Enhancing Intrusion Detection in Autonomous Vehicles Using Ontology-Driven Mitigation
Abstract
1. Introduction
- Enhance the interpretability of detected intrusions through the formalization of relationships between threats and mitigation strategies.
- Enhance IDS decision making by providing a knowledge-driven framework to recommend appropriate countermeasures.
2. Related Work
- -
- Lack of Mitigation-Centric Integration: Most existing ontologies focus exclusively on descriptive modeling of threats (e.g., [8,10]) or vehicular context (e.g., [11,14]). They lack the functional capability to seamlessly link a detected intrusion event to an appropriate, context-aware mitigation strategy using automated reasoning.
- -
- Absence of Formal Coherence Validation: Prior works often integrate ontologies into specific, existing systems (IDS, driver assistance), but they rarely provide a formal validation of the ontology’s internal semantic consistency and reasoning capability before deployment, which is critical for trustworthy, safety-related systems.
- -
- Limited: Existing models are often closely tied to specific sensor types, network topologies (e.g., CAN Bus in [21]), or simple detection primitives, limiting their generalizability to new threats and complex, layered attack scenarios in autonomous vehicles.
3. Intrusion in Autonomous Vehicle: Classification and Challenges
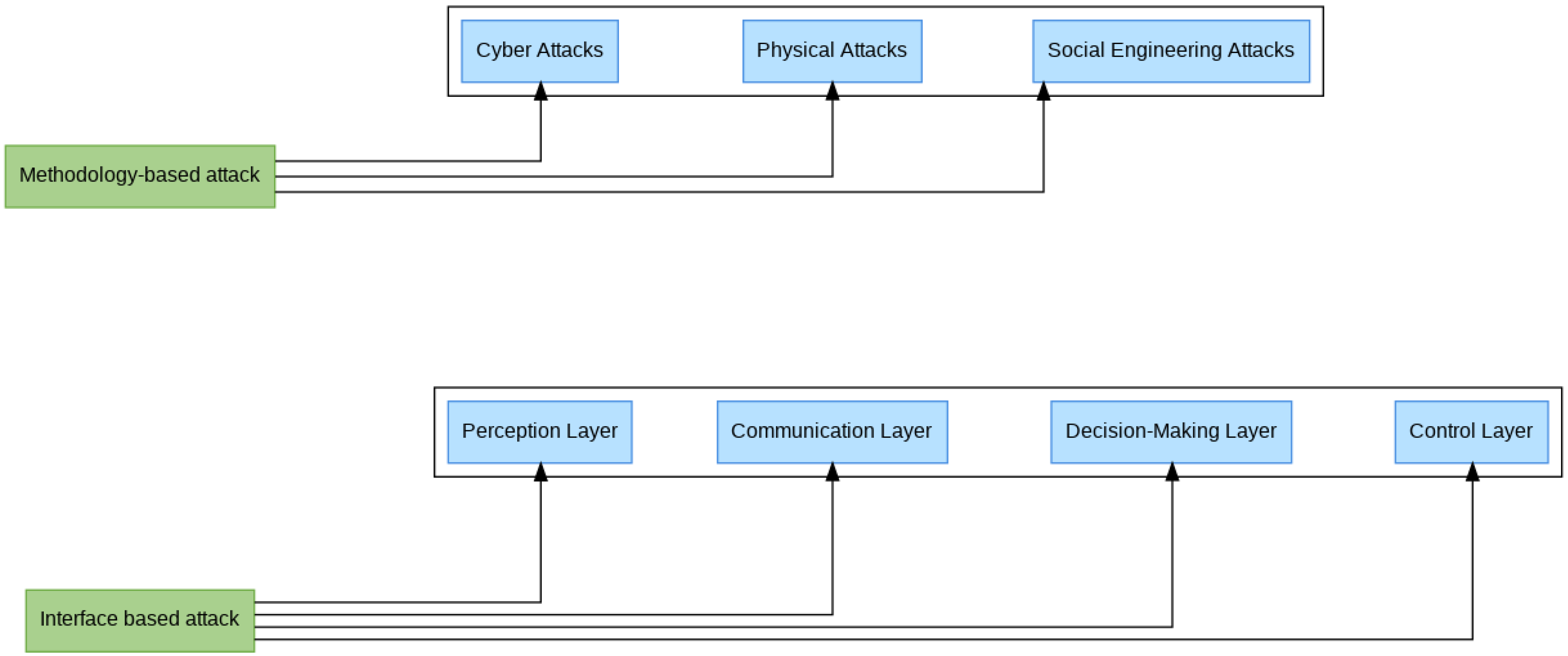
3.1. Classification of Attack
3.1.1. Interface Based Attack
- Attacks on the perception layer (sensor level): Sensors play a major role in the detection of the environment. For example, GPS spoofing involves injecting fake GPS signals to mislead the navigation system into addressing the wrong destination. LiDAR and camera spoofing involve manipulating the data collected by these sensors to create false objects or hide real obstacles, which disrupt the vehicle’s decision-making process [28]. Finally, adversarial attacks on AI modify the input data used by artificial intelligence models, which can mislead the vehicle and lead to incorrect driving decisions [29].
- Attacks on the communication layer: AVs constantly interact with other vehicles (V2V) and external infrastructures (V2I). Man-in-the-Middle (MitM) attacks intercept these communications, enabling attackers to modify or falsify them. On the other hand, Denial of Service (DoS/DDoS) attacks aim to saturate communication networks, disrupting essential services such as navigation, communication with other vehicles or security alerts [30]. On the other hand, false message injection is another potentially devastating attack, where falsified messages are sent into V2V or V2I channels, distorting coordination and decision-making between vehicles and the infrastructure.
- Attacks on the decision-making layer: AVs depend on artificial intelligence systems to make decisions in real-time. Data poisoning involves injecting malicious data into learning models, distorting vehicle behavior, and increasing the risk of erroneous decisions [31]. In addition, manipulation of reinforcement learning involves altering the rewards given to the AI system to influence its learning process, which disrupts the vehicle’s decisions and may lead it to adopt unsafe behavior.
