A Study on Decision-Making Opinion Exploration in Windows-Based Information Security Monitoring Tool Development
Abstract
1. Introduction
2. Related Work
2.1. Computer Basic Information
2.2. Usage Behaviors
2.3. Information Security Control
2.4. Network Behaviors and Printing Control
3. Methodology
3.1. The Assessment Model for an Information Security Tool Development: Overview
3.2. The Literature Study Method
- Step one: selecting the topic
- Step two: searching the literature
- Step three: developing the argument
- Step four: doing the literature survey
- Step five: the literature critique
- Step six: writing the review
3.3. The Delphi Method
- The anonymity of Delphi participants: it allows participants to express their opinions freely without undue social pressure to conform to others’ views in the group.
- Iteration: based on the progress of the group’s work from one round to another, it allows participants to refine their views.
- Controlled feedback: it informs participants of other participants’ views and provides Delphi participants with an opportunity to clarify or change their views.
- Statistical aggregation of group responses: it allows quantitative analysis and data interpretation.
- The question is not suitable for precise analytical technology but can benefit from collective subjective judgment.
- Individuals who need to contribute to the study do not have a well-communicated history and may represent different backgrounds in terms of experience or expertise.
- In face-to-face communication, more people need to interact effectively.
- Time and cost make frequent group meetings infeasible.
- Supplementing the group communication process can improve the efficiency of face-to-face meetings.
- Differences among individuals are very serious or politically unpopular; thus, it is necessary to adjudicate the communication process and (or) be anonymous.
