Abstract
With recent advances in mobile and internet technologies, the digital payment market is an increasingly integral part of people’s lives, offering many useful and interesting services, e.g., m-banking and cryptocurrency. The m-banking system allows users to pay for goods, services, and earn money via cryptotrading using any device such as mobile phones from anywhere. With the recent trends in global digital markets, especially the cryptocurrency market, m-banking is projected to have a brighter future. However, information stored or conveyed via these channels is more vulnerable to different security threats. Thus, the aim of this study is to examine the influence of security and confidentiality on m-banking patronage using artificial intelligence ensemble methods (ANFIS, GPR, EANN, and BRT) for the prediction of safety and secrecy effects. AI models were trained and tested using 745 datasets obtained from the study areas. The results indicated that AI models predicted the influence of security with high precision (NSE > 0.95), with the GPR model outperformed the other models. The results indicated that security and privacy were key influential parameters of m-payment system patronage (m-banking), followed by service and interface qualities. Unlike previous m-banking studies, the study results showed ease of use and culture to have no influence on m-banking patronage. These study results would assist m-payment system stakeholders, while the approach may serve as motivation for researchers to use AI techniques. The study also provides directions for future m-banking studies.
1. Introduction
M-banking is a subset of mobile commerce which involves the selling of goods and services, and content generation via radiocommunication devices (i.e., mobile devices) regardless of space or time [1,2]. As mobile commerce (m-commerce) is increasingly becoming popular, m-payment systems (e.g., m-banking and internet banking) continue to ease digital transactions between individuals and organizations [3]. For this study, m-banking is defined as any form of payment for services rendered or in exchange for goods in which a mobile device is used to initiate, approve, and authenticate transactions [4,5,6]. M-banking involves the use of mobile computing devices, such as modern smartphones, to smoothly and seamlessly conduct banking [7]. Therefore, it comprises mobile, electronic, internet, and online banking [8]. In the last two decades, the payment or banking industry experienced rapid and robust development, especially in developed nations. The international digital payment market was valued at USD 3.9 billion in 2019, and it is projected to reach over USD 8.5 billion by the last quarter of 2025 [9,10]. STC Pay Vice president Mr. Alenazi A., during the 2019 ePay Summit, argued that, “in addition to governments’ insistence for cashless society, technological changes, mobile and internet penetrations are other reasons for the payment industry accelerated growth” [10]. Furthermore, m-banking services enable banks and other e-commerce organizations to attain a competitive advantage through the provision of m-banking services such as cryptocurrency trading, and the payment for goods and services. Issues related to the provision of suitable and secure m-banking services are critically important, especially customers’ intent to use, and the continued patronage of m-banking platforms is especially interesting to practitioners and scholars, since “monetary institutions, payment service providers, trusted third parties, systems, and software service providers can benefit greatly from enhanced understanding of the security and privacy issues, and other key factors” undermining m-banking progress, especially in developing nations [10,11].
With growing trends in the virtual coin market (that is, cryptocurrency), m-banking systems and segments are gradually becoming popular in Europe and other parts of the world, especially in African regions [12]. However, different user groups and organizations may perceive m-banking advantages differently and accordingly accept innovative payment platforms. For instance, Kamdjoug [11] argued that Africa is the most multicultural region in the world, as each country has different tribal and cultural groups speaking different languages. While there is a need to understand different user groups’ behaviors and cultures, and the importance of secure m-banking services, few studies have been carried out in an attempt to fill this gap. In view of the present state of m-banking studies, the purpose of this research is to examine safety and secrecy issues affecting continued m-banking patronage. To achieve this objective, four artificial intelligence (AI) models (i.e., adaptive neurofuzzy inference system (ANFIS), Gaussian process regression (GPR), emotional artificial neural network (EANN), and boosted regression tree (BRT)) were employed.
Factors affecting m-banking are usually measured using empirical models such as the technology acceptance model (TAM), the unified theory of acceptance and use of technology (UTAUT), and the DeLone and McLean (D&M) model of information systems, which are time-consuming, and sometimes produce inaccurate and unreliable results [7]. However, the above-mentioned models are still relevant and useful. Cavus [3] argued that empirical models have the disadvantage of being “time-consuming, costly, and unreliable compared to AI-based models”. The authors used two approaches of AI-based and empirical techniques to investigate factors affecting the sustainable growth of m-banking in developing nations. Findings clearly showed that the AI-based technique was more reliable and accurate than the classical approach, as the AI-based method was able to detect and handle hidden data by identifying irrelevant parameters among the study input parameters that were not detected by the empirical approach. Thus, the machine-learning approach was more robust, accurate, flexible, and reliable than the empirical approach.
AI-based techniques have proven to have greater performance in studies that involve investigation of human emotions, attitudes, and behaviour towards computer-based systems due to their robustness and prediction ability compared to conventional models [3,13]. The novelty of this study is that the study presents an all-inclusive, and exceptional results from a cross-country perspective. Also, the study identifies the key security issues associated with m-banking services, assesses the main determinants of m-banking patronage, highlights the robustness, flexibility, accuracy, and prediction powers of AI-based approaches over the usual classical techniques (e.g., “technology acceptance model” (TAM), and “unified theory of acceptance and use of technology” (UTAUT)) used in a large number of m-banking studies.
The study can assist banks and other payment institutions in understanding the influence of security, privacy, and other parameters on m-banking continued patronage and progress not only in the study locations, but in other countries with emerging digital payment systems. Furthermore, findings of the study highlight the prediction ability of machine learning approaches, as the study AI-based models predict the influence of security, and privacy with higher precision compared to other empirical techniques usually used in prior m-banking and m-payments studies. Thus, banks and other financial institutions can use the study findings for improved services.
The remaining sections of this study are arranged as follows: Theoretical background of the study, material and methods were presented in Section 2. Section 3 picks up from where Section 2 stops by presenting and debating the study findings. Lastly, conclusions, suggestions, limitations, and directions for upcoming research are offered in Section 4.
2. Materials and Methods
In this section, the theoretical framework of the paper is developed with the review of conventional “technology acceptance theories”, m-banking system features, challenges, user groups differences, and methods employed.
2.1. Technology Acceptance Models
A quite number of study models have been offered and used to explain different user groups’ sentiments, and behaviour towards computer-based systems usage, in this case m-banking systems. These models comprise of; revised DeLone and McLean [14] model of “Information Systems Success” which highlight the importance of independent variable in information systems research; updated Fishbein, et al. [15] “theory of reasoned action (TRA)”, which describes users’ action from psychological point of view; Davis [16] “technology acceptance model (TAM)”; Ajzen [17] “theory of planned behavior (TPB)”; Venkatesh, et al. [18] extended “unified theory of acceptance and use of technology (UTAUT2)”; and Smith and McSweeney [19] updated “innovation diffusion theory (IDT)” for technologies adoption.
The above-mentioned models are useful, and widely used by information systems scholars to explain users’ technology adoption behaviours in different IT settings (e.g., see [2,16,20]). However, some scholars (e.g., see [3,21,22]) criticized the use of conventional models. The authors argued that the approach is “time consuming, bias in nature, and sometimes produced inaccurate results”, especially, in studies that involve human behaviour, and emotions compared to AI-based models such as “emotional artificial neural network” (EANN), “support vector machine” (SVM), “adaptive neuro fuzzy inference system” (ANFIS), and “boosted regression tree” (BRT).
