1. Introduction
High-speed access to mobile data has become one of the most significant demands of smartphone subscribers. The increasing availability of intelligent equipment and the ever-growing demand for multi-media streaming services have drastically increased the volume of mobile data traffic [
1]. In 2016, the total generated mobile data was 8.8 Exabyte, 50% of which belonged to video content. It is estimated that this amount will reach 71 Exabyte in 2020, 75% of which will belong to video content [
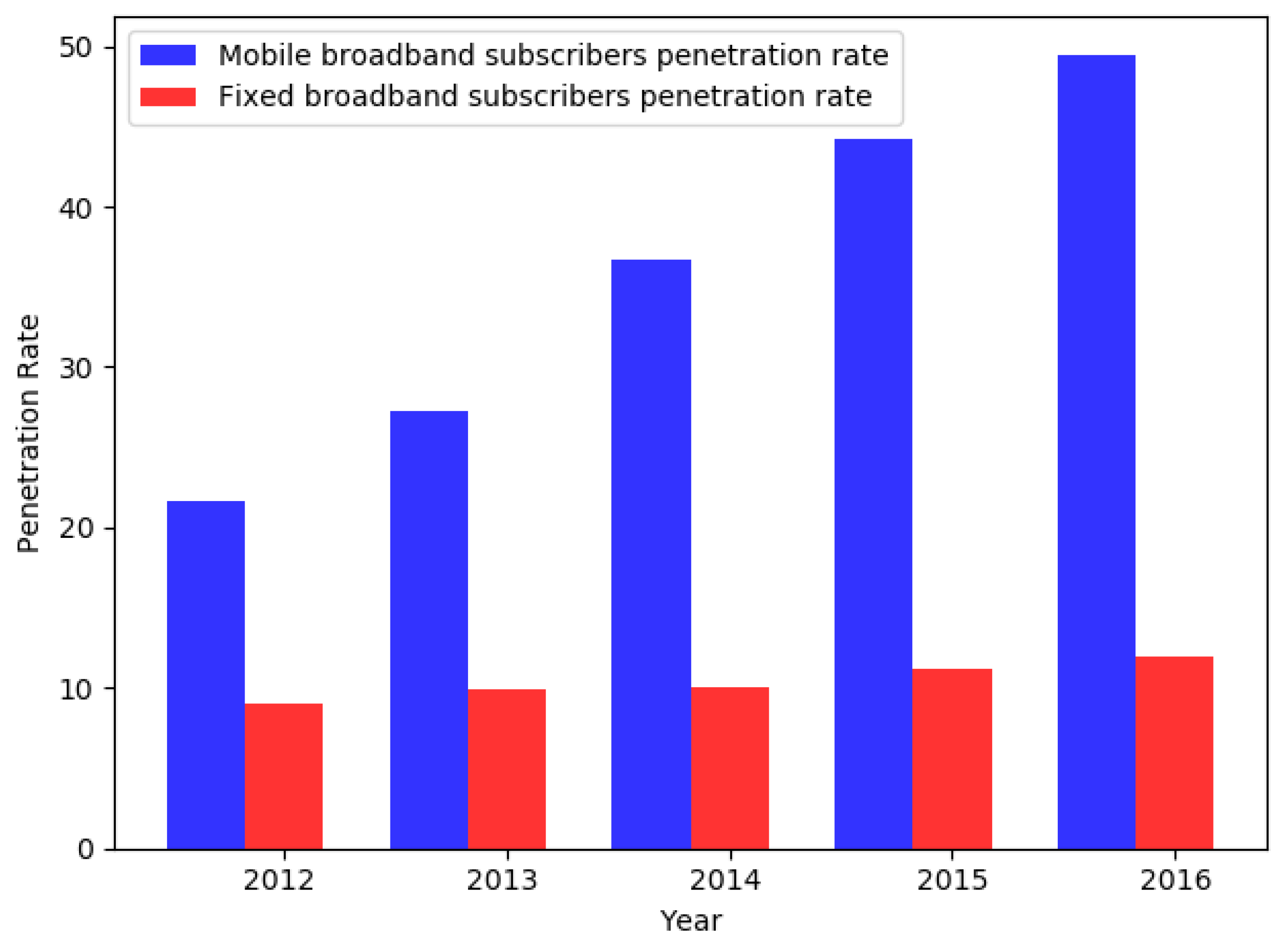
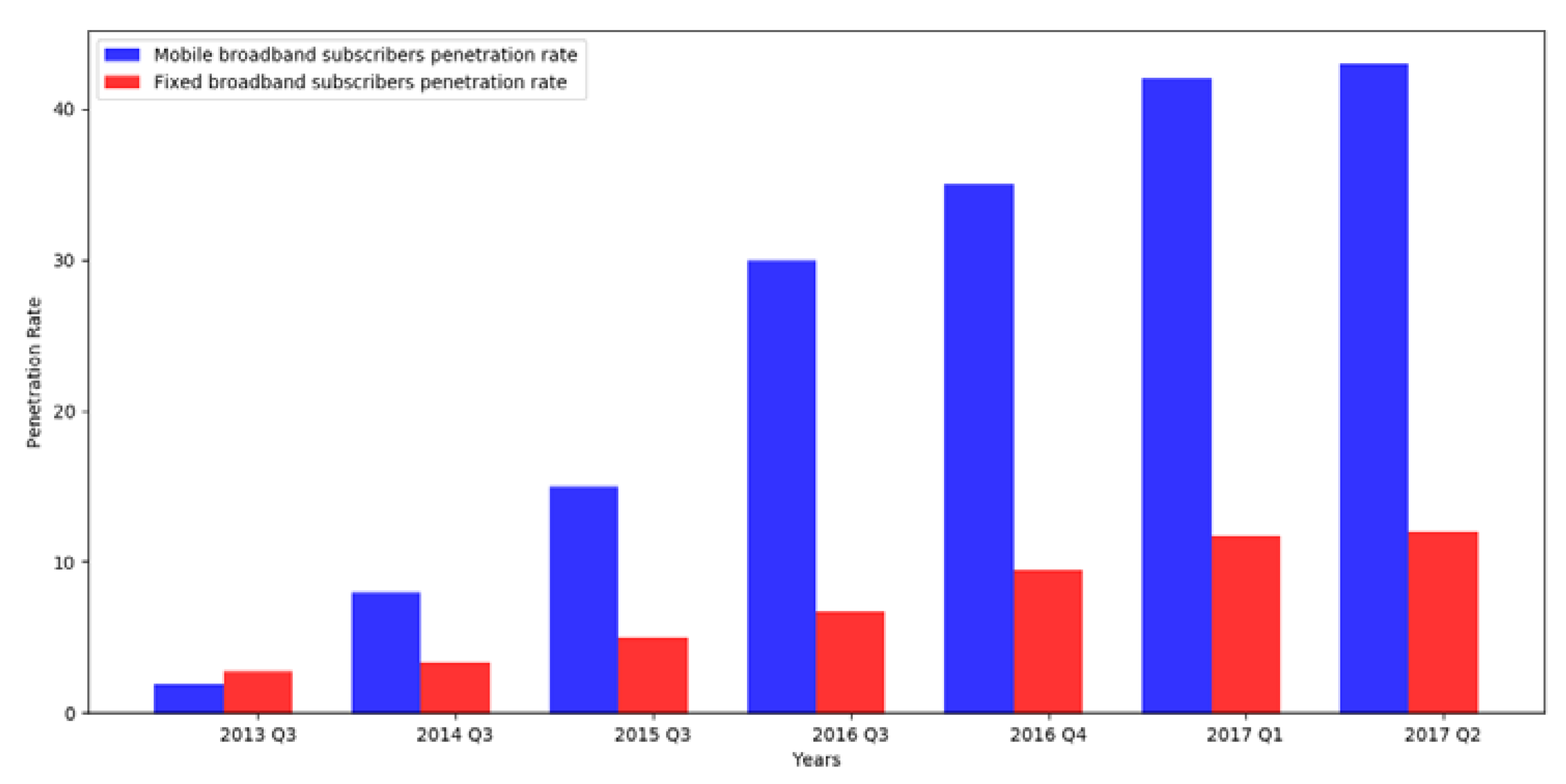
2]. Network operators have spent lots of R&D costs on providing better data. Therefore, it has led to the significant expansion of mobile broadband. Statistics and figures indicate that the mobile broadband subscriber growth rate has been steadily higher than that of fixed broadband in the world. A fixed broadband penetration rate reached 11.9% in 2016, from 0.9% in 2012, while mobile broadband penetration rate reached 49.4% in 2016 from 21.7% in 2012
Figure 1. Like other countries [
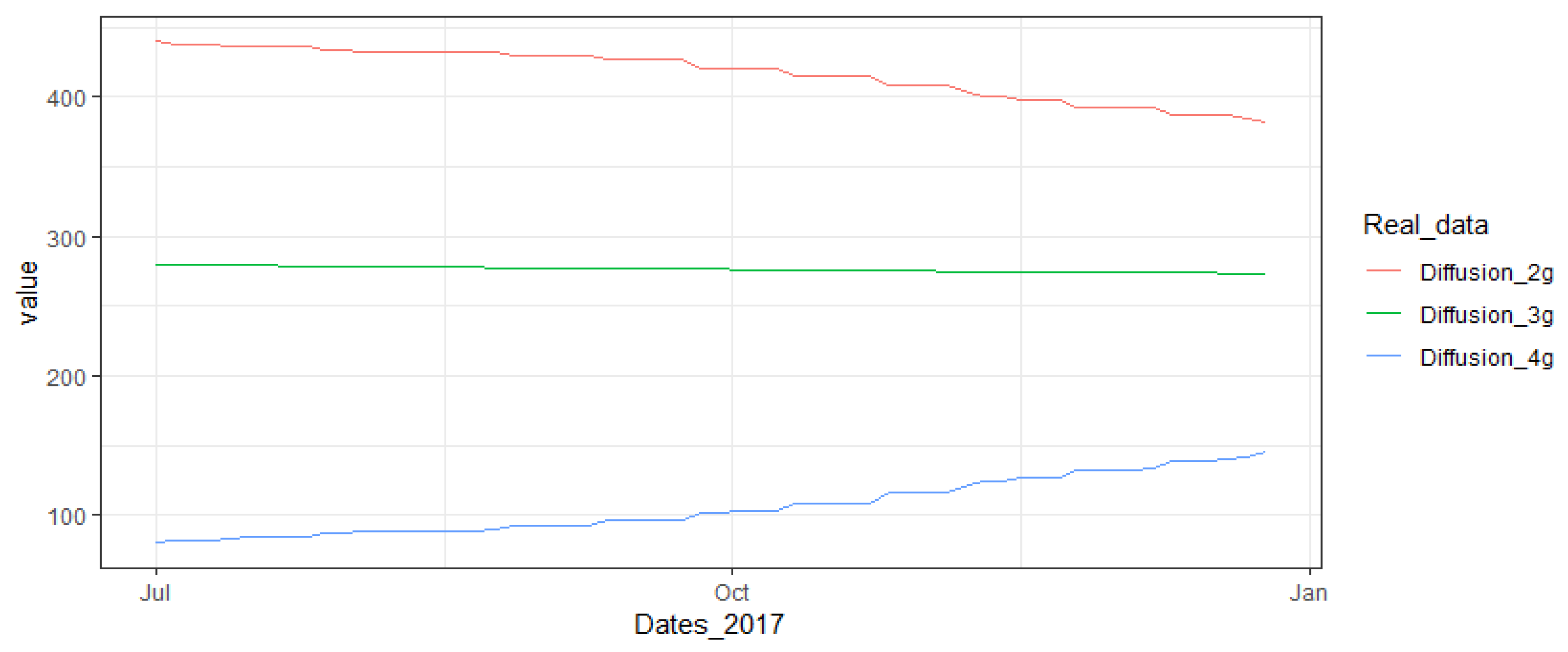
3], in Iran, mobile broadband penetration rate has been much higher than that of fixed broadband, as the growth rate of fixed broadband subscribers has moved from 2.81% in the summer 2012 only to 12% in the spring 2017, while the growth rate of mobile broadband subscribers has shifted from 1.92% in summer 2012 to 42.5% in spring 2017
Figure 2.
Cellular network technologies, like the third generation (3G) and fourth-generation (4G) of mobile networks, have considerably contributed to the development of mobile broadband. 3G technology was developed during the 90s and entered the global market in 2002. This technology was becoming widespread in 2007. Actually, in December 2007, 190 operators in 40 countries provided 3G services to their subscribers. In Iran, Rightel operator, which was established in 2007, received the 3G service license in January 2010, but it started its work in June 2011. Therefore, 3G mobile networks entered the market with a delay of 9 years. The commercialization of 3G in the country coincided with the commercialization of 4G in the world. The 4G technology was launched in September 2014 by the Irancell operator. Afterwards, Mobile Telecommunication Company of Iran (MCI) and Rightel started 4G mobile networks. Limitations such as mobility, low-rate of transmission, and bandwidth constraints were among the most important reasons leading mobile operators to go to launch 4G mobile networks.
