations from all parties and issues proof of identity and public/private key pairs to each party;
- Brand Party (BP): The BP is responsible for the design of the product, reviewing whether the product manufacturer has produced a product that meets the standards, and controlling the eligibility of the product to be marketed. The supply chain only operates when the brand decides to produce a luxury product;
- Product Manufacturer (PM): Based on the product design drawings sent by the BP, the PM sends raw material requirements to the MS. When the BP gives them the go-ahead, the PM will produce the product and attach a web page or client interactive website containing the blockchain network to the product, which it sends to the distributor;
- Material Supplier (MS): the MS provides the raw materials for manufacturing products according to the raw material demand information sent by the PM, and records the sources of materials;
- Product Distributor (PD): the PD is a third-party sales platform or direct shop that sells products to customers, and which can upload transactions;
- Logistics Provider (LP): responsible for the delivery of products from third-party sales platforms or directly managed shops to consumers, able to confirm upload transactions with consumers and deliverymen, and record the logistics path of products;
- Consumers (CO): when the integrity of the products received is confirmed, the CO (or DM) will confirm the upload with the logistics provider;
- Deliveryman (DM): when the integrity of the product is confirmed, the DM (or CO) will confirm the upload with the logistics provider;
- Third-Party Verify Organization (TPVO): inspection agencies that check the information about luxury products through an app or with the client.
- Step 1: The registration phase for each role in the system. All Brand Parties (BP), Material Suppliers (MS), Product Manufacturers (PM), Product Distributors (PD), Logistics Providers (LP), Deliverymen (DM), and Consumers (CO) need to authenticate their access to the blockchain at the CA node in the center of the blockchain. Then, they will get the ECDSA signed public and private keys issued by the CA node, which will add them to the blockchain network, where they interact through a channel;
- Step 2: When a BP wants to design a new product, it enters the product design development phase. The BP makes a design for the new product, applies for a patent, signs the design and the patent license with a private key, and sends it to the PM, who verifies that the signature is correct and then signs the information about the raw materials needed to develop the new product, sending this to the MS. After the MS verifies the correctness of the signature, it returns a confirmation message of the product’s raw material content, which contains the product’s raw material identification code, the product’s raw material content, and the source of the raw material. After verifying the correctness of the message, the PM adds the information that the product is a sample and signs the above product information, and uploads it to the blockchain center via a sorting node to update the local ledger;
- Step 3: After the PM has completed the production of the product sample, it enters the product evaluation and approval phase. The PM carries out a corresponding evaluation of the produced sample product and, after the evaluation, sends the product-related evaluation data and raw material-related information, signed with a private key, to the BP. If the BP approves the product, they return a signed production certificate for the product to the PM;
- Step 4: After the PM has obtained the production certificate for the product and verified its correctness, it enters the ordering and production phase. The PD sends the order to the BP, who confirms the order information and sends it to the PM with a signature. The PM produces the product according to the order information, signs the information on the raw materials required to produce the product, and sends it to the MS, who verifies that the signature is correct and provides the required raw materials for production, sending the information on the raw materials to the PM with a signature. The PM verifies the correctness of the signature and then proceeds with the mass production of the product, while marking the product with a unique identification code that allows the user to query the product information in the future. Once the product has been produced, the PM sends the product to the PD and integrates the information about the product into the order information, signing it with a private key and uploading it to the blockchain center via a sorting node to update the local ledger;
- Step 5: The product purchase and logistics delivery phase. After the CO purchases the product from the PD, the product is signed by both parties and enters the logistics delivery phase. During the product delivery process, the CO can check the information related to the product logistics in real-time. There are two situations in logistics delivery: (1) When two DMs hand over the product, both DMs need to jointly scan the code to confirm the product is complete and error-free, triggering a smart contract to upload the logistics information, timestamp, and identity information of both parties to the blockchain center. (2) When the CO receives the product, they also need to confirm that the product is complete and then scan the code with the DM to trigger the smart contract, which uploads the logistics information, timestamp, name of the signatory, and the DM’s information to the blockchain center. When there is a problem with the delivery of the product, the logistics and delivery can be traced;
- Step 6: All TPVO validation (e.g., consumers, inspection bodies, blockchain values, product approval certificates, etc.) can be verified using the public keys of the BP, MS, PM, and PD. After that, they can verify the complete production history and legitimacy of the product. Furthermore, the TPVO verifies the signature information of the PM and MS to confirm that the content of the raw material is correct and that the product is a sample or commercially available. Moreover, the TPVO verifies the signatures of the PM and BP and the product approval certificate to verify the marketing authorization of the product. In addition, the TPVO verifies the signatures of the PM and the BP to obtain test data for the product. Finally, the TPVO can verify the route of the product during logistics and the handover between the two parties.
3.2. Notation
3.3. Initialization Phase
- (1)
- In the luxury product structure, information about the product, its specific content, and the material supplier, product manufacturer, consumer, and logistics order numbers are recorded;
- (2)
- Role types and related procedural structures are assigned to those involved in the supply chain;
- (3)
- In the structure of the product order, information about the product order, its specific content, and status, as well as the product distributor and product manufacturer numbers, are recorded;
- (4)
- In the structure of the logistics order, information about the logistics order, specific contents, status, the number of couriers handing it over during the logistics delivery, the handover time, and the numbers of product distributors, consumers, and logistics companies are recorded.
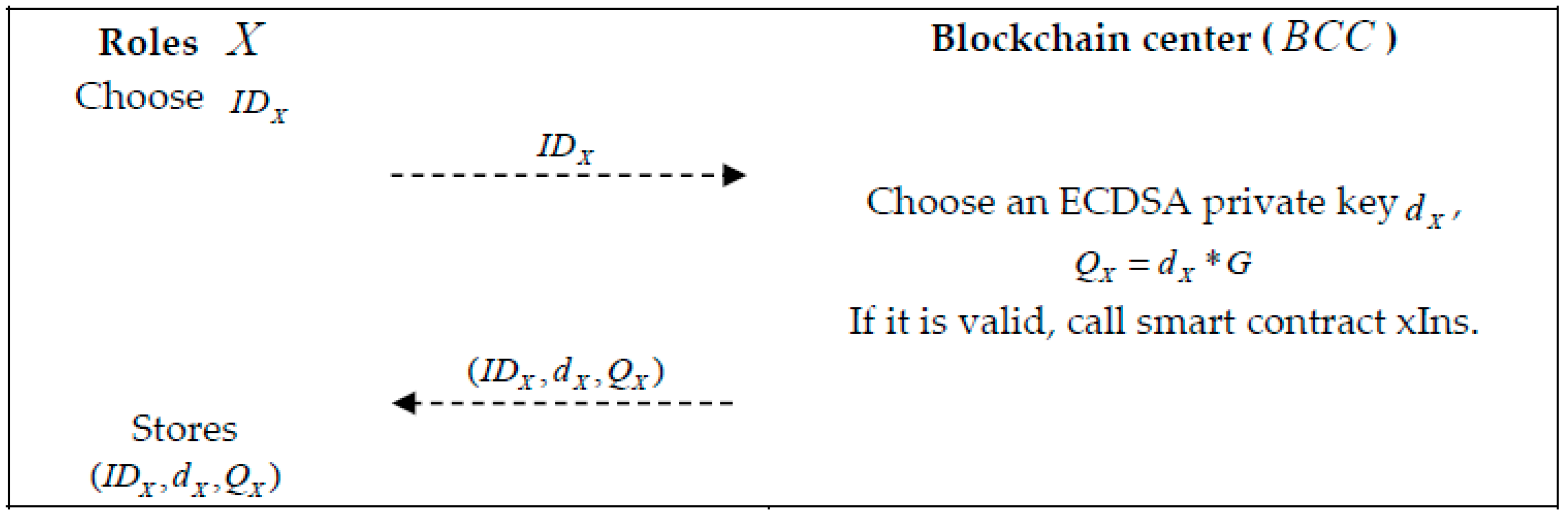
3.4. Registration Phase
- Step 1: Those involved in the system, in all roles , each generate an identity and then send their generated through the application to a CA node in the blockchain center for registration and validation, to determine the legitimacy of their identity;
- Step 2: The CA node at the center of the blockchain generates an ECDSA private key based on the roles in the system and calculates the public key :When the correct identities of all roles have been verified, the smart contract registration will be triggered, as shown in Algorithm 1;
- Step 3: All roles in the system receive the signature message parameter and store it.