- Attacks on the control layer: These attacks aim to directly modify the vehicle’s actions. Braking override prevents the vehicle from stopping, even in situations where stopping is necessary to avoid an accident [32]. Acceleration manipulation forces the vehicle to accelerate unexpectedly, compromising the safety of passengers and other road users.
3.1.2. Methodology-Based Attack
- Cyber-attacks: these are attempts to intrude into a vehicle’s electronic systems, usually carried out remotely by malicious attackers [33]. One of the most common forms is the exploitation of vulnerabilities in vehicle systems via wireless connections. Using these exploits, attackers may assume control of vital vehicle systems, as happens in vehicle hacking incidents, particularly those concerning Tesla cars. Another form of cyber attack involves malware and ransom ware, which are used to infect vehicle systems. This is designed either to disable the vehicle or compromise sensitive data, thus forcing the attacker to demand a ransom to unlock access or deter the disclosure of private information [34]. Backdoors or logic bombs can also be introduced in their use upon software updates to the vehicles. The backdoor serves to establish remote access to the vehicle’s systems, while the logic bomb can be activated at a specific time to disrupt its operation.
- Physical attacks: The direct impact is on vehicle hardware parts, especially sensors and communication systems. For instance, the manipulation of sensors includes acts such as covering, blocking, or degrading, all of which impede correct perceptions by the vehicle of its environment [35]. This may lead to errors of judgment or failure of autonomous driving systems that could compromise vehicle safety.
- Social engineering attacks: also known as insider threats, these exploit the manipulation of individuals or loopholes in the supply chain to compromise a vehicle’s systems. Various phishing techniques and fraudulent software updates are commonly used to trick users or employees into installing malware in vehicle systems [36]. Many of these attacks come looking like genuine software updates but possess malicious content that would allow an attacker to take control of the system.
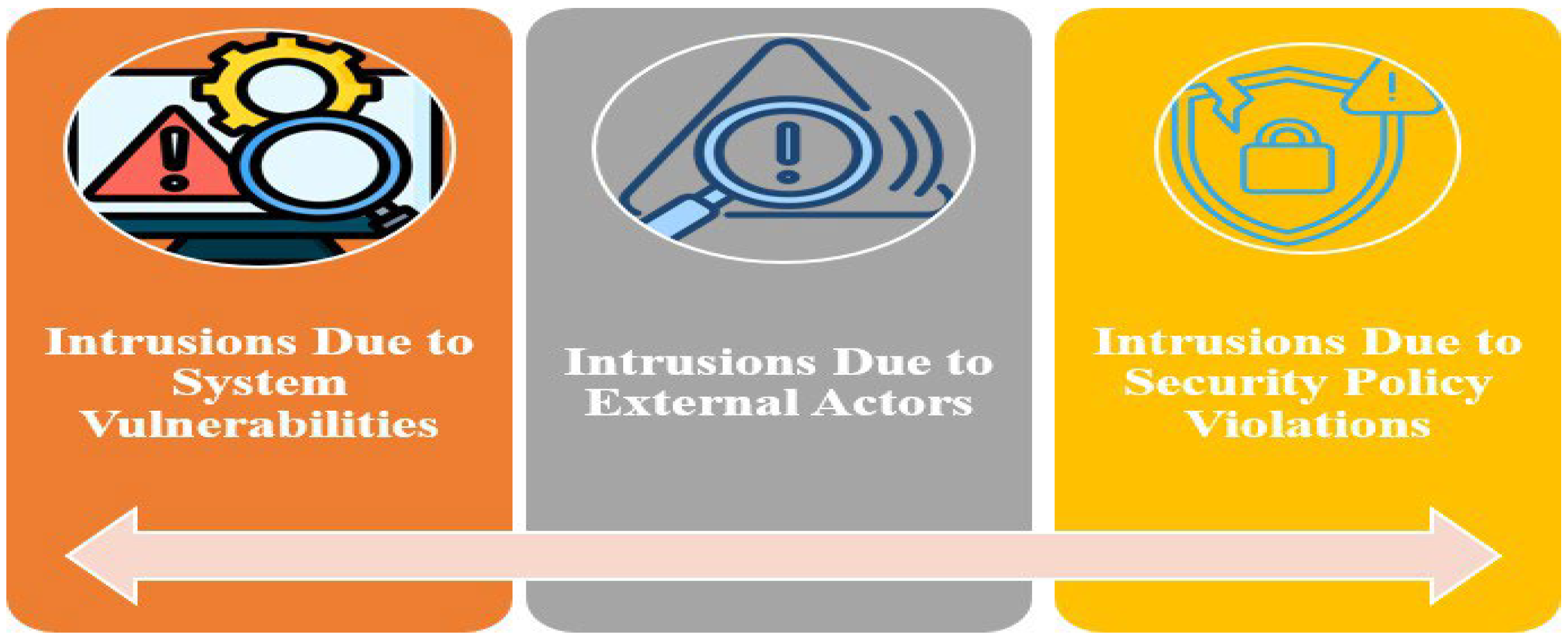
3.2. Challenges Related to the Safety of Autonomous Vehicles
3.2.1. Intrusions Due to System Vulnerabilities
- Software-based vulnerabilities: Unpatched software, unsecured third-party applications, and malicious firmware updates can allow attackers to exploit the system.
- Communication vulnerabilities: AVs communicate via Vehicle-to-Everything (V2X) protocols, which are susceptible to eavesdropping, spoofing, and man-in-the-middle attacks.
- Hardware-based vulnerabilities: Malfunctioning electronic control units (ECUs), sensor failures, or unauthorized physical access can introduce security risks.
3.2.2. Intrusions Due to External Actors
- Environmental factors: Sensor manipulation (e.g., LiDAR jamming), GPS spoofing, and adversarial road signs can mislead AV decision-making.
- Malicious drivers: Attackers inside nearby vehicles may inject false information into AV networks to mislead detection systems.
