Named Data Networking for Efficient IoT-based Disaster Management in a Smart Campus
Abstract
1. Introduction
- a thorough investigation and comparison of existing ICN-based DMS;
- the proposition, design, and development of an efficient DMS (i.e., NDN-DM), specifically related to disaster scenarios in an SC;
- mathematical modeling and formal verification of the proposed approach using timed automata-based transition systems and a real-time model checker, respectively;
- simulation of an IoT-based SC disaster scenario in NS2;
- evaluation and comparative analysis of the proposed scheme with a state-of-the-art NDN-based disaster management scheme shows promising results in terms of delay and energy consumption.
2. Related Work
2.1. Naming and Forwarding Approaches Used with the Named Data Network
2.2. PULL and PUSH Schemes
| Ref. | Problem Addressed Or Contribution | Parameters Evaluated | Tools Used | Limitation |
|---|---|---|---|---|
| [40] | Manage disaster scenarios | End-to-end delay. | NS3. | Effect on energy |
| using the ICN concept. | Traffic load. | DVB-S2. | consumption | |
| In disaster situations, various | Hit rate. | DVB-RCS2. | not defined. | |
| caching techniques applied. | ||||
| [41] | Baseline NDN framework | Save bandwidth. | ndnSIM | Consumer and |
| that helps in efficient | Efficient data | module. | producer are | |
| data retrieval based on the | retrieval time. | NS3. | both static nodes. | |
| same interest packet. | ||||
| [32] | Location-based NDN | High memory | MATLAB. | Applicable for |
| framework is proposed. | consumption. | small-sized data. | ||
| [53] | Hierarchical Naming | Scalability. | NS3. | Encryption applied, |
| scheme based on NDN | Security. | ndnSIM | which can be | |
| architecture is proposed. | module. | time-consuming. | ||
| [14] | Multiple PUSH-based | Reliable communication | MATLAB. | High resource |
| techniques are proposed. | between nodes. | consumption. | ||
| [43] | Model for forwarding | Delay to transfer | NS2. | Inefficient for |
| interest packets. | information. | disaster situations. | ||
| [31] | PUSH technique is | Decreased data transfer | ndnSIM. | Memory and energy |
| proposed for | time. | consumption in | ||
| VNDN. | IoT-based NDN. | |||
| [54] | DTN proposed with the | Memory consumption. | MATLAB. | Not suitable in IoT |
| help of ICN. | Accuracy measure in | because of resource | ||
| decentralized scenarios. | consumption. | |||
| [29] | Modified the existing | Increased throughput. | NS3. | Only suitable for |
| NDN by introducing SIT | post-disaster | |||
| (Satisfied Interest Table). | scenarios. | |||
| [45] | Emergency delivery of | Security improved by | MATLAB. | Unsupportive |
| message in the NDN-based | by using encryption. | in an IoT real | ||
| PULL technique. | Decreased delay in | environment. | ||
| message delivery. | ||||