| Algorithm 1. A scheme for chain code registration. |
| var X[]Roles X |
| func Registration (X_name string, X_detail string, var X_role RoleType) (idNumber string) { |
| idNumber = GenerateUniqueID() |
| X = append (X, Roles X{ |
| idNumber: product_idNumber, |
| name: X_name, |
| detail: X_detail, |
| Role: X_role, |
| }) |
| return idNumber |
| } |
3.5. Product Design and Development Phase
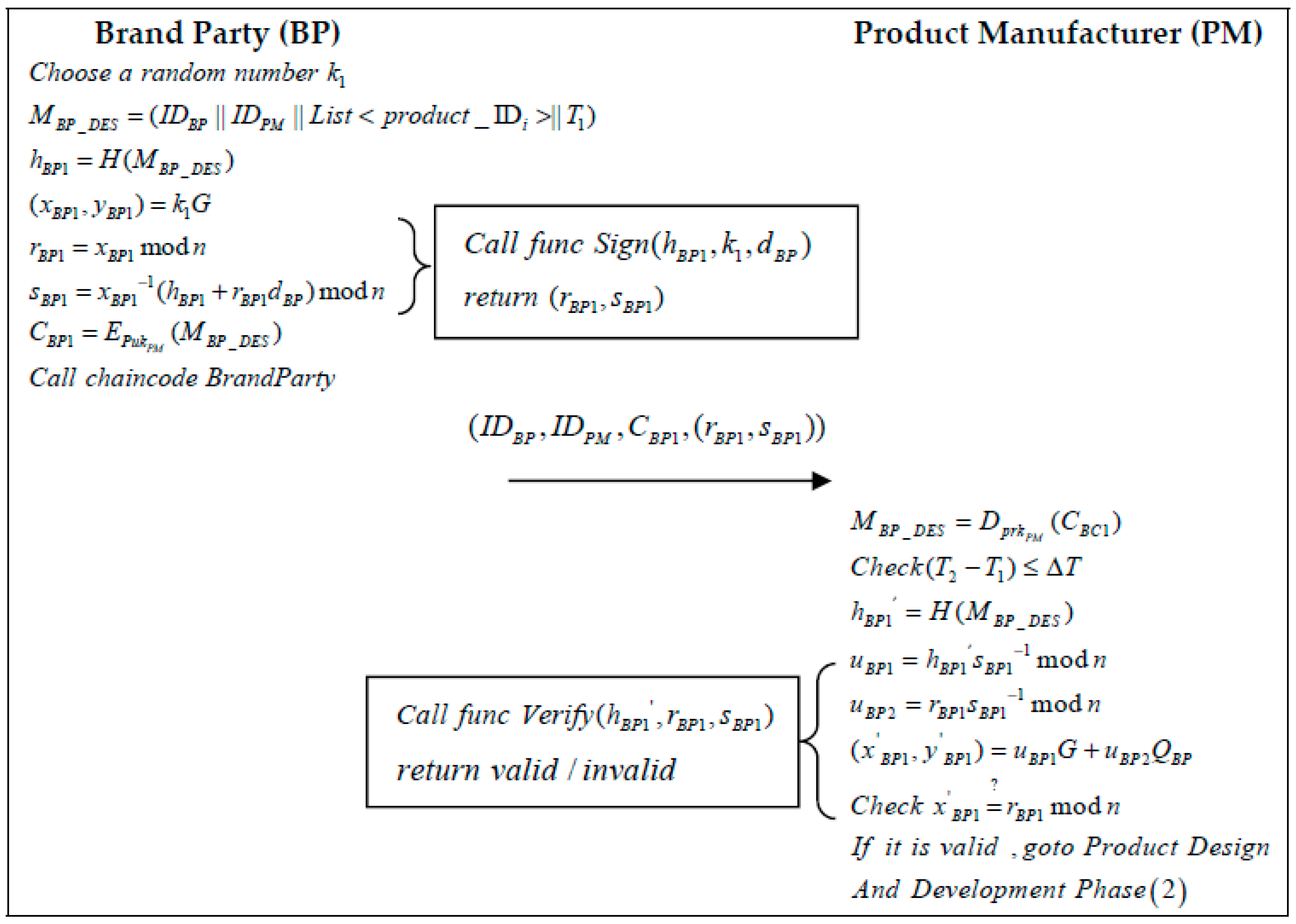
- Step 1: When the BP designs a new product, it signs the design and the patent license and delivers it to the PM at time . The design includes product information and product material information. The BP chooses a random number and generates a message containing multiple product identifiers:The BP then calculates the message hash and executes the “Sign” algorithm to generate the signature . The “Sign” algorithm is shown in Algorithm 2:
| Algorithm 2. A scheme for a communication protocol. |
| func Sign (h string,k string, d string)(r string, s string){ |
| (x,y) = k*G; |
| r = x%n |
| s = (h + r*d)/x%n |
| return r,s |
| } |
| func Verify(h string,r string,s string)(result string){ |
| u1 = h/s%n |
| u2 = r/s%n |
| (x,y) = u1*G + u2*Q |
| If x = r{ |
| return “valid” |
| }else{ |
| return “invalid” |
| } |
| } |
- Step 2: When the PM receives a message from the BP at moment, it first decrypts the message using its private key:Secondly, the PM verifies the validity of the timestamp:Once the validity of the time has been verified, the PM uses the “Verify” function in Algorithm 2 to calculate a hash value to verify the message:If the signature verification is valid, the PM signs the raw material type and content requirements for the product at time and delivers them to the MS. The PM chooses a number at random and also generates the product raw material requirement information :The PM then calculates the message hash and executes the “Sign” algorithm to generate the signature . The “Sign” algorithm is shown in Algorithm 2:The generated message is encrypted with the MS public key:The PM then sends the information to the MS.
| Algorithm 3. Chain code of the product design and development phase. |
| var LP []LuxuryProduct; count = 0; |
| func BrandParty (int num, P_Name string, P_kind string, ID_BP string, Date string, Product_INF string, Signature string) (Product_IDs []string){ |
| for i:= 0; i < num; i++ { |
| count = count + 1 |
| LP = append (LP, new LuxuryProduct{Product _idNumber = Generate_product_id()}) |
| Product_IDs = append(Product_IDs, TP[count]. Product_idNumber) |
| } |
| for i:= 0; i < num; i++ { |
| index:= SearchProduct_ID(Product_IDs[i]); |
| LP[index].Product_name = P_Name |
| LP[index].Product_kind = P_kind |
| LP[index].Product_brand_idNumber = ID_BP |
| LP[index].Product_information = append(LP[index].Product_information, Product _INF) |
| LP[index].designDate = Date |
| LP[index].BP_Signature = Signature |
| } |
| } |
| func ProductManufacturer (Material string, ID_PM string, Product_INF string, price string, Product_IDs []string, Signature string) { |
| for i:= 0; i < Product_IDs.Length; i++ { |
| index:= SearchProduct_ID(Product_IDs[i]); |
| LP[index].Product_material = Material |
| LP[index].Product_information = append(LP[index].Product_information, Product _INF) |
| LP[index].Product_price = price |
| LP[index].createDate = time.Now() |
| LP[index].Product_manufacturer_idNumber = ID_PM |
| LP[index].PM_Signature = Signature |
| } |
| } |
| func MaterialSupplier (ID_MS string, Product_IDs []string, Signature string){ |
| for i:= 0; i < Product_IDs.Length; i++ { |
| index:= SearchProduct_ID(Product_IDs[i]); |
| LP[index].Product_MS_idNumber = ID_MS |
| LP[index].MS_Signature = Signature |
| } |
| } |
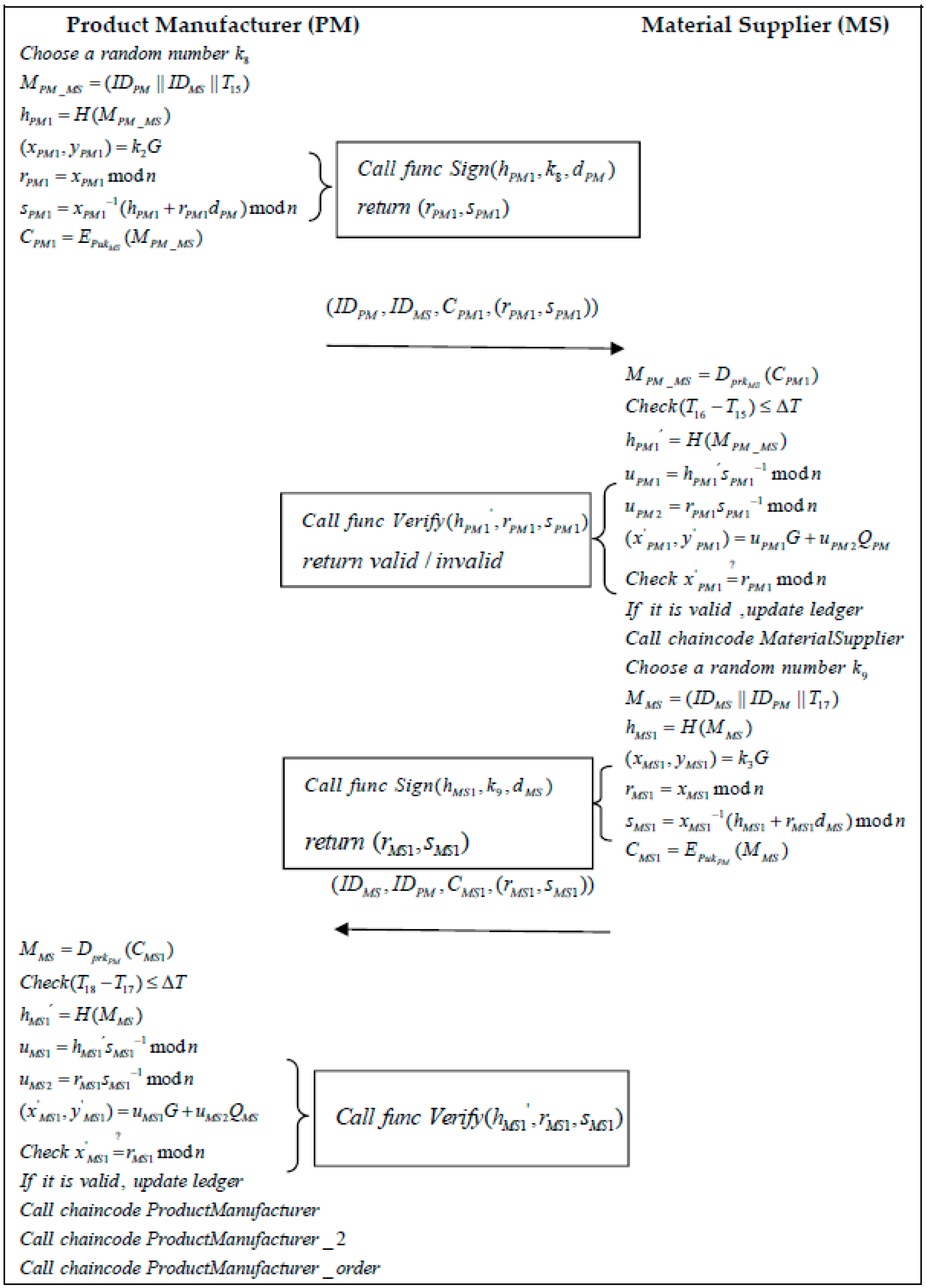
- Step 3: When the MS receives a message from the PM at moment, it first decrypts the message using its private key:Secondly, the PM verifies the validity of the timestamp:Once the validity of the time has been verified, the PM uses the “Verify” function in Algorithm 2 to calculate a hash value to verify the message:If the signature verification is valid, the MS executes the “Material Supplier” function at time . The algorithm of this function is shown in Algorithm 3, which provides the PM with the raw materials needed to produce the product according to the raw material requirements in the PM’s message, as well as the type, content, and source of the raw materials. The MS randomly selects a number and generates a message :The MS then calculates the message hash and executes the “Sign” algorithm to generate the signature . The “Sign” algorithm is shown in Algorithm 2:The generated message is encrypted by the PM’s public key:The MS then sends the information to the PM.
