A Blockchain-Based Cross-Domain Authentication Scheme for Unmanned Aerial Vehicle-Assisted Vehicular Networks
Abstract
1. Introduction
- This work proposed a cross-domain authentication architecture that integrates blockchain technology with UAV-assisted vehicular networks. This architecture leverages blockchain’s decentralized trust mechanism to enhance security and eliminate single points of failure, while UAVs dynamically manage cross-domain communications, significantly improving the efficiency and scalability of the authentication process.
- The proposed scheme incorporates biometric information (e.g., user’s biometric keys) and Physical Unclonable Functions (PUF) to enhance privacy protection and resistance against attacks. By utilizing encryption, hashing, and anonymization techniques, the scheme effectively safeguards user identities and defends against common security threats such as identity forgery and data tampering.
- The proposed scheme adopts Elliptic Curve Cryptography (ECC). This protocol significantly reduces computational and communication overhead, making it suitable for resource-constrained vehicular devices. Moreover, the protocol adopts a dynamic key agreement mechanism that meets real-time requirements and ensures robust scalability and security in vehicular environments.
- The proposed scheme demonstrates the security using the ROR model. Detail security analysis and experimental comparisons show that our proposed scheme offers better communication efficiency and security than other related schemes.
2. Related Work
3. Preliminaries
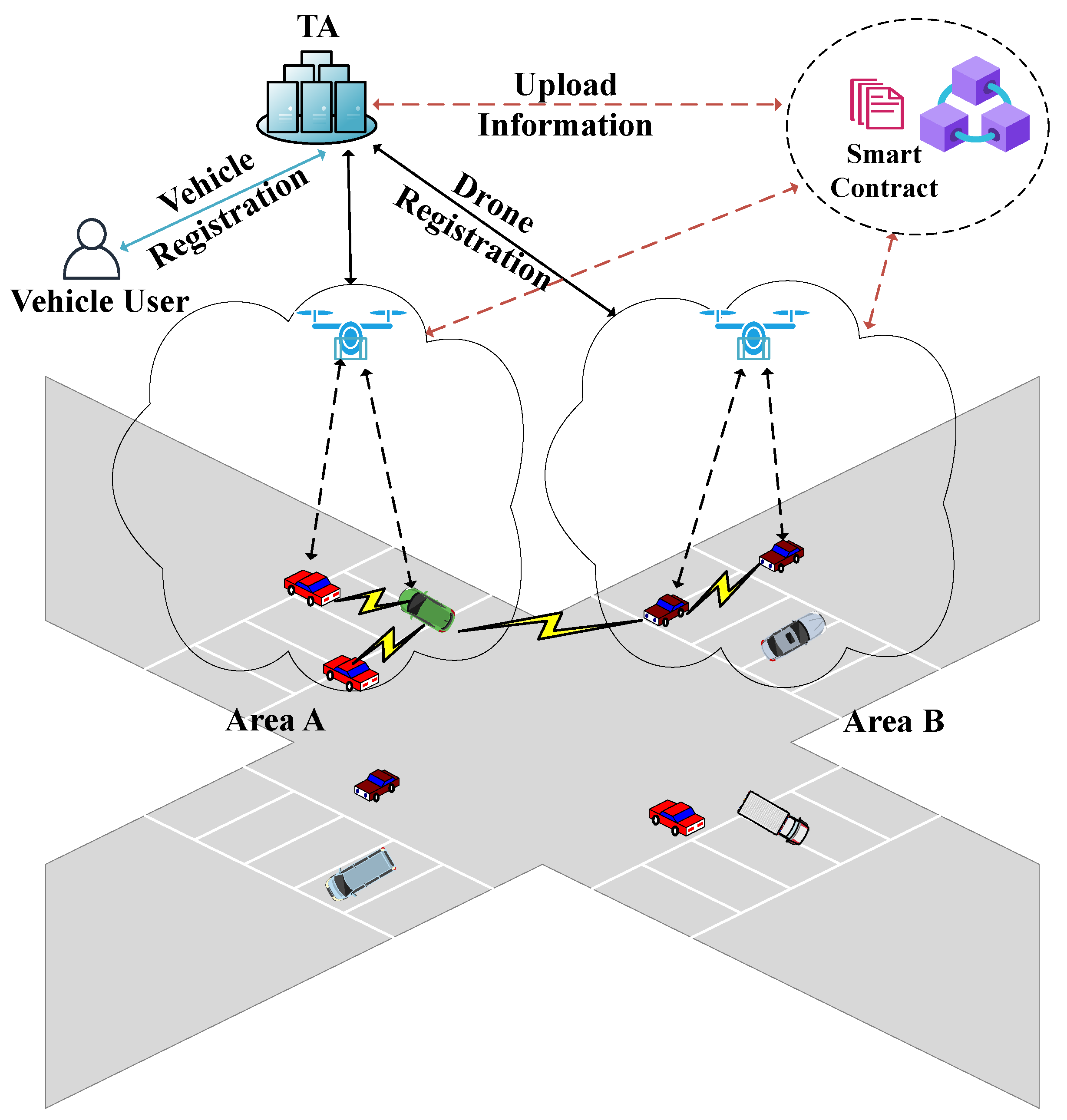
3.1. System Model
3.2. Attack Model
3.3. Scheme Symbol Definition
4. Proposed Scheme
4.1. System Initialization
- The TA selects a secure parameter k for the generation of prime numbers q and p.
