Dyn-Pri: A Dynamic Privacy Sensitivity Assessment Framework for V2G Interactive Service Scenarios
Abstract
1. Introduction
- (1)
- Three-Element Quantification Privacy Sensitivity Model: We decompose privacy sensitivity into (I) objective data attributes, (C) context-driven subjective risk, and (P) participant-experience-based subjective risk, quantifying each with dedicated indicators. Its novelty lies in the unification of objective and dual subjective factors.
- (2)
- Dynamic Intertwining Extension: We extend the static three-element model by explicitly capturing and learning the real-time, bidirectional influences among I, C, and P, replacing fixed weights with reinforcement learning-driven adaptive mappings. Its novelty lies in the explicit modeling of time-varying bidirectional effects.
- (3)
- Self-Optimizing Holistic Model: We integrate the intrinsic scores and learned intertwining effects into a single holistic score that self-optimizes across varying V2G scenarios, validated against four EV-user privacy profiles in four distinct V2G services across three operational scales, demonstrating superior accuracy and demand-side response support. Its novelty lies in the closed-loop, scenario-aware calibration.
2. Dyn-Pri: A Privacy Sensitivity Assessment Framework for V2G Interaction Service Scenarios
- I: The sharing data’s objective privacy sensitivity.
- C: The sharing data’s subjective privacy sensitivity related to the V2G service operational context.
- P: The sharing data’s subjective privacy sensitivity related to the privacy security experiences of V2G service participants.
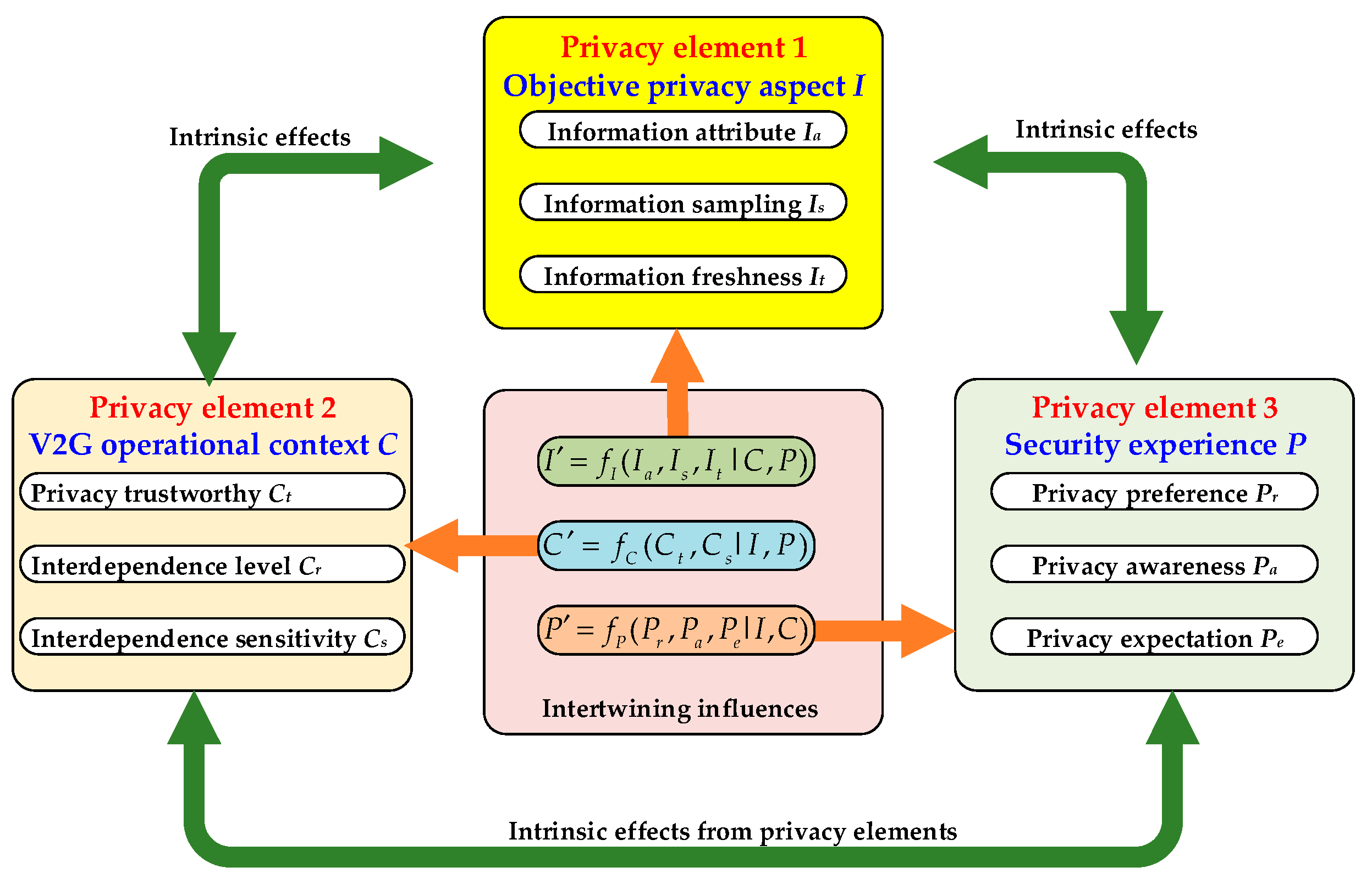
2.1. The Privacy Sensitivity Quantification Method Compounding the Respective Intrinsic Effects of Privacy Elements for V2G Interaction Service Scenarios
2.1.1. Objective Privacy Sensitivity of Sharing Information in V2G Interaction Service
2.1.2. Subjective Privacy Sensitivity Related to V2G Service Operational Context
2.1.3. Subjective Privacy Sensitivity Related to V2G Service Participants’ Security Experiences
