Secure Context-Aware Traffic Light Scheduling System: Integrity of Vehicles’ Identities
Abstract
1. Introduction
2. Related Work
2.1. Context-Aware Traffic Light Scheduling Algorithms
2.2. Secure Traffic Light Scheduling Algorithms
3. The Possible Attacks in the Context-Aware Traffic Light Scheduling Systems and Threat Models
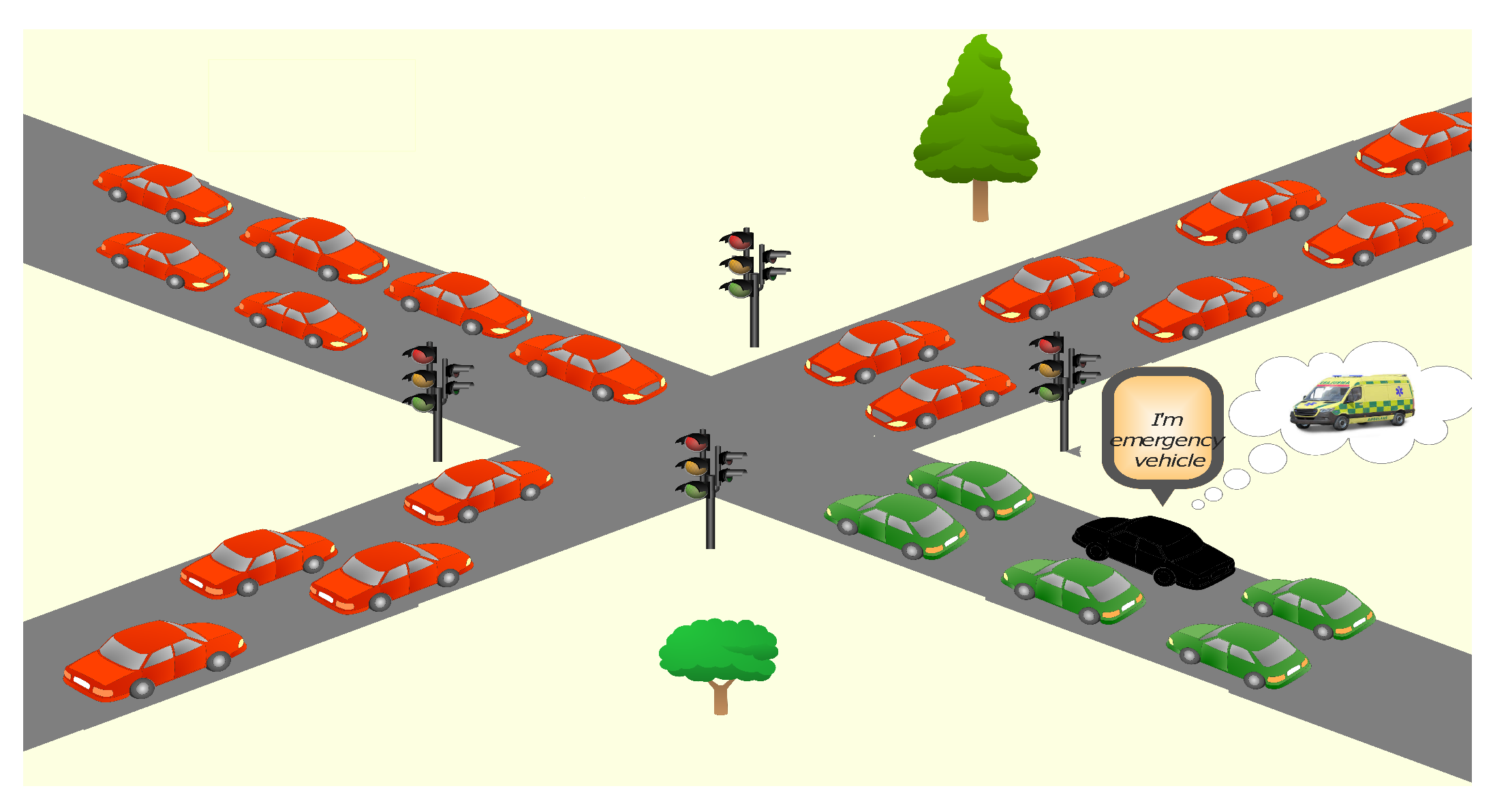
- Vehicles on the same traffic flow as the attacker vehicle can take advantage of the attack. They are scheduled to pass the intersection fast with the fake emergency vehicle announced. Thus, we can call these vehicles innocent beneficiaries (i.e., gainers); they are colored green in Figure 1.
- Vehicles on the other flows will be negatively affected by the attack (i.e., victims). They will have to wait for the traffic flow that contains the fake emergency vehicle to pass through the intersection. These vehicles are colored red in Figure 1.
