Design of a Secure Energy Trading Model Based on a Blockchain
Abstract
1. Introduction
2. Background
2.1. Prosumer
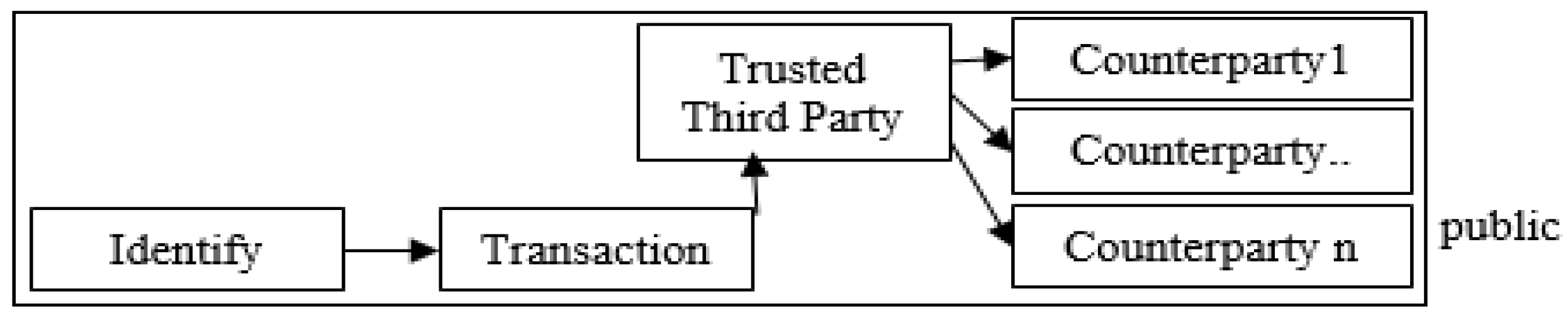
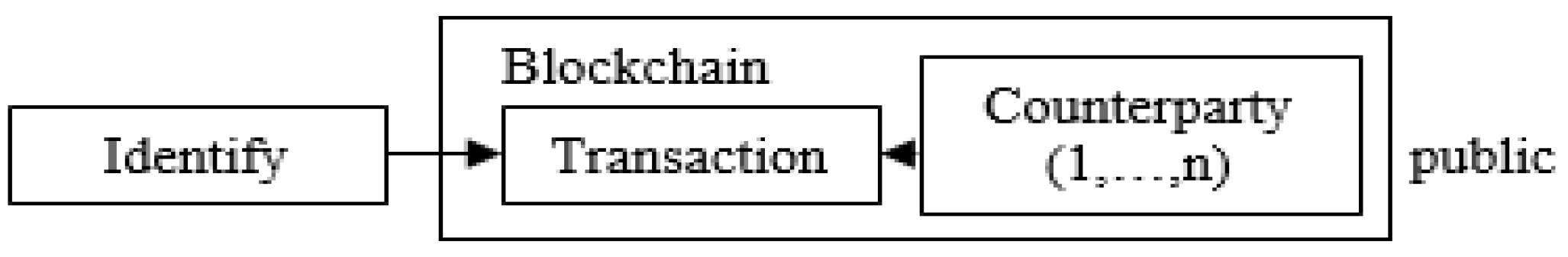
2.2. Blockchain
2.3. Problem Definition
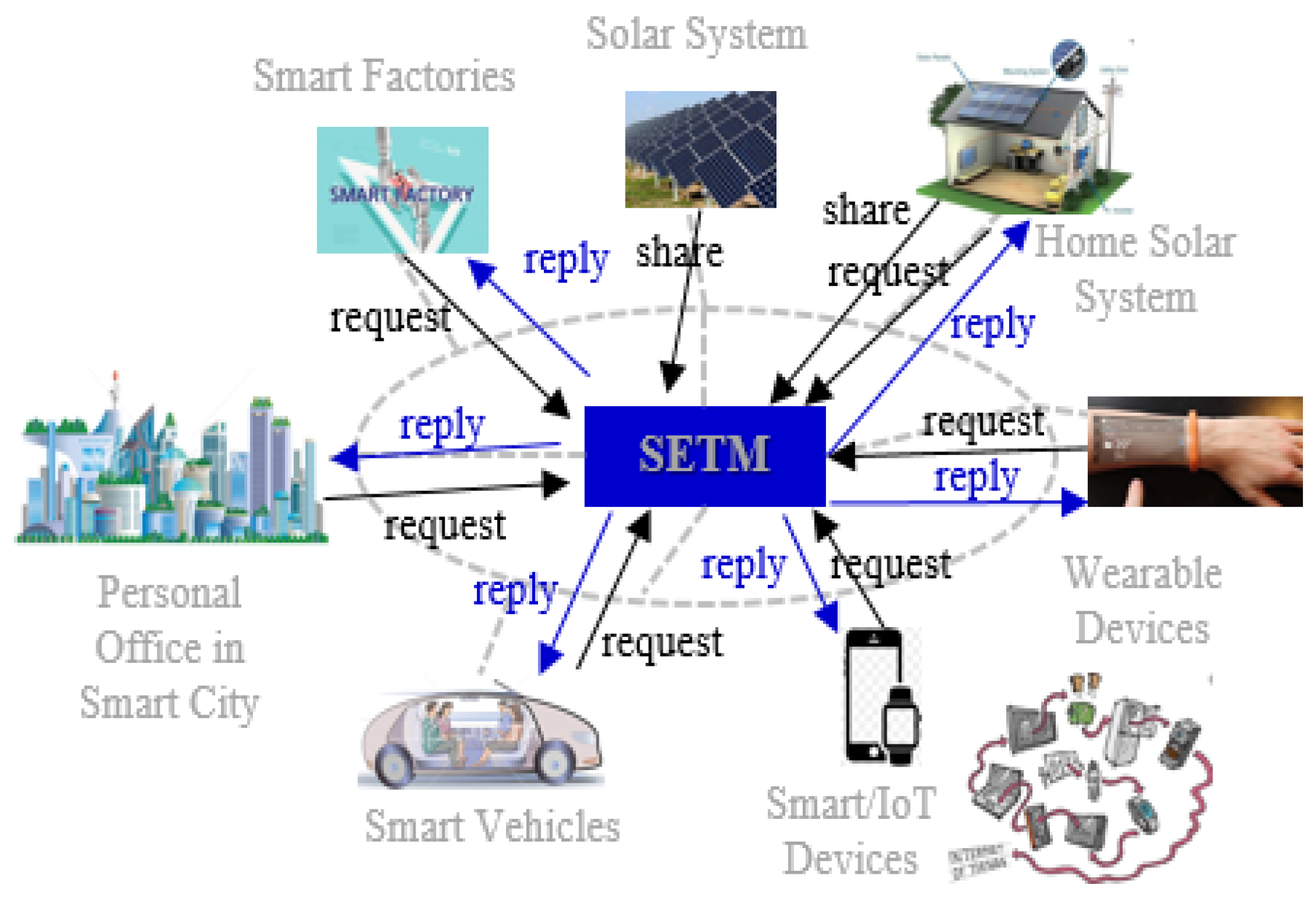
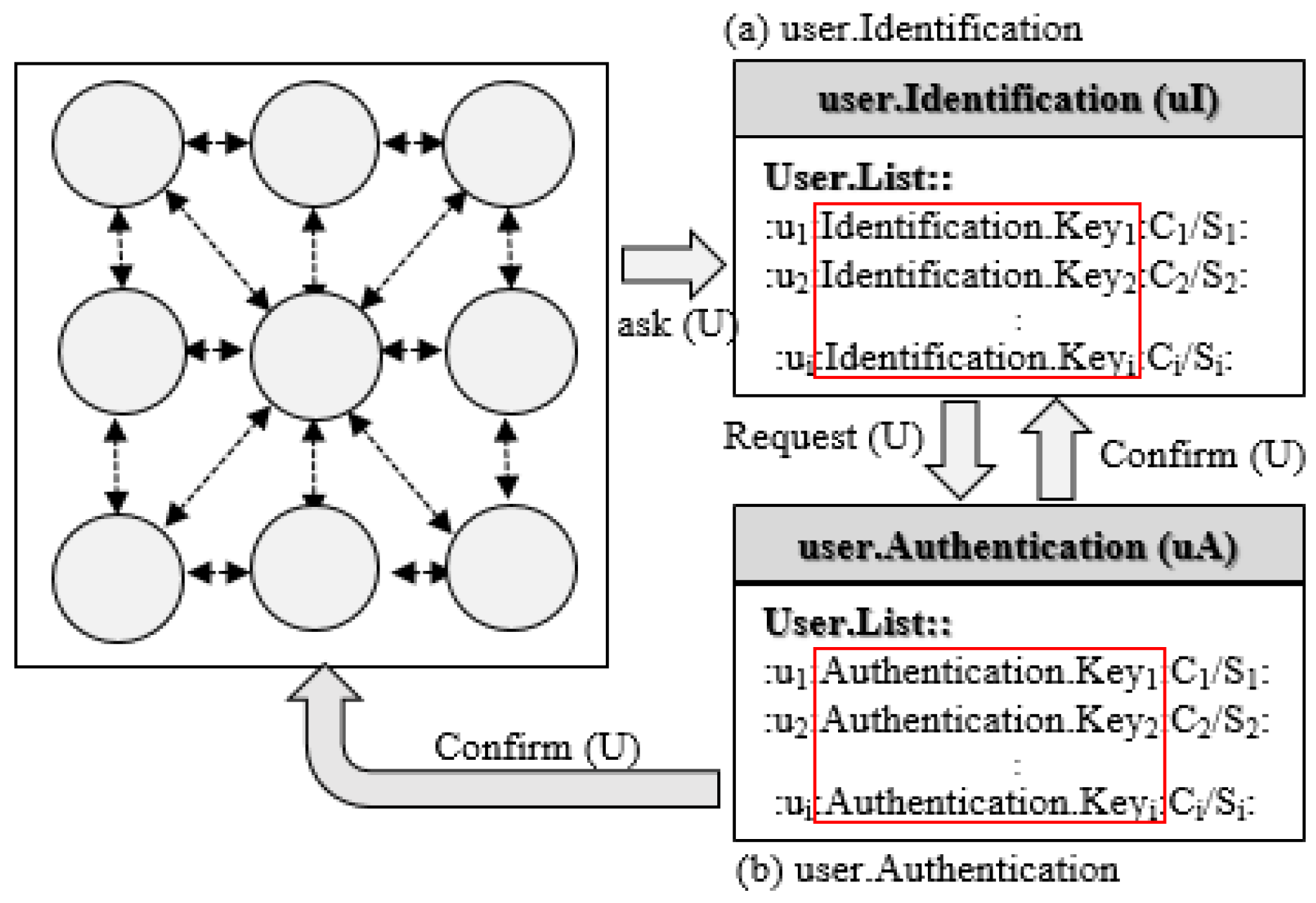
3. Secure Energy Trading Model (SETM)
3.1. SETM Structure
3.2. Energy Market Mechanism
3.3. Messages Flow in SETM
4. Implementation
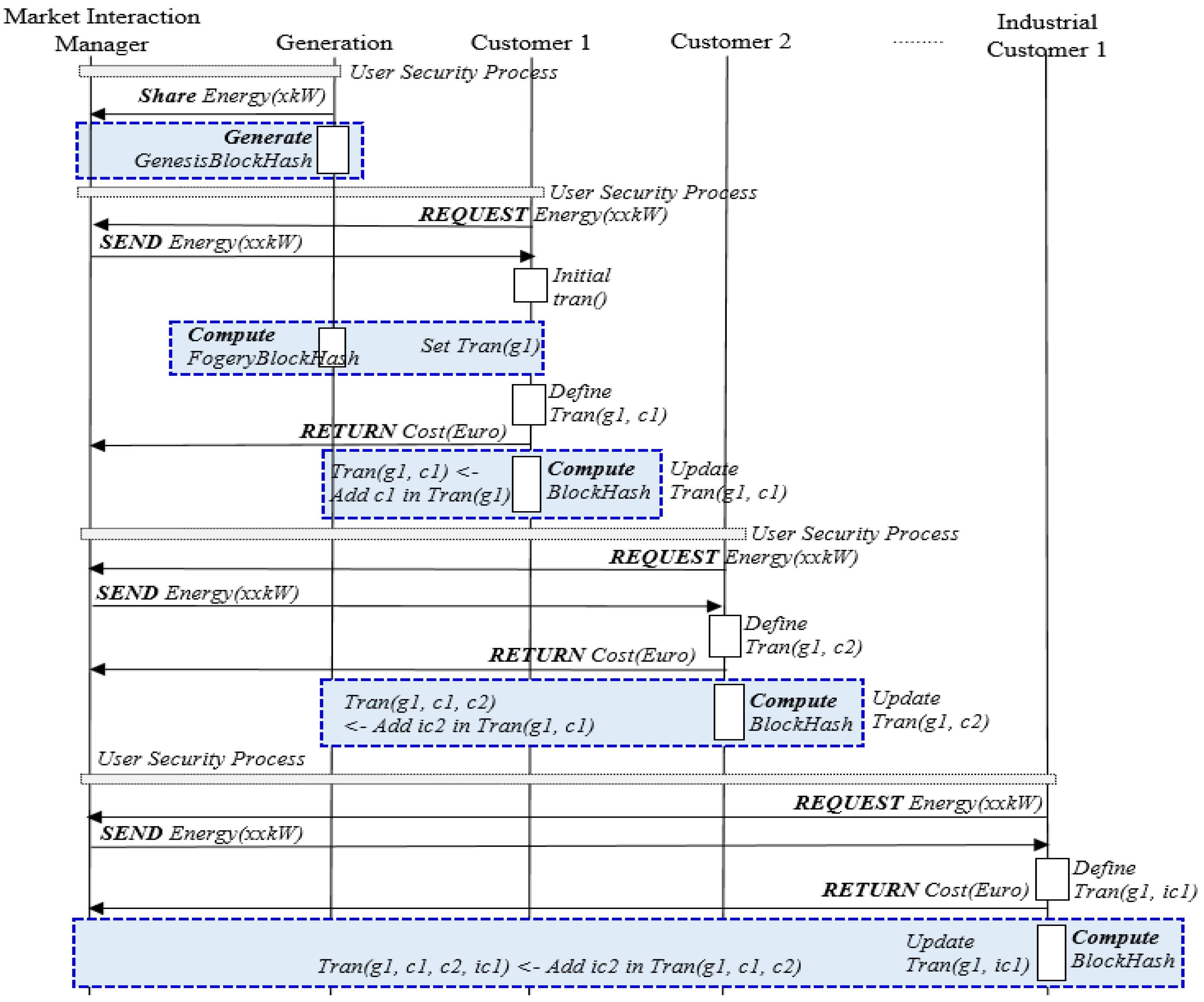
4.1. Case Study
4.2. SETM Sequence Diagram
| Algorithm 1 user.SecurityAlgorithm |
|
5. Discussion
5.1. Model Compare
5.2. Security Analysis
| Algorithm 2 SETM.Transaction Algorithm |
|
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| SETM | Secure Energy Trade Model |
| IoT | Internet of Things |
| 5G | 5 Generation |
References
- Kosnik, E. Production for consumption: Prosumer, citizen-consumer, and ethical consumption in a postgrowth context. Econ. Anthropol. 2018, 5, 123–134. [Google Scholar] [CrossRef]
- Zafar, R.; Mahmood, A.; Razzaq, S.; Ali, W.; Naeem, U.; Shehzad, K. Prosumer based energy management and sharing in smart grid. Renew. Sustain. Energy Rev. 2018, 82, 1675–1684. [Google Scholar] [CrossRef]
- Zhang, S.; Lee, J.H. A Group Signature and Authentication Scheme for Blockchain-Based Mobile-Edge Computing. IEEE Internet Things J. 2019, 7, 4557–4565. [Google Scholar] [CrossRef]