2.2. Mobile Banking System Features, and Challenges
M-banking is an alternate method of payment in which individuals and organizations use portable devices (e.g., tablets, smart-phones, personal digital assistant (PDA)), or mobile phones to make payment for services rendered, goods, bills and invoice settlement via “wireless communication technologies” such as mobile telephone networks, or imminence technologies [23]. Portable devices can be used for different payments purposes such as digital contents (e.g., ringtones, music, logos, games, or news), concerts, trams, flights and taxis fares, and parking fees. M-banking systems allow individuals to use portable devices to connect to a server to make payment by verifying, authorizing, and confirming completed dealings [1].
M-banking platforms encompass all gadgets (technologies) presented to individual user as well as all tasks performed by the imbursement institutions to carry out such imbursement transactions. In recent past, few number of technology solutions and architectures have been suggested to improve m-banking security, functionalities, scalability, and cost [24,25,26]. M-banking services broadly fall into two main categories: (i) bills and invoices payments and (ii) purchases payments [27]. In bills and invoices payments, the system not only allows access to “computer-based payments”, but also online banking payments, direct debit assignments, and other forms of mobile funds transfers. While in purchase payments, the system competes with or supplements the usual cash, credit or debit cards, cheques, and other touchable transactions.
M-banking platforms allow users to conduct financial dealings of all kinds using any device, anytime, and anyway. However, its development continued to face series of challenges ranging from cultural, information and service excellence, security and secrecy issues, to user authentication challenges, especially in emerging countries. The system comprises of three different parties (i.e., “financial institutions, internet services providers, and telecommunication services providers”), each performing unique value-added services in the payments delivery channel [1,28]. Due to the security and privacy impediments, and dynamism of m-banking dispersion, different standpoints are required to offer explanations for the security, dispersion, and competitive challenges. Prior m-banking studies ignore the importance of safety, secrecy, attractiveness, and continued patronage, especially in emerging digital markets. Therefore, additional research is needed to investigate these issues to determine their influence on users’ continued patronage, and level of attractiveness [25].
Although the above-mentioned theoretical models and systems dispersion have improved our understanding of factors influencing user behaviour and acceptance of m-banking services. However, there is need for further investigation of these factors, and other security and privacy issues involved in m-banking services using different techniques e.g., AI-based methods. While the classical approaches are still valid and useful in scientific research, the authors believe that our choice of AI-based techniques will serve our study objectives better than the conventional theoretical models. Furthermore, the ensemble approach employed can assist in obtaining precise, reliable, and balanced results regarding security and privacy effects on m-banking patronage as argued by Rajaee [21].
2.3. Method
The objective of this study is to examine the effects of security and privacy on m-banking patronage, and progress in the emerging digital markets, and few advanced markets, using artificial intelligence (AI) based techniques. Also, the study intended to identify other key m-banking determinants and the present state of “digital financial market”. Furthermore, the study employed an AI-based collaborative approach (i.e., ensemble methods) to scrutinize the influence of security in the proposed models. Taylor ranking and fit measurement diagram was used to rank the effects of the study autonomous parameters on the reliant parameter. The research focuses on emerging markets such as India, Nigerian, Pakistan, Cyprus, and Iraq.
2.3.1. Study Design and Measurement Scales
The study is a quantitative and cross-country type. The study data collection tool consists of six constructs. Four of the constructs were adopted from prior studies (Lewis [29] and Sharma [30]), while the remaining two were formulated and verified via “exploratory factor analysis using five 5-points Likert scale” as suggested by [31]. Two out of the four adopted constructs have three dimensions each, and the other two have four and six items, u, while the two formulated constructs have five dimensions each. Thus, the study data collection tools comprise of six autonomous parameters with twenty-six items, and one reliant variable (i.e., m-banking). First part of the survey form contained queries about participants’ demographic information such as age, nationality, gender, qualification, and status. While in the second part, information regarding safety and secrecy issues affecting m-banking continued growth were obtained (see, Appendix A).
2.3.2. Data Collection and Sampling Techniques
For sampling techniques, a quota-sampling method was used to gain better judgements form different sections of the study areas (Nigeria and Cyprus) regarding the effects of security and privacy on m-banking services. The survey hyperlink was sent to various participants comprising of students, academics, business individuals, and other civil servants via social media flatforms (e.g., Facebook, WhatsApp, LinkedIn, and Instagram). A total of 801 responses were received, out of which 745 (93%) were found to be valid, and useful, which is an excellent return rate [32]. Also, the authors sent private emails to some selected banks, informing them about the purpose of the research, and request for information regarding customers patronage, and security challenges. 427 (57.3%) responses were collected from Nigeria, and 318 (42.7%) from Cyprus. To ensure proper selection of security and privacy determinants, private emails were also sent to eight cyber security specialists. The security experts checked and confirmed that the study constructs items covered all aspects of security challenges facing the global digital payment markets.
2.3.3. Data Examination Techniques
The undertaken study employed artificial intelligence (AI) based methods. Thus, the study data were processed and examined using statistical packages (i.e., SPSS 26.0) and simulation software (i.e., MATLAB 2021b). The SPSS package was used to analyze respondents’ demographic information, and checked the consistencies level of the study constructs items i.e., “exploratory factor analysis” (EFA). The EFA results for all of the constructs stood above 0.80 (see, Appendix B) indicating an outstanding reliability amongst the items [33]. Simulation software (i.e., MATLAB 2021b) was used in training, testing, and validation of the study AI-based models in order to obtain predictions regarding the influence of the study autonomous variables on the reliant factor, and sigmaPlot software was used to export and depict the study charts and figures.
2.4. Artificial Intelligence Techniques
Recently, several m-banking studies were conducted in an attempt to discover key determinants of m-banking success in both emerging and developed digital markets e.g., see [3,10,27,28]. These factors are usually assessed using conventional models such as “technology acceptance model” (TAM), “unified theory of acceptance and use of technology” (UTAUT), and “innovation diffusion theory” (IDT) for technology espousal. Though these models are still relevant and useful, some scholars criticized the use of models. For instance, Nourani, Gökçekuş, and Umar [13] argued that “predictions based on these approaches are usually time consuming, bias-based, and sometimes produce inaccurate and unreliable results” compared to AI-based approaches. Additionally, studies have shown that artificial intelligence (AI) has proven to have greater performances in research that are complex in nature (e.g., people attitudes, emotions, and cultural values) due to their robustness, flexibility, and prediction ability” [3]. Thus, this study employed four AI techniques: “adaptive neuro fuzzy inference system” (ANFIS), “Gaussian process regression” (GPR), “emotional artificial neural network” (EANN), and “boosted regression tree” (BRT) in order to overcome the limitations of the classical approaches used by prior m-banking studies.
2.5. Ensemble Techniques
Ensemble approach is a “machine learning technique” (ML) in which prediction results of separate models are combined to enhance the performance of the final model i.e., the study reported model. Also, studies have shown that “different approaches may provide different results for a particular problem” [13,34]. At present, use of collaborative methods in science and engineering-based research have proven to be efficient, and produced better results than sole modelling methods. Thus, the study employed the techniques (i.e., ensemble techniques) to boost the performance of the study separate AI models so that precise and reliable results can be obtained. Structures of the study AI models (ANFIS, GPR, EANN, and BRT) were presented in the subsequent subsections.