- Step 4: When the PM receives a message from the MS at moment, it first decrypts the message using its private key:Secondly, the PM verifies the validity of the timestamp:Once the validity of the time has been verified, the PM uses the “Verify” function in Algorithm 2 to calculate a hash value to verify the message:
3.6. Product Evaluation and Approval Phase
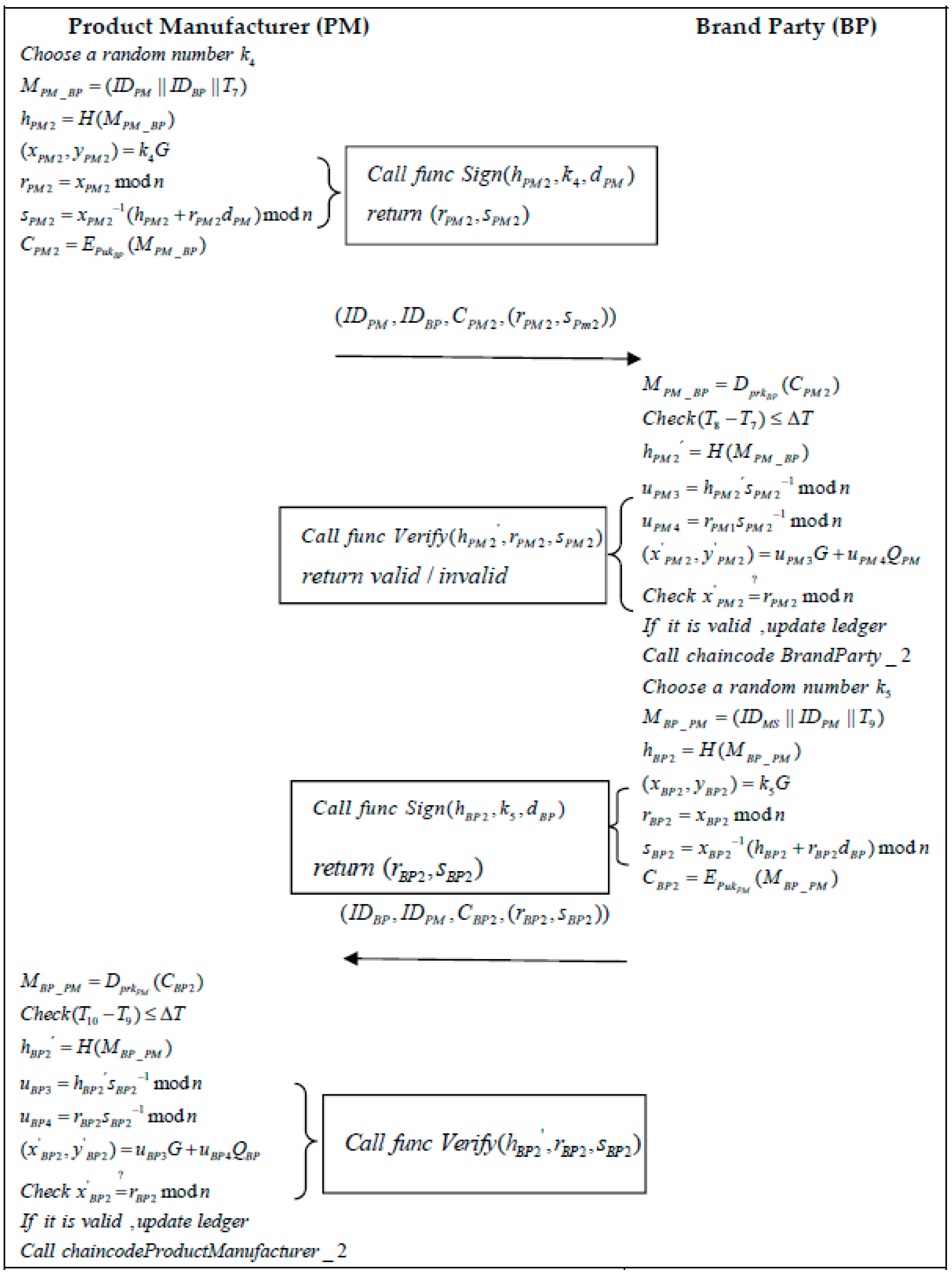
- Step 1: For the product samples produced during the product design and development phase, the PM evaluates the product, finishes the evaluation at moment , and sends the test results to the BP with a signature. The PM randomly selects a number and generates the product evaluation result information :The PM then calculates the message hash and executes the “Sign” algorithm to generate the signature . The “Sign” algorithm is shown in Algorithm 2:The generated message is encrypted by the BP public key:The PM then sends the information to the BP.
- Step 2: When the BP receives a message from the PM at moment , it first decrypts the message using its private key:Secondly, the BP verifies the validity of the timestamp:Once the validity of the time has been verified, the BP uses the “Verify” function in Algorithm 2 to calculate a hash value to verify the message:If the signature verification is valid, the BP looks at the test data of the product at moment . If it is satisfied with the test data of the product, it executes the “BrandParty_2” function, the algorithm of which is shown in Algorithm 4, signs the production license of the product, and gives it to the PM. The BP selects a random number and generates the product license information :The BP then calculates the message hash and executes the “Sign” algorithm to generate the signature . The “Sign” algorithm is shown in Algorithm 2:The generated encrypted message is encrypted by the PM’s public key:The BP then sends the information to the PM.
- Step 3: When the PM receives a message from the BP at moment , it first decrypts the message using its private key:Secondly, the PM verifies the validity of the timestamp:Once the validity of the time has been verified, the PM uses the “Verify” function in Algorithm 2 to calculate a hash value to verify the message:If the signature verification is valid, the PM executes the “ProductManufacturer_2” function, the algorithm for which is shown in Algorithm 4, and updates the local ledger with the information.