- It is necessary to maintain the heterogeneity of the participants to ensure the effectiveness of the outcome.
3.4. The AHP Method
3.5. The Pearson Correlation Coefficient and the Cosine Distance
3.5.1. The Pearson Correlation Coefficient
3.5.2. The Cosine Distance
4. Study Results of the Assessment Model for Development of an Information Security Tool
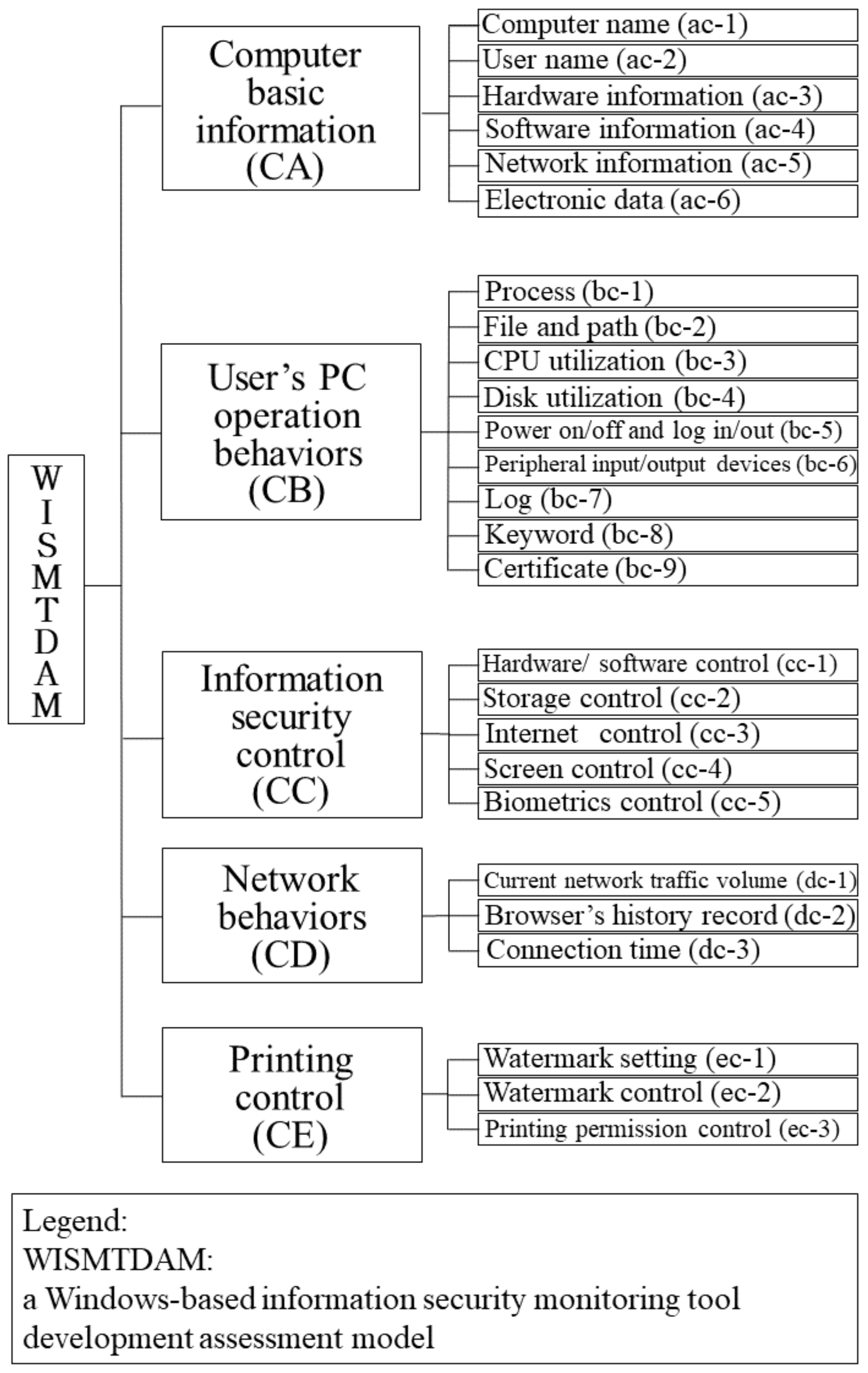
4.1. The Decision Criteria Hierarchy Establishment in the Proposed Assessment Model
4.2. The AHP Survey Works in the Proposed Assessment Model
4.3. The AHP Analysis Results
4.3.1. The AHP Analytical Result about the Main Decision Constructs
4.3.2. The AHP Analytical Result about the Decision Criteria under the Construct CA
4.3.3. The AHP Analytical Result about the Decision Criteria under the Construct CB
4.3.4. The AHP Analytical Result about the Decision Criteria under the Construct CC
4.3.5. The AHP Analytical Result about the Decision Criteria under the Construct CD
4.3.6. The AHP Analytical Result about the Decision Criteria under the Construct CE
4.3.7. The AHP Analytical Result about the Overall Decision Criteria Priority
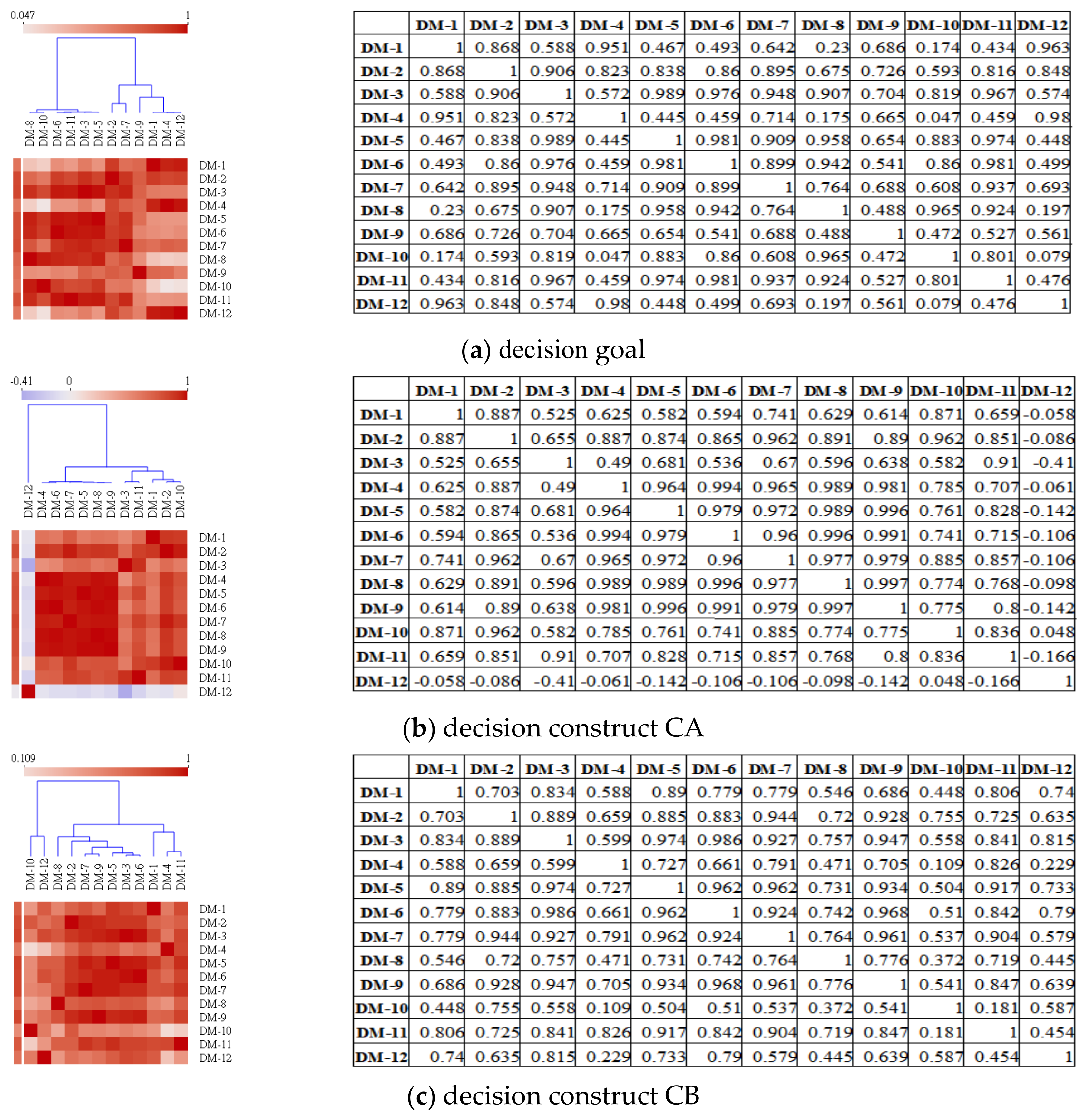
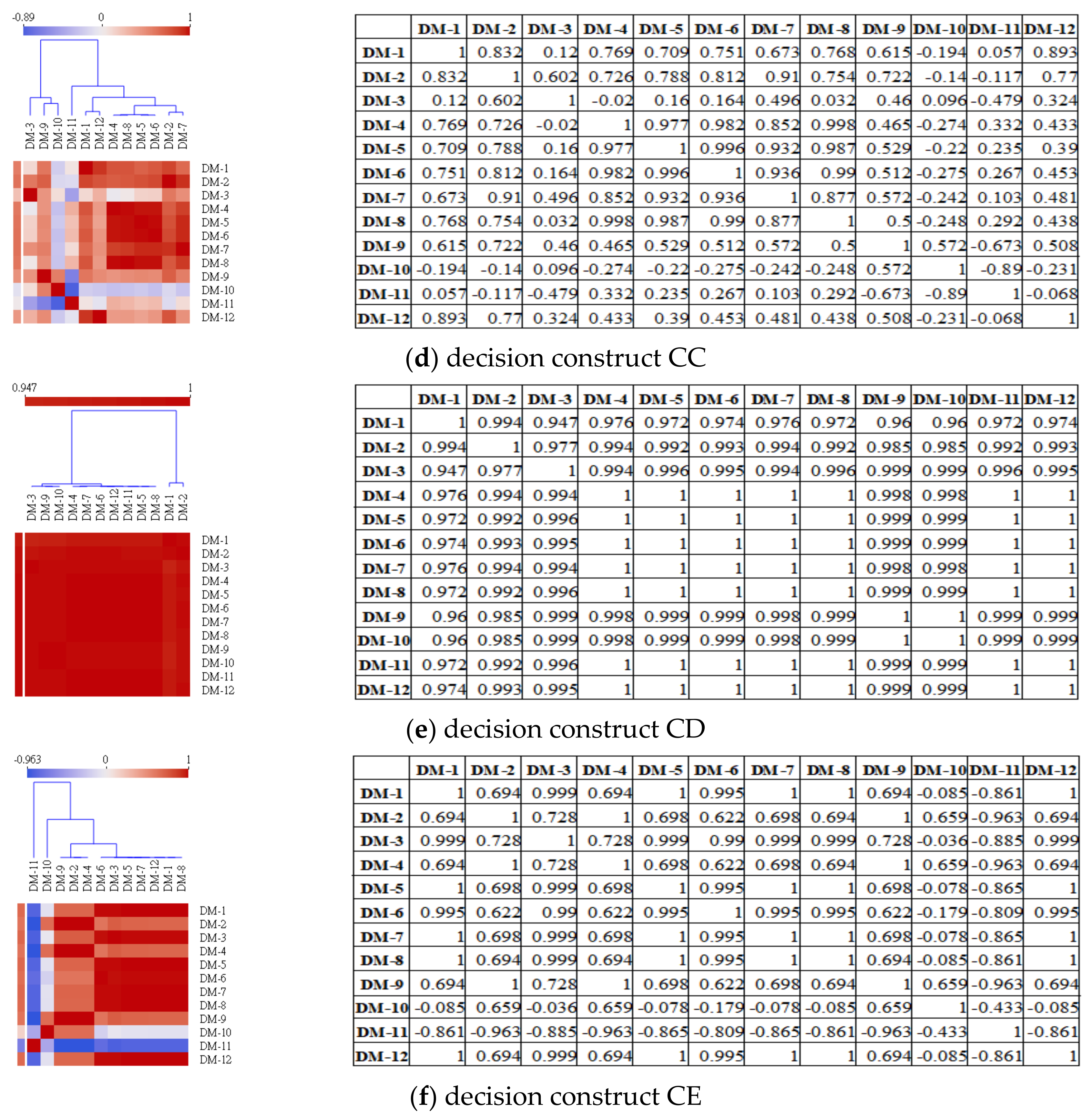
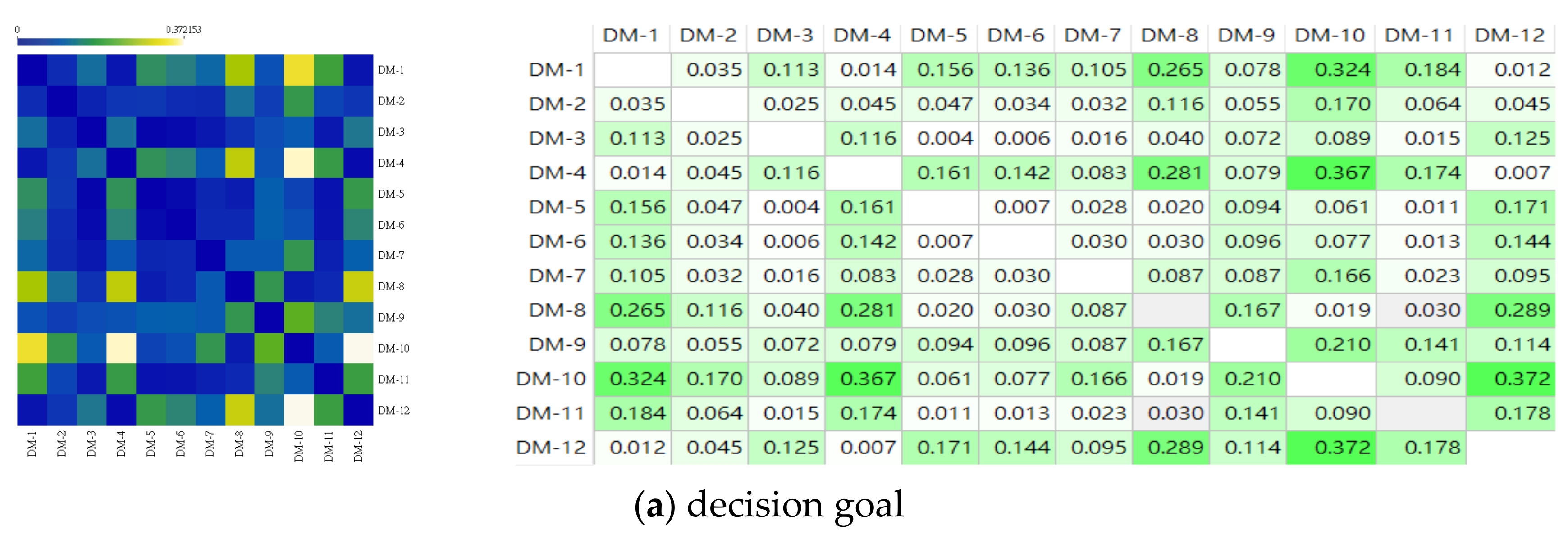
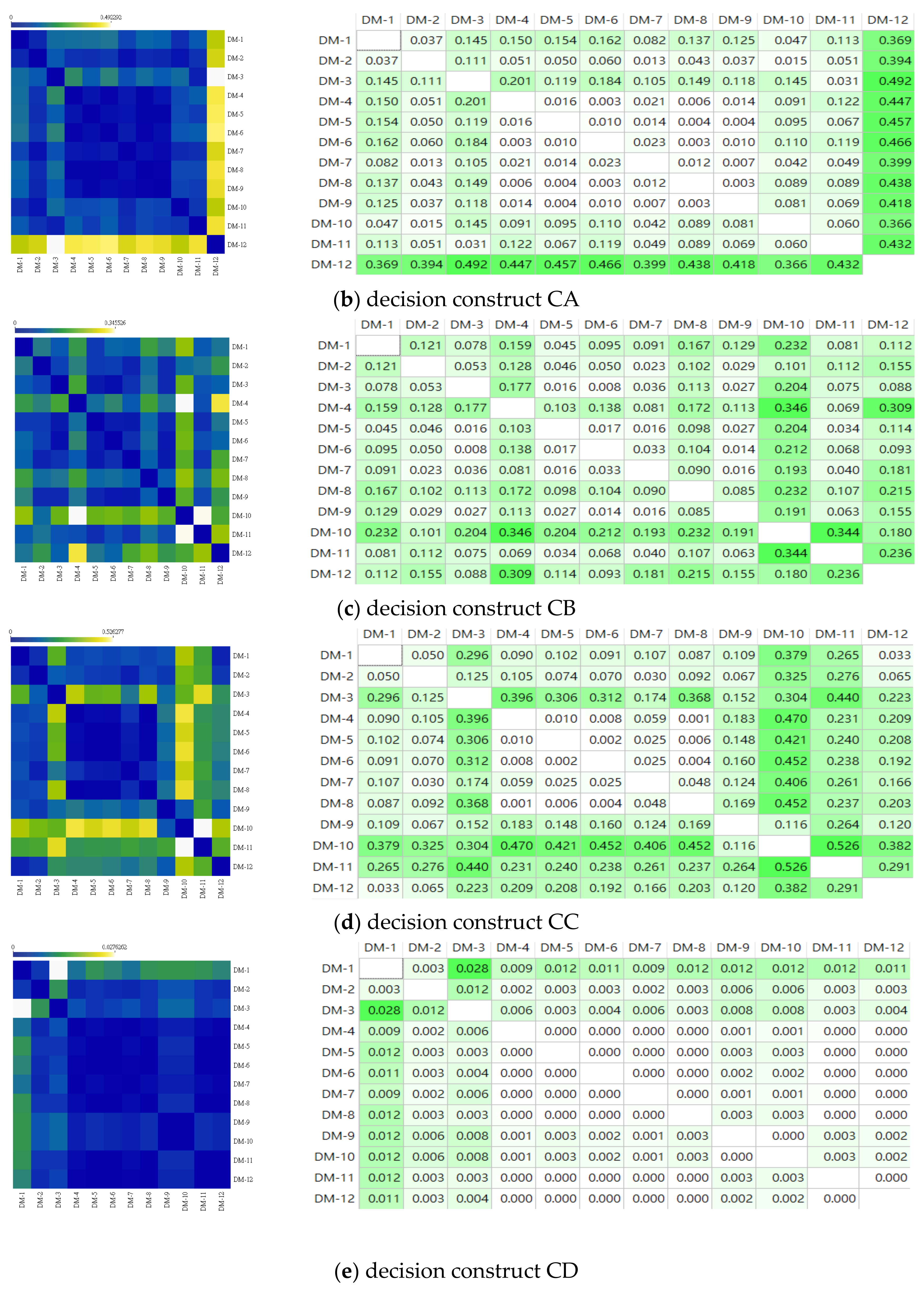
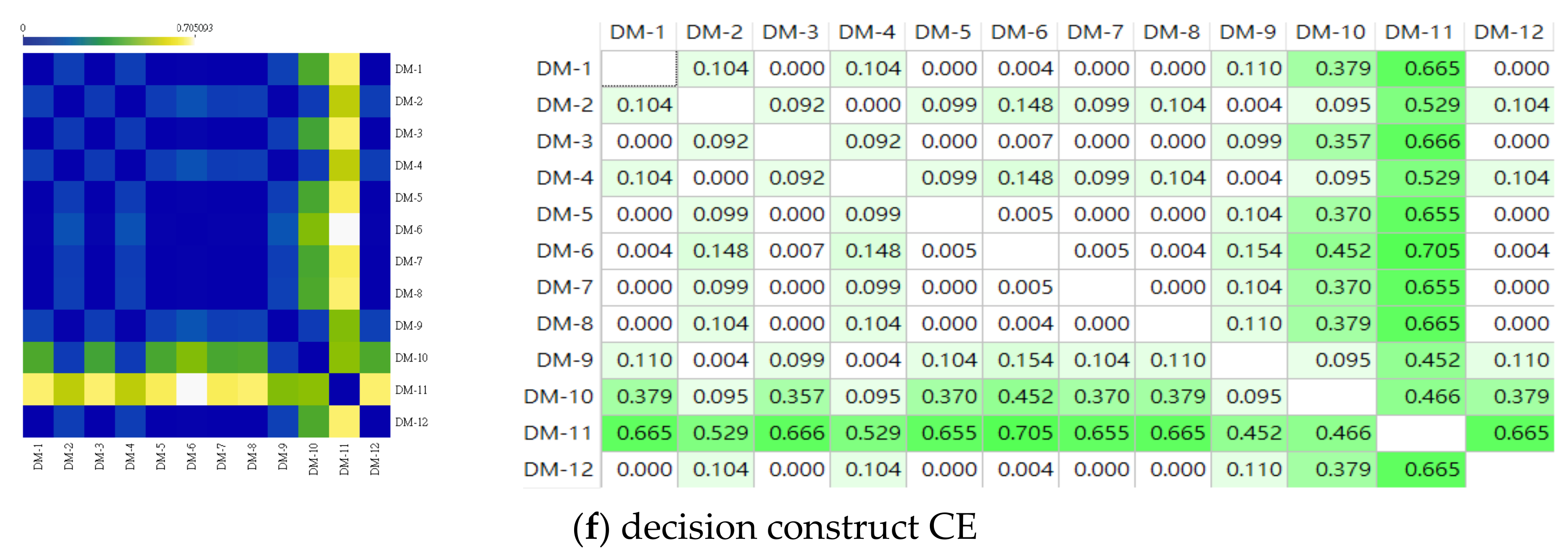
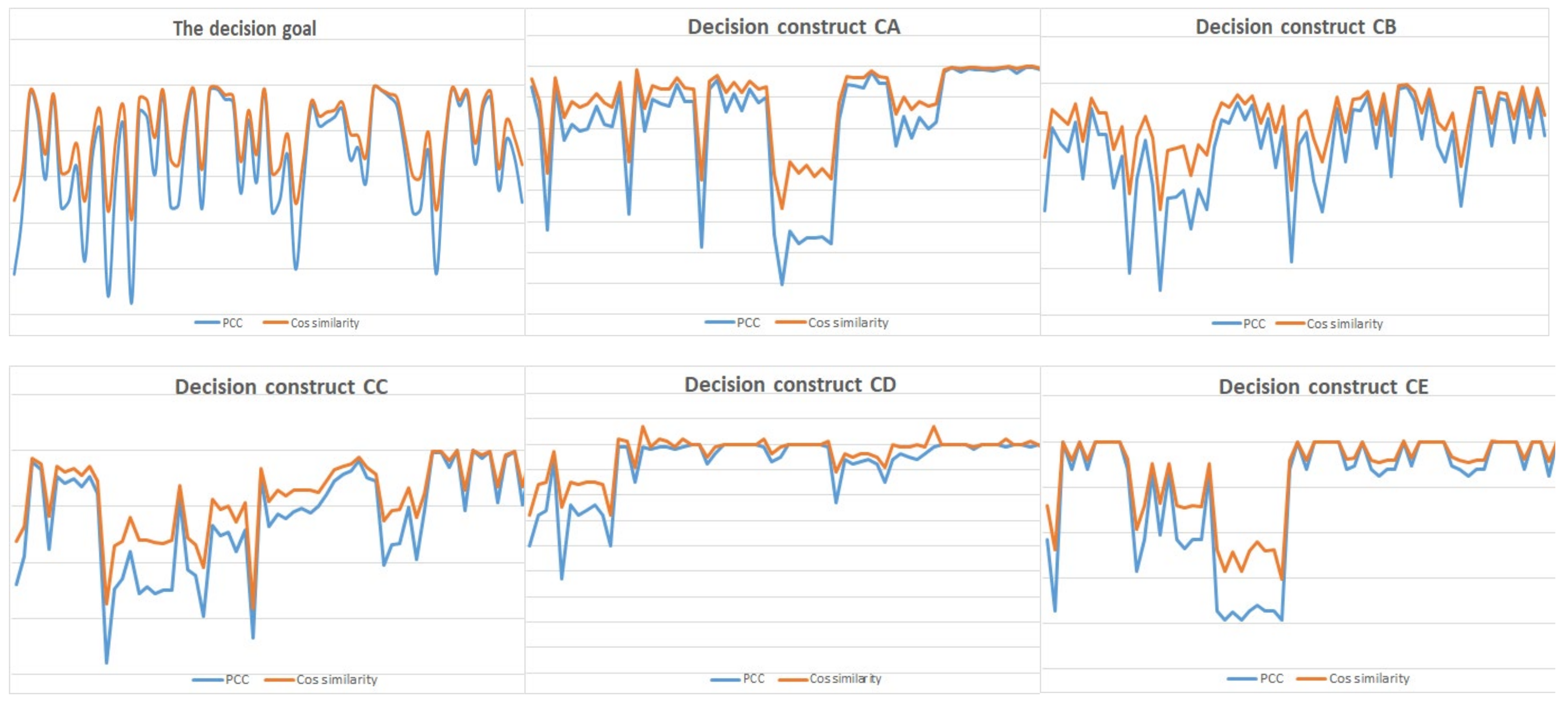
4.4. The Decision Opinion Correlation and Similarity Analysis
4.4.1. The Correlation Analysis for the Decision-Makers’ Decision Opinions
4.4.2. The Similarity Analysis for the DMs’ Decision Opinions
5. Discussion
5.1. Further Explorations on the Absolute Weights of Decision Criteria for the Development of a Windows-Based Information Security Monitoring Tool
