As a result of the advancement of technology in power systems, the importance of using new methods to protect smart grids (SGs) becomes more apparent, and one of these methods is blockchain. In October 2008, in the reference [
1], blockchain technology distribution was seen under the alias “Satoshi Nakamoto”, with the aim of supporting the first Bitcoin cryptocurrency, and it resulted in the start of the Bitcoin network in January 2009. After that, Bitcoin has arrived inchmeal at the financial industry systems, and is recognized as the most influential and important cryptocurrency. Besides, blockchain technology after Bitcoin has become a game-variable innovation around the world, and lots of industries exist which will be interrupted via blockchain, including the life sciences, legal industry, health care, financial services, cyber security, supply series management, cloud storage, charity, electing, government, social interests, energy management, private transport and ride sharing, retail, and actual estate between others [
2,
3,
4]. Blockchain usages in carbon credits, distributed energy resources, and renewable and power system data security versus cyber-attacks are really encouraging [
5,
6].
So, the available electricity market must be modified to benefit from this novel technology. In this study, there are two purposes, including examining how a great industrial user is able to manage best under such a novel blockchain on the basis of an electricity market as well as how to be safe from cyber-attacks like false data injection attack (FDIA).
1.1. Background
Networking, informatization, and intelligentization have been gradually realized by power systems [
7] with the help of the usage of advanced information technology like calculation, communication, control, and perception, as well as using the expansion of the cyber-physical power system (CPPS). Meanwhile, real-time analytical promotion, efficient allocation of power systems and scientific decisions, interface terminals, and the open communication networks also carry potential security risks [
8,
9]. In comparison with the relatively strong initial power system, investigations on the security protection of electrical power information networks are in the initial stages, with a great deal of security vulnerabilities unknown [
10]. Due to the remarkable interest relevance and high transmissibility of an electrical power grid, after the attack, it will have a rigid effect on industrial production, power security, and the livelihood of people, which has attracted considerable regard [
11]. As a new attack method for major industrial facilities, safe and stable power system operation, whose defense and attack structure needs further research and investigation [
12], have been threatened by cyber-attack.
Pursuant to the purposes of the attack, cyber-attacks versus power systems are able to be categorized as integrity, confidentiality of information, and destruction of availability. The availability destruction is obtained in attacks modifying network topology, black hole attacks, and unavailable information due to communication interruption, whose common layouts are denial of service (DOS) attacks. The integrity destruction is obtained in replay attack, man-in-the-middle attack, and wrong information due to false data injection (FDI), whose common layouts are FDI attacks. The confidentiality destruction is obtained in internal employee attack, utilization of malware, and illegal usage and data leakage, whose common layout is brute force password cracking [
13,
14]. As a common way to destroy the integrity of information, the FDIA is able to interrupt the outcomes of state estimation analysis, therefore misleading the control center’s decision. The FDIA was first introduced by Liu in 2009, and the FDIA’s point is to conduct coordinated attacks on sensors, falsify specific measurements, and manipulate particular state estimation information [
15,
16].
Over the past decade, the concept of the micro-grid (MG) is gaining more popularity resulting from its economic and technical benefits like higher reliability and resilience, closeness to the users, higher power quality, lower power losses, less operation cost, and self-healing capability [
17,
18]. Nevertheless, along with these benefits, several significant challenges exist in the management and operation of the micro-grids (MGs), which have attracted the attention of plenty of researchers [
19]. In the ordinary power network, the distributed system operator (DSO) is responsible for applying the optimal energy management throughout the grid.
Nevertheless, in recent power networks, DSOs and MGs might have various policies and owners. As the network is able to be formed of some intercoupled MGs, the total network operation can be significantly affected by any change in any of the subsystems. So, a coordinator of a strong system level is required for the total network energy management.
Developments in management and economic laws in the electricity industry have long been taking place in this large industry under the congestion of the power system structure. The problem of congestion of the transmission network is considered as one of the most important issues in the discussion of the full implementation of the restructuring of power systems. Congestion means using a transmission network outside the operating range. Restrictions such as transmission line capacity and transformers, maximum and minimum voltage values, and maximum voltage angles of the busbars (which are determined by various studies on the network) are among the limitations of operation. The consequences of congestion in power systems include sudden price jumps in some areas, increased market power, increased electricity prices, reduced efficiency of the electricity network, reduced competition, etc. [
20,
21]. When the power grid is congested, the capacity of some transmission lines no longer meets the needs of all customers. In this case, the independent system operator, as the main institution for maintaining the security of the power system, acts in different ways to manage the network’s congestion. Independent system operation (ISO) is an institution that is responsible for coordinating and maintaining the security and reliability of power systems; in this regard, density management is the main task of this institution, which always tries to encourage investors and private owners of electric generators to participate in density management [
22].
Congestion may be demonstrated during operation or in network operation planning. When using the power system, factors such as the sudden departure of one or more transmission lines or transformers in the network, the unexpected cessation of production in one or more generators in the system, and unforeseen changes in energy consumption, as well as uncoordinated transactions in electricity sales, can lead to network congestion. In planning the operation of a power system, the provision of an inappropriate program for the generation and consumption of electricity, the implementation of which violates the restrictions on the operation of the transmission network, is the main cause of network congestion [
23].
Lately, blockchain has been promoted as a reliable and effective technology for online financial operations via communication only between peer-to-peer transaction networks and without the intervention of third parties [
24]. The data are able to be reserved in the distributed databases, which are generally small, instead of reserving all data in a central data center by using blockchain. This might result in increasing the total cloud system security, since more of the losses from attacks on such databases are simply able to be locally prevented. So, blockchain is able to be successfully used in different areas, like the Internet of Things (IoT) and the financial sector.