| [46] | Routing protocol proposed | Energy efficiency. | NS3. | Incompatible in |
| for MANET using CCN. | disaster situations. | |||
| [13] | Architecture based on NDN | Interest satisfaction rate. | NS2. | Cloud infrastructure |
| for an IoT smart home | Data retrieval delay. | proposed but not | ||
| environment is proposed. | suitable for real time | |||
| disaster management. | ||||
| [47] | PUSH-based data delivery | Less power consumption. | MATLAB. | Not discussed in |
| using basic NDN | Effective in terms of | disaster management | ||
| architecture. | resource usage. | scenarios. | ||
| [27] | New protocol is proposed | Throughput increased. | NS2. | Packet collision |
| based on a VCCN (vehicular | Less interest packet delay. | SUMO. | not avoided. | |
| content centric network). | Less network load. | |||
| [55] | Efficient multicasting and | Gain high throughput. | NS2. | Extra overhead on |
| collision avoidance protocol | Less battery | the network due | ||
| is proposed for MANETs. | consumption. | to the routing table. | ||
| [44] | Hybrid NDN method is | Measured network | NS2. | Inefficient for |
| proposed for fragmented | efficiency through | complex networks. | ||
| networks. | latency and throughput. | Memory parameter | ||
| needs improvement. | ||||
| [38] | Framework is proposed | In disasters, efficient | Discrete | Evaluated only in |
| based on NDN/CCN | recovery of cached data. | event simulator. | the case of a fragmented | |
| architecture in case of link failure. | network. | |||
| [56] | Priority-based interest | Less queuing delay. | NS2. | Complex when |
| packet forwarding | Efficiently achieving | the number of nodes | ||
| mechanism in CCN. | content based on priority. | increased. |
3. Methodology
3.1. Design Details of NDN-DM
3.2. Smart Campus Use Case Scenario Used in NDN-DM
3.3. Disaster Event Handling in NDN-DM
3.4. Customization of Packet and Table Headers
3.5. Alert Packet Forwarding Algorithm
3.6. Mathematical Modeling and Analysis
4. Experimental Setup
5. Results Analysis and Discussion
5.1. Delay
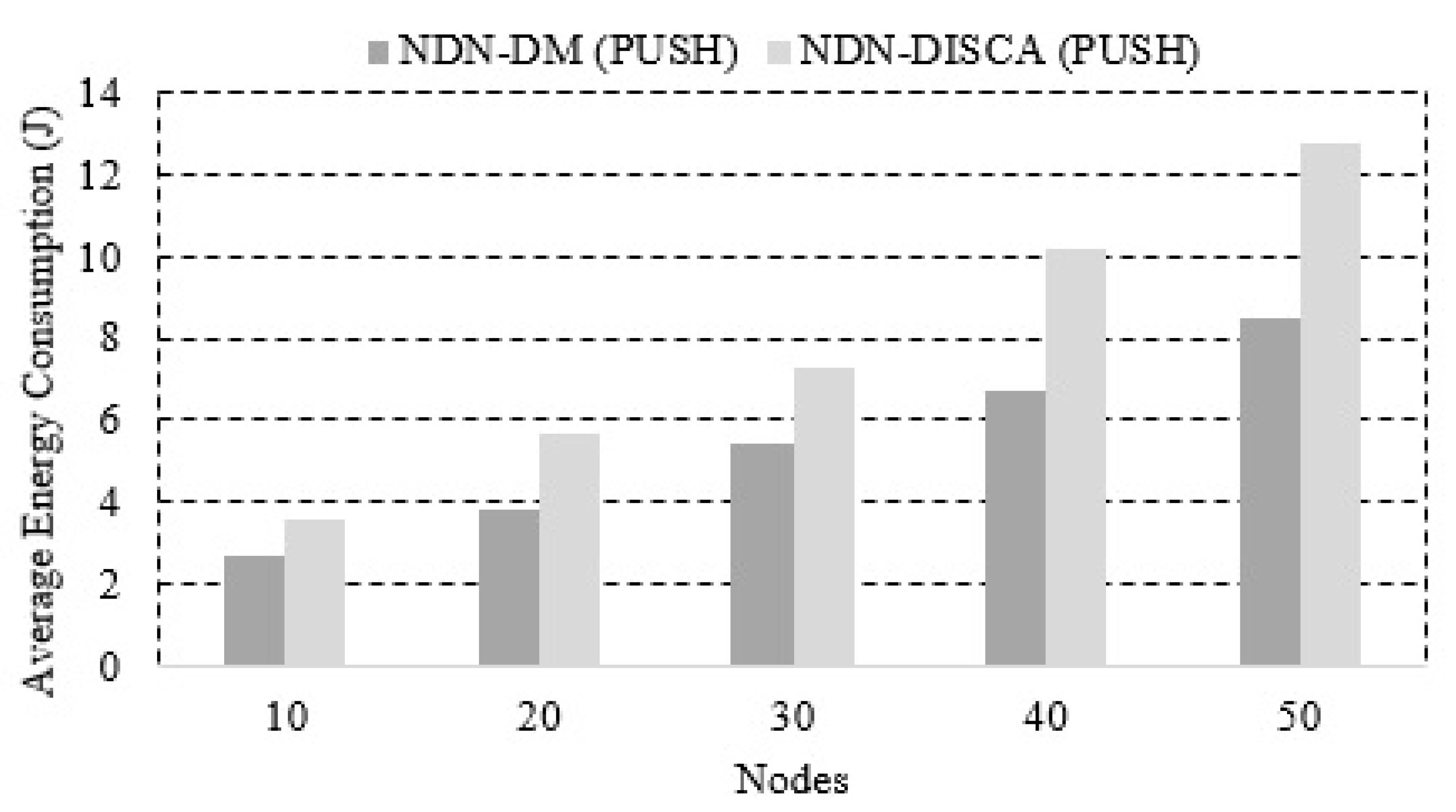
5.2. Energy Consumption
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Abbreviations
| CS | Content Store | IM | Interest Message |
| DM | Data Message | IFA | Interest Flooding Attack |
| DoS | Denial of Service | ICN | Information Centric Networking |
| DMS | Disaster Management System | NDN | Named Data Networking |
| FS | Fire Sensor | SL-1 | Smart Lab 1 |
| FE | Fire Exit | SL-2 | Smart Lab 2 |
| FIB | Forwarding Information Base | SC | Smart Campus |
| HC | Hop Count | TL | Threshold Limit |
References
- Din, I.U.; Almogren, A.; Guizani, M.; Zuair, M. A decade of Internet of Things: Analysis in the light of healthcare applications. IEEE Access 2019, 7, 89967–89979. [Google Scholar] [CrossRef]