3.2.3. Intrusions Due to Security Policy Violations
- Confidentiality attacks: Data breaches exposing AV sensor or user data.
- Integrity attacks: Tampering with AV decision-making by injecting false control commands.
- Availability attacks: Denial-of-Service (DoS) or jamming attacks that disrupt communication.
4. Security Requirements for Intrusion Detection in Autonomous Vehicle
4.1. Authentication & Access Control
- Multi-factor authentication (MFA): enhances security by requiring multiple authentication factors (e.g., passwords, biometrics, and security tokens) to access vehicle systems.
- Role-based access control (RBAC): implementation of strict authorization policies based on user roles (e.g., driver, manufacturer, service technician) to limit system access and minimize security risks.
4.2. Secure Communication
- End-to-end encryption (E2EE): Encrypting all V2X communications with secure cryptographic protocols, as TLS/SSL will prevent eavesdropping and any kind of data tampering.
- Intrusion Prevention Systems (IPS): Implement security solutions to detect and block malicious network traffic in real time, reducing the risk of network-based attacks such as Man-in-the-Middle and Denial-of-Service.
- Blockchain for V2X security: This involves the use of decentralized authentication to verify the legitimacy of messages exchanged among vehicles, infrastructure, and cloud services, reducing the possibility of injecting fake messages.
4.3. AI-Based Intrusion Detection Systems (IDS)
- Anomaly-based detection: applying machine learning algorithms to detect deviations from the normal operation of network communications, sensor inputs, and system behaviors, hence identifying potential attacks in real time [44].
- Adversarial ML defense techniques: This is the implementation of robust AI models with resistance to adversarial attacks by improving training methods, using adversarial learning, and integrating model-checking techniques to improve resilience [45].
4.4. Secure Software & Hardware
- Secure booting and code signing: it implements cryptographic validation mechanisms that guarantee the execution of the software on vehicle components that are trusted and verified; prevents unauthorized firmware updates or injections of malware.
- Hardware Security Modules (HSM): The use of dedicated security chips for securely storing and managing keys prevents any unauthorized access to the encryption keys and thus protects the sensitive vehicle data.
4.5. Resilience & Recovery Mechanisms
- Safety mechanisms: design autonomous systems to enter a safe operating mode if a cyber attack is detected, enabling the vehicle to stop or continue operating with minimal risk to passengers and the environment.
- Redundant systems: Integrate backup sensors, isolated control units, redundant communication networks to retain vital functionality during system failure or security breaches.
5. Methodology and Proposed Ontology
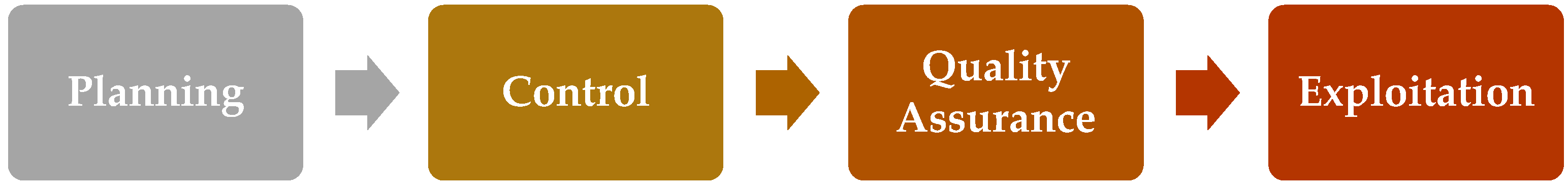
5.1. Procedures for Ontology Creation