- The absolute weight sums of these sixteen decision criteria under the five decision constructs, CC, CD, CB, CA, and CE, are 32.2%, 26.2%, 23.2%, 5.3%, and 3.1%, respectively. We can find that the decision construct weight ranking based on the absolute weights of these sixteen decision criteria in the top three significant groups is the same as the ranking of the decision constructs’ relative weights (please see Table 5).
- Looking over the distribution of these sixteen decision criteria under the five decision constructs, CC, CD, CB, CA, and CE, the ratios of decision criteria to decision construct are 4/5, 3/3, 2/3, 2/6, and 1/3, respectively. Those ratios imply that the decision constructs CC, CD, and CB should receive more developing priorities in a Windows-based information security monitoring tool.
5.2. Further Discussions on the Pearson Correlations and Cosine Similarities among Decision-Makers’ Decision Opinions
6. Conclusions and Recommendations
6.1. Conclusions
- The decision-makers’ decision opinions under the decision construct CD have the closest Pearson correlation coefficients and cosine similarity. The decision-makers’ decision opinions have larger Pearson correlation coefficients and closer cosine similarities in the decision goal and decision constructs CB and CA, but the decision-makers’ decision opinions in decision constructs CC and CE have smaller Pearson correlation coefficients and far cosine similarities. Therefore, the decision-makers’ decision opinions under the decision goal and the decision constructs CD, CB, and CA are more convergent than the decision-makers’ decision opinions under the decision constructs CD and CB.
- In the decision goal and the five decision constructs, no two or more decision-makers had very close decision opinions in the Pearson correlation coefficient and cosine similarity.