2.5.1. ANFIS Model
As shown in Figure 1, the study ANFIS structure comprises of five layers: (i) the fuzzifying layer, which transports the inputs values and determines their membership functions; (ii) the implication layer, which generates the firing strengths for the network rules; (iii) the normalizing layer which normalized the calculated firing strengths of each of the study inputs in order to have a balance firing strengths amongst the inputs; (iv) the defuzzifying layer which is responsible for taken the normalized values of the study parameters to the fifth layer; and (v) the aggregation layer, which is the final layer is responsible for the return of final outcome (i.e., prediction result), in this case the predicted influence of the study inputs on m-banking system attractiveness. El-Hasnony, [34] in their study argued that “ANFIS is one of the best techniques among machine learning (ML) methods, and can produce valid results in studies that involves human feeling and emotions such as that of m-banking, and Internet of Things” (IoT). The authors stressed that accuracy of an ANFIS model largely depends on its input parameters, and may outperform other ML models (e.g., GPR, and BRT) in hybrid regression problems. The green color represent the number layers, while light pink represent the inputs parameters, the light blue and yellow colors represents the hidden layers, and dark green is the output of the model.
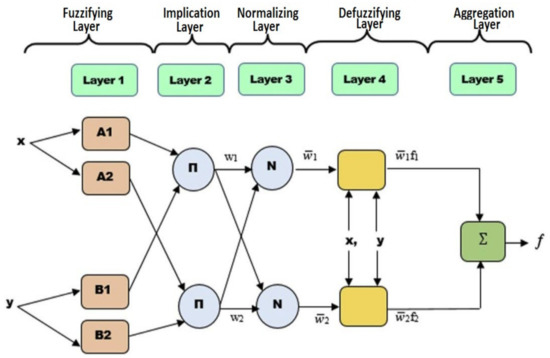
Figure 1.
Study ANFIS model structure.
2.5.2. GPR Model
The study GPR model is offered in Figure 2, consisting of two major components; the estimation component, and the gaussian regression component, where U denote the gaussian elements (GU), while Y denote the outcome (i.e., targeted output), and K and 0 represent the covariance and mean of the study variables (i.e., autonomous and reliant variables of (x and y)), as shown in Figure 2.
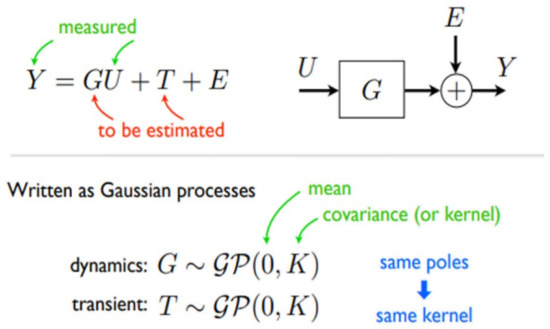
Figure 2.
Study GPR model structure.
2.5.3. EANN Model
Emotional artificial neural network (EANN) was used to evaluate the emotional aspects of the study construct to determine participants feelings regarding the safety of their funds, and other sensitive information on m-banking flatforms. EANN is an improved version of artificial neural network (ANN) which allows neurons to produce hormones for changing cognitive, emotional, and physical capacities. The general structure of the study EANN comprises of three key units, hormones weights adjustment unit (Ha, Hb, and Hc), the neurons’ output and input unit, and the bias values and synopsis functions unit as shown in Figure 3.
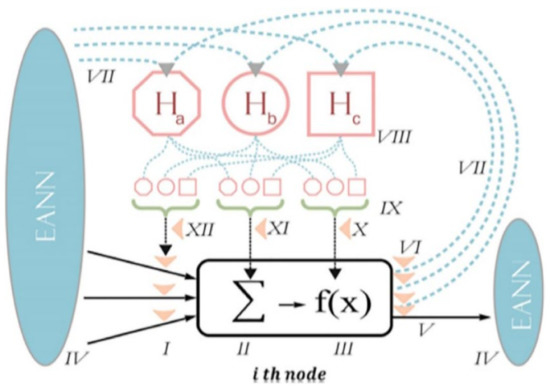
Figure 3.
Study EANN model structure [35].
As seen in Figure 3, the study EANN model has three hormones’ secretors with ith nerve-cell output. The ith nerve-cell output was explained using Equation (1) as per [36].
where j, h, and I represent the output, hidden, and inputs neurons respectively, f represent the neuron function activator, while ∂, ζ, Φ, and χ represent the function weight activation values, and γ, β, θ, and α represent the neurons weights. The model hormones values were assessed and enforced on the neuron network using Equations (2) and (3) as suggested by [35].
Hi,h = glandity i,h x Yi
2.5.4. BRT Model
The study BRT model contains three hierarchies as shown in Figure 4: an input regression ladder, normalization regression ladder, and output ladder. The study input values were inputted into the input ladder which transported them to the normalization ladder for weights adjustment, then to the output ladder for predictions. The red lines and dots indicates the margin of errors in the model regression process. Figure 4 depicts the diagram of the study BRT model.
Figure 4.
Study BRT model structure.
2.6. Data Normalization, Models Validation and Performance Comparisons
The study data normalization method, models’ validation and performance assessments indices were offered in the following subsections.
2.6.1. Data Normalization
Normalization of study inputs simplifies arithmetic calculations in “AI-based modelling and simulation, which in turn reduces results processing time, and increases models’ accuracy” [13,37]. Thus, data for the study were normalized using Max-Min normalization formular as given in Equation (4).
where Nnorm stands for the variable to be normalized, while N, Nmin, and Nmax represent the input, minimum, and maximum observed values, respectively.
2.6.2. Models’ Validation, and Performance Comparisons
The main reason for using AI models for regression problems is to obtain reliable and accurate results, which are usually hard to achieve using conventional approaches without deep understanding and past knowledge of the concept. But, owing to overfitting issues in several AI models, performance of the models at the testing phase is not always consistent with the training phase performance, making it difficult if not impossible for researchers to obtain correct results for hidden datasets. This and other reasons necessitate the needs for models’ validation to overcome the overfitting problems. There are different kinds of validation methods (e.g., leave-one-out validation, k-fold cross-validation, and holdout validation etc.). Thus, this research employed the k-fold cross-validation using five regression problems assessment metrics (namely Nash-Sutcliffe efficiency (NSE), i.e., coefficient of determination, root mean square error (RMSE), mean absolute error (MAE), mean absolute percentage error (MAPE), and relative root mean square error (rRMSE)) to assess the models training and testing results. The five arithmetic metrics were described using Equations (5)–(9), respectively, as per [35].
Overall proposed procedure for conducting the study is presented in Figure 5, comprising of four key steps. The four different colors represent the experimental stage, single modelling stage, fitness levels of the models, and the estimated security influence respectively. While the green color represents the training and testing data proportion percentages.
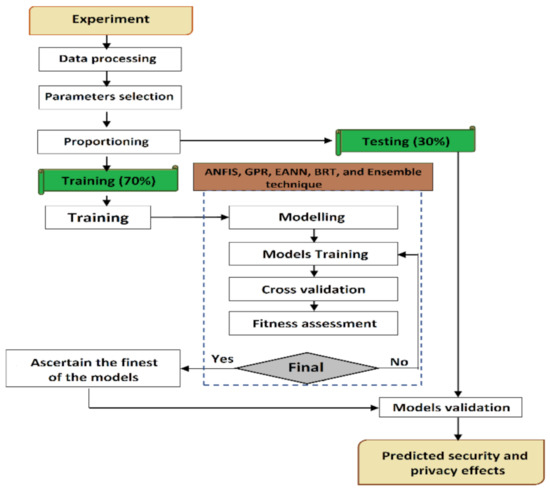
Figure 5.
Study proposed methodology structure.