- The parameters and E represent the multiplicative group and the elliptic curve, respectively, while G denotes the additive cyclic group.
- P serves as a generator of the group G.
- The TA randomly chooses as the system’s main secret key and calculates the system public key .
- The TA selects one secure one-way hash function . The system’s public parameters are then made public and are defined as .
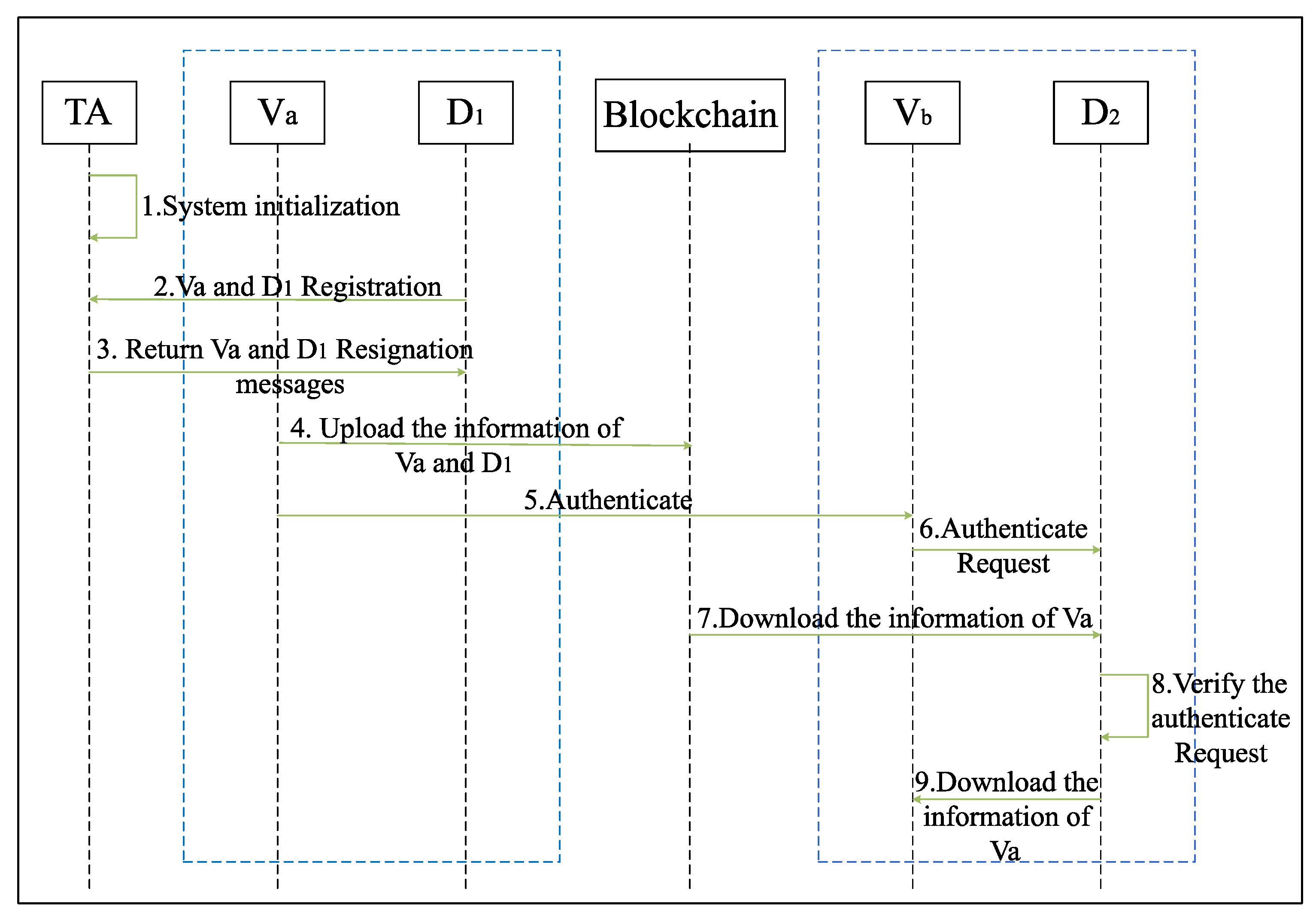
4.2. Entity Registration
- Vehicle users provide their identity to the TA.
