1. Introduction
The reliability and security of critical infrastructures is vital to the stability of a country’s social system. The growing threat of international terrorism may imperil facilities and cause massive loss to people’s lives and properties. Such man-made disasters often seriously damage facilities, resulting in general or partial impacts on the normal order of society, leading to large-scale supply shortages of products or service interruptions. Some attacks will affect the sustainability of key facilities, making it difficult to ensure the normal supply, so it is necessary to consider the location of facilities under attack. In practice, there may be multiple rounds of confrontation between the attackers and defenders, so dynamic attack defense issues need to be considered to ensure the long-term sustainability of the facilities.
Terrorists always seek out the most critical facilities to conduct attacks and maximize the loss of the social system. To strengthen the security and reliability of critical facilities, facility locations should be well planned and fortified, and coping measures, such as backup systems and service reassignments, should be prepared for in advance of an attack. Our problems fall into the class of an incapacitated facility location, which is a variant of the
p-median problem first proposed by German scholar Alfred Weber [
1]. In the paper of Huizhen [
2], they further study the mathematical nature of the semiLagrangian relaxation (SLR) applied to solve the un-capacitated facility location (UFL). On this basis, SLR for UFL is improved in theory, and the way to improve its computing capability is discussed. Monabbati [
3] use their proposed sub-additive dual ascent procedure to find an optimal sub-additive dual function based on Klabjan’s generator sub-additive function to solve the so called uncapacitated facility location problem (UFLP). Glover [
4] proposes a simple multi-wave algorithm for solving the uncapacitated facility location problem (UFLP) to minimize the combined costs of selecting facilities to be opened and assigning each customer to an opened facility in order to meet the customers’ demands. On the basis of an incapacitated facility location problem with interdiction and fortification, the
r-interdiction median problem with fortification (RIMF) occurs. In the existing literature, node interdictions have been divided into two groups, i.e.,
r-interdiction median models (RIM) and r-interdiction covering models (RIC). The RIM model was originally formulated by Church and Scaparra [
5], where interdiction strategies seek
p facilities that have already been located. The model determines a subset of
r facilities, and if these facilities are lost, the impact on the average service distance or the total weighted distance from the customer is at its greatest. In the RIC model, the objective is to specify
