A Secure Data Sharing Platform Using Blockchain and Interplanetary File System
Abstract
1. Introduction
2. Related Work
2.1. Digital Content Protection
2.2. Blockchain in Cloud
2.3. Blockchain in IoT
2.4. Access Control Using Blockchain
3. Motivation
4. Problem Statement
- Identity management Users are first authenticated using RSA signatures before giving them access to data.
- Security of digital assets: Adding encryption to the data hashes ensures the security and avoids data leakage.
- Authenticity of owner: Seller can trust the owner by checking the reviews about owner and its data.
- Quality of data: Rating or reviews depict the quality of data; therefore, by checking the reviews, buyer will only get high quality data.
- Management of fake reviews: Fake reviews are being identified using Watson analyzer.
- Dispute handling: Arbitrator is introduced to resolve downloading disputes.
- User incentive: By giving incentives, sellers are being motivated to give feedback on used data to aid future customers. The comparison of existing work with proposed scenario is given in Table 1.
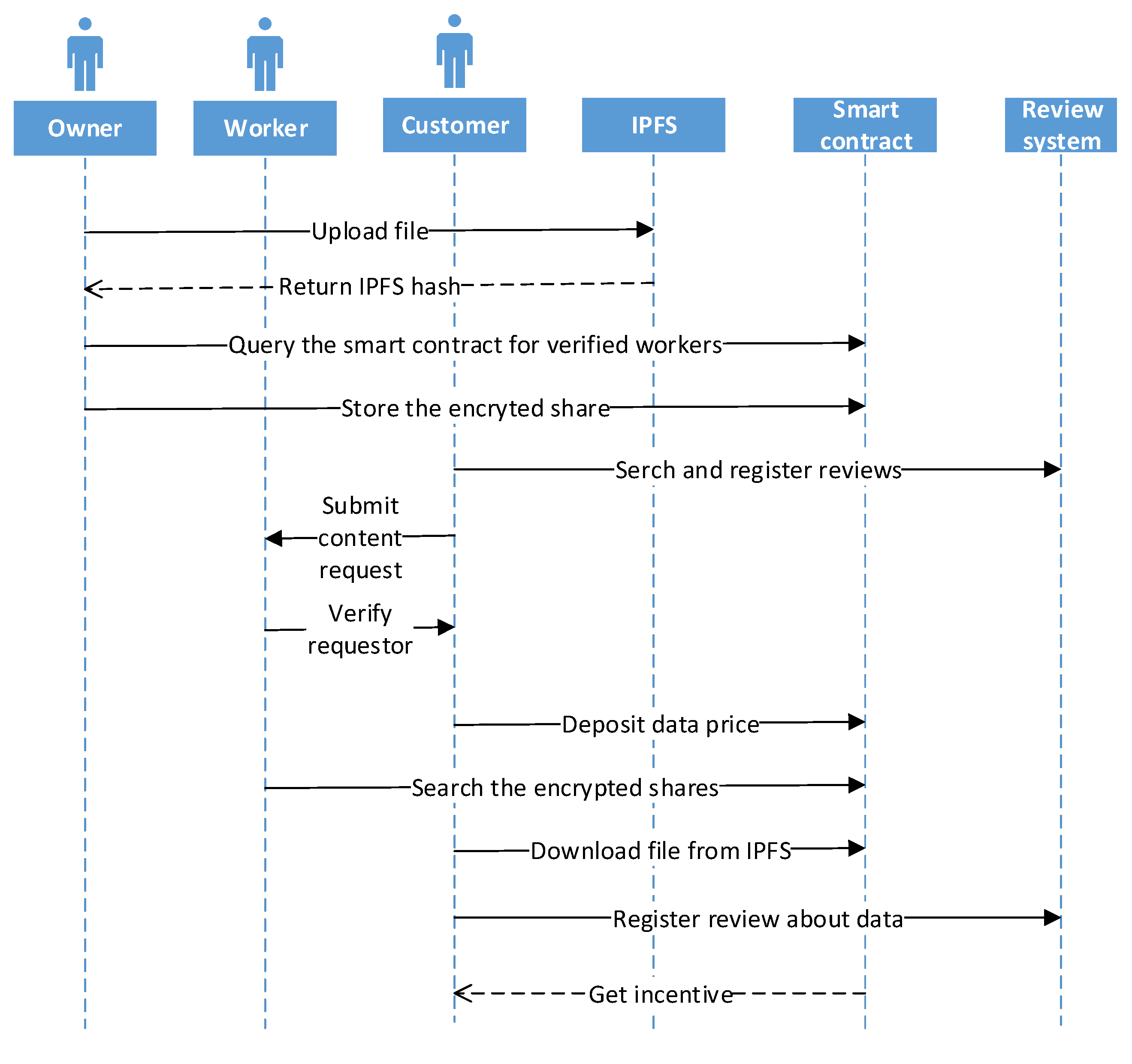
5. System Model
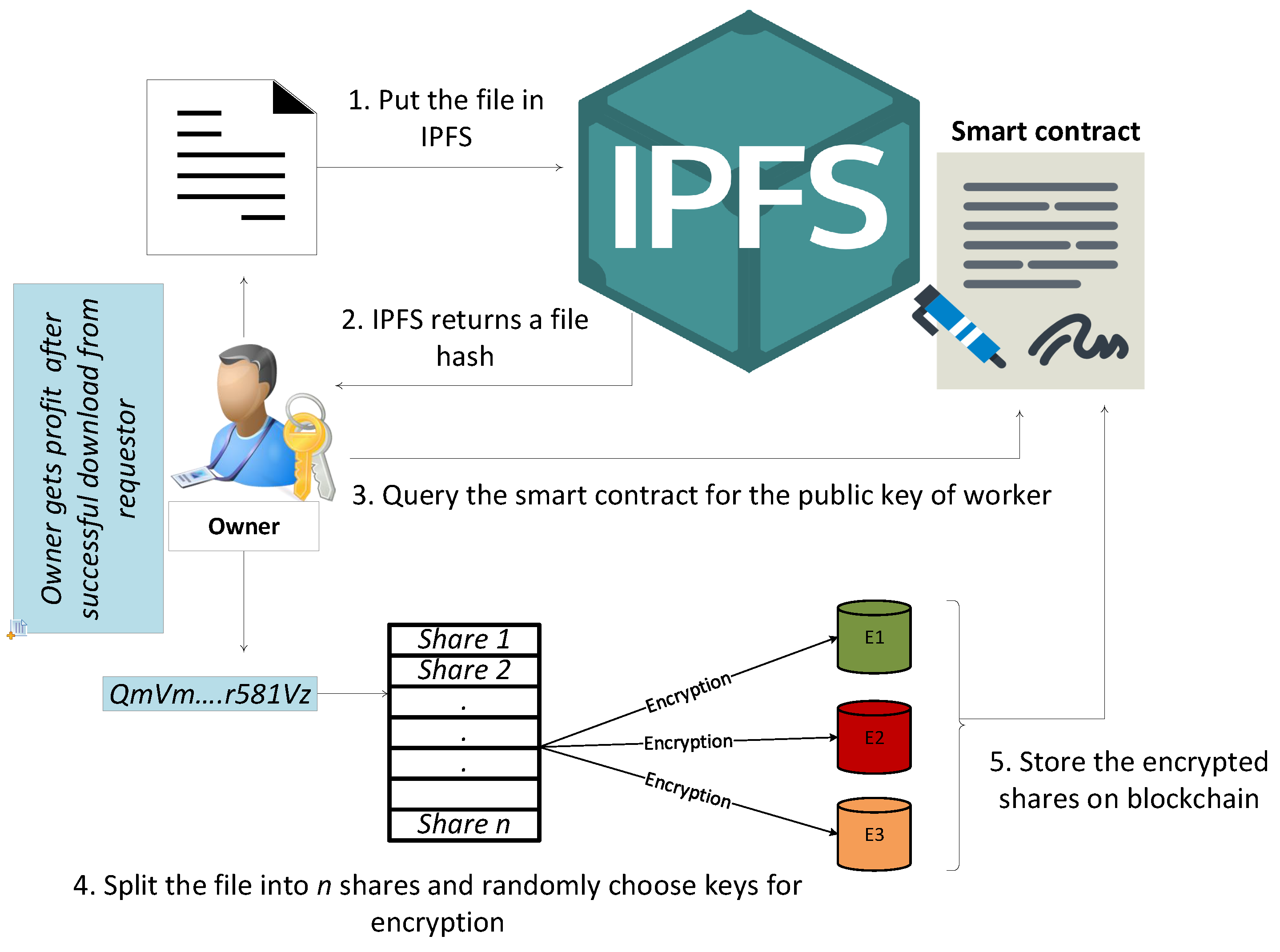
5.1. Data Sharing
//upload the plain file meta