- The TA receives the vehicle’s real identity and checks if the identity is unique. If it is not unique, the TA requires the vehicle to choose a new real identity . If it is unique, the TA proceeds as follows:
- Compute the private key .
- Compute the public key .
- Compute as the shared secret key between the TA and the vehicle.
- The is securely stored on the smart contract via a secure channel. After storing , the parameter is broadcasted to the TA, where serves as the pointer for the TA to check the index of in the smart contract.
- The pointer and the public key are sent to the blockchain.
- The vehicle inputs the real identity and the biometric information into the On-Board Unit (OBU). The OBU then performs the following calculations:
- .
- .
- The OBU stores in its memory and replaces with .
- The TA selects as the unique identifier for the drone. The drone’s private key is computed as . The public key is then calculated as and stored in the smart contract.
- The drone selects a challenge value and computes , where PUF represents a Physical Unclonable Function. The response is calculated as . The drone stores the tuple .
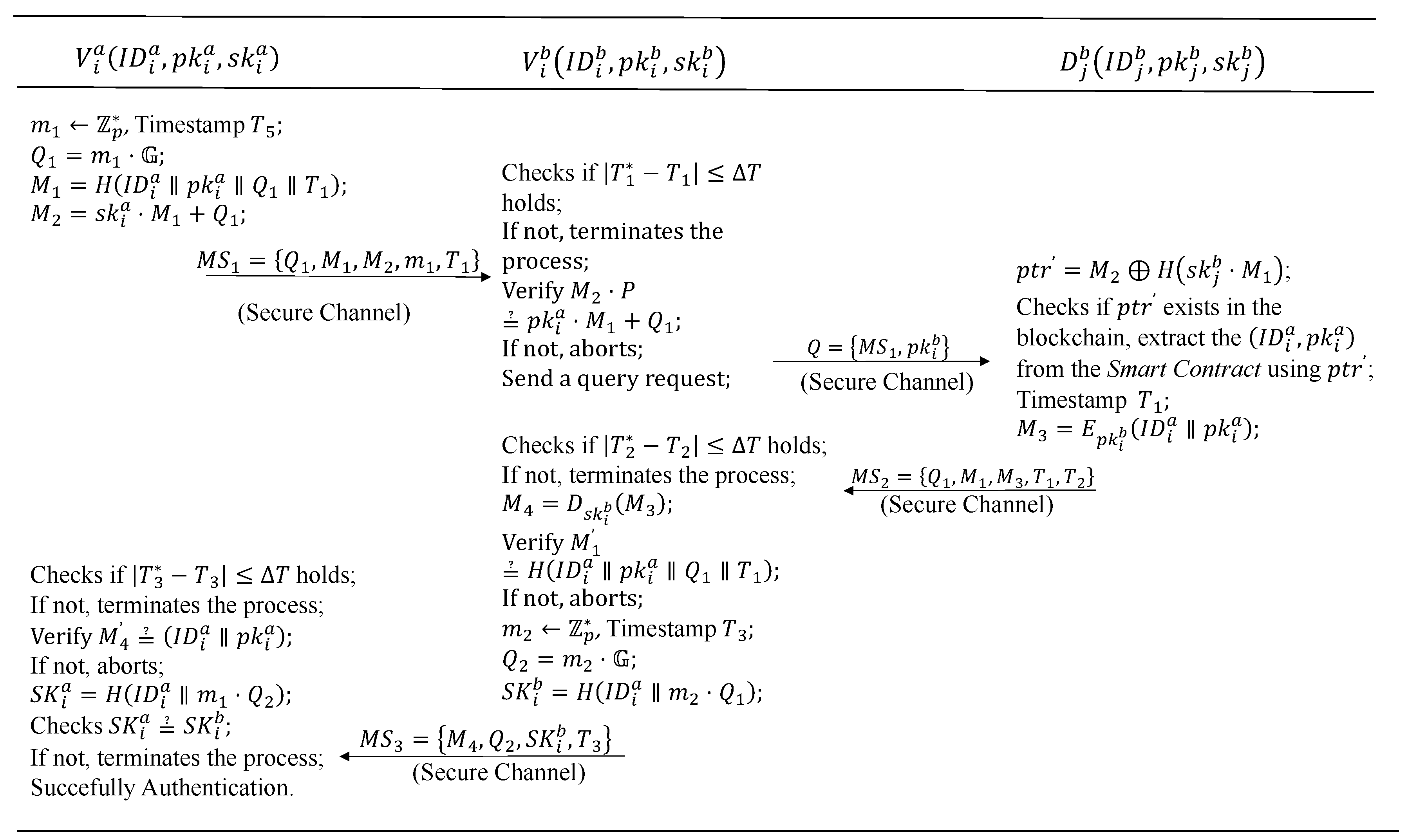
4.3. Cross-Domain Authentication and Key Agreement
- Vehicle initiates authentication request to : The OBU of generates a random number and a timestamp , computes , , and . The OBU sends message to vehicle .