- Hwang, J.; Choi, M.i.; Lee, T.; Jeon, S.; Kim, S.; Park, S.; Park, S. Energy prosumer business model using blockchain system to ensure transparency and safety. Energy Procedia 2017, 141, 194–198. [Google Scholar] [CrossRef]
- Park, L.W.; Lee, S.; Chang, H. A sustainable home energy prosumer-chain methodology with energy tags over the blockchain. Sustainability 2018, 10, 658. [Google Scholar] [CrossRef]
- Andoni, M.; Robu, V.; Flynn, D.; Abram, S.; Geach, D.; Jenkins, D.; McCallum, P.; Peacock, A. Blockchain technology in the energy sector: A systematic review of challenges and opportunities. Renew. Sustain. Energy Rev. 2019, 10, 143–174. [Google Scholar] [CrossRef]
- Sultana, T.; Almogren, A.; Akbar, M.; Zuair, M.; Ullah, I.; Javaid, N. Data sharing system integrating access control mechanism using blockchain-based smart contracts for IoT devices. Appl. Sci. 2020, 10, 488. [Google Scholar] [CrossRef]
- Yan, Z.; Lee, J.H. The road to DNS privacy. Future Gener. Comput. Syst. 2020, 112, 604–611. [Google Scholar] [CrossRef]
- Guan, Z.; Lu, X.; Wang, N.; Wu, J.; Du, X.; Guizani, M. Towards secure and efficient energy trading in IIoT-enabled energy internet: A blockchain approach. Future Gener. Comput. Syst. 2020, 110, 686–695. [Google Scholar] [CrossRef]
- Madhav, B.V.; Balu, S.B.; Laxman, W.S. Time Efficient Secure Negotiation in E-Trading. IRE J. 2019, 2. [Google Scholar]
- Sharma, P.K.; Park, J.H. Blockchain based hybrid network architecture for the smart city. Future Gener. Comput. Syst. 2018, 86, 650–655. [Google Scholar] [CrossRef]