ipfs.files.add(buf, function (err, meta_result) {
if(err) {
console.log(err);
return res.sendStatus(500);
}
console.log(meta_result);
res.json({ “meta_hash”: meta_result[0].hash,
“file_hash”: fileMeta.hash,
“address”: recipient_addr,
“email”: recipient_email });
}:
SSS
- Combination of k or greater number of makes it easy to compute original file
- In other case, if there is k − 1 or less number of then it would be difficult to reconstruct the actual data, therefore S becomes undetermined. It is known to be threshold scheme, where k = n means that all the involved entities need to reconstruct the actual secret S [5]. In our case, split size and number of shares are taken as 5 and 3, respectively. When shares are generated using SSS, these shares are encrypted and stored into smart contract. These shares can only be decrypted by verified workers whose public key is searched by the owner while uploading the file to IPFS.
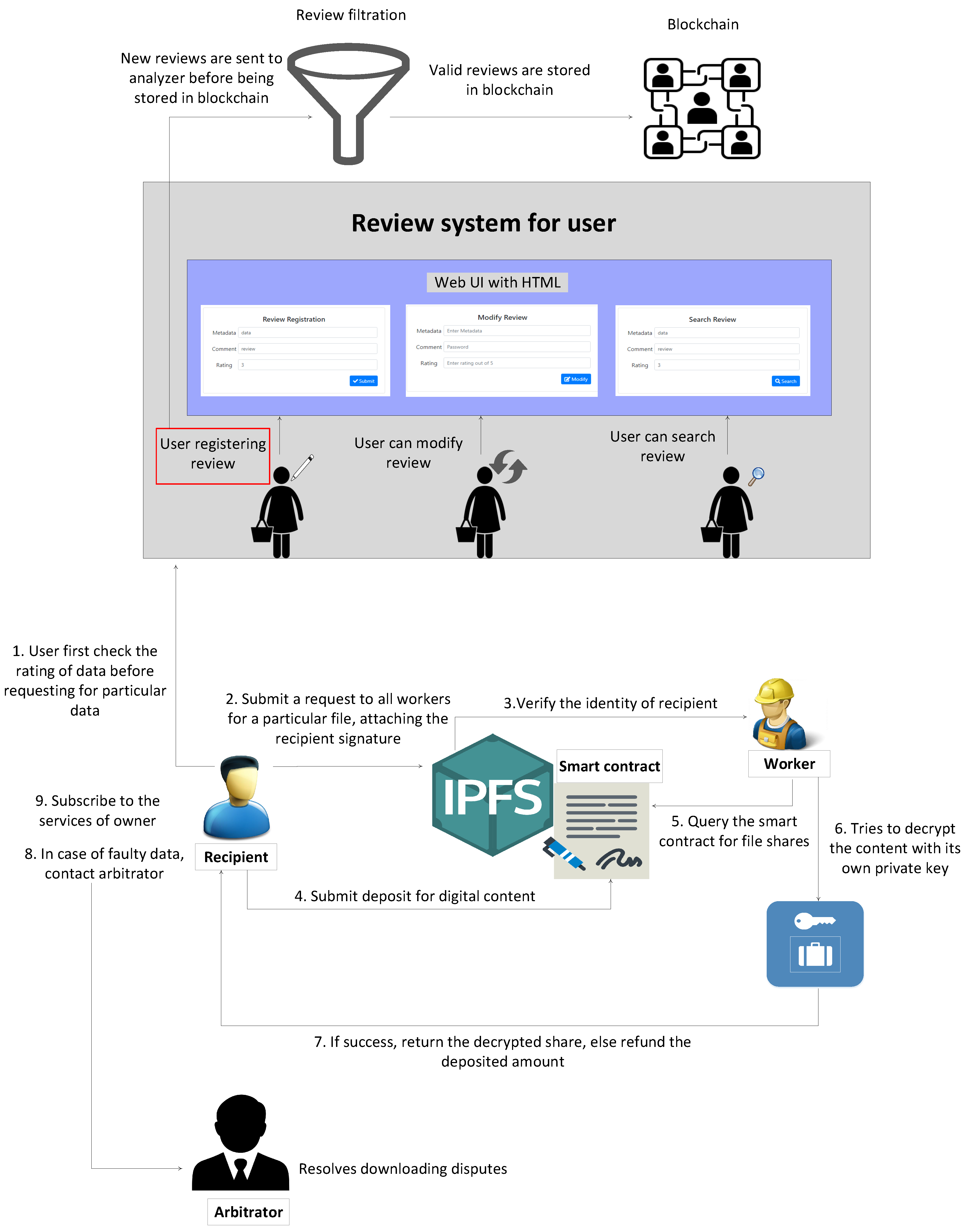
5.2. Data Retrieval
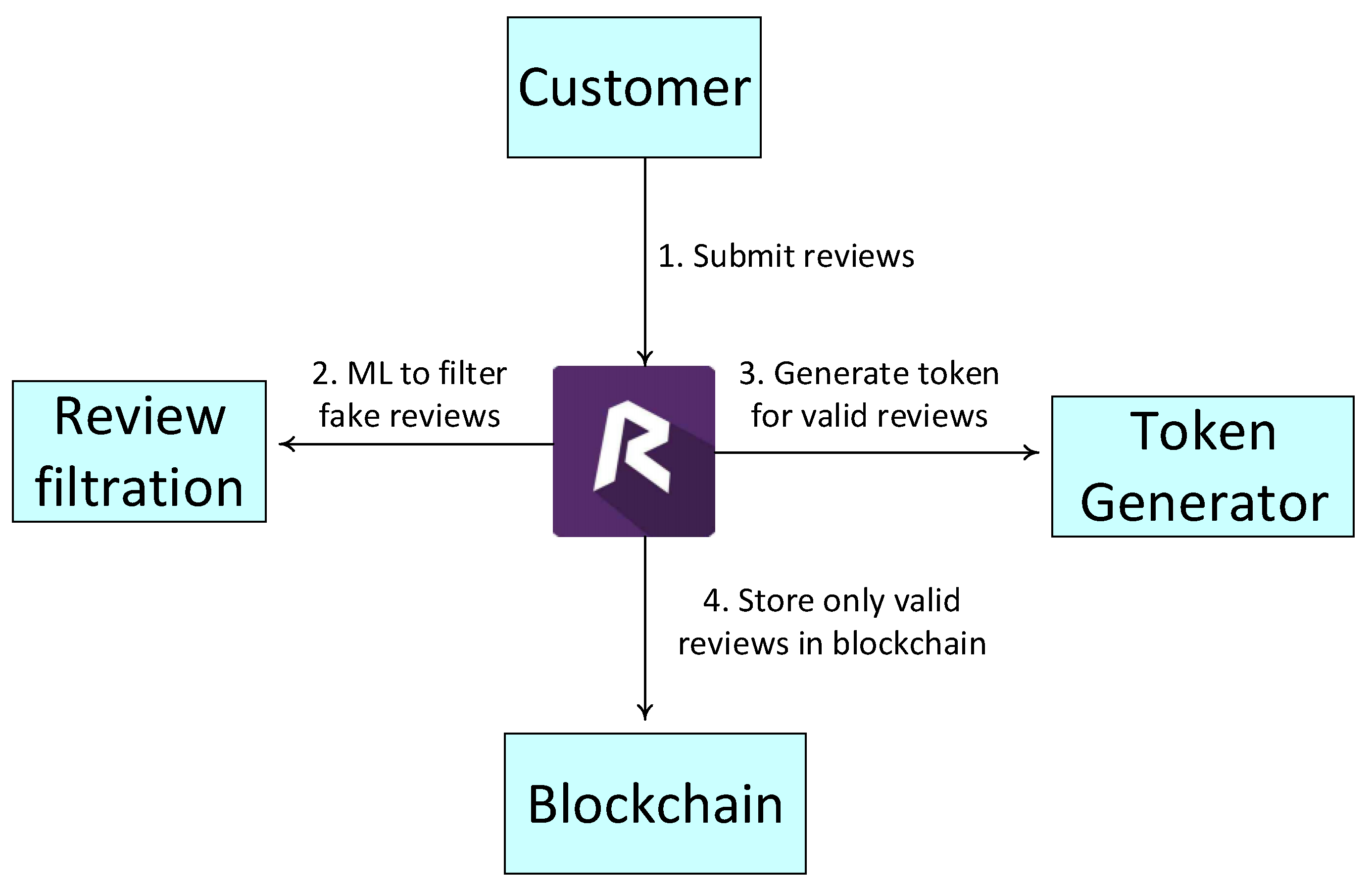
5.2.1. Data Review System
5.2.2. Detection of Fake Reviews
- Vote Manipulation:A situation where owner asks his friends or employees to post fake reviews regarding the quality of product.