Peer-to-peer (P2P) energy trading research based on blockchain has been studied. In [
25], a blockchain with seven components based on MG energy market was offered and a smart contract was used to make a high-performance information system on the basis of the blockchain strategy. In [
26], blockchain has been used to constitute a machine to machine electricity market in a chemical industry context, and a private blockchain on the basis of software system multichain was applied to validate energy transaction.
With the aim of facilitating a P2P market, a two-layer energy market system on the basis of multi-agent and blockchain technology has been suggested in [
27]. For electric vehicles, also, a blockchain-based consortium for local aggregators has been proposed in [
28] with the aim of auditing and validating electricity market plug-in hybrid electric vehicles (PHEVs). A novel blockchain-based energy system has been suggested in [
29] with the aim of enabling electric vehicles to share transactions and publicly audit without the support of any reliable interposition. Plus, the consortium blockchain method was expanded to generic energy blockchain transactions with the aim of transaction security and credit-based payment. In [
30], a decentralized energy dealing system using blockchain on the basis of tokens, streams of unknown encrypted messaging, and multi-signatures is proposed with the aim of solving issues of the privacy and security of information of demand and dealing.
In [
31], forward and real-time markets have been proposed for bilateral agreements in P2P energy dealing. In [
32], the energy broker’s role has been proposed via amplification learning for indirect energy trading between customers. For electric vehicles, [
33], a special P2P trading system was studied with the aim of reducing the effect of the charging procedure during the working hours of power systems. Additionally, in [
34], in P2P energy trading, different game– and auction–theoretic methods were studied, and in [
35], especially, a Nash bargaining view was applied with the aim of developing a frame of bilateral trans-active energy dealing for numerous contributors. For P2P trading, in [
36], restrictions of physical low-voltage networks have been investigated by applying sensitivity analysis. Furthermore, in [
37], power damages were assigned for MG peer-to-peer blockchain market contributors. At the power distribution system level, [
38] suggested a day-ahead forecasting energy market strategy to help distribution system operators in order to optimize distributed energy resource applications; however, in [
39], a novel P2P energy market on the basis of the content of multi-class energy management with the aim of coordinating dealing amongst prosumers with heterogeneous preferences was introduced.
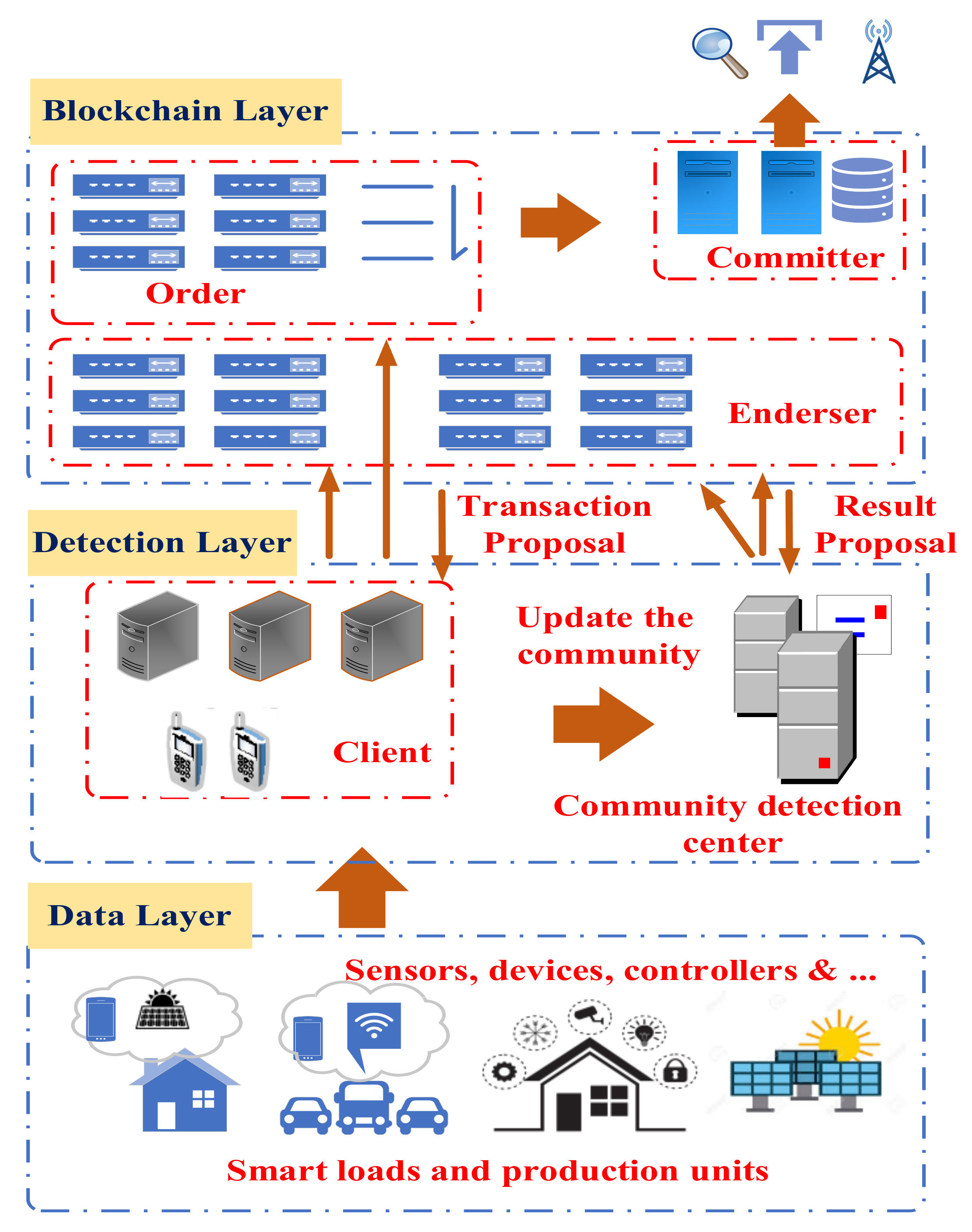
Blockchain can be considered as the main technology of Bitcoin and some other types of cryptocurrencies, making this one of the world’s most breathtaking technologies in 2010. The problem of transmission network conjunction has always been one of the serious obstacles against the full implementation of the restructuring of power systems, the correct and free communication of the producers and consumers, and the main challenge of independent system operation. Therefore, the policy of using distributed generation resources to manage the conjunction of transmission lines has been of particular importance. The policy of applying the transparent blockchain technology will aid in reducing risks and provide superior security to the grid, hence financial fraud is eliminated and the entire operational charge is attenuated. In order to illustrate the matters occurring in the usual blockchain layouts, mainly because of the storage and high level of elaborations of hash address computations, a blockchain technology is proposed in this article. Plus, a new data restoration technique is expanded with the aim of providing an approach to restore the appropriate and accurate data.