3. Results and Discussion
In this section, sensitivity examination, models validation, fitness assessment, models prediction, and parameters influence ranking results were offered.
3.1. Sensitivity Examination Results
Use of pertinent input parameters in machine learning modelling is essential in achieving desired and suitable results. While, inclusion of insignificant parameters on the other hand not only reduces model precision but also increase computing time and cost [13].
Sensitivity examination is an important instrument for removing insignificant parameters in AI models. For this study, the method was used to select the most significant parameters from all of the conceivable inputs used in the experiment. The nearer the parameter value to 1, the higher the correlation with the reliant variable vice versa. The study sensitivity examination result is presented in Table 1, using Equation (10).
where Ns denote the value of mean for the study conceivable inputs, n denote the sum of observations made. While Nobs represents the observed influence of the parameters, and Npre is the forecasted influence of the parameters used in the study.

Table 1.
Results of sensitivity examination.
As seen in Table 1, security and privacy parameters are the most relevant parameters in terms of influence on m-banking attractiveness and continued patronage in the study areas (i.e., Nigeria and Cyprus) with DC values of 0.9991 and 0.9899, respectively. Service excellence and interface quality came third and fourth with DC values of 0.8693 and 0.8211, respectively, while ease of use and culture were the least important parameters with DC values of 0.4762 and 0.4386, thus being excluded from the experimental datasets (as their inclusion will reduce the models’ accuracy).
3.2. AI Models Results and Discussion
In this study, four AI models (ANFIS, GPR, EANN, and BRT) were employed to model the influence of security and privacy on m-banking attractiveness, and patronage in the study areas, and performance of the study models in both confirmation and training were assessed using “k-fold cross-validation” with five arithmetic assessment metrics of; NSE, RMSE, MAE, MAPE, and rRMSE, and the results were offered in Table 2. The arithmetic assessment metrics used involved computing both fitness level and forecasting error of the models as both are essential for assessing the efficacy of any AI models. Based on the results, it can be understood that the GRP model outperformed the other models with NSE 0.9999, RMSE 0.0001, MAE 0.0002, MAPE 0.0123, and rRMSE 0.0147 in the confirmation phases, followed by the EANN model with NSE, RMSE, MAE, MAPE, and rRMSE values of 0.9998, 0.0009, 0.0037, 0.0623, and 0.0792, respectively. While ANFIS and BRT models came third and fourth in the testing performance ranking. Cai, et al. [38] argued that “GPR model usually has the highest forecasting ability compared to other AI models due its flexibility, and ability in handling data uncertain via its kernel functions”. As shown in Table 2, performance of the GPR model significantly improved in the confirmation phase compared to other models.

Table 2.
AI models performance metrics.
As shown in Table 2, all of the study’s developed models have perform excellently in both confirmation and training phases as their rRMSE values stood at <10%. An rRMSE values below 10% is considered to be an excellent result, while values between 11–20% good, 21–30% fair, and above 30% poor [39]. Another essential pointer that determined model predicting skill is MAPE [40]. The lesser the model MAPE value, the higher the precision of the model. Table 2 clearly indicates that GPR has the least MAPE values (0.0123) compared to other models, signifying the model forecasting skill above others. Furthermore, the fitness level of the models was checked using scatter plots as shown in Figure 6 and Figure 7, (i.e., training and testing scatter plots), GPR and EANN models have better fitness level as the models’ observed data are more flattened along the bisector diagonal than the other models (ANFIS and BRT). The greater performance displayed by the AI models may not be unconnected with the models’ ability to capture and generalize both nonlinear and linear patterns of study datasets. Table 2 depicts the performance of the AI-based employed models in training and testing phases.
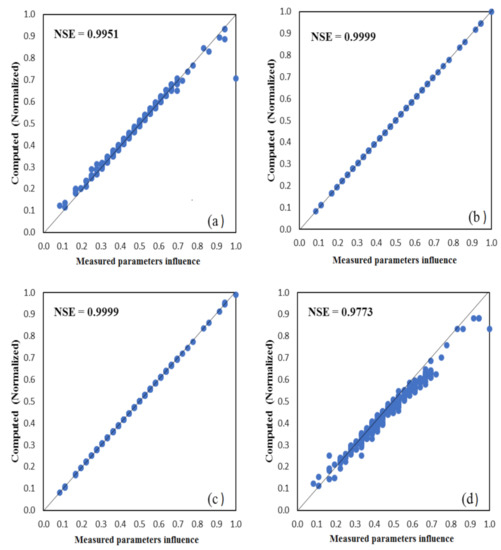
Figure 6.
Training scatter plots between observed and computed parameters influence on m-banking attractiveness by (a) ANFIS, (b) GPR, (c) EANN, and (d) BRT.
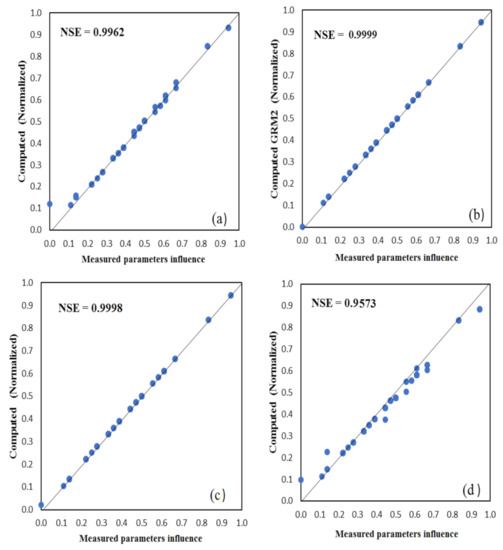
Figure 7.
Testing scatter plots between observed and computed parameters influence on m-banking attractiveness by (a) ANFIS, (b) GPR, (c) EANN, and (d) BRT.
As shown in Figure 8, the radar plot was used to depict the predictions made by the developed models, and further examined the correctness and stability of the employed models. A model with slight difference between NSE and RMSE values in both training and confirmation phases is a stable model. Thus, based on Table 2 results, it can be said that GRP is the most stable and accurate model with the same NSE and RMSE values in both verification and training phases compared to other models. The GPR model shows the same steadiness even in the radar plot.
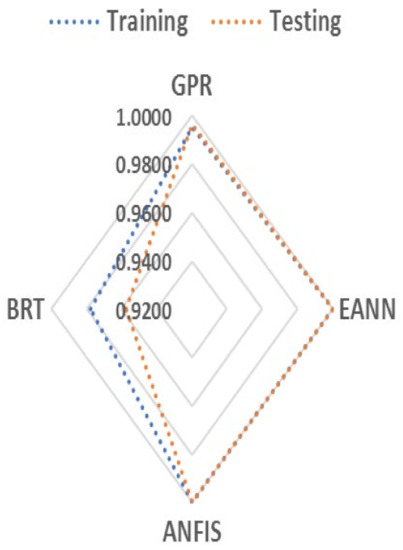
Figure 8.
Study radar plot for comparing the correctness and steadiness of the AI models using NSE training and confirmation phases values.
