Security Issues and Solutions for Connected and Autonomous Vehicles in a Sustainable City: A Survey
Abstract
1. Introduction
- (1)
- A summary of the security issues and solutions for AVs associated with different sensors, controllers, and in-vehicle networks.
- (2)
- An investigation of the connectivity technologies of CVs and analysis of their advantages and applications in CAVs, as well as identifying the security issues of each type.
- (3)
- An analysis of the impact of cyber-attacks on CAVs: cyber-attacks on intra-vehicle systems to impact the individual CAVs and cyber-attacks on vehicle connectivity to impact the cooperative CAV.
- (4)
- Proposed future directions to enhance the CAV security.
2. Security Issues Facing AVs and Solutions
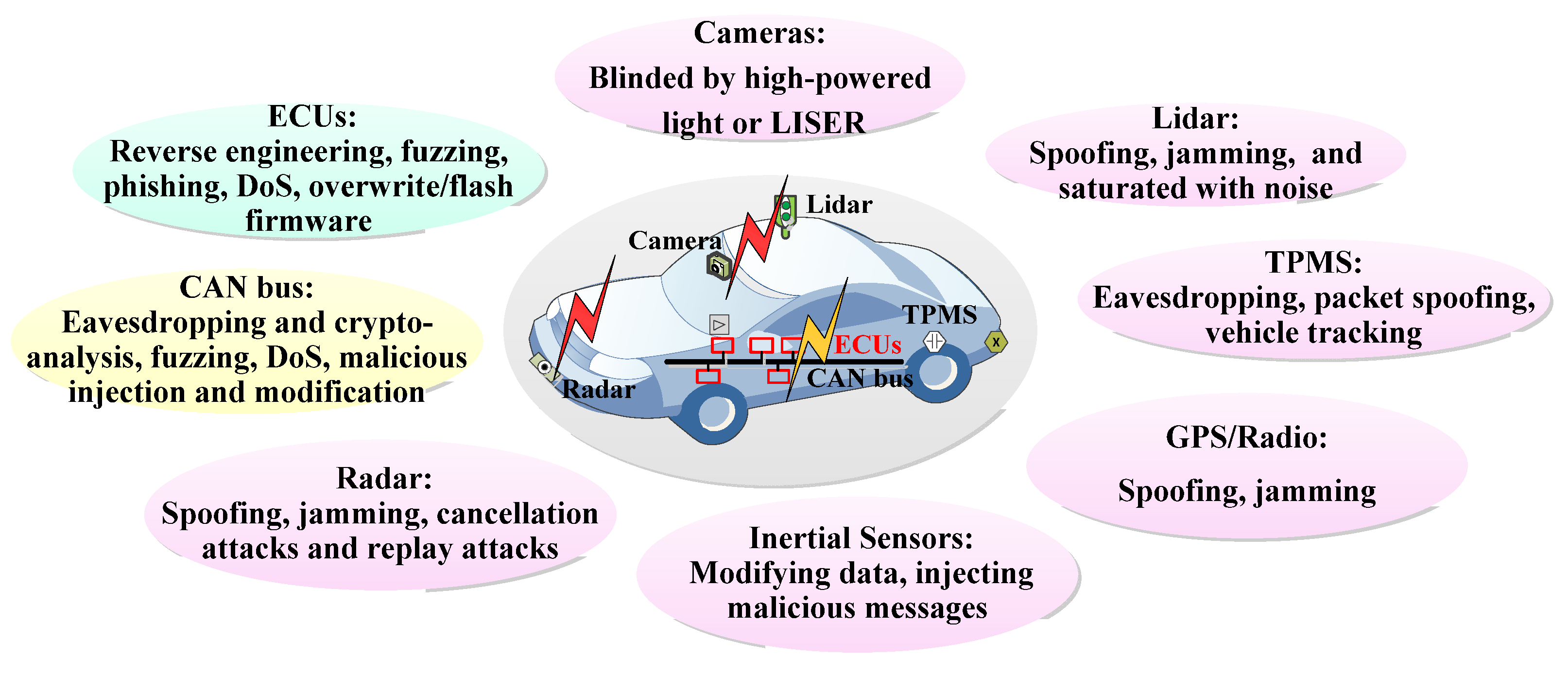
2.1. Sensors
| Type | Application | Security Issues | Solutions | References |
|---|---|---|---|---|
| Camera | Interprets objects/signs. An array of cameras to provide 360 views, while stereo-cameras can extract extra depth information. | Extra light from other sources may decrease the sensitivity of the sensors; intense light (e.g., laser, IR LEDs) can directly blind/blaze the sensors. |
| [4,5,9,10,14,15,16,17] |