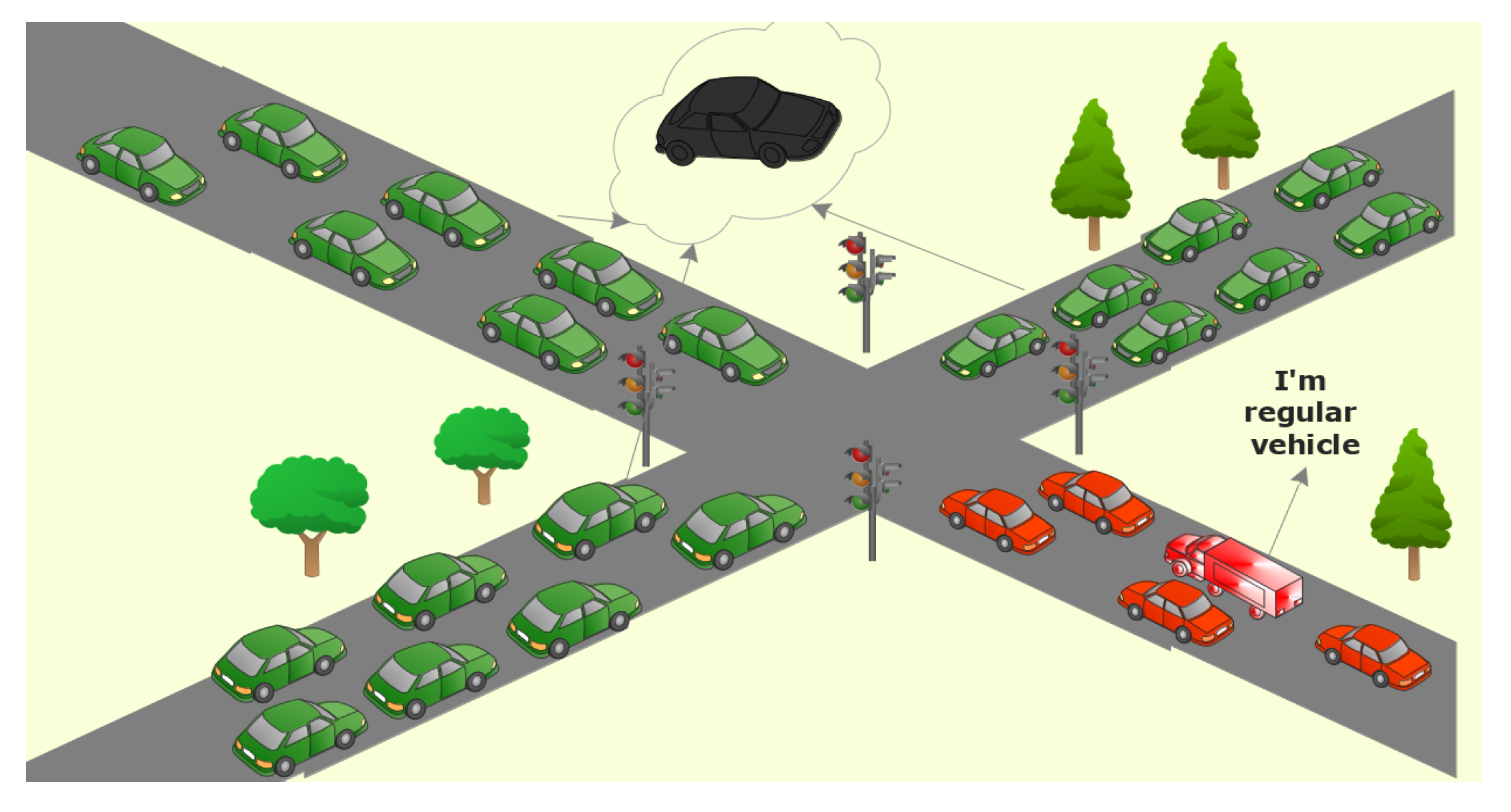
- Vehicles on the other side of the emergency vehicle can take advantage of the attack. They are scheduled to pass the intersection quickly due to the denial of emergency vehicles. Thus, these vehicles are the gainers of this attack; they are colored green in Figure 2. One of these vehicles may be the initiator of this type of attack.
- Vehicles on the same traffic flow will be negatively affected by the attack (i.e., victims). These vehicles are red in Figure 2.
4. Secure Context-Aware Traffic Light Scheduling System
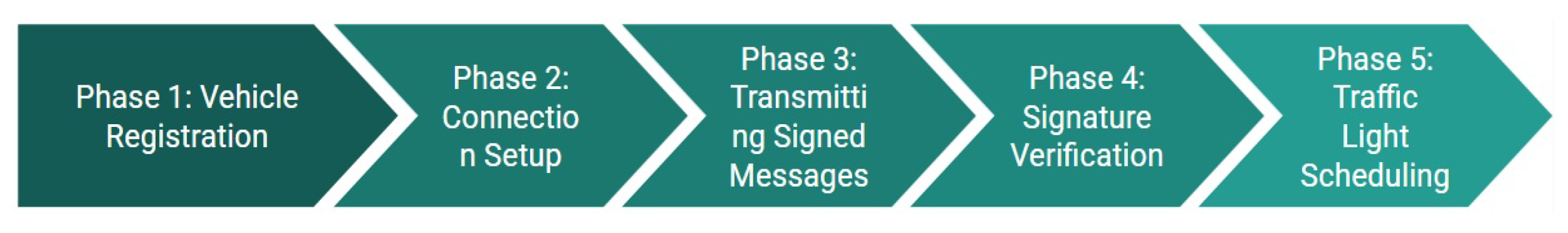
- Phase 1: Vehicle Registration
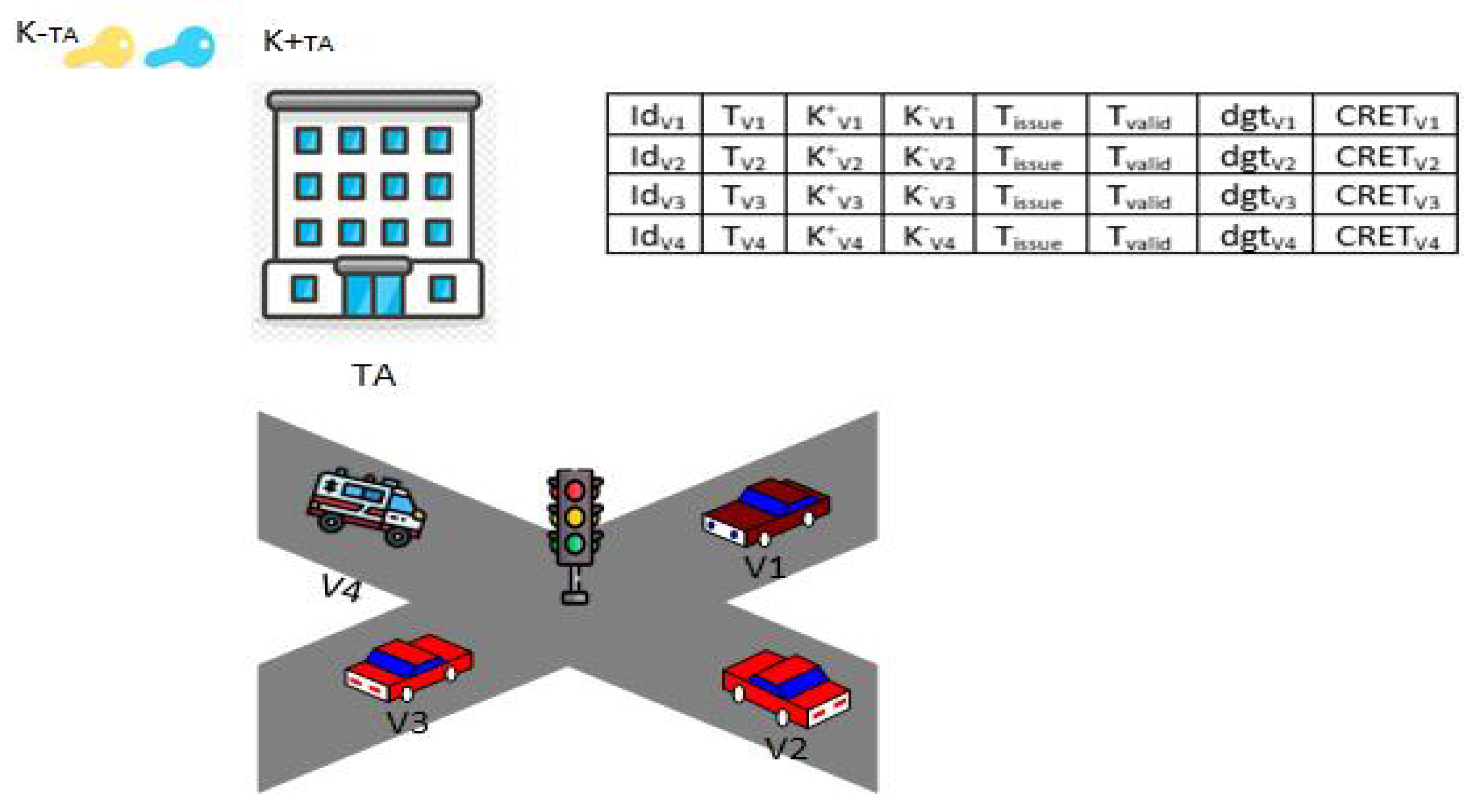
- All vehicles on the road network should be registered with a certain traffic authority (TA). This is centrally run by the government. Each vehicle should be assigned a unique identifier to be distinguished and tracked over the road network. Its type (), if it is an ambulance, fire truck, police, or regular vehicle, should also be identified inside the associated database of the TA.
- Generation of cryptographic keys: The traffic authority (TA) produces a distinct ECDSA key pair which includes a public key () and private key () for every registered vehicle, using Cryptographically Secure Pseudorandom Number Generation (CSPRNG) [36].
- Message Digest: The generated message should be hashed using an efficient and secure function such as SHA-2 [34]. This is to create a message digest for that vehicle that could be added to any message and prove the identities of vehicles. This includes the vehicle identification , emergency type , public key , issuing date/time (, and validity period . Equation (1) computes the message digest used to sign messages efficiently.