As seen in Figure 8, 1.0000 value at the top left in the radar plot represents the target result, while the remaining four values of 0.9800, 0.9600, 0.9400, and 0.92000, respectively, represent the models’ prediction concerning security and privacy influence on m-banking continual usage. Furthermore, the Taylor diagram for measuring “goodness of fit” and ranking of input parameters was used to further assess the performance of the study AI models, and confirm the prediction results obtained from the models with regards to the influence of the study input parameters on m-banking continued patronage in the study areas (i.e., Nigeria and Cyprus). The diagram offers reliable and accurate means of assessing models’ performance, and parameters ranking by comparing three statistical indices (i.e., correlation coefficient, RMSE, and standard deviation) in a graphical manner to assess the relative performance of different models. As shown in Figure 9 and Figure 10, the association between the fields is represented by the “azimuthal position of the test field, while the standard deviation of the pattern is the radial measured from the origin, and the RMSE cantered value is proportional to the distance between the actual and the estimated fields with the same units as the standard deviation” in the diagram [41]. When there is an increase in the association value, the RMSE value decreases vice versa. Thus, a perfect model “is the one separated by the reference point with the correlation coefficient equivalent to 1, and similar abundance of varieties contrasted with the observation” [42]. Just such as the scatter and radar plots results, the Taylor diagram results also show that all of the four AI (ANFIS, GPR, EANN, and BRT) models have an accurate prediction ability, with correlation coefficient values greater than 0.95 in the confirmation phase and greater than 0.9 in the training phase. Additionally, the models’ standard deviation values are lesser than the actual data with minor variation suggesting that the overestimation results of the models does not in any way influenced the performance of the models. Also, based on the Taylor results, it can be said that the GPR model outshined the other models in terms of prediction skill as the model perfectly predicts the security and privacy influence on m-banking in both training and confirmation phases. This result is in contrast with the findings of El-Hasnony, [34] who argued that ANFIS may outperform other machine learning (ML) methods such as BRT, and GPR in hybrid ML regression problems. Based on the studied Taylor diagram, the studied AI models were ranked as follows: (1) GPR, (2) EANN, (3) ANFIS, and (4) BRT (as shown in Figure 9 and Figure 10).
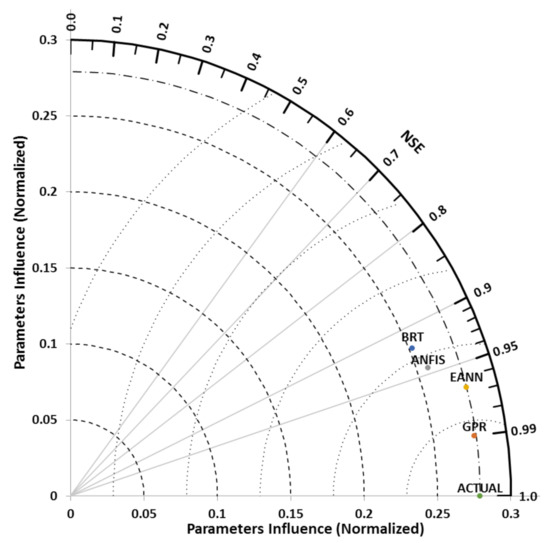
Figure 9.
Training stage performance comparisons of the study models using the Taylor diagram.
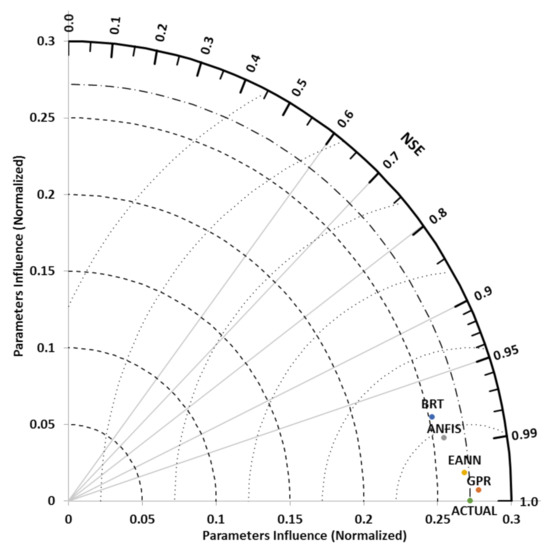
Figure 10.
Testing stage performance comparisons of the study models using the Taylor diagram.
Two parameters (i.e., ease of use and culture) were excluded from the research experimental data due to low DC values as shown in Table 1 (i.e., sensitivity analysis results). The two parameters were later assessed using the same validation assessment metrics as per Table 2, and inclusively ranked with the other parameters (i.e., security, privacy, service excellence, and interface quality) using Taylor diagram to validate the sensitivity examination results, and further determine whether the two are relevance or otherwise by checking the parameters standard deviations and correlations via Taylor diagram. Based on the Taylor ranking results, the correlation values for the excluded parameters were far away from the maximum correlation values of 1. In terms of correlation, the diagram ranked the parameters as follows: (1) security, (2) privacy, (3) service excellence, (4) interface quality, (5) ease of use, and (6) culture (as shown in Figure 11).
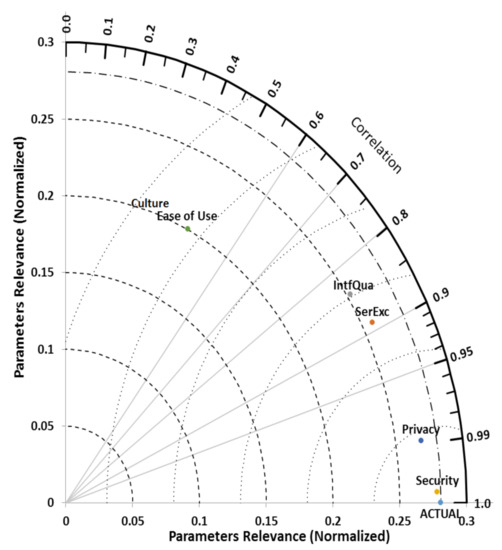
Figure 11.
Parameters’ relevance ranking using the Taylor diagram.
Based on the models’ prediction results, it can be said that security and privacy were the two leading parameters influencing m-banking attractiveness, and continued patronage which in turn affects its continued growth in the study areas (i.e., Nigeria and Cyprus), followed by service and interface quality parameters. As shown in Figure 8, the models’ prediction results of 0.9800, 0.9600, 0.9400, and 0.9200 for GPR, EANN, ANFIS, and BRT respectively, clearly indicate that people concern for security and privacy with regards to “m-banking platforms” were the major reasons for the sluggish progress of m-payment systems in the study locations. This result is supported by the findings of Moghavvemi, [5] that “protection and secrecy issues were the major obstacles to m-banking progress not only in emerging markets but also in advanced markets”. For service and interface parameters, the results indicate that there is a strong correlation between “m-banking platforms” and the quality of interface and service offered. As shown in Figure 11, (Taylor diagram parameters ranking results) the two parameters were found to be relevant as their correlation values of 0.8761 and 0.8211 were close to the maximum correlation value of 1 signifying an association with the reliant parameter (i.e., m-banking). This finding is reinforced by the results of Zhou [43], and Choi [44], who argued that in addition to safety and confidentiality issues, “service excellence and interface quality” may likely have negative influence on “m-banking” patronage not only in emerging markets but also in advanced markets.
