Detection of Distributed Denial of Service (DDoS) Attacks in IOT Based Monitoring System of Banking Sector Using Machine Learning Models
Abstract
:1. Introduction
- This study proposed efficient machine learning model (SVM, KNN, and RF) for the classification of DDOS attacks using Banking Dataset based on their excellent performance. Further, no prior research has ever compared or used these (SVM, KNN, and RF) three approaches of DDoS attacks detection.
- We investigated the training parameters’ influence on the classification accuracy (%), pres (%), recall (%) and F1-score (%) and time complexity (ms).
- To check the evaluation performance of ML models, we compared SVM, KNN, and RF in order to find out the most efficient model. The comparative result indicates that SVM is more robust as compared to KNN, RF and existing machine learning methods (ML/DL).
2. Related Work
3. Materials and Methods
3.1. Dataset Description
3.1.1. Fraud Detection Dataset
3.1.2. Data Preprocessing
- (a)
- Removal of Socket Information
- (b)
- Remove White Spaces
- (c)
- Label Encoding
- (d)
- Data Normalization
- (e)
- Feature Ranking
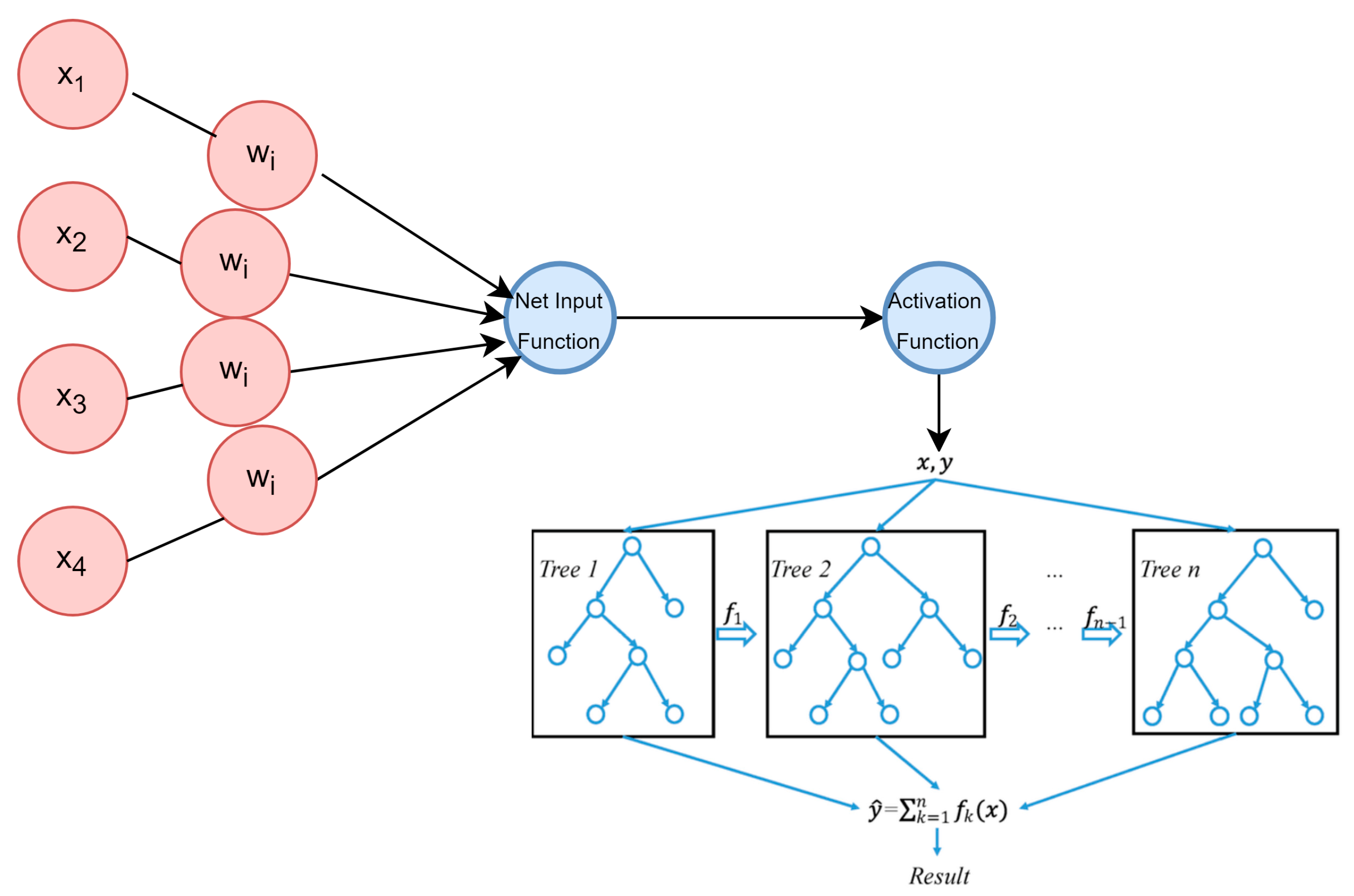
3.2. Machine Learning Models
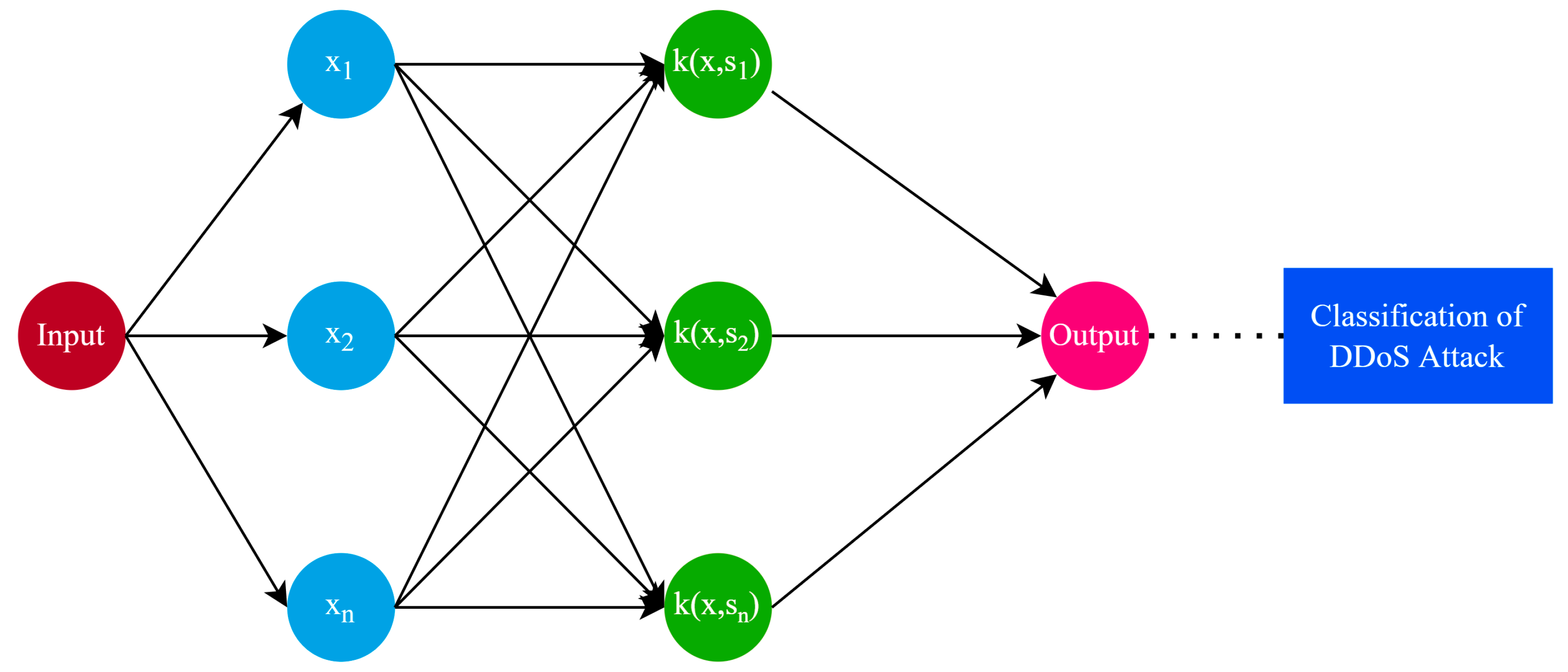
3.2.1. Support Vector Machine
3.2.2. Random Forests
3.2.3. K-Nearest Neighbors
3.3. Performance Metrics
4. Results
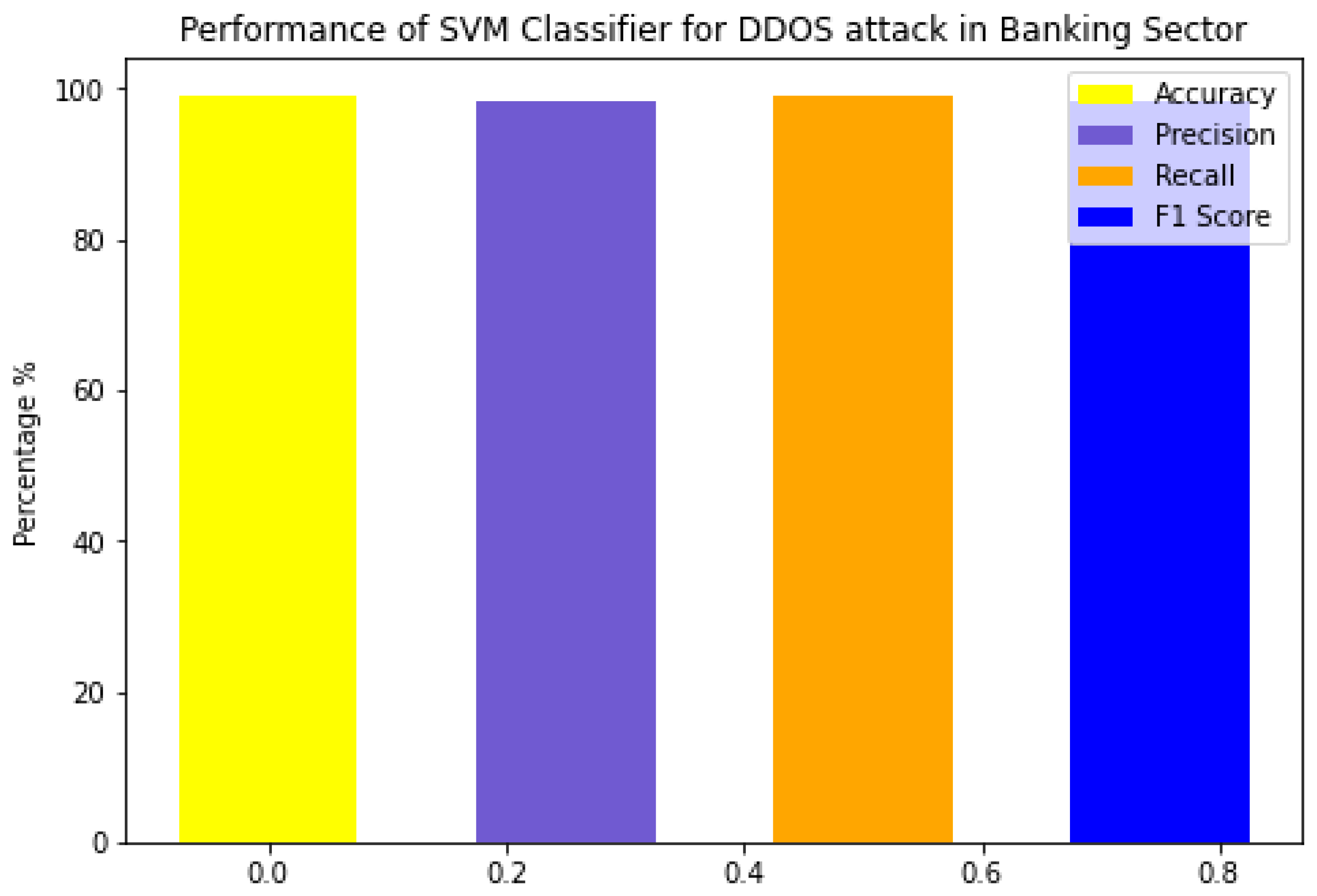
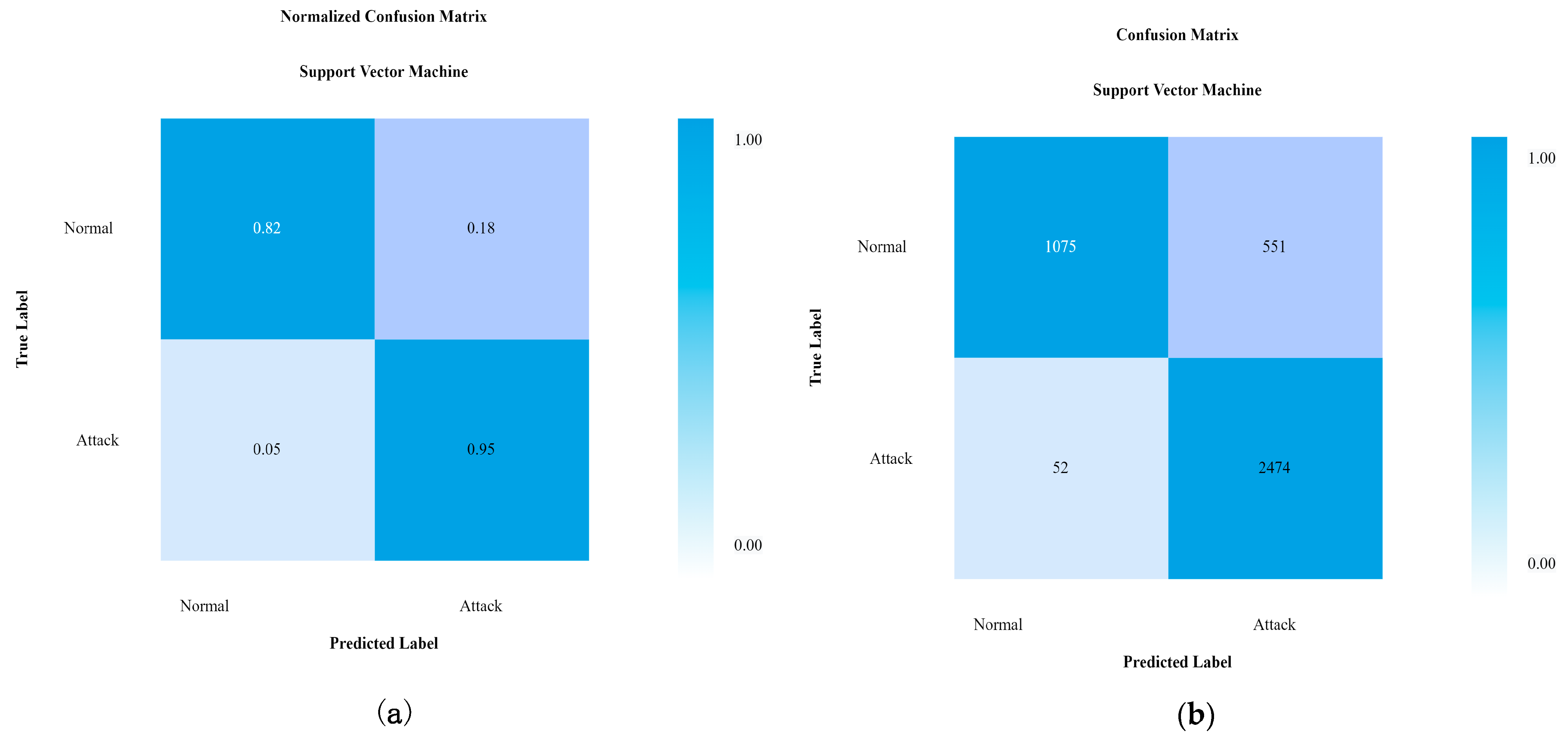
4.1. Performance of SVM Model
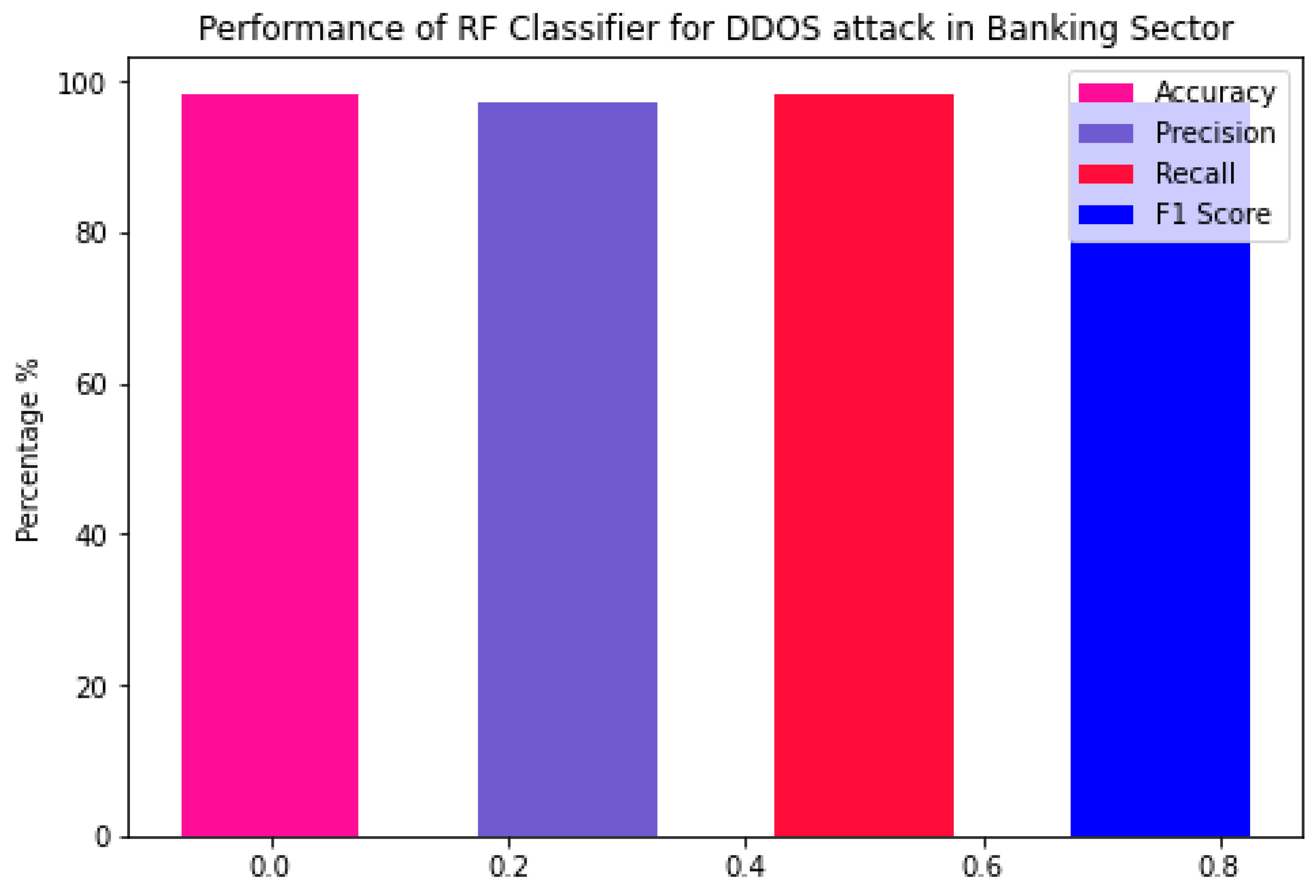
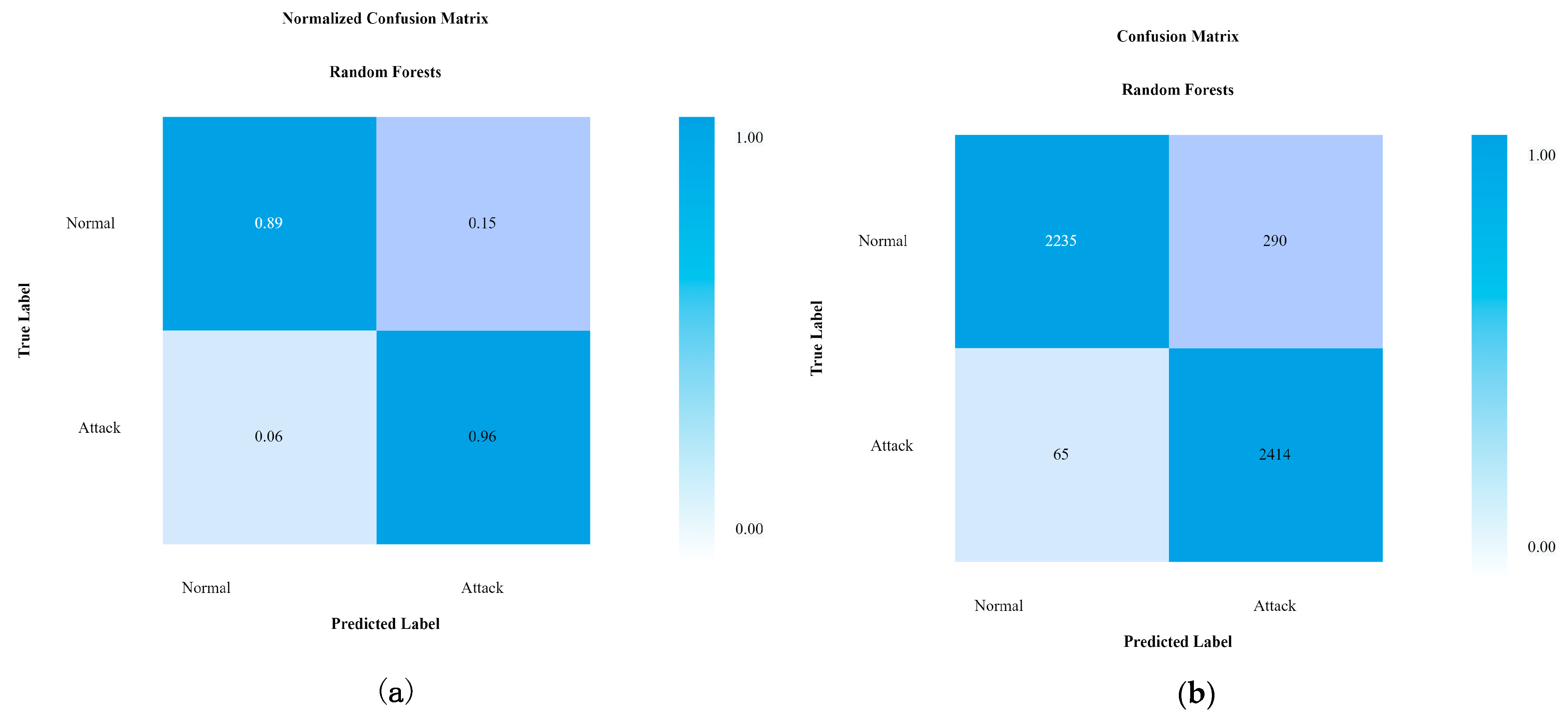
4.2. Performance of Random Forests
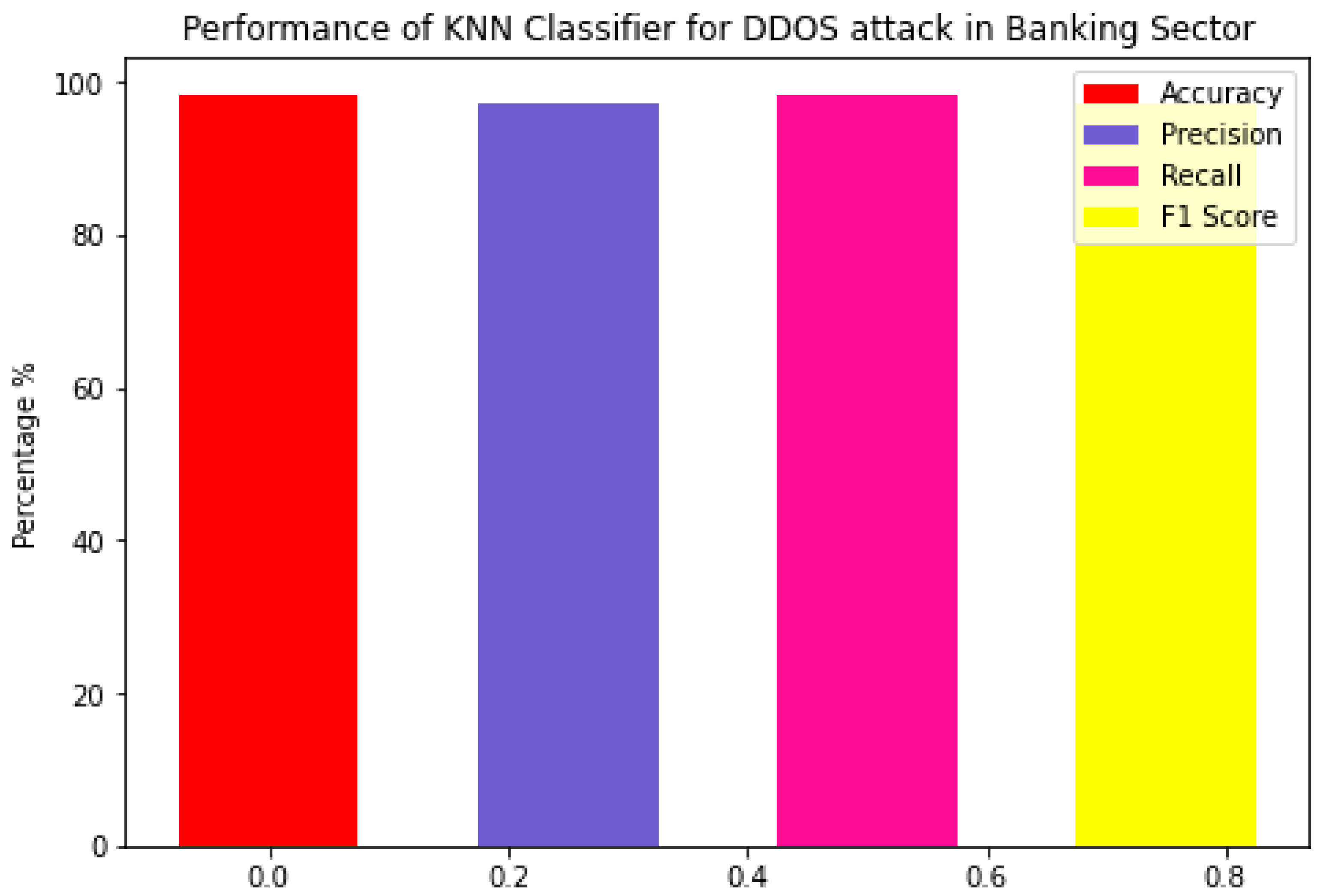
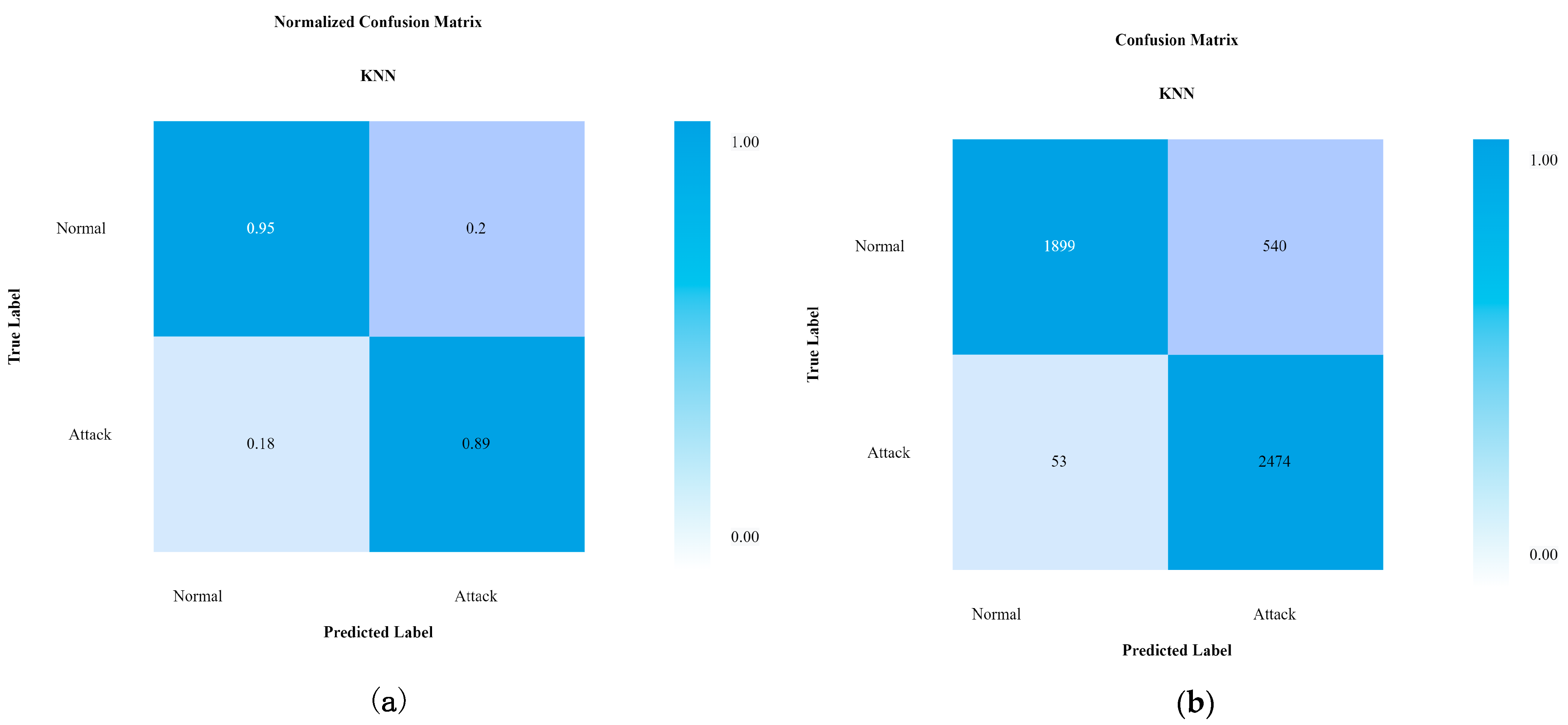
4.3. Performance of KNN
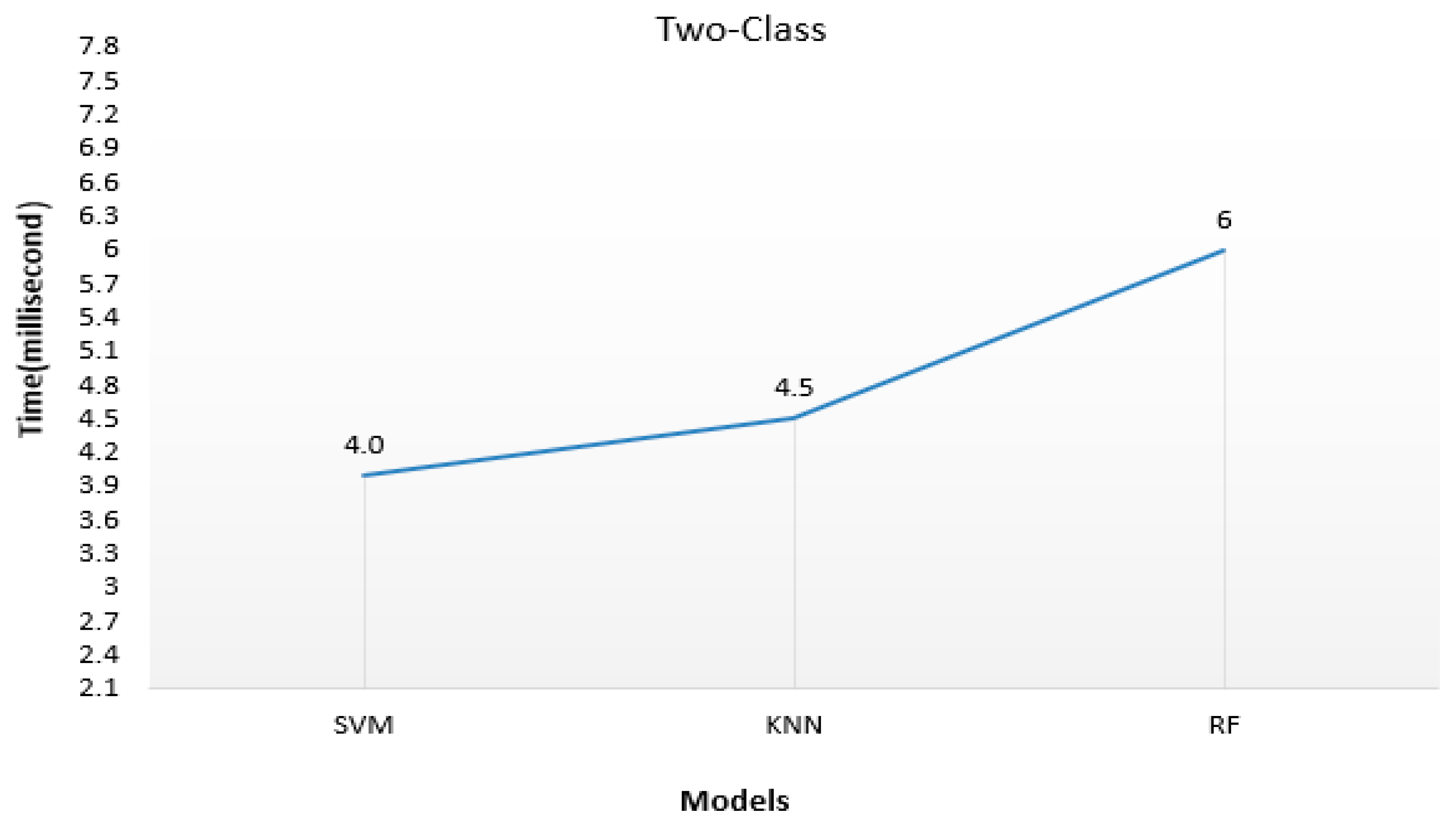
4.4. Time Complexity (sec)
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| AI | Artificial intelligence |
| ML | Machine learning |
| DL | Deep learning |
| DDoS | Distributed Denial-of-Service |
| LDA | Latent Dirichlet Allocation |
| DNN | Deep Neural Network |
| HTTP | Hypertext Transfer Protocol |