| Lidar, radar, and ultrasonic | Lidar provides a “3D” map of the surrounding environment and depth perception. Radar detects obstacles and measures distances in bad weather conditions/low light situations. Ultrasonic assists short-range detection. | Spoofing, jamming, saturation, cancellation attacks, and replay attacks. |
| [4,5,9,18,19,20] |
| GPS | Provides real-time position data of the vehicle through the connection with multiple satellites. | Spoofing, jamming. |
| [11,21,22] |
| TPMS | Measures the pressure of each tire and provides real-time information to the vehicle system. | Eavesdropping, packet spoofing, vehicle tracking, message forgery. |
| [12,23] |
| Inertial measurement units | Includes gyroscopes, accelerometers, etc., to provide velocity, acceleration, and orientation data to the control system. | Data modification and injection attacks, DoS. Typically, attacks need physical access to the sensor to interfere with its readings, or alternatively to intercept communication between the sensor and control unit. |
| [2,5,13,18] |
| Engine control sensor | Includes temperature, air flow sensors, etc., to acquire performance data to adjust engine conditions. |
2.2. In-Vehicle Network
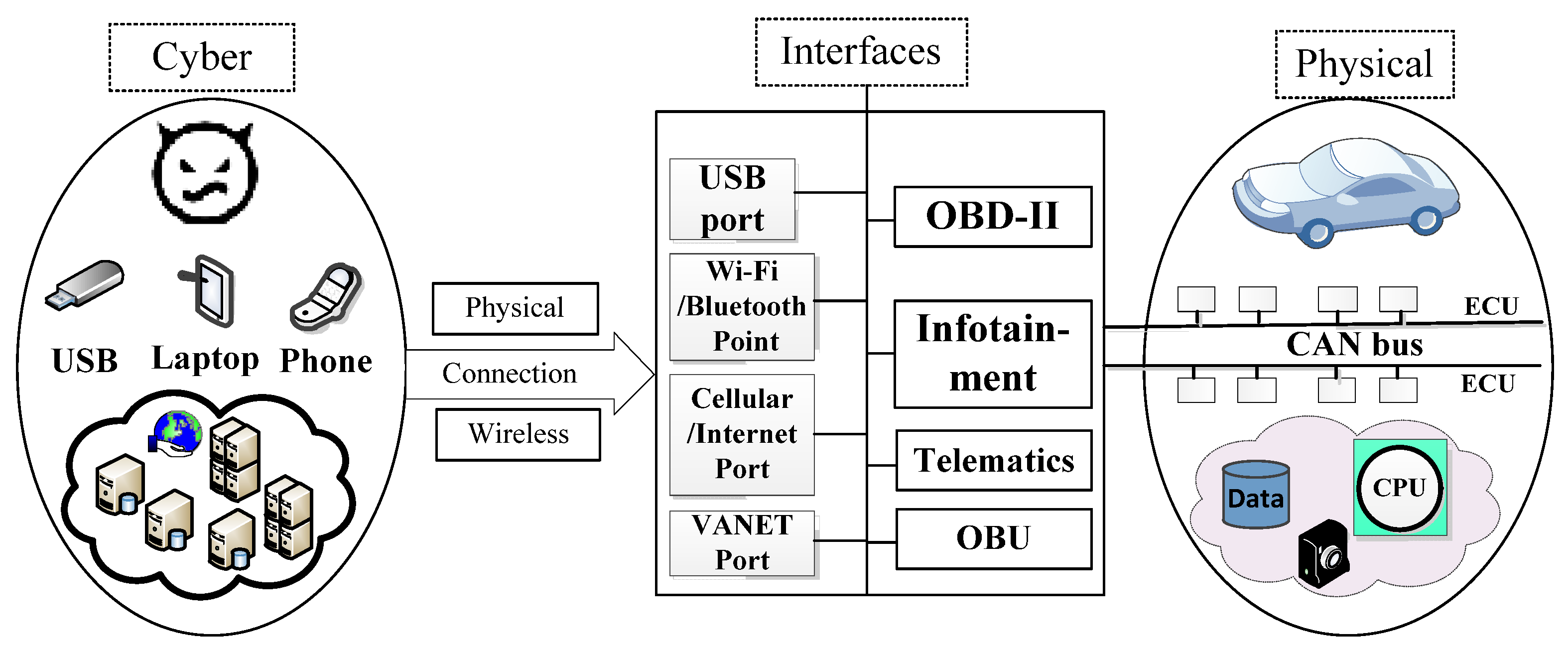
2.3. Electronic Control Unit (ECU)