| Algorithm 4. Chain code of the product evaluation and approval phase. |
| func BrandParty_2 (ID_BP string, Product_INF string, Product_IDs []string, Signature string) { |
| for i:= 0; i < Product_IDs.Length; i++ { |
| index:= SearchProduct_ID(Product_IDs[i]); |
| LP[index].Product_brand_idNumber = ID_BP |
| LP[index].Product_information = append(LP[index].Product_information, Product _INF) |
| LP[index].BP_Signature = Signature |
| } |
| } |
| func ProductManufacturer_2 (result string, ID_PM string, Product_INF string, Product_IDs []string, Signature string) { |
| for i:= 0; i < Product_IDs.Length; i++ { |
| index:= SearchProduct_ID(Product_IDs[i]); |
| LP[index].testResult = result |
| LP[index].Product_information = append(LP[index].Product_information, Product _INF) |
| LP[index].Product_manufacturer_idNumber = ID_PM |
| LP[index].PM_Signature = Signature |
| } |
| } |
3.7. Product Ordering and Production Phase
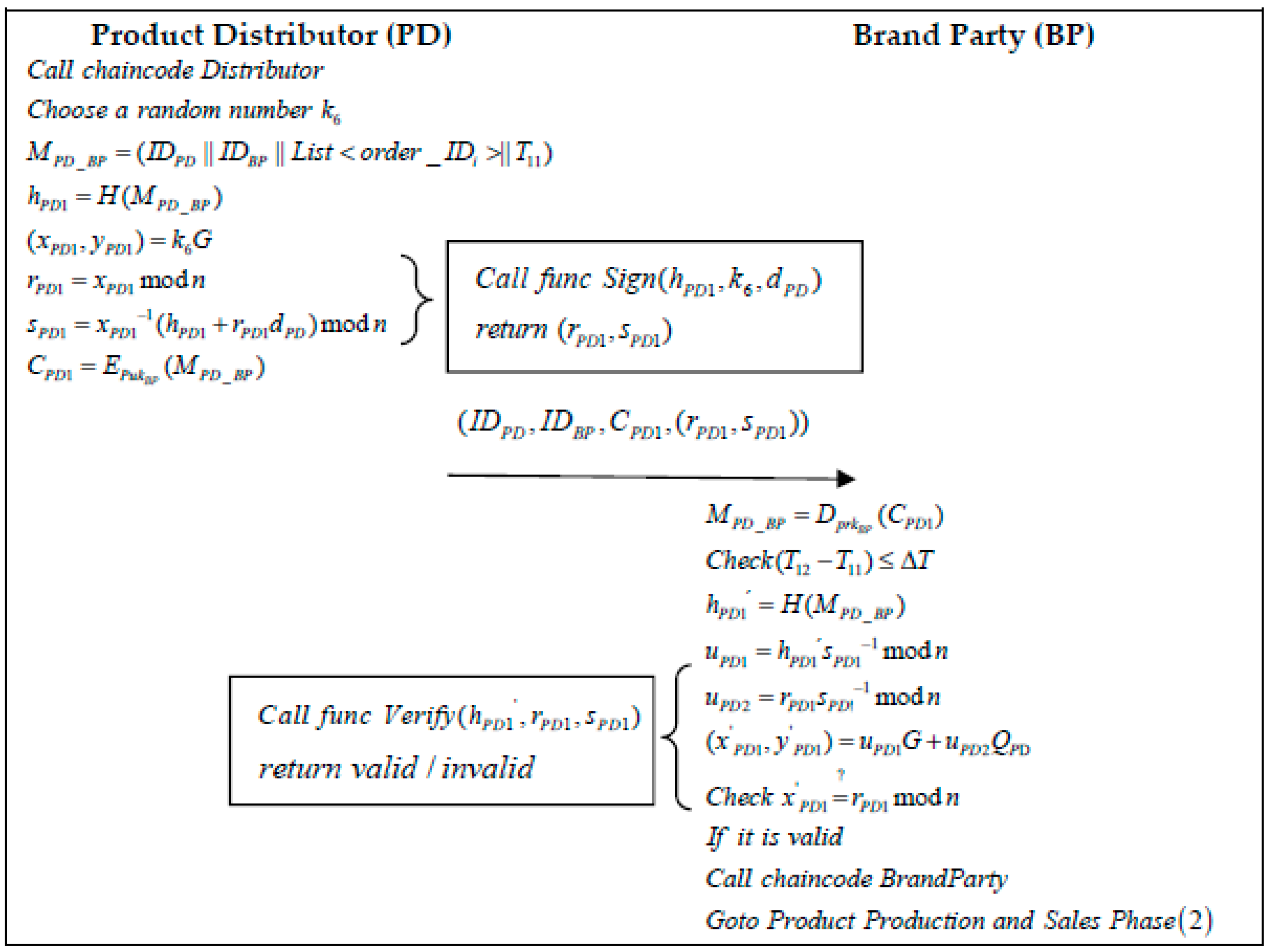
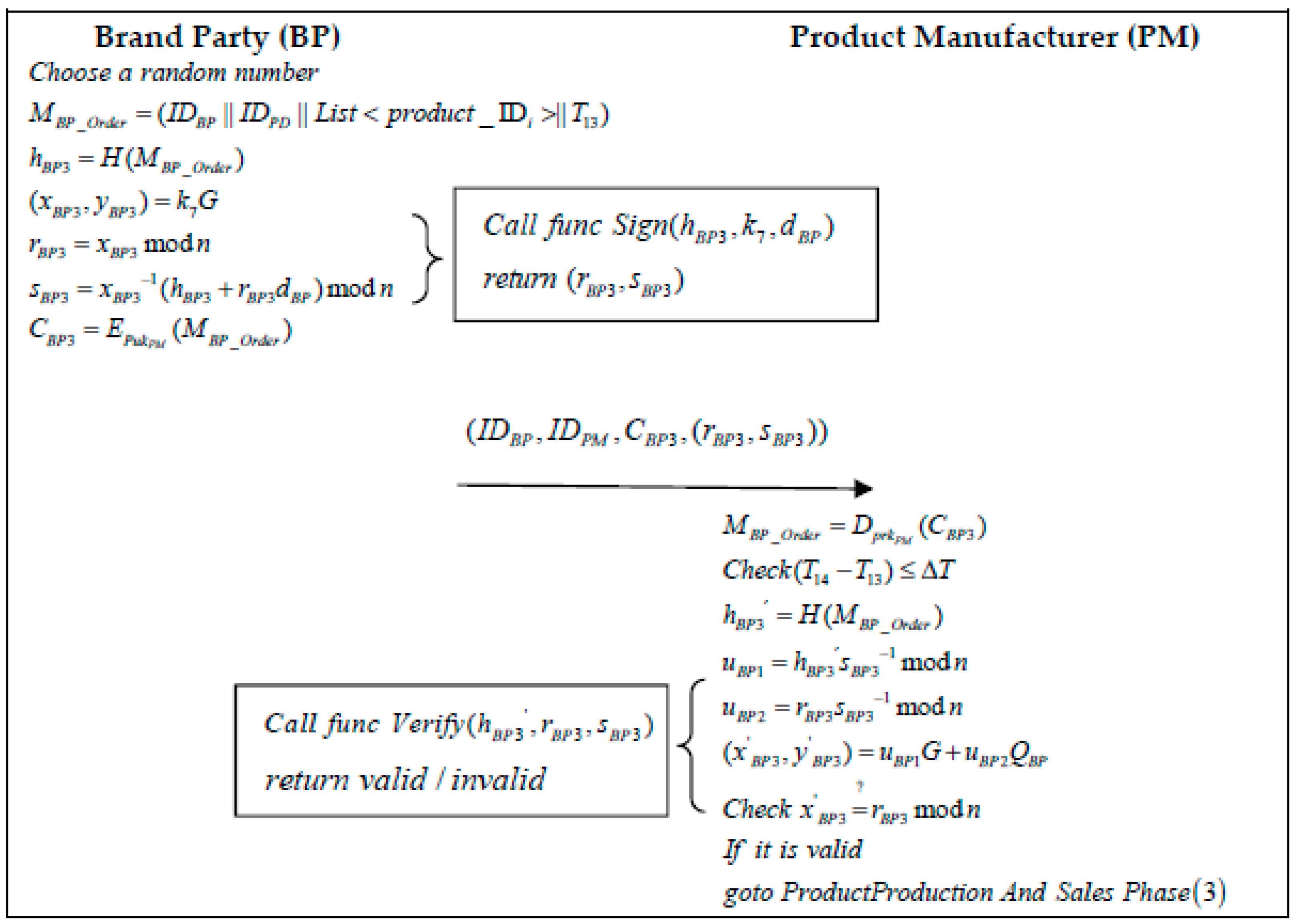
- Step 1: When a PD wants to order a product, it submits an order request to the brand at moment and generates an order for the product, executing the “Distributor” function, the algorithm of which is shown in Algorithm 5. This function signs the order contents and sends those to the BP. The PD selects a random number and generates the product order information :The PD then calculates the message hash and executes the “Sign” algorithm to generate the signature . The “Sign” algorithm is shown in Algorithm 2:The generated encrypted message is encrypted by the BP public key:The PD then sends the information to the BP.
- Step 2: When a BP receives a message from a PD at a moment , it first decrypts the message using its private key:Secondly, the BP verifies the validity of the timestamp:
| Algorithm 5. Chain code of the product production and sales phase. |
| var PO []ProductOrder |
| func Distributor (ID_PD string, ID_BP string, kind string, Order_INF string, Order_IDs []string, state string) { |
| for i:= 0; i < Order_IDs.Length; i++ { |
| index:= SearchOrder_ID(Order_IDs[i]); |
| PO[index].Order_PD_idNumber = ID_PD |
| PO[index]. Order_kind = kind |
| PO[index].Order_brand_idNumber = ID_BP |
| PO[index].Order_information = Order_INF |
| PO[index].Order_createDate = time.Now() |
| PO[index].Order_state = state |
| } |
| } |
| func ProductManufacture_order (ID_PM string, Order_IDs []string, state string) { |
| for i:= 0; i < Order_IDs.Length; i++ { |
| index:= SearchOrder_ID(Order_IDs[i]); |
| PO[index].Order_PM_idNumber = ID_PM |
| PO[index].Order_state = state |
| } |
| } |
- Step 3: When the PM receives a message from the BP at moment , it first decrypts the message using its private key:Secondly, the PM verifies the validity of the timestamp:Once the validity of the time has been verified, the PM uses the “Verify” function in Algorithm 2 to calculate a hash value to verify the message:If the signature verification is valid, the PM signs the product material type and content requirements at moment and delivers them to the MS. The PM chooses a random number and generates the product raw material requirement information :The PM then calculates the message hash and executes the “Sign” algorithm to generate the signature . The “Sign” algorithm is shown in Algorithm 2:The generated message is encrypted by the MS’s public key:The PM then sends the information to the MS.