| DNN | Deep Neural Network |
References
- Sahingoz, O.K.; Buber, E.; Demir, O.; Diri, B. Machine learning based phishing detection from URLs. Expert Syst. Appl. 2019, 117, 345–357. [Google Scholar] [CrossRef]
- Kambourakis, G.; Moschos, T.; Geneiatakis, D.; Gritzalis, S. Detecting DNS amplification attacks. In CRITIS 2007: Critical Information Infrastructures Security; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2008; Volume 5141 LNCS, pp. 185–196. [Google Scholar] [CrossRef]
- Ezekiel, S.; Divakaran, D.M.; Gurusamy, M. Dynamic attack mitigation using SDN. In Proceedings of the 2017 27th International Telecommunication Networks and Applications Conference (ITNAC), Melbourne, VIC, Australia, 22–24 November 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Javeed, D.; Gao, T.; Khan, M.T. SDN-enabled hybrid DL-driven framework for the detection of emerging cyber threats in IoT. Electronics 2021, 10, 918. [Google Scholar] [CrossRef]
- Kushwah, G.S.; Ranga, V. Voting extreme learning machine based distributed denial of service attack detection in cloud computing. J. Inf. Secur. Appl. 2020, 53, 102532. [Google Scholar] [CrossRef]
- Osanaiye, O.; Choo, K.-K.R.; Dlodlo, M. Analysing Feature Selection and Classification Techniques for DDoS Detection in Cloud. In Proceedings of the Southern Africa Telecommunication Networks and Applications Conference (SATNAC) 2016, George, South Africa, 7 September 2016; pp. 198–203. [Google Scholar]
- Ahmad, I.; Wang, X.; Zhu, M.; Wang, C.; Pi, Y.; Khan, J.A.; Li, G. EEG-Based Epileptic Seizure Detection via Machine/Deep Learning Approaches: A Systematic Review. Comput. Intell. Neurosci. 2022, 2022, 6486570. [Google Scholar] [CrossRef] [PubMed]
- Ahmad, S.; Ullah, T.; Ahmad, I.; AL-Sharabi, A.; Ullah, K.; Khan, R.A.; Ali, M. A Novel Hybrid Deep Learning Model for Metastatic Cancer Detection. Comput. Intell. Neurosci. 2022, 2022, 8141530. [Google Scholar] [CrossRef]
- Ahmad, I.; Ullah, I.; Khan, W.U.; Ur Rehman, A.; Adrees, M.S.; Saleem, M.Q.; Shafiq, M. Efficient algorithms for E-healthcare to solve multiobject fuse detection problem. J. Healthc. Eng. 2021, 2021, 9500304. [Google Scholar] [CrossRef]