3. Security Issues Facing CVs and Solutions
3.1. Bluetooth
3.2. Wi-Fi
3.3. Cellular Network
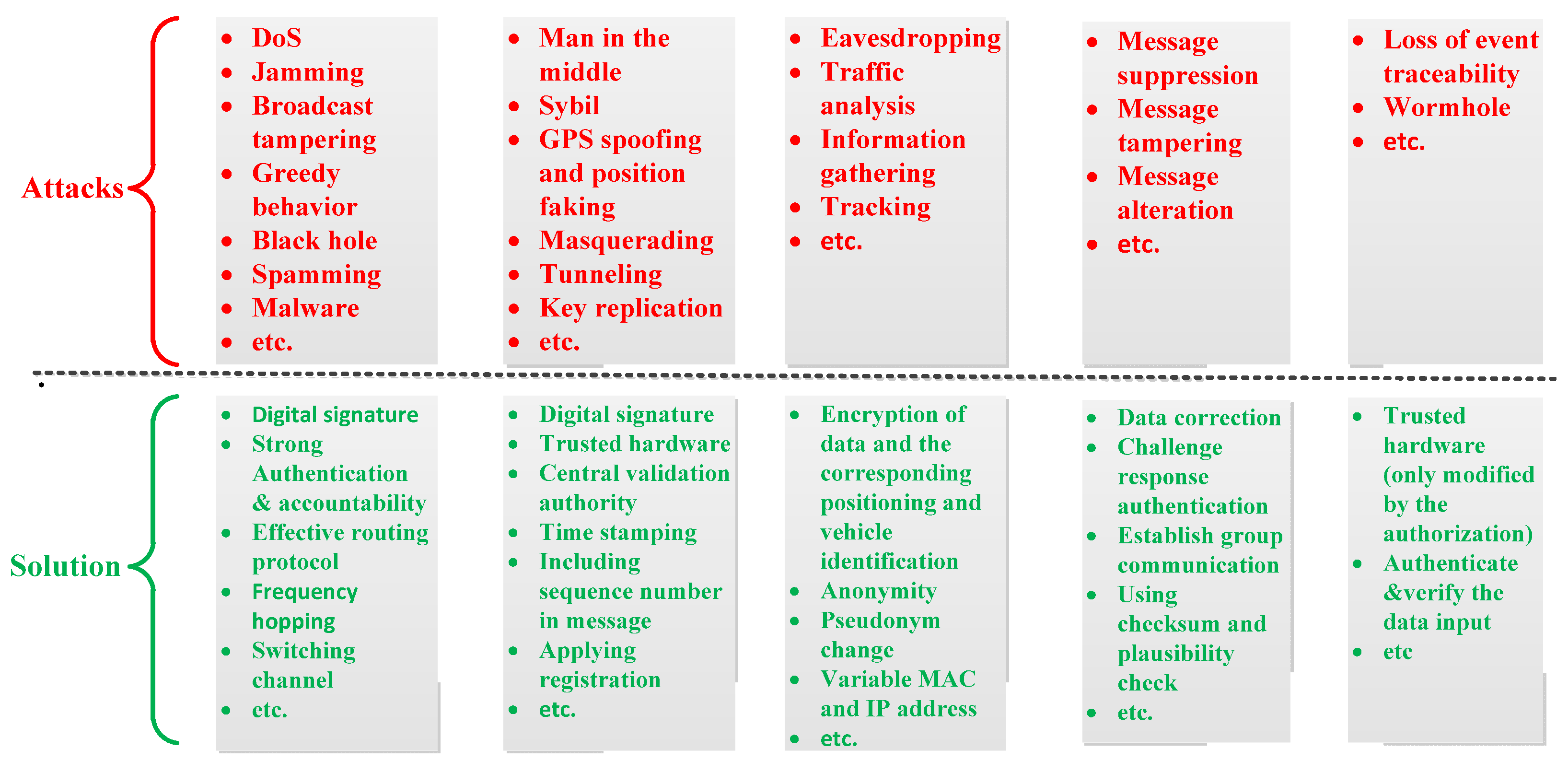
3.4. VANET
3.4.1. Efficient Authentication with Privacy Preservation and Key Management in Group Signature
3.4.2. Privacy Protection and Effective Pseudonym Change Strategy
3.4.3. Trust Management and Enhancement
3.4.4. RSU Assisted Security and RSU Power Abuse
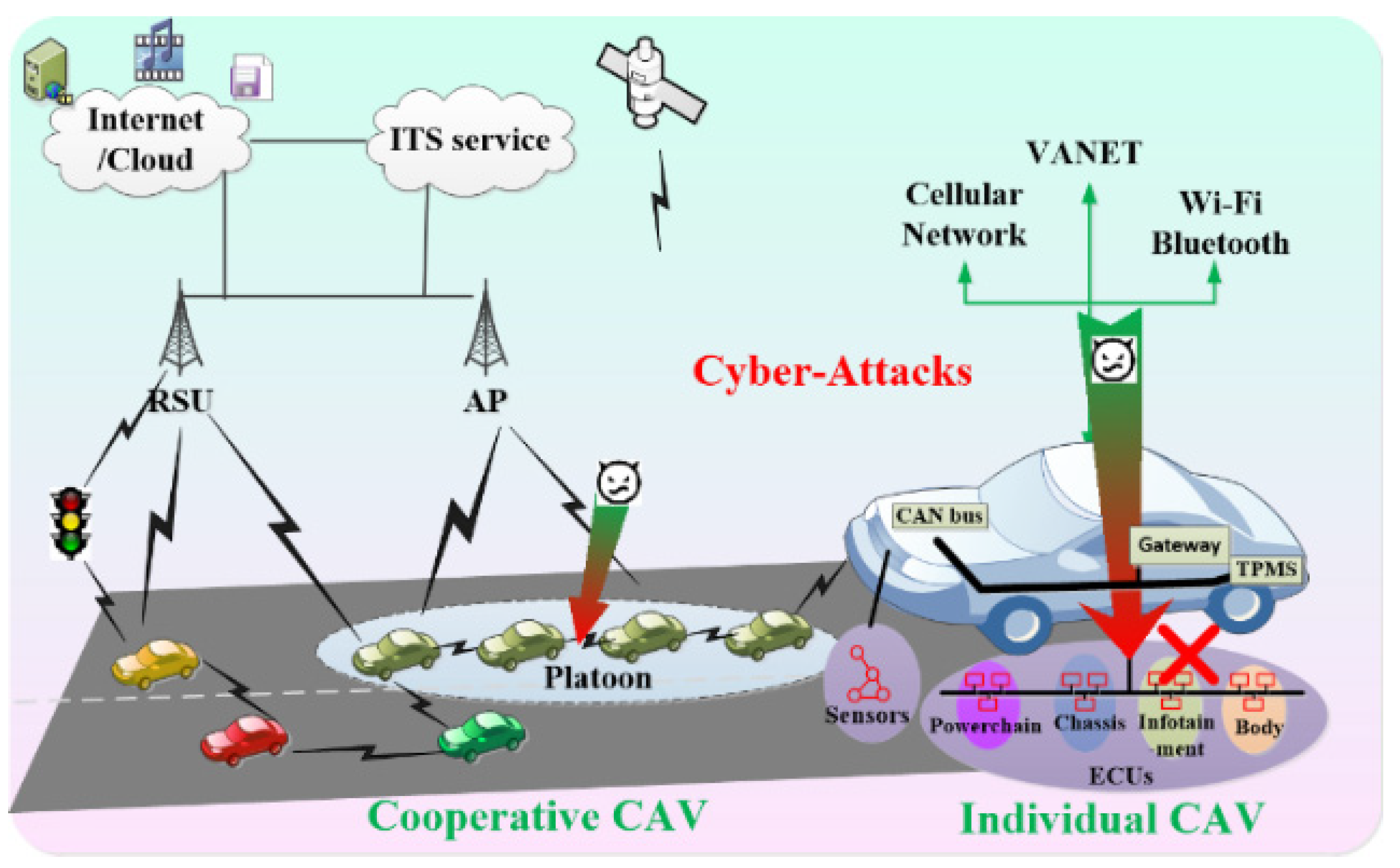
4. Security Issues and Solutions for CAVs
4.1. Cyber-Attacks on Intra-Vehicle Systems
4.1.1. Models of the Attacks
4.1.2. Attack Impacts on Intra-Vehicle Systems
4.1.3. Open Issues of Intra-Vehicle System Security
4.2. Cyber-Attacks on Inter-Vehicle Systems
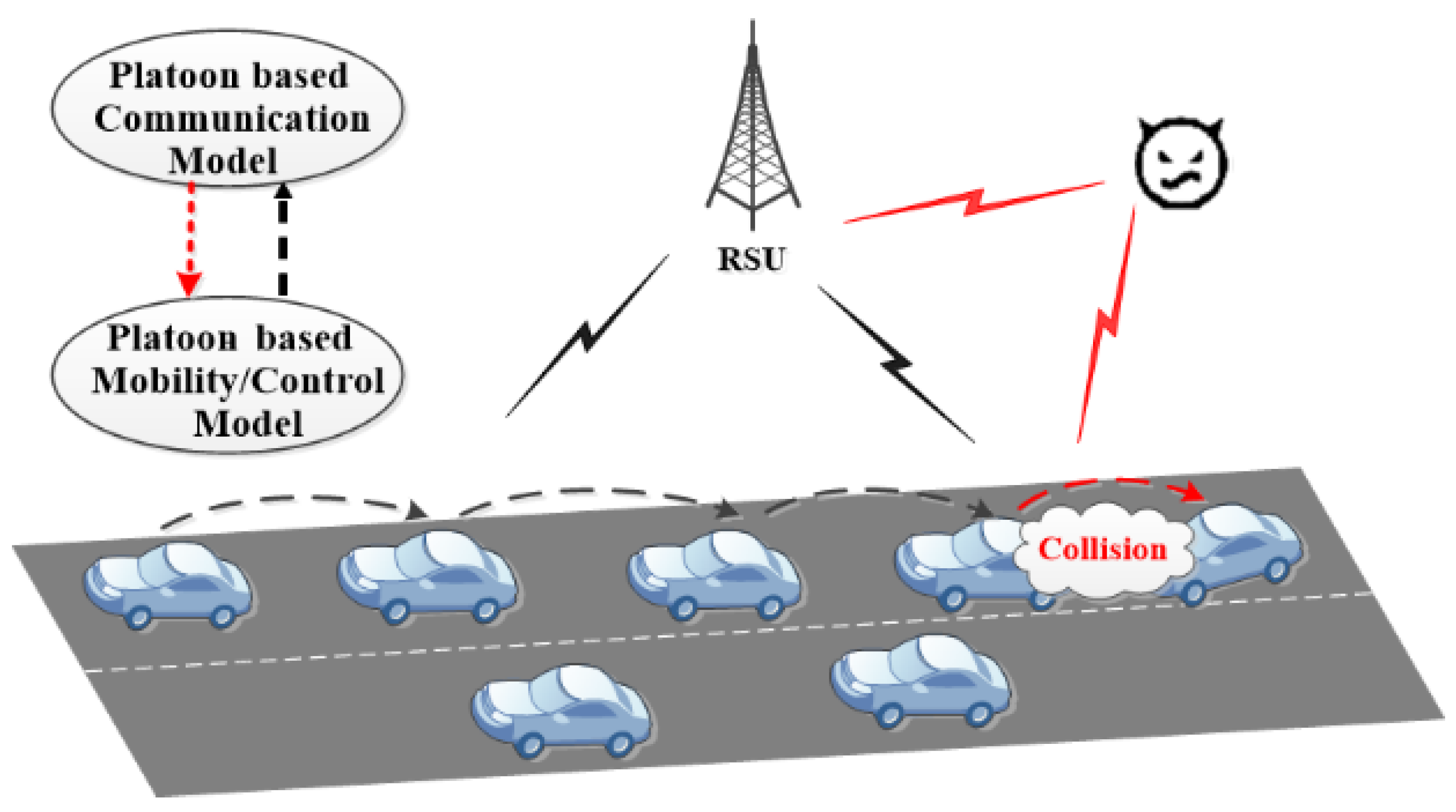
4.2.1. Models of Attacks on Platoon
4.2.2. Diverse Types of Cyber-Attacks
4.2.3. Open Issues of Inter-Vehicle System Security
5. Discussion and Future Works
5.1. Secure the Perception and Operation of CAVs
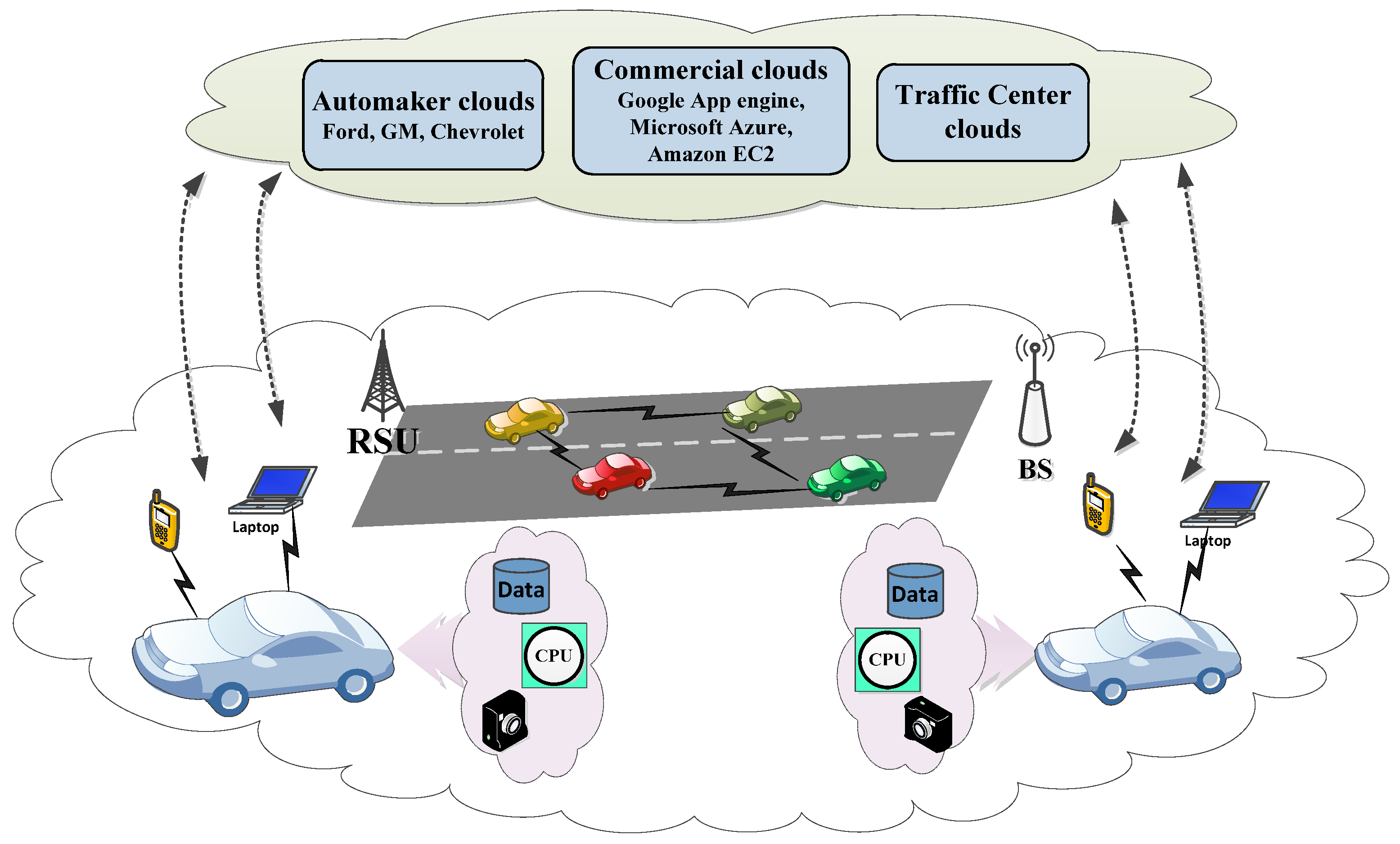
5.2. CAV Integrated with the Cloud
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- NHTSA. SAE Define 5 Levels of Vehicle Automation. Available online: https://www.sema.org/sema-enews/2017/11/ettn-tech-alert-nhtsa-sae-define-5-levels-of-vehicle-automation (accessed on 19 May 2022).