- Planning: The problem is identified, and the tasks required to deal with it are outlined. It includes the detection of security threats on autonomous vehicles, the identification of mitigation techniques, the assessment of their impact, and structuring tasks by categorizing relevant elements, such as vehicle communication, attack types, and mitigation strategies. Besides that, this step will define actors and their attributes, mapping their interactions within the system.
- Control ensures the ontology’s execution is accurate, error-free, and that the identified security issues are effectively re-solved.
- Quality Assurance follows, focusing on testing the ontology and validating the interactions between different entities to confirm its reliability.
- Exploitation is the final stage, where the ontology is deployed in real-world scenarios after extensive testing. Figure 3 illustrates this ontology-based process:
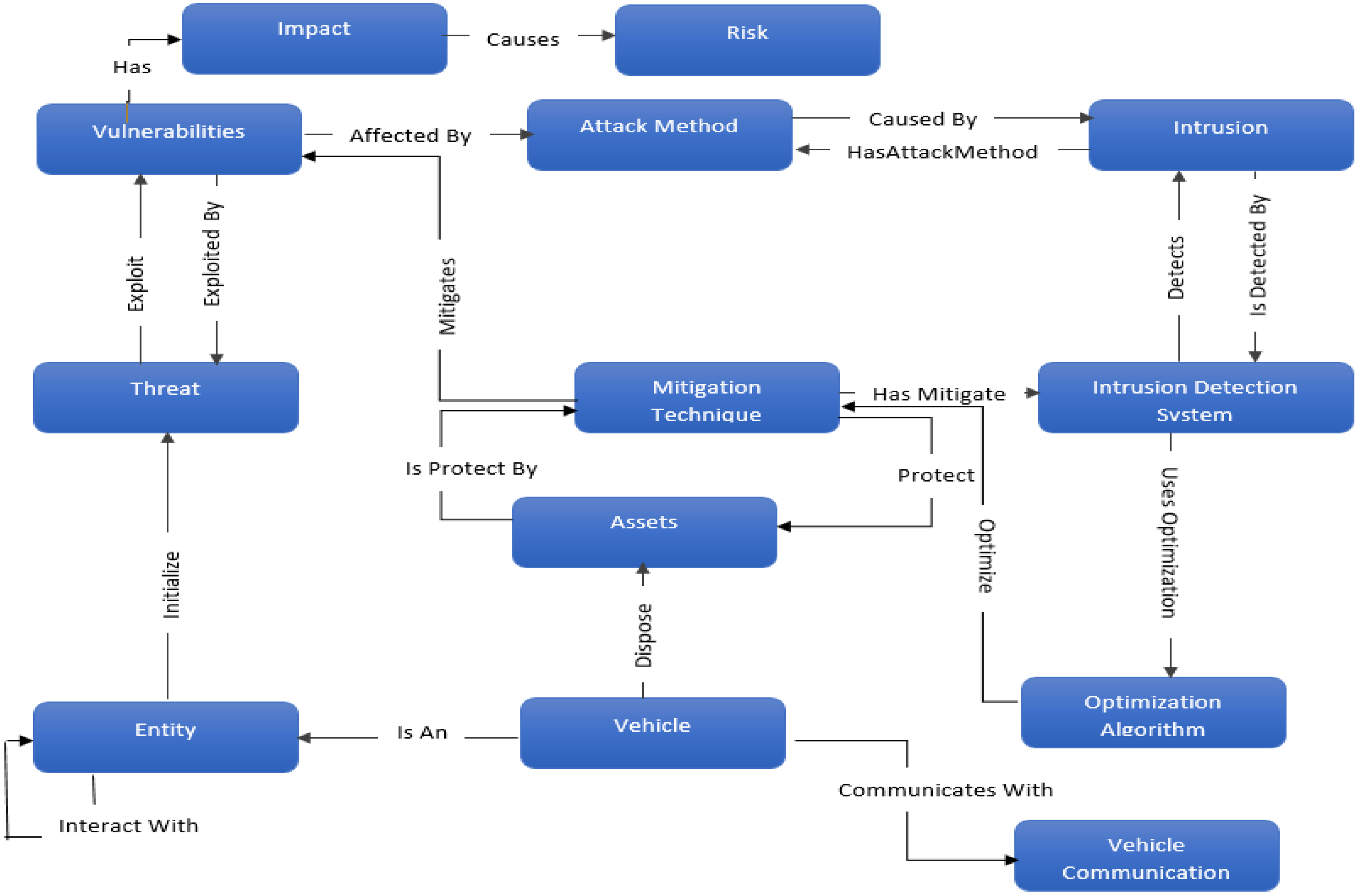
5.2. Proposed Ontology
5.3. Ontology-Based to Secure Autonomous Vehicles
5.3.1. Specification
5.3.2. Conceptualization
- A concept C1 is a subclass of concept C2 if and only if every instance of C1 is also an instance of C2. For example, a Vehicle is a subclass of the class Entity.
- A Disjoint Decomposition of concept C is a set of subclasses of C that do not cover C entirely and do not share any common instances. For example, the concepts Low, Moderate, and Critical form a Disjoint Decomposition of the concept of Security Level.
- An Exhaustive Decomposition of concept C is a set of subclasses of C that together cover C completely and may share common instances.
- A Partition of concept C is a set of subclasses of C that together cover C entirely and have no overlapping instances. For instance, the concepts Proactive, Detective, and Corrective form a Partition of concept types.
5.3.3. Formalization
- LiDAR_Spoofing_Attack_01: LiDARAttack
- Weak_Sensor_Filtering: Vulnerability
- False_Obstacle_Detection: Impact
- Enable_Sensor_Fusion: Mitigation
- LiDAR_Spoofing_Attack_01 exploits Vulnerability Weak_Sensor_Filtering
- LiDAR_Spoofing_Attack_01 has Impact False_Obstacle_Detection
- LiDAR_Spoofing_Attack_01 mitigated By Enable_Sensor_Fusion
- CAN_DoS_Attack_01: DoSAttack
- Bus_Flooding_Vulnerability: Vulnerability
- Loss_of_Communication: Impact
- CAN_Bus_Message_Rate_Limiting: Mitigation
- CAN_DoS_Attack_01 exploits Bus_Flooding_Vulnerability
- CAN_DoS_Attack_01 has Impact Loss_of_Communication
- CAN_DoS_Attack_01 mitigated By CAN_Bus_Message_Rate_Limiting
5.3.4. Implementation and Test
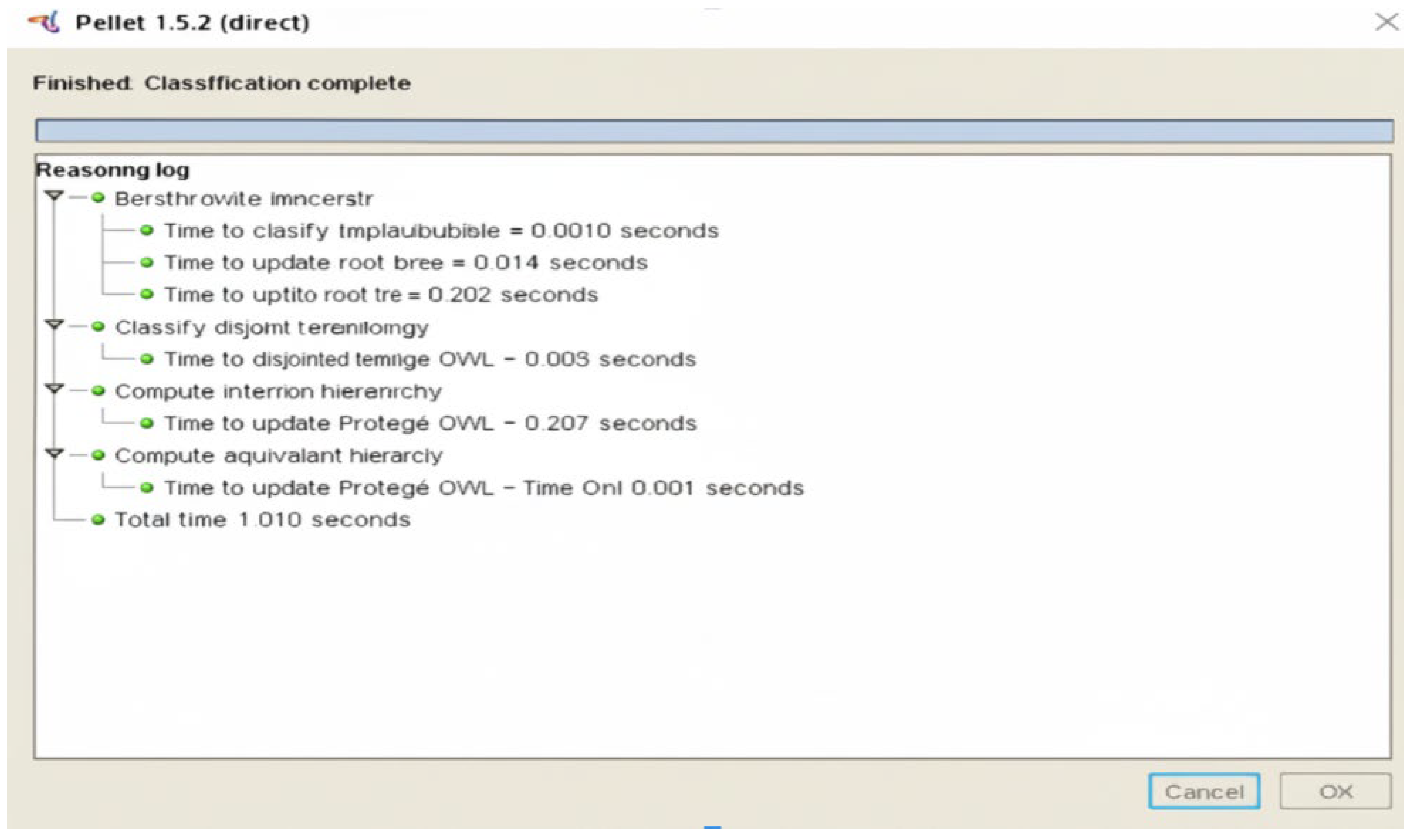
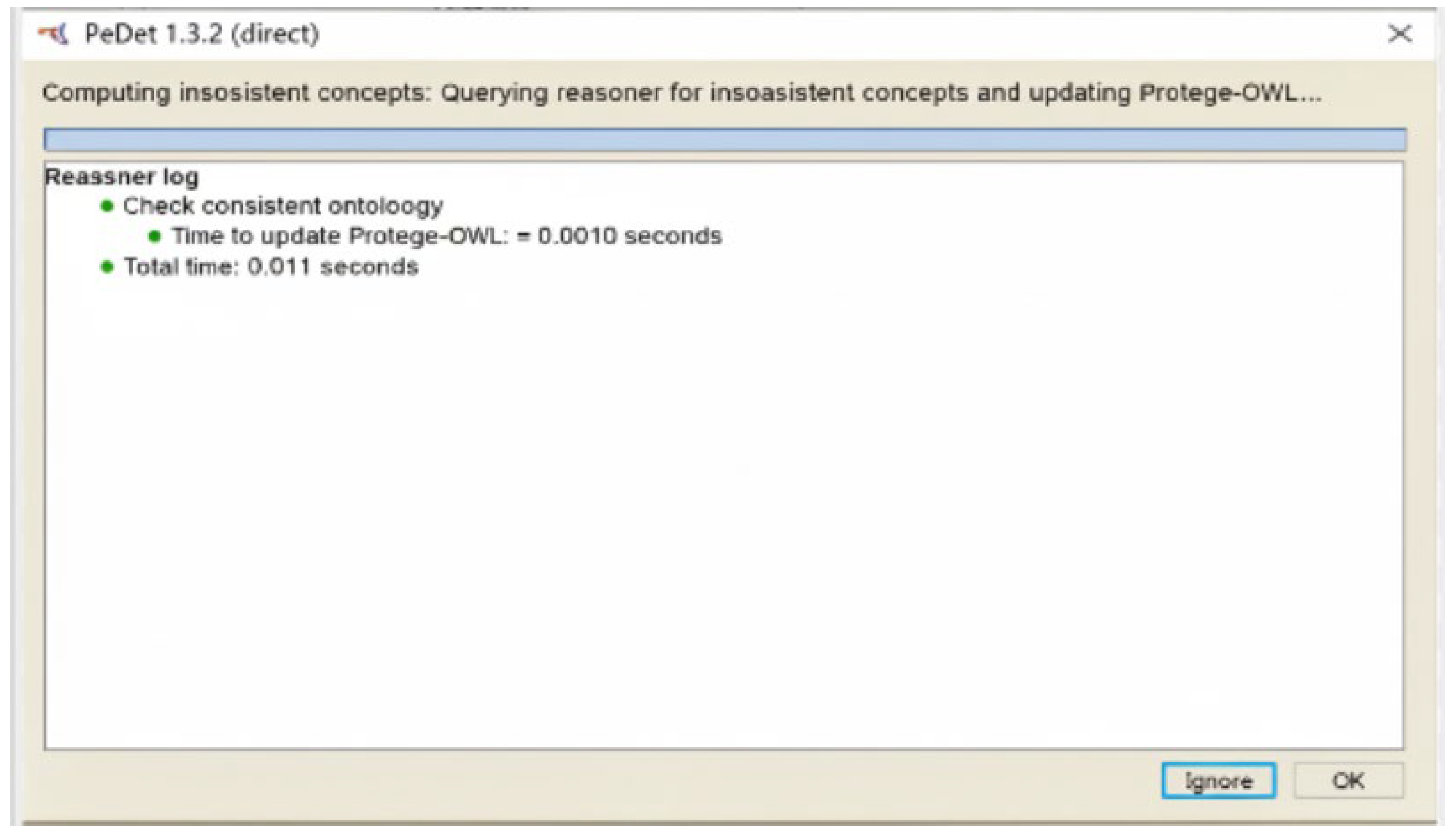
Internal Validation: Logical Consistency of the Ontology
External Validation: Proof of Effectiveness (IDS Ontology-Driven Mitigation PoC)
- Implementation of the Detection Module as Input for Ontology-Based Mitigation
- Dataset:
- ✓
- Data cleaning: removing corrupted data
- ✓
- Data transforming: transform data into numerical features
- ✓
- Labeling: to differentiate the attack classes
- ✓