- Ahmad, I.; Liu, Y.; Javeed, D.; Ahmad, S. A decision-making technique for solving order allocation problem using a genetic algorithm. IOP Conf. Ser. Mater. Sci. Eng. 2020, 853, 012054. [Google Scholar] [CrossRef]
- Wang, Y.; Wang, W.; Ahmad, I.; Tag-Eldin, E. Multi-Objective Quantum-Inspired Seagull Optimization Algorithm. Electronics 2022, 11, 1834. [Google Scholar] [CrossRef]
- Ahmad, I.; Liu, Y.; Javeed, D.; Shamshad, N.; Sarwr, D.; Ahmad, S. A review of artificial intelligence techniques for selection & evaluation. IOP Conf. Ser. Mater. Sci. Eng. 2020, 853, 012055. [Google Scholar]
- Ali, S.; Javaid, N.; Javeed, D.; Ahmad, I.; Ali, A.; Badamasi, U.M. A blockchain-based secure data storage and trading model for wireless sensor networks. In Proceedings of the International Conference on Advanced Information Networking and Applications, Caserta, Italy, 15–17 April 2020. [Google Scholar]
- Chayomchai, A.; Phonsiri, W.; Junjit, A.; Boongapim, R.; Suwannapusit, U. Factors affecting acceptance and use of online technology in Thai people during COVID-19 quarantine time. Manag. Sci. Lett. 2020, 10, 3009–3016. [Google Scholar] [CrossRef]
- Mhamane, S.S.; Lobo, L.M.R.J. Internet banking fraud detection using HMM. In Proceedings of the 2012 Third International Conference on Computing, Communication and Networking Technologies (ICCCNT’12), Coimbatore, India, 26–28 July 2012. [Google Scholar] [CrossRef]
- Alimolaei, S. An intelligent system for user behavior detection in Internet Banking. In Proceedings of the 2015 4th Iranian Joint Congress on Fuzzy and Intelligent Systems (CFIS), Zahedan, Iran, 9–11 September 2015. [Google Scholar] [CrossRef]
- Fang, L.; Li, Y.; Liu, Z.; Yin, C.; Li, M.; Cao, Z.J. A Practical Model Based on Anomaly Detection for Protecting Medical IoT Control Services against External Attacks. IEEE Trans. Ind. Inform. 2021, 17, 4260–4269. [Google Scholar] [CrossRef]