r facilities of
p existing facilities, which, when removed, results in a maximum drop in coverage. Church and Scaparra [
6] then put forward the interdiction median problem with fortification (IMF) model, which involves finding a subset of
q facilities in
p different locations of the supply or service facility; when these
q facilities harden, they provide the best protection from a subsequent optimal
r-interdiction strike. Church and Scaparra [
7] propose the
r-interdiction median problem with fortification (RIMF) model, where the leader and follower respectively conduct interdiction and fortification, assuming that one side has complete information about the other side.
Figure 1 below shows the study process from the
p-median problem to the RIMF problem.
A number of studies on the
r-interdiction problem in the literature have strived to develop more reliable and invulnerable systems. Snyder [
8] presents a stochastic location model with risk pooling (LMRP) to optimize location, inventory, and allocation decisions under random parameters described by discrete scenes. Scaparra et al. [
9] present an optimization modeling approach to allocate protection resources among a system of facilities so that the disruptive effects of possible intentional attacks to the system are minimized. In the work of Aksen et al. [
10], the authors elaborate on a budget-constrained extension of the RIMF model, where the objective function is to find the optimal allocation of protection resources to a given service system consisting of
p facilities such that the disruptive effects of
r possible attacks are minimized. Liberatore et al. [
11] present the stochastic
r-interdiction median problem with fortification (S-RIMF), where the model takes into consideration a random number of possible losses. Zhu et al. [
12] studies the
r-interdiction median problem with probabilistic protection, assuming that defensive resources are allocated based on the degree of importance of the service facility. Medal et al. [
13] integrate the facility location and the facility reinforcement decisions into the formulation and assume that the decision-maker is risk averse and thus interested in mitigating against the facility disruption scenario with the greatest consequences. Mahmoodjanloo [
14] puts forward a tri-level model under the defender–attacker–defender framework based on leader–follower games for facility protection against disturbance in an
r-interdiction median problem. Mahmoodjanloo [
14] focuses on reducing the effect of intentional attacks, in which facilities are located and strengthened within a limited budget. Sadeghi [