According to specifications detailed by IMT-advanced, any 4G mobile network should meet the following minimum requirements [
6]:
It should be completely based on Internet Protocol (IPV6)
For high mobility communications such as from cars and trains, data transmission rate should be 100 megabits per second (Mbps), and for low mobility communications such as pedestrians and stationary users, data transmission rate should be 1 gigabit per second (Gbps)
As the most prominent representative of 4G, Long Term Evolution (LTE) technology has become very popular. LTE was developed in 2004 and commercialized during 2010–2011. LTE, which is often marketed as 4GLTE, is a standard for transmitting high-speed wireless data for data terminals and mobile devices. LTE is based on GSM/EDGE and UMTS/HSPA technologies, which have greatly enhanced the capacity and speed via a different radio interface, together with core network improvements. LTE standard has been developed by the 3rd Generation Partnership Project (3GPP). Differences of mobile telecommunications technologies (MTTs) have been presented in
Table 1.
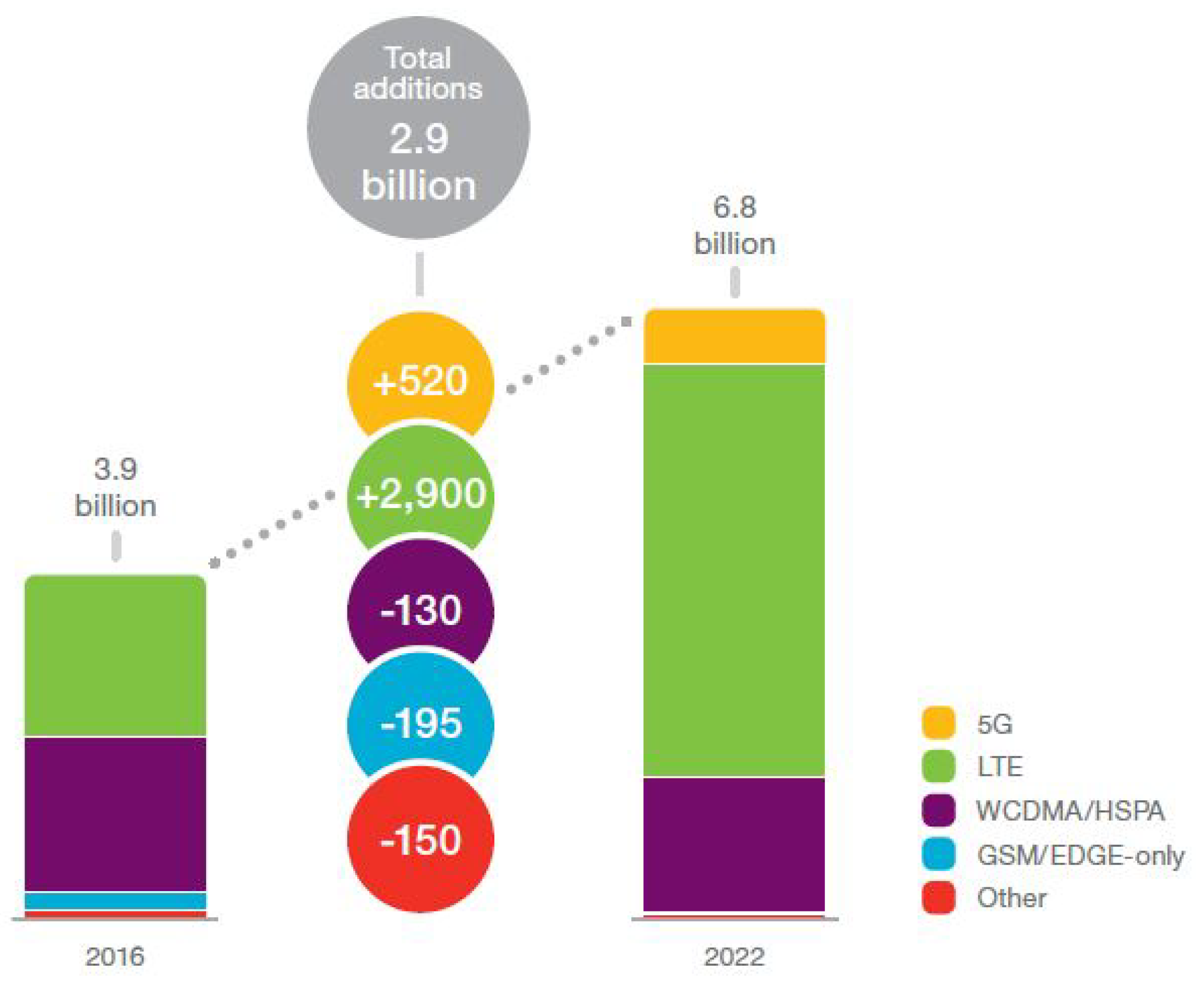
Several studies have shown the widespread market share of LTE in the next five years so that if mobile operators cannot properly manage this technology, they will eventually lose much of their subscribers’ market share. The Ericsson 2016 [
2] report has illustrated this trend
Figure 3. According to this report, there were 3.9 billion smartphone subscribers in 2016, of which 1700 million are 4G, 1800 million are 3G (UMTS/HSPA), 300 million are 2G (GSM/EDGE), and another one million subscribers use other cellular mobile networks. It is estimated that by the year 2022, 2700 million persons will be added to 4G subscribers and 540 million persons to 5G subscribers, while 3G, 2G, and other mobile network technologies will lose 65 million, 95 million, and 130 million subscribers, respectively.