- Using, N.; Learning, M. A Comprehensive Study of Anomaly Detection Schemes in IoT Networks Using Machine Learning Algorithms. Sensors 2021, 21, 8320. [Google Scholar] [CrossRef]
- Salem, O.; Alsubhi, K.; Shaafi, A.; Gheryani, M.; Mehaoua, A.; Boutaba, R. Man-in-the-Middle Attack Mitigation in Internet of Medical Things. IEEE Trans. Ind. Inform. 2022, 18, 2053–2062. [Google Scholar] [CrossRef]
- Gupta, D.; Gupta, M.; Bhatt, S.; Tosun, A.S. Detecting Anomalous User Behavior in Remote Patient Monitoring. In Proceedings of the 2021 IEEE 22nd International Conference on Information Reuse and Integration for Data Science (IRI), Las Vegas, NV, USA, 10–12 August 2021; pp. 33–40. [Google Scholar] [CrossRef]
- Saeedi, K. Machine Learning for Ddos Detection in Packet Core Network for IoT. Master’s Thesis, Luleå University of Technology, Luleå, Sweden, 2019. [Google Scholar]
- Tahir Ullah, K. Internet of Things (IOT) systems and its security challenges. Int. J. Adv. Res. Comput. Eng. Technol. 2019, 8, 12. [Google Scholar]
- Kamruzzaman, M.M. New Opportunities, Challenges, and Applications of Edge-AI for Connected Healthcare in Smart Cities. In Proceedings of the 2021 IEEE Globecom Workshops (GC Wkshps), Madrid, Spain, 7–11 December 2021. [Google Scholar]
- Jegadeesan, S.; Azees, M.; Ramesh Babu, N.; Subramaniam, U.; Almakhles, J.D. EPAW: Efficient Privacy Preserving Anonymous Mutual Authentication Scheme for Wireless Body Area Networks (WBANs). IEEE Access 2020, 8, 48576–48586. [Google Scholar] [CrossRef]
- Oppliger, R.; Rytz, R.; Holderegger, T. Internet banking: Client-side attacks and protection mechanisms. Computer 2009, 42, 27–33. [Google Scholar] [CrossRef]
- Zachos, G.; Essop, I.; Mantas, G.; Porfyrakis, K.; Ribeiro, J.C. An Anomaly-Based Intrusion Detection System Internet of Medical Things Networks. Electronics 2021, 10, 2562. [Google Scholar] [CrossRef]
- Lange, T.; Kettani, H. On Security Threats of Botnets to Cyber Systems. In Proceedings of the 2019 6th International Conference on Signal Processing and Integrated Networks (SPIN), Noida, India, 7–8 March 2019; pp. 176–183. [Google Scholar]