- Vote Buying:When companies hire special employees to post reviews using fake emails and user names by paying them handsome amount of money.
- Vote on wrong thing:This category has nothing to do with fake reviews, but most of the times, customers do not actually give review on the product they are supposed to register review on. For example, a customer has booked a room in a hotel and may not like the beach closer to the hotel. Then, the customer is most likely to give negative reviews.
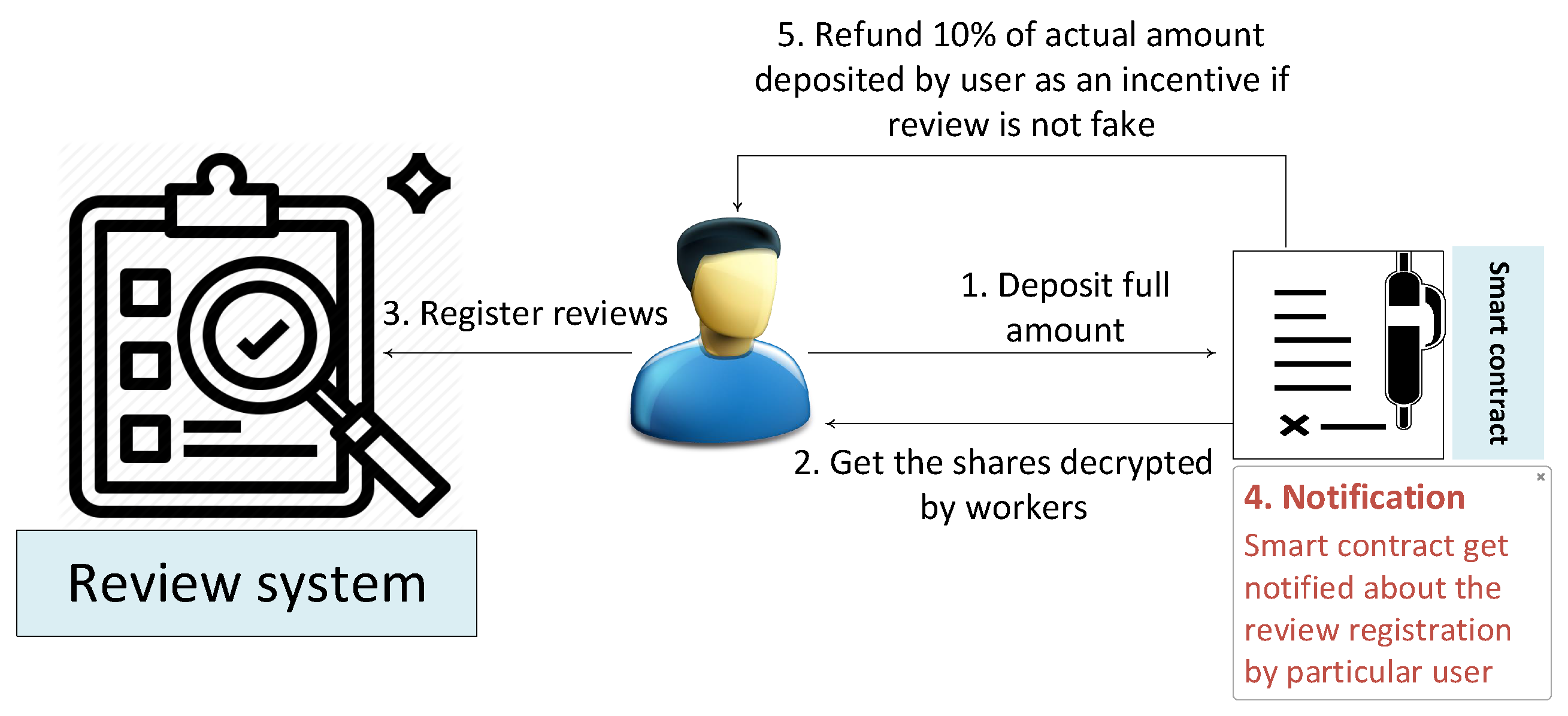
5.2.3. Data Distribution to Customers
//RSA key pair generation
key0.generateKeyPair(2048, 65537);\\
fs.writeFileSync(“privateKey_0.pem”, key0.exportKey(’pkcs8-private-pem’));
fs.writeFileSync("publicKey_0.pem", key0.exportKey(’pkcs8-public-pem’));
console.log(“0 - RSA Key Pairs saved.”);
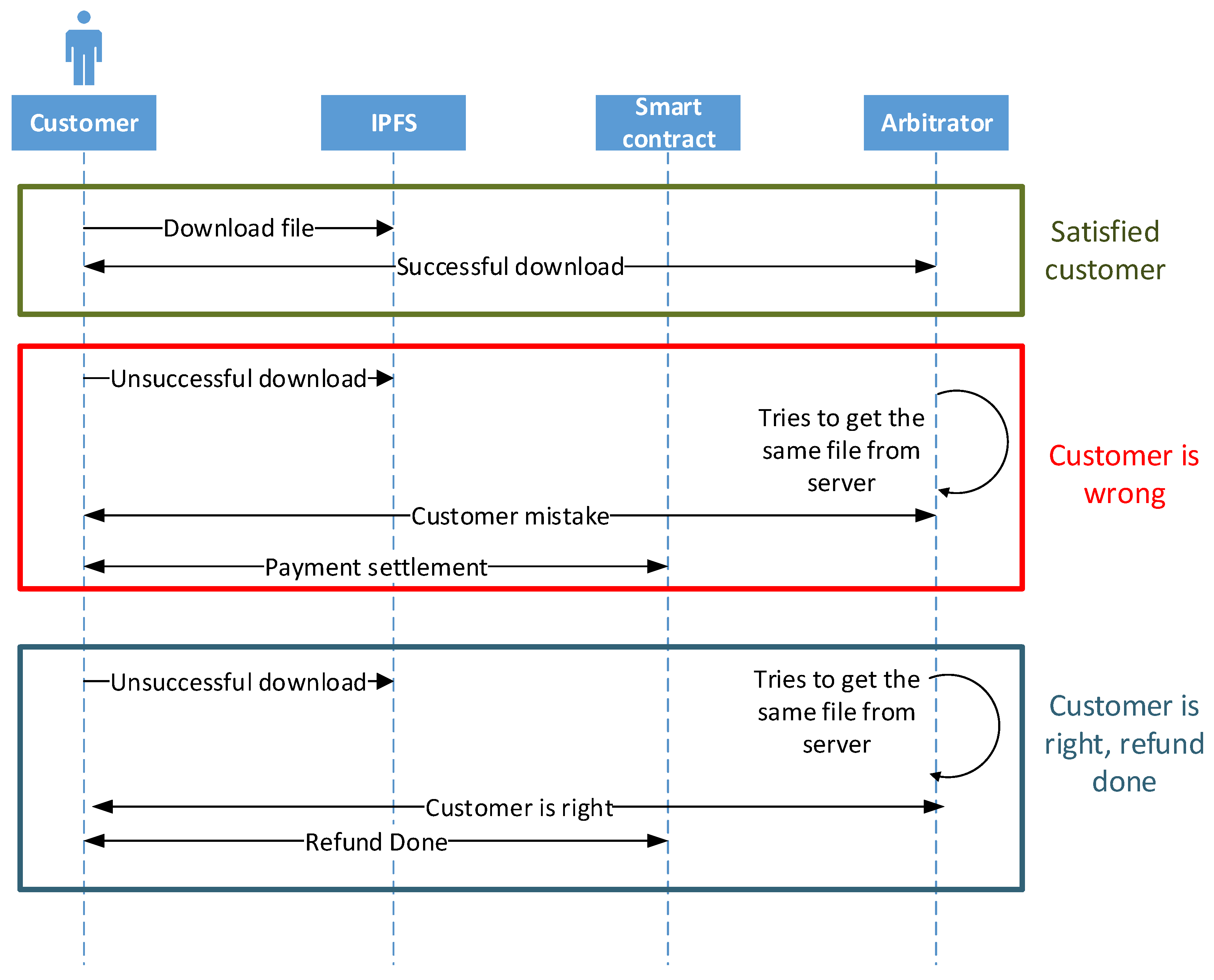
5.2.4. Dispute Handling
- Case 1: In this scenario, a customer submits the price for digital content, gets access to the hashes and gets the digital data on IPFS. These is no dispute in this case, customer successfully downloads the accurate and complete data from the server. The scenario for satisfied customer is shown in green box in Figure 6.
- Case 2: After downloading the file from server, customer gets to know that data is either incomplete or faulty. To verify the claim of customer, arbitrator decrypts the same hash and access the data from IPFS. When data is cross-checked by arbitrator, it finds the data as complete and accurate. As a result, it is concluded that customer’s claim is wrong and there is no refund policy in this case.
- Case 3: When arbitrator tries to download the file from server, and same error occurs as highlighted by customer, then a refund is done to customer through smart contract by paying back the full deposited amount. In case, the arbitrator makes decision, that customer’s claim is right, and there is some fault or error, while downloading the file from IPFS.
5.3. Smart Contract Design
5.3.1. IPFS Storage Contract
//Add file
function addFile(bytes32 id, bool isVisible) public {
require(!blacklist[msg.sender] && FileMap[id].timestamp == 0);
.
.
.
emit confirmFileIndexID( FileList.length-1, id);
}
// File deletion
function deleteFile(uint index, bytes32 id, address[] memory addr) public {
.
.
.
FileList[index] = 0;
emit confirmFileDeletion( index, id);
}
//Search content
function setRecipients(bytes32 id, bytes32[] memory newShares) public {
.
.