- Rehman, W.U.; Salam, T.; Almogren, A.; Haseeb, K.; Din, I.U.; Bouk, S.H. Improved Resource Allocation in 5G MTC Networks. IEEE Access 2020, 8, 49187–49197. [Google Scholar] [CrossRef]
- Shahid, M.H.; Hameed, A.R.; ul Islam, S.; Khattak, H.A.; Din, I.U.; Rodrigues, J.J. Energy and delay efficient fog computing using caching mechanism. Comput. Commun. 2020, 154, 534–541. [Google Scholar] [CrossRef]
- Tayyaba, S.K.; Khattak, H.A.; Almogren, A.; Shah, M.A.; Din, I.U.; Alkhalifa, I.; Guizani, M. 5G Vehicular Network Resource Management for Improving Radio Access Through Machine Learning. IEEE Access 2020, 8, 6792–6800. [Google Scholar]
- Awan, K.A.; Din, I.U.; Almogren, A.; Guizani, M.; Altameem, A.; Jadoon, S.U. Robusttrust—A pro-privacy robust distributed trust management mechanism for internet of things. IEEE Access 2019, 7, 62095–62106. [Google Scholar] [CrossRef]
- Awan, K.A.; Din, I.U.; Almogren, A.; Guizani, M.; Khan, S. StabTrust—A Stable and Centralized Trust-Based Clustering Mechanism for IoT Enabled Vehicular Ad-Hoc Networks. IEEE Access 2020, 8, 21159–21177. [Google Scholar] [CrossRef]
- Wazir, W.; Khattak, H.A.; Almogren, A.; Khan, M.A.; Din, I.U. Doodle-Based Authentication Technique Using Augmented Reality. IEEE Access 2020, 8, 4022–4034. [Google Scholar] [CrossRef]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Sultana, T.; Almogren, A.; Akbar, M.; Zuair, M.; Ullah, I.; Javaid, N. Data Sharing System Integrating Access Control Mechanism using Blockchain-Based Smart Contracts for IoT Devices. Appl. Sci. 2020, 10, 488. [Google Scholar] [CrossRef]
- Arshad, S.; Shahzaad, B.; Azam, M.A.; Loo, J.; Ahmed, S.H.; Aslam, S. Hierarchical and flat-based hybrid naming scheme in content-centric networks of things. IEEE Internet Things J. 2018, 5, 1070–1080. [Google Scholar] [CrossRef]
- Alghamdi, A.; Shetty, S. Survey toward a smart campus using the internet of things. In Proceedings of the 2016 IEEE 4th International Conference on Future Internet of Things and Cloud (FiCloud), Vienna, Austria, 22–24 August 2016; pp. 235–239. [Google Scholar]
- Dar, B.K.; Shah, M.A.; Islam, S.U.; Maple, C.; Mussadiq, S.; Khan, S. Delay-Aware Accident Detection and Response System Using Fog Computing. IEEE Access 2019, 7, 70975–70985. [Google Scholar] [CrossRef]
- Hannan, A.; Arshad, S.; Azam, M.; Loo, J.; Ahmed, S.; Majeed, M.; Shah, S. Disaster management system aided by named data network of things: Architecture, design, and analysis. Sensors 2018, 18, 2431. [Google Scholar] [CrossRef] [PubMed]
- Majeed, M.F.; Ahmed, S.H.; Muhammad, S.; Song, H.; Rawat, D.B. Multimedia streaming in information-centric networking: A survey and future perspectives. Comput. Netw. 2017, 125, 103–121. [Google Scholar] [CrossRef]
- Amadeo, M.; Campolo, C.; Quevedo, J.; Corujo, D.; Molinaro, A.; Iera, A.; Aguiar, R.L.; Vasilakos, A.V. Information-centric networking for the internet of things: challenges and opportunities. IEEE Netw. 2016, 30, 92–100. [Google Scholar] [CrossRef]