- Aski, V.; Dhaka, V.S.; Kumar, S.; Parashar, A.; Ladagi, A. A multi-factor access control and ownership transfer framework for future generation healthcare systems. In Proceedings of the 2020 Sixth International Conference on Parallel, Distributed and Grid Computing (PDGC), Waknaghat, India, 6–8 November 2020; pp. 93–98. [Google Scholar] [CrossRef]
- Mehmood, M.; Javed, T.; Nebhen, J.; Abbas, S.; Abid, R.; Bojja, G.R.; Rizwan, M. A hybrid approach for network intrusion detection. Comput. Mater. Contin. 2021, 70, 91–107. [Google Scholar] [CrossRef]
- Ramapatruni, S.; Narayanan, S.N.; Mittal, S.; Joshi, A.; Joshi, K. Anomaly Detection Models for Smart Home Security. In Proceedings of the 2019 IEEE 5th Intl Conference on Big Data Security on Cloud (BigDataSecurity), IEEE Intl Conference on High Performance and Smart Computing, (HPSC) and IEEE Intl Conference on Intelligent Data and Security (IDS), Washington, DC, USA, 27–29 May 2019; pp. 19–24. [Google Scholar] [CrossRef]
- Hameed, M.; Yang, F.; Ghafoor, M.I.; Jaskani, F.H.; Islam, U.; Fayaz, M.; Mehmood, G. IOTA-Based Mobile Crowd Sensing: Detection of Fake Sensing Using Logit-Boosted Machine Learning Algorithms. Wirel. Commun. Mob. Comput. 2022, 2022, 6274114. [Google Scholar] [CrossRef]
- Kaushik, I.; Sharma, N. Black hole attack and its security measure in wireless sensors networks. In Handbook of Wireless Sensor Networks: Issues and Challenges in Current Scenario’s; Springer: Cham, Switzerland, 2020; Volume 1132. [Google Scholar]
- Dilraj, M.; Nimmy, K.; Sankaran, S. Towards Behavioral Profiling Based Anomaly Detection for Smart Homes. In Proceedings of the TENCON 2019–2019 IEEE Region 10 Conference (TENCON), Kochi, India, 17–20 October 2019; pp. 1258–1263. [Google Scholar]
- Javeed, D.; Khan, M.T.; Ahmad, I.; Iqbal, T.; Badamasi, U.M.; Ndubuisi, C.O.; Umar, A. An efficient approach of threat hunting using memory forensics. Int. J. Comput. Netw. Commun. Secur. 2020, 8, 37–45. [Google Scholar] [CrossRef]