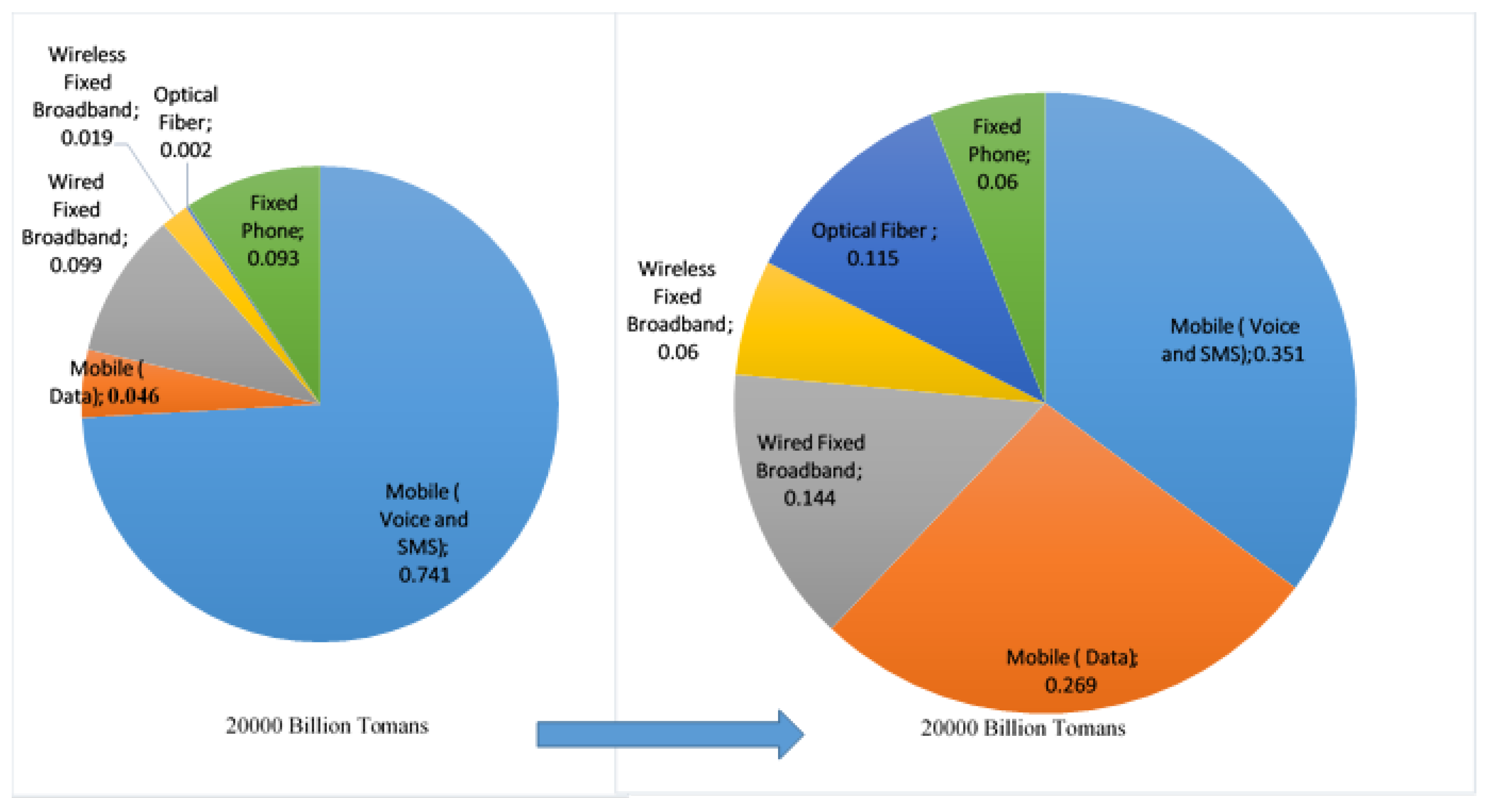
According to an analysis by the Ministry of Information and Communications Technology (ICT) of Iran [
5], the total portfolio of domestic operators was 6250 billion dollars in the year 2015, 74.1% of which was voice and SMS, and only 4.6% was mobile data. With the development of mobile infrastructure and the availability of high-speed broadband, as well as the widespread diffusion of various OTT technologies such as Telegram, a penetration rate of 78%, and Instagram with a penetration rate of 54% by the end of spring 2017, it is forecast that of the 20,937,500,000 dollar revenues for domestic operators in 2020, only 35.1% would be voice and SMS, and 26.9% for mobile data. It reflects the fact that by 2022, the share of voice and SMS will be halved, and the data share will roughly get six times higher. The portfolio revenue change of Iranian operators is shown in
Figure 4.
Since the introduction of LTE technology for the first time in Iran (i.e., September 2014), domestic mobile operators have been investing heavily in developing this technology. The increase in coverage of this network from 47.86% in November 2016 to 58.82% in June 2017 indicates an increase in the number of 4G transmitter/receiver base stations (BTS) across the country. However, in spite of the large investments of the three main domestic operators, namely MCI, Irancell, and Rightel, in the development of 4G LTE network, as well as the increasing penetration of mobile broadband in the country—about 42.5% by the end of the spring of 2017—the LTE mobile penetration rate in Iran is estimated to be 10% by the end of spring 2017. This indicates that the main volume of mobile broadband subscribers in the country is still using UMTS/HSPA 3G networks. In other words, about 26 million of total mobile broadband subscribers (i.e., 34 million subscribers by the end of spring 2017) are currently using 3G cellular networks. Given the mobile broadband penetration rate and the third-generation share in it (85%), it is clear that mobile broadband subscribers are locked in these third-generation UMTS/HSPA networks, and the poor reception of the fourth generation will slow down future investments in LTE networks. This can result in some unintended negative consequences as following:
Failure to provide a large number of high-quality services: With the help of LTE technology, operators can provide much more diverse and high-quality services. Some of the major advantages of this technology include faster mobile data, more bandwidth, much less latency, better management of data traffic, high-level video streaming, Voice over LTE (VoLTE), Video over LTE (ViLTE), entry to vertical markets (e.g., public safety, health and transportation), low legacy cost due to more integrability with fifth-generation networks (5G), network’s better efficiency, cell broadcast, and lots of value-added services.
Inability to compete with OTT technologies: Because LTE operators can provide better quality services than OTT technologies, such as VoLTE versus Voice over Internet Protocol (VOIP) offered by WhatsApp or ViLTE compared to the video over the Internet protocol provided by Skype.
Loss of many revenue opportunities: The revenue generated by LTE is forecast to be
$ 350 billion by 2020 [
8]. Considering that Iran is 1.08% of the world’s population, its share of this amount can be equal to 3.780 billion. So, if the fourth generation is not well understood, Iranian operators will lose that income share.
Prolongation of payback period: If operators’ subscribers migrate slowly from 3G to 4G, this can prolong the payback period of the 4G network and create many costs for operators.
The lack of integrability with fifth-generation networks (5G) and the loss of many IoT opportunities: IoT is recognized to have a tremendous effect over the ICT industry in the near future. The Forbes Media Company forecasts that the IoT revenue share will be
$ 14.4 trillion by 2022. Of this,
$ 2.5 trillion has been spent on improving employees’ productivity, another 2.5 trillion in reducing costs, 2.7 trillion in improving logistics and supply chains, 3 trillion in reducing market entry time, and 3.7 trillion in improving the customers’ experience [
9]. 5G plays a pivotal role in realizing the IoT and utilizing its capacities. 4G technologies, in particular, LTE-Advanced Pro technology, have a high potential to integrate with 5G in comparison to other cellular technologies. With this technology, operators can get integrated with 5G networks without getting stuck at a huge legacy cost. Therefore, if the operators only stay on 3G networks, huge costs will be imposed on them to migrate to 5G networks, and they will lose huge opportunities.
Therefore, it is important for managers of Iranian operators to know by which scenarios they can encourage non-4G subscribers to switch to fourth-generation technologies. For such scenarios, they should know the mechanism underlying the diffusion of three competing MTTs (i.e., 2G, 3G, and 4G) in the country. This study is primarily aimed at discovering this mechanism. The rest of this paper is organized as follows: The second section covers the literature review where various types of studies are discussed, and their limitations are explained. The third section ideals with materials and methods where agent-based modeling (ABM) is discussed in a step-by-step way. In the fourth section, the results are presented through model evaluation in which both verification and verification are clearly discussed. In the fifth section, a discussion of the model’s outputs is presented, and finally a conclusion is elaborated as the sixth section.