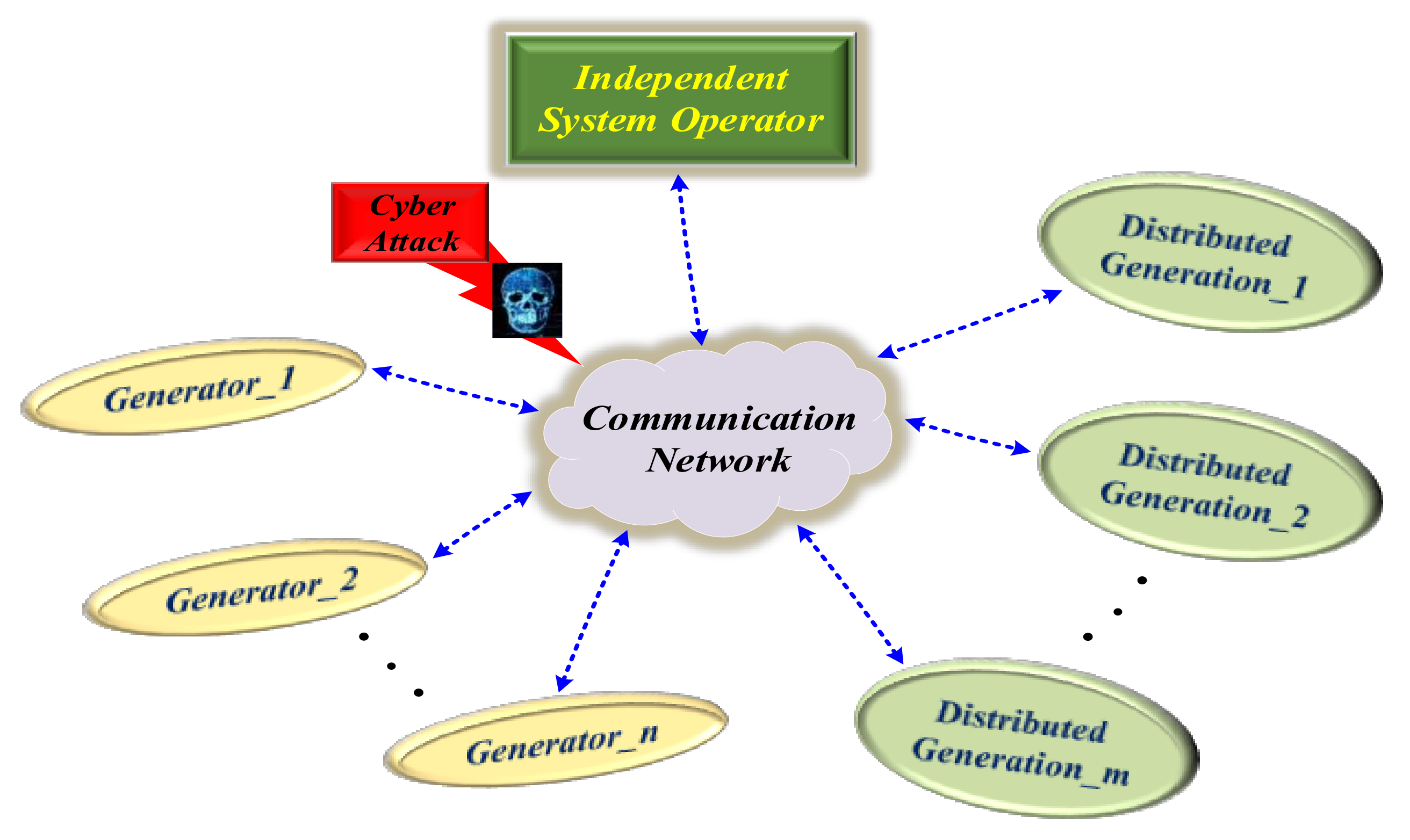
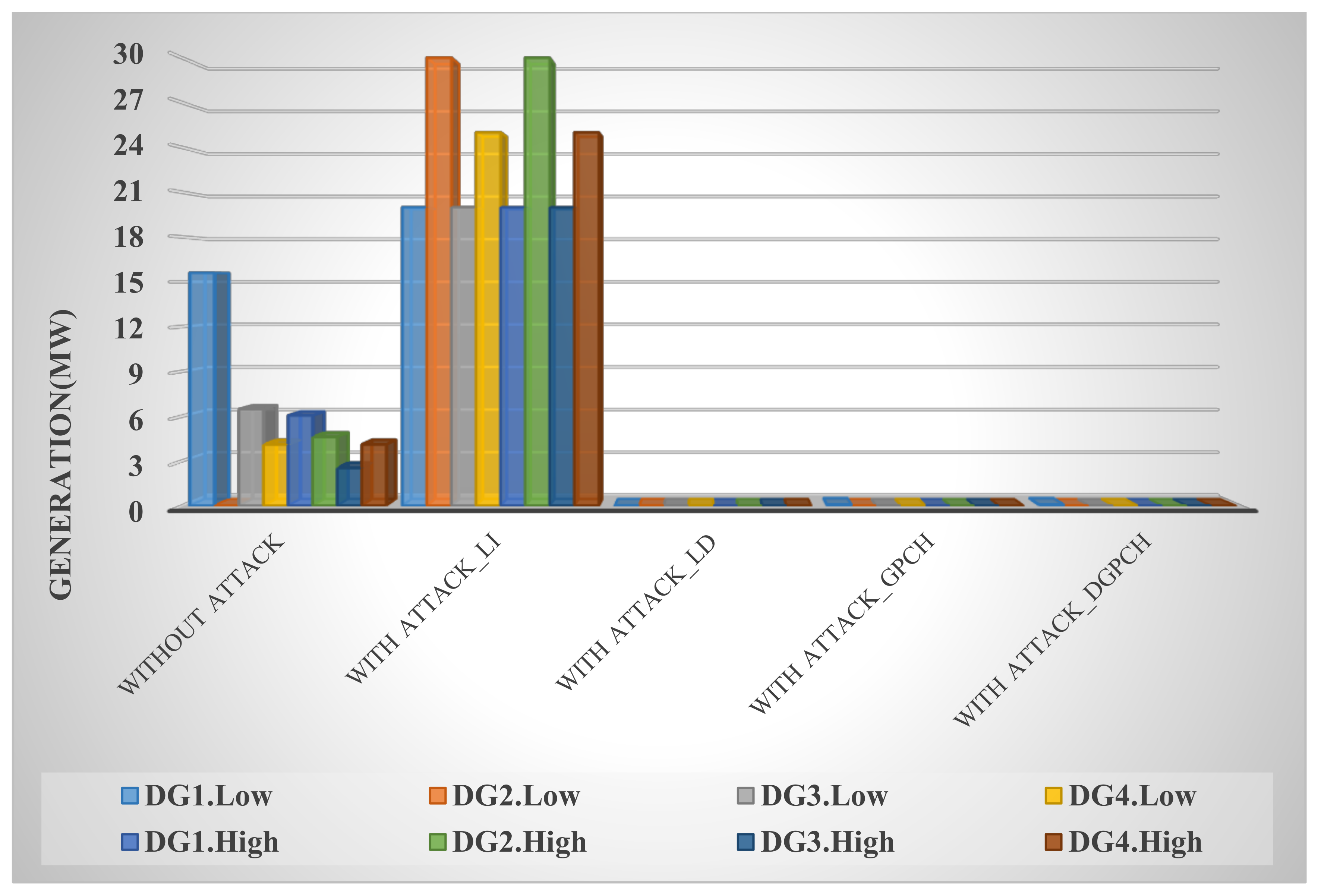
Nowadays, with the use of communication networks to exchange information between ISO and under-operating agents, sabotage cyber-attacks, including the false data injection attack (FDIA), are on the rise in order to destroy network stability and inflict financial losses. Therefore, providing a solution and policy to secure the information exchanged between systems is of great importance, so the use of blockchain technology as a solution to secure data is essential.