- Among all pairs of decision-makers’ decision opinions, there does not exist a positive correlation between the size of the decision criterion set and Pearson correlation coefficients/cosine similarities. However, a corresponding change exists between the Pearson correlation coefficients and cosine similarities (see Figure 5).
6.2. Recommendations
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- References Data-Exposure-Report-G (2019). Available online: https://www.code42.com/resources/report-2019-data-exposure// (accessed on 5 July 2020).
- 2020 Insider Threat Report (2020). Available online: https://www.cybersecurity-insiders.com/portfolio/2020-insider-threat-report-gurucul/ (accessed on 5 July 2020).
- Desktop Operating System Market Share Worldwide (2020). Available online: https://gs.statcounter.com/os-market-share/desktop/worldwide (accessed on 8 July 2020).
- Hazra, S. Development of an IT Asset Management Tool for Enterprise Information System. Asian J. Converg. Technol. 2018, 4. [Google Scholar]
- Dey, M. Information security management-a practical approach. In Proceedings of the AFRICON 2007, Windhoek, South Africa, 26–28 September 2007; IEEE: New York, NY, USA, 2007. [Google Scholar]
- Karjalainen, M. Developing an Information Security Management System. Bachelor’s Thesis, Laurea University of Applied Sciences, Vantaa, Finland, May 2014. [Google Scholar]
- Stanton, J.M.; Stam, K.R.; Mastrangelo, P.; Jolton, J. Analysis of end user security behaviors. Comput. Secur. 2005, 24, 124–133. [Google Scholar] [CrossRef]
- Shropshire, J.; Warkentin, M.; Sharma, S. Personality, attitudes, and intentions: Predicting initial adoption of information security behavior. Comput. Secur. 2015, 49, 177–191. [Google Scholar] [CrossRef]
- Otero, R.A.; Otero, C.E.; QureshI, A. A multi-criteria evaluation of information security controls using boolean features. Int. J. Netw. Secur. Appl. 2010, 2, 1–11. [Google Scholar]
- Stoll, M.; Felderer, M.; Breu, R. Information management for holistic, collaborative information security management. In Emerging Trends in Computing, Informatics, Systems Sciences, and Engineering; Springer: New York, NY, USA, 2013; pp. 211–224. [Google Scholar]
- Otero, A.R. An Information Security Control Assessment Methodology for Organizations. Ph.D. Thesis, Nova Southeastern University, Fort Lauderdale, FL, USA, 2014. [Google Scholar]
- Ahmad, A.; Maynard, B.S.; Park, S. Information security strategies: Towards an organizational multi-strategy perspective. J. Intell. Manuf. 2014, 25, 357–370. [Google Scholar] [CrossRef]
- Kurundkar, G.D.; Naik, N.A.; Khamitkar, S.D. Network intrusion detection using Snort. Int. J. Eng. Res. Appl. 2012, 2, 1288–1296. [Google Scholar]
- Yamada, T.; Fujii, Y.; Echizen, I.; Tanimoto, K.; Tezuka, S. Print traceability systems framework using digital watermarks for binary images. In Proceedings of the 2004 IEEE International Conference on Systems, Man and Cybernetics (IEEE Cat. No. 04CH37583); The Hague, The Netherlands, 10–13 October 2004, IEEE: New York, NY, USA, 2004; Volume 4. [Google Scholar]
- Chen, J.; Li, S. Design of paper CPU project to improve student understanding of CPU working principle. In Proceedings of the ACM Turing Celebration Conference-China, Shanghai, China, 19–10 May 2018. [Google Scholar]
- Sanders, A.D. Teaching tip: Utilizing simple hacking techniques to teach system security and hacker identification. J. Inf. Syst. Educ. 2003, 14, 5. [Google Scholar]
- Soubramanien, V.; Wei, S.P.; Ektare, M.; Chen, H. Method and Apparatus for Security Information Visualization. U.S. Patent No. 8,874,550, 28 October 2014. [Google Scholar]
- Al-Shehri, Y.; Clarke, N.L. Information security awareness and culture. In Advances in Communications, Computing, Networks and Security, Proceedings of the MSc/MRes Programmes from the School of Computing, Communications and Electronics, Plymouth, UK, 2008–2009; Lulu Press: Morrisville, NC, USA, 2009; Volume 6, p. 12. [Google Scholar]
- Itradat, A.; Sultan, S.; Al-Junaidi, M.; Qaffaf, R.; Mashal, F.; Daas, F. Developing an ISO27001 Information Security Management System for an Educational Institute: Hashemite University as a Case Study. Jordan J. Mech. Ind. Eng. 2014, 8, 102–118. [Google Scholar]
- Englander, I.; Englander, A. The Architecture of Computer Hardware and Systems Software: An Information Technology Approach; Wiley: Hoboken, NJ, USA, 2003. [Google Scholar]
- Fawcett, P.E. Method and System for Identifying and Obtaining Computer Software from a Remote Computer. U.S. Patent No. 6,073,214, 6 June 2000. [Google Scholar]
- Folco, R.C.S.; Breno, H.L.; Santos, T.N.D. Network Efficiency and Power Savings. U.S. Patent No. 9,170,976, 27 October 2015. [Google Scholar]
- Nabae, T. Communication Network System. U.S. Patent No. 7,551,634, 23 June 2009. [Google Scholar]
- Fenz, S.; Pruckner, T.; Manutscheri, A. Ontological mapping of information security best-practice guidelines. In Proceedings of the International Conference on Business Information Systems, Poznan, Poland, 27–29 April 2009; Springer: Berlin/Heidelberg, Germany, 2009. [Google Scholar]
- Munson, J.C.; Wimer, S. Watcher: The missing piece of the security puzzle. In Proceedings of the Seventeenth Annual Computer Security Applications Conference, New Orleans, LA, USA, 10–14 December 2001; IEEE: New York, NY, USA, 2001. [Google Scholar]
- Simbolon, N.; Hardiyanti, D.Y. Security Audit on Loan Debit Network Corporation System Using Cobit 5 and ISO 27001: 2013. J. Phys. Conf. Ser. 2019, 1196, 012033. [Google Scholar]
- Payer, M.; Gross, T.R. Protecting applications against TOCTTOU races by user-space caching of file metadata. In Proceedings of the 8th ACM SIGPLAN/SIGOPS Conference on Virtual Execution Environments, London, UK; 3-4 March 2012. [Google Scholar]
- Wang, X.; Wang, Y.; Liu, Q.; Sun, Y.; Xie, P. Insider detection by analyzing process behaviors of file access. In Advances in Parallel and Distributed Computing and Ubiquitous Services; Springer: Singapore, 2016; pp. 209–219. [Google Scholar]
- Ben-Menahem, A.; Ben-Zvi, N.; Miller, R.W. Software Licensing Using Certificate Issued by Authorized Authority. U.S. Patent No. 7,788,181, 31 August 2010. [Google Scholar]
- Yu, Q.; Li, J.; Zhang, Y.; Wu, W.; Huang, X.; Xiang, Y. Certificate-based encryption resilient to key leakage. J. Syst. Softw. 2016, 116, 101–112. [Google Scholar] [CrossRef]
- Thakare, S.; Pankaj, I.; Meshram, B.B. IDS: Intrusion detection system the survey of information security. Int. J. Emerg. Technol. Adv. Eng. 2012, 2, 86–90. [Google Scholar]
- Shang, T.; Zhuang, H.; Liu, J. Comprehensive security management system for Hadoop platforms. In Proceedings of the 2018 IEEE International Conference on Intelligence and Safety for Robotics (ISR), Shenyang, China, 24–27 August 2018; IEEE: New York, NY, USA, 2018. [Google Scholar]
- Lim, K.-S.; SeungBong, L.; Sangjin, L. Applying a stepwise forensic approach to incident response and computer usage analysis. In Proceedings of the 2009 2nd International Conference on Computer Science and Its Applications, Jeju, Korea, 10–12 December 2012; IEEE: New York, NY, USA, 2009. [Google Scholar]