- Koscher, K.; Czeskis, A.; Roesner, F.; Patel, S.; Kohno, T.; Checkoway, S.; McCoy, D.; Kantor, B.; Anderson, D.; Shacham, H.; et al. Experimental Security Analysis of a Modern Automobile. In Proceedings of the 2010 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 16–19 May 2010; pp. 447–462. [Google Scholar]
- Chris, V.; Charlie, M. Remote Exploitation of an Unaltered Passenger Vehicle. White Paper. 2015; p. 93. Available online: https://illmatics.com/Remote%20Car%20Hacking.pdf (accessed on 8 August 2022).
- Petit, J.; Shladover, S.E. Potential cyberattacks on automated vehicles. IEEE Trans. Intell. Transp. Syst. 2015, 16, 546–556. [Google Scholar] [CrossRef]
- Parkinson, S.; Ward, P.; Wilson, K.; Miller, J. Cyber Threats Facing Autonomous and Connected Vehicles: Future Challenges. IEEE Trans. Intell. Transp. Syst. 2017, 18, 2898–2915. [Google Scholar] [CrossRef]
- Checkoway, S.; McCoy, D.; Kantor, B.; Anderson, D.; Shacham, H.; Savage, S.; Koscher, K.; Czeskis, A.; Roesner, F.; Kohno, T. Comprehensive Experimental Analyses of Automotive Attack Surfaces. In Proceedings of the USENIX Security Symposium, San Francisco, CA, USA, 8–12 August 2011. [Google Scholar]
- Quy, V.K.; Nam, V.H.; Linh, D.M.; Ban, N.T.; Han, N.D. Communication Solutions for Vehicle Ad-hoc Network in Smart Cities Environment: A Comprehensive Survey. Wirel. Pers. Commun. 2022, 122, 2791–2815. [Google Scholar] [CrossRef]
- Zhang, K.; Ni, J.; Yang, K.; Liang, X.; Ren, J.; Shen, X.S. Security and privacy in smart city applications: Challenges and solutions. IEEE Commun. Mag. 2017, 55, 122–129. [Google Scholar] [CrossRef]
- Péter, G.; Kiss, B.; Tihanyi, V. Vision and odometry based autonomous vehicle lane changing. ICT Express 2019, 5, 219–226. [Google Scholar] [CrossRef]
- Zablocki, É.; Ben-Younes, H.; Pérez, P.; Cord, M. Explainability of vision-based autonomous driving systems: Review and challenges. arXiv 2021, arXiv:2101.05307. [Google Scholar] [CrossRef]
- Zhang, F.; Wang, Z.; Zhong, Y.; Chen, L. Localization Error Modeling for Autonomous Driving in GPS Denied Environment. Electronics 2022, 11, 647. [Google Scholar] [CrossRef]
- Yang, S.; Chen, Y.; Shi, R.; Wang, R.; Cao, Y.; Lu, J. A Survey of Intelligent Tires for Tire-road Interaction Recognition. IEEE Trans. Intell. Veh. 2022. [Google Scholar] [CrossRef]
- Liu, Z.; Wang, L.; Wen, F.; Zhang, H. IMU/vehicle calibration and integrated localization for autonomous driving. In Proceedings of the 2021 IEEE International Conference on Robotics and Automation (ICRA), Xi’an, China, 30 May–5 June 2021; pp. 4013–4019. [Google Scholar]
- Understanding the Fatal Tesla Accident on Autopilot and the NHTSA Probe. Available online: https://electrek.co/2016/07/01/understanding-fatal-tesla-accident-autopilot-nhtsa-probe/ (accessed on 8 August 2022).
- Mahajan, S.; Bhosale, R.; Kulkarni, P. Obstacle detection using mono vision camera and laser scanner. Int. J. Res. Eng. Technol. 2013, 2, 684–690. [Google Scholar]
- Du, J.; Masters, J.; Barth, M. Lane-level positioning for in-vehicle navigation and automated vehicle location (AVL) systems. In Proceedings of the 7th International IEEE Conference on Intelligent Transportation Systems, Washington, WA, USA, 3–9 October 2004; pp. 35–40. [Google Scholar]
- Grisleri, P.; Fedriga, I. The braive autonomous ground vehicle platform. IFAC Proc. 2010, 43, 497–502. [Google Scholar] [CrossRef]
- Petit, J. Automated Vehicles Vulnerabilities. In Proceedings of the ESCAR USA, Detroit, MI, USA, 1–2 June 2016. [Google Scholar]
- Stottelaar, B.G. Practical Cyber-Attacks on Autonomous Vehicles; University of Twente: Enschede, The Netherlands, 2015. [Google Scholar]
- Lu, G.; Zeng, D.; Tang, B. Anti-jamming filtering for DRFM repeat jammer based on stretch processing. In Proceedings of the 2010 2nd International Conference on Signal Processing Systems (ICSPS), Kuala Lumpur, Malaysia, 7–10 May 2010; Volume 1, pp. V1-78–V1-82. [Google Scholar]
- Cui, Y.; Ge, S.S. Autonomous vehicle positioning with GPS in urban canyon environments. IEEE Trans. Robot. Autom. 2003, 19, 15–25. [Google Scholar]
- Tippenhauer, N.O.; Pöpper, C.; Rasmussen, K.B.; Capkun, S. On the requirements for successful GPS spoofing attacks. In Proceedings of the 18th ACM Conference on Computer and Communications Security, Chicago, IL, USA, 17–21 October 2011; pp. 75–86. [Google Scholar]
- Rouf, I.; Miller, R.; Mustafa, H.; Taylor, T.; Oh, S.; Xu, W.; Gruteser, M.; Trappe, W.; Seskar, I. Security and privacy vulnerabilities of in-car wireless networks: A tire pressure monitoring system case study. In Proceedings of the 19th USENIX Security Symposium, Washington, DC, USA, 11–13 August 2010; pp. 11–13. [Google Scholar]
- Wolf, M.; Weimerskirch, A.; Paar, C. Security in automotive bus systems. In Proceedings of the Workshop on Embedded Security in Cars, Bochum, Germany, 11–12 November 2004. [Google Scholar]
- Wolf, M.; Weimerskirch, A.; Wollinger, T. State of the art: Embedding security in vehicles. EURASIP J. Embed. Syst. 2007, 2007, 074706. [Google Scholar] [CrossRef]
- Jafarnejad, S.; Codeca, L.; Bronzi, W.; Frank, R.; Engel, T. A car hacking experiment: When connectivity meets vulnerability. In Proceedings of the 2015 IEEE Globecom Workshops (GC Wkshps), San Diego, CA, USA, 6–10 December 2015; pp. 1–6. [Google Scholar]
- Woo, S.; Jo, H.J.; Lee, D.H. A practical wireless attack on the connected car and security protocol for in-vehicle CAN. IEEE Trans. Intell. Transp. Syst. 2015, 16, 993–1006. [Google Scholar] [CrossRef]
- Vanhoef, M.; Piessens, F. Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2. In Proceedings of the CCS’17: 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 30 October–3 November 2017. [Google Scholar]
- Huang, J.-L.; Yeh, L.-Y.; Chien, H.-Y. ABAKA: An anonymous batch authenticated and key agreement scheme for value-added services in vehicular ad hoc networks. IEEE Trans. Veh. Technol. 2011, 60, 248–262. [Google Scholar] [CrossRef]
- An Analysis and Comparison of Hardware Security Modules for the Automotive Domain. Available online: https://www.escar.info/images/Datastore/2014_escar_Vortraege_USA/Frederic_Stumpf_escar_USA_2014.pdf (accessed on 8 August 2022).