- Data splitting: split the data into train and test data (70/30)
- -
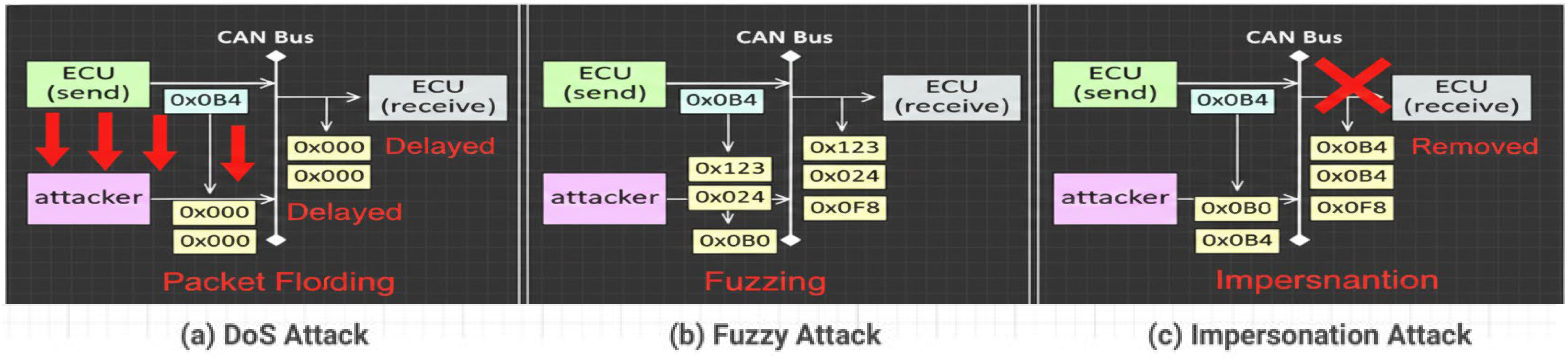
- DoS Attack (High Severity): Upon detection of a high-frequency injection, the reasoner filtered mitigation strategies based on maximum effectiveness against ‘Availability Attacks’. The result instantly selected CAN Bus Traffic Filtering and Rate Limiting as the optimal action.
- -
- Fuzzy Attack (Medium Severity): For messages with spoofed random IDs and data, the ontology identified the attack as a form of ‘Integrity Violation’. The system successfully selected the mitigation: Message Authentication (MAC-based).
- -
- Impersonation Attack (High Integrity Risk): The injection of a forged, known ID was classified as a specific ‘Trust Attack’. The reasoning engine selected the most effective countermeasure: ECU Isolation and/or Revocation of the Impersonated Node.
- (1)
- Identify malicious traffic on the CAN bus by an intrusion detection ML-based,
- (2)
- Recognize the type of attack instantly, and
- (3)
- Use semantic reasoning to decide the appropriate mitigation action without any manual intervention.
6. Discussion
7. Conclusions and Perspectives
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Wu, W.; Li, R.; Xie, G.; An, J.; Bai, Y.; Zhou, J.; Li, K. A Survey of Intrusion Detection for In-Vehicle Networks. IEEE Trans. Intell. Transp. Syst. 2020, 21, 919–933. [Google Scholar] [CrossRef]
- Cho, K.T.; Shin, K.G. Viden: Attacker identification on in-vehicle networks. In Proceedings of the ACM Conference on Computer and Communications Security, Dallas, TX, USA, 30 October–3 November 2017; pp. 1109–1123. [Google Scholar] [CrossRef]
- Taylor, A.; Japkowicz, N.; Leblanc, S. Frequency-based anomaly detection for the automotive CAN bus. In Proceedings of the 2015 World Congress on Industrial Control Systems Security (WCICSS), London, UK, 14–16 December 2015; pp. 45–49. [Google Scholar] [CrossRef]
- Song, H.M.; Kim, H.R.; Kim, H.K. Intrusion detection system based on the analysis of time intervals of CAN messages for in-vehicle network. In Proceedings of the 2016 International Conference on Information Networking ICOIN, Kota Kinabalu, Malaysia, 13–15 January 2016; pp. 63–68. [Google Scholar] [CrossRef]
- Manale, B.; Mazri, T. Intrusion detection method for GPS based on deep learning for autonomous vehicle. Int. J. Electron. Secur. Digit. Forensics 2022, 14, 37–52. [Google Scholar] [CrossRef]
- Bandeira, J.; Bittencourt, I.I.; Espinheira, P.; Isotani, S. FOCA: A Methodology for Ontology Evaluation. arXiv 2017, arXiv:1612.03353. [Google Scholar] [CrossRef]
- Neuhaus, F. What is an Ontology? arXiv 2018, arXiv:1810.09171. [Google Scholar] [CrossRef] [PubMed]
- Filman, R.; Linden, T. SafeBots: A paradigm for software security controls. In Proceedings of the New Security Paradigms Workshop, Lake Arrowhead, CA, USA, 17–20 September 1996; Volume Part F1294, pp. 45–51. [Google Scholar] [CrossRef]