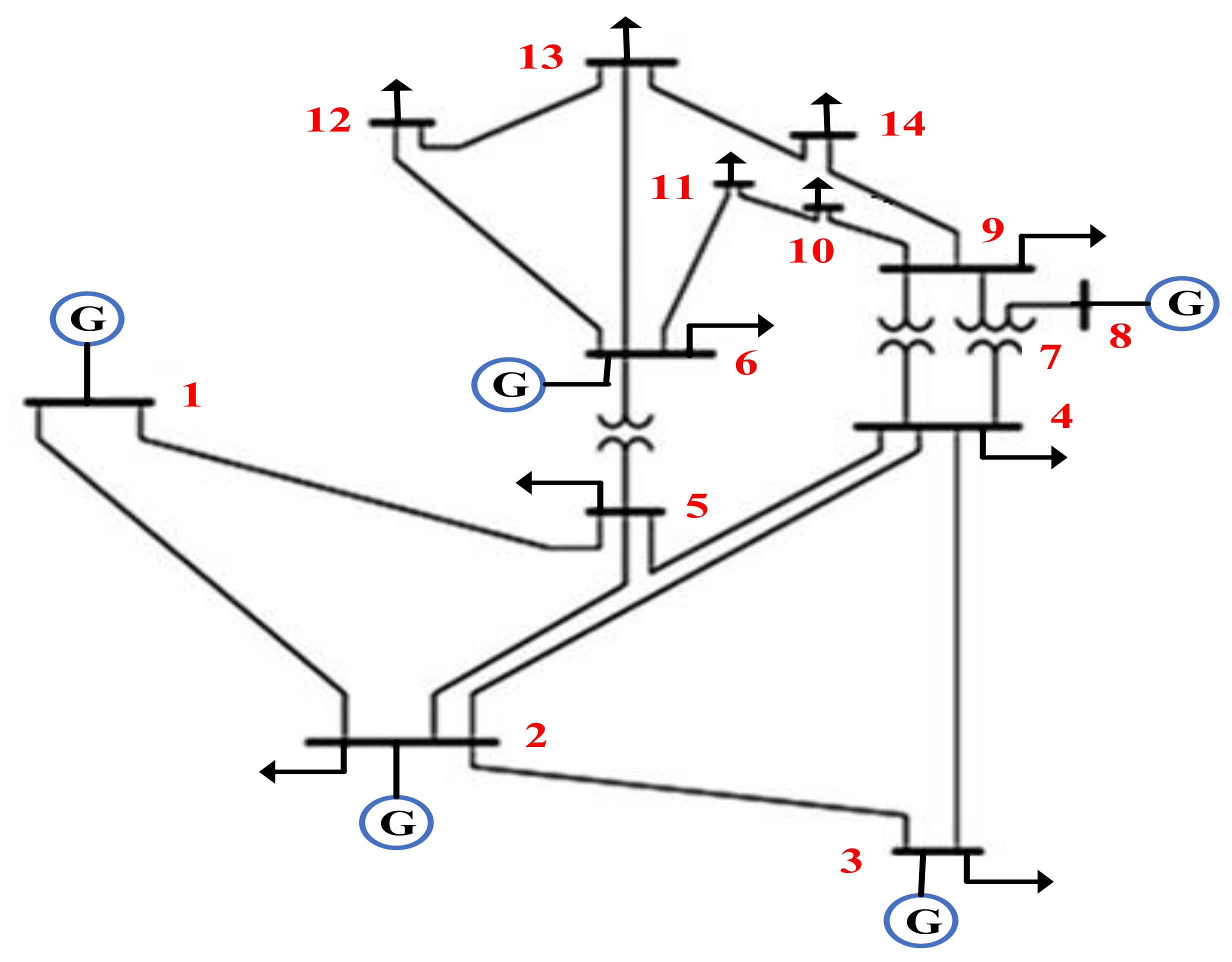
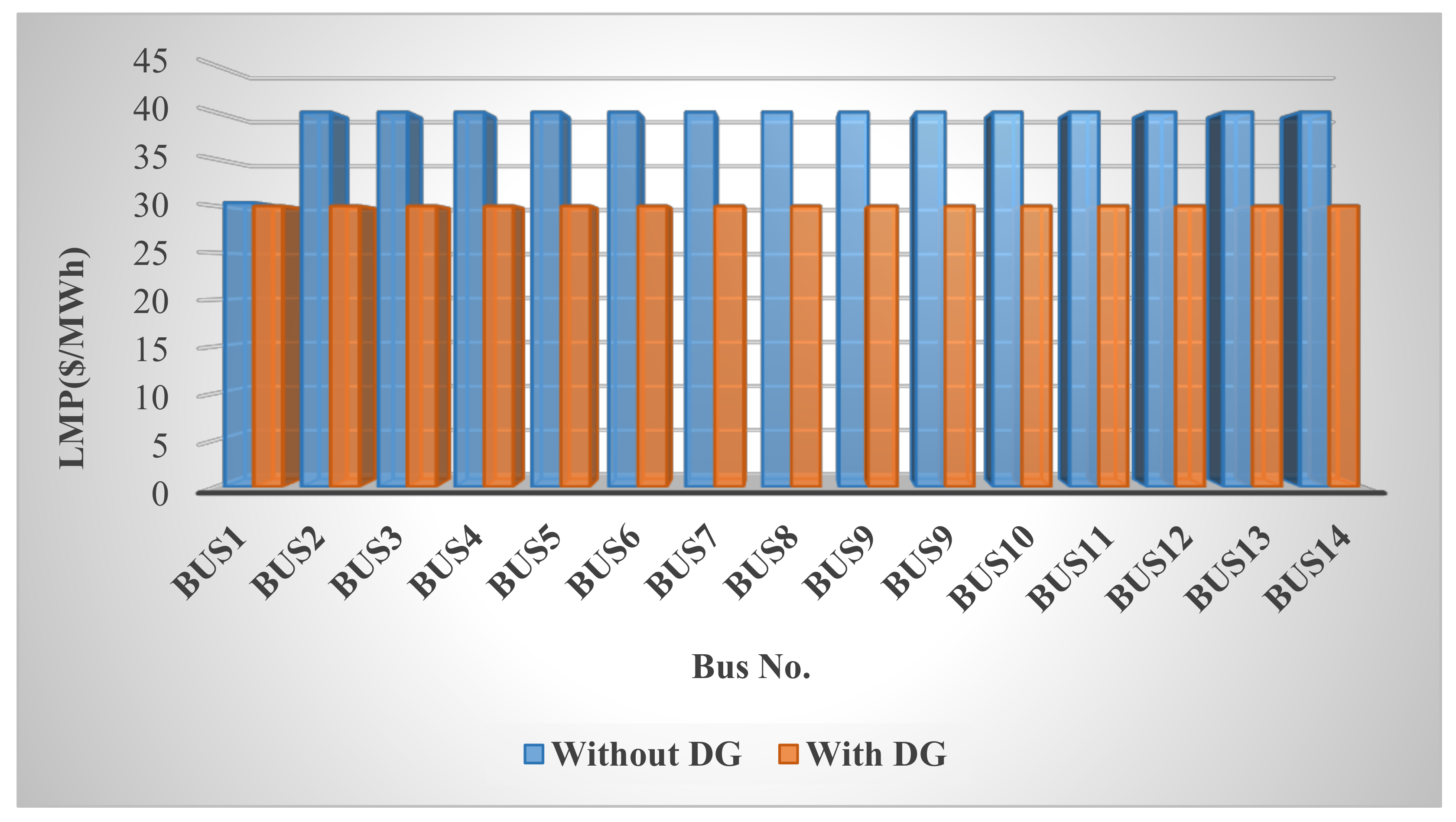
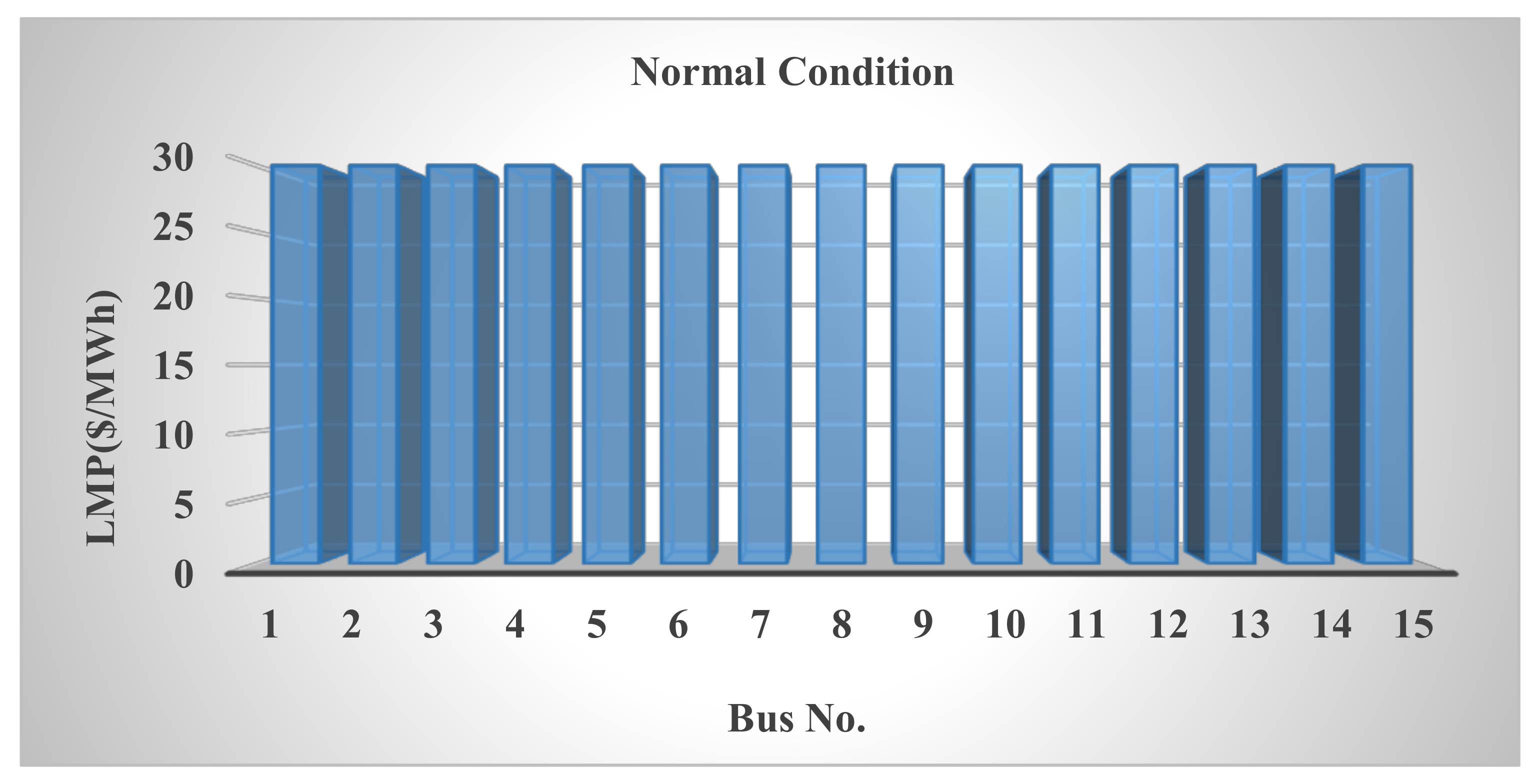
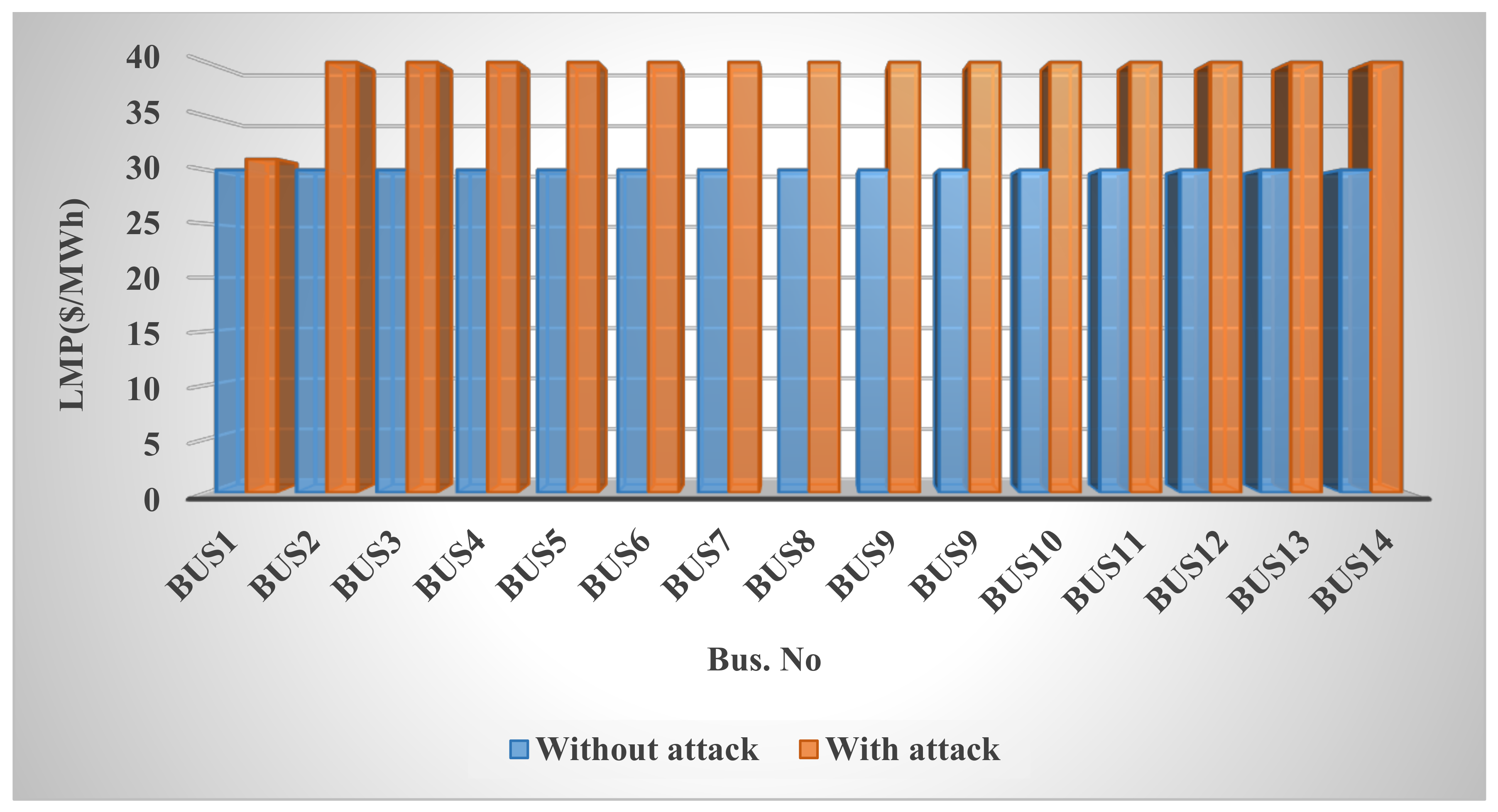