- Haseeb, K.; Islam, N.; Almogren, A.; Din, I.U. Intrusion Prevention Framework for Secure Routing in WSN-Based Mobile Internet of Things. IEEE Access 2019, 7, 185496–185505. [Google Scholar] [CrossRef]
- Haseeb, K.; Din, I.U.; Almogren, A.; Islam, N.; Altameem, A. RTS: A Robust and Trusted Scheme for IoT-based Mobile Wireless Mesh Networks. IEEE Access 2020. [Google Scholar] [CrossRef]
- Baccelli, E.; Mehlis, C.; Hahm, O.; Schmidt, T.C.; Wählisch, M. Information centric networking in the IoT: Experiments with NDN in the wild. In Proceedings of the 1st ACM Conference on Information-Centric Networking, Paris, France, 24–26 September 2014; pp. 77–86. [Google Scholar]
- Masood, F.; Almogren, A.; Abbas, A.; Khattak, H.A.; Din, I.U.; Guizani, M.; Zuair, M. Spammer detection and fake user identification on social networks. IEEE Access 2019, 7, 68140–68152. [Google Scholar] [CrossRef]
- Xylomenos, G.; Ververidis, C.N.; Siris, V.A.; Fotiou, N.; Tsilopoulos, C.; Vasilakos, X.; Katsaros, K.V.; Polyzos, G.C. A survey of information-centric networking research. IEEE Commun. Surv. Tutor. 2013, 16, 1024–1049. [Google Scholar] [CrossRef]
- Akbar, M.S.; Khaliq, K.A.; Rais, R.N.B.; Qayyum, A. Information-centric networks: Categorizations, challenges, and classifications. In Proceedings of the 2014 23rd Wireless and Optical Communication Conference (WOCC), Newark, NJ, USA, 9–10 May 2014; pp. 1–5. [Google Scholar]
- Din, I.U.; Hassan, S.; Khan, M.K.; Guizani, M.; Ghazali, O.; Habbal, A. Caching in information-centric networking: Strategies, challenges, and future research directions. IEEE Commun. Surv. Tutor. 2017, 20, 1443–1474. [Google Scholar] [CrossRef]
- Din, I.U.; Hassan, S.; Almogren, A.; Ayub, F.; Guizani, M. PUC: Packet Update Caching for energy efficient IoT-based Information-Centric Networking. Future Gener. Comput. Syst. 2019. [Google Scholar] [CrossRef]
- Din, I.U.; Kim, B.S.; Hassan, S.; Guizani, M.; Atiquzzaman, M.; Rodrigues, J.J. Information-centric network-based vehicular communications: Overview and research opportunities. Sensors 2018, 18, 3957. [Google Scholar] [CrossRef]
- Rayes, A.; Morrow, M.; Lake, D. Internet of things implications on icn. In Proceedings of the 2012 IEEE International Conference on Collaboration Technologies and Systems (CTS), Denver, CO, USA, 21–25 May 2012; pp. 27–33. [Google Scholar]
- Hassan, S.; Din, I.U.; Habbal, A.; Zakaria, N.H. A popularity based caching strategy for the future Internet. In Proceedings of the 2016 ITU Kaleidoscope: ICTs for a Sustainable World (ITU WT), Bangkok, Thailand, 14–16 November 2016; pp. 1–8. [Google Scholar]
- Amadeo, M.; Campolo, C.; Molinaro, A. Internet of things via named data networking: The support of push traffic. In Proceedings of the 2014 IEEE International Conference and Workshop on the Network of the Future (NOF), Paris, France, 3–5 December 2014; pp. 1–5. [Google Scholar]