- Denker, G.; Kagal, L.; Finin, T.; Paolucci, M.; Sycara, K. Security for DAML Web Services: Annotation and Matchmaking. In Proceedings of the Semantic Web-ISWC 2003, Sanibel Island, FL, USA, 20–23 October 2003; Fensel, D., Sycara, K., Mylopoulos, J., Eds.; Springer: Berlin/Heidelberg, Germany, 2003; pp. 335–350. [Google Scholar] [CrossRef]
- Simmonds, A.; Sandilands, P.; Van Ekert, L. An ontology for network security attacks. In Lecture Notes in Computer Science; (Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Berlin/Heidelberg, Germany, 2004; Volume 3285, pp. 317–323. [Google Scholar] [CrossRef]
- Kannan, S.; Thangavelu, A.; Kalivaradhan, R. An Intelligent Driver Assistance System (I-DAS) for Vehicle Safety Modelling using Ontology Approach. Int. J. UbiComp 2010, 1, 15–29. [Google Scholar] [CrossRef]
- Stocker, M.; Rönkkö, M.; Kolehmainen, M. Making sense of sensor data using ontology: A discussion for road vehicle classification. In Proceedings of the 6th International Congress on Environmental Modelling and Software, Leipzig, Germany, 1 July 2012. [Google Scholar]
- Fernandez, S.; Hadfi, R.; Ito, T.; Marsa-Maestre, I.; Velasco, J.R. Ontology-Based Architecture for Intelligent Transportation Systems Using a Traffic Sensor Network. Sensors 2016, 16, 1287. [Google Scholar] [CrossRef]
- Xiong, Z.; Dixit, V.V.; Waller, S.T. The development of an ontology for driving context modelling and reasoning. In Proceedings of the IEEE International Conference on Intelligent Transportation Systems, Rio de Janeiro, Brazil, 1–4 December 2016; pp. 13–18. [Google Scholar] [CrossRef]
- Robinson, V.B.; Mackay, D.S. Semantic modeling for the integration of geographic information and regional hydroecological simulation management. Comput. Environ. Urban Syst. 1995, 19, 321–339. [Google Scholar] [CrossRef]
- Seliverstov, A.; Rossetti, R.J.F. An ontological approach to spatio-temporal information modelling in transportation. In Proceedings of the 2015 IEEE 1st International Smart Cities Conference ISC2, Guadalajara, Mexico, 25–28 October 2015. [Google Scholar] [CrossRef]
- Baccigalupo, C.; Plaza, E. Poolcasting: A Social Web Radio Architecture for Group Customisation. In Proceedings of the Third International Conference on Automated Production of Cross Media Content for Multi-Channel Distribution (AXMEDIS’07), Barcelona, Spain, 28–30 November 2007; pp. 115–122. [Google Scholar] [CrossRef]
- Alaya, B.; Sellami, L.; Lorenz, P. An ontological approach to the detection of anomalies in vehicular ad hoc networks. Ad Hoc Netw. 2024, 156, 103417. [Google Scholar] [CrossRef]
- Wang, Y.; Ren, Y.; Qin, H.; Cui, Z.; Zhao, Y.; Yu, H. A Dataset for Cyber Threat Intelligence Modeling of Connected Autonomous Vehicles. Sci. Data 2025, 12, 366. Available online: https://www.nature.com/articles/s41597-025-04439-5 (accessed on 15 April 2024). [CrossRef]
- Hireche, S.; Dennai, A.; Kadri, B. OAIDS: An Ontology-Based Framework for Building an Intelligent Urban Road Traffic Automatic Incident Detection System. SpringerLink. Available online: https://link.springer.com/chapter/10.1007/978-3-030-96311-8_36 (accessed on 15 April 2024).