2. Literature Review
In our complex world, we observe a variety of complex phenomena such as new social norms formation, rumor spreading, the emergence of new technologies, and the fall of traditional businesses. To study phenomena, social sciences researchers most often use reductionism approach, through which they reduce such phenomena to some lower-level variables and model the relationships among them through a scheme of equations (e.g., partial differential equations and ordinary differential equations). This reductionism approach, which is often called equation-based modeling (EBM) has a long background in the field of mobile technology adoption, where most of these EBM studies can be classified into two classes of (1) statistical regression-based studies [
10,
11,
12,
13,
14] and (2) Multi-Criteria Decision Making (MCDM) ones [
15,
16,
17,
18,
19,
20]. Statistical regression-based models have some basic limitations. The first limitation of statistical regression-based models is that they are formulated based on some simplistic assumptions that can distort the accuracy of solutions. For instance, in linear regression, the variables are considered to be linearly related in which the independent variables can take a range of values, while dependent ones only have a random value. Additionally, successive observations of independent variables are regarded to be uncorrelated, and the co-linearity among variables has to be taken into consideration [
21]. The second limitation is that such models are very prone to the prediction error; therefore, there can be a great gap between the outcome variable and real-world data. The third limitation is that in multiple regression, the beta value is indirectly calculated by a test, so in case of a negative beta, the final judgment becomes really difficult [
18]. MCDM studies have been frequently used to identify the major criteria affecting the adoption of mobile services. Liu (2010) used the Analytical Hierarchy Process (AHP) to prioritize the critical factors of mobile handset usage on the basis of employees’ opinions. In that study, the critical factors were divided into four factors of (1) economic value, (2) relational value, (3) knowledge value, and (4) convenience value, that the convenience value was finally selected as the most critical factor [
15]. Phan and Diam (2011) ranked and clustered the major influencers on mobile service adoption using AHP and cluster analysis. Their study included five total factors of habits, social factors, technology, ease of use, and usefulness. The results showed that the last two factors play a vital role in the adoption process [
16]. Regardless of business aspects, Nikou and Mezei (2013) could rank the factors impacting students to adopt mobile services using an AHP approach. They identified 20 mobile services in five distinct categories. The results of their study indicated that five services of “short message,” “mobile email,” “mobile internet surfing,” “mobile search,” and “mobile Google map” were believed to be the most important services affecting mobile adoption [
17]. However, none of these studies dealt with the diffusion problem in a crisp manner, so the lack of a fuzzy assessment is their biggest limitation.
Buyukozkan (2009) developed a fuzzy AHP (FAHP) to prioritize the requirements of mobile experiences according to organizational criteria and opinions expressed by users and experts. However, considering a small number of criteria is considered to be the prime limitation of this study [
19]. Combining the FAHP and extent analysis approach, Lin (2013) developed a fuzzy assessment model for prioritizing factors affecting the quality of mobile banking. The opinions of two different groups were used in this study, one of which possessed a little experience of mobile banking, while another one had a high level of experience in it. However, the results show that two groups had chosen the criterion of "customer services" as the most critical factor influencing the effectiveness of electronic banking [
20]. Sheih and colleagues (2014) used FAHP to rank critical factors of mobile services adoption by Taiwan citizens. They grouped all factors into three groups of “factors related to mobile,” “factors related to mobile hardware,” and “psychological factors of users” [
18]. Nevertheless, these studies had two major shortcomings. The first of which was that the cause and effect relationships among factors affecting technology adoption were not considered, and the second one was that the intensity of these relationships was not also taken into consideration.
Generally, as it can be observed in all EBM studies of technology adoption and diffusion, in modeling how a technology is adopted and diffused in a society over time, the whole society is reduced into some socio-economic factors with the qualities of unbounded rationality and (most often) perfect information, and the model built from the relationships among such factors is analyzed to explain the technology adoption and diffusion in the society, while very important factors such as adaptability and the evolutionary nature of all engaged actors along with network effects go unaddressed.
For overcoming deficiencies and limitations of reductionism approach, in the past two decades, the framework of complex adaptive system (CAS) has shown lots of promise. In contrast to reductionism approach, under this framework, the socio-economic phenomena such as technology adoption and diffusion are studied in an organic manner where the economic agents are supposed to be both boundedly rational and adaptive. Based on CAS framework, the socio-economic aggregates such as technology diffusion emerge out of the ways agents of a socio-economic system interact and decide. As the most powerful methodology for CAS modeling, agent-based modeling (ABM) has gained an increasing application among academia and industry. ABMs show how simple behavioral rules of agents and local interactions among them at a micro-scale can create surprisingly complex patterns at a macro-scale. This methodology has gained an increasing popularity, both in academia and industry such as the study of critical infrastructures dependence [
22], consumption of services of sustainable eco-systems [
23], economic sciences [
24,
25], and management [
26,
27]. For adoption and diffusion studies, a number of works have used ABM for studying the adoption and diffusion of technologies such as environmental technologies [
28], energy technologies [
29], health and medical technologies [
30,
31,
32], agricultural technologies [
33], cinema technologies [
34], transportation technologies [
35], electricity production [
36], alternative fuels [
37,
38], organic farming practices [
39], automobile markets [
40], fuel cell vehicles [
41,
42], mobile phone [
43], and smart metering [
44].
However, to the best of authors’ knowledge, no systematic study has been conducted on the adoption and diffusion of mobile telecommunications technologies (MTTs) so far. Using agent ABM and social network theory (SNT), the prime purpose of this study is to discover the mechanism underlying the diffusion of three competing MTTs in Iran, through which all telecoms planners would get practical insights in order to speed up the diffusion of a targeted MTT.
6. Conclusions
Developing the appropriate scenarios for increasing the 4G technology diffusion in Iran has been the motivation behind the development of this model. In this regard, the mechanism underlying the diffusion of MTTs in Iranian society was studied. To better identify this mechanism, prior studies were first investigated, and because of reasons such as (1) simplistic neoclassical assumptions like unbounded rationality and perfect information, (2) non-inclusion of network effects and non-linear interactions of micro-level individual adopters, (3) learnability and adaptability of individual adopters, (4) bottom-up nature of technology adoption, (5) heterogeneity and multiplicity of influential factors, agent-based modeling (ABM) was chosen as the modeling approach in tandem with social network theory (SNT). This model is mainly theory-based, where real-world empirical data, theories, and extension of the works of [
64,
65,
66,
67] have been taken into account, and it is to a lesser extent evidence-based because some new variables (e.g., handset compatibility) are added authors.