15] presents a new formulation and solution method for the partial fortification and interdiction of a tri-level shortest path problem which extends the existing network interdiction models to a more practical environment. Zheng et al. [
16] present an exact approach to solve the
r-interdiction median problem with fortification. Their methods include a greedy heuristic and an iterative algorithm, solving a set cover problem iteratively to ensure the best solution upon termination. Khanduzi [
17] implements two novel approaches to solve the multi-period interdiction problem with fortification. Roboredo [
18] proposes a branch-and-cut algorithm for the RIMF problem, which is the best exact algorithm found. Furthermore, Roboredo [
19] also put forward a branch-and-cut algorithm for the
r-interdiction covering problem with fortification (RICF) problem, which is faster in solving large instances compared with the exact method found in the literature. Biswas and Pal [
20] propose an interesting hybrid goal programing model and genetic algorithm in a fuzzy environment. Barma et al. [
21] present a novel linear programming(LP) model with antlion optimization algorithm for multi-depot vehicle routing problem(VRP). In conclusion, in the previous literatures, there is almost no multi-round attack defense confrontation. Most papers generally consider a bi-objective function for at most a three level RIMF problem. In this paper we present, for the first time, a cyclic equilibrium gaming case of the
r-interdiction median problem with fortification based on the study of Dong [
22]. We consider it a dynamic Stackelberg game [
23], involving two non-cooperative, fully rational players to protect (or attack) the facility as much as possible. Each side makes the most optimal decision based on the other’s decision. We present a bi-objective mixed integer linear programming model to formulate the cyclic dynamic gaming case of the
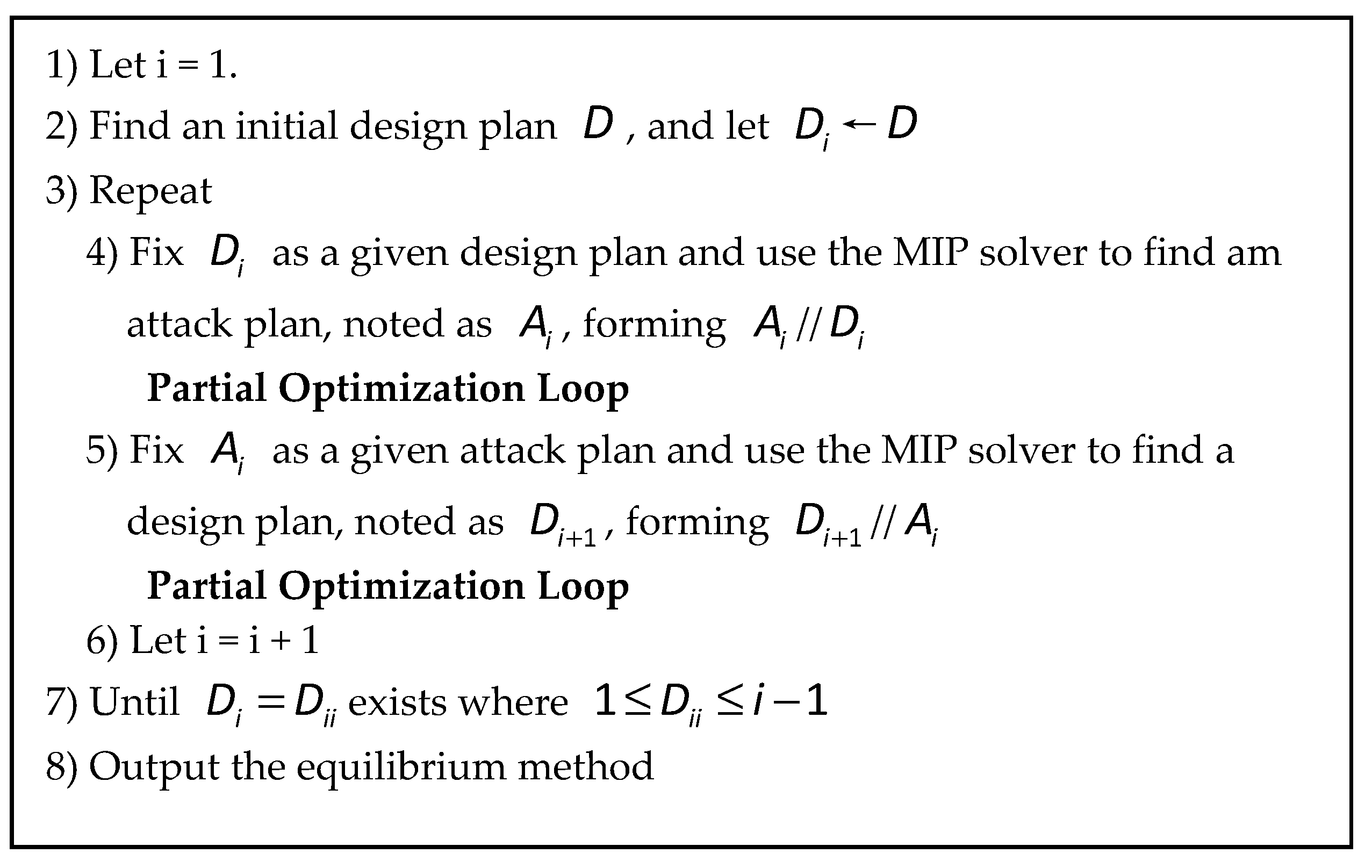
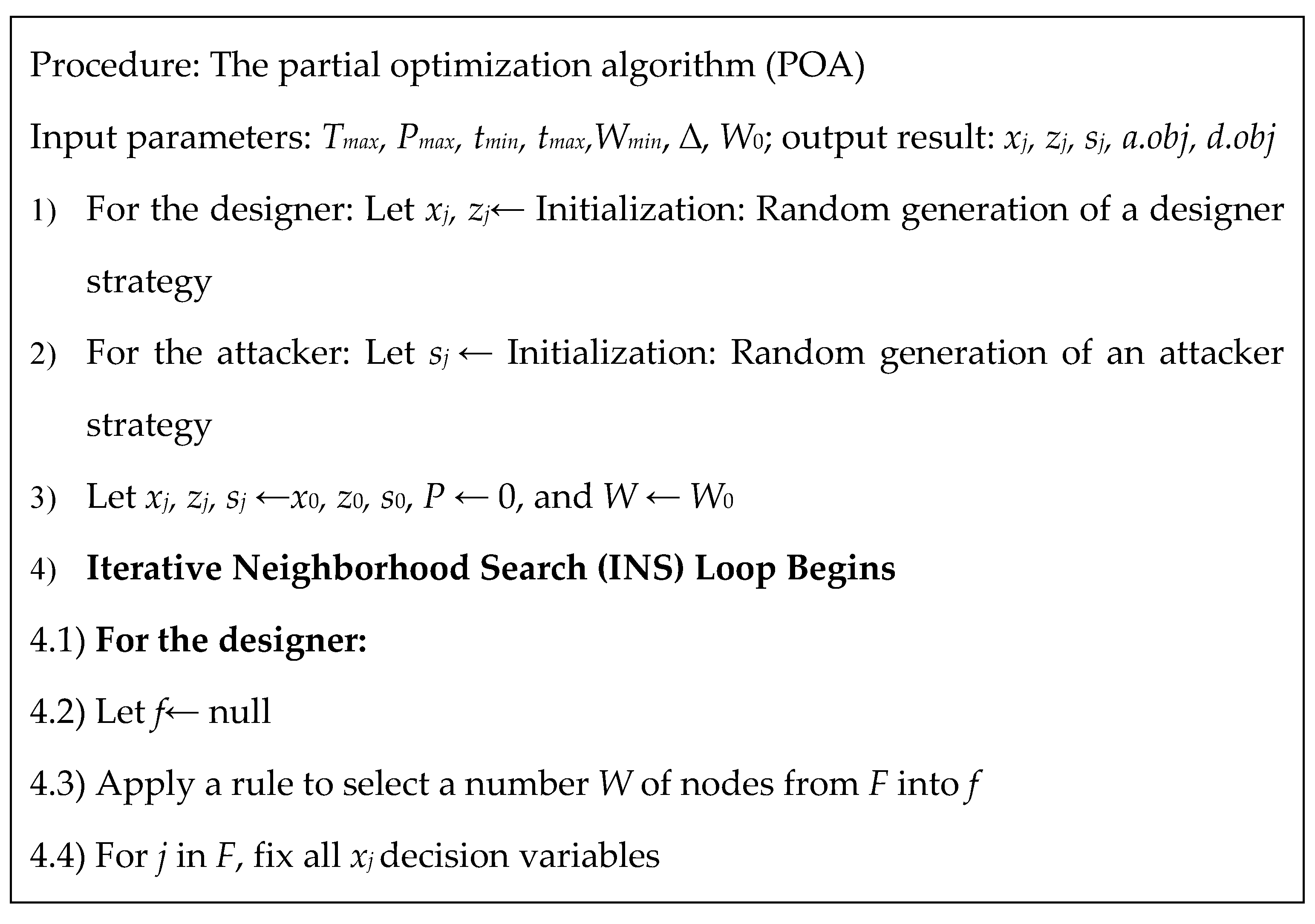
r-interdiction median problem with fortification (CDGC-RIMF). Using the cyclic algorithm, the computer generate two decision packages for both the attacker and defender until the equilibrium was cyclically reached. For the large-sized problem, we developed a heuristic algorithm based on the partial optimization strategy [
24,
25] to efficiently solve the problem with near-optimal solutions. Contributions of the paper are outlined as follows.
This article first brings up the CDGC-RIMF problem, which considers cyclic decision periods/phases in large-scale scenes with two opposite objectives.
This article constructs the mixed-integer linear programming (MILP) model so as to solve it by an efficient and easy way through the CPLEX solver.
For the large-size scenes, we developed a heuristic algorithm that implemented dynamic iterative partial optimization alongside MILP (DIPO-MILP).