For the two excluded parameters (i.e., ease of use and culture), based on the Taylor ranking results (Figure 11) and sensitivity examination results (Table 1), it was discovered that the two parameters were found to be irrelevant as their DC and ranking values were less than 0.5 indicating an insignificant association with the study reliant variable. This result is in contrast with the findings of Rahman [45], Lu [46], and Al-Okaily [47], who stressed that “peoples’ culture influenced their intention to use m-banking and other m-payment systems”, especially in multilingual countries. However, our findings clearly show that culture is not as important as before, since people are now more concerned about the safety and secrecy of their funds and other confidential information than their cultural values as predicted by all the study proposed models. Precision of the study findings may not be unconnected with the study choice of EANN which is a new version of ANN with higher prediction ability, and the use of Taylor diagram to rank the study models and determine the influence of the study input parameters on m-banking continued patronage and progress. Also, the study sensitivity examination result is supported by the findings of Chenarlogh [48], Roshani [49], and Jafari [50], who stressed that machine learning approach (e.g., ANN, ANFIS, and EANN) may produce more accurate and reliable results than the empirical approaches. Furthermore, Azimirad [51] in their study argued that hybrid machine learning techniques can improve study outcomes not only in engineering problems, but also in computer-based studies.
4. Conclusions
In this research, four different machine learning techniques (i.e., GPR, EANN, ANFIS, and BRT) were employed to study and model the influence of system security, ease of usage, secrecy, service and interface qualities, and culture on “m-banking” continued patronage in emerging digital markets. All the study’s proposed AI models performed excellently in both training and confirmation stages, and perfectly predicted the influence of the study considered input parameters on “m-banking” continued patronage and progress in the study areas (i.e., Nigeria and Cyprus) with higher accuracy as all of the models NSE values were > 0.95 indicating a strong correlation between the reliant and autonomous parameters. But although all of the models performed pretty-well, the GPR model outshined the other models with the following values in the confirmation stage; NSE = 0.9999, RMSE = 0.0001, MAE = 0.0002, MAPE = 0.0123, and rRMSE = 0.0147, respectively. This may not be unconnected with the model’s ability to handle undefined experimental datasets compared to other ML models, e.g., CNN, ANN, BRT, EANN, and ANFIS etc. Prior to the development of the study proposed models, sensitivity examination techniques were used in choosing relevant input parameters. The sensitivity investigation results indicated that all of the study autonomous parameters are relevant except ease of use and culture which are found to be statistically irrelevant with DC values < 0.5. Furthermore, Taylor diagram was used to rank the parameters, and the diagram shows the same sign as per the sensitivity outcome. Thus, this was excluded from the study experimental datasets. The undertaken study findings highlighted the skill, reliability, and robustness of the “machine learning techniques” in terms of prediction of safety and secrecy influence on m-banking continued patronage and progress in emerging digital markets with high precision. Also, the study results clearly show that security and privacy were the main factors responsible for people’s lack of interest or continued patronage of m-banking services, followed by quality of m-banking services offered and interface quality. Stakeholders in the “Digital payment markets” can use the study results to address some of the security challenges confronting m-banking continued patronage not only in emerging digital markets, but also in advanced markets. Also, the study approaches can serve as motivation for researchers to employ “machine learning techniques” in future research, although the study developed AI models and Taylor diagrams have proven to be more accurate and robust. The study is limited to the dataset used, the study areas which are emerging digital markets, and the approach employed. Thus, future research should employ other “machine learning” techniques (e.g., ensemble tree (LSBOOST) and multiple linear regression (MLR)) to further investigate the influence of security and confidentiality on m-banking patronage not only in emerging digital payment markets, but also in advance markets.
Author Contributions
Methodology, N.C., Y.B.M., A.Y.G., M.L.I., A.H. and M.B.; conceptualization, N.C., Y.B.M., A.M.T., D.M., A.Y.G. and M.B.; investigation, N.C., Y.B.M., D.M., A.M.T., M.B., M.L.I. and A.H.; data curation, M.B., A.Y.G., A.H., M.L.I., A.H., D.M., Y.B.M. and N.C.; writing, N.C., Y.B.M., A.Y.G. and D.M.; writing—review and editing, N.C., Y.B.M., A.M.T., A.H., D.M., M.L.I. and A.M.T. All authors have read and agreed to the published version of the manuscript.
Funding
The study is funded by the authors.
Institutional Review Board Statement
The study was conducted according to the guidelines of the Declaration of Helsinki, and it was approved by the Scientific Research Ethics Committee of Near East University with approval number (NEU/AS/2021/138) dated 7 December 2021.
Informed Consent Statement
Informed consent statement was sent to all study participants, and they have all assent to it.
Data Availability Statement
The study data is available on request at Near East University, Nicosia, Cyprus, Department of Computer Information Systems, or via the corresponding author.
Acknowledgments
The authors wish to thank the Nigerian Banks for their role toward successful completion of this work, and participants who take much of their time to provide the authors with the necessary data. Additionally, we wish to appreciate the security experts that helps in assessing the entire study procedures.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A
Section (A)—General
Kindly tick (√) the following answer concerning your demographic information.

Table A1.
Demographic Information.
Table A1.
Demographic Information.
| 1. Gender | ( ) Male | ( ) Female | ||
| 2. Age group | ( ) 18–25 | ( ) 26–35 | ( ) 36 and above | |
| 3. Education level | ( ) SSCE | ( ) ND | ( ) Barchelor/HND | 3. Education level |
| 4. Employment Status | ( ) Academics | ( ) Students | ( ) Banking Staff | ( ) Security expert |
| 5. Nationality | ( ) Nigeria | ( ) Cyprus |
Note: SSCE = Senior School Certificate; ND = National Diploma; HND = Higher National Diploma.
Section (B)—Responses
“Please kindly tick (√) the response that best reflects your beliefs with respect to the developed user-authentication mobile apps for m-banking 1 to 5 Likert scale ranging from (1) strongly disagree, (2) disagree, (3) neutral, (4) agree and (5) strongly agree”.

Table A2.
Participants Responses.
Table A2.
Participants Responses.
| Items | Sd | D | N | A | Sa | |
|---|---|---|---|---|---|---|
| H1 | Ease of use (Lewis, 2006) | |||||
| EoU1 | “Overall, I am satisfied with how easy it is to use this System” | |||||
| EoU2 | “It was simple to use this system” | |||||
| EoU3 | “I was able to complete the tasks and scenarios quicklyusing this system” | |||||
| EoU4 | “I felt comfortable using this system” | |||||
| EoUe5 | “It was easy to learn to use this system”. | |||||
| EoU6 | “I believe I could be protected using this System” | |||||
| H2 | Privacy (Authors of this study) | |||||
| Priv1 | “I fear that while I am paying a bill by mobile phone, I might make mistakes since the correctness of the inputted information is difficult to check from the screen” | |||||
| Priv2 | “I fear that while I am using mobile banking services, the Government can intercept my personal information” | |||||
| Priv3 | “I fear that while I am using mobile banking services, third parties can access my account or see my account information” | |||||
| Priv4 | “I fear that the list of PIN codes may be lost and end up in the wrong hands” | |||||
| Priv5 | “Generally, I fear that my personal information can be accessed through m-banking platform” | |||||
| H3 | Interface quality (Shama, 2019; Lewis, 2006) | |||||
| IntQual1 | “The interface of this system was pleasant”. | |||||
| IntQual2 | “I liked using the interface of this system”. | |||||
| IntQual3 | “This system has all of the functions and capabilities I expect it to have” | |||||
| IntQual4 | “Overall, I am satisfied with this system” | |||||
| H4 | System Security (Authors of this study) | |||||
| SysSq1 | “The security features of the system are pleasant to me” | |||||
| SysSq2 | “Velocity anomalies during login can be handle by the system” | |||||
| SysSq3 | “The authentication process provided in the system is more reliable, robust, and can help safeguard customers funds” | |||||
| SysSq4 | “The system is capable of handling DDoS attacks” | |||||
| SysSq5 | “In general, I am satisfied with the level of security provided in the systems” | |||||
| H5 | Service quality (Shama, 2019; Lewis, 2006) | |||||
| SQ1 | “The call centre representatives always help me when I need support with m-banking” | |||||
| SQ2 | “The call centre representatives always pay personal attention when I experience problems with m-banking” | |||||
| SQ3 | “The call centre representatives have adequate knowledge to answer my queries related to m-banking” | |||||
| H6 | Cultural values (Shama, 2019) | |||||
| CV1 | “People who are important to me think that I should use Mobile banking apps” | |||||
| CV2 | “People who influence my behaviour think that I should use Mobile banking apps” | |||||
| CV3 | “People whose opinions that I value prefer that I use Mobile Banking” | |||||
| CV4 | “Generally, my culture encourages the use of m-banking services” |
Appendix B

Table A3.