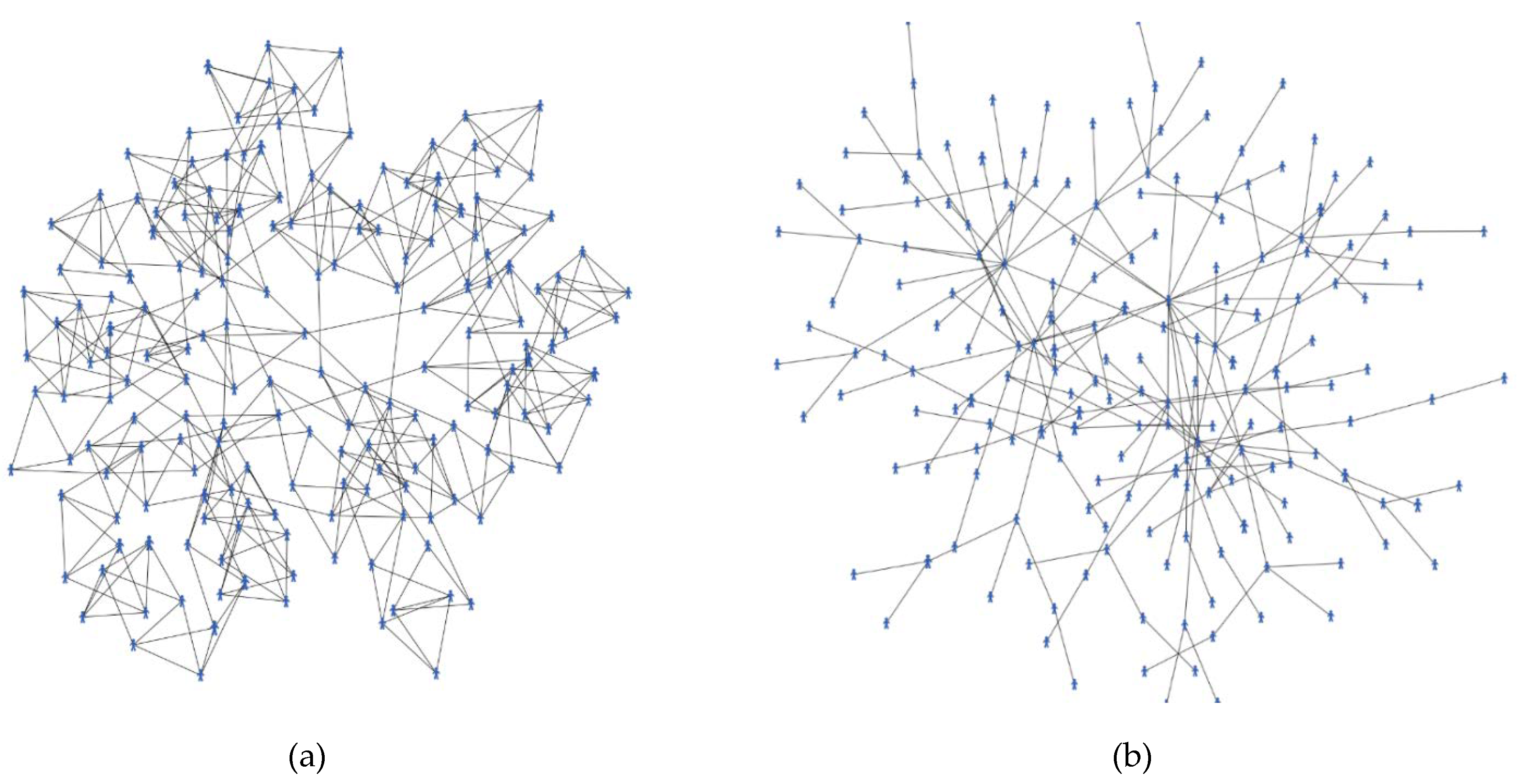
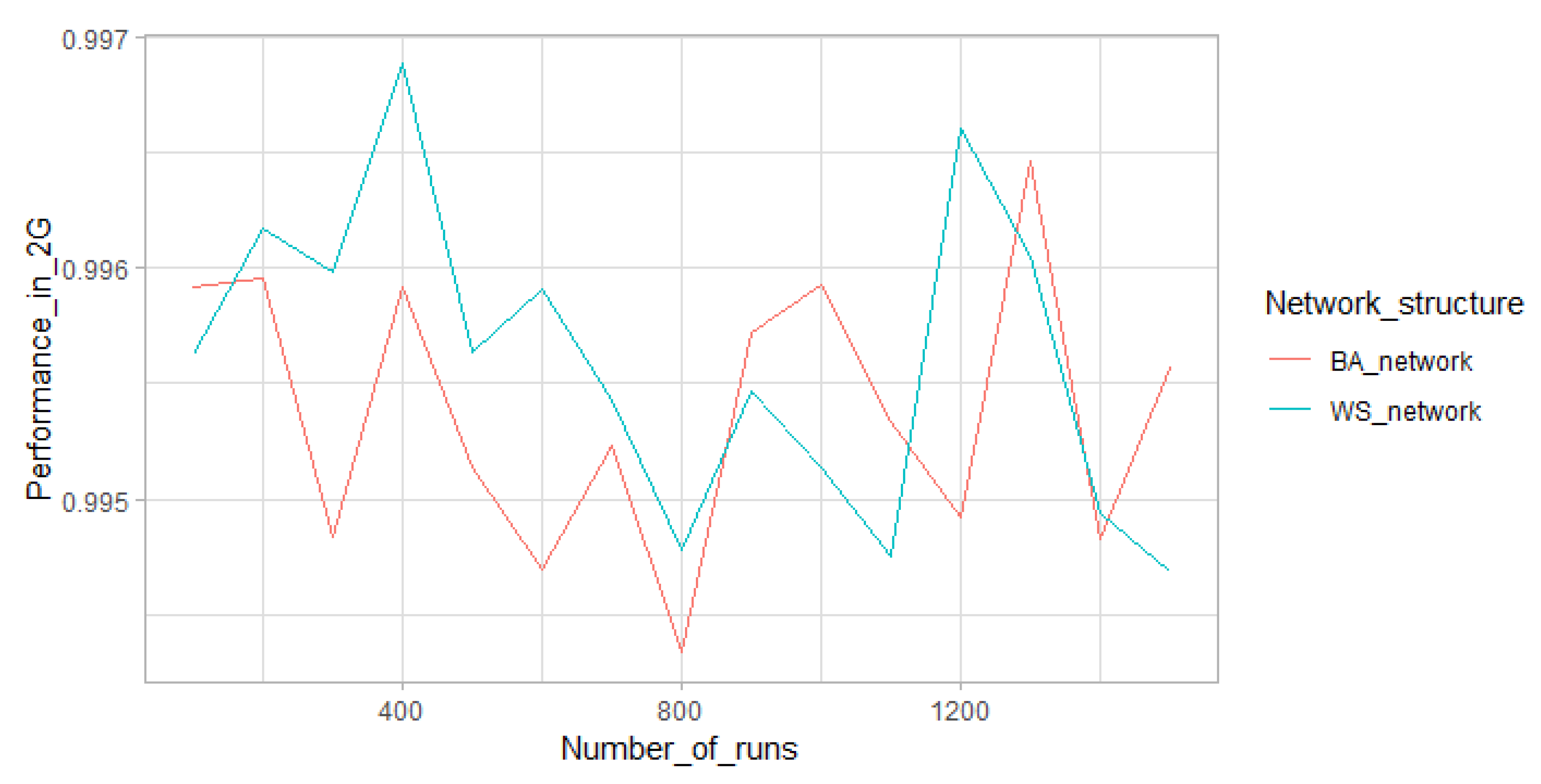
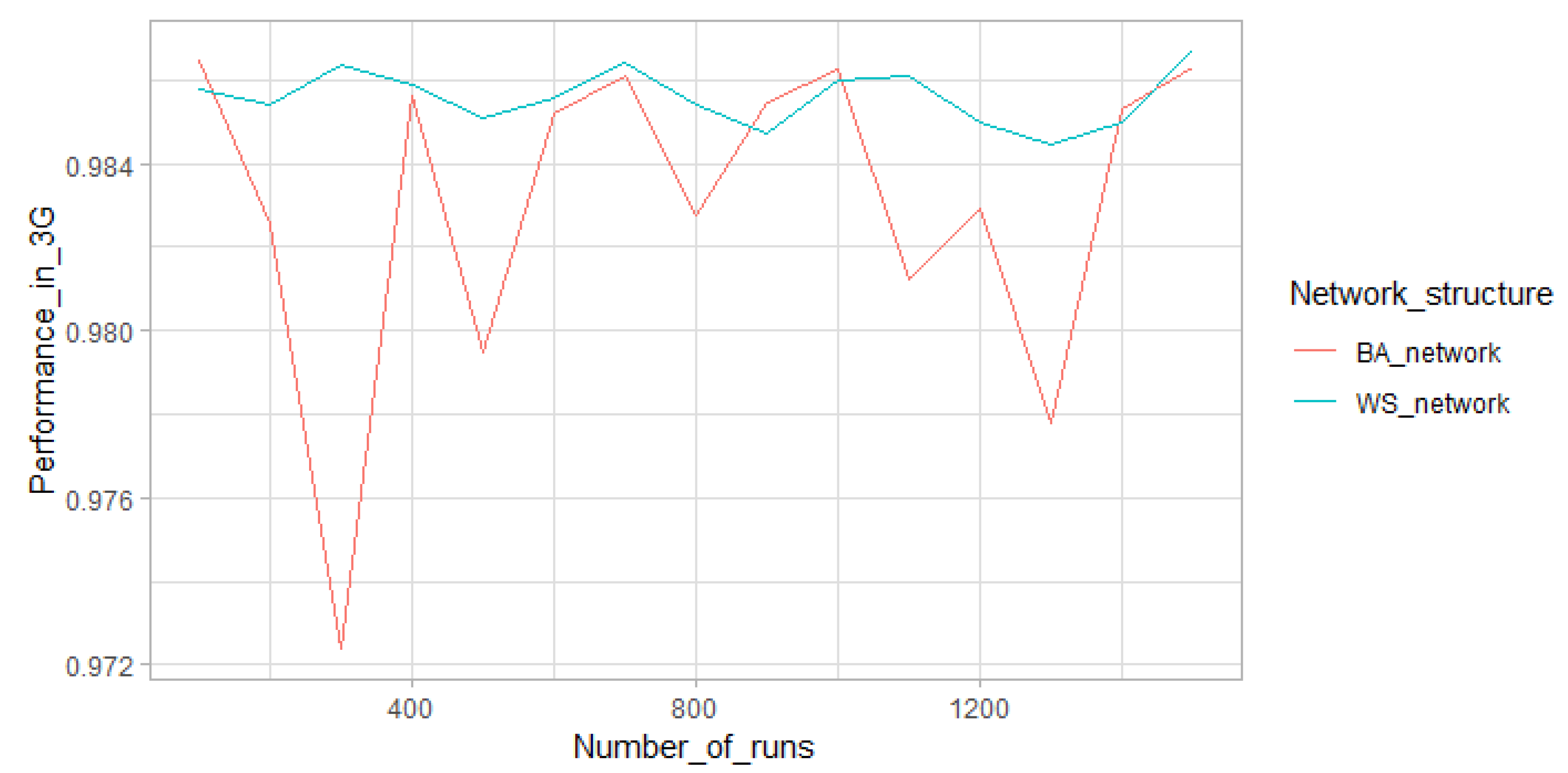
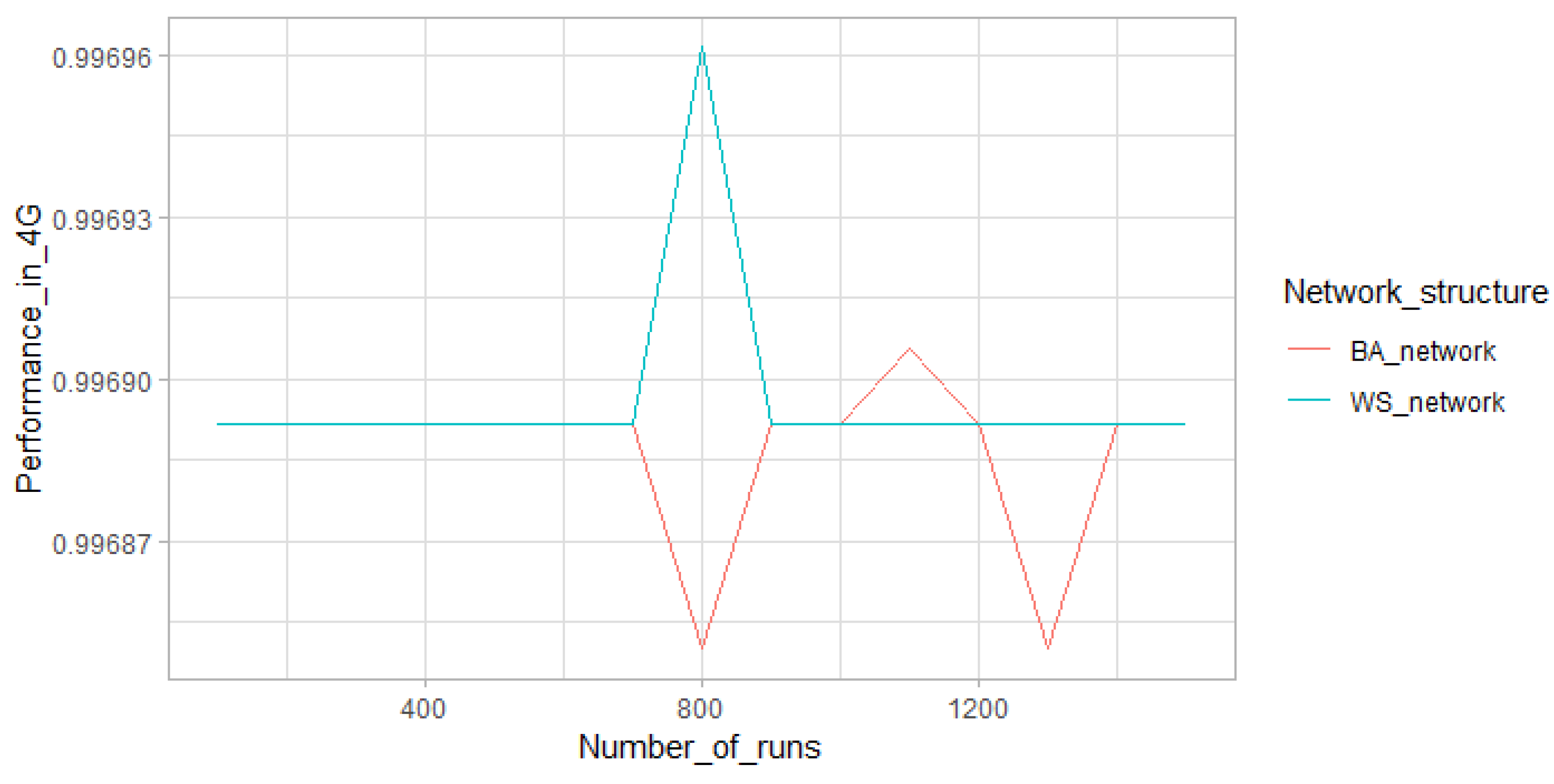
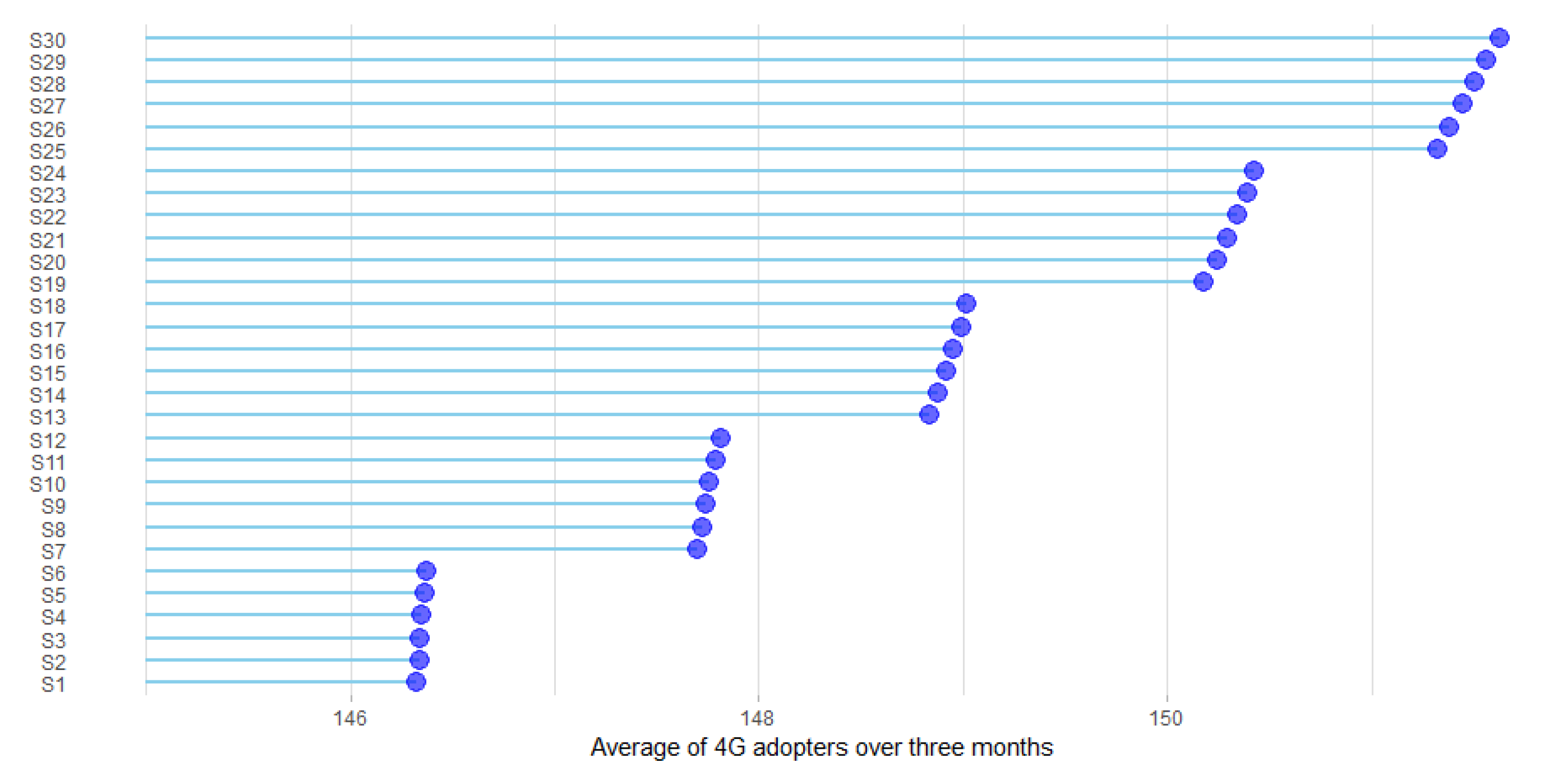
The model’s input parameters can be grouped as (1) number of adopters (i.e., 2G, 3G, and 4G), (2) adopters’ memory parameters (i.e., innovators, early-adopters, early-majority, late-majority, and laggards), (3) network topology parameters (i.e., WSN and PAN) and (4) advertisement and handset compatibility parameters. They were directly calibrated according to empirical studies. The model was implemented by Netlogo 6.0.1, and the data were analyzed by R 3.5.3. The performance of the model was simulated in two different social network topologies by 9000 experiment runs for the second half of 2017 actually, 1500 simulation runs for each MTT in each social network structure. The Shapiro–Wilk test was used to check the normality of data, showing that none of them were normal. Data normalization methods such as standard (z-score), log transformation, and box-cox were used to normalize the data, but none of them could normalize the data. Therefore, as a non-parametric test of correlation, spearman test was used to measure the model’s outputs with real data for the second half of 2017, and the results indicated the high predictive accuracy of model’s performance, and it was figured out that Watts–Strogatz small-world network (WSN) has the highest similarity with the social network of Iranian people where the clustering coefficient (CC) is high (i.e., 0.34 for this study because of the size of sample, but it tends to ¾ (0.75) in case of large N) and average path length (L) is low (i.e., 2.90 for this study, but it will approximately converge to 7.90 for real number of Iranian population). High CC indicates that the friends of a person tend to be friends of each other, and low L shows that when two persons want to reach each other, they can do it by a limited number of steps. Several number of studies affirmed this finding that social networks mainly follow a WSN structure [
67,
80,
96,
97,
98,
99].