- Liu, D.; Lee, J.H. CNN based Malicious Website Detection by Invalidating Multiple Web Spams. IEEE Access 2020, 8, 97258–97266. [Google Scholar] [CrossRef]
- Mengelkamp, E.; Notheisen, B.; Beer, C.; Dauer, D.; Weinhardt, C. A blockchain-based smart grid: Towards sustainable local energy markets. Comput. Sci. Res. Dev. 2018, 33, 207–214. [Google Scholar] [CrossRef]
- Hahn, A.; Singh, R.; Liu, C.C.; Chen, S. Smart contract-based campus demonstration of decentralized transactive energy auctions. In Proceedings of the 2017 IEEE Power & Energy Society Innovative Smart Grid Technologies Conference (ISGT), Washington, DC, USA, 23–26 April 2017; pp. 1–5. [Google Scholar]
- Aitzhan, N.Z.; Svetinovic, D. Security and privacy in decentralized energy trading through multi-signatures, blockchain and anonymous messaging streams. IEEE Trans. Dependable Secur. Comput. 2016, 15, 840–852. [Google Scholar] [CrossRef]
- Cheng, S.; Zeng, B.; Huang, Y. Research on Application Model of Blockchain Technology in Distributed Electricity Market; IOP Conference Series: Earth and Environmental Science; IOP Publishing: Bristol, UK, 2017; Volume 93, p. 012065. [Google Scholar]




| Name | Days for Forecasting | min bid Euro/MWh | max bid Euro/MWh |
|---|---|---|---|
| personal consumer 1 | 9 | 34 | 46 |
| (Home solar system) | |||
| personal consumer 2 | 4 | 34 | 46 |