Sample demographic distribution.
Table A3.
Sample demographic distribution.
| Demographic Variable | Frequencies | Percentage |
|---|---|---|
| Nationality | ||
| Nigeria | 427 | 57.3 |
| Cyprus | 318 | 42.7 |
| Gender | ||
| Male | 411 | 55.2 |
| Female | 334 | 44.8 |
| Age group | ||
| 18–25 | 241 | 32.3 |
| 26–35 | 381 | 51.2 |
| 36 and above | 123 | 16.5 |
| Educational qualification | ||
| SSCE | 73 | 9.8 |
| ND | 110 | 14.8 |
| Bachelor/HND | 397 | 53.3 |
| Masters or higher | 165 | 22.1 |
| Employment status | ||
| Academics | 173 | 23.2 |
| Students | 368 | 49.4 |
| Other civil servants | 89 | 11.9 |
| Business | 107 | 14.4 |
| Security experts | 8 | 1.1 |
References
- Kim, C.; Mirusmonov, M.; Lee, I. An empirical examination of factors influencing the intention to use mobile payment. Comput. Hum. Behav. 2010, 26, 310–322. [Google Scholar] [CrossRef]
- Park, J.; Amendah, E.; Lee, Y.; Hyun, H. M-payment service: Interplay of perceived risk, benefit, and trust in service adoption. Hum. Factors Ergon. Manuf. Serv. Ind. 2019, 29, 31–43. [Google Scholar] [CrossRef]
- Cavus, N.; Mohammed, Y.B.; Yakubu, M.N. An Artificial Intelligence-Based Model for Prediction of Parameters Affecting Sustainable Growth of Mobile Banking Apps. Sustainability 2021, 13, 6206. [Google Scholar] [CrossRef]
- Zhou, L.; Gozgor, G.; Huang, M.; Lau, M.C.K. The impact of geopolitical risks on financial development: Evidence from emerging markets. J. Compet. 2020, 12, 93. [Google Scholar] [CrossRef]
- Moghavvemi, S.; Mei, T.X.; Phoong, S.W.; Phoong, S.Y. Drivers and barriers of mobile payment adoption: Malaysian merchants’ perspective. J. Retail. Consum. Serv. 2021, 59, 102364. [Google Scholar] [CrossRef]
- Lee, S.-J.; Rho, M.J.; Yook, I.H.; Park, S.-H.; Jang, K.-S.; Park, B.-J.; Lee, O.; Lee, D.K.; Kim, D.-J.; Choi, I.Y. Design, development and implementation of a smartphone overdependence management system for the self-control of smart devices. Appl. Sci. 2016, 6, 440. [Google Scholar] [CrossRef] [Green Version]
- Nguyen, O.T. Factors affecting the intention to use digital banking in Vietnam. J. Asian Financ. Econ. Bus. 2020, 7, 303–310. [Google Scholar] [CrossRef]
- Malaquias, R.F.; Hwang, Y. An empirical study on trust in mobile banking: A developing country perspective. Comput. Hum. Behav. 2016, 54, 453–461. [Google Scholar] [CrossRef]
- Kaur, S.J.; Ali, L.; Hassan, M.K.; Al-Emran, M. Adoption of digital banking channels in an emerging economy: Exploring the role of in-branch efforts. J. Financ. Serv. Mark. 2021, 26, 107–121. [Google Scholar] [CrossRef]
- Alkhowaiter, W.A. Digital payment and banking adoption research in Gulf countries: A systematic literature review. Int. J. Inf. Manag. 2020, 53, 102102. [Google Scholar] [CrossRef]
- Kamdjoug, J.R.K.; Wamba-Taguimdje, S.-L.; Wamba, S.F.; Kake, I.B. Determining factors and impacts of the intention to adopt mobile banking app in Cameroon: Case of SARA by afriland First Bank. J. Retail. Consum. Serv. 2021, 61, 102509. [Google Scholar] [CrossRef]
- Momtaz, P.P. The pricing and performance of cryptocurrency. Eur. J. Financ. 2021, 27, 367–380. [Google Scholar] [CrossRef]
- Nourani, V.; Gökçekuş, H.; Umar, I.K. Artificial intelligence based ensemble model for prediction of vehicular traffic noise. Environ. Res. 2020, 180, 108852. [Google Scholar] [CrossRef] [PubMed]
- DeLone, W.H.; McLean, E.R. The DeLone and McLean model of information systems success: A ten-year update. J. Manag. Inf. Syst. 2003, 19, 9–30. [Google Scholar] [CrossRef]
- Fishbein, M.; Ajzen, I.; Albarracin, D.; Hornik, R. A reasoned action approach: Some issues, questions, and clarifications. In Prediction and Change of Health Behavior; Lawrence Erlbaum Associates, Inc.: Mahwah, NJ, YSA, 2007; pp. 281–295. [Google Scholar] [CrossRef]
- Davis, F.D. Perceived usefulness, perceived ease of use, and user acceptance of information technology. MIS Q. 1989, 19, 319–340. [Google Scholar] [CrossRef] [Green Version]
- Ajzen, I. The theory of planned behavior. Organ. Behav. Hum. Decis. Processes 1991, 50, 179–211. [Google Scholar] [CrossRef]
- Venkatesh, V.; Thong, J.Y.; Xu, X. Consumer acceptance and use of information technology: Extending the unified theory of acceptance and use of technology. MIS Q. 2012, 36, 157–178. [Google Scholar] [CrossRef] [Green Version]
- Smith, J.R.; McSweeney, A. Charitable giving: The effectiveness of a revised theory of planned behaviour model in predicting donating intentions and behaviour. J. Community Appl. Soc. Psychol. 2007, 17, 363–386. [Google Scholar] [CrossRef]
- Merhi, M.; Hone, K.; Tarhini, A. A cross-cultural study of the intention to use mobile banking between Lebanese and British consumers: Extending UTAUT2 with security, privacy and trust. Technol. Soc. 2019, 59, 101151. [Google Scholar] [CrossRef]
- Rajaee, T.; Ebrahimi, H.; Nourani, V. A review of the artificial intelligence methods in groundwater level modeling. J. Hydrol. 2019, 572, 336–351. [Google Scholar] [CrossRef]
- Ghiasi, R.; Ghasemi, M.R.; Noori, M. Comparative studies of metamodeling and AI-Based techniques in damage detection of structures. Adv. Eng. Softw. 2018, 125, 101–112. [Google Scholar] [CrossRef]
- Kumar, V.; Lai, K.-K.; Chang, Y.-H.; Bhatt, P.C.; Su, F.-P. A structural analysis approach to identify technology innovation and evolution path: A case of m-payment technology ecosystem. J. Knowl. Manag. 2020, 25, 477–499. [Google Scholar] [CrossRef]
- De Reuver, M.; Ondrus, J. When technological superiority is not enough: The struggle to impose the SIM card as the NFC Secure Element for mobile payment platforms. Telecommun. Policy 2017, 41, 253–262. [Google Scholar] [CrossRef]
- Téllez, J.; Zeadally, S. Architectures and Models for Mobile Payment Systems. In Mobile Payment Systems; Springer: Berlin/Heidelberg, Germany, 2017; pp. 35–91. [Google Scholar] [CrossRef]