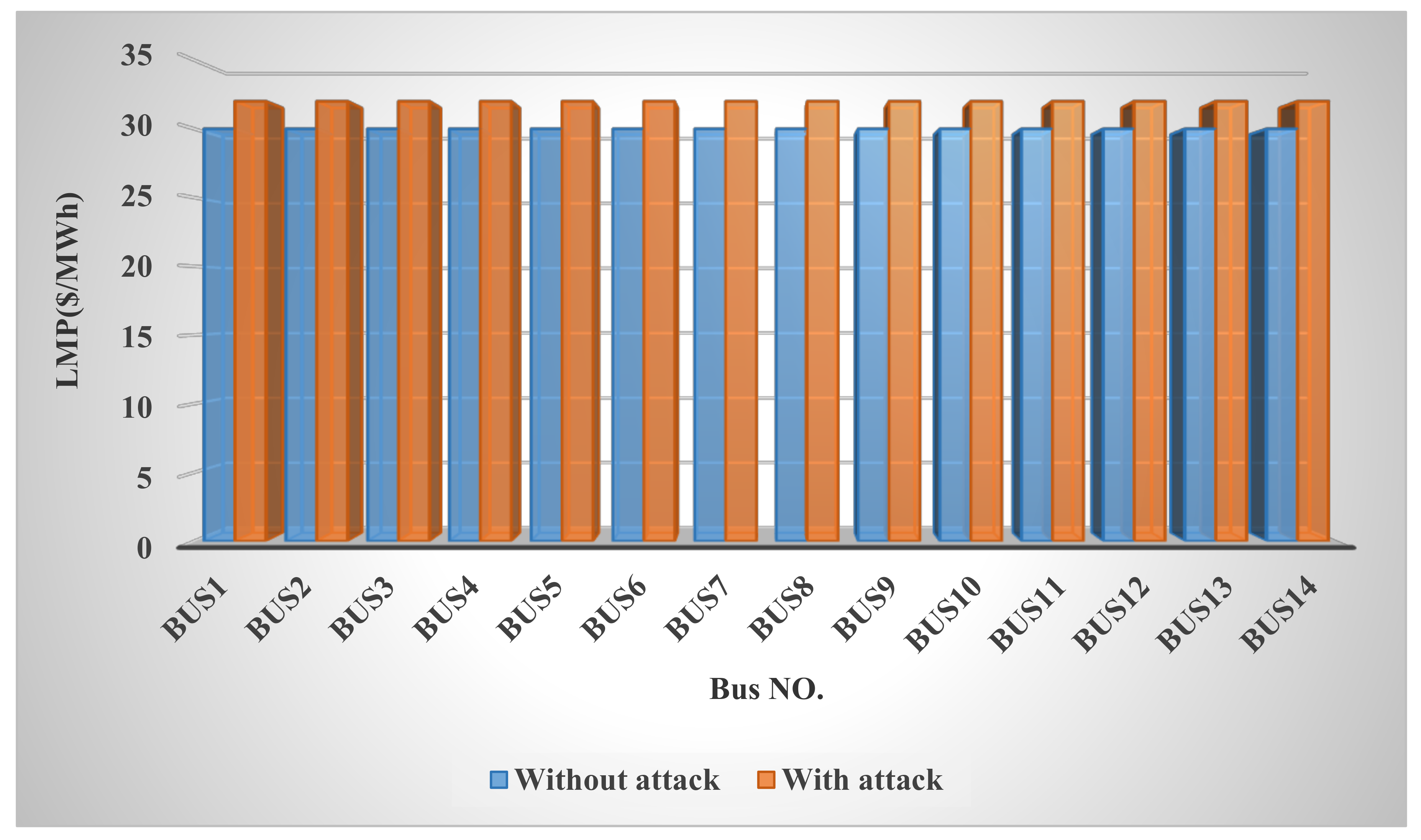
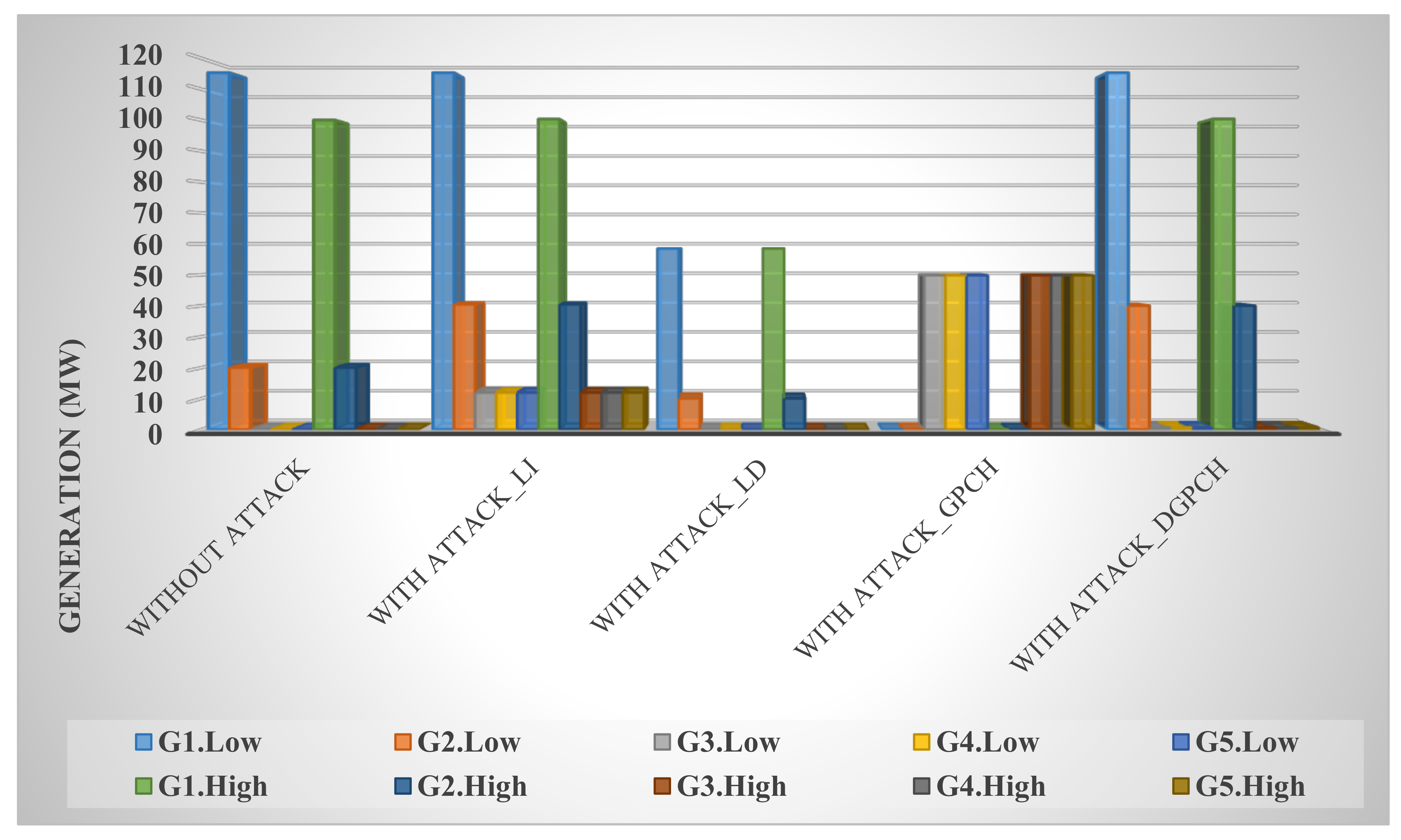
In this paper, the system under study is first examined under various conditions, including normal mode and false data injection into exchanged data such as loads, prices, and productions, and it is shown that this cyber-attack disrupts network congestion, reduces welfare, increases costs, and upsets the balance of production and demand.