- verifies identity: Upon receiving , the OBU of checks the timestamp’s validity. If , the session terminates. Otherwise, it verifies . If the verification succeeds, the OBU of sends a query request to the drone .
- queries Blockchain: Upon receiving the query request, computes and checks if is on the blockchain. If not, the session terminates. Otherwise, the drone uses to query and retrieve vehicle ’s information from the smart contract. It generates a timestamp and computes . The message is sent to vehicle .
- Generates session key : Upon receiving , the OBU of checks the timestamp’s validity. If , the session terminates. Otherwise, it computes and verifies . If incorrect, the session terminates. Otherwise, it selects a random number and a timestamp , computes , and the session key . The message is sent to vehicle .
- Confirms session key and : Upon receiving , the OBU of checks the timestamp’s validity. If , the session terminates. Otherwise, it computes . If incorrect, the session terminates. Otherwise, it calculates the session key and verifies if . If correct, vehicles and successfully negotiate session keys and , and the authentication is complete.
5. Security Proof and Analysis
5.1. Security Proof
- : Simulates passive eavesdropping by allowing to intercept all messages exchanged between participants.
- : Models the compromise of sensitive data stored on the vehicle, allowing to access internal parameters such as private keys.
- : Simulates active attacks, such as replay or man-in-the-middle attacks, by letting send a message m to a participant instance and receive its response.
- : Grants access to the session key established by the instance .
- : Evaluates the semantic security of the session key. If a session key is established and is fresh, receives either the real session key or a random string, determined by a randomly chosen bit . The adversary wins if it guesses e correctly with a probability exceeding .
- Game (Real Protocol Execution): This represents the real protocol under attack. The adversary guesses the random bit e. By definition of semantic security,
- Game (Eavesdropping Query): In this game, can issue queries to observe all transmitted messages. However, parameters like , , and session keys are computed using secure cryptographic operations (e.g., elliptic curve operations and hash functions). Without knowledge of the private keys, cannot derive the session key. Thus,
- Game (Hash Query Collision): attempts to distinguish between the session key and a random value by querying the hash function. A successful attack requires finding a collision in the hash function, which occurs with probability proportional to . Therefore,
- Game (Corruption and Replay): In this game, can use and queries to manipulate messages or access stored data. However, the session keys depend on the private keys and unique parameters (e.g., timestamps, random numbers) that are infeasible to guess within polynomial time. Thus,
5.2. Security Analysis
- Privacy Protection: The proposed scheme ensures the privacy of vehicle and drone identity information. During the entity registration phase, the real identity of vehicles and of drones is transformed into pseudonyms or processed values using secure hash functions, such as and . Since the hash functions are one-way and computationally secure, attackers cannot derive real identities from the pseudonyms, even if they gain access to intermediate data on the blockchain. This guarantees privacy protection throughout the system.
- Integrity and Authenticity: Message integrity and authenticity are ensured using cryptographic mechanisms. During cross-domain authentication, vehicles compute message signatures (e.g., ) and verify them through elliptic curve cryptography (ECC). The inability to derive the private key from the public key ensures that adversaries cannot forge valid signatures or tamper with messages. For instance, verifying guarantees the integrity and authenticity of the transmitted data.
- Non-repudiation: Non-repudiation is achieved through the use of vehicle-specific cryptographic keys. When a vehicle transmits its message , the corresponding signature is uniquely tied to its private key . The verification process ensures that only the legitimate vehicle could have generated the signature. Furthermore, the TA can use stored information (e.g., and ) to trace the actual identity of the vehicle, ensuring accountability for all transmitted data.
- Traceability: The TA securely tracks the real identity of vehicles and drones by maintaining a mapping between pseudonyms and real identities. For example, is derived using a secret parameter known only to the TA, ensuring that no unauthorized entity can reverse-engineer the mapping. This enables the TA to trace malicious or misbehaving entities while preserving privacy for legitimate users.
- Resistance to Replay Attacks: The scheme employs timestamps (e.g., , , ) to prevent replay attacks. Each timestamp is checked for validity before proceeding with the protocol. If a received timestamp deviates from the current time by more than the allowed threshold , the session is terminated. This ensures that old or intercepted messages cannot be reused by adversaries.