- Studnia, I.; Nicomette, V.; Alata, E.; Deswarte, Y.; Kaâniche, M.; Laarouchi, Y. Survey on security threats and protection mechanisms in embedded automotive networks. In Proceedings of the 2013 43rd Annual IEEE/IFIP Conference on Dependable Systems and Networks Workshop (DSN-W), Washington, DC, USA, 24–27 June 2013; pp. 1–12. [Google Scholar]
- Valasek, C.; Miller, C. A Survey of Remote Automotive Attack Surfaces; Scribd: Washington, DC, USA, 2014. [Google Scholar]
- Nilsson, D.; Larson, U.; Jonsson, E. Creating a secure infrastructure for wireless diagnostics and software updates in vehicles. In Proceedings of the SAFECOMP 2008, Newcastle upon Tyne, UK, 22–25 September 2008; pp. 207–220. [Google Scholar]
- Nilsson, D.K.; Larson, U. A Defense-in-Depth Approach to Securing the Wireless Vehicle Infrastructure. JNW 2009, 4, 552–564. [Google Scholar] [CrossRef]
- Qualcomm. Expanding and Evolving the Cellular System for V2X Communications—Introduced in 3GPP Release 14—Part of LTE Advanced Pro; Qualcomm Technologies: San Diego, CA, USA, 2016. [Google Scholar]
- Sawant, H.; Tan, J.; Yang, Q.; Wang, Q. Using Bluetooth and sensor networks for intelligent transportation systems. In Proceedings of the IEEE intelligent Transportation Systems Conference, Washington, DC, USA, 3–6 October 2004. [Google Scholar]
- Dardanelli, A.; Maggi, F.; Tanelli, M.; Zanero, S.; Savaresi, S.M.; Kochanek, R.; Holz, T. A security layer for smartphone-to-vehicle communication over Bluetooth. IEEE Embed. Syst. Lett. 2013, 5, 34–37. [Google Scholar] [CrossRef]
- Humayed, A.; Lin, J.; Li, F.; Luo, B. Cyber-Physical Systems Security--A Survey. IEEE Internet Things J. 2017, 4, 1802–1831. [Google Scholar] [CrossRef]
- Han, K.; Potluri, S.D.; Shin, K.G. On authentication in a connected vehicle: Secure integration of mobile devices with vehicular networks. In Proceedings of the 2013 ACM/IEEE International Conference on Cyber-Physical Systems (ICCPS), Philadelphia, PA, USA, 8–11 August 2013; pp. 160–169. [Google Scholar]
- Spill, D.; Bittau, A. BlueSniff: Eve Meets Alice and Bluetooth. WOOT 2007, 7, 1–10. [Google Scholar]
- Haataja, K. Security Threats and Countermeasures in Bluetooth-Enabled Systems. Ph.D. Thesis, University of Kuopio, Kuopio, Finland, 2009. [Google Scholar]
- Rhoades, B.B.; Conrad, J.M. A survey of alternate methods and implementations of an intelligent transportation system. In Proceedings of the SoutheastCon, Charlotte, NC, USA, 30 March–2 April 2017; pp. 1–8. [Google Scholar]
- Chou, C.-M.; Li, C.-Y.; Chien, W.-M.; Lan, K.-C. A feasibility study on vehicle-to-infrastructure communication: WiFi vs. WiMAX. In Proceedings of the 2009 Tenth International Conference on Mobile Data Management: Systems, Services and Middleware, Taipei, Taiwan, 18–20 May 2009; pp. 397–398. [Google Scholar]
- Jeong, S.; Baek, Y.; Son, S.H. A Hybrid V2X System for Safety-Critical Applications in VANET. In Proceedings of the 2016 IEEE 4th International Conference on Cyber-Physical Systems, Networks, and Applications (CPSNA), Nagoya, Japan, 6–7 October 2016; pp. 13–18. [Google Scholar]
- Su, K.-C.; Wu, H.-M.; Chang, W.-L.; Chou, Y.-H. Vehicle-to-vehicle communication system through Wi-Fi network using android smartphone. In Proceedings of the 2012 International Conference on Connected Vehicles and Expo (ICCVE), Beijing, China, 12–16 December 2012; pp. 191–196. [Google Scholar]
- Viittala, H.; Soderi, S.; Saloranta, J.; Hamalainen, M.; Iinatti, J. An experimental evaluation of wifi-based vehicle-to-vehicle (V2V) communication in a tunnel. In Proceedings of the Vehicular Technology Conference (VTC Spring), Dresden, Germany, 2–5 June 2013; pp. 1–5. [Google Scholar]
- Seamless, Secure Connection to Wi-Fi® Networks. Available online: http://www.wi-fi.org/discover-wi-fi/wi-fi-certified-passpoint (accessed on 8 August 2022).
- Jansons, J.; Barancevs, A. Using wireless networking for vehicular environment: IEEE 802.11 a standard performance. In Proceedings of the 2012 Second International Conference on Digital Information Processing and Communications (ICDIPC), Washington, DC, USA, 7–8 January 2012; pp. 5–9. [Google Scholar]
- Lu, N.; Cheng, N.; Zhang, N.; Shen, X.; Mark, J.W. Connected vehicles: Solutions and challenges. IEEE Internet Things J. 2014, 1, 289–299. [Google Scholar] [CrossRef]
- Security Issues of WiFi—How it Works. Available online: https://www.alienvault.com/blogs/security-essentials/security-issues-of-wifi-how-it-works (accessed on 8 August 2022).
- Seo, H.; Lee, K.-D.; Yasukawa, S.; Peng, Y.; Sartori, P. LTE evolution for vehicle-to-everything services. IEEE Commun. Mag. 2016, 54, 22–28. [Google Scholar] [CrossRef]
- Lee, J.; Kim, Y.; Kwak, Y.; Zhang, J.; Papasakellariou, A.; Novlan, T.; Sun, C.; Li, Y. LTE-advanced in 3GPP Rel-13/14: An evolution toward 5G. IEEE Commun. Mag. 2016, 54, 36–42. [Google Scholar] [CrossRef]
- Khanh, Q.V.; Hoai, N.V.; Manh, L.D.; Le, A.N.; Jeon, G. Wireless communication technologies for IoT in 5G: Vision, applications, and challenges. Wirel. Commun. Mob. Comput. 2022, 2022, 3229294. [Google Scholar] [CrossRef]
- Araniti, G.; Campolo, C.; Condoluci, M.; Iera, A.; Molinaro, A. LTE for vehicular networking: A survey. IEEE Commun. Mag. 2013, 51, 148–157. [Google Scholar] [CrossRef]
- Sun, S.-H.; Hu, J.-L.; Peng, Y.; Pan, X.-M.; Zhao, L.; Fang, J.-Y. Support for vehicle-to-everything services based on LTE. IEEE Wirel. Commun. 2016, 23, 4–8. [Google Scholar] [CrossRef]
- Expanding Your Horizons with Lte Direct—Enabling the Next Generation of Proximal Services. Available online: https://www.qualcomm.com/documents/srg-whitepaper-expanding-your-horizons-lte-direct (accessed on 8 August 2022).
- V2X Cellular Solutions. October. 2016. Available online: https://www.5gamericas.org/v2x-cellular-solutions/ (accessed on 8 August 2022).
- Cheng, N.; Lyu, F.; Chen, J.; Xu, W.; Zhou, H.; Zhang, S.; Shen, X. Big data driven vehicular networks. IEEE Netw. 2018, 32, 160–167. [Google Scholar] [CrossRef]
- Mejri, M.N.; Ben-Othman, J.; Hamdi, M. Survey on VANET security challenges and possible cryptographic solutions. Veh. Commun. 2014, 1, 53–66. [Google Scholar] [CrossRef]
- Papadimitratos, P.; Hubaux, J.-P. Report on the secure vehicular communications: Results and challenges ahead workshop. ACM SIGMOBILE Mob. Comput. Commun. Rev. 2008, 12, 53–64. [Google Scholar] [CrossRef]
- Hasrouny, A.E.S.H.; Bassil, C.; Laouiti, A. VANET Security Challenges and Solutions: A Survey. Veh. Commun. 2017, 7, 7–20. [Google Scholar] [CrossRef]
- Mershad, K.; Artail, H. A framework for secure and efficient data acquisition in vehicular ad hoc networks. IEEE Trans. Veh. Technol. 2013, 62, 536–551. [Google Scholar] [CrossRef]
- Dhamgaye, A.; Chavhan, N. Survey on Security Challenges in VANET 1. 2013. Available online: https://citeseerx.ist.psu.edu/viewdoc/summary?doi=10.1.1.300.3967 (accessed on 8 August 2022).