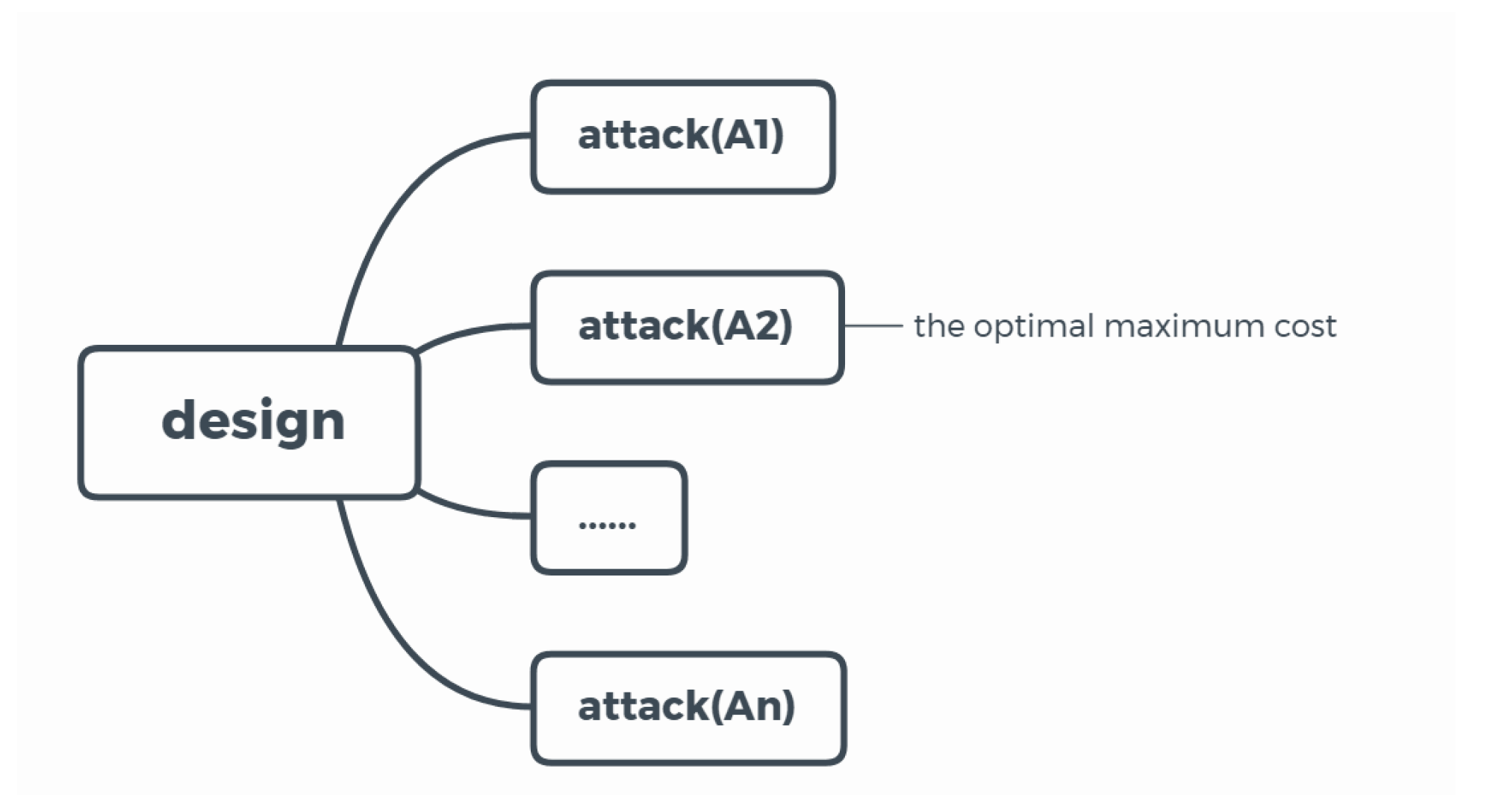
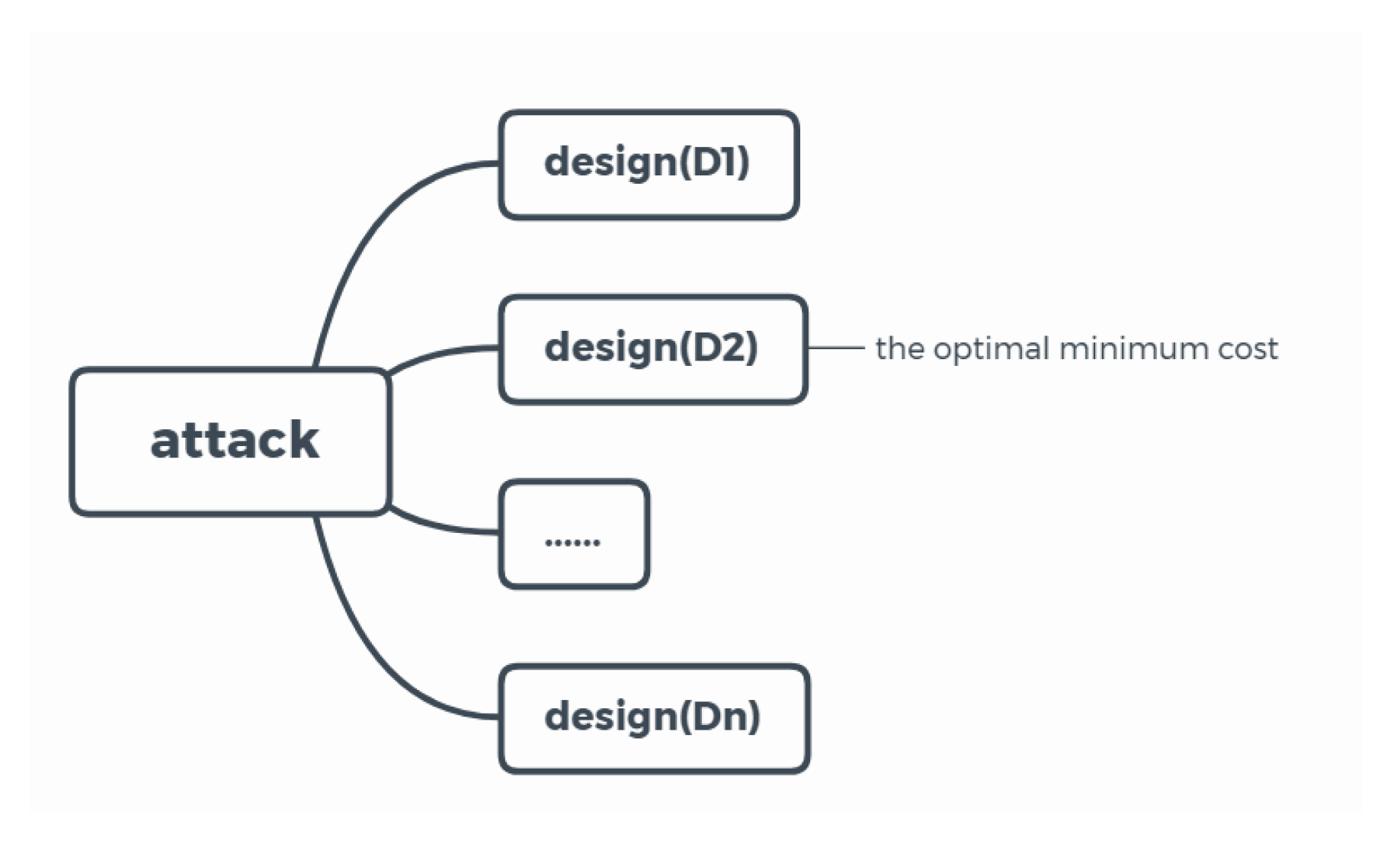
Our model put the wise decision of the attacker into consideration. The objective of attacker was to consider the optimized rearrangement of the defender faced with the destruction to achieve the worst loss possible.
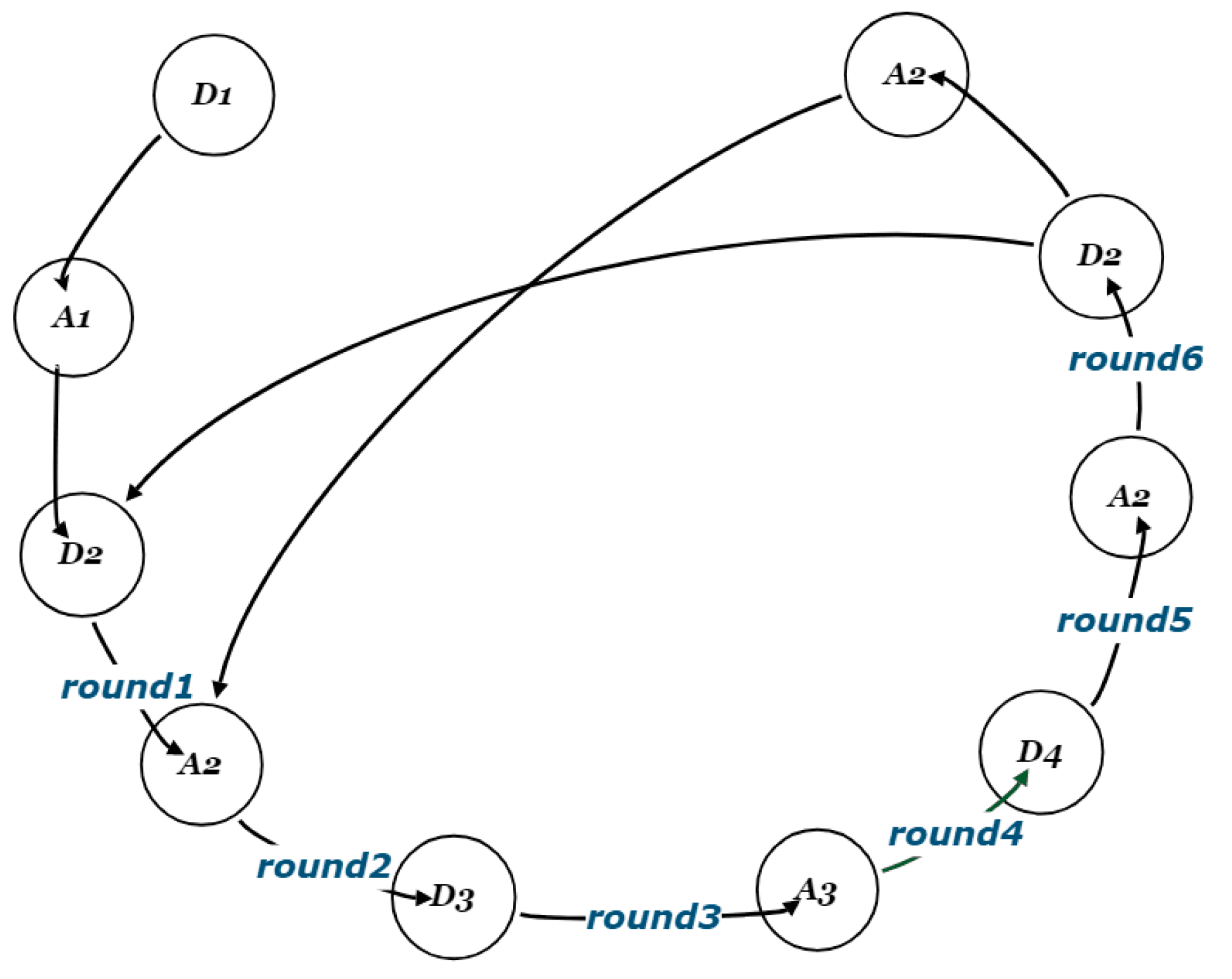
Our algorithm generated two decision packages for both the attacker and defender, thereby reaching an optimal cyclic equilibrium.
In the cyclic confrontation process, each side made the most optimal confrontation plan until the balance of the cyclic confrontation was reached. Through this model, the decision package of the two sides could be produced. For the protector, it could predict the other side’s decision in advance (the protector knew that the attacker would make the most optimal confrontation plan) and then make the decision for the next step. It could help the facility manager make wise decisions for site selection and defense in advance, so as to ensure the long-term sustainability of the facility.
The remaining paper is organized as follows. In
Section 2, we formally describe the CDGC-RIMF model. In
Section 3, we present the notation, the property of the cyclic bi-objective MILP model, and a partial optimization algorithm for large-scale problems. In