- Alkhalifa, I.S.; Almogren, A.S. NSSC: Novel Segment Based Safety Message Broadcasting in Cluster-Based Vehicular Sensor Network. IEEE Access 2020, 8, 34299–34312. [Google Scholar] [CrossRef]
- Sourlas, V.; Tassiulas, L.; Psaras, I.; Pavlou, G. Information resilience through user-assisted caching in disruptive content-centric networks. In Proceedings of the 2015 IFIP Networking Conference (IFIP Networking), Toulouse, France, 20–22 May 2015; pp. 1–9. [Google Scholar]
- Islam, N.; Haseeb, K.; Almogren, A.; Din, I.U.; Guizani, M.; Altameem, A. A framework for topological based map building: A solution to autonomous robot navigation in smart cities. Future Gener. Comput. Syst. 2019, in press. [Google Scholar] [CrossRef]
- Majeed, M.F.; Ahmed, S.H.; Dailey, M.N. Enabling push-based critical data forwarding in vehicular named data networks. IEEE Commun. Lett. 2016, 21, 873–876. [Google Scholar] [CrossRef]
- Yan, Z.; Zeadally, S.; Park, Y.J. A novel vehicular information network architecture based on named data networking (NDN). IEEE Internet Things J. 2014, 1, 525–532. [Google Scholar] [CrossRef]
- Zanella, A.; Bui, N.; Castellani, A.; Vangelista, L.; Zorzi, M. Internet of things for smart cities. IEEE Internet Things J. 2014, 1, 22–32. [Google Scholar] [CrossRef]
- Siddiqua, A.; Shah, M.A.; Khattak, H.A.; Din, I.U.; Guizani, M. iCAFE: Intelligent Congestion Avoidance and Fast Emergency services. Future Gener. Comput. Syst. 2019, 99, 365–375. [Google Scholar] [CrossRef]
- Nour, B.; Sharif, K.; Li, F.; Biswas, S.; Moungla, H.; Guizani, M.; Wang, Y. A survey of Internet of Things communication using ICN: A use case perspective. Comput. Commun. 2019, 142–143, 95–123. [Google Scholar] [CrossRef]
- Piro, G.; Cianci, I.; Grieco, L.A.; Boggia, G.; Camarda, P. Information centric services in smart cities. J. Syst. Softw. 2014, 88, 169–188. [Google Scholar] [CrossRef]
- Ahmed, S.H.; Bouk, S.H.; Kim, D.; Sarkar, M. Bringing Named Data Networks into Smart Cities. In Smart Cities: Foundations, Principles, and Applications; John Wiley & Sons, Inc.: Hoboken, NJ, USA, 2017; pp. 275–309. [Google Scholar]
- Khan, O.A.; Shah, M.A.; Din, I.U.; Kim, B.S.; Khattak, H.A.; Rodrigues, J.J.; Farman, H.; Jan, B. Leveraging named data networking for fragmented networks in smart metropolitan cities. IEEE Access 2018, 6, 75899–75911. [Google Scholar] [CrossRef]
- Mochida, T.; Nozaki, D.; Okamoto, K.; Qi, X.; Wen, Z.; Sato, T.; Yu, K. Naming scheme using NLP machine learning method for network weather monitoring system based on ICN. In Proceedings of the 2017 20th International Symposium on Wireless Personal Multimedia Communications (WPMC), Bali, Indonesia, 17–20 December 2017; pp. 428–434. [Google Scholar]