- Raya, M.; Hubaux, J.-P. Securing vehicular ad hoc networks. J. Comput. Secur. 2007, 15, 39–68. [Google Scholar] [CrossRef]
- Perrig, A.; Canetti, R.; Tygar, J.D.; Song, D. The TESLA Broadcast Authentication Protocol. Rsa Cryptobytes. 2005; Volume 5. Available online: https://people.eecs.berkeley.edu/~tygar/papers/TESLA_broadcast_authentication_protocol.pdf (accessed on 8 August 2022).
- Wasef, A.; Jiang, Y.; Shen, X. ECMV: Efficient certificate management scheme for vehicular networks. In Proceedings of the Global Telecommunications Conference, New Orleans, LA, USA, 30 November–4 December 2008; pp. 1–5. [Google Scholar]
- Studer, A.; Shi, E.; Bai, F.; Perrig, A. TACKing together efficient authentication, revocation, and privacy in VANETs. In Proceedings of the 2009 6th Annual IEEE Communications Society Conference on Sensor, Mesh and Ad Hoc Communications and Networks, Rome, Italy, 22–26 June 2009; pp. 1–9. [Google Scholar]
- Wong, C.K.; Gouda, M.; Lam, S.S. Secure group communications using key graphs. IEEE/ACM Trans. Netw. 2000, 8, 16–30. [Google Scholar] [CrossRef]
- Zheng, X.; Huang, C.-T.; Matthews, M. Chinese remainder theorem based group key management. In Proceedings of the 45th Annual Southeast Regional Conference, Winston-Salem, NC, USA, 23–24 March 2007; pp. 266–271. [Google Scholar]
- Zhou, J.; Ou, Y.H. Key tree and Chinese remainder theorem based group key distrubution scheme. J. Chin. Inst. Eng. 2009, 32, 967–974. [Google Scholar] [CrossRef]
- Calandriello, G.; Papadimitratos, P.; Hubaux, J.-P.; Lioy, A. Efficient and robust pseudonymous authentication in VANET. In Proceedings of the fourth ACM International Workshop on Vehicular Ad Hoc Networks, Montreal, QC, Canada, 10 September 2007; pp. 19–28. [Google Scholar]
- Lu, R.; Lin, X.; Zhu, H.; Ho, P.-H.; Shen, X. ECPP: Efficient conditional privacy preservation protocol for secure vehicular communications. In Proceedings of the INFOCOM 2008—The 27th Conference on Computer Communications, Phoenix, AZ, USA, 13–18 April 2008; pp. 1229–1237. [Google Scholar]
- Boualouache, A.; Senouci, S.-M.; Moussaoui, S. A survey on pseudonym changing strategies for Vehicular Ad-Hoc Networks. arXiv 2017, arXiv:1704.00679. [Google Scholar] [CrossRef]
- Freudiger, J.; Raya, M.; Félegyházi, M.; Papadimitratos, P.; Hubaux, J.-P. Mix-zones for location privacy in vehicular networks. In Proceedings of the ACM Workshop on Wireless Networking for Intelligent Transportation Systems (WiN-ITS), Vancouver, BC, Canada, 14 August 2007. [Google Scholar]
- Lu, R.; Lin, X.; Luan, T.H.; Liang, X.; Shen, X. Pseudonym changing at social spots: An effective strategy for location privacy in vanets. IEEE Trans. Veh. Technol. 2012, 61, 86–96. [Google Scholar] [CrossRef]
- Emara, K.; Woerndl, W.; Schlichter, J.H. POSTER: Context-Adaptive User-Centric Privacy Scheme for VANET. In Proceedings of the SecureComm, Dallas, TX, USA, 26–29 October 2015; pp. 590–593. [Google Scholar]
- Sampigethaya, K.; Li, M.; Huang, L.; Poovendran, R. AMOEBA: Robust location privacy scheme for VANET. IEEE J. Sel. Areas Commun. 2007, 25, 8. [Google Scholar] [CrossRef]
- Buttyán, L.; Holczer, T.; Weimerskirch, A.; Whyte, W. Slow: A practical pseudonym changing scheme for location privacy in vanets. In Proceedings of the 2009 IEEE Vehicular Networking Conference (VNC), Tokyo, Japan, 28–30 October 2009; pp. 1–8. [Google Scholar]
- Wiedersheim, B.; Ma, Z.; Kargl, F.; Papadimitratos, P. Privacy in inter-vehicular networks: Why simple pseudonym change is not enough. In Proceedings of the 2010 Seventh International Conference on Wireless On-demand Network Systems and Services (WONS), Kranjska Gora, Slovenia, 3–5 February 2010; pp. 176–183. [Google Scholar]
- Lefevre, S.; Petit, J.; Bajcsy, R.; Laugier, C.; Kargl, F. Impact of v2x privacy strategies on intersection collision avoidance systems. In Proceedings of the Vehicular Networking Conference (VNC), Boston, MA, USA, 16–18 December 2013; pp. 71–78. [Google Scholar]
- Wagner, I.; Eckhoff, D. Privacy assessment in vehicular networks using simulation. In Proceedings of the Simulation Conference (WSC), Savannah, GA, USA, 7–10 December 2014; pp. 3155–3166. [Google Scholar]
- Eckhoff, D. Simulation of Privacy-Enhancing Technologies in Vehicular Ad-Hoc Networks. Ph.D. Thesis, Friedrich-Alexander-Universität Erlangen-Nürnberg (FAU), Erlangen, Germany, 2016. [Google Scholar]
- Eckhoff, D.; Protsenko, M.; German, R. Toward an open source location privacy evaluation framework for vehicular networks. In Proceedings of the Vehicular Technology Conference (VTC Fall), Vancouver, BC, Canada, 14–17 September 2014; pp. 1–2. [Google Scholar]
- Zhang, J. A survey on trust management for vanets. In Proceedings of the 2011 IEEE International Conference on Advanced information networking and applications (AINA), Singapore, 22–25 March 2011; pp. 105–112. [Google Scholar]
- Kerrache, C.A.; Calafate, C.T.; Cano, J.-C.; Lagraa, N.; Manzoni, P. Trust management for vehicular networks: An adversary-oriented overview. IEEE Access 2016, 4, 9293–9307. [Google Scholar] [CrossRef]
- Hoppe, T.; Kiltz, S.; Dittmann, J. Security threats to automotive CAN networks–practical examples and selected short-term countermeasures. Comput. Saf. Reliab. Secur. 2011, 96, 11–25. [Google Scholar] [CrossRef]
- Thing, V.L.; Wu, J. Autonomous Vehicle Security: A Taxonomy of Attacks and Defences. In Proceedings of the 2016 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Singapore, 3–7 September 2016; pp. 164–170. [Google Scholar]
- Zhang, T.; Antunes, H.; Aggarwal, S. Defending connected vehicles against malware: Challenges and a solution framework. IEEE Internet Things J. 2014, 1, 10–21. [Google Scholar] [CrossRef]
- Vallance, C. Car Hack Uses Digital-Radio Broadcasts to Seize Control; BBC: Manchester, UK, 2015. [Google Scholar]
- Idika, N.; Mathur, A.P. A Survey of Malware Detection Techniques; Purdue University: West Lafayette, IN, USA, 2007; Volume 48. [Google Scholar]
- Fadlullah, Z.M.; Nishiyama, H.; Kato, N.; Fouda, M.M. Intrusion detection system (IDS) for combating attacks against cognitive radio networks. IEEE Netw. 2013, 27, 51–56. [Google Scholar] [CrossRef]
- Larson, U.E.; Nilsson, D.K.; Jonsson, E. An approach to specification-based attack detection for in-vehicle networks. In Proceedings of the Intelligent Vehicles Symposium, Eindhoven, The Netherlands, 4–6 June 2008; pp. 220–225. [Google Scholar]
- Song, H.M.; Kim, H.R.; Kim, H.K. Intrusion detection system based on the analysis of time intervals of CAN messages for in-vehicle network. In Proceedings of the 2016 International Conference on Information Networking (ICOIN), Kota Kinabalu, Malaysia, 13–15 January 2016; pp. 63–68. [Google Scholar]