- Teng, S.; Khong, K.W. Examining actual consumer usage of E-wallet: A case study of big data analytics. Comput. Hum. Behav. 2021, 121, 106778. [Google Scholar] [CrossRef]
- Pal, A.; Herath, T.; Rao, H.R. Why do people use mobile payment technologies and why would they continue? An examination and implications from India. Res. Policy 2021, 50, 104228. [Google Scholar] [CrossRef]
- Baabdullah, A.M.; Alalwan, A.A.; Rana, N.P.; Kizgin, H.; Patil, P. Consumer use of mobile banking (M-Banking) in Saudi Arabia: Towards an integrated model. Int. J. Inf. Manag. 2019, 44, 38–52. [Google Scholar] [CrossRef] [Green Version]
- Lewis, J.R. Sample sizes for usability tests: Mostly math, not magic. Interactions 2006, 13, 29–33. [Google Scholar] [CrossRef]
- Sharma, S.K. Integrating cognitive antecedents into TAM to explain mobile banking behavioral intention: A SEM-neural network modeling. Inf. Syst. Front. 2019, 21, 815–827. [Google Scholar] [CrossRef]
- Shen, W.; Zhou, M.; Yang, F.; Yu, D.; Dong, D.; Yang, C.; Zang, Y.; Tian, J. Multi-crop convolutional neural networks for lung nodule malignancy suspiciousness classification. Pattern Recognit. 2017, 61, 663–673. [Google Scholar] [CrossRef]
- Ungerman, O.; Dedkova, J.; Gurinova, K. The impact of marketing innovation on the competitiveness of enterprises in the context of industry 4.0. J. Compet. 2018, 10, 132. [Google Scholar] [CrossRef]
- Sharma, P.; Machiwal, D. Streamflow forecasting: Overview of advances in data-driven techniques. In Advances in Streamflow Forecasting; Elsevier: Amsterdam, The Netherlands, 2021; pp. 1–50. [Google Scholar] [CrossRef]
- El-Hasnony, I.M.; Barakat, S.I.; Mostafa, R.R. Optimized ANFIS model using hybrid metaheuristic algorithms for Parkinson’s disease prediction in IoT environment. IEEE Access 2020, 8, 119252–119270. [Google Scholar] [CrossRef]
- Nourani, V. An emotional ANN (EANN) approach to modeling rainfall-runoff process. J. Hydrol. 2017, 544, 267–277. [Google Scholar] [CrossRef]
- Hussain, S.A.; Cavus, N.; Sekeroglu, B. Hybrid Machine Learning Model for Body Fat Percentage Prediction Based on Support Vector Regression and Emotional Artificial Neural Networks. Appl. Sci. 2021, 11, 9797. [Google Scholar] [CrossRef]
- Cavus, N.; Mohammed, Y.B.; Yakubu, M.N. Determinants of learning management systems during COVID-19 pandemic for sustainable education. Sustainability 2021, 13, 5189. [Google Scholar] [CrossRef]
- Cai, H.; Jia, X.; Feng, J.; Li, W.; Hsu, Y.-M.; Lee, J. Gaussian Process Regression for numerical wind speed prediction enhancement. Renew. Energy 2020, 146, 2112–2123. [Google Scholar] [CrossRef]
- Rabehi, A.; Guermoui, M.; Lalmi, D. Hybrid models for global solar radiation prediction: A case study. Int. J. Ambient. Energy 2020, 41, 31–40. [Google Scholar] [CrossRef]
- Gaya, M.; Zango, M.; Yusuf, L.; Mustapha, M.; Muhammad, B.; Sani, A.; Tijjani, A.; Wahab, N.; Khairi, M. Estimation of turbidity in water treatment plant using Hammerstein-Wiener and neural network technique. Indones. J. Electr. Eng. Comput. Sci. 2017, 5, 666–672. [Google Scholar] [CrossRef]
- Taylor, K.E. Summarizing multiple aspects of model performance in a single diagram. J. Geophys. Res. Atmos. 2001, 106, 7183–7192. [Google Scholar] [CrossRef]
- Gholami, H.; Mohammadifar, A.; Golzari, S.; Kaskaoutis, D.G.; Collins, A.L. Using the Boruta algorithm and deep learning models for mapping land susceptibility to atmospheric dust emissions in Iran. Aeolian Res. 2021, 50, 100682. [Google Scholar] [CrossRef]
- Zhou, Q.; Lim, F.J.; Yu, H.; Xu, G.; Ren, X.; Liu, D.; Wang, X.; Mai, X.; Xu, H. A study on factors affecting service quality and loyalty intention in mobile banking. J. Retail. Consum. Serv. 2021, 60, 102424. [Google Scholar] [CrossRef]
- Choi, H.; Park, J.; Kim, J.; Jung, Y. Consumer preferences of attributes of mobile payment services in South Korea. Telemat. Inform. 2020, 51, 101397. [Google Scholar] [CrossRef]
- Rahman, T.; Noh, M.; Kim, Y.S.; Lee, C.K. Effect of word of mouth on m-payment service adoption: A developing country case study. Inf. Dev. 2021, 47, 771–780. [Google Scholar] [CrossRef]
- Lu, J.; Wei, J.; Yu, C.-S.; Liu, C. How do post-usage factors and espoused cultural values impact mobile payment continuation? Behav. Inf. Technol. 2017, 36, 140–164. [Google Scholar] [CrossRef]
- Al-Okaily, M.; Lutfi, A.; Alsaad, A.; Taamneh, A.; Alsyouf, A. The determinants of digital payment systems’ acceptance under cultural orientation differences: The case of uncertainty avoidance. Technol. Soc. 2020, 63, 101367. [Google Scholar] [CrossRef]
- Chenarlogh, V.A.; Razzazi, F.; Mohammadyahya, N. A multi-view human action recognition system in limited data case using multi-stream CNN. In Proceedings of the 2019 5th Iranian Conference on Signal Processing and Intelligent Systems (ICSPIS), Shahrood, Iran, 18–19 December 2019; pp. 1–11. [Google Scholar] [CrossRef]
- Roshani, M.; Sattari, M.A.; Ali, P.J.M.; Roshani, G.H.; Nazemi, B.; Corniani, E.; Nazemi, E. Application of GMDH neural network technique to improve measuring precision of a simplified photon attenuation based two-phase flowmeter. Flow Meas. Instrum. 2020, 75, 101804. [Google Scholar] [CrossRef]
- Jafari Gukeh, M.; Moitra, S.; Ibrahim, A.N.; Derrible, S.; Megaridis, C.M. Machine Learning Prediction of TiO2-Coating Wettability Tuned via UV Exposure. ACS Appl. Mater. Interfaces 2021, 13, 46171–46179. [Google Scholar] [CrossRef]
- Azimirad, V.; Ramezanlou, M.T.; Sotubadi, S.V.; Janabi-Sharifi, F. A consecutive hybrid spiking-convolutional (CHSC) neural controller for sequential decision making in robots. Neurocomputing 2022, 40, 319–336. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).