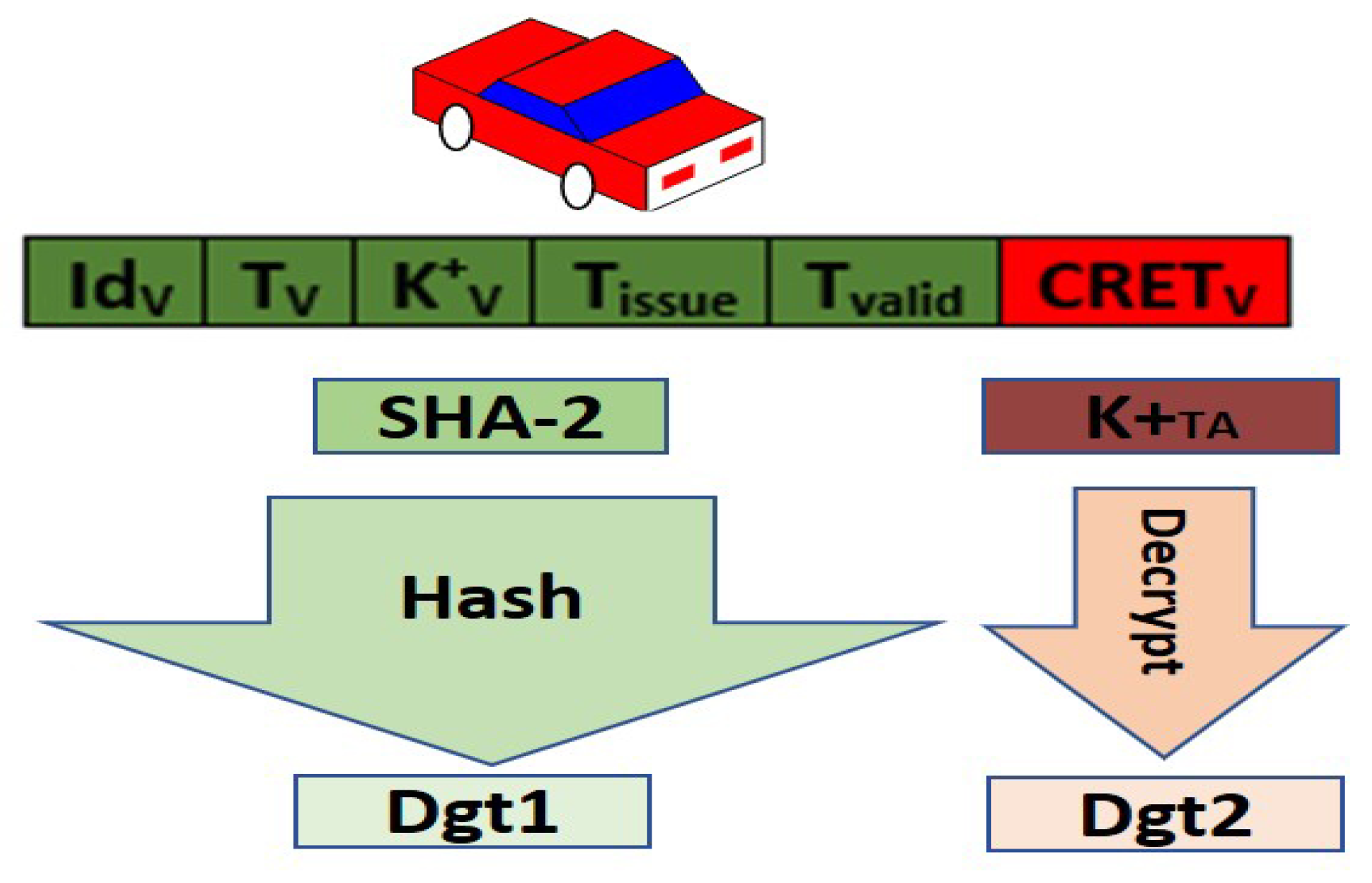
- Certificate generation: The TA generates a digital certificate () that is encrypted by the private key of that TA () for every vehicle. The is used to be encrypted by the private key of the TA. Equation (2) illustrates how to generate the certificate of each vehicle v inside the TA. The private key is known by the assigned vehicle, and it remains secure within the TA and connected to that .
- Phase 2: Connection Setup
- Phase 3: Transmitting Signed Messages.
- Message Creation: Based on the target and mission of each message, its fields are selected accordingly. For example, periodic “hello” messages contain , , , , etc. Traffic report messages contain the covered area, traffic speed, traffic density, etc. Other data announcing and gathering messages can be created and sent according to the running protocol’s targets and procedures.
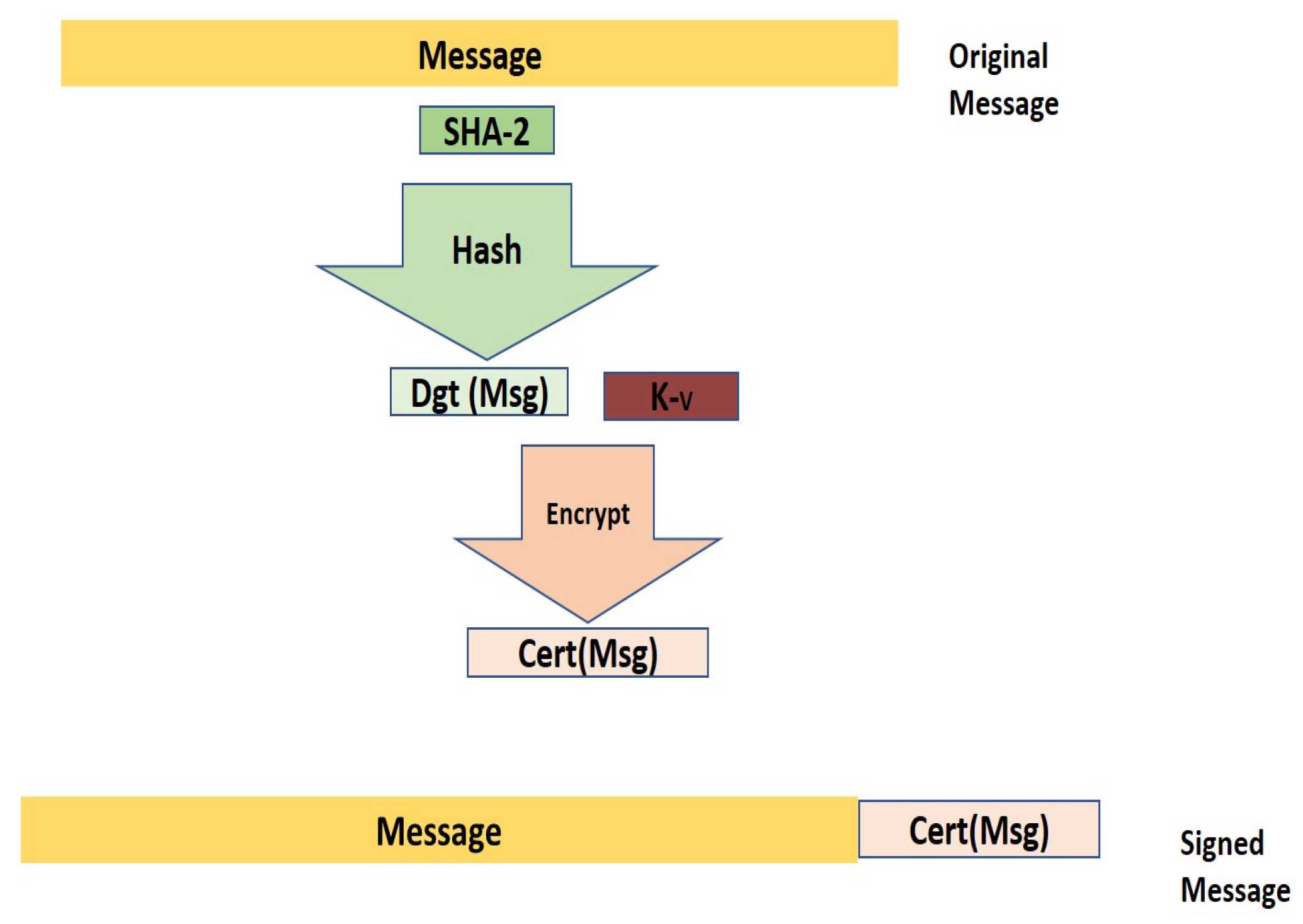
- Sign the Message: The ShA-2 hashing algorithm is used to generate a message digest for that message ()). Then, the private key of the sender vehicle () is used to create a message certificate () by encrypting the . The latter certificate ensures that this vehicle initiates that message and other fields of the message have not been manipulated by other users or attackers. Using the hashing algorithm before encrypting the data reduces its size; thus, it reduces the time complexity for the encryption and decryption processes.The value of is added as a signature at the end of the original message. It is mainly used to verify the content of the message and the identity of its initiator. Figure 6 graphically illustrates the steps and techniques of signing a message.
- Phase 4: Signature Verification
- Phase 5: Traffic Light Scheduling
4.1. The Computational and Message Overhead Complexity
4.1.1. Computational Overhead
4.1.2. Message Overhead (Signature Size)
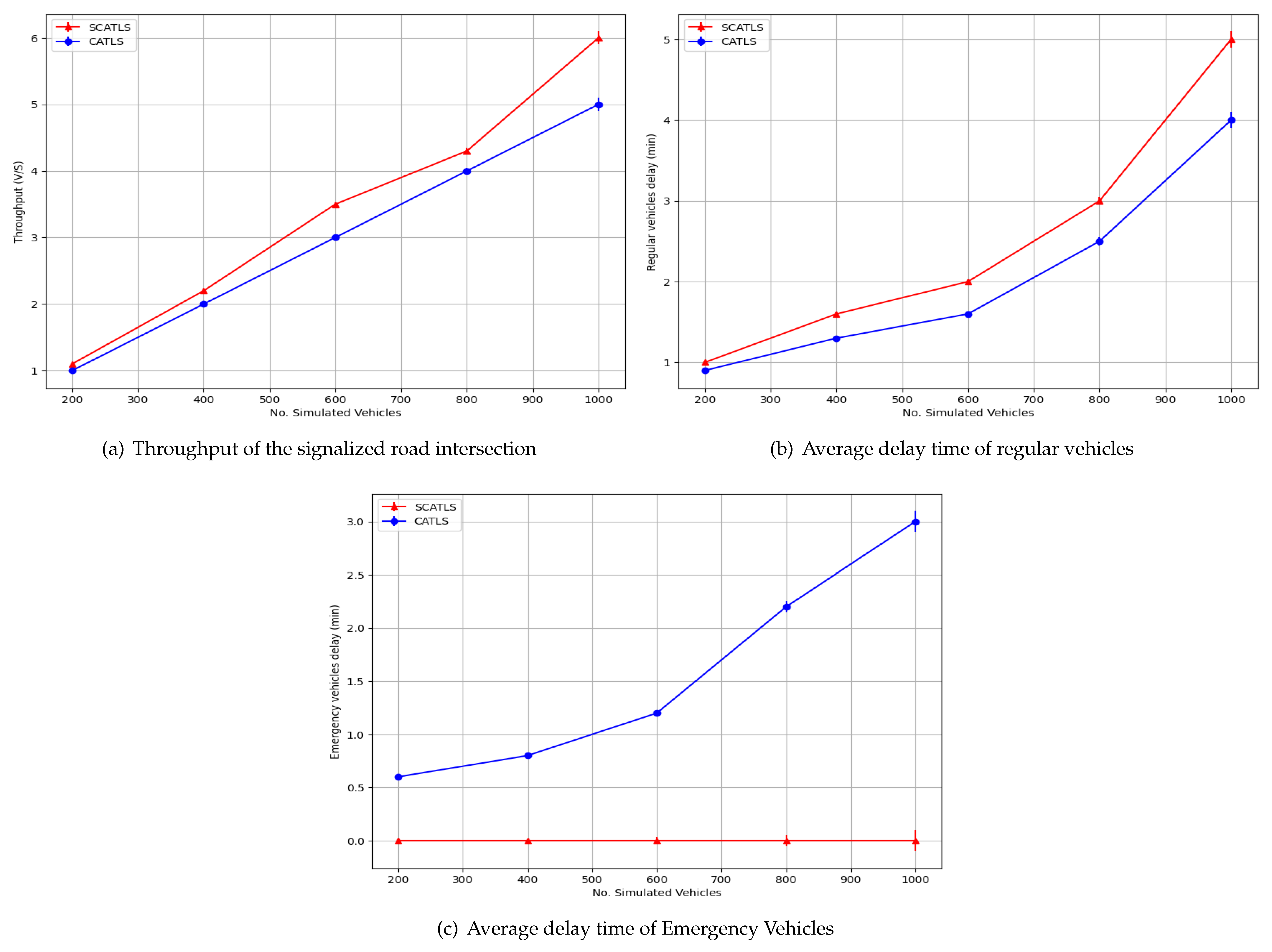
5. Performance Evaluation
5.1. Impersonation Attack
5.2. Modification Attack