| (Wearable Devices) | |||
| personal consumer 3 | 9 | 36 | 48 |
| (Smart Devices) | |||
| personal consumer 4 | 18 | 36 | 48 |
| (Smart Vehicles) | |||
| personal consumer 5 | 8 | 38 | 48 |
| (Personal Office) | |||
| industrial consumer 1 | 1393 | 36 | 50 |
| (Smart Factories) | |||
| generation 1 | 342 | 40 | 52 |
| (Solar System) |
| Ref. | Main Technologies | Pricing Mechanism | Security Analysis |
|---|---|---|---|
| [13] | private blockchain, smart meters | market auction mechanism | Unknown people can infer a user electricity usage habits based on the data. |
| [14] | blockchain, smart meters, smart contract | market auction mechanism | In case, the cost of each auction can be retrieved in the blockchain, the subsequent auction may be affected. |
| [15] | blockchain, multiple signatures, anonymous encrypted information flow | negotiate energy prices anonymously | Achieved many security and privacy requirements. |
| [5] | blockchain, IoT | adjust prices of electric energy according to the trading situation | nothing |
| [16] | blockchain | distributed pricing mechanism | include the private information in the transaction |
| SETM | blockchain, IoT | negotiable energy prices, multi-agent used | use the user security (user authentication and user identification |
| Security Problem | Security Strength |
|---|---|
| Lack security and stability | SETM applied user.security = [uA, uI] to all participants, so without user.security, no one can join the trade system. The user.security can keep the security in stability. |