- Step 4: When the MS receives a message from the BP at a moment , it first decrypts the message using its private key:Secondly, the MS verifies the validity of the timestamp:Once the validity of the time has been verified, the MS uses the “Verify” function in Algorithm 2 to calculate a hash value to verify the message:If the signature verification is valid, the MS executes the “Material Supplier” function at moment . The algorithm of this function is shown in Algorithm 3 and provides the PM with the raw materials needed to produce the product according to the raw material requirements in its message, as well as the type, content, and source of the raw materials. The information is signed and given to the PM. The MS selects a random number and generates a message :The MS then calculates the message hash and executes the “Sign” algorithm to generate the signature . The “Sign” algorithm is shown in Algorithm 2:The generated message is encrypted by the PM’s public key:The MS then sends the information to the PM.
- Step 5: When the PM receives a message from the MS at moment , it first decrypts the message using its private key:Secondly, the PM verifies the validity of the timestamp:Once the validity of the time has been verified, the MS uses the “Verify” function in Algorithm 2 to calculate a hash value to verify the message:If the signature verification is valid, the product ordered by the PD is manufactured, tested, and evaluated, then the “ProductManufacturer”, “ProductManufacturer_2”, and “ProductManufacturer_order” functions are executed with Algorithms 3, 4, and 5, respectively, and the local book is updated with the information to ship the product to the PD.
3.8. Product Purchase and Logistics Distribution Phase
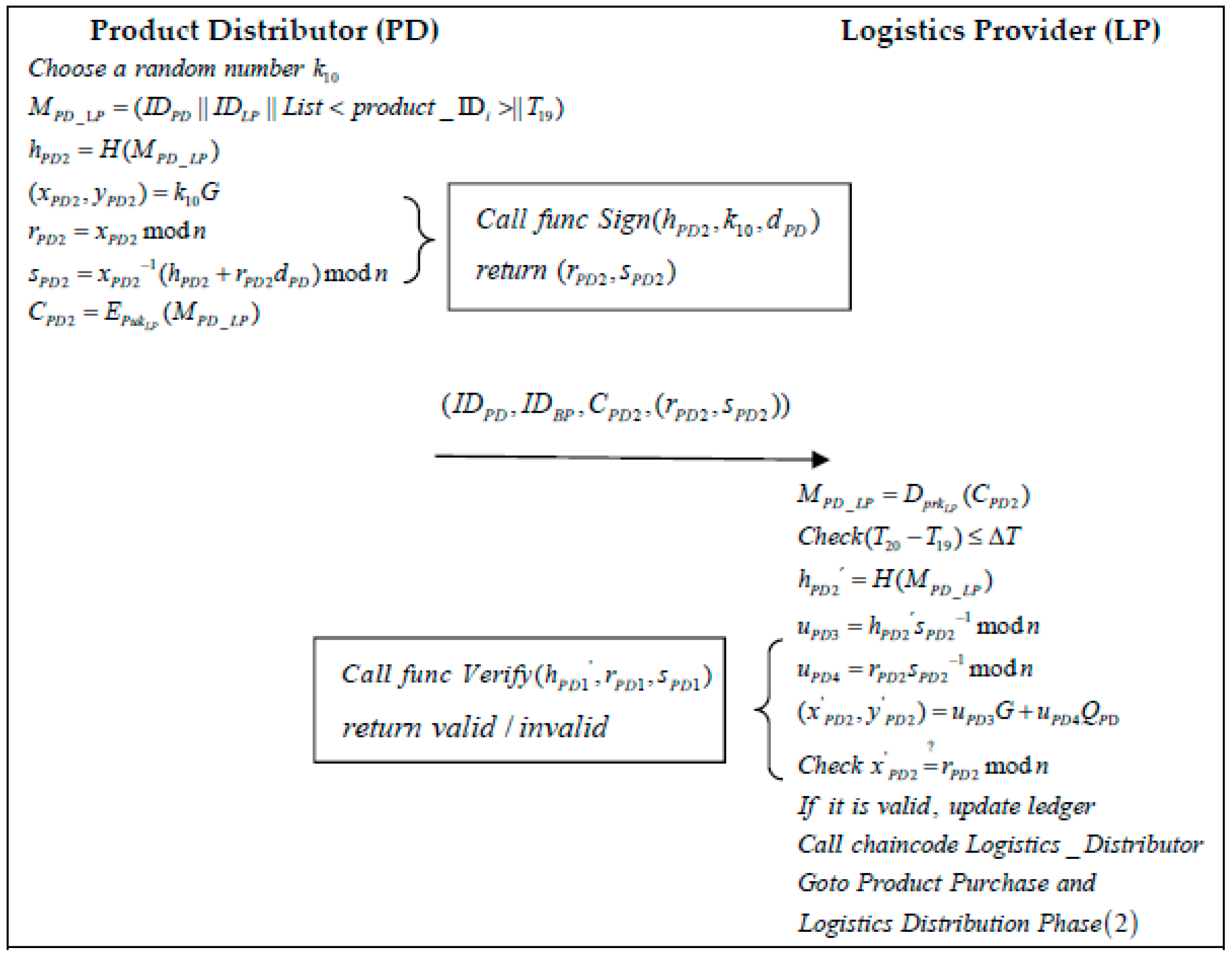
- Step 1: When a CO wants to buy a product, they request that the PD buy it. The PD executes the “Distributor_sell” function, the algorithm of which is shown in Algorithm 6, and sends the PD UID, CO UID, and order type to the LP at moment . The PD randomly selects a number and generates the information related to the logistics order :The PD then calculates the message hash and executes the “Sign” algorithm to generate the signature . The “Sign” algorithm is shown in Algorithm 2:The generated message is encrypted by the LP’s public key:The PD then sends the information to the LP.
- Step 2: When an LP receives a message from a PD at a moment , it first decrypts the message using its private key:Secondly, the LP verifies the validity of the timestamp:Once the validity of the time has been verified, the LP uses the “Verify” function in Algorithm 2 to calculate a hash value to verify the message:If the signature verification is valid, the LP generates the corresponding logistics order for each product at moment and executes the “Logistics_Distributor” function, the algorithm of which is shown in Algorithm 6. At moment , the logistics order is assigned to the DM, while the LP randomly selects a random number and generates the logistics order UID information :
| Algorithm 6. Chain code of the product purchase and logistics distribution phase. |
| func Distributor_sell (ID_CO string, ID_PD string, Product_INF string, Product_IDs []string, Signature string) { |
| for i:= 0; i < Product_IDs.Length; i++ { |
| index:= SearchProduct _ID(Product_IDs[i]); |
| LP[index].Product_consumer_idNumber = ID_CO |
| LP[index].Product_distributor_idNumber = ID_PD |
| LP[index].Product_information = Product_INF |
| LP[index].PD_Signature = Signature |
| } |
| } |
| var LO []LogisticsOrder |
| func Logistics_Distributor (ID_PD string, ID_CO string, ID_P []string, kind string, Product_IDs []string, state string, Signature string) { |
| for i:= 0; i < Product_IDs.Length; i++ { |
| LO[i].Logistics_idNumber = Generate_Logistics_id() |
| LO[i].Logistics_distributor_idNumber = ID_PD |
| LO[i].Logistics_company_idNumber = ID_LP |
| LO[i].Logistics_consumer_idNumber = ID_CO |
| LO[i].Logistics_product_idNumber = Product_IDs [i] |
| LO[i].Logistics_kind = kind |
| LO[i].Logistics_createDate = time.Now() |
| LO[i].Logistics_state = state |
| } |
| for i:= 0; i < Product_IDs.Length; i++ { |
| index_P:= SearchProduct_ID(Product_IDs[i]); |
| index_L:= SearchLogistics_ID(Product_IDs[i]); |
| LP[index_P].Product_courier_idNumber = LO[index_L].Logistics_idNumber |
| LP[index_P].LP_Signature = Signature |
| } |
| } |
- Step 3: When a DM receives a message from an LP at moment , it first decrypts the message using its private key:Secondly, the DM verifies the validity of the timestamp:Once the validity of the time has been verified, the DM uses the “Verify” function in Algorithm 2 to calculate a hash value to verify the message:If the signature verification is valid, the DM executes the “Deliveryman_DM” function, the algorithm of which is shown in Algorithm 7. The product is then delivered.