- Kang, M.-J.; Kang, J.-W. A Novel Intrusion Detection Method Using Deep Neural Network for In-Vehicle Network Security. In Proceedings of the Vehicular Technology Conference (VTC Spring), Nanjing, China, 15–18 May 2016; pp. 1–5. [Google Scholar]
- Acarman, T.; Liu, Y.; Ozguner, U. Intelligent cruise control stop and go with and without communication. In Proceedings of the American Control Conference, Minneapolis, MN, USA, 14–16 June 2006; p. 6. [Google Scholar]
- Tsugawa, S.; Kato, S. Energy ITS: Another application of vehicular communications. IEEE Commun. Mag. 2010, 48, 11. [Google Scholar] [CrossRef]
- Jia, D.; Lu, K.; Wang, J.; Zhang, X.; Shen, X. A survey on platoon-based vehicular cyber-physical systems. IEEE Commun. Surv. Tutor. 2016, 18, 263–284. [Google Scholar] [CrossRef]
- Amoozadeh, M.; Raghuramu, A.; Chuah, C.N.; Ghosal, D.; Zhang, H.M.; Rowe, J.; Levitt, K. Security vulnerabilities of connected vehicle streams and their impact on cooperative driving. IEEE Commun. Mag. 2015, 53, 126–132. [Google Scholar] [CrossRef]
- Xu, L.; Wang, L.Y.; Yin, G.; Zhang, H. Communication information structures and contents for enhanced safety of highway vehicle platoons. IEEE Trans. Veh. Technol. 2014, 63, 4206–4220. [Google Scholar] [CrossRef]
- Seiler, P.; Pant, A.; Hedrick, K. Disturbance propagation in vehicle strings. IEEE Trans. Autom. Control. 2004, 49, 1835–1842. [Google Scholar] [CrossRef]
- Öncü, S.; Ploeg, J.; van de Wouw, N.; Nijmeijer, H. Cooperative adaptive cruise control: Network-aware analysis of string stability. IEEE Trans. Intell. Transp. Syst. 2014, 15, 1527–1537. [Google Scholar] [CrossRef]
- Alipour-Fanid, A.; Dabaghchian, M.; Zeng, K. Platoon Stability and Safety Analysis of Cooperative Adaptive Cruise Control under Wireless Rician Fading Channels and Jamming Attacks. arXiv 2017, arXiv:1710.08476. [Google Scholar]
- Di Maio, A.; Palattella, M.R.; Soua, R.; Lamorte, L.; Vilajosana, X.; Alonso-Zarate, J.; Engel, T. Enabling sdn in vanets: What is the impact on security? Sensors 2016, 16, 2077. [Google Scholar] [CrossRef]
- Alipour-Fanid, A.; Dabaghchian, M.; Zhang, H.; Zeng, K. String stability analysis of cooperative adaptive cruise control under jamming attacks. In Proceedings of the 2017 IEEE 18th International Symposium on High Assurance Systems Engineering (HASE), Suzhou, China, 23–27 October 2017; pp. 157–162. [Google Scholar]
- Petrillo, A.; Pescapé, A.; Santini, S. A collaborative control strategy for platoons of autonomous vehicles in the presence of message falsification attacks. In Proceedings of the 2017 5th IEEE International Conference on Models and Technologies for Intelligent Transportation Systems (MT-ITS), San Francisco, CA, USA, 6–8 April 2017; pp. 110–115. [Google Scholar]
- Hall, R.; Chin, C. Vehicle sorting for platoon formation: Impacts on highway entry and throughput. Transp. Res. Part C Emerg. Technol. 2005, 13, 405–420. [Google Scholar] [CrossRef]
- Liu, B.; Jia, D.; Lu, K.; Chen, H.; Yang, R.; Wang, J.; Barnard, Y.; Wu, L. Infrastructure-assisted message dissemination for supporting heterogeneous driving patterns. IEEE Trans. Intell. Transp. Syst. 2017, 18, 2865–2876. [Google Scholar] [CrossRef]
- Liu, B.; Jia, D.; Wang, J.; Lu, K.; Wu, L. Cloud-Assisted Safety Message Dissemination in VANET–Cellular Heterogeneous Wireless Network. IEEE Syst. J. 2017, 11, 128–139. [Google Scholar] [CrossRef]
- Silva, C.M.; Masini, B.M.; Ferrari, G.; Thibault, I. A survey on infrastructure-based vehicular networks. Mob. Inf. Syst. 2017, 2017, 6123868. [Google Scholar] [CrossRef]
- Liu, S.; Wang, J.; Wang, Z.; Yu, B.; Hu, W.; Liu, Y.; Tang, J.; Song, S.L.; Liu, C.; Hu, Y. Brief industry paper: The necessity of adaptive data fusion in infrastructure-augmented autonomous driving system. In Proceedings of the 2022 IEEE 28th Real-Time and Embedded Technology and Applications Symposium (RTAS), Milano, Italy, 4–6 May 2022; pp. 293–296. [Google Scholar]
- Xu, W.; Zhou, H.; Cheng, N.; Lyu, F.; Shi, W.; Chen, J.; Shen, X. Internet of vehicles in big data era. IEEE/CAA J. Autom. Sin. 2017, 5, 19–35. [Google Scholar] [CrossRef]
- Zhang, S.; Chen, J.; Lyu, F.; Cheng, N.; Shi, W.; Shen, X. Vehicular communication networks in the automated driving era. IEEE Commun. Mag. 2018, 56, 26–32. [Google Scholar] [CrossRef]
- Chen, C.; Seff, A.; Kornhauser, A.; Xiao, J. Deepdriving: Learning affordance for direct perception in autonomous driving. In Proceedings of the IEEE International Conference on Computer Vision, Santiago, Chile, 7–13 December 2015; pp. 2722–2730. [Google Scholar]
- Cao, B.; Kim, M.J.; Wang, J.R.; van Santen, J.P.; Mau, T.; Wang, J. Articulation-to-Speech Synthesis Using Articulatory Flesh Point Sensors’ Orientation Information. In Proceedings of the Interspeech 2018, Hyderabad, India, 2–6 September 2018; pp. 3152–3156. [Google Scholar]
- Azarang, A.; Kehtarnavaz, N. Image fusion in remote sensing by multi-objective deep learning. Int. J. Remote Sens. 2020, 41, 9507–9524. [Google Scholar] [CrossRef]
- Shao, H.; Li, J.; Zhang, J.; Yu, H.; Sun, J. Eye-based recognition for user identification on mobile devices. ACM Trans. Multimed. Comput. Commun. Appl. (TOMM) 2020, 16, 1–19. [Google Scholar] [CrossRef]
- Zhu, H.; Wei, H.; Li, B.; Yuan, X.; Kehtarnavaz, N. A review of video object detection: Datasets, metrics and methods. Appl. Sci. 2020, 10, 7834. [Google Scholar] [CrossRef]
- Zeng, X.; Wang, Z.; Hu, Y. Enabling Efficient Deep Convolutional Neural Network-based Sensor Fusion for Autonomous Driving. arXiv 2022, arXiv:2202.11231. [Google Scholar]
- Thomaidis, G.; Vassilis, K.; Lytrivis, P.; Tsogas, M.; Karaseitanidis, G.; Amditis, A. Target tracking and fusion in vehicular networks. In Proceedings of the Intelligent Vehicles Symposium (IV), Baden-Baden, Germany, 5–9 June 2011; pp. 1080–1085. [Google Scholar]
- Haykin, S.S. Kalman Filtering and Neural Networks; John Wiley & Sons, Inc.: Hoboken, NJ, USA, 2001. [Google Scholar]
- Rauch, A.; Klanner, F.; Rasshofer, R.; Dietmayer, K. Car2x-based perception in a high-level fusion architecture for cooperative perception systems. In Proceedings of the Intelligent Vehicles Symposium (IV), Madrid, Spain, 3–7 June 2012; pp. 270–275. [Google Scholar]
- Bateni, S.; Wang, Z.; Zhu, Y.; Hu, Y.; Liu, C. Co-optimizing performance and memory footprint via integrated cpu/gpu memory management, an implementation on autonomous driving platform. In Proceedings of the 2020 IEEE Real-Time and Embedded Technology and Applications Symposium (RTAS), Sydney, Australia, 21–24 April 2020; pp. 310–323. [Google Scholar]