2.2. The Dynamic Privacy Sensitivity Quantification Method Considered the Intertwining Influences Among Privacy Elements for V2G Interaction Service Scenarios
2.3. Dyn-Pri: A Holistic Privacy Sensitivity Assessment Model Integrating the Privacy Elements’ Intrinsic Effects with the Intertwining Influences Among Them
3. Experimental Validations and Analysis
3.1. The Experimental Validation Settings and the Related V2G Service Dataset
3.1.1. The Dataset Descriptions of V2G Service Case
3.1.2. The V2G Service Operator Settings
3.1.3. The V2G Service Settings of EV Users and Typical Interactive Services
3.1.4. The Default Hyper-Parameters of Reinforcement Learning During Dyn-Pri’s Self-Optimization
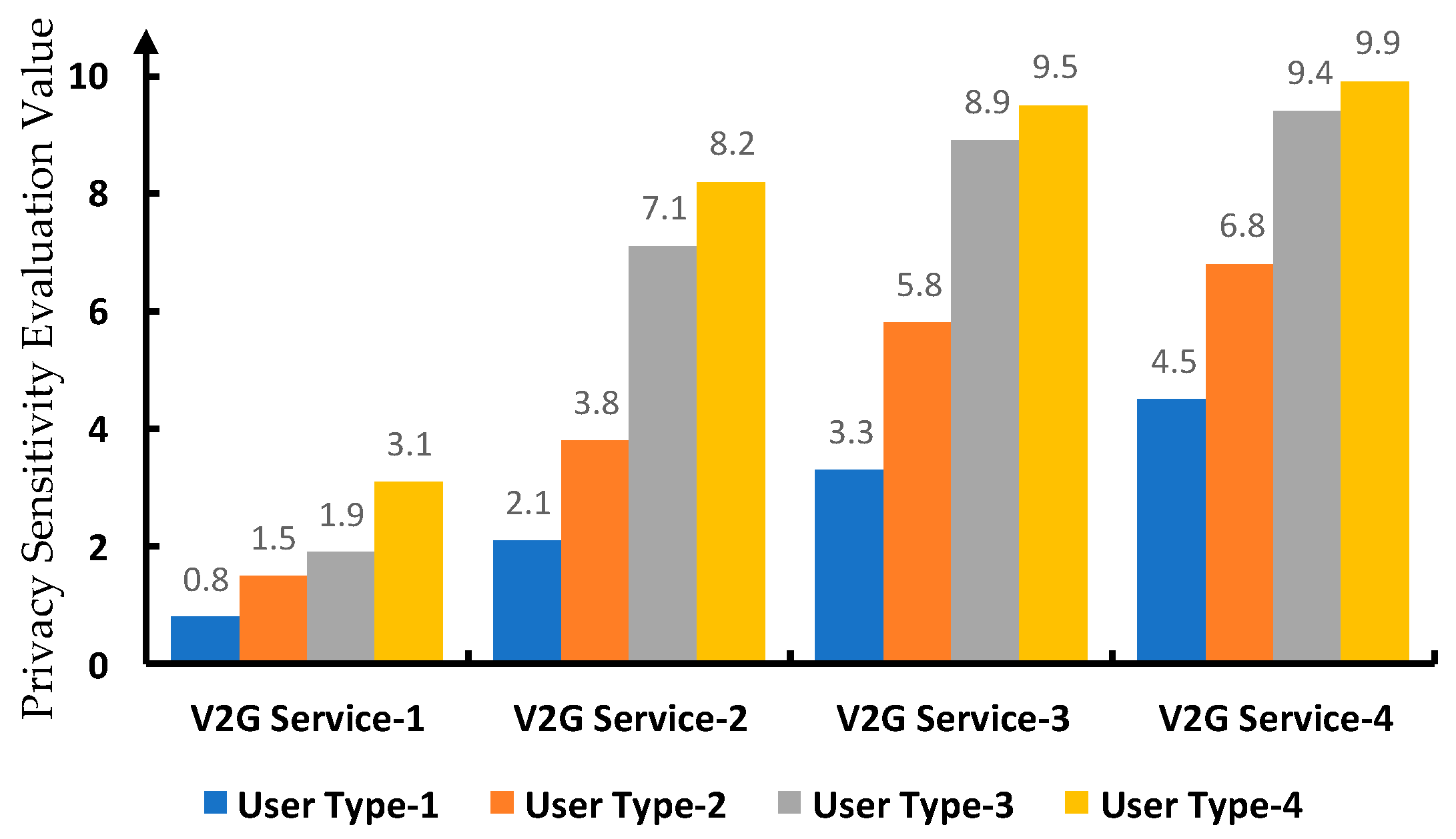
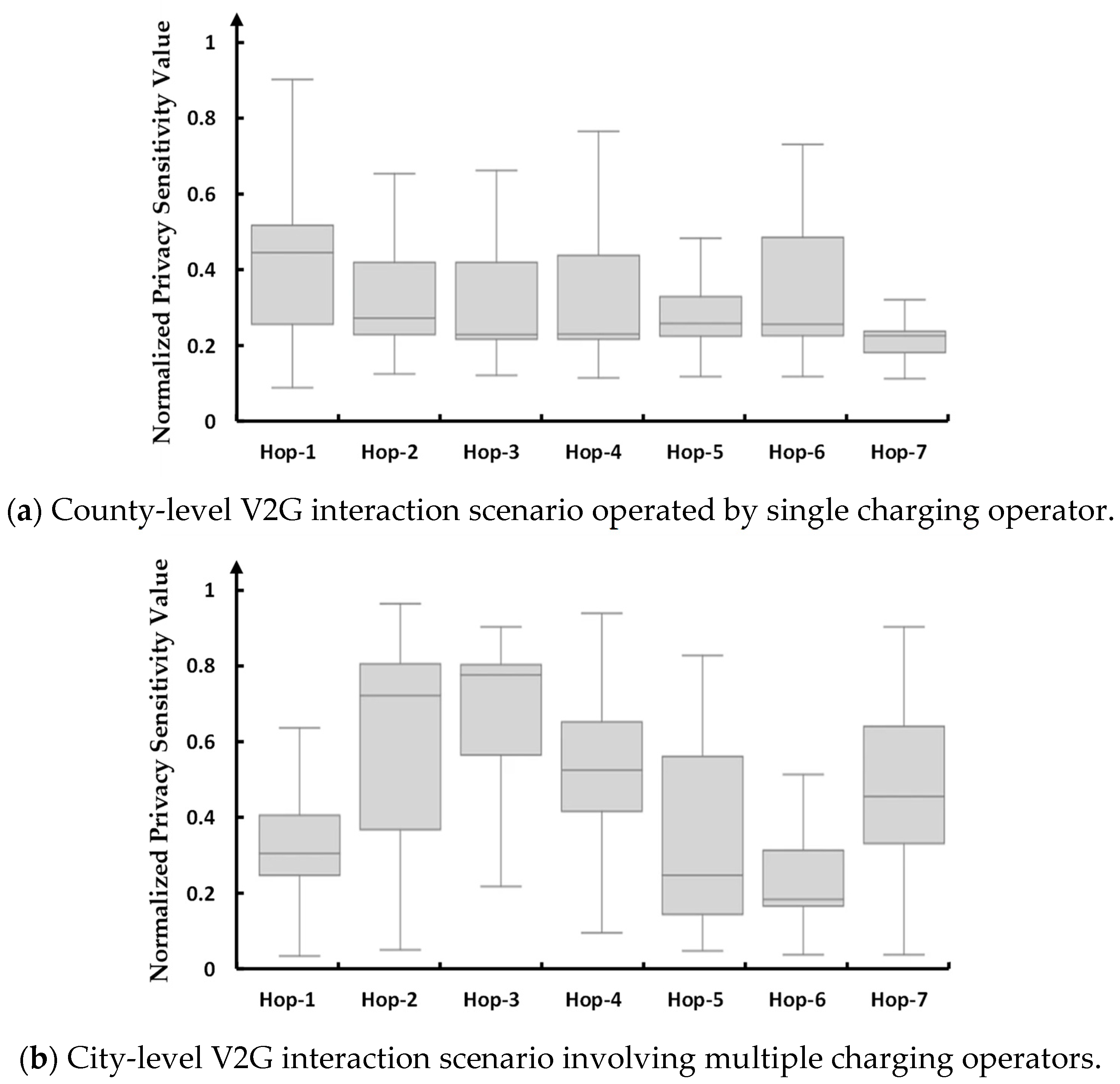
3.2. The Validations of the Dyn-Pri’s Fundamental Feasibility and Capability in Assessing the Privacy Sensitivity
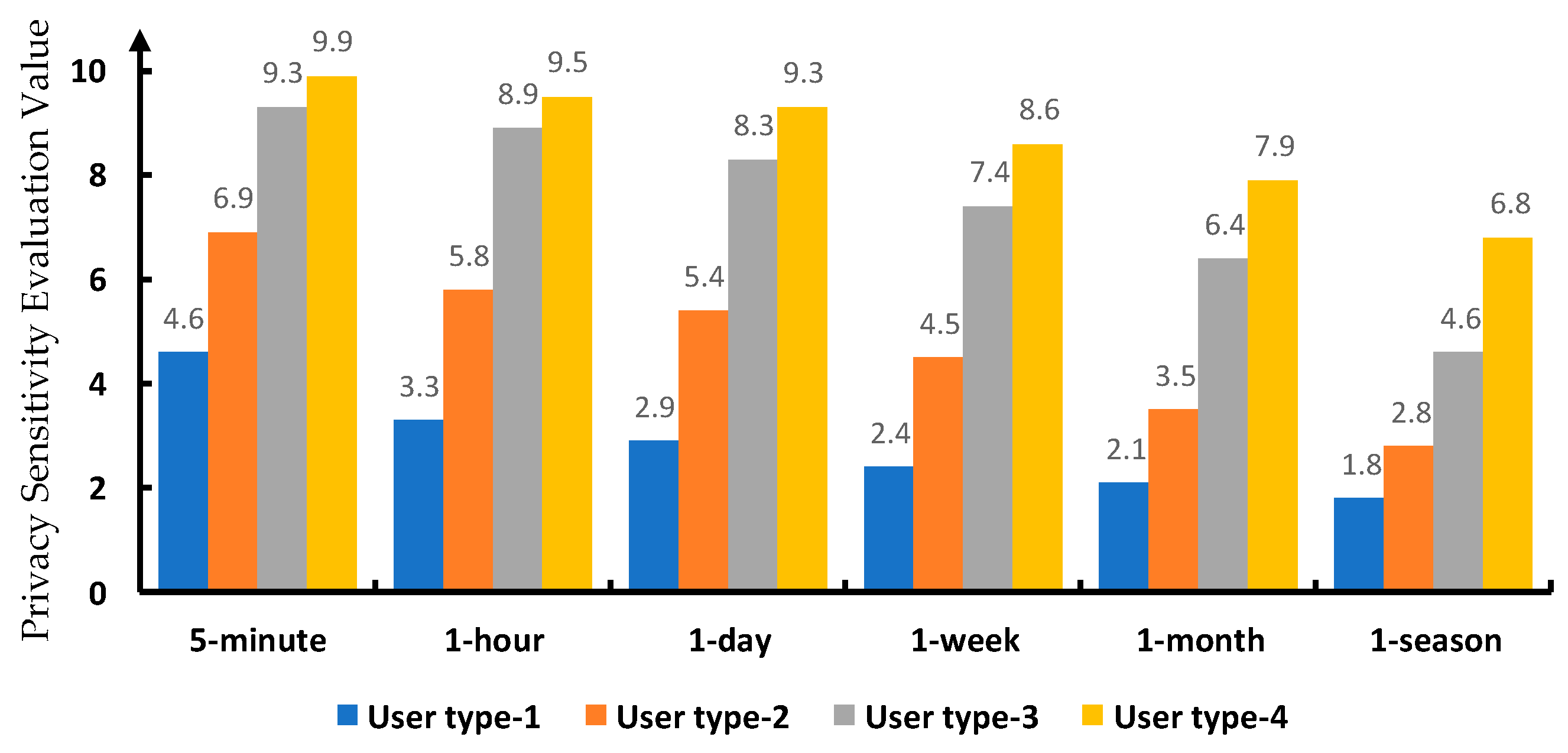
3.3. The Analysis of Impact Factors on Privacy Sensitivity Assessment of Dyn-Pri
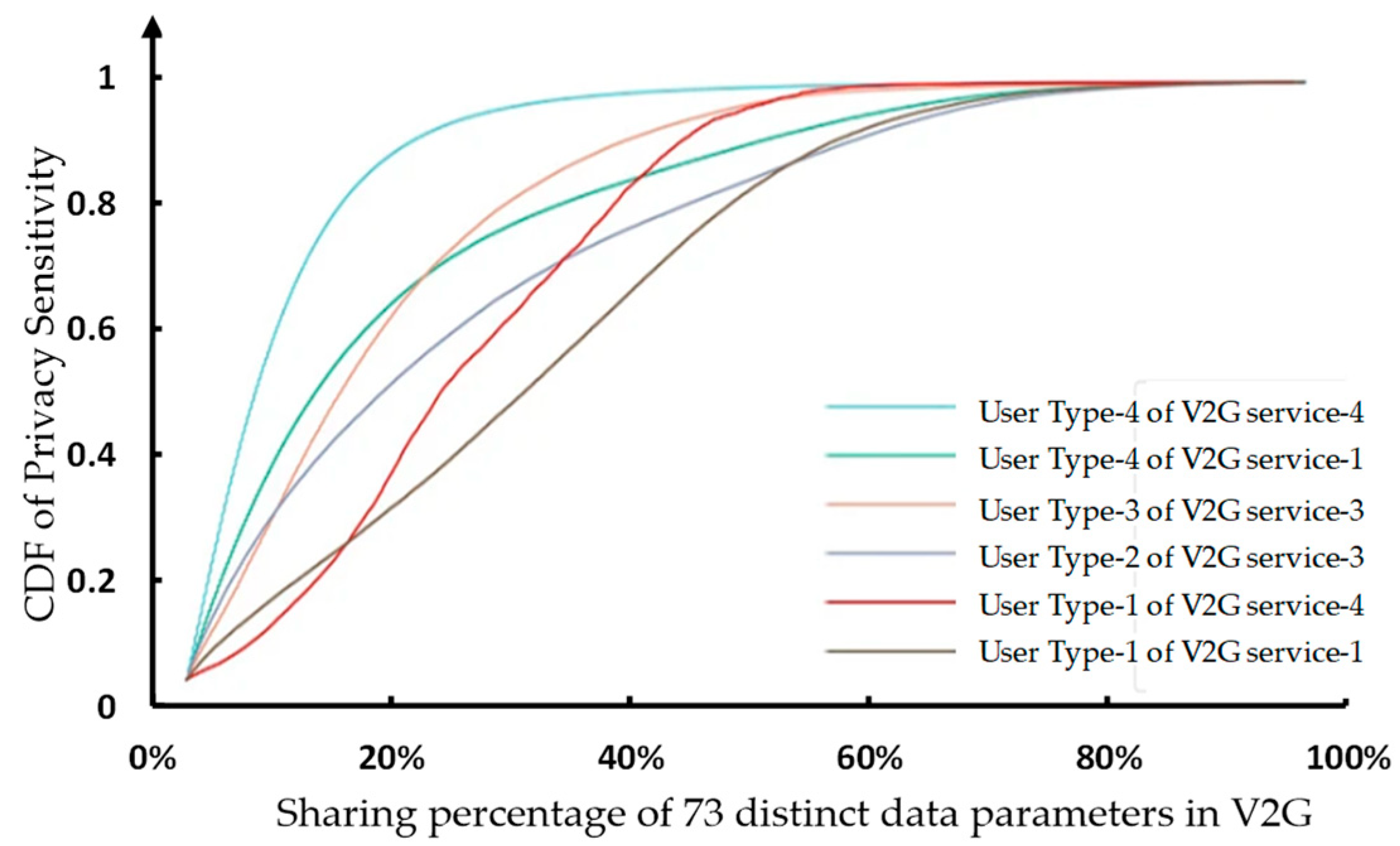