- Resistance to Collusion Attacks: The use of unique session keys and pseudonyms for each entity prevents collusion attacks. Revoked vehicles or drones cannot participate in the system due to the removal of their corresponding identifiers (e.g., ) from the blockchain. Additionally, the shared secrets (e.g., ) remain inaccessible to colluding entities, further enhancing system resilience.
5.3. Formal Verification Using ProVerif
6. Performance Evaluation
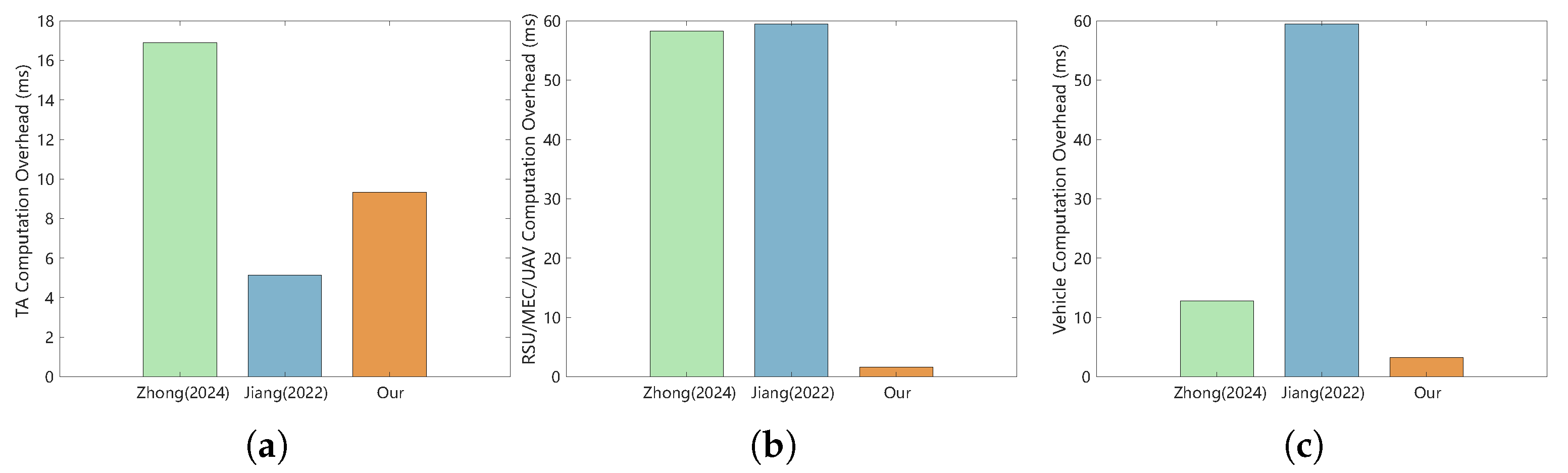
6.1. Computation Overhead
6.2. Communication Overhead
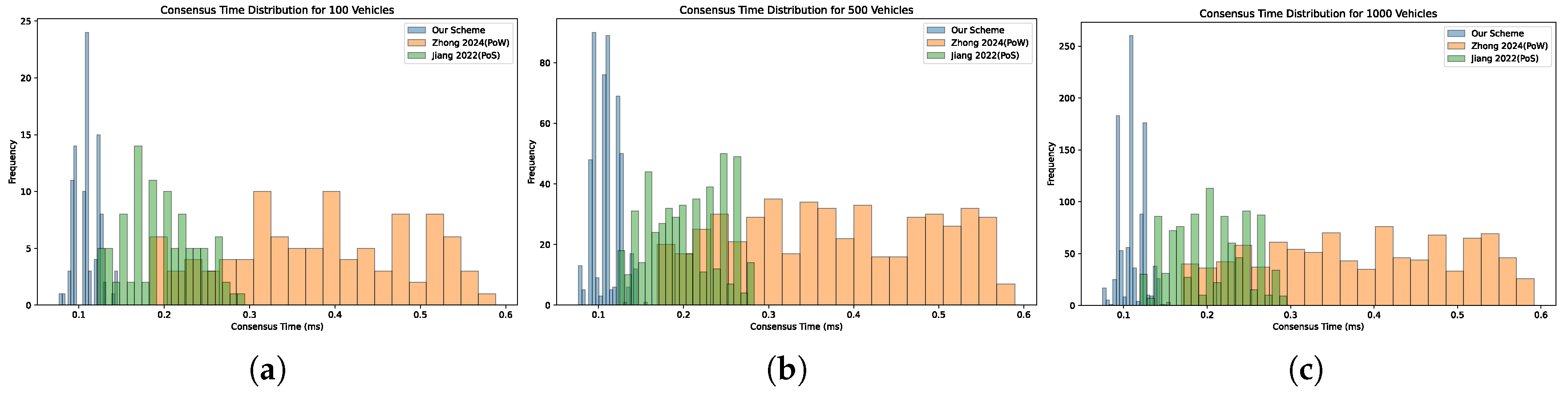
6.3. Consensus Times
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Lin, C.; He, D.; Huang, X.; Kumar, N.; Choo, K.K.R. BCPPA: A blockchain-based conditional privacy-preserving authentication protocol for vehicular ad hoc networks. IEEE Trans. Intell. Transp. Syst. 2020, 22, 7408–7420. [Google Scholar]
- Zhang, J.; Zhong, H.; Cui, J.; Xu, Y.; Liu, L. SMAKA: Secure many-to-many authentication and key agreement scheme for vehicular networks. IEEE Trans. Inf. Forensics Secur. 2020, 16, 1810–1824. [Google Scholar]
- Li, X.; Liu, Y.; Yin, X. An Anonymous Conditional Privacy-Preserving Authentication Scheme for VANETs. In Proceedings of the 2019 IEEE 21st International Conference on High Performance Computing and Communications; IEEE 17th International Conference on Smart City; IEEE 5th International Conference on Data Science and Systems (HPCC/SmartCity/DSS), Zhangjiajie, China, 10–12 August 2019; pp. 1763–1770. [Google Scholar] [CrossRef]
- Zhang, J.; Zhong, H.; Cui, J.; Tian, M.; Xu, Y.; Liu, L. Edge Computing-Based Privacy-Preserving Authentication Framework and Protocol for 5G-Enabled Vehicular Networks. IEEE Trans. Veh. Technol. 2020, 69, 7940–7954. [Google Scholar] [CrossRef]
- Lai, C.; Lu, R.; Zheng, D.; Shen, X. Security and Privacy Challenges in 5G-Enabled Vehicular Networks. IEEE Netw. 2020, 34, 37–45. [Google Scholar] [CrossRef]
- Xiong, J.; Bi, R.; Zhang, Y.; Li, Q.; Lin, L.; Tian, Y. Privacy-Preserving Outsourcing Learning for Connected Autonomous Vehicles: Challenges, Solutions, and Perspectives. IEEE Netw. 2024, 38, 41–47. [Google Scholar] [CrossRef]
- Wang, X.; Fu, L.; Zhang, Y.; Gan, X.; Wang, X. VDNet: An infrastructure-less UAV-assisted sparse VANET system with vehicle location prediction. Wirel. Commun. Mob. Comput. 2016, 16, 2991–3003. [Google Scholar] [CrossRef]
- Du, J.; Wang, J.; Sun, A.; Qu, J.; Zhang, J.; Wu, C.; Niyato, D. Joint Optimization in Blockchain- and MEC-Enabled Space–Air–Ground Integrated Networks. IEEE Internet Things J. 2024, 11, 31862–31877. [Google Scholar] [CrossRef]
- Khabbaz, M.; Antoun, J.; Assi, C. Modeling and Performance Analysis of UAV-Assisted Vehicular Networks. IEEE Trans. Veh. Technol. 2019, 68, 8384–8396. [Google Scholar] [CrossRef]
- Hu, J.; Chen, C.; Cai, L.; Khosravi, M.R.; Pei, Q.; Wan, S. UAV-assisted vehicular edge computing for the 6G internet of vehicles: Architecture, intelligence, and challenges. IEEE Commun. Stand. Mag. 2021, 5, 12–18. [Google Scholar]