- Sbeyti, H. Mobile user authentication based on user behavioral pattern (MOUBE). Int. J. Comput. Sci. Secur. 2016, 10, 1. [Google Scholar]
- Wang, Z.; Ma, P.; Chi, Y.; Zhang, J. Medical devices are at risk: Information security on diagnostic imaging system. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018. [Google Scholar]
- Cárdenas, A.A.; Manadhata, P.K.; Rajan, S.P. Big data analytics for security. IEEE Secur. Priv. 2013, 11, 74–76. [Google Scholar] [CrossRef]
- Yoshida, T. Communication Analysis Apparatus. U.S. Patent No. 7,337,155, 26 February 2008. [Google Scholar]
- Cavusoglu, H.; Cavusoglu, H.; Son, J.Y.l.; Benbasat, I. Institutional pressures in security management: Direct and indirect influences on organizational investment in information security control resources. Inf. Manag. 2015, 52, 385–400. [Google Scholar] [CrossRef]
- Mei, Z.; Yangqun, L. Internet of Things Experiment Platform Based on Open Source Ecosystem. In Proceedings of the 2019 International Conference on Smart Grid and Electrical Automation (ICSGEA), Xiangtan, China, 10–11 August 2019; IEEE: New York, NY, USA, 2019. [Google Scholar]
- He, J.; Li, K.; Chai, X. Method for Executing Managment Operation by Communication Terminal and a Terminal and System Thereof. U.S. Patent No. 7,953,836, 31 May 2011. [Google Scholar]
- Systems of Information Security Indicators for Industrial Enterprises. Autom. Doc. Math. Linguist. 2019, 53, 216–224. [CrossRef]
- Sulistyowati, I.; Ginardi, R.V.H. Information security risk management with octave method and iso/eic 27001: 2013 (case study: Airlangga university). IPTEK J. Proc. Ser. 2019, 1, 32–38. [Google Scholar]
- Vendrow, V.; Chau, V.D. Shared Directory System. U.S. Patent Application 13/399,343, 2014. [Google Scholar]
- Minh, Q.T.; Nguyen, K.; Yamada, S. DRANs: Resilient disaster recovery access networks. In Proceedings of the 2013 IEEE 37th Annual Computer Software and Applications Conference Workshops, Kyoto, Japan, 22–26 July 2013; IEEE: New York, NY, USA, 2013. [Google Scholar]
- Featherston, L.N.; Lee, D.M.; Getzinger, T.W. Dynamic WAN Port Detection. U.S. Patent No. 7,280,547, 9 October 2007. [Google Scholar]
- Payne, R.; Brown, P.; Ormston, C.; Garrett, A. Information Security. U.S. Patent Application No. 10/511,904, 15 August 2005. [Google Scholar]
- Abbas, J.; Mahmood, H.K.; Hussain, F. Information security management for small and medium size enterprises. Sci. Int. 2015, 27, 2393–2398. [Google Scholar]
- Vildjiounaite, E.; Mäkelä, S.M.; Lindholm, M.; Riihimäki, R.; Kyllönen, V.; Mäntyjärvi, J.; Ailisto, H. Unobtrusive multimodal biometrics for ensuring privacy and information security with personal devices. In Proceedings of the International Conference on Pervasive Computing; Pisa, Italy, 13–17 March 2006, Springer: Berlin/Heidelberg, Germany, 2006. [Google Scholar]
- Shabtai, A.; Tenenboim-Chekina, L.; Mimran, D.; Rokach, L.; Shapira, B.; Elovici, Y. Mobile malware detection through analysis of deviations in application network behavior. Comput. Secur. 2014, 43, 1–18. [Google Scholar] [CrossRef]
- Kind, A.; Stoecklin, M.P.; Dimitropoulos, X. Histogram-based traffic anomaly detection. IEEE Trans. Netw. Serv. Manag. 2009, 6, 110–121. [Google Scholar] [CrossRef]
- Aggarwal, A.; Kumar, S.; Shah, A.; Viswanath, B.; Zhang, L.; Kumaraguru, P. Spying Browser Extensions. Analysis and Detection. arXiv 2016, arXiv:1612.00766. [Google Scholar]
- Xue, L.; Guozi, S. Design and implementation of a malware detection system based on network behavior. Secur. Commun. Netw. 2015, 8, 459–470. [Google Scholar] [CrossRef]
- Momose, H.; Nimura, K. Printing Control Apparatus, Printing Control Method, and Computer Program Product for Realizing the Method. U.S. Patent No. 6,301,013, 9 October 2001. [Google Scholar]
- Yamada, K. Print Control Device and Recording Medium Containing Program for Controlling Printing Device. U.S. Patent No. 8,159,723, 17 April 2012. [Google Scholar]
- Ishige, T.; Kito, N.; Obi, H. Printing System, Printer and Print Request Control Server. U.S. Patent Application No. 13/482,766, 2012. [Google Scholar]
- Natriello, G. For the record: Reviewing literature. Teach. Coll. Rec. 2000, 102, 693–695. [Google Scholar] [CrossRef]
- Rankin, E. Changing the hollow conventions of academic writing. Chron. High. Educ. 1998, 44, A64. [Google Scholar]
- Kruse, S.D.; Warbel, A. Developing a Comprehensive Literature Review: An Inquiry into Method. Bachelor’s Thesis, University of Akron, Akron, OH, USA, 2010. [Google Scholar]
- Machi, L.A.; McEvoy, B.T. The Literature Review: Six Steps to Success; Corwin Press: Thousand Oaks, CA, USA, 2016. [Google Scholar]
- Skulmoski, G.J.; Hartman, F.T.; Krahn, J. The Delphi method for graduate research. J. Inf. Technol. Educ. Res. 2007, 6, 1–21. [Google Scholar] [CrossRef]
- Norman, D.; Helmer, O. An experimental application of the Delphi method to the use of experts. Manag. Sci. 1963, 9, 458–467. [Google Scholar]
- Linstone, H.A.; Turoff, M. (Eds.) The Delphi Method; Addison-Wesley: Reading, MA, USA, 1975. [Google Scholar]
- Rowe, G.; Wright, G. The Delphi technique as a forecasting tool: Issues and analysis. Int. J. Forecast. 1999, 15, 353–375. [Google Scholar] [CrossRef]
- Okoli, C.; Pawlowski, S.D. The Delphi method as a research tool: An example, design considerations and applications. Inf. Manag. 2004, 42, 15–29. [Google Scholar] [CrossRef]
- Saaty, T.L. A scaling method for priorities in hierarchical structures. J. Math. Psychol. 1977, 15, 234–281. [Google Scholar] [CrossRef]
- Chi, L.-P.; Zhuang, Z.Y.; Fu, C.H.; Huang, J.H. A knowledge discovery education framework targeting the effective budget use and opinion explorations in designing specific high cost product. Sustainability 2018, 10, 2742. [Google Scholar] [CrossRef]
- Zhuang, Z.-Y.; Chiang, I.J.; Su, C.R.; Chen, C.Y. Modelling the decision of paper shredder selection using analytic hierarchy process and graph theory and matrix approach. Adv. Mech. Eng. 2017, 9, 1687814017737668. [Google Scholar] [CrossRef]
- Abbas, M.S. Consistency Analysis for Judgment Quantification in Hierarchical Decision Model. Ph.D. Thesis, Portland State University, Portlnad, OR, USA, 2016. [Google Scholar]
- Rodgers, L.J.; Nicewander, W.A. Thirteen ways to look at the correlation coefficient. Am. Stat. 1988, 42, 59–66. [Google Scholar] [CrossRef]
- Zhou, H.; Deng, Z.; Xia, Y.; Fu, M. A new sampling method in particle filter based on Pearson correlation coefficient. Neurocomputing 2016, 216, 208–215. [Google Scholar] [CrossRef]
- Sedgwick, P. Pearson’s correlation coefficient. BMJ 2012, 345, e4483. [Google Scholar] [CrossRef]
- Garcia, A.A.; Sayago, A.; Gonzalez, A.G. The correlation coefficient: An overview. Crit. Rev. Anal. Chem. 2006, 36, 41–59. [Google Scholar]
- Chowdhury, G.G. Introduction to Modern Information Retrieval; Facet Publishing: London, UK, 2010. [Google Scholar]