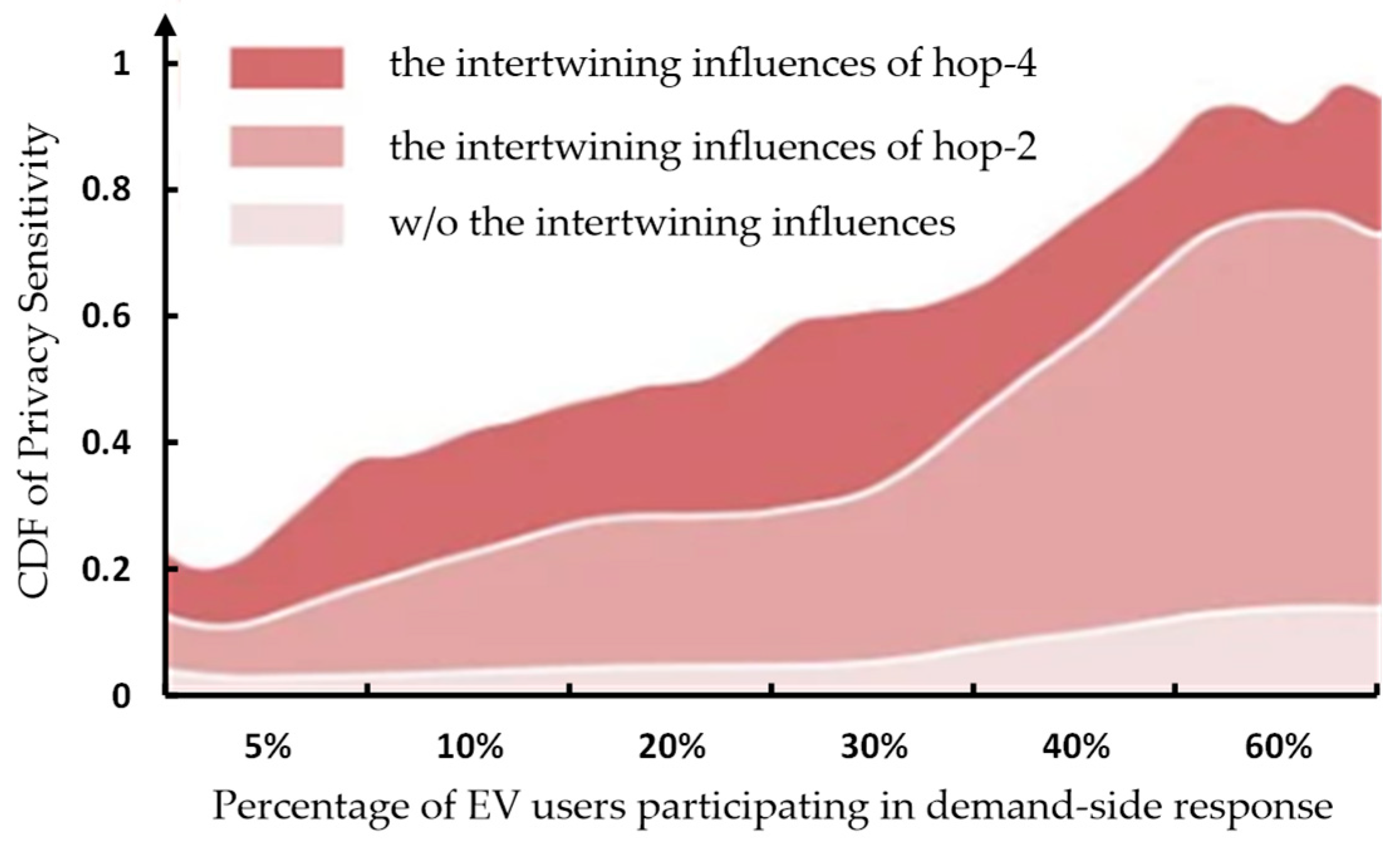
3.4. The Validations of Privacy Sensitivity Differentiation in the Intertwining Influences
3.5. The Computational Complexity Analysis of Dyn-Pri
4. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Li, Q.; Zhang, Y.; Chen, J. Development forms and challenges of ubiquitous power Internet of things. Autom. Electr. Power Syst. 2020, 44, 13–22. [Google Scholar]
- Zhang, Y.; Wang, A.; Zhang, H. Overview of smart grid development in China. Prot. Control Mod. Power Syst. 2021, 49, 180–187. [Google Scholar]
- Ren, Q.; Zhao, M.; Yang, X.; Tian, H.; Feng, H. Application of Canvas Fingerprint-Based Identity Authentication Technology in Smart Grid Data Security. In Proceedings of the 2024 4th International Conference on Blockchain Technology and Information Security (ICBCTIS), Wuhan, China, 17–19 August 2024. [Google Scholar]
- Nafees, M.N.; Saxena, N.; Cardenas, A.; Grijalva, S.; Burnap, P. Cardenas. Smart Grid Cyber-Physical Situational Awareness of Complex Operational Technology Attacks: A Review. ACM Comput. Surv. 2023, 55, 1–36. [Google Scholar] [CrossRef]