| Algorithm 7. Chain code of the product purchase and logistics distribution phase. |
| DM_Num = 0 |
| func Deliveryman_DM(ID_DM_1 string, ID_DM_2 string, Location string, Logistics_IDs []string, state string, Signature string) { |
| for i:= 0; i < Logistics_IDs.Length; i++ { |
| index_L:= SearchLogistics_ID(Logistics_IDs[i]); |
| index_P:= SearchLogistics_Product_ID(Logistics_IDs[i]) |
| LO[index_L].Logistics_inf[DM_Num].Shipper_idNumber = ID_DM_1 |
| LO[index_L].Logistics_inf[DM_Num].Recipient_idNumber = ID_DM_2 |
| LO[index_L].Logistics_inf[DM_Num].Recipient_Location = Location |
| LO[index_L].Logistics_inf[DM_Num].Recipient_time = time.Now() |
| LO[index_L].Logistics_state = state |
| LP[index_P].DM_Signature[DM_num] = Signature |
| } |
| DM_Num += 1 |
| } |
| func Receiver (ID_DM string,ID_CO string, Location string, Logistics_ID string, state string, Signature string) { |
| index_L:= SearchLogistics_ID(Logistics_ID); |
| index_P:= SearchLogistics_Product_ID(Logistics_IDs[i]) |
| LO[index_L].Logistics_inf[DM_Num].Shipper_idNumber = ID_DM |
| LO[index_L].Logistics_inf[DM_Num].Recipient_idNumber = ID_CO |
| LO[index_L].Logistics_inf[DM_Num].Recipient_Location = Location |
| LO[index_L].Logistics_inf[DM_Num].Recipient_time = time.Now() |
| LO[index_L].Logistics_finishDate = time.Now() |
| LO[index_L].Logistics_state = state |
| LP[index_P].CO_Signature = Signature |
| } |
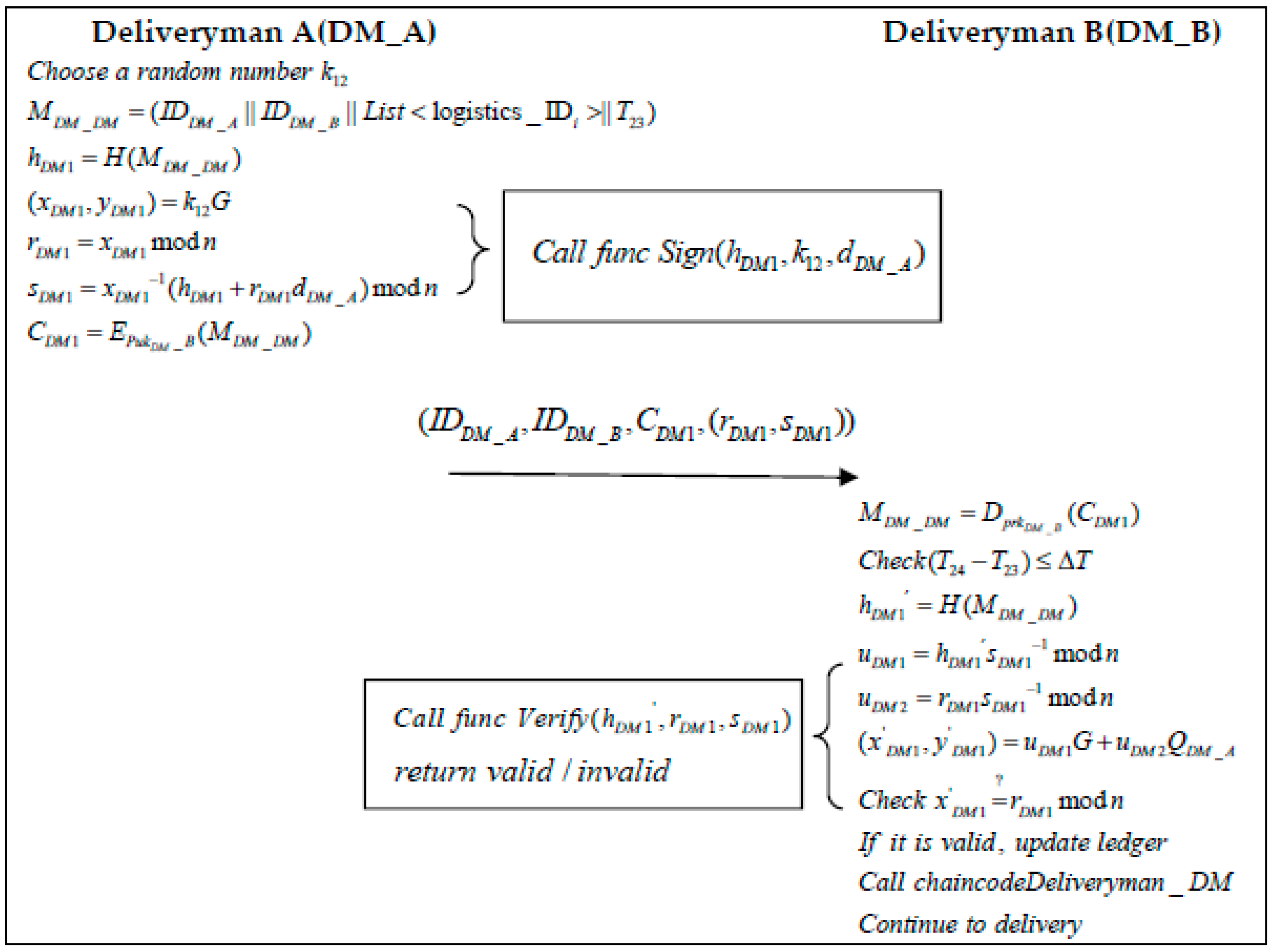
- Step 4: The distribution handover process of the products takes one of two kinds:
- (a)
- When DM A delivers the product to DM B at moment .
- Step 1: DM_A randomly selects a number and generates the information related to the logistics order :DM_A then calculates the message hash and executes the “Sign” algorithm to generate the signature . The “Sign” algorithm is shown in Algorithm 2:The generated message is encrypted by DM_B’s public key:DM_A then sends the information to DM_B.
- Step 2: When DM_B receives a message from DM_A at a moment , it first decrypts the message using its private key:Secondly, DM_B verifies the validity of the timestamp:Once the validity of the time has been verified, DM_B uses the “Verify” function in Algorithm 2 to calculate a hash value to verify the message:If the signature verification is valid, DM_B executes the “Deliveryman_DM” function using Algorithm 7 and proceeds with the delivery of the product.
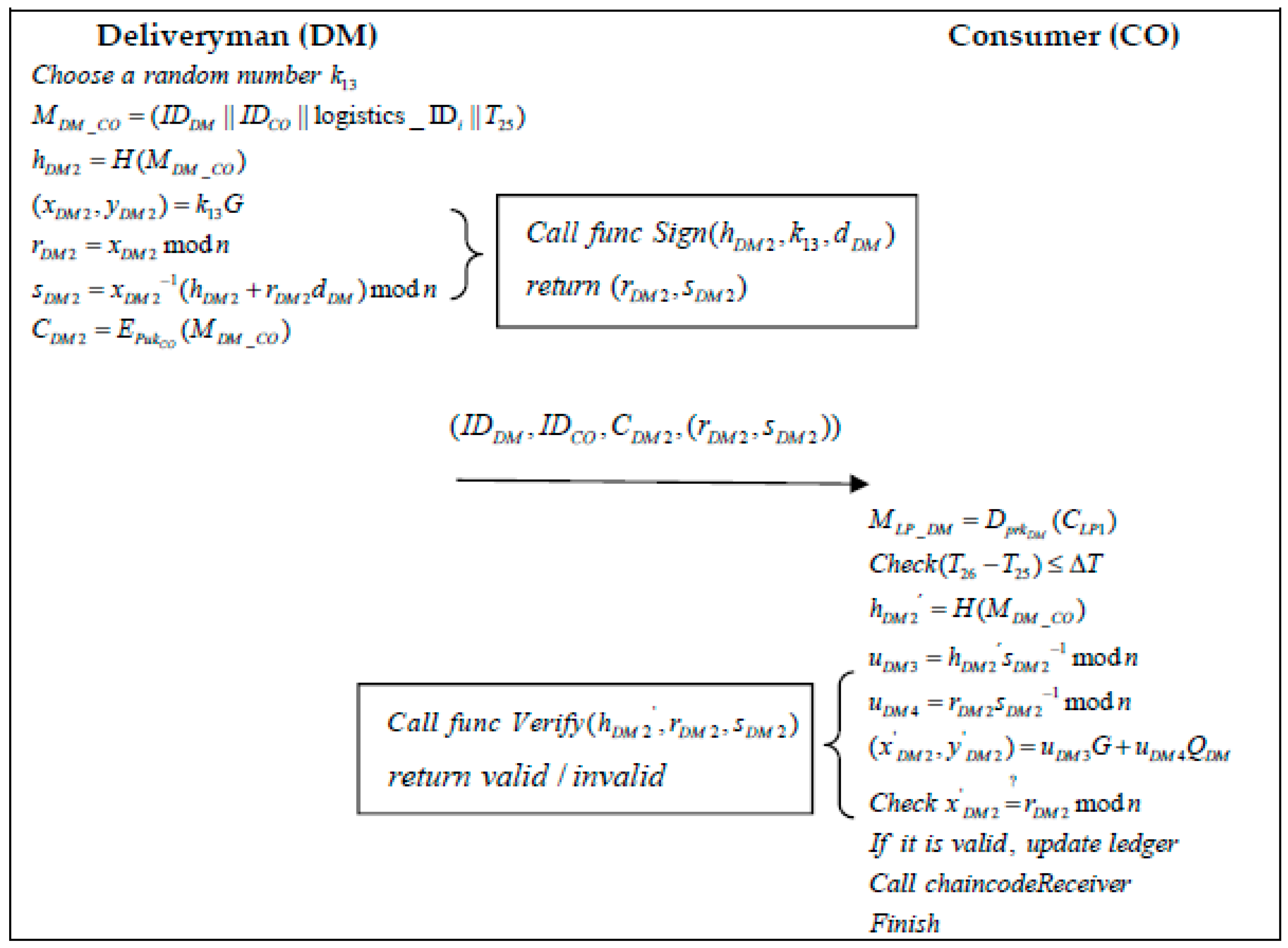
- (b)
- When the DM hands over the product he has delivered to the CO at moment .