- Kusban, M.; Budiman, A. Palmprint recognition using the cosine method. In Proceedings of the IOP Conference Series: Materials Science and Engineering, Kazimierz Dolny, Poland, 21–23 November 2019; IOP Publishing: Bristol, UK, 2019; Volume 674. [Google Scholar]
- Aggarwal, C.C. Towards systematic design of distance functions for data mining applications. In Proceedings of the Ninth ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, Washington, DC, USA, 24–27 August 2003. [Google Scholar]
- Zou, B.-J.; Umugwaneza, M.P. Shape-based trademark retrieval using cosine distance method. In Proceedings of the 2008 Eighth International Conference on Intelligent Systems Design and Applications, Kaohsiung, Taiwan, 26–28 November 2008; IEEE: New York, NY, USA, 2008; Volume 2. [Google Scholar]
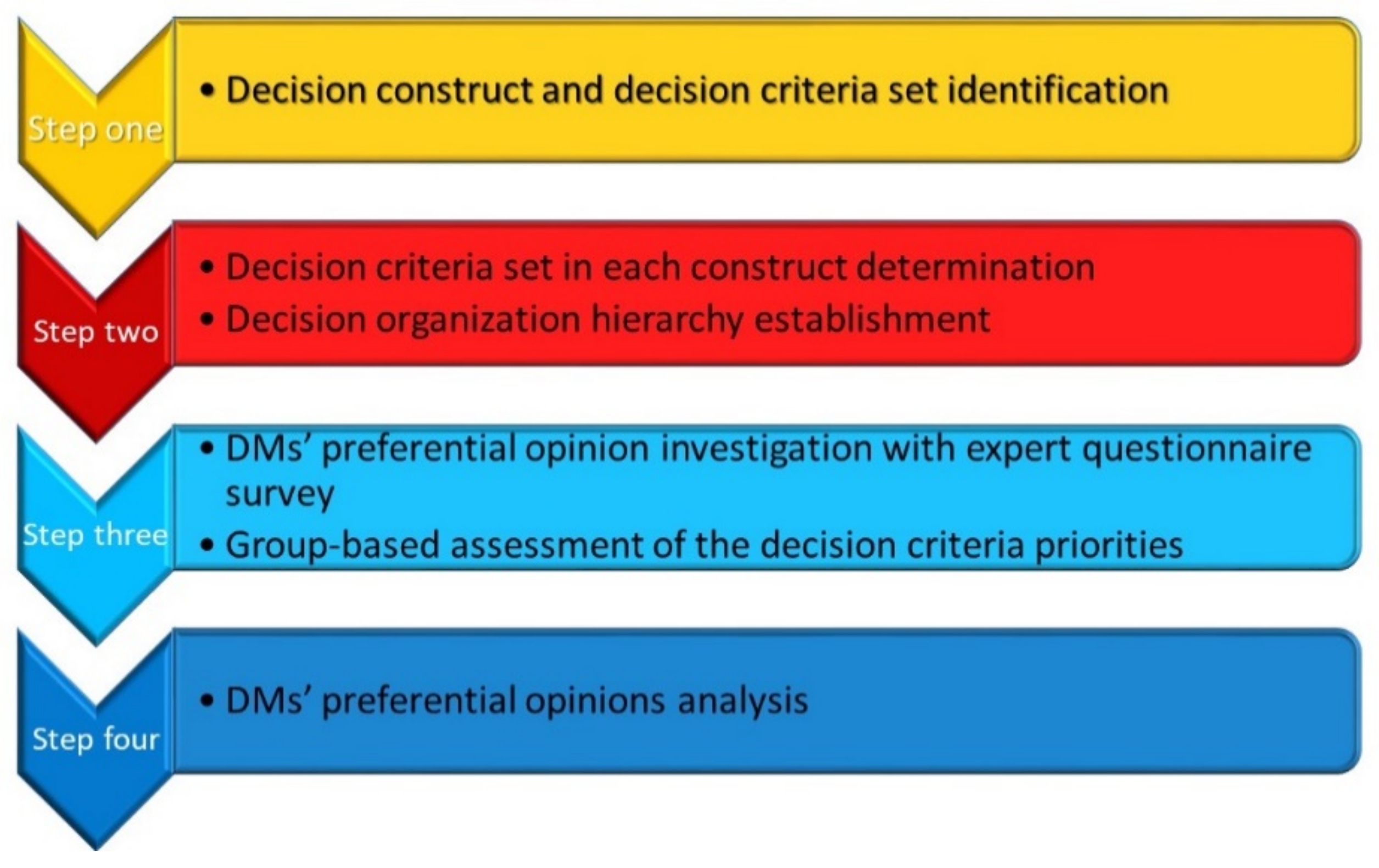
| Step | Adopted Method | Expected Results |
|---|---|---|
| 1 | Literature study method | To find the decision constructs and the possible decision criteria set for the assessment model for development of an information security monitoring tool |
| 2 | Delphi method: Consulting with potential decision-makers | To identify the decision criteria under each decision construct for the assessment model for development of an information security monitoring tool |
| Delphi method: Consulting with decision-makers via email/instant message apps/face-to-face interviews several times | To confirm a suitable decision hierarchy for the assessment model for development of an information security monitoring tool | |
| 3 | AHP method: Receiving pairwise comparison matrices with consistency check | To receive decision-makers’ preferential opinions for the assessment model for development of an information security monitoring tool with the consistency verification |
| Receiving group opinion assessment in the multiple criteria decision-making field | To receive group opinion assessment of all decision-makers for the assessment model for development of an information security monitoring tool | |
| 4 | Two data-driven decision-making analytical (Pearson correlation and cosine similarity) methods | To understand the correlations and similarities among all decision-makers’ preferential decision opinions |
| Pearson Correlation Coefficient Value | Interpretation |
|---|---|
| 0.90 to 1.00 | Very high correlation |
| 0.70 to 0.89 | High correlation |
| 0.50 to 0.69 | Moderate correlation |
| 0.30 to 0.49 | Low correlation |
| 0.00 to 0.29 | Little if any correlation |
| Criteria | Operational Definition |
|---|---|
| Computer name | To get the name of a computer |
| User name | To get information of users’ accounts, which can be used by users to log in to the computer |
| Hardware information | To get information of CPU, memory, physical disk drive, logical disk drive, and setting of network interface card |
| Software information | To get information of operating system version, installed software, services, and update with Windows Update Agent |
| Network information | To get computer’s network interface card configuration and routing setting information |
| Electronic data | To get information of data stored in the computer |
| Process | To list processes of normal software and green software |
| File and path | To list files change in specific path, to get protected path, to set path of monitored REGISTRY and to get path of monitored REGISTRY |
| CPU utilization | To get information of CPU utilization rate |
| Disk utilization | To get information of disk capacity utilization rate |
| Power on/off and log in/out | To get records of power on/off and users’ login/logout from system log |
| Peripheral input/output devices | To operate/get current media devices (such as compact disc-read only memory (CD-ROM) drive, etc.) and USB devices |
| Log | To get the latest system log and read specific types of system log To get a setting of POWERSHELL log execution or enable/disable log execution |
| Keyword | To monitor and operate strings in clipper
|
| Certificate | To get records of installed certificates from system log |
| Hardware/software control | Computer hardware devices operations
|
| Storage control | To list/remove computer disk drive, to get/remove current shared directory in a computer |
| Internet control | Computer network connection operations
|
| Screen control | To detect if screen saver is installed To capture screen picture, save the captured picture in computer, and return the path of the captured picture |
| Biometrics control | To log in to the computer with voice, fingerprint, iris, or face recognition |
| Current network traffic volume | To get a record of current network traffic volume |
| Browser’s history record | To get current browser’s browsing history |
| Connection time | To get length of time that the computer connects to the network |
| Watermark setting | To get/modify current watermark setting |
| Watermark control | To enable/disable watermark module |
| Printing permission control | To enable/disable printing permissions for a specific user account |
| Type | #Decision-Makers | Percentage | |
|---|---|---|---|
| Gender | Male | 8 | 66.67% |
| Female | 4 | 33.33% | |
| Degree | Ph.D. | 12 | 100.00% |
| Industry category | Government | 1 | 8.33% |
| Academy | 5 | 41.67% | |
| R&D institute | 1 | 8.33% | |
| Information industry | 5 | 41.67% | |
| Position | Supervisor (information department) | 1 | 8.33% |
| Professor | 5 | 41.67% | |
| Information professional | 6 | 50.00% | |
| Age | 31–40 | 3 | 25.00% |
| 41–50 | 5 | 41.67% | |
| 51–65 | 4 | 33.33% | |
| Service time (years) | 1~10 | 3 | 25.00% |
| 11~20 | 4 | 33.33% | |
| 21+ | 5 | 41.67% |
| Decision Constructs | Relative Weight | Ranking | Consistency Analysis |
|---|---|---|---|
| Information security control (CC) | 0.340 | 1 | Inconsistency = 0.02 with 0 missing judgments. |
| Network behavior (CD) | 0.262 | 2 | |
| User’s PC operation behavior (CB) | 0.260 | 3 | |
| Computer basic information (CA) | 0.083 | 4 | |
| Printing control (CE) | 0.056 | 5 |
| Decision Constructs | Relative Weight | Ranking | Consistency Analysis |
|---|---|---|---|
| Network information (ac−5) | 0.345 | 1 | Inconsistency = 0.02 with 0 missing judgments. |
| Software information (ac-4) | 0.284 | 2 | |
| Hardware information (ac-3) | 0.161 | 3 | |
| Computer name (ac-1) | 0.107 | 4 | |
| Electronic data (ac-6) | 0.056 | 5 | |
| Username (ac-2) | 0.047 | 6 |
| Decision Constructs | Relative Weight | Ranking | Consistency Analysis |
|---|---|---|---|
| Log (bc-7) | 0.312 | 1 | Inconsistency = 0.02 with 0 missing judgments. |
| Process (bc-1) | 0.193 | 2 | |
| File and path (bc-2) | 0.120 | 3 | |
| Certificate (bc-9) | 0.109 | 4 | |
| Power on/off and log in/out (bc-5) | 0.080 | 5 | |
| Peripheral input/output devices (bc-6) | 0.080 | 6 | |
| Keyword (bc-8) | 0.055 | 7 | |
| CPU utilization (bc-3) | 0.026 | 8 | |
| Disk utilization (bc-4) | 0.025 | 9 |
| Decision Constructs | Relative Weight | Ranking | Consistency Analysis |
|---|---|---|---|