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Macías-Escrivá, F.D.; Haber, R.; Del Toro, R.; Hernandez, V. Self-adaptive systems: A survey of current approaches, research challenges, and applications. Expert Syst. Appl. 2013, 40, 7267–7279. [Google Scholar]
- Younes, M.B.; Boukerche, A.; Mammeri, A. Context-aware traffic light self-scheduling algorithm for intelligent transportation systems. In Proceedings of the 2016 IEEE Wireless Communications and Networking Conference, Doha, Qatar, 3–6 April 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Younes, M.B.; Boukerche, A. An efficient dynamic traffic light scheduling algorithm considering emergency vehicles for intelligent transportation systems. Wirel. Netw. 2018, 24, 2451–2463. [Google Scholar]
- Alqarqaz, M.; Bani Younes, M.; Qaddoura, R. An object classification approach for autonomous vehicles using machine learning techniques. World Electr. Veh. J. 2023, 14, 41. [Google Scholar]
- Younes, M.B.; Roman Alonso, G.; Boukerche, A. A distributed infrastructure-based congestion avoidance protocol for vehicular ad hoc networks. In Proceedings of the 2012 IEEE Global Communications Conference (GLOBECOM), Anaheim, CA, USA, 3–7 December 2012; IEEE: New York, NY, USA, 2012; pp. 73–78. [Google Scholar]
- Barba, C.T.; Mateos, M.A.; Soto, P.R.; Mezher, A.M.; Igartua, M.A. Smart city for VANETs using warning messages, traffic statistics and intelligent traffic lights. In Proceedings of the 2012 IEEE intelligent vehicles symposium, Madrid, Spain, 3–7 June 2012; IEEE: New York, NY, USA, 2012; pp. 902–907. [Google Scholar]
- Mahalakshmi, V.; Karthikeyana, B. Context-aware acquisition module (CAAM) using Road Side Unit (RSU) to Vehicle unicast communication for Intelligent transport systems in edge computing. Elsevier (ssrn): Amesterdam, The Netherlands, 2024; Preprint submitted. [Google Scholar]
- Younes, M.B.; Boukerche, A. A performance evaluation of a context-aware path recommendation protocol for vehicular ad-hoc networks. In Proceedings of the 2013 IEEE Global Communications Conference (GLOBECOM), Atlanta, GA, USA, 9–13 December 2013; IEEE: New York, NY, USA, 2013; pp. 516–521. [Google Scholar]