- Sun, H.; Wang, J.; Weng, J.; Tan, W. KG-ID: Knowledge Graph-Based Intrusion Detection on In-Vehicle Network. IEEE Trans. Intell. Transp. Syst. 2025, 26, 4988–5000. [Google Scholar] [CrossRef]
- Bakare, O.; Karie, N.; Ryan, R.; Murray, I. Towards an Ontological Digital Forensic Investigation Framework for Autonomous Vehicles. In Proceedings of the 2024 6th International Conference on Advancements in Computing (ICAC), Colombo, Sri Lanka, 12–13 December 2024; p. 204. [Google Scholar] [CrossRef]
- Gu, X.; Wu, Q.; Fan, P.; Cheng, N.; Chen, W.; Letaief, K.B. DRL-Based Federated Self-Supervised Learning for Task Offloading and Resource Allocation in ISAC-Enabled Vehicle Edge Computing. Digit. Commun. Netw. 2025, 11, 1614–1627. [Google Scholar] [CrossRef]
- Xie, Y.; Wu, Q.; Fan, P.; Cheng, N.; Chen, W.; Wang, J.; Letaief, K.B. Resource Allocation for Twin Maintenance and Computing Task Processing in Vehicular Edge Computing Network. arXiv 2025, arXiv:2407.07575. [Google Scholar] [CrossRef]
- Bakraouy, Z.; Abbass, W.; Baina, A.; Bellafkih, M. MAS for Services Availability in Cloud of Things Network: Monitoring and Reactivity. In Proceedings of the 12th International Conference on Intelligent Systems: Theories and Applications (SITA’18), Rabat, Morocco, 24 October 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Abdallah, E.E.; Aloqaily, A.; Fayez, H. Identifying Intrusion Attempts on Connected and Autonomous Vehicles: A Survey. Procedia Comput. Sci. 2023, 220, 307–314. [Google Scholar] [CrossRef]
- Loukas, G.; Karapistoli, E.; Panaousis, E.; Sarigiannidis, P.; Bezemskij, A.; Vuong, T. A taxonomy and survey of cyber-physical intrusion detection approaches for vehicles. Ad Hoc Netw. 2019, 84, 124–147. [Google Scholar] [CrossRef]
- Hu, X.; Liu, T.; Shu, T.; Nguyen, D. Spoofing Detection for LiDAR in Autonomous Vehicles: A Physical-Layer Approach. IEEE Internet Things J. 2024, 11, 20673–20689. [Google Scholar] [CrossRef]
- Girdhar, M.; Hong, J.; Moore, J. Cybersecurity of Autonomous Vehicles: A Systematic Literature Review of Adversarial Attacks and Defense Models. IEEE Open J. Veh. Technol. 2023, 4, 417–437. Available online: https://ieeexplore.ieee.org/abstract/document/10097455 (accessed on 16 April 2024). [CrossRef]
- Praseed, A.; Thilagam, P.S. DDoS Attacks at the Application Layer: Challenges and Research Perspectives for Safeguarding Web Applications. IEEE Commun. Surv. Tutor. 2019, 21, 661–685. [Google Scholar] [CrossRef]
- Madhavi, S.; Santhosh, N.C.; Rajkumar, S.; Praveen, R. Pythagorean Fuzzy Sets-based VIKOR and TOPSIS-based multi-criteria decision-making model for mitigating resource deletion attacks in WSNs. J. Intell. Fuzzy Syst. 2023, 44, 9441–9459. [Google Scholar] [CrossRef]
- Hataba, M.; Sherif, A.; Mahmoud, M.; Abdallah, M.; Alasmary, W. Security and Privacy Issues in Autonomous Vehicles: A Layer-Based Survey. IEEE Open J. Commun. Soc. 2022, 3, 811–829. [Google Scholar] [CrossRef]
- Stottelaar, B.G.B. Practical Cyber-Attacks on Autonomous Vehicles. Available online: https://essay.utwente.nl/66766/ (accessed on 30 April 2024).