- Step 1: The DM randomly selects a number and generates the information related to the logistics order :The DM then calculates the message hash and executes the “Sign” algorithm to generate the signature . The “Sign” algorithm is shown in Algorithm 2:The generated message is encrypted by the CO public key:The DM then sends the information to the CO.
- Step 2: When a CO receives a message from a DM at moment , it first decrypts the message using its private key:Secondly, the CO verifies the validity of the timestamp:Once the validity of the time has been verified, the CO uses the “Verify” function in Algorithm 2 to calculate a hash value to verify the message:If the signature verification is valid, the CO executes the “Receiver” function, the algorithm of which is shown in Algorithm 7, and updates the local ledger with the information to complete the product purchase and logistic distribution phase.
4. Analysis
4.1. Dispersive and Transparent
4.2. Unforgeable, Traceable Data
4.3. Data Integrity
4.4. Non-Repudiation
4.5. Man-in-the-Middle Attack
4.6. Replay Attack
5. Discussion
5.1. Throughput and Latency of Smart Contract Calling
5.2. Resource Utilization
5.3. Computation Cost
5.4. Communication Costs
5.5. Function Comparison
6. Conclusions
- (1).
- Anti-counterfeit traceability management of luxury products using Hyperledger Fabric technology;
- (2).
- ECDSA signature algorithm used to ensure data integrity;
- (3).
- Smart contracts designed in the process of ordering, production, sales, and logistics of luxury products, and relevant information updated in real-time;
- (4).
- Calculation and communication cost analysis;
- (5).
- Consumer or third-party verification of information about the product through the blockchain.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Wang, Y.; Lin, J.; Choi, T.-M. Gray market and counterfeiting in supply chains: A review of the operations literature and implications to luxury industries. Transp. Res. Part E Logist. Transp. Rev. 2020, 133, 101823. [Google Scholar] [CrossRef]
- Dan, A.I.; Ran, W.X.; Hu, D.; Xu, X.; Pan, S.E. Study on Optimization of Anti-counterfeiting Process of Luxury Goods Based on EPC IOT. Logist. Technol. 2012, 31, 4. [Google Scholar]
- Chen, C.-L.; Lim, Z.-Y.; Liao, H.-C.; Deng, Y.-Y.; Chen, P. A Traceable and Verifiable Tobacco Products Logistics System with GPS and RFID Technologies. Appl. Sci. 2021, 11, 4939. [Google Scholar] [CrossRef]
- Deepa, N.; Pham, Q.-V.; Nguyen, D.C.; Bhattacharya, S.; Prabadevi, B.; Gadekallu, T.R.; Maddikunta, P.K.R.; Fang, F.; Pathirana, P.N. A survey on blockchain for big data: Approaches, opportunities, and future directions. Futur. Gener. Comput. Syst. 2022, 131, 209–226. [Google Scholar] [CrossRef]
- Stamatellis, C.; Papadopoulos, P.; Pitropakis, N.; Katsikas, S.; Buchanan, W.J. A Privacy-Preserving Healthcare Framework Using Hyperledger Fabric. Sensors 2020, 20, 6587. [Google Scholar] [CrossRef]
- Chen, C.-L.; Wang, T.; Tsaur, W.-J.; Weng, W.; Deng, Y.-Y.; Cui, J. Based on Consortium Blockchain to Design a Credit Verifiable Cross University Course Learning System. Secur. Commun. Netw. 2021, 2021, 8241801. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 23 September 2022).
- Hyperledger Fabric. Available online: https://wiki.hyperledger.org/display/Fabric (accessed on 1 June 2021).
- Qi, M.; Chen, J.; Chen, Y. A secure biometrics-based authentication key exchange protocol for multi-server TMIS using ECC. Comput. Methods Programs Biomed. 2018, 164, 101–109. [Google Scholar] [CrossRef] [PubMed]
- Puthal, D.; Ranjan, R.; Nanda, A.; Nanda, P.; Jayaraman, P.; Zomaya, A.Y. Secure authentication and load balancing of distributed edge datacenters. J. Parallel Distrib. Comput. 2019, 124, 60–69. [Google Scholar] [CrossRef]
- Mohit, P.; Amin, R.; Biswas, G. Design of authentication protocol for wireless sensor network-based smart vehicular system. Veh. Commun. 2017, 9, 64–71. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumari, S.; Li, X.; Wu, F. Design of an efficient and provably secure anonymity preserving three-factor user authentication and key agreement scheme for TMIS. Secur. Commun. Netw. 2016, 9, 1983–2001. [Google Scholar] [CrossRef]
- Moon, A.H.; Iqbal, U.; Bhat, G.M. Implementation of Node Authentication for WSN Using Hash Chains. Procedia Comput. Sci. 2016, 89, 90–98. [Google Scholar] [CrossRef]
- Internet Says, The Advantages and Disadvantages of RFID The Advantages of Electronic Tag Technology. Available online: https://www.maigoo.com/goomai/153745.html (accessed on 3 May 2022).
- Hochholdinger, S.; Arnoux, M.; Delémont, O.; Esseiva, P. Forensic intelligence on illicit markets: The example of watch counterfeiting. Forensic Sci. Int. 2019, 302, 109868. [Google Scholar] [CrossRef]
- Pérez, J.B.; Queiruga-Dios, A.; Martínez, V.G.; Del Rey, M. Traceability of Ready-to-Wear Clothing through Blockchain Technology. Sustainability 2020, 12, 7491. [Google Scholar] [CrossRef]
- Agrawal, T.K.; Kumar, V.; Pal, R.; Wang, L.; Chen, Y. Blockchain-based framework for supply chain traceability: A case example of textile and clothing industry. Comput. Ind. Eng. 2021, 154, 107130. [Google Scholar] [CrossRef]
- Han, W.; Zhu, Z. An ID-based mutual authentication with key agreement protocol for multiserver environment on elliptic curve cryptosystem. Int. J. Commun. Syst. 2014, 27, 1173–1185. [Google Scholar] [CrossRef]
- Chang, S.E.; Chen, Y.-C.; Lu, M.-F. Supply chain re-engineering using blockchain technology: A case of smart contract based tracking process. Technol. Forecast. Soc. Chang. 2019, 144, 1–11. [Google Scholar] [CrossRef]
- Crosby, M.; Pattanayak, P.; Verma, S.; Kalyanaraman, V. Blockchain technology: Beyond bitcoin. Appl. Innov. 2016, 2, 71. [Google Scholar]
- Chen, C.L.; Deng, Y.Y.; Li, C.T.; Zhu, S.; Chiu, Y.J.; Chen, P.Z. An IoT-based traceable drug anti-counterfeiting management system. IEEE Access 2020, 8, 224532–224548. [Google Scholar] [CrossRef]
- Schmidt, C.G.; Wagner, S.M. Blockchain and supply chain relations: A transaction cost theory perspective. J. Purch. Supply Manag. 2019, 25, 100552. [Google Scholar] [CrossRef]
- Androulaki, E.; Cachin, C.; De Caro, A.; Sorniotti, A.; Vukolic, M. Permissioned blockchains and hyperledger fabric. Ercim News 2017, 110, 9–10. [Google Scholar]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, G.; et al. Hyperledger fabric: A distributed operating system for permissioned blockchains. In Proceedings of the 13th EuroSys Conference, Porto, Portugal, 23–26 April 2018; ACM: New York, NY, USA, 2018; pp. 1–15. [Google Scholar]
- Nasir, Q.; Qasse, I.A.; Abu Talib, M.; Nassif, A.B. Performance Analysis of Hyperledger Fabric Platforms. Secur. Commun. Netw. 2018, 2018, 3976093. [Google Scholar] [CrossRef]
- A Blockchain Platform for the Enterprise-Hyperledger Fabric. Available online: https://hyperledger-fabric.readthedocs.io/en/release-2.2 (accessed on 23 September 2022).