- Dzemydienė, D.; Burinskienė, A. Integration of context awareness in smart service provision system based on wireless sensor networks for sustainable cargo transportation. Sensors 2021, 21, 5140. [Google Scholar]
- Pavlin, G.; Boudreault, R.; Penders, A.; Lafond, D.; de Graaf, M.; Swiebel, A. Extracting actionable information from heterogeneous sensors in the field: A distributed hybrid AI approach in constrained domains. In Proceedings of the Conference: 2023 Ground Vehicle Systems Engineering and Technology Symposium, GVSETS, Novi, MI, USA, 15–17 August 2023. [Google Scholar]
- De Amicis, R.; Conti, G.; Piffer, S.; Prandi, F. Service oriented computing for ambient intelligence to support management of transport infrastructures. J. Ambient. Intell. Humaniz. Comput. 2011, 2, 201–211. [Google Scholar]
- Grimm, D.; Stang, M.; Sax, E. Context-aware security for vehicles and fleets: A survey. IEEE Access 2021, 9, 101809–101846. [Google Scholar]
- Dzemydienė, D.; Burinskienė, A.; Miliauskas, A. Integration of multi-criteria decision support with infrastructure of smart services for sustainable multi-modal transportation of freights. Sustainability 2021, 13, 4675. [Google Scholar]
- Sattar, F.; Karray, F.; Kamel, M.; Nassar, L.; Golestan, K. Recent advances on context-awareness and data/information fusion in ITS. Int. J. Intell. Transp. Syst. Res. 2016, 14, 1–19. [Google Scholar]
- He, Z.; Zhang, D. Cost-efficient traffic-aware data collection protocol in VANET. Ad Hoc Netw. 2017, 55, 28–39. [Google Scholar]
- Wu, Q.; Zhu, M.; Rao, N.S.V. Integration of sensing and computing in an intelligent decision support system for homeland security defense. Pervasive Mob. Comput. 2009, 5, 182–200. [Google Scholar]
- Dzemydiene, D.; Dzindzalieta, R. Multi-Layered Architecture of Decision Support System for Monitoring of Dangerous Good Transportation. In DB&Local Proceedings; 2012; pp. 128–141. Available online: https://cris.mruni.eu/cris/entities/publication/76488d8b-376b-4016-b90a-e268e6bfa83b (accessed on 5 July 2025).