- He, Q.; Meng, X.; Qu, R. Towards a Severity Assessment Method for Potential Cyber Attacks to Connected and Autonomous Vehicles. J. Adv. Transp. 2020, 2020, 1–15. [Google Scholar] [CrossRef]
- Akowuah, F.; Kong, F. Physical Invariant Based Attack Detection for Autonomous Vehicles: Survey, Vision, and Challenges. In Proceedings of the 2021 Fourth International Conference on Connected and Autonomous Driving (MetroCAD), Detroit, MI, USA, 28–29 April 2021; Available online: https://ieeexplore.ieee.org/abstract/document/9499330 (accessed on 20 March 2024).
- Thing, V.L.L.; Wu, J. Autonomous Vehicle Security: A Taxonomy of Attacks and Defences. In Proceedings of the 2016 IEEE International Conference on Internet of Things IEEE Green Computing and Communications IEEE Cyber, Physical and Social Computing and IEEE Smart Data IThings-GreenCom-CPSCom-Smart Data 2016, Chengdu, China, 15–18 December 2016; pp. 164–170. [Google Scholar] [CrossRef]
- Boumiza, S.; Braham, R. Intrusion Threats and Security Solutions for Autonomous Vehicle Networks. In Proceedings of the 2017 IEEE/ACS 14th International Conference on Computer Systems and Applications (AICCSA), Hammamet, Tunisia, 30 October–3 November 2017; Available online: https://ieeexplore.ieee.org/abstract/document/8308273 (accessed on 25 March 2024).
- Petit, J.; Shladover, S.E. Potential Cyberattacks on Automated Vehicles. IEEE Trans. Intell. Transp. Syst. 2015, 16, 546–556. Available online: https://ieeexplore.ieee.org/abstract/document/6899663 (accessed on 25 March 2024). [CrossRef]
- Golle, P.; Greene, D.; Staddon, J. Detecting and correcting malicious data in VANETs. In Proceedings of the 1st ACM International Workshop on Vehicular Ad Hoc Networks, in VANET ’04, Philadelphia, PA, USA, 1 October 2024; Association for Computing Machinery: New York, NY, USA, 2004; pp. 29–37. [Google Scholar] [CrossRef]
- Schmidt, R.; Leinmüller, T.; Schoch, E.; Held, A.; Schäfer, G. Vehicle Behavior Analysis to Enhance Security in VANETs. Comput. Sci. Eng. 2008. Available online: https://www.semanticscholar.org/paper/Vehicle-Behavior-Analysis-to-Enhance-Security-in-Schmidt-Leinm%C3%BCller/470b806a3e385be3980f5f1e545d30af51b1359a (accessed on 26 March 2024).
- Ghosh, M.; Varghese, A.; Kherani, A.A.; Gupta, A. Distributed Misbehavior Detection in VANETs. In Proceedings of the 2009 IEEE Wireless Communications and Networking Conference, Budapest, Hungary, 5–8 April 2009; pp. 1–6. [Google Scholar] [CrossRef]
- Lingras, S.; Basu, A. The Security of Autonomous Vehicle Software and its National Security Implications. Eur. J. Appl. Sci. Eng. Technol. 2025, 3, 16. [Google Scholar] [CrossRef]
- Rajapaksha, S.; Kalutarage, H.; Al-Kadri, M.O.; Petrovski, A.; Madzudzo, G.; Cheah, M. AI-Based Intrusion Detection Systems for In-Vehicle Networks: A Survey. ACM Comput. Surv. 2023, 55, 237. [Google Scholar] [CrossRef]
- Lundberg, H. Increasing the Trustworthiness of AI-Based In-Vehicle IDS UsingeXplainable AI. 2022. Available online: https://urn.kb.se/resolve?urn=urn:nbn:se:miun:diva-45223 (accessed on 30 March 2024).
- Sharma, P.; Austin, D.; Liu, H. Attacks on Machine Learning: Adversarial Examples in Connected and Autonomous Vehicles. In Proceedings of the 2019 IEEE International Symposium on Technologies for Homeland Security (HST), Woburn, MA, USA, 5–6 November 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Khalid, F.; Hasan, S.R. Chapter 9—Hardware security of autonomous vehicles. In Handbook of Power Electronics in Autonomous and Electric Vehicles; Rashid, M.H., Ed.; Academic Press: Cambridge, MA, USA, 2024; pp. 125–138. [Google Scholar] [CrossRef]
- Sjoberg, K. Resilience and Recovery [Connected and Autonomous Vehicles]. IEEE Veh. Technol. Mag. 2021, 16, 93–96. [Google Scholar] [CrossRef]
- Roche, C. TOTh 2010, Terminology & Ontology: Theories and applications. In TOTh 2010, Terminology & Ontology: Theories and Applications; Institut Porphyre, Savoir et Connaissance: Annecy, France, 2010; Volume 2010, Available online: https://hal.science/hal-01354936 (accessed on 12 June 2024).
- Vanitha, K.; Venkatesh, M.S.; Ravindra, K.; Lakshmi, S.V. The Development Process of the Semantic Web and Web Ontology. Int. J. Adv. Comput. Sci. Appl. 2011, 2, 122–125. [Google Scholar] [CrossRef]
- Poyyamozhi, S.; Yang, R.; Krovi, V.; Rai, R.; Smith, B