.
for (uint j = 0; j < addr.length; j++) {
FileMap[id].recipients[ addr[j] ] = value;
}
}
5.3.2. Data Recipient Contract
// Deposit money
function DepositEtherToBuycontent() public payable {
.
.
.
emit DepositMoneyDone(msg.sender, "Money Deposited,
Customer Waiting for decrypted share"); //trigger event
}
5.3.3. Review System Contract
6. Implementation Details
6.1. Simulation Setup
Visual Studio Code
Ganache
Metamask
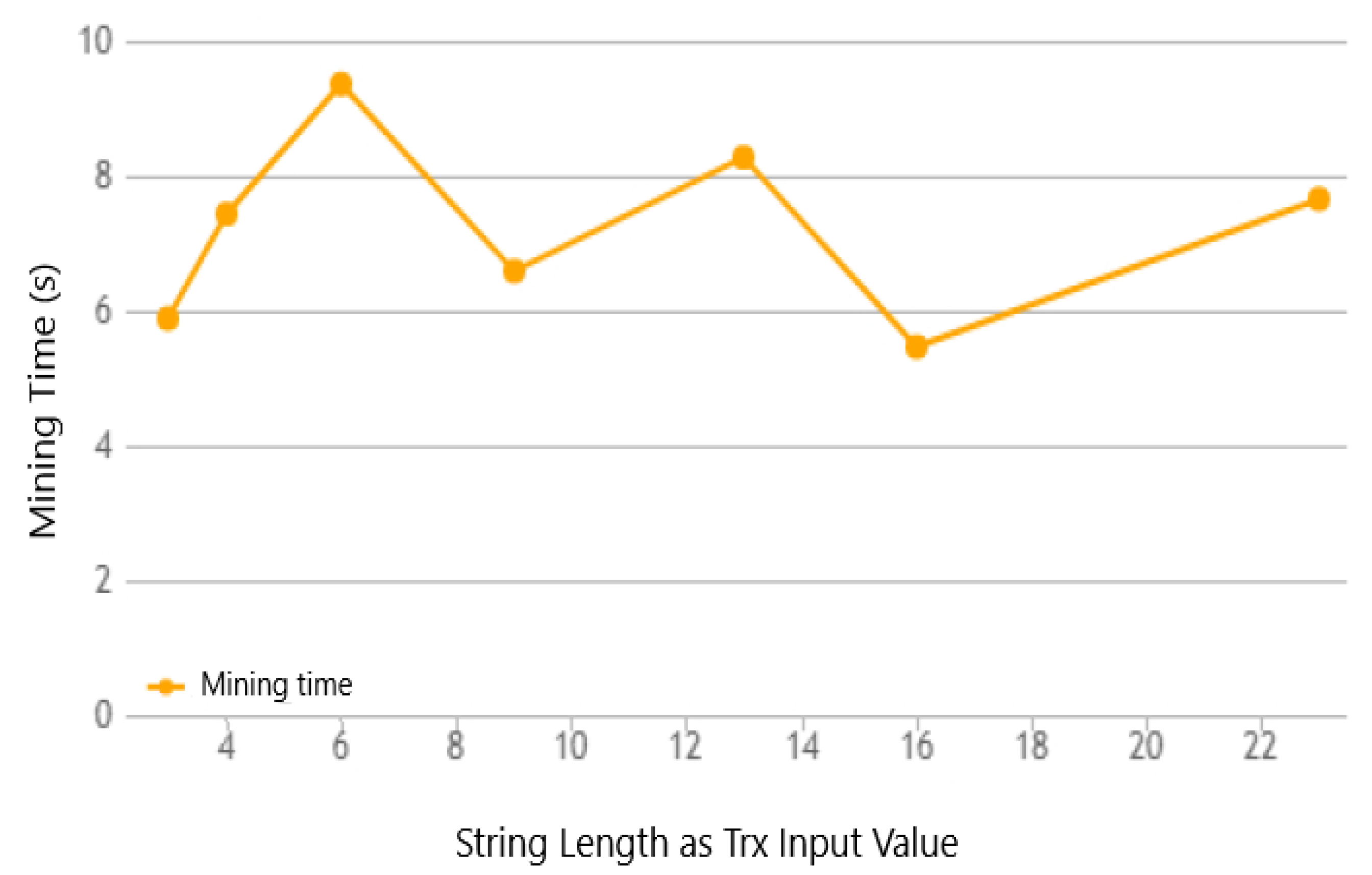
6.2. Simulation Results
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Shrestha, A.K.; Vassileva, J. Blockchain-Based Research Data Sharing Framework for Incentivizing the Data Owners. In International Conference on Blockchain; Springer: Cham, Switzerland, 2018; pp. 259–266. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: Https://bitco.in/pdf/bitcoin.pdf (accessed on 6 April 2019).
- Crosby, M.; Pattanayak, P.; Verma, S.; Kalyanaraman, V. Blockchain technology: Beyond bitcoin. Appl. Innov. 2016, 2, 71. [Google Scholar]
- Benet, J. Ipfs-content addressed, versioned, p2p file system. arXiv 2014, arXiv:1407.3561. [Google Scholar]
- Shamir, A. How to share a secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Wood, G. Ethereum: A secure decentralised generalised transaction ledger. Ethereum Proj. Yellow Pap. 2014, 151, 1–32. [Google Scholar]
- Hopwood, D.; Bowe, S.; Hornby, T.; Wilcox, N. Zcash Protocol Specification; GitHub: San Francisco, CA, USA, 2016. [Google Scholar]
- Wu, A.; Zhang, Y.; Zheng, X.; Guo, R.; Zhao, Q.; Zheng, D. Efficient and privacy-preserving traceable attribute-based encryption in blockchain. Ann. Telecommun. 2019, 74, 401–411. [Google Scholar] [CrossRef]
- Zhang, Z.; Zhao, L. A Design of Digital Rights Management Mechanism Based on Blockchain Technology. In International Conference on Blockchain; Springer: Cham, Switzerland, 2018; pp. 32–46. [Google Scholar]
- Ma, Z.; Jiang, M.; Gao, H.; Wang, Z. Blockchain for digital rights management. Future Gener. Comput. Syst. 2018, 89, 746–764. [Google Scholar] [CrossRef]
- Rowhani-Farid, A.; Allen, M.; Barnett, A.G. What incentives increase data sharing in health and medical research? A systematic review. Res. Integr. Peer Rev. 2017, 2, 4. [Google Scholar] [CrossRef]
- Zhu, L.; Wu, Y.; Gai, K.; Choo, K.K.R. Controllable and trustworthy blockchain-based cloud data management. Future Gener. Comput. Syst. 2019, 91, 527–535. [Google Scholar] [CrossRef]
- Li, J.; Wu, J.; Chen, L. Block-secure: Blockchain based scheme for secure P2P cloud storage. Inf. Sci. 2018, 465, 219–231. [Google Scholar] [CrossRef]
- Li, J.; Wang, X.; Huang, Z.; Wang, L.; Xiang, Y. Multi-level multi-secret sharing scheme for decentralized e-voting in cloud computing. J. Parallel Distrib. Comput. 2019, 130, 91–97. [Google Scholar] [CrossRef]
- Huang, Q.; Ma, Z.; Yang, Y.; Niu, X.; Fu, J. Attribute based DRM scheme with dynamic usage control in cloud computing. China Commun. 2014, 11, 50–63. [Google Scholar] [CrossRef]
- Sun, W.; Yu, S.; Lou, W.; Hou, Y.T.; Li, H. Protecting your right: Verifiable attribute-based keyword search with fine-grained owner-enforced search authorization in the cloud. IEEE Trans. Parallel Distrib. Syst. 2016, 27, 1187–1198. [Google Scholar] [CrossRef]
- Xia, Q.I.; Sifah, E.B.; Asamoah, K.O.; Gao, J.; Du, X.; Guizani, M. MeDShare: Trust-less medical data sharing among cloud service providers via blockchain. IEEE Access 2017, 5, 14757–14767. [Google Scholar] [CrossRef]
- Hammi, M.T.; Hammi, B.; Bellot, P.; Serhrouchni, A. Bubbles of Trust: A decentralized blockchain-based authentication system for IoT. Comput. Secur. 2018, 78, 126–142. [Google Scholar] [CrossRef]