- Younes, M.B.; Boukerche, A. SCOOL: A secure traffic congestion control protocol for VANETs. In Proceedings of the 2015 IEEE Wireless Communications and Networking Conference (WCNC), New Orleans, LA, USA, 9–12 March 2015; IEEE: New York, NY, USA, 2015; pp. 1960–1965. [Google Scholar]
- Dzemydienė, D. Development of intelligent service system for multimodal transport management. In Development of Smart Context-Aware Services for Cargo Transportation: An Operational Management Approach; Springer International Publishing: Cham, Switzerland, 2022; pp. 371–403. [Google Scholar]
- Rashwan, A.M. Context-Aware and Real-Time Entrustment Framework for Securing Next Generation Internet Communications. Ph.D. Thesis, Queen’s University, Kingston, ON, Canada, 2018. [Google Scholar]
- Pathre, A.; Agrawal, C.; Jain, A. A novel defense scheme against DDOS attack in VANET. In Proceedings of the 2013 Tenth International Conference on Wireless and Optical Communications Networks (WOCN), Bhopal, India, 26–28 July 2013; IEEE: New York, NY, USA, 2013; pp. 1–5. [Google Scholar]
- Sylla, T.; Chalouf, M.A.; Mendiboure, L.; Krief, F. Context-Aware Security and Privacy as a Service for the Connected and Autonomous Vehicle. In Cooperative Intelligent Transport Systems: Control and Management; ISTE Ltd.: London, UK, 2024; p. 295. [Google Scholar]
- Bermad, N.; Zemmoudj, S.; Omar, M. Context-aware negotiation, reputation and priority traffic light management protocols for VANET-based smart cities. Telecommun. Syst. 2019, 72, 131–153. [Google Scholar]
- Aleko, D.R.; Djahel, S. An efficient adaptive traffic light control system for urban road traffic congestion reduction in smart cities. Information 2020, 11, 119. [Google Scholar]
- Mizher, M.A.; Sihwail, R.; Baker, M.B.; Mazhar, A.A.; Mizher, M.A.; Ibrahim, D. A review of cybersecurity for internet-of-things based on next generation healthcare networks. In Proceedings of the AIP Conference Proceedings, Amman, Jordan, 28–29 June 2022; AIP Publishing: Melville, NY, USA, 2023; Volume 2979. [Google Scholar]
- Said Solaiman, O.; Sihwail, R.; Shehadeh, H.; Hashim, I.; Alieyan, K. Hybrid Newton–sperm swarm optimization algorithm for nonlinear systems. Mathematics 2023, 11, 1473. [Google Scholar]
- Liu, J.; Li, J.; Zhang, L.; Dai, F.; Zhang, Y.; Meng, X.; Shen, J. Secure intelligent traffic light control using fog computing. Future Gener. Comput. Syst. 2018, 78, 817–824. [Google Scholar]
- Khalid, T.; Khan, A.N.; Ali, M.; Adeel, A.; ur Rehman Khan, A.; Shuja, J. A fog-based security framework for intelligent traffic light control system. Multimed. Tools Appl. 2019, 78, 24595–24615. [Google Scholar]
- Elsagheer Mohamed, S.A.; AlShalfan, K.A. Intelligent traffic management system based on the Internet of Vehicles (IoV). J. Adv. Transp. 2021, 2021, 4037533. [Google Scholar]
- Özkul, M.; Capuni, I.; Domnori, E. Context-aware intelligent traffic light control through secure messaging. J. Adv. Transp. 2018, 2018, 4251701. [Google Scholar]
- Johnson, D.; Menezes, A.; Vanstone, S. The elliptic curve digital signature algorithm (ECDSA). Int. J. Inf. Secur. 2001, 1, 36–63. [Google Scholar]
- Sihwail, R.; Ibrahim, D. A New Image Encryption Method Using an Optimized Smart Codebook. Hum. Behav. Emerg. Technol. 2025, 2025, 7807003. [Google Scholar]
- Ibrahim, D.; Sihwail, R.; Arrifin, K.A.Z.; Abuthawabeh, A.; Mizher, M. A novel color visual cryptography approach based on Harris Hawks Optimization Algorithm. Symmetry 2023, 15, 1305. [Google Scholar]
- Pieprzyk, J.; Sadeghiyan, B. (Eds.) Design of Hashing Algorithms; Springer: Berlin/Heidelberg, Germany, 1993. [Google Scholar]
- Mizher, M.A.A.J.A.; Sulaiman, R.; Abdalla, A.M.A.; Mizher, M.A.A. A simple flexible cryptosystem for meshed 3D objects and images. J. King Saud Univ.-Comput. Inf. Sci. 2021, 33, 629–646. [Google Scholar]
- Kelly, J.R. Cryptographically Secure Pseudo-Random Number Generator. U.S. Patent No. 6,275,586, 14 August 2001. [Google Scholar]
- Chaves, R.; Sousa, L.; Sklavos, N.; Fournaris, A.P.; Kalogeridou, G.; Kitsos, P.; Sheikh, F. Secure hashing: Sha-1, sha-2, and sha-3. In Circuits and Systems for Security and Privacy; CRC Press: Boca Raton, FL, USA, 2016; pp. 105–132. [Google Scholar]
- Clark, J.; Ali, F. Analysis of ECDSA’s Computational Impact on IoT Network Performance. In Proceedings of the 2023 ACM Southeast Conference, Virtual, 12–14 April 2023; pp. 196–200. [Google Scholar]
- Network Simulator ns-2. Available online: http://www.isi.edu/nsnam/ns/ (accessed on 1 June 2025).