- Javeed, D.; Gao, T.; Khan, M.T.; Shoukat, D. A hybrid intelligent framework to combat sophisticated threats in secure industries. Sensors 2022, 22, 1582. [Google Scholar] [CrossRef] [PubMed]
- Shaikh, H.; Khan, M.S.; Mahar, Z.A.; Anwar, M.; Raza, A.; Shah, A. A conceptual framework for determining acceptance of internet of things (IoT) in higher education institutions of Pakistan. In Proceedings of the 2019 International Conference on Information Science and Communication Technology (ICISCT), Karachi, Pakistan, 9–10 March 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Huang, K.; Yang, L.X.; Yang, X.; Xiang, Y.; Tang, Y.Y. A Low-Cost Distributed Denial-of-Service Attack Architecture. IEEE Access 2020, 8, 42111–42119. [Google Scholar] [CrossRef]
- Razib, A.M.; Javeed, D.; Khan, M.T.; Alkanhel, R.; Muthanna, M.S.A. Cyber Threats Detection in Smart Environments Using SDN-Enabled DNN-LSTM Hybrid Framework. IEEE Access 2022, 10, 53015–53026. [Google Scholar] [CrossRef]
- Dawod, A.; Georgakopoulos, D.; Jayaraman, P.P.; Nirmalathas, A.; Parampalli, U. IoT Device Integration and Payment via an Autonomic Blockchain-Based Service for IoT Device Sharing. Sensors 2022, 22, 1344. [Google Scholar] [CrossRef]
- Hanafizadeh, P.; Amin, M.G. The Transformative Potential of Banking Service Domains with the Emergence of FinTechs; Palgrave Macmillan: London, UK, 2022; No. 0123456789. [Google Scholar]
- Yan, W. Security Optimization Management for loT-Assisted Bank Liquidity Risk Emergency Using Big Data Analytic-Based Case Reasoning. Wirel. Commun. Mob. Comput. 2022, 2022, 8396931. [Google Scholar] [CrossRef]
- Mishra, P.; Guru Sant, T. Role of Artificial Intelligence and Internet of Things in Promoting Banking and Financial Services during COVID-19: Pre and Post Effect. In Proceedings of the 2021 5th International Conference on Information Systems and Computer Networks (ISCON), Mathura, India, 22–23 October 2021. [Google Scholar]
- Javeed, D.; Gao, T.; Khan, M.T.; Ahmad, I. A Hybrid Deep Learning-Driven SDN Enabled Mechanism for Secure Communication in Internet of Things (IoT). Sensors 2021, 21, 4884. [Google Scholar] [CrossRef]