- Liang, W.; Tang, M.; Long, J.; Peng, X.; Xu, J.; Li, K.C. A Secure Fabric Blockchain-based Data Transmission Technique for Industrial Internet-of-Things. IEEE Trans. Ind. Inform. 2019, 15, 358–3592. [Google Scholar] [CrossRef]
- Steichen, M.; Fiz Pontiveros, B.; Norvill, R.; Shbair, W. Blockchain-Based, Decentralized Access Control for IPFS. In Proceedings of the 2018 IEEE International Conference on Blockchain (Blockchain-2018), Halifax, NS, Canada, 30 July 2018–3 August 2018; pp. 1499–1506. [Google Scholar]
- Gaby, G.; Chandra, L.; Enderson, T. Towards Secure Interoperability between Heterogeneous Blockchains using Smart Contracts. In Proceedings of the Future Technologies Conference (FTC), Vancouver, BC, Canada, 15–16 November 2017; pp. 73–81. [Google Scholar]
- Dias, J.P.; Reis, L.; Ferreira, H.S.; Martins, Â. Blockchain for access control in e-health scenarios. arXiv 2018, arXiv:1805.12267. [Google Scholar]
- Fukumitsu, M.; Hasegawa, S.; Iwazaki, J.; Sakai, M.; Takahashi, D. A proposal of a secure P2P-type storage scheme by using the secret sharing and the blockchain. In Proceedings of the 2017 IEEE 31st International Conference on Advanced Information Networking and Applications (AINA), Taipei, Taiwan, 27–29 March 2017; pp. 803–810. [Google Scholar]
- Guo, R.; Shi, H.; Zhao, Q.; Zheng, D. Secure attribute-based signature scheme with multiple authorities for blockchain in electronic health records systems. IEEE Access 2018, 6, 11676–11686. [Google Scholar] [CrossRef]
- Nizamuddin, N.; Salah, K.; Azad, M.A.; Arshad, J.; Rehman, M.H. Decentralized document version control using ethereum blockchain and IPFS. Comput. Electr. Eng. 2019, 76, 183–197. [Google Scholar] [CrossRef]
- Agyekum, O.; Opuni-Boachie, K.; Xia, Q.; Sifah, E.B.; Gao, J.; Xia, H.; Du, X.; Guizani, M. A Secured Proxy-Based Data Sharing Module in IoT Environments Using Blockchain. Sensors 2019, 19, 1235. [Google Scholar] [CrossRef]
- Wang, S.; Zhang, Y.; Zhang, Y. A blockchain-based framework for data sharing with fine-grained access control in decentralized storage systems. IEEE Access 2018, 6, 38437–38450. [Google Scholar] [CrossRef]
- Panescu, A.T.; Manta, V. Smart Contracts for Research Data Rights Management over the Ethereum Blockchain Network. Sci. Technol. Libr. 2018, 37, 235–245. [Google Scholar] [CrossRef]
- Dai, M.; Zhang, S.; Wang, H.; Jin, S. A low storage room requirement framework for distributed ledger in blockchain. IEEE Access 2018, 6, 22970–22975. [Google Scholar] [CrossRef]
- Nizamuddin, N.; Hasan, H.; Salah, K.; Iqbal, R. Blockchain-Based Framework for Protecting Author Royalty of Digital Assets. Arab. J. Sci. Eng. 2019, 44, 3849–3866. [Google Scholar] [CrossRef]
- Hasan, H.R.; Salah, K. Proof of delivery of digital assets using blockchain and smart contracts. IEEE Access 2018, 6, 65439–65448. [Google Scholar] [CrossRef]
- Chen, Y.; Li, H.; Li, K.; Zhang, J. An improved P2P file system scheme based on IPFS and Blockchain. In Proceedings of the 2017 IEEE International Conference on Big Data (Big Data), Boston, MA, USA, 11–14 December 2017; pp. 2652–2657. [Google Scholar]
- Park, J.S.; Youn, T.Y.; Kim, H.B.; Rhee, K.H.; Shin, S.U. Smart contract-based review system for an IoT data marketplace. Sensors 2018, 18, 3577. [Google Scholar] [CrossRef]
- Truffle Suite. Available online: Https://truffleframework.com/tutorials/configuring-visual-studio-code (accessed on 23 April 2019).
- Truffle Suite. Available online: Https://truffleframework.com/docs/ganache/ overview (accessed on 23 April 2019).
- MetaMask. Available online: https://metamask.io/ (accessed on 23 April 2019).