- Wang, Z.; Jiang, Z.; Wang, Z.; Tang, X.; Liu, C.; Yin, S.; Hu, Y. Enabling Latency-Aware Data Initialization for Integrated CPU/GPU Heterogeneous Platform. IEEE Trans. Comput. -Aided Des. Integr. Circuits Syst. 2020, 39, 3433–3444. [Google Scholar] [CrossRef]
- Wang, Z.; Wang, Z.; Liu, C.; Hu, Y. Understanding and tackling the hidden memory latency for edge-based heterogeneous platform. In Proceedings of the 3rd USENIX Workshop on Hot Topics in Edge Computing (HotEdge 20), Santa Clara, CA, USA, 6 February 2020. [Google Scholar]
- Levine, S.; Pastor, P.; Krizhevsky, A.; Ibarz, J.; Quillen, D. Learning hand-eye coordination for robotic grasping with deep learning and large-scale data collection. Int. J. Robot. Res. 2016, 37, 421–436. [Google Scholar] [CrossRef]
- Mnih, V.; Kavukcuoglu, K.; Silver, D.; Rusu, A.A.; Veness, J.; Bellemare, M.G.; Graves, A.; Riedmiller, M.; Fidjeland, A.K.; Ostrovski, G.; et al. Human-level control through deep reinforcement learning. Nature 2015, 518, 529–533. [Google Scholar] [CrossRef]
- Bojarski, M.; Del Testa, D.; Dworakowski, D.; Firner, B.; Flepp, B.; Goyal, P.; Jackel, L.D.; Monfort, M.; Muller, U.; Zhang, J.; et al. End to end learning for self-driving cars. arXiv 2016, arXiv:1604.07316. [Google Scholar]
- Wang, Z.; Zeng, X.; Tang, X.; Zhang, D.; Hu, X.; Hu, Y. Demystifying Arch-hints for Model Extraction: An Attack in Unified Memory System. arXiv 2022, arXiv:2208.13720. [Google Scholar]
- Wan, J.; Zhang, D.; Zhao, S.; Yang, L.; Lloret, J. Context-aware vehicular cyber-physical systems with cloud support: Architecture, challenges, and solutions. IEEE Commun. Mag. 2014, 52, 106–113. [Google Scholar] [CrossRef]
- Lee, E.-K.; Gerla, M.; Pau, G.; Lee, U.; Lim, J.-H. Internet of Vehicles: From intelligent grid to autonomous cars and vehicular fogs. Int. J. Distrib. Sens. Netw. 2016, 12, 1550147716665500. [Google Scholar] [CrossRef]
- Christodorescu, M.; Jha, S. Static Analysis of Executables to Detect Malicious Patterns; University of Wisconsin—Madison Department of Computer Sciences: Madison, WI, USA, 2006. [Google Scholar]
- Wang, Z.; Wang, R.; Jiang, Z.; Tang, X.; Yin, S.; Hu, Y. Towards a Secure Integrated Heterogeneous Platform via Cooperative CPU/GPU Encryption. In Proceedings of the 2021 IEEE 30th Asian Test Symposium (ATS), Matsuyama, Japan, 22–25 November 2021; pp. 115–120. [Google Scholar]
- Schultz, M.G.; Eskin, E.; Zadok, F.; Stolfo, S.J. Data mining methods for detection of new malicious executables. In Proceedings of the 2001 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 14–16 May 2001; pp. 38–49. [Google Scholar]
- Tesauro, G.J.; Kephart, J.O.; Sorkin, G.B. Neural networks for computer virus recognition. IEEE Expert 1996, 11, 5–6. [Google Scholar] [CrossRef]

| Components | Application | Security Issues | Solutions |
|---|---|---|---|
| CAN bus |
|
|
|
| ECUs |
|
|
|
| Application | Attacks | Existing Enhancement | Open Issues | |
|---|---|---|---|---|
| Bluetooth | V2P and specific scenarios with low density and low speed of vehicles (e.g., rural roads). | Pin interception. Injection of fake pin. Traceability attack. Infection attack. | Strong PIN authentication. Frequency hopping. Pre-shared key for authentication and encryption. | Security risks caused by frequent iterations of versions. Security risks caused by different pairing modes. |
| Wi-Fi | Built-in or brought-in. Scenarios: V2V, V2I, V2P, etc. | DoS, cracking, rekeying, karma attack, etc. | MIMO to improve transmission. Passpoint/Hotspot 2.0 provide Wi-Fi with security, WPA 2. | Long establishing time, including association, authentication, etc. Unsecure mode (e.g., WPA 2 is cracked). |
| Services | Transmission Mode | Advantages | Open Issues | |
|---|---|---|---|---|
| C-V2X | V2V, V2P, V2I, V2N |
|
|
|
| Feature | C-V2X | VANET |
|---|---|---|
| Capacity | High | Medium |
| Mobility | Very high (support speed up to 350 km/h) | Medium |
| Coverage | Ubiquitous | Medium |
| Delay | Goal is 100ms (C-plane) and 10 ms round-trip and 5 ms (U-plane) | Goal is 100ms (safety-critical application) and 500ms (non-safety-critical application) |
| V2I support | Native, due to the centralized architecture with enhancements | Yes, only intermittent and short-lived connectivity |
| V2V support | Potential, through D2D extension | Native, through extensions in MAC protocols |
| Network infrastructure | Adopting existing cellular infrastructure for V2I communications | Requiring high investment on network backbone devices |
| Security issues |
|
|
| Control Message Code | Controlled Function | Impacted Control Module |
|---|---|---|
| 07 AE...1F 87 | Continuously activates lock replay | Body control module |
| 07 AE...CE 32 | Temporary RPM increase | Engine control module |
| 07 AE...25 2B | Engages front-left brake | Electronic brake control |
| 00 00...00 00 | Falsify speedometer reading | Other modules |
| Type | Description | Attacks/Consequences | Defenses |
|---|---|---|---|
| DoS | Introduce the topmost priority nonsense message frequently to systems. |
|
|
| Fuzzing attack | Massive amounts of random data can be inputted to the system. |
| |
| Code modification and injections | Carry out malicious modifications of code; inject malicious messages to the bus system. |
|
|
| Replay attack | Retransmit eavesdropped packer to system. |
|
|
| Malware injection | Malware codes can modify themselves to look different each time they replicate and deceive the system to download them into system. |
|
|
| Cyber Physical Attacks | Workable Solutions |
|---|---|
| Message tampering |
|
| Forgery attacks |
|
| Message saturation |
|
| Replay attack |
|
| Node impersonation |
|
| Routing attack (i.e., Black hole, Grey hole, Worm hole, and Tunneling) |
|
| Spoofing and jamming attack |
|
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, Z.; Wei, H.; Wang, J.; Zeng, X.; Chang, Y. Security Issues and Solutions for Connected and Autonomous Vehicles in a Sustainable City: A Survey. Sustainability 2022, 14, 12409. https://doi.org/10.3390/su141912409
Wang Z, Wei H, Wang J, Zeng X, Chang Y. Security Issues and Solutions for Connected and Autonomous Vehicles in a Sustainable City: A Survey. Sustainability. 2022; 14(19):12409. https://doi.org/10.3390/su141912409
Chicago/Turabian StyleWang, Zhendong, Haoran Wei, Jianda Wang, Xiaoming Zeng, and Yuchao Chang. 2022. "Security Issues and Solutions for Connected and Autonomous Vehicles in a Sustainable City: A Survey" Sustainability 14, no. 19: 12409. https://doi.org/10.3390/su141912409
APA StyleWang, Z., Wei, H., Wang, J., Zeng, X., & Chang, Y. (2022). Security Issues and Solutions for Connected and Autonomous Vehicles in a Sustainable City: A Survey. Sustainability, 14(19), 12409. https://doi.org/10.3390/su141912409