Section 4, we present some computational experiments, including the small- and large-scale problems, and analyze the protection effect to make up a fortified facility. Finally, in
Section 5, we summarize our work and present suggestions for future works.
2. Problem Description and Formulation
The problem involved a general service supply system composed of several facilities and a number of demand nodes that received goods or services from their nearest service sites. A number p of facilities were built out of a set of potential locations sites, denoted as F (). Notation N, indexed by i, represents the set of demand nodes. Each demand node i, was associated with a demand . The distances between the facilities and the demand nodes were known parameters, denoted as dij, where and . The service cost was expressed as the sum of total demands weighted by the distances to their closest facilities. Each candidate site was characterized with a fixed cost to build a facility and a fixed fortification cost to protect the built facility. The attacker (follower) intended to carry out the most devastating attack possible and was assumed to have the ability to destroy the maximum r number of facilities after considering all possible design plans from the designer. The designer, who was able to protect g facilities from being attacked, tried to minimize the establishment and protective cost as well as system loss with consideration of all possible attacks by the attacker.
We formulated the cyclic dynamic gaming case of the r-interdiction median problem as a bi-objective MILP model, as shown below. The sets, parameters, and decision variables used in the mathematical formulation were introduced in advance, as follows.
Sets:
: Set of demands;
: Set of candidate sites.
Parameters:
: Index of demand that ;
: Index representing candidate site that ;
: Demand of node ;
: Number of potential sites;
: Number of built (located) facilities;
: Number of interdicted facilities;
: Number of defense facilities, q < p, r < p–q;
: Setup cost at site j;
: Fortification cost at site j;
: Distance from demand i to site j;
: A large number.
Variables:
: ;
: ;
: ;
: ;
: ;
X: Set for facility location, ;
Y: Set for service assignment, ;
S: Set for interdicted facility, ;
Z: Set for defense facility, .
The main goal of the designer was to design a service network with the objective of minimizing the sum of fixed and variable costs of a system facing disturbance. The goal of the attacker was to maximize the objective of the designer.