| References | Blockchain | Data Encryption | IPFS | Reputation System | Access Control | Incentive | Review Validation | Dispute Handling |
|---|---|---|---|---|---|---|---|---|
| Base paper 1 [28] Base paper 2 [30] Base paper 3 [31] Base paper 4 [33] Proposed scenario | ✓ ✓ ✓ ✓ ✓ | ✗ ✗ ✗ ✗ ✓ | ✗ ✓ ✓ ✗ ✓ | ✗ ✗ ✗ ✓ ✓ | ✓ ✗ ✗ ✗ ✓ | ✗ ✓ ✓ ✗ ✓ | ✗ ✗ ✗ ✗ ✓ | ✗ ✓ ✓ ✗ ✓ |
| Functions | Transaction Gas | Execution Gas | Actual Cost (ether) |
|---|---|---|---|
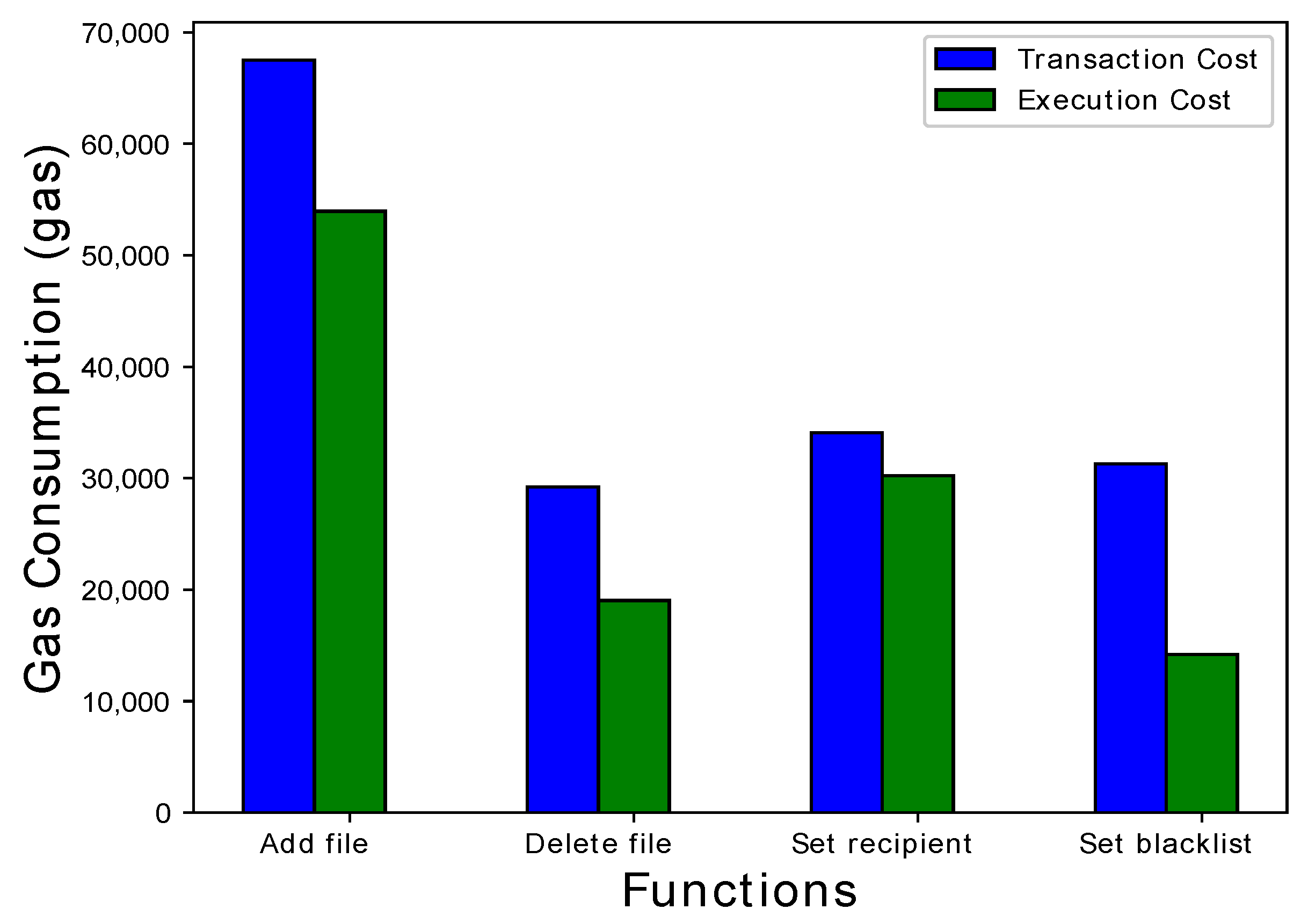
| Contract creation Add file Delete file Set receipient Set blacklist | 1,808,235 67,512 29,206 34,098 31,290 | 1,338,219 53,948 19,034 30,231 14,203 | 0.00361647 0.000107896 0.000058412 0.000060462 0.000028402 |
| Functions | Transaction Gas | Execution Gas | Actual Cost (ether) |
|---|---|---|---|
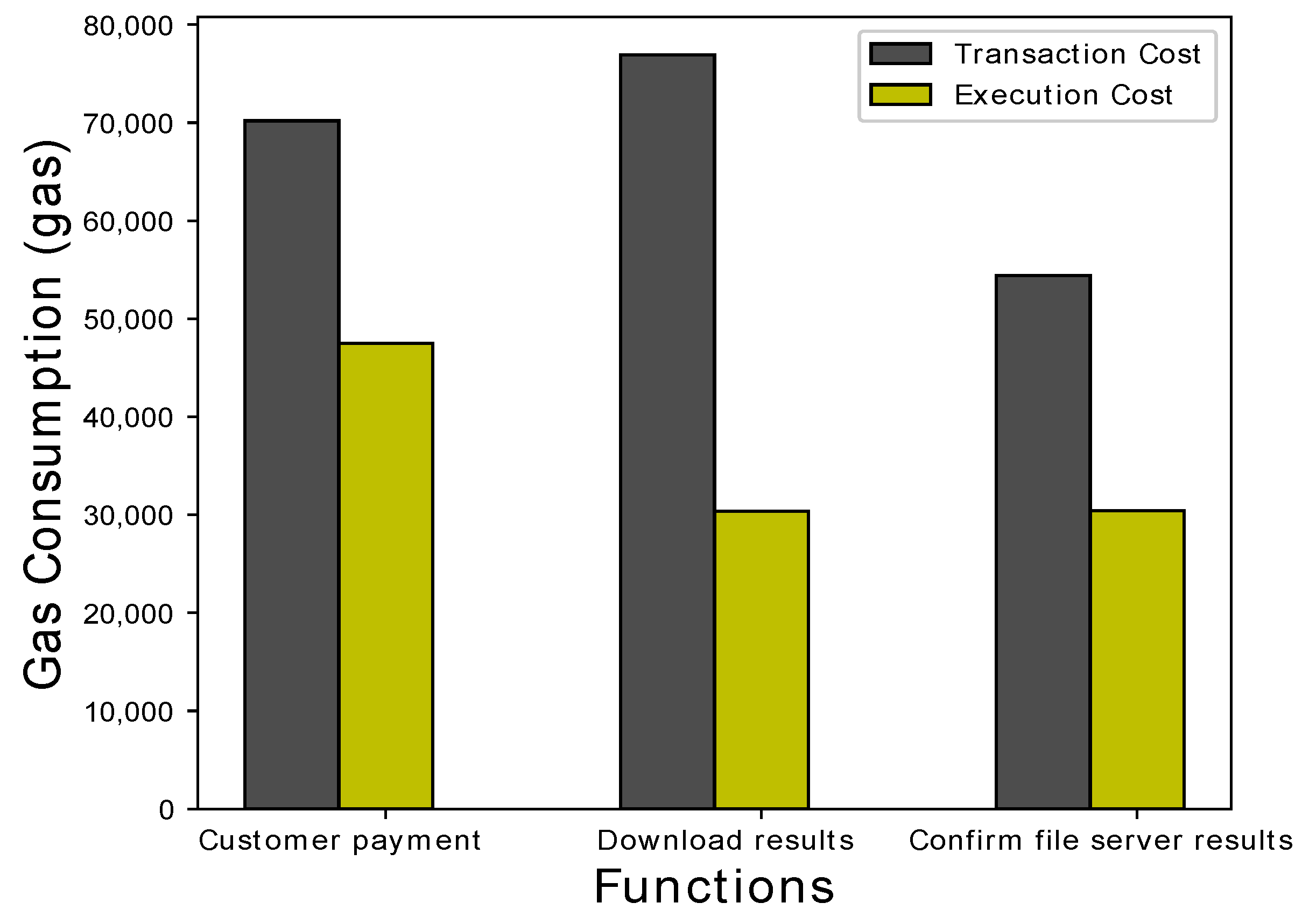
| Contract Creation Customer Payment Download Results Confirm fIle Server Results | 1,723,531 70,190 30,373 54,428 | 1,277,355 47,510 30,412 76,930 | 0.003447062 0.00014038 0.000060746 0.000108856 |
| Functions | Transaction Gas | Execution Gas | Actual Cost (ether) |
|---|---|---|---|
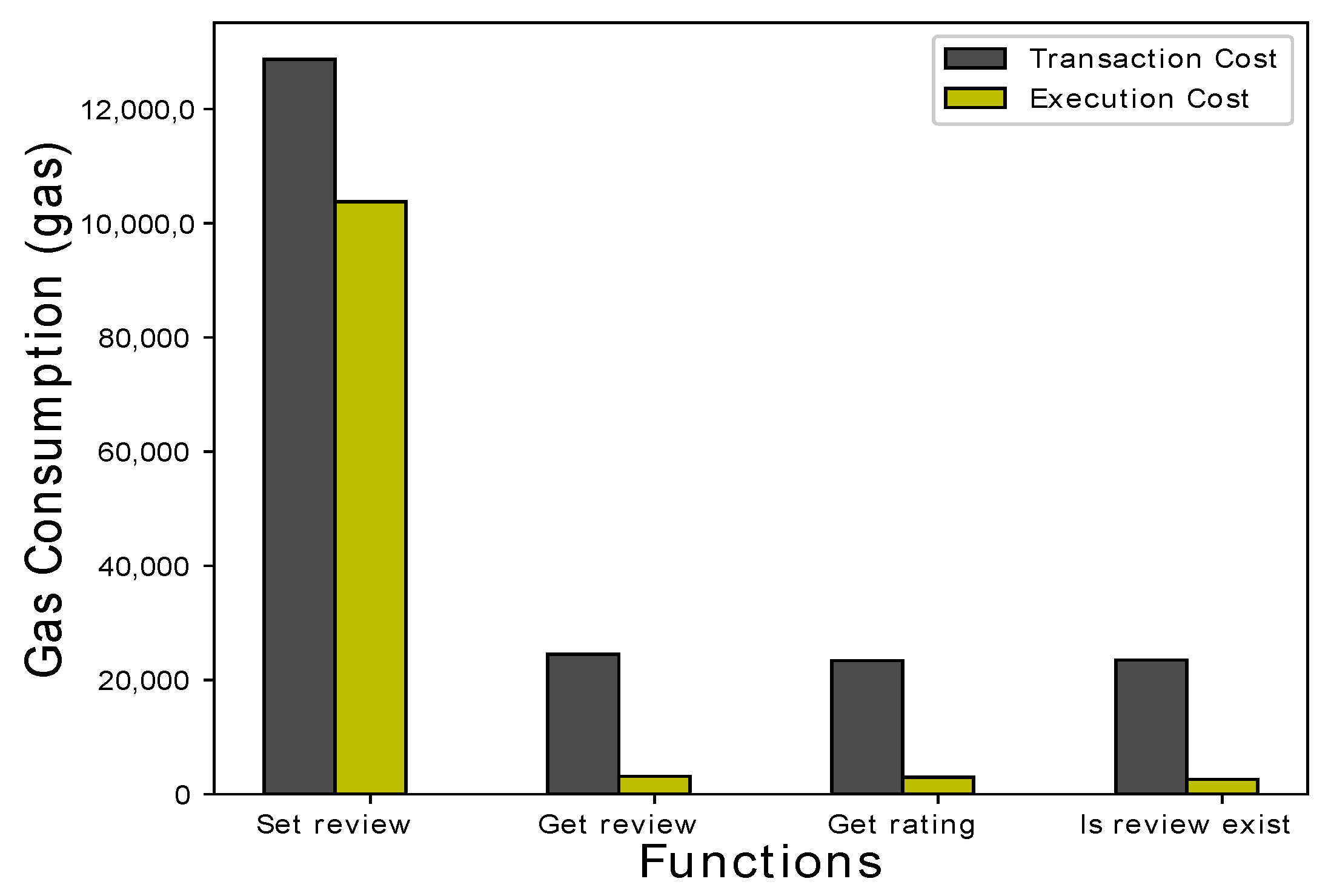