| Internet control (cc-3) | 0.381 | 1 | Inconsistency = 0.01 with 0 missing judgments. |
| Hardware/software control (cc-1) | 0.251 | 2 | |
| Storage control (cc-2) | 0.210 | 3 | |
| Screen control (cc-4) | 0.103 | 4 | |
| Biometrics control (cc-5) | 0.054 | 5 |
| Decision Constructs | Relative Weight | Ranking | Consistency Analysis |
|---|---|---|---|
| Browser’s history record (dc-2) | 0.677 | 1 | Inconsistency = 0.00471 with 0 missing judgments. |
| Current network traffic volume (dc-1) | 0.240 | 2 | |
| Connection time (dc-3) | 0.083 | 3 |
| Decision Constructs | Relative Weight | Ranking | Consistency Analysis |
|---|---|---|---|
| Watermark control (ec-2) | 0.547 | 1 | Inconsistency = 0.00471 with 0 missing judgments. |
| Watermark setting (ec-1) | 0.336 | 2 | |
| Printing permission control (ec-3) | 0.117 | 3 |
| Decision Constructs | Relative Weight | Ranking | Consistency Analysis |
|---|---|---|---|
| Browser’s history record (dc-2) | 0.177 | 1 | Inconsistency = 0.01 with 0 missing judgments. |
| Internet control (cc-3) | 0.130 | 2 | |
| Hardware/software control (cc-1) | 0.085 | 3 | |
| Log (bc-7) | 0.081 | 4 | |
| Storage control (cc-2) | 0.072 | 5 | |
| Current network traffic volume (dc-1) | 0.063 | 6 | |
| Process (bc-1) | 0.050 | 7 | |
| Screen control (cc-4) | 0.035 | 8 | |
| File and path (bc-2) | 0.031 | 9 | |
| Watermark control (ec-2) | 0.031 | 10 | |
| Network information (ac-5) | 0.029 | 11 | |
| Certificate (bc-9) | 0.028 | 12 | |
| Software information (ac-4) | 0.024 | 13 | |
| Connection time (dc-3) | 0.022 | 14 | |
| Power on/off and log in/out (bc-5) | 0.021 | 15 | |
| Peripheral input/output devices (bc-6) | 0.021 | 16 | |
| Watermark setting (ec-1) | 0.019 | 17 | |
| Biometrics control (cc-5) | 0.018 | 18 | |
| Keyword (bc-8) | 0.014 | 19 | |
| Hardware information (ac-3) | 0.013 | 20 | |
| Computer name (ac-1) | 0.009 | 21 | |
| CPU utilization (bc-3) | 0.007 | 22 | |
| Disk utilization (bc-4) | 0.007 | 23 | |
| Printing permission control (ec-3) | 0.007 | 24 | |
| Electronic data (ac-6) | 0.005 | 25 | |
| Username (ac-2) | 0.004 | 26 |
| (a) The Matrix of Criterion Weight Vectors under the Decision Goal | |||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| CS | DM-1 | DM-2 | DM-3 | DM-4 | DM-5 | DM-6 | DM-7 | DM-8 | DM-9 | DM-10 | DM-11 | DM-12 | Aggr. |
| CA | 0.089 | 0.075 | 0.087 | 0.095 | 0.088 | 0.063 | 0.069 | 0.080 | 0.22 | 0.103 | 0.034 | 0.042 | 0.083 |
| CB | 0.370 | 0.293 | 0.226 | 0.304 | 0.207 | 0.220 | 0.196 | 0.181 | 0.242 | 0.230 | 0.174 | 0.338 | 0.260 |
| CC | 0.186 | 0.293 | 0.383 | 0.173 | 0.423 | 0.392 | 0.356 | 0.512 | 0.242 | 0.561 | 0.446 | 0.176 | 0.340 |
| CD | 0.319 | 0.278 | 0.259 | 0.374 | 0.238 | 0.233 | 0.343 | 0.168 | 0.242 | 0.072 | 0.282 | 0.373 | 0.262 |
| CE | 0.047 | 0.062 | 0.046 | 0.054 | 0.043 | 0.092 | 0.036 | 0.058 | 0.054 | 0.034 | 0.064 | 0.070 | 0.056 |
| (b) The Matrix of Criterion Weight Vectors under the CA construct | |||||||||||||
| CR | DM-1 | DM-2 | DM-3 | DM-4 | DM-5 | DM-6 | DM-7 | DM-8 | DM-9 | DM-10 | DM-11 | DM-12 | Aggr. |
| ac-1 | 0.217 | 0.127 | 0.121 | 0.088 | 0.075 | 0.098 | 0.101 | 0.1 | 0.099 | 0.082 | 0.055 | 0.091 | 0.107 |
| ac-2 | 0.034 | 0.044 | 0.043 | 0.052 | 0.036 | 0.041 | 0.052 | 0.035 | 0.059 | 0.051 | 0.033 | 0.055 | 0.047 |
| ac-3 | 0.139 | 0.154 | 0.344 | 0.099 | 0.186 | 0.122 | 0.163 | 0.145 | 0.164 | 0.147 | 0.289 | 0.045 | 0.161 |
| ac-4 | 0.346 | 0.324 | 0.212 | 0.254 | 0.223 | 0.226 | 0.269 | 0.233 | 0.222 | 0.392 | 0.289 | 0.251 | 0.284 |
| ac-5 | 0.225 | 0.32 | 0.244 | 0.465 | 0.435 | 0.475 | 0.366 | 0.44 | 0.401 | 0.287 | 0.289 | 0.135 | 0.345 |
| ac-6 | 0.039 | 0.031 | 0.036 | 0.041 | 0.045 | 0.039 | 0.048 | 0.049 | 0.056 | 0.042 | 0.045 | 0.423 | 0.056 |
| (c) The Matrix of Criterion Weight Vectors under the CB construct | |||||||||||||
| CR | DM-1 | DM-2 | DM-3 | DM-4 | DM-5 | DM-6 | DM-7 | DM-8 | DM-9 | DM-10 | DM-11 | DM-12 | Aggr. |
| bc-1 | 0.256 | 0.173 | 0.206 | 0.267 | 0.233 | 0.192 | 0.239 | 0.219 | 0.197 | 0.048 | 0.311 | 0.079 | 0.193 |
| bc-2 | 0.14 | 0.186 | 0.092 | 0.103 | 0.104 | 0.071 | 0.132 | 0.117 | 0.09 | 0.277 | 0.057 | 0.107 | 0.12 |
| bc-3 | 0.016 | 0.022 | 0.024 | 0.023 | 0.021 | 0.021 | 0.026 | 0.027 | 0.034 | 0.019 | 0.042 | 0.022 | 0.026 |
| bc-4 | 0.017 | 0.022 | 0.019 | 0.021 | 0.019 | 0.021 | 0.021 | 0.21 | 0.027 | 0.023 | 0.042 | 0.032 | 0.025 |
| bc-5 | 0.047 | 0.066 | 0.062 | 0.108 | 0.085 | 0.073 | 0.089 | 0.076 | 0.08 | 0.077 | 0.082 | 0.065 | 0.08 |
| bc-6 | 0.04 | 0.096 | 0.054 | 0.196 | 0.069 | 0.098 | 0.086 | 0.078 | 0.1 | 0.035 | 0.081 | 0.072 | 0.08 |
| bc-7 | 0.226 | 0.313 | 0.373 | 0.179 | 0.296 | 0.351 | 0.303 | 0.306 | 0.337 | 0.272 | 0.252 | 0.311 | 0.312 |
| bc-8 | 0.039 | 0.061 | 0.028 | 0.044 | 0.041 | 0.047 | 0.04 | 0.081 | 0.072 | 0.143 | 0.039 | 0.04 | 0.055 |
| bc-9 | 0.219 | 0.062 | 0.143 | 0.058 | 0.131 | 0.127 | 0.063 | 0.075 | 0.063 | 0.106 | 0.093 | 0.271 | 0.109 |
| (d) The Matrix of Criterion Weight Vectors under the CC construct | |||||||||||||
| CR | DM-1 | DM-2 | DM-3 | DM-4 | DM-5 | DM-6 | DM-7 | DM-8 | DM-9 | DM-10 | DM-11 | DM-12 | Aggr. |
| cc-1 | 0.171 | 0.307 | 0.252 | 0.208 | 0.27 | 0.268 | 0.35 | 0.224 | 0.231 | 0.195 | 0.141 | 0.2 | 0.251 |
| cc-2 | 0.342 | 0.266 | 0.131 | 0.151 | 0.132 | 0.15 | 0.165 | 0.151 | 0.231 | 0.195 | 0.141 | 0.411 | 0.21 |
| cc-3 | 0.374 | 0.307 | 0.0516 | 0.52 | 0.468 | 0.478 | 0.382 | 0.504 | 0.231 | 0.117 | 0.312 | 0.264 | 0.381 |
| cc-4 | 0.082 | 0.089 | 0.067 | 0.079 | 0.094 | 0.069 | 0.066 | 0.085 | 0.231 | 0.448 | 0.055 | 0.058 | 0.103 |
| cc-5 | 0.032 | 0.032 | 0.034 | 0.042 | 0.037 | 0.036 | 0.037 | 0.035 | 0.077 | 0.044 | 0.352 | 0.066 | 0.054 |
| (e) The Matrix of Criterion Weight Vectors under the CD construct | |||||||||||||
| CR | DM-1 | DM-2 | DM-3 | DM-4 | DM-5 | DM-6 | DM-7 | DM-8 | DM-9 | DM-10 | DM-11 | DM-12 | Aggr. |
| dc-1 | 0.319 | 0.278 | 0.183 | 0.243 | 0.231 | 0.236 | 0.243 | 0.231 | 0.23 | 0.23 | 0.231 | 0.236 | 0.24 |
| dc-2 | 0.615 | 0.663 | 0.742 | 0.669 | 0.692 | 0.682 | 0.669 | 0.692 | 0.648 | 0.648 | 0.692 | 0.682 | 0.677 |
| dc-3 | 0.066 | 0.058 | 0.075 | 0.088 | 0.077 | 0.082 | 0.088 | 0.077 | 0.122 | 0.122 | 0.077 | 0.082 | 0.083 |
| (f) The Matrix of Criterion Weight Vectors under the CE construct | |||||||||||||
| CR | DM-1 | DM-2 | DM-3 | DM-4 | DM-5 | DM-6 | DM-7 | DM-8 | DM-9 | DM-10 | DM-11 | DM-12 | Aggr. |
| ec-1 | 0.231 | 0.455 | 0.25 | 0.455 | 0.236 | 0.178 | 0.236 | 0.231 | 0.429 | 0.648 | 0.25 | 0.231 | 0.336 |
| ec-2 | 0.692 | 0.455 | 0.681 | 0.455 | 0.682 | 0.751 | 0.682 | 0.692 | 0.429 | 0.23 | 0.095 | 0.692 | 0.547 |
| ec-3 | 0.077 | 0.091 | 0.069 | 0.091 | 0.082 | 0.07 | 0.082 | 0.077 | 0.143 | 0.122 | 0.655 | 0.077 | 0.117 |
| Classification | Strength | % | Pairs of Decision-Makers |
|---|---|---|---|
| Positive | Very high | 27.27 | (3,5), (6,11), (5,6), (4,12), (3,6), (5,11), (3,11), (8,10), (1,12), (5,8), (1,4), (3,7), (6,8), (7,11),(8,11), (5,7), (3,8), (2,3) |
| High | 24.24 | (6,7), (2,7), (5,10), (1,2), (6,10), (2,6), (2,12), (2,5), (2,4), (3,10), (2,11), (10,11), (7,8), (2,9), (4,7), (3,9) | |