- Aljuhani, A. Machine learning approaches for combating distributed denial of service attacks in modern networking environments. IEEE Access 2021, 9, 42236–42264. [Google Scholar] [CrossRef]
- ur Rehman, S.; Khaliq, M.; Imtiaz, S.I.; Rasool, A.; Shafiq, M.; Javed, A.R.; Jalil, Z.; Bashir, A.K. Diddos: An approach for detection and identification of distributed denial of service (ddos) cyberattacks using gated recurrent units (gru). Future Gener. Comput. Syst. 2021, 118, 453–466. [Google Scholar] [CrossRef]
- Guo, C.; Wang, H.; Dai, H.N.; Cheng, S.; Wang, T. Fraud risk monitoring system for e-banking transactions. In Proceedings of the 2018 IEEE 16th Intl Conf on Dependable, Autonomic and Secure Computing, 16th Intl Conf on Pervasive Intelligence and Computing, 4th Intl Conf on Big Data Intelligence and Computing and Cyber Science and Technology Congress (DASC/PiCom/DataCom/CyberSciTech), Athens, Greece, 12–15 August 2018; pp. 106–113. [Google Scholar]

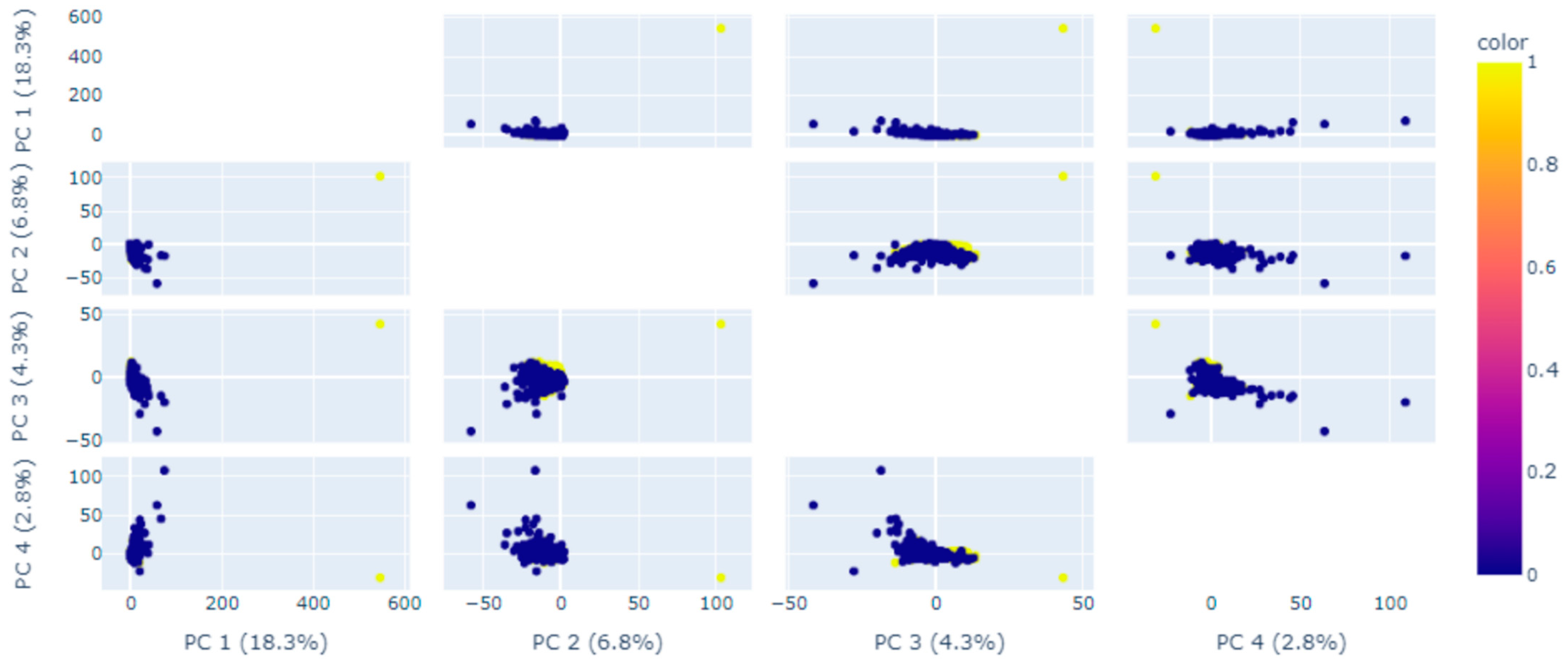
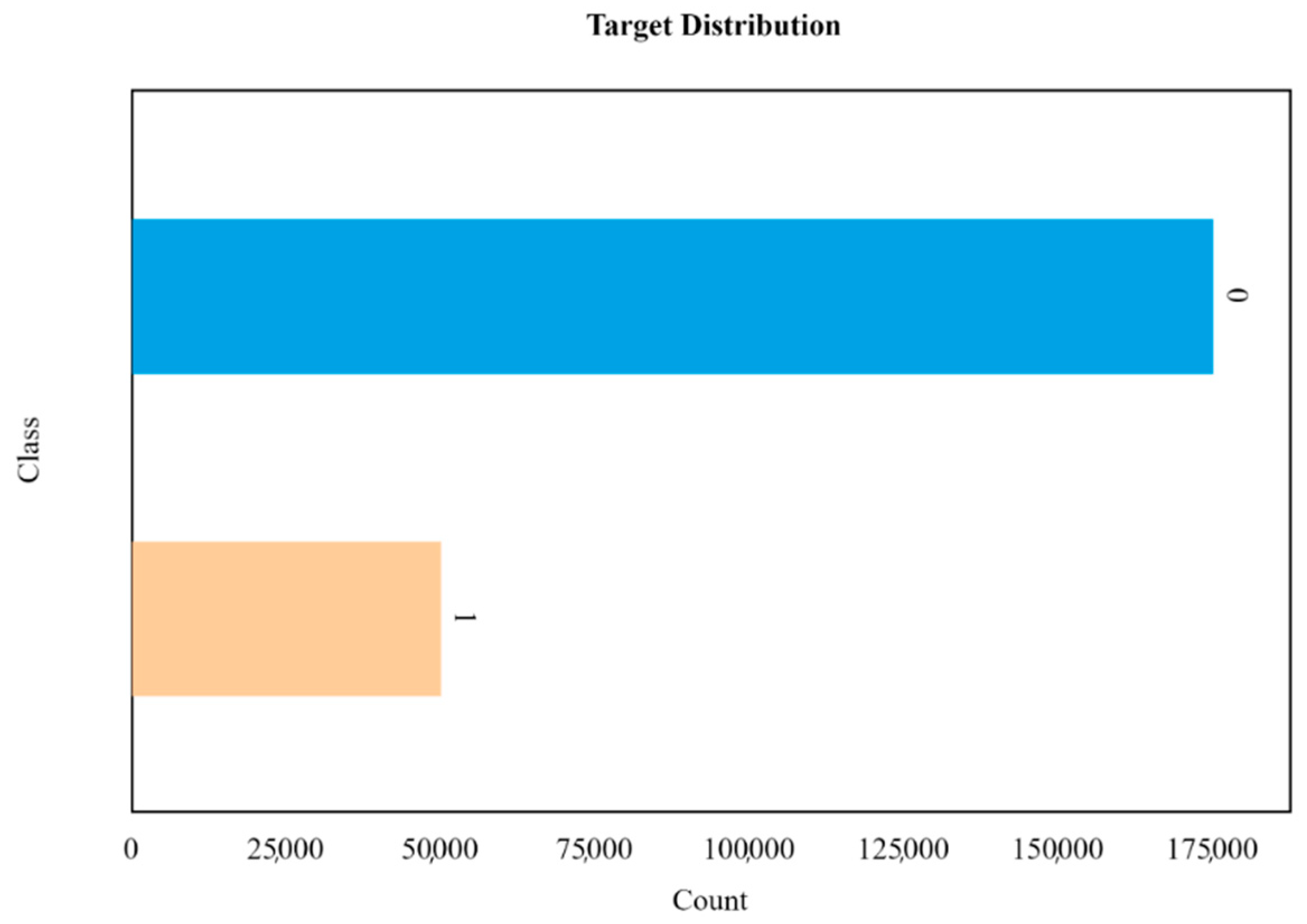
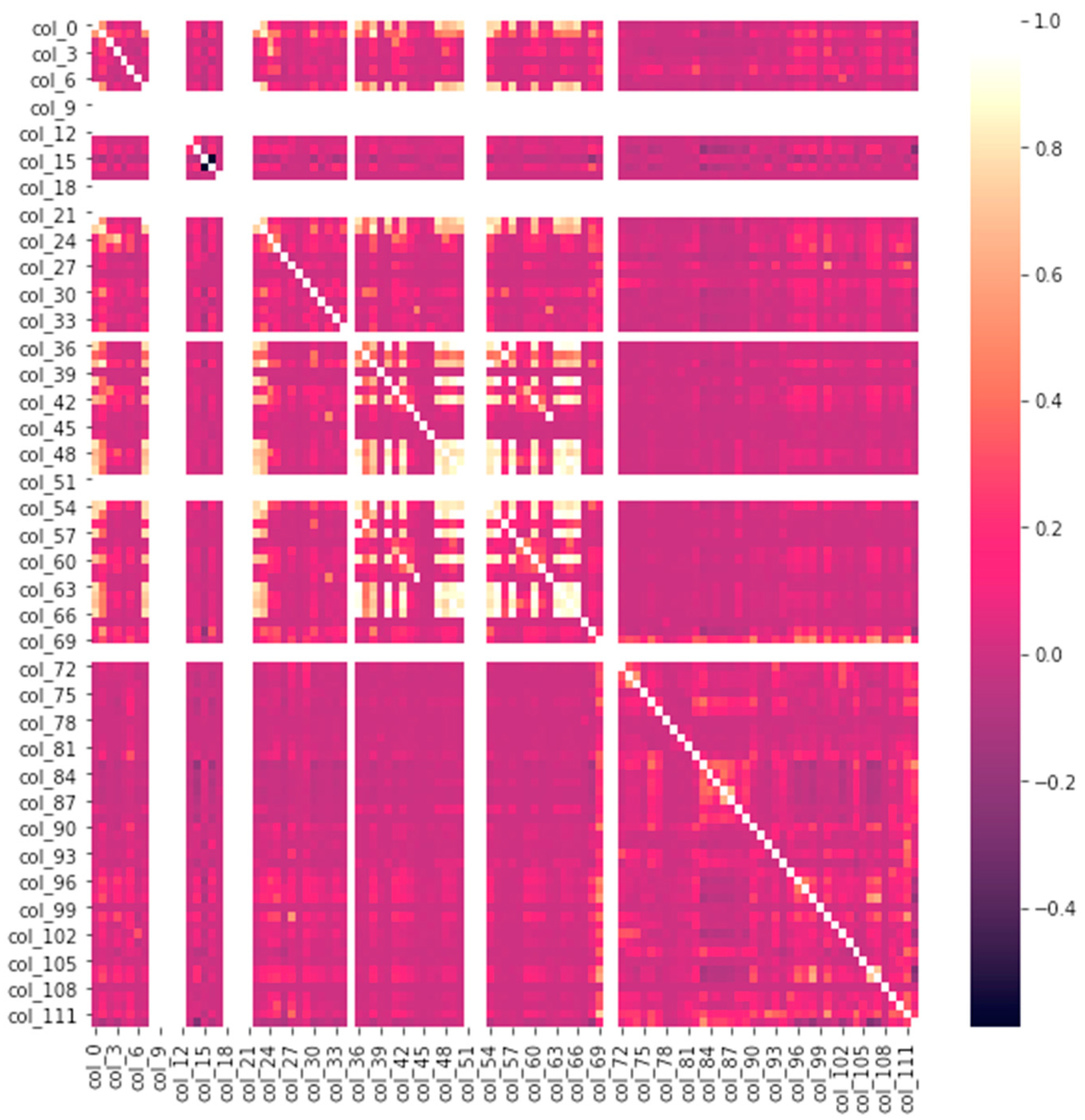

| Feature/Attribute | Description | Variable Type |
|---|---|---|
| ID | ATM ID | Input Variable |
| State | State of Railway (Connectivity) | Input Variable |
| Spkts | Source Packets (Sent to destination) | Input Variable |
| Dpkts | Destination Packets (Received at destination) | Input Variable |
| Sbytes | Source Bytes (Sent from Source) | Input Variable |
| Dbytes | Destination Bytes (Received from Source) | Input Variable |
| Attack_Cat | Category of an Attack Here we have used DDoS attacks, if the label shows 0, there will be no attack, if label will be 1, there will be DDoS attack. | Output/Target Variable with Nine Classes |
| Metric | Description |
|---|---|
| Accuracy | |
| Precision | |
| Recall | |
| F1 Score |
| Model | Accuracy% | Precision% | Recall% | F1 Score% |
|---|---|---|---|---|
| SVM | 99.8 | 99.07 | 98.32 | 98.5 |
| RF | 97.5 | 97.23 | 96.5 | 97.0 |