- Yang, W.; Guan, Z.; Wu, L. Secure Data Access Control With Fair Accountability in Smart Grid Data Sharing: An Edge Blockchain Approach. IEEE Internet Things J. 2021, 8, 8632–8643. [Google Scholar] [CrossRef]
- Wang, M.; Peng, C.; He, W. Differential privacy measurement model based on graph theory and mutual information. Comput. Sci. 2020, 47, 270–277. [Google Scholar]
- Mohan, S.N.; Ravikumar, G.; Govindarasu, M. Distributed Intrusion Detection System using Semantic-based Rules for SCADA in Smart Grid. In Proceedings of the IEEE/PES Transmission and Distribution Conference and Exposition (T&D), Chicago, IL, USA, 12–15 October 2020. [Google Scholar]
- Song, H.; Luo, T.; Li, J. Common Criterion of Privacy Metrics and Parameters Analysis Based on Error Probability for Randomized Response. IEEE Access 2019, 7, 16964–16978. [Google Scholar] [CrossRef]
- Zhao, K. Overview of the application of intelligent set in prediction system. CAAI Trans. Intell. Technol. 2022, 1–16. [Google Scholar]
- Presekal, A.; Ştefanov, A.; Semertzis, I.; Palensky, P. Spatio-Temporal Advanced Persistent Threat Detection and Correlation for Cyber-Physical Power Systems Using Enhanced GC-LSTM. IEEE Trans. Smart Grid 2025, 16, 1654–1666. [Google Scholar] [CrossRef]
- Rong, M.A.; Chen, X.; Liu, H. Research on User Privacy Measurement and Privacy Protection in Mobile Crowdsensing. Netinfo Secur. 2018, 18, 64–72. [Google Scholar]
- Huang, W.Q.; Xia, J.F.; Yu, M. Personal Privacy Metric based on Public Social Network Data. J. Phys.-Energy 2018, 1087, 032007. [Google Scholar] [CrossRef]
- Danesh Pazho, A.; Yao, S.; Alinezhad Noghre, G.; Rahimi Ardabili, B.; Katariya, V.; Tabkhi, H. Towards Adaptive Human-centric Video Anomaly Detection: A Comprehensive Framework and A New Benchmark. arXiv 2024, arXiv:2408.14329. [Google Scholar]
- Wang, W.; Ma, W.; Yan, K. Trust-aware privacy-preserving QoS prediction with graph neural collaborative filtering for internet of things services. Complex Intell. Syst. 2025, 11, 191. [Google Scholar] [CrossRef]