| Authors | Year | Objective | Technologies | Merits | Demerits |
|---|---|---|---|---|---|
| Dan et al. [2] | 2012 | Proposed a luxury anti-counterfeiting system architecture and hierarchy based on the EPC Internet of Things (IoT) | EPC and IoT | Proposed a system architecture that can meet the demand for luxury anti-counterfeiting | Encryption and decryption methods are not specific enough and need to be improved |
| Hochholdinger et al. [15] | 2019 | Marks or traces, from a forensic intelligence perspective, can achieve a watch anti-counterfeiting effect | Link Analysis and Chemical and Physical Profiling | Revealed the links between watches that were unknown or uncertain and demonstrated the interconnection of all watches on a chemical and physical level | Specialized personnel are required to conduct the identification operation, and the marks produced are sporadic and unstable |
| Perez et al. [16] | 2020 | Introduced the latest traceability program and recommended a framework for garments | Blockchain and Hash Functions | Ensures the authenticity, reliability, and integrity of clothing while ensuring the transparency of the supply chain | The specific process for garment production was not presented |
| Kumar et al. [17] | 2021 | Investigated and proposed a blockchain-based traceability framework for traceability in a multi-tier T&C supply chain | Blockchain and Smart Contract | A framework combining the blockchain and supply chain was proposed | The specific flow of data was not reflected |
| Symbol | Description |
|---|---|
| User identification | |
| Identification of the i-th product of the BP | |
| Identification of the i-th product order | |
| Identification of the i-th logistics order | |
| A collection of N product representations | |
| A collection of N product order representations | |
| A collection of N logistics order representations | |
| Elliptic curves defined on a finite group | |
| A generated point based on an elliptic curve E | |
| i-th random value on the elliptic curve | |
| Private key for user X | |
| Public key for user X | |
| Elliptic curve eigenvalues of X | |
| ECDSA signature value for X | |
| Encryption of message M using the public key of user x | |
| Decryption of message M using the private key of user x | |
| One-way hash function for message M | |
| i-th hash value of X | |
| i-th timestamp | |
| Threshold for checking the validity of timestamps | |
| Information from the BP (product information) | |
| Information from the BP (product orders) | |
| Message is sent from X to Y | |
| Information from MS (type of raw material, content, source, etc.) | |
| Verify if A1 is equal to A2 |
| Phase | Party | Message | Hash Value | Verification | |
|---|---|---|---|---|---|
| Sender | Receiver | ||||
| Product Design and Development Phase | BP | PM | |||
| PM | MS | ||||
| MS | PM | ||||
| Product Evaluation and Approval Phase | PM | BP | |||
| BP | PM | ||||
| Product Ordering and Production Phase | PD | BP | |||
| BP | PM | ||||
| PM | MS | ||||
| MS | PM | ||||
| Product Purchase and Logistics Distribution Phase | PD | LP | |||
| LP | DM | ||||
| DM_A | DM_B | ||||
| DM | CO | ||||
| Phase | Party | Signature | Verification | |
|---|---|---|---|---|
| Sender | Receiver | |||
| Product Design and Development Phase | BP | PM | ||
| PM | MS | |||
| MS | PM | |||
| Product Evaluation and Approval Phase | PM | BP | ||
| BP | PM | |||
| Product Ordering and Production Phase | PD | BP | ||
| BP | PM | |||
| PM | MS | |||
| MS | PM | |||
| Product Purchase and Logistics Distribution Phase | PD | LP | ||
| LP | DM | |||
| DM_A | DM_B | |||
| DM | CO | |||
| Phase | Party | Encryption | Decryption | |
|---|---|---|---|---|
| Sender | Receiver | |||
| Product Design and Development Phase | BP | PM | ||
| PM | MS | |||
| MS | PM | |||
| Product Evaluation and Approval Phase | PM | BP | ||
| BP | PM | |||
| Product Ordering and Production Phase | PD | BP | ||
| BP | PM | |||
| PM | MS | |||
| MS | PM | |||
| Product Purchase and Logistics Distribution Phase | PD | LP | ||
| LP | DM | |||
| DM_A | DM_B | |||
| DM | CO | |||
| Phase | Party | Sent Time | Received Time | Validation | |
|---|---|---|---|---|---|
| Sender | Receiver | ||||
| Product Design and Development Phase | BP | PM | |||
| PM | MS | ||||
| MS | PM | ||||
| Product Evaluation and Approval Phase | PM | BP | |||
| BP | PM | ||||
| Product Ordering and Production Phase | PD | BP | |||
| BP | PM | ||||
| PM | MS | ||||
| MS | PM | ||||
| Product Purchase and Logistics Distribution Phase | PD | LP | |||
| LP | DM | ||||
| DM_A | DM_B | ||||
| DM | CO | ||||
| Configuration | Detail |
|---|---|
| CPU | Intel(R) Core(TM) i5-8300H CPU@2.30 GHz |
| Memory | 8 G |
| Network | 4 Gbit/s |
| SSD | 60 GB |
| Name | Succ | Fail | Send Rate (TPS) | Max Latency (s) | Min Latency (s) | Avg Latency (s) | Throughput (TPS) |
|---|---|---|---|---|---|---|---|
| test Product Design and Development Phase_100 | 492 | 1 | 98.5 | 2.70 | 0.28 | 0.82 | 64.8 |
| test Product Evaluation and Approval Phase_100 | 983 | 1 | 192.3 | 7.27 | 0.74 | 4.00 | 95.6 |
| test Product Ordering and Production Phase_100 | 976 | 1 | 195.4 | 7.79 | 0.34 | 4.03 | 96.2 |
| test Product Purchase and Logistics Distribution Phase_100 | 994 | 0 | 197.9 | 8.45 | 0.20 | 3.10 | 102.6 |
| Name | CPU% (max) | CPU% (avg) | Memory(max) [MB] | Memory(avg)[MB] | Traffic In [MB] | Traffic Out [MB] | Disc Wirte [MB] | Disc Read [MB] |
|---|---|---|---|---|---|---|---|---|
| dev-peer0.org1.example.com-alcohol-supply-contract_1.0-035019925cd56f13a2148f77f6a81fe7d139997b666c1264978d0b99d97bd8d0 | 6.80 | 1.83 | 17.1 | 17.1 | 1.32 | 0.566 | 0.00 | 0.00 |
| dev-peer0.org2.example.com-alcohol-supply-contract_1.0-035019925cd56f13a2148f77f6a81fe7d139997b666c1264978d0b99d97bd8d0 | 5.79 | 1.61 | 17.0 | 17.0 | 1.29 | 0.527 | 0.00 | 0.00 |
| cli | 0.00 | 0.00 | 15.2 | 15.2 | 0.00 | 0.00 | 0.00 | 0.00 |
| Peer0.org1.example.com | 24.06 | 9.61 | 123 | 122 | 4.04 | 2.36 | 3.89 | 0.00 |
| orderer.example.com | 12.75 | 4.48 | 110 | 109 | 2.57 | 5.13 | 5.53 | 0.00 |
| Peer0.org2.example.com | 22.40 | 8.88 | 146 | 145 | 3.98 | 2.24 | 3.89 | 0.00 |
| Phase | Participant 1 | Participant 2 | Participant 3 | Participant 4 |
|---|---|---|---|---|
| Product Design and Development Phase | BP: | PM: | MS: | N/A |
| Product Evaluation and Approval Phase | PM: | BP: | N/A | N/A |
| Product Ordering and Production Phase | PD: | BP: | PM: | MS: |
| Product Purchase and Logistics Distribution Phase | PD: | LP: | DM: | CO: |
| Phase | Message Length | 3.5 G (14 Mpbs) | 4 G (100 Mpbs) | 5 G (20 Gpbs) |
|---|---|---|---|---|
| Product Design and Development Phase | 4032 bits | 0.288 ms | 0.040 ms | 0.202 μs |
| Product Evaluation and Approval Phase | 2688 bits | 0.192 ms | 0.027 ms | 0.134 μs |
| Product Ordering and Production Phase | 5376 bits | 0.384 ms | 0.054 ms | 0.269 μs |
| Product Purchase and Logistics Distribution Phase | 5376 bits | 0.384 ms | 0.054 ms | 0.269 μs |
| Authors | Year | Objective | 1 | 2 | 3 | 4 | 5 | 6 |
|---|---|---|---|---|---|---|---|---|
| Dan et al. [2] | 2012 | Proposed a luxury anti-counterfeiting system architecture and hierarchy based on the EPC Internet of Things (IoT) | N | Y | Y | Y | N | Y |
| Hochholdinger et al. [15] | 2019 | Marks or traces, from a forensic intelligence perspective, can achieve a watch anti-counterfeiting effect | N | N | N | N | N | Y |
| Perez et al. [16] | 2020 | Introduced the latest traceability program and recommended a framework for garments | Y | Y | N | N | Y | Y |
| Agrawal et al. [17] | 2021 | Investigated and proposed a blockchain-based traceability framework for traceability in a multi-tier T&C supply chain | Y | N | Y | N | Y | Y |
| Our proposed method | 2022 | Proposed a blockchain-based framework for product traceability and documentation of logistics processes | Y | Y | Y | Y | Y | Y |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, C.-L.; Guo, L.-H.; Zhou, M.; Tsaur, W.-J.; Sun, H.; Zhan, W.; Deng, Y.-Y.; Li, C.-T. Blockchain-Based Anti-Counterfeiting Management System for Traceable Luxury Products. Sustainability 2022, 14, 12814. https://doi.org/10.3390/su141912814
Chen C-L, Guo L-H, Zhou M, Tsaur W-J, Sun H, Zhan W, Deng Y-Y, Li C-T. Blockchain-Based Anti-Counterfeiting Management System for Traceable Luxury Products. Sustainability. 2022; 14(19):12814. https://doi.org/10.3390/su141912814
Chicago/Turabian StyleChen, Chin-Ling, Long-Hui Guo, Ming Zhou, Woei-Jiunn Tsaur, Hongyu Sun, Wanbing Zhan, Yong-Yuan Deng, and Chun-Ta Li. 2022. "Blockchain-Based Anti-Counterfeiting Management System for Traceable Luxury Products" Sustainability 14, no. 19: 12814. https://doi.org/10.3390/su141912814
APA StyleChen, C.-L., Guo, L.-H., Zhou, M., Tsaur, W.-J., Sun, H., Zhan, W., Deng, Y.-Y., & Li, C.-T. (2022). Blockchain-Based Anti-Counterfeiting Management System for Traceable Luxury Products. Sustainability, 14(19), 12814. https://doi.org/10.3390/su141912814