- De Cola, T.; Gonzalez, G.; Mujica, V.E. Applicability of ICN-based network architectures to satellite-assisted emergency communications. In Proceedings of the 2016 IEEE Global Communications Conference (GLOBECOM), Washington, DC, USA, 4–8 December 2016; pp. 1–6. [Google Scholar]
- Amadeo, M.; Campolo, C.; Molinaro, A. Multi-source data retrieval in IoT via named data networking. In Proceedings of the 1st ACM Conference on Information-Centric Networking, Paris, France, 24–26 September 2014; pp. 67–76. [Google Scholar]
- Afanasyev, A.; Moiseenko, I.; Zhang, L. ndnSIM: NDN Simulator for NS-3; Tech. Rep; University of California: Los Angeles, CA, USA, 2012; Volume 4. [Google Scholar]
- Xu, Z.; Su, Z.; Xu, Q.; Qi, Q.; Yang, T.; Li, J.; Fang, D.; Han, B. Delivering mobile social content with selective agent and relay nodes in content centric networks. Peer-to-Peer Netw. Appl. 2017, 10, 296–304. [Google Scholar] [CrossRef]
- Siddiqa, A.; Shah, M.A.; Maryam, H.; Arshad, S.; Wahid, A. EMCA: Efficient multicasting and collision avoidance in CC-MANETs. In Proceedings of the 2017 IEEE 13th International Conference on Emerging Technologies (ICET), Islamabad, Pakistan, 27–28 December 2017; pp. 1–6. [Google Scholar]
- Hasegawa, T.; Tara, Y.; Ryu, K.; Koizumi, Y. Emergency message delivery mechanism in NDN networks. In Proceedings of the 3rd ACM Conference on Information-Centric Networking, Kyoto, Japan, 26–28 September 2016; pp. 199–200. [Google Scholar]
- Shih, C.S.; Hsiu, P.C.; Chang, Y.H.; Kuo, T.W. Framework designs to enhance reliable and timely services of disaster management systems. In Proceedings of the 35th International Conference on Computer-Aided Design, Austin, TX, USA, 7–10 November 2016; p. 107. [Google Scholar]
- Ahmed, S.H.; Kim, D. Named data networking-based smart home. Ict Express 2016, 2, 130–134. [Google Scholar] [CrossRef]
- Khattak, H.A.; Ameer, Z.; Din, U.I.; Khan, M.K. Cross-layer design and optimization techniques in wireless multimedia sensor networks for smart cities. Comput. Sci. Inf. Syst. 2019, 16, 1–17. [Google Scholar] [CrossRef]
- Toor, A.; ul Islam, S.; Sohail, N.; Akhunzada, A.; Boudjadar, J.; Khattak, H.A.; Din, I.U.; Rodrigues, J.J. Energy and performance aware fog computing: A case of DVFS and green renewable energy. Future Gener. Comput. Syst. 2019, 101, 1112–1121. [Google Scholar] [CrossRef]
- Ahmad, A.; Khan, A.; Javaid, N.; Hussain, H.M.; Abdul, W.; Almogren, A.; Alamri, A.; Azim Niaz, I. An optimized home energy management system with integrated renewable energy and storage resources. Energies 2017, 10, 549. [Google Scholar] [CrossRef]
- Almogren, A.S. Intrusion detection in Edge-of-Things computing. J. Parallel Distrib. Comput. 2020, 137, 259–265. [Google Scholar] [CrossRef]
- Lee, G.; Han, L.; Park, Y.; Lee, J.B.; Kim, J.; In, H.P. An energy-efficient routing protocol for CCN-based MANETs. Int. J. Smart Home 2013, 7, 143–152. [Google Scholar]