- Li, H.; Kumar, N.; Chen, R. Deep Reinforcement Learning. In Proceedings of the 2018 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Calgary, AB, Canada, 17 April 2018. [Google Scholar]
- Papageorgiou, E.; Theodoropoulos, T.; Tserpes, K. Energy-Efficient Task Offloading in Edge Computing: A Survey of Deep Reinforcement Learning Approaches. In Proceedings of the International Conference on the Economics of Grids, Clouds, Systems, and Services; Springer: Cham, Switzerland, 2025. [Google Scholar]
- Li, H.; Qu, H.; Tan, X.; You, L.; Zhu, R.; Fan, W. UrbanEV: An Open Benchmark Dataset for Urban Electric Vehicle Charging Demand Prediction. Sci. Data 2025, 12, 523. [Google Scholar] [CrossRef] [PubMed]
- GB/T 32960.3-2016; Technical Specifications of Remote Service and Management System for EVs-Part 3: Communication Protocol and Data Format. China National Standard: Beijing, China, 2016.


Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Published by MDPI on behalf of the World Electric Vehicle Association. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, T.; Wang, J.; Zhang, N.; Guo, J.; Tao, Y.; Li, Q.; Li, Z. Dyn-Pri: A Dynamic Privacy Sensitivity Assessment Framework for V2G Interactive Service Scenarios. World Electr. Veh. J. 2025, 16, 459. https://doi.org/10.3390/wevj16080459
Liu T, Wang J, Zhang N, Guo J, Tao Y, Li Q, Li Z. Dyn-Pri: A Dynamic Privacy Sensitivity Assessment Framework for V2G Interactive Service Scenarios. World Electric Vehicle Journal. 2025; 16(8):459. https://doi.org/10.3390/wevj16080459
Chicago/Turabian StyleLiu, Tianbao, Jingyang Wang, Nan Zhang, Jing Guo, Yanyan Tao, Qingyao Li, and Zi Li. 2025. "Dyn-Pri: A Dynamic Privacy Sensitivity Assessment Framework for V2G Interactive Service Scenarios" World Electric Vehicle Journal 16, no. 8: 459. https://doi.org/10.3390/wevj16080459
APA StyleLiu, T., Wang, J., Zhang, N., Guo, J., Tao, Y., Li, Q., & Li, Z. (2025). Dyn-Pri: A Dynamic Privacy Sensitivity Assessment Framework for V2G Interactive Service Scenarios. World Electric Vehicle Journal, 16(8), 459. https://doi.org/10.3390/wevj16080459