Objective 1 (from the designer):
Objective 1 (from the attacker):
Subject to:
- (1)
,
- (2)
,
- (3)
,
- (4)
,
- (5)
,
- (6)
,
- (7)
,
- (8)
,
- (9)
.
In the above model, Constraint (1) indicates that the designer built
p facilities out of the set of candidate facilities. Constraint (2) ensures that, at most,
r facilities were to be interdicted. Constraint (3) stipulates that the designer could maximally protect
q facilities. Constraint (4) makes sure that each demand was serviced by one facility. Constraint (5) states that only the facilities that were set up and not attacked at the same time (or were attacked but protected at the same time) could serve the demands. Constraint (6) indicates that only the built facilities were allowed to be protected. Constraint (7) determines whether a site had a valid facility, i.e.,
bj = 1 if site
j had a valid facility or
bj = 0 if otherwise. Constraint (8) is a new constraint for the closest assignment, a different version from the related constraints devised by Church [
6] and Liberatore et al. [
11]. This constraint normally used the set of existing valid facilities (not including
j) that was further than
j from demand
i. However, these sets had to be recalculated when the fortification or interdiction changed; a phenomenon associated with considerable computational complexity. Constraint (9) states that all of the decision variables were binary.


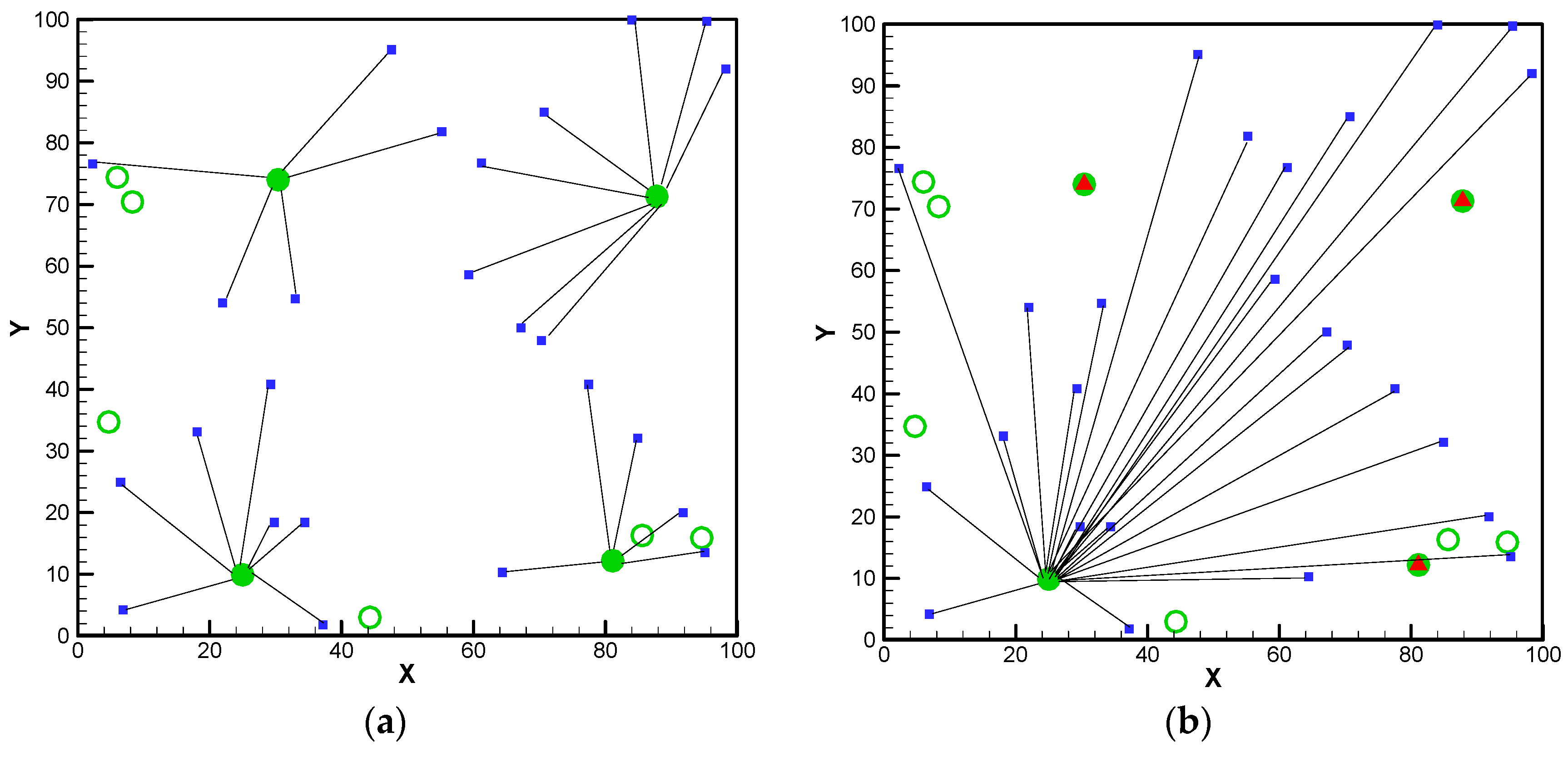
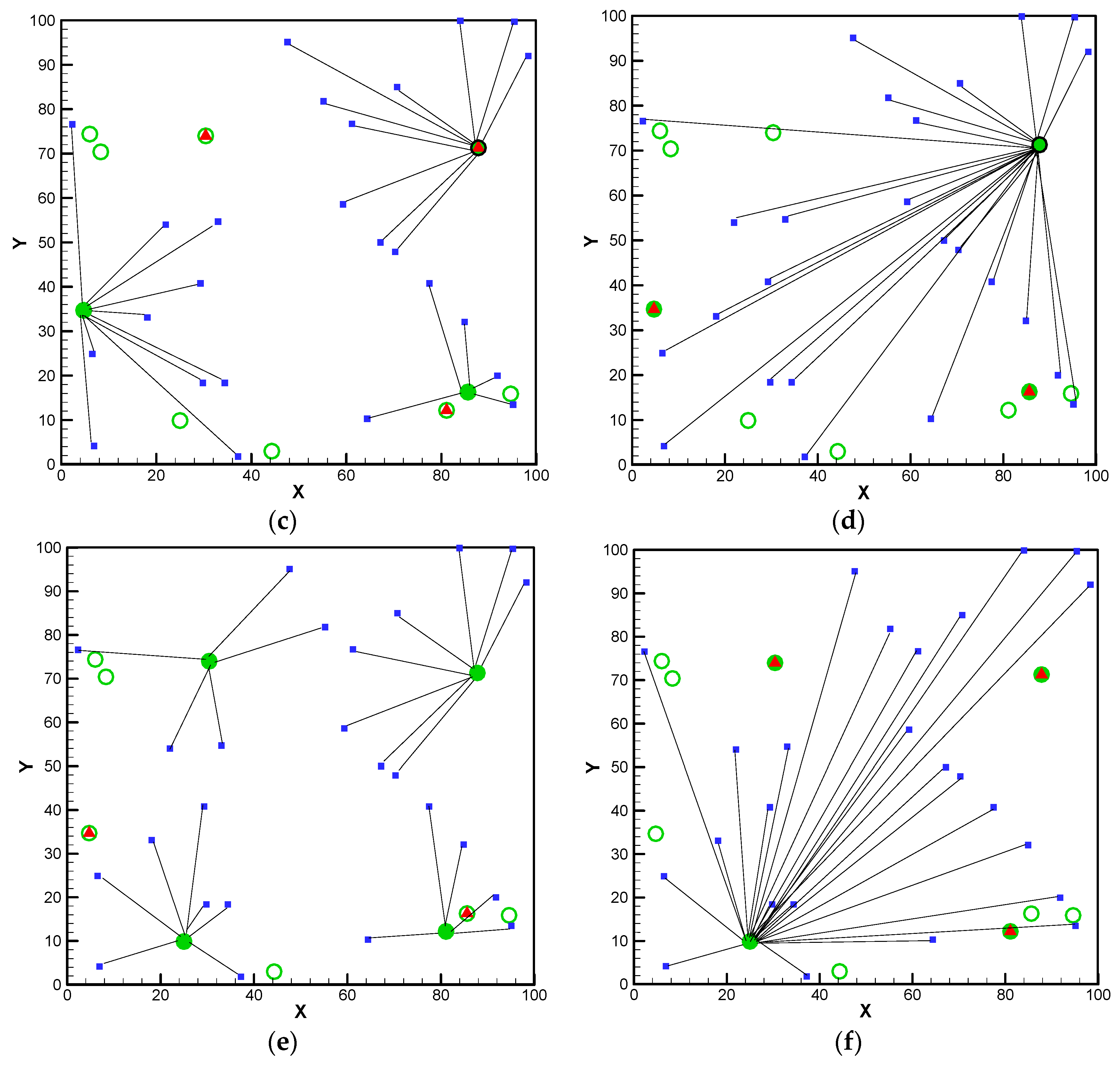
 —the potential locations of facilities;
—the potential locations of facilities;  —interdiction on the facilities;
—interdiction on the facilities;  —facilities in use;
—facilities in use;  —fortified facilities in use,
—fortified facilities in use,  —demands.
—demands.
 —the potential locations of facilities;
—the potential locations of facilities;  —interdiction on the facilities;
—interdiction on the facilities;  —facilities in use;
—facilities in use;  —fortified facilities in use,
—fortified facilities in use,  —demands.
—demands.