- Zhu, Y.; Zhou, Y.; Wang, J.; Yang, B.; Zhang, M. A Lightweight Cross-Domain Direct Identity Authentication Protocol for VANETs. IEEE Internet Things J. 2024, 11, 37741–37757. [Google Scholar] [CrossRef]
- Zhong, Q.; Zhao, X.; Xia, Y.; Liu, X. CD-BASA: An Efficient Cross-Domain Batch Authentication Scheme Based on Blockchain With Accumulator for VANETs. IEEE Trans. Intell. Transp. Syst. 2024, 25, 14560–14571. [Google Scholar] [CrossRef]
- Rajput, U.; Abbas, F.; Oh, H. A Hierarchical Privacy Preserving Pseudonymous Authentication Protocol for VANET. IEEE Access 2016, 4, 7770–7784. [Google Scholar] [CrossRef]
- Jiang, S.; Chen, X.; Cao, Y.; Xu, T.; He, J.; Cui, Y. APKI: An anonymous authentication scheme based on PKI for VANET. In Proceedings of the IEEE 2022 7th International Conference on Computer and Communication Systems (ICCCS), Wuhan, China, 22–25 April 2022; pp. 530–536. [Google Scholar]
- Mao, W.; Jiang, P.; Zhu, L. BTAA: Blockchain and TEE-Assisted Authentication for IoT Systems. IEEE Internet Things J. 2023, 10, 12603–12615. [Google Scholar] [CrossRef]
- Yao, Y.; Chang, X.; Mišić, J.; Mišić, V.B.; Li, L. BLA: Blockchain-Assisted Lightweight Anonymous Authentication for Distributed Vehicular Fog Services. IEEE Internet Things J. 2019, 6, 3775–3784. [Google Scholar] [CrossRef]
- Shen, M.; Liu, H.; Zhu, L.; Xu, K.; Yu, H.; Du, X.; Guizani, M. Blockchain-Assisted Secure Device Authentication for Cross-Domain Industrial IoT. IEEE J. Sel. Areas Commun. 2020, 38, 942–954. [Google Scholar] [CrossRef]
- Phan, T.C.; Singh, P. A Recent Connected Vehicle - IoT Automotive Application Based on Communication Technology. Int. J. Data Inform. Intell. Comput. 2023, 2, 40–51. [Google Scholar] [CrossRef]
- Danjuma Maiwada, U.; Yakubu, M.M.; Maiwada, A.D.; Yalli, J.S.; Yakasai, I.K. Techniques to improve 5G blockchain scalability issues through an analysis of a blockchain scalability. Int. J. Data Inform. Intell. Comput. 2024, 3, 8–25. [Google Scholar] [CrossRef]
- Zhang, J.; Cui, J.; Zhong, H.; Bolodurina, I.; Liu, L. Intelligent Drone-assisted Anonymous Authentication and Key Agreement for 5G/B5G Vehicular Ad-Hoc Networks. IEEE Trans. Netw. Sci. Eng. 2020, 8, 2982–2994. [Google Scholar] [CrossRef]
- Cui, J.; Liu, X.; Zhong, H.; Zhang, J.; Wei, L.; Bolodurina, I.; He, D. A Practical and Provably Secure Authentication and Key Agreement Scheme for UAV-Assisted VANETs for Emergency Rescue. IEEE Trans. Netw. Sci. Eng. 2024, 11, 1454–1468. [Google Scholar] [CrossRef]
- Lin, C.; Huang, X.; He, D. EBCPA: Efficient Blockchain-Based Conditional Privacy-Preserving Authentication for VANETs. IEEE Trans. Dependable Secur. Comput. 2023, 20, 1818–1832. [Google Scholar] [CrossRef]
- Zhu, J.; Wang, X.; Huang, H.; Cheng, S.; Wu, M. A NSGA-II Algorithm for Task Scheduling in UAV-Enabled MEC System. IEEE Trans. Intell. Transp. Syst. 2022, 23, 9414–9429. [Google Scholar] [CrossRef]