- Amadeo, M.; Campolo, C.; Iera, A.; Molinaro, A. Information Centric Networking in IoT scenarios: The case of a smart home. In Proceedings of the 2015 IEEE international conference on communications (ICC), London, UK, 8–12 June 2015; pp. 648–653. [Google Scholar]
- Seedorf, J.; Kutscher, D.; Gill, B.S. Decentralised interest counter aggregation for ICN in disaster scenarios. In Proceedings of the 2016 IEEE Globecom Workshops (GC Wkshps), Washington, DC, USA, 4–8 December 2016; pp. 1–6. [Google Scholar]
- Maryam, H.; Shah, M.A.; Arshad, S.; Siddiqa, A.; Wahid, A. TFS: A reliable routing protocol for Vehicular Content Centric Networks. In Proceedings of the 2017 IEEE 13th International Conference on Emerging Technologies (ICET), Islamabad, Pakistan, 27–28 December 2017; pp. 1–6. [Google Scholar]
- Aamir, M. Content-priority based interest forwarding in content centric networks. arXiv 2014, arXiv:1410.4987. [Google Scholar]
- Ullah, R.; Rehman, M.A.U.; Kim, B.S. Hierarchical Name-Based Mechanism for Push-Data Broadcast Control in Information-Centric Multihop Wireless Networks. Sensors 2019, 19, 3034. [Google Scholar] [CrossRef]
- Razouqi, Q.; Boushehri, A.; Gaballah, M.; Alsaleh, L. Extensive simulation performance analysis for DSDV, DSR and AODV MANET routing protocols. In Proceedings of the 2013 IEEE 27th International Conference on Advanced Information Networking and Applications Workshops, Barcelona, Spain, 25–28 March 2013; pp. 335–342. [Google Scholar]










| Parameters | Specification |
|---|---|
| Simulation Area | 50 m × 100 m |
| Total nodes | 50 |
| Number of producer nodes | 1 |
| Number of consumer nodes | 49 |
| Transmission range | 20 m |
| Model for mobility | Single node mobile |
| Node speed | 0.2 s |
| Layer L2 | 802.11a |
| Caching policy | LCE |
| ICN communication stack | NDN |
| Nodes | 10 | 20 | 30 | 40 | 50 |
|---|---|---|---|---|---|
| Delay (%) | 2 | 4 | 7 | 8 | 10 |
| Energy (%) | 3 | 13 | 18 | 20 | 17 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ali, Z.; Shah, M.A.; Almogren, A.; Ud Din, I.; Maple, C.; Khattak, H.A. Named Data Networking for Efficient IoT-based Disaster Management in a Smart Campus. Sustainability 2020, 12, 3088. https://doi.org/10.3390/su12083088
Ali Z, Shah MA, Almogren A, Ud Din I, Maple C, Khattak HA. Named Data Networking for Efficient IoT-based Disaster Management in a Smart Campus. Sustainability. 2020; 12(8):3088. https://doi.org/10.3390/su12083088
Chicago/Turabian StyleAli, Zain, Munam Ali Shah, Ahmad Almogren, Ikram Ud Din, Carsten Maple, and Hasan Ali Khattak. 2020. "Named Data Networking for Efficient IoT-based Disaster Management in a Smart Campus" Sustainability 12, no. 8: 3088. https://doi.org/10.3390/su12083088
APA StyleAli, Z., Shah, M. A., Almogren, A., Ud Din, I., Maple, C., & Khattak, H. A. (2020). Named Data Networking for Efficient IoT-based Disaster Management in a Smart Campus. Sustainability, 12(8), 3088. https://doi.org/10.3390/su12083088