| KNN | 98.74 | 98.53 | 97.33 | 98.53 |
| Reference | Model | Accuracy % | Dataset |
|---|---|---|---|
| Current Study | SVM, RF, KNN | 99.8, 97.5, 98.74 | Banking Fraud Detection (Kaggle) |
| Dawod et al. [39] | ANN Model | 83.5% | IoT Banking Devices Datasets |
| Hanafizadeh et al. [40] | CNN-LSTM | 78%, 79% | Banking Fraud Time Series Data |
| Yan et al. [41] | SVM | 86.7% | DDoS Datasets |
| Mishra et al. [42] | Trees | 85.55% | DDoS Datasets |
| Gao, Aljuhani, et al. [43,44] | ML (KNN, SVM, ANN) | 83%, 84%, 81% | Banking Datasets |
| Rehman et al. [45] | GRU | 81.7% | DDoS Datasets |
| Guo et al. [46] | ANN, SVM | 88.5%, 91% | Real Time Dataset |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Islam, U.; Muhammad, A.; Mansoor, R.; Hossain, M.S.; Ahmad, I.; Eldin, E.T.; Khan, J.A.; Rehman, A.U.; Shafiq, M. Detection of Distributed Denial of Service (DDoS) Attacks in IOT Based Monitoring System of Banking Sector Using Machine Learning Models. Sustainability 2022, 14, 8374. https://doi.org/10.3390/su14148374
Islam U, Muhammad A, Mansoor R, Hossain MS, Ahmad I, Eldin ET, Khan JA, Rehman AU, Shafiq M. Detection of Distributed Denial of Service (DDoS) Attacks in IOT Based Monitoring System of Banking Sector Using Machine Learning Models. Sustainability. 2022; 14(14):8374. https://doi.org/10.3390/su14148374
Chicago/Turabian StyleIslam, Umar, Ali Muhammad, Rafiq Mansoor, Md Shamim Hossain, Ijaz Ahmad, Elsayed Tag Eldin, Javed Ali Khan, Ateeq Ur Rehman, and Muhammad Shafiq. 2022. "Detection of Distributed Denial of Service (DDoS) Attacks in IOT Based Monitoring System of Banking Sector Using Machine Learning Models" Sustainability 14, no. 14: 8374. https://doi.org/10.3390/su14148374
APA StyleIslam, U., Muhammad, A., Mansoor, R., Hossain, M. S., Ahmad, I., Eldin, E. T., Khan, J. A., Rehman, A. U., & Shafiq, M. (2022). Detection of Distributed Denial of Service (DDoS) Attacks in IOT Based Monitoring System of Banking Sector Using Machine Learning Models. Sustainability, 14(14), 8374. https://doi.org/10.3390/su14148374