- Canetti, R.; Shahaf, D.; Vald, M. Universally composable authentication and key-exchange with global PKI. In Proceedings of the Public-Key Cryptography–PKC 2016: 19th IACR International Conference on Practice and Theory in Public-Key Cryptography, Taipei, Taiwan, 6–9 March 2016; Proceedings, Part II 19. Springer: Berlin/Heidelberg, Germany, 2016; pp. 265–296. [Google Scholar]
- Sciancalepore, S.; Piro, G.; Boggia, G.; Bianchi, G. Public key authentication and key agreement in IoT devices with minimal airtime consumption. IEEE Embed. Syst. Lett. 2016, 9, 1–4. [Google Scholar] [CrossRef]
- Sahu, P.; Kumar, V. Design and Performance Analysis of a Lightweight Authentication Protocol for Vehicular Ad-Hoc Networks. In Proceedings of the 2023 International Conference on IoT, Communication and Automation Technology (ICICAT), Gorakhpur, India, 23–24 June 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Tahir, H.; Mahmood, K.; Ayub, M.F.; Saleem, M.A.; Ferzund, J.; Kumar, N. Lightweight and Secure Multi-Factor Authentication Scheme in VANETs. IEEE Trans. Veh. Technol. 2023, 72, 14978–14986. [Google Scholar] [CrossRef]
- Chen, Y.; Zhang, J.; Wei, X.; Wang, Y.; Cui, J. Cross-Domain Authentication Scheme for Vehicles Based on Given Virtual Identities. IEEE Internet Things J. 2024, 11, 15869–15879. [Google Scholar] [CrossRef]
- Yang, Y.; Wei, L.; Wu, J.; Long, C.; Li, B. A Blockchain-Based Multidomain Authentication Scheme for Conditional Privacy Preserving in Vehicular Ad-Hoc Network. IEEE Internet Things J. 2022, 9, 8078–8090. [Google Scholar] [CrossRef]
- Chen, C.; Shi, F.; Yu, H.; Fei, N. Anonymous authentication based on cloud storage for cross-regional vehicles in VANET. In Proceedings of the 2016 IEEE International Conference on Ubiquitous Wireless Broadband (ICUWB), Nanjing, China, 16–19 October 2016; pp. 1–4. [Google Scholar]
- Li, P.; Ma, H.; Lai, J.; Zhou, D.; Huang, L.; Li, Y.; Zang, R.; Fang, J. BlockPPA: Blockchain-Assisted Privacy-Preserving Authentication for Cross-Domain Electric Vehicle Charging. IEEE Trans. Veh. Technol. 2024, 74, 3212–3224. [Google Scholar] [CrossRef]
- Gao, B.; Yan, H.; Tian, R. A Privacy-Aware Cross-Domain Device Authentication Scheme for IIoT Based on Blockchain. In Proceedings of the 2021 IEEE 23rd Int Conf on High Performance Computing & Communications; 7th Int Conf on Data Science & Systems; 19th Int Conf on Smart City; 7th Int Conf on Dependability in Sensor, Cloud Big & Data Systems & Application (HPCC/DSS/SmartCity/DependSys), Haikou, China, 20–22 December 2021; pp. 561–570. [Google Scholar] [CrossRef]
- Canetti, R.; Krawczyk, H. Analysis of Key-Exchange Protocols and Their Use for Building Secure Channels. In Proceedings of the International Conference on the Theory and Application of Cryptographic Techniques: Advances in Cryptology, Innsbruck, Austria, 6–10 May 2001. [Google Scholar]