- Behrisch, M.; Bieker, L.; Erdmann, J.; Krajzewicz, D. SUMO–simulation of urban mobility: An overview. In Proceedings of the SIMUL 2011, The Third International Conference on Advances in System Simulation, Barcelona, Spain, 23–29 October 2011. [Google Scholar]

| Control Mechanism | Traffic Characteristics Gathering | Technology Used | Main Considerations | Considered Vehicles |
|---|---|---|---|---|
| Context-aware schedule [2,3] | Periodic advertisement messages | Context-aware algorithms and sensors | Optimize traffic signal timings to reduce traffic congestion and travel time | Emergency vehicles |
| Context-aware negotiation [23] | Real-time traffic data | VANETs, and sensors | Reduce the congestion at signalized intersections | Regular vehicles |
| SmartLight [4] | Collect traffic characteristics | VANETs, and sensors | Reduce fuel consumption and waiting time of vehicles | Heavy vehicles |
| Efficient Adaptive Control System [24] | Detect the presence of vehicles | Magnetometer sensor | Reduce traffic congestion and improve traffic flow efficiency | Regular vehicles |
| Secure Mechanism | Security Tool | Technology Used | Security Considerations | Vehicle Considerations |
|---|---|---|---|---|
| Secure intelligent traffic light [27] | Diffie–Hellman (CDH) algorithms, and puzzle | Fog computing | Prevent DoS attacks | Only regular vehicles |
| A fog-based security framework [28] | Digital signatures | Fog computing | Prevent replay, DoS, Sybil, and impersonation attacks | Only regular vehicles |
| Intelligent traffic management system [29] | Digital and anonymous certificates | VANETs and Internet of Vehicles (IoV) | Ensuring that vehicles are communicating with real traffic signals | Only regular vehicles |
| Secure context aware [30] | Digital signature certificates | Sensors and VANETs | Prevent message alteration, message replay attack, and identity impersonation of a vehicle | Only regular vehicles |
| The Threat | Initiator | Definition | Beneficiaries | Affected |
|---|---|---|---|---|
| Impersonation Attack | Regular Vehicle (Attacker) | A regular vehicle (attacker) pretends to be an emergency vehicle | The attacker vehicle and all vehicles located on the same traffic flow (Less waiting delay time) | All vehicles located on the other competing traffic flows (More waiting delay time) |
| Packet Manipulation Attack | External Intruder | An external intruder manipulates the packet sent by the emergency vehicle to make it look like a regular vehicle | All vehicles located on the traffic flows that are competing with the traffic flow that originally contains the emergency vehicle (Less waiting delay time) | The emergency vehicle and all the vehicles located on the same traffic flow (More waiting delay time) |
| Parameter | Value |
|---|---|
| Simulator | NS-2.35, SUMO 1.24.0 |
| Transmission range (m) | 200 |
| No. of traffic lights | 1 |
| No. of emergency vehicles | 1 |
| Simulation area () | 1000 m × 1000 m |
| Number of vehicles | 200, 400, 600, 800, 1000 |
| Simulation time | 10,000 |
| The map | 4 legs intersection |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Published by MDPI on behalf of the World Electric Vehicle Association. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yahia, M.; Bani Younes, M.; Najjar, F.; Audat, A.; Ghoul, S. Secure Context-Aware Traffic Light Scheduling System: Integrity of Vehicles’ Identities. World Electr. Veh. J. 2025, 16, 448. https://doi.org/10.3390/wevj16080448
Yahia M, Bani Younes M, Najjar F, Audat A, Ghoul S. Secure Context-Aware Traffic Light Scheduling System: Integrity of Vehicles’ Identities. World Electric Vehicle Journal. 2025; 16(8):448. https://doi.org/10.3390/wevj16080448
Chicago/Turabian StyleYahia, Marah, Maram Bani Younes, Firas Najjar, Ahmad Audat, and Said Ghoul. 2025. "Secure Context-Aware Traffic Light Scheduling System: Integrity of Vehicles’ Identities" World Electric Vehicle Journal 16, no. 8: 448. https://doi.org/10.3390/wevj16080448
APA StyleYahia, M., Bani Younes, M., Najjar, F., Audat, A., & Ghoul, S. (2025). Secure Context-Aware Traffic Light Scheduling System: Integrity of Vehicles’ Identities. World Electric Vehicle Journal, 16(8), 448. https://doi.org/10.3390/wevj16080448