| Moderate | 22.73 | (7,12), (7,9), (1,9), (2,8), (4,9), (5,9), (1,7), (7,10), (2,10), (1,3), (3,12), (3,4), (9,12), (6,9),(9,11) | |
| Low | 16.67 | (6,12), (1,6), (8,9), (11,12), (9,10), (1,5), (4,11), (4,6), (5,12), (4,5), (1,11) | |
| Little | 9.09 | (1,8), (8,12), (4,8), (1,10), (10,12), (1,4) |
| Classification | Strength | % | Pairs of Decision-Makers |
|---|---|---|---|
| Positive | Very high | 27.27 | (8,9), (5,9), (6,8), (4,6), (6,9), (4,8), (5,8), (4,9), (5,6), (7,9), (7,8), (5,7), (4,7), (4,5), (2,10), (2,7), (6,7), (3,11) |
| High | 33.33 | (2,8), (2,9), (1,2), (2,4), (7,10), (2,5), (1,10), (2,6), (7,11), (211), (10,11), (5,11), (9,11), (4,10), (9,10), (8,10), (8,11), (5,10), (1,7), (6,10), (6,11), (4,11) | |
| Moderate | 21.21 | (3,5), (3,7), (1,11), (2,3), (3,9), (1,8), (1,4), (1,9), (3,8), (1,6), (1,5), (3,10), (3,6), (1,3) | |
| Low | 01.52 | (3,4) | |
| Little | 01.52 | (10,12) | |
| Negative | Little | 13.64 | (1,12), (4,12), (2,12), (8,12), (6,12), (7,12), (9,12), (5,12), (11,12) |
| Low | 01.52 | (3,12) |
| Classification | Strength | % | Pairs of Decision-Makers |
|---|---|---|---|
| Positive | Very high | 21.21 | (3,6), (3,5), (6,9), (5,7), (5,6), (7,9), (3,9), (2,7), (5,9), (2,9), (3,7), (6,7), (5,11), (7,11) |
| High | 43.94 | (1,5), (2,3), (2,5), (2,6), (9,11), (6,11), (3,11), (1,3), (4,11), (3,12), (1,11), (4,7), (6,12), (1,6), (1,7), (8,9), (7,8), (3,8), (2,10), (6,8), (1,12), (5,12), (5,8), (4,5), (2,11), (2,8), (8,11), (4,9), (1,2) | |
| Moderate | 22.73 | (1,9), (4,6), (2,4), (9,12), (2,12), (3,4), (1,4), (10,12), (7,12), (3,10), (1,8), (9,10), (7,10), (6,10), (5,10) | |
| Low | 7.58 | (4,8), (11,12), (1,10), (8,12), (8,10) | |
| Little | 4.55 | (4,12), (10,11), (4,10) |
| Classification | Strength | % | Pairs of Decision-Makers |
|---|---|---|---|
| Positive | Very high | 13.64 | (4,8), (5,6), (6,8), (5,8), (4,6), (4,5), (6,7), (5,7), (2,7) |
| High | 21.21 | (1,12), (7,8), (4,7), (1,2), (2,6), (2,5), (2,12), (1,4), (1,8), (2,8), (1,6), (2,4), (2,9), (1,5) | |
| Moderate | 13.64 | (1,7), (1,9), (2,3), (7,9), (9,10), (5,9), (6,9), (9,12), (8,9) | |
| Low | 15.15 | (3,7), (7,12), (4,9), (3,9), (6,12), (8,12), (4,12), (5,12), (4,11), (3,12) | |
| Little | 15.15 | (8,11), (6,11), (5,11), (3,6), (3,5), (1,3), (7,11), (3,10), (1,11), (3,8) | |
| Negative | Little | 16.67 | (3,4), (11,12), (2,11), (2,10), (1,10), (5,10), (10,12), (7,10), (8,10), (4,10), (6,10) |
| Low | 1.52 | (3,11) | |
| Moderate | 1.52 | (9,11) | |
| High | 1.52 | (10,11) |
| Classification | Strength | % | Pairs of Decision-Makers |
|---|---|---|---|
| Positive | Very high | 100.0 | All pairs of 12 DMs |
| Classification | Strength | % | Pairs of Decision-Makers |
|---|---|---|---|
| Positive | Very high | 36.36 | (7,8), (5,7), (5,8), (4,9), (2,9), (2,4), (8,12), (7,12), (5,12), (112), (1,8), (1,7), (1,5), (3,7), (3,5), (3,8), (3,12), (1,3), (6,8), (6,7), (5,6), (6,12), (1,6), (3,6), |
| High | 4.55 | (3,4), (3,9), (2,3) | |
| Moderate | 31.82 | (7,9), (5,9), (4,7), (4,5), (2,7), (2,5), (8,9), (4,8), (2,8), (9,12), (4,12), (2,12), (1,9), (1,4), (1,2), (9,10), (4,10), (2,10), (6,9), (4,6), (2,6) | |
| Negative | Little | 10.61 | (3,10), (7,10), (5,10), (10,12), (8,10), (1,10), (6,10) |
| Low | 1.52 | (10,11) | |
| High | 10.61 | (6,11), (11,12), (8,11), (1,11), (7,11), (5,11), (3,11), | |
| Very high | 4.55 | (4,11), (2,11), (9,11) |
| Closest | Farthest | Ranking | ||
|---|---|---|---|---|
| Pair of Decision-Makers | Cosine Distance | Pair of Decision-Makers | Cosine Distance | |
| (3,5) | 0.004 | (10,12) | 0.372 | 1 |
| (3,6) | 0.006 | (4,10) | 0.367 | 2 |
| (4,12), (5,6) | 0.007 | (1,10) | 0.324 | 3 |
| (5,11) | 0.011 | (8,12) | 0.289 | 4 |
| (1,12) | 0.012 | (4,8) | 0.281 | 5 |
| Closest | Farthest | Ranking | ||
|---|---|---|---|---|
| Pair of Decision-Makers | Cosine Distance | Pair of Decision-Makers | Cosine Distance | |
| (4,6), (6,8), (8,9) | 0.003 | (3,12) | 0.492 | 1 |
| (5,8), (5,9), | 0.004 | (6,12) | 0.466 | 2 |
| (4,8) | 0.006 | (5,12) | 0.457 | 3 |
| (7,9) | 0.007 | (4,12) | 0.447 | 4 |
| (5,6), (6,9) | 0.010 | (8,12) | 0.438 | 5 |
| Closest | Farthest | Ranking | ||
|---|---|---|---|---|
| Pair of Decision-Makers | Cosine Distance | Pair of Decision-Makers | Cosine Distance | |
| (3,6) | 0.008 | (4,10) | 0.346 | 1 |
| (6,9) | 0.014 | (10,11) | 0.344 | 2 |
| (3,5), (5,7), (7,9) | 0.016 | (4,12) | 0.309 | 3 |
| (5,6) | 0.017 | (11,12) | 0.236 | 4 |
| (2,7) | 0.023 | (1,10), (8,10) | 0.232 | 5 |
| Closest | Farthest | Ranking | ||
|---|---|---|---|---|
| Pair of Decision-Makers | Cosine Distance | Pair of Decision-Makers | Cosine Distance | |
| (4,8) | 0.001 | (10,11) | 0.526 | 1 |
| (5,6) | 0.002 | (4,10) | 0.470 | 2 |
| (6,8) | 0.004 | (6,10), (8,10) | 0.452 | 3 |
| (5,8) | 0.006 | (3,11) | 0.440 | 4 |
| (4,6) | 0.008 | (5,10) | 0.421 | 5 |
| Closest | Farthest | Ranking | ||
|---|---|---|---|---|
| Pair of Decision-Makers | Cosine Distance | Pair of Decision-Makers | Cosine Distance | |
| (1,3), (1,5), (1,7), (1,8), (1,12), (2,4), (3,5), (3,7), (3,8), (3,12), (5,7), (5,8), (5,12), (7,8), (7,12), (8,12) | 0.000 | (6,11) | 0.705 | 1 |
| (1,6), (2,9), (4,9), (6,8), (6,12) | 0.004 | (3,11) | 0.666 | 2 |
| (5,6), (6,7) | 0.005 | (1,11), (8,11), (11,12) | 0.665 | 3 |
| (3,6) | 0.007 | (5,11), (7,11) | 0.655 | 4 |
| (2,3), (3,4) | 0.092 | (2,11), (4,11) | 0.529 | 5 |
| Decision Goal/Decision Construct | Range | Mean Value | |
|---|---|---|---|
| Pearson correlation coefficients | decision goal | 0.989~0.047 | 0.5180 |
| decision construct CA | 0.997~−0.41 | 0.2935 | |
| decision construct CB | 0.986~0.109 | 0.5475 | |
| decision construct CC | 0.998~−0.89 | 0.0540 | |
| decision construct CD | 1.000~0.947 | 0.9735 | |
| decision construct CE | 1.000~−0.963 | 0.0185 | |
| Cosine distance | decision goal | 0.004~0.372 | 0.1012 |
| decision construct CA | 0.003~0.492 | 0.1290 | |
| decision construct CB | 0.008~0.346 | 0.1143 | |
| decision construct CC | 0.001~0.526 | 0.1905 | |
| decision construct CD | 0.000~0.028 | 0.0038 | |
| decision construct CE | 0.000~0.705 | 0.1809 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fu, C.-H.; Chen, C.-Y. A Study on Decision-Making Opinion Exploration in Windows-Based Information Security Monitoring Tool Development. Sustainability 2021, 13, 3815. https://doi.org/10.3390/su13073815
Fu C-H, Chen C-Y. A Study on Decision-Making Opinion Exploration in Windows-Based Information Security Monitoring Tool Development. Sustainability. 2021; 13(7):3815. https://doi.org/10.3390/su13073815
Chicago/Turabian StyleFu, Chen-Hua, and Chih-Yung Chen. 2021. "A Study on Decision-Making Opinion Exploration in Windows-Based Information Security Monitoring Tool Development" Sustainability 13, no. 7: 3815. https://doi.org/10.3390/su13073815
APA StyleFu, C.-H., & Chen, C.-Y. (2021). A Study on Decision-Making Opinion Exploration in Windows-Based Information Security Monitoring Tool Development. Sustainability, 13(7), 3815. https://doi.org/10.3390/su13073815