| Vulnerable to forgery and price tampering | A blockchain in SETM prevents the forgery and the tampering in the transactions. |
| Vulnerable to participants exploiting the system by trying to modify/block/interrupt the transactions | If someone who has joined the trade system, modified the transaction, then the rules of the blockchain are broken. If the rules are broken, the trade system will be blocked. |
| Centralization of the data handling process is inadequate to keep track of the vast amount of data. | Basically, a blockchain is a peer-to-peer distributed digital record of validated transactions, not the centralized data handling. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ko, H.; Praça, I. Design of a Secure Energy Trading Model Based on a Blockchain. Sustainability 2021, 13, 1634. https://doi.org/10.3390/su13041634
Ko H, Praça I. Design of a Secure Energy Trading Model Based on a Blockchain. Sustainability. 2021; 13(4):1634. https://doi.org/10.3390/su13041634
Chicago/Turabian StyleKo, Hoon, and Isabel Praça. 2021. "Design of a Secure Energy Trading Model Based on a Blockchain" Sustainability 13, no. 4: 1634. https://doi.org/10.3390/su13041634
APA StyleKo, H., & Praça, I. (2021). Design of a Secure Energy Trading Model Based on a Blockchain. Sustainability, 13(4), 1634. https://doi.org/10.3390/su13041634