- Son, S.; Lee, J.; Park, Y.; Park, Y.; Das, A.K. Design of blockchain-based lightweight V2I handover authentication protocol for VANET. IEEE Trans. Netw. Sci. Eng. 2022, 9, 1346–1358. [Google Scholar] [CrossRef]


| Scheme | [11] | [12] | [22] | [26] | [27] | Our Scheme |
|---|---|---|---|---|---|---|
| Integrity and Authenticity | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Non-repudiation | ✓ | × | × | × | × | ✓ |
| Traceability | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Replay Attacks | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Collusion Attacks | × | × | × | × | × | ✓ |
| Symbols | Descriptions |
|---|---|
| P | Long-term secret value |
| p | Generators of G |
| System public key | |
| The i-th vehicle | |
| The j-th UAV | |
| Identity information of vehicle | |
| Identity information of UAV | |
| Private key of vehicle | |
| Private key and public key of vehicle | |
| Private key of UAV | |
| Private key and public key of UAV | |
| Timestamp | |
| Symmetric encryption | |
| Symmetric decryption | |
| Hash function | |
| ⊕ | Exclusive-OR operation |
| Notation | Description | Time (ms) |
|---|---|---|
| Time cost of a bilinear pairing operation | 11.751 ms | |
| Time cost of a bilinear group exponential operation | 0.298 ms | |
| Time cost of an elliptic curve multiplication operation | 1.592 ms | |
| Time cost of an elliptic curve point addition operation | 0.011 ms | |
| Time cost of a hash function operation | 0.002 ms | |
| Time cost of a decryption algorithm | 0.029 ms | |
| Time cost of an encryption algorithm | 6.041 ms | |
| Time cost of an exponentiation based on RSA accumulator | 18.3512 ms | |
| Scalar multiplication based on bilinear pairing | 5.1330 ms | |
| Time cost of a module exponential operation | 0.048 ms | |
| Time cost of a module multiplication operation | 0.0016 ms | |
| Time cost of an XOR operation | 0.0005 ms |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Published by MDPI on behalf of the World Electric Vehicle Association. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, W.; Zhang, S.; Liu, G.; Zhao, Y. A Blockchain-Based Cross-Domain Authentication Scheme for Unmanned Aerial Vehicle-Assisted Vehicular Networks. World Electr. Veh. J. 2025, 16, 199. https://doi.org/10.3390/wevj16040199
Wang W, Zhang S, Liu G, Zhao Y. A Blockchain-Based Cross-Domain Authentication Scheme for Unmanned Aerial Vehicle-Assisted Vehicular Networks. World Electric Vehicle Journal. 2025; 16(4):199. https://doi.org/10.3390/wevj16040199
Chicago/Turabian StyleWang, Wenming, Shumin Zhang, Guijiang Liu, and Yue Zhao. 2025. "A Blockchain-Based Cross-Domain Authentication Scheme for Unmanned Aerial Vehicle-Assisted Vehicular Networks" World Electric Vehicle Journal 16, no. 4: 199. https://doi.org/10.3390/wevj16040199
APA StyleWang, W., Zhang, S., Liu, G., & Zhao, Y. (2025). A Blockchain-Based Cross-Domain Authentication Scheme for Unmanned Aerial Vehicle-Assisted Vehicular Networks. World Electric Vehicle Journal, 16(4), 199. https://doi.org/10.3390/wevj16040199