| Contract creation Set review Get review Get rating Does review exist | 673,317 128,705 23,364 23,470 - | 468,305 103,785 3106 2589 - | 0.001346 0.000257 0.000046 0.000046 - |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Naz, M.; Al-zahrani, F.A.; Khalid, R.; Javaid, N.; Qamar, A.M.; Afzal, M.K.; Shafiq, M. A Secure Data Sharing Platform Using Blockchain and Interplanetary File System. Sustainability 2019, 11, 7054. https://doi.org/10.3390/su11247054
Naz M, Al-zahrani FA, Khalid R, Javaid N, Qamar AM, Afzal MK, Shafiq M. A Secure Data Sharing Platform Using Blockchain and Interplanetary File System. Sustainability. 2019; 11(24):7054. https://doi.org/10.3390/su11247054
Chicago/Turabian StyleNaz, Muqaddas, Fahad A. Al-zahrani, Rabiya Khalid, Nadeem Javaid, Ali Mustafa Qamar, Muhammad Khalil Afzal, and Muhammad Shafiq. 2019. "A Secure Data Sharing Platform Using Blockchain and Interplanetary File System" Sustainability 11, no. 24: 7054. https://doi.org/10.3390/su11247054
APA StyleNaz, M., Al-zahrani, F. A., Khalid, R., Javaid, N., Qamar, A. M., Afzal, M. K., & Shafiq, M. (2019). A Secure Data Sharing Platform Using Blockchain and Interplanetary File System. Sustainability, 11(24), 7054. https://doi.org/10.3390/su11247054