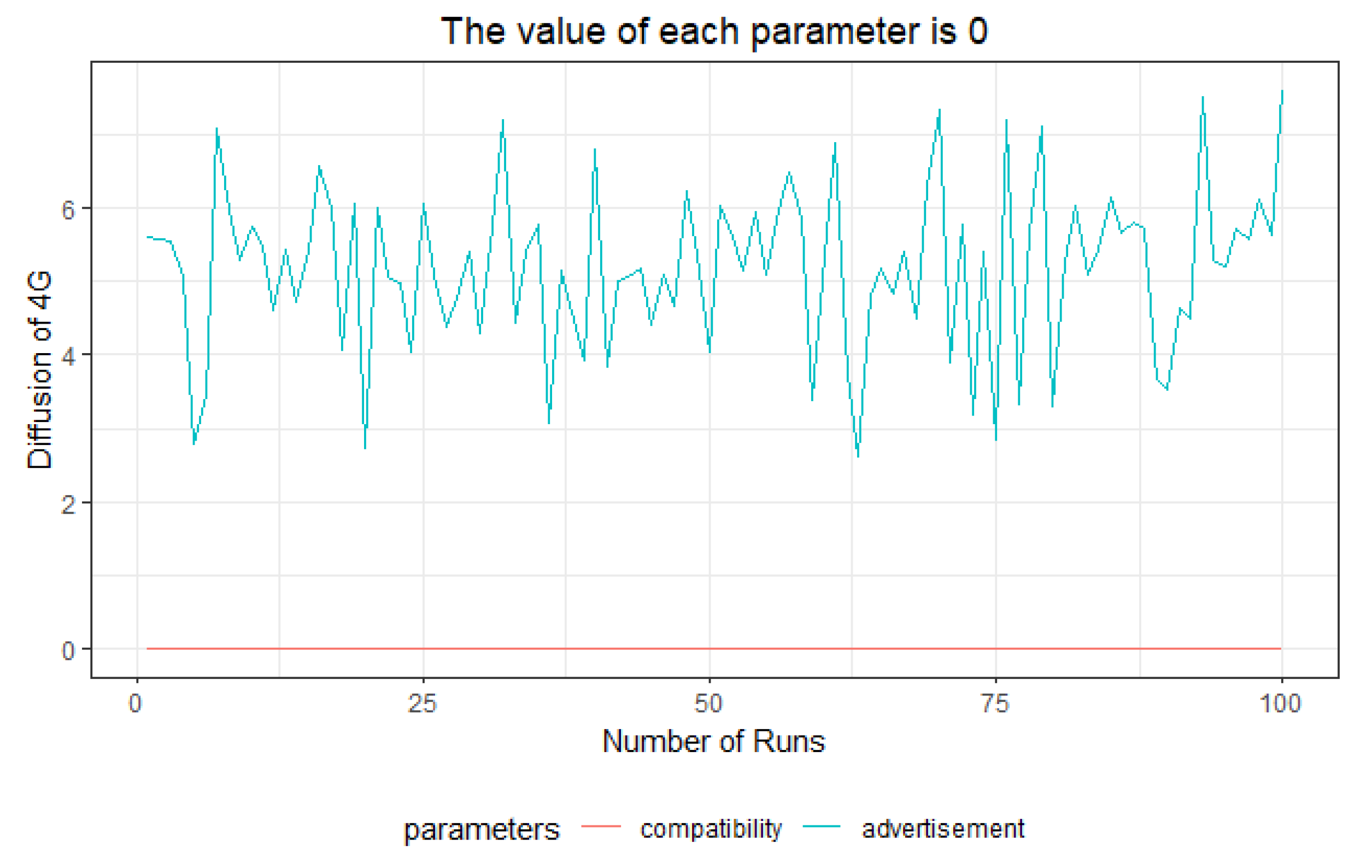
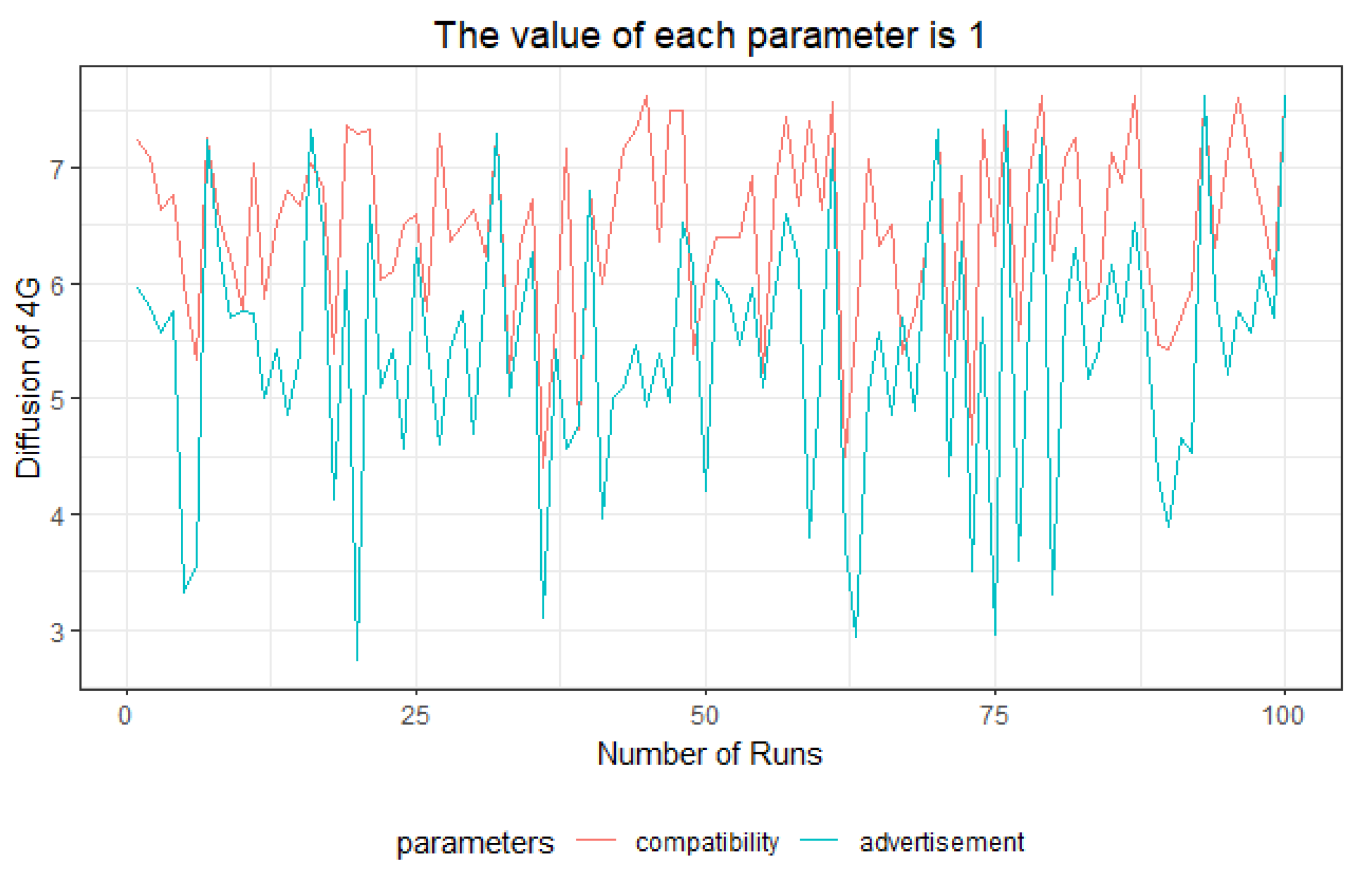
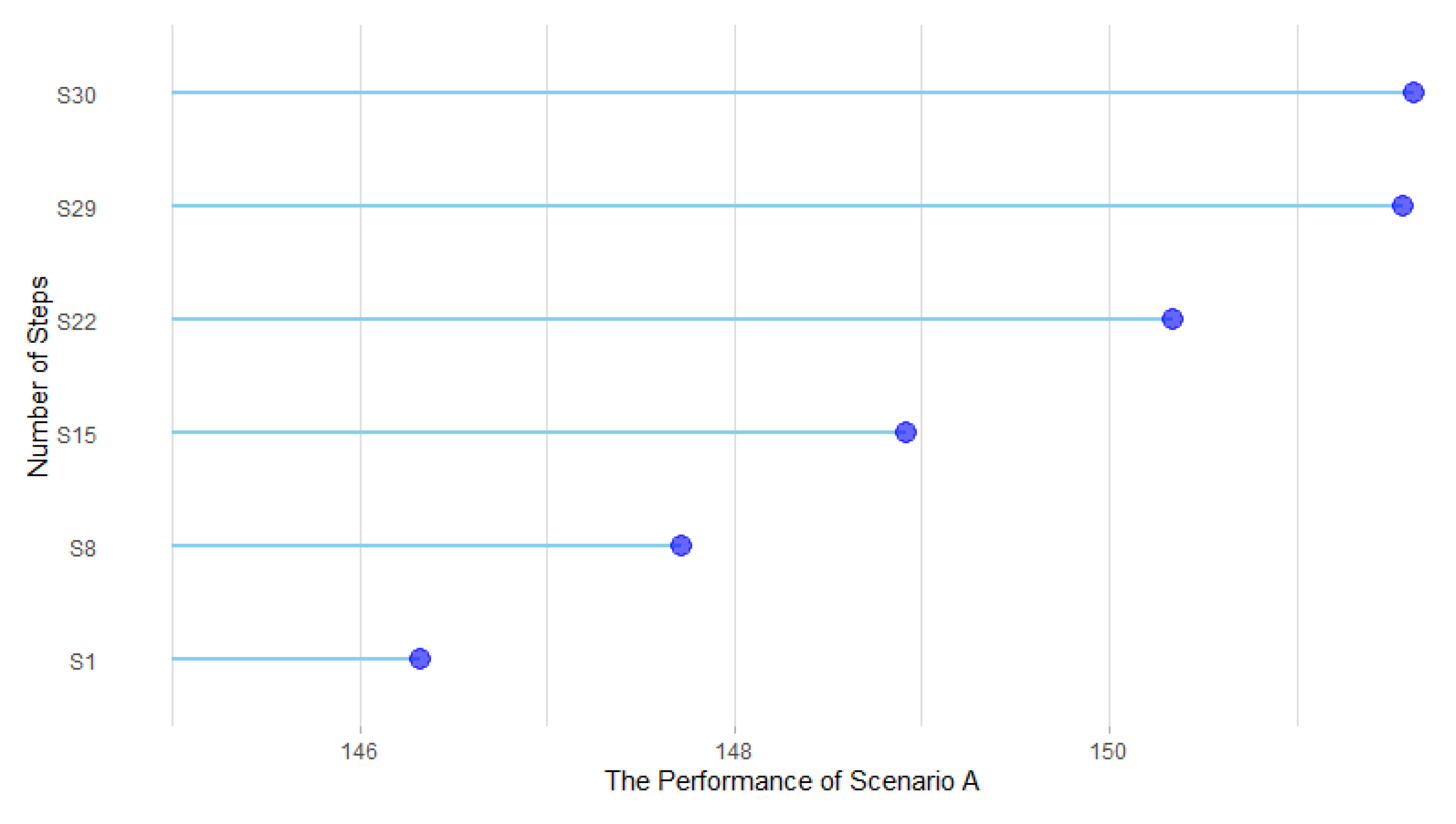
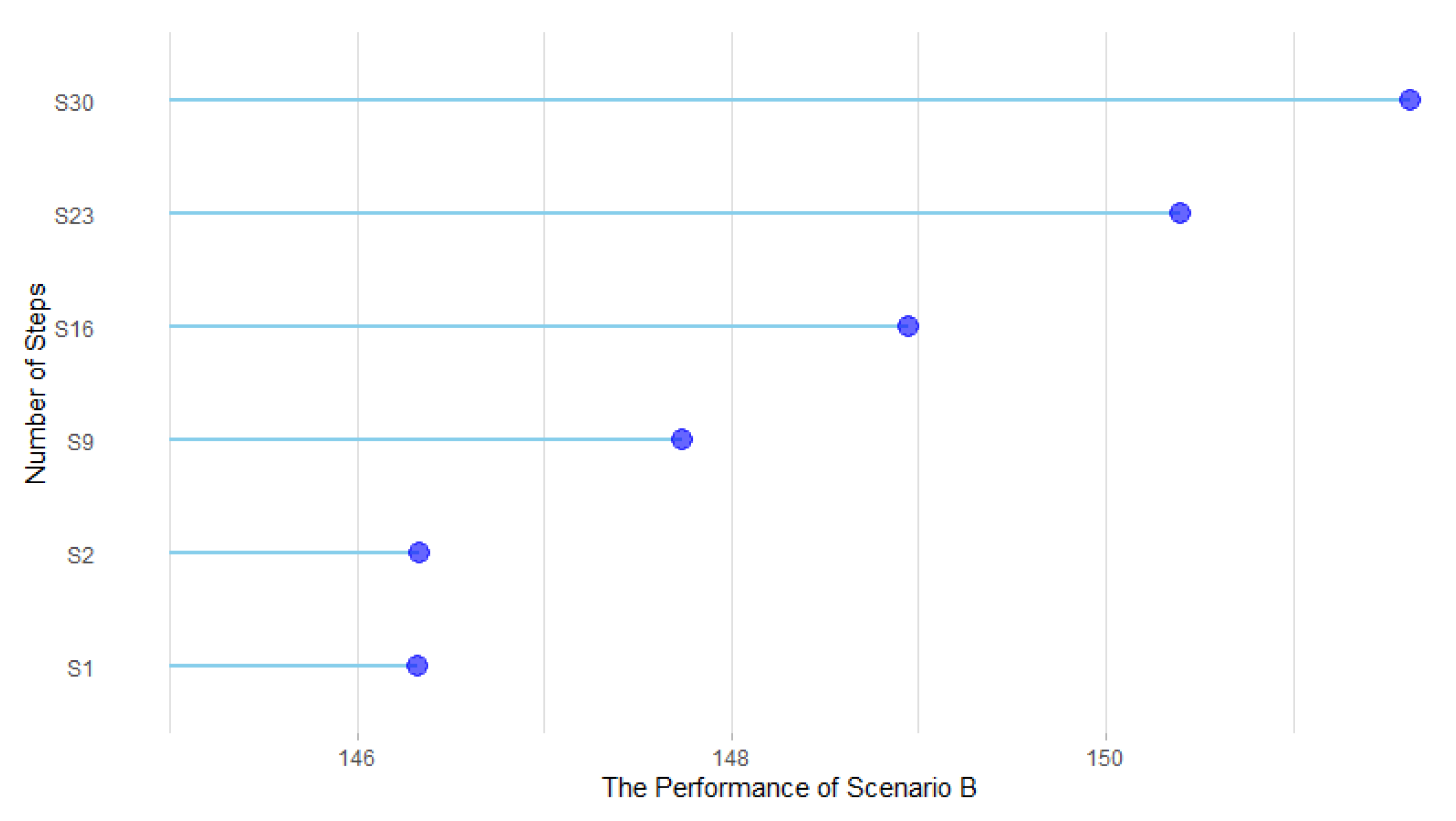
In order to formulate scenarios for accelerating 4G diffusion, the decision parameters were selected from input parameters, and the necessity and influence of decision parameters were studied in 100 simulation runs for the first quarter of 2018. In terms of necessity, the results showed that if the value of advertisement is zero, 4G technology could get diffused over the society, which is mainly because of the technology push nature of MTTs [
102,
103,
104] and WSN topology of Iran’s social network, where world-of-mouth plays a critical role [
100,
101], while 4G could never be diffused if the handset compatibility is zero. In addition, in terms of influence, the compatibility parameter was found to have a higher performance in increasing 4G technology than advertisement parameter. Thereafter, a number of operational steps were extracted through the states of each parameter (i.e., six states for advertisement and five states for compatibility). Using these results, the most appropriate scenarios were extracted; scenarios that continuously increased 4G technology diffusion in Iran by the least number of operational steps and turning points. Like any scientific work, especially researches on empirical ABMs, this work has had some limitations. The first limitation was the inaccessibility and incompleteness of some individual-level data, such as the reluctance to innovation (R2I) score for which Individual Innovativeness (II) Scale was distributed among 1250 individuals, out of which 903 returned, and 800 of them were complete. The second limitation was the fact that some social recorded data were not up-to-date and needed to be collected from various sources.
Two topics can be recommended for future researches. The first topic is about the study of model application in other communities, which can provide useful information on model generalizability in other case studies. The second topic is that the entry of the fifth-generation of mobile technologies (5G) in 2020 [
105,
106] will definitely affect the diffusion of other MTTs, which investigating this effect is worth being the subject of a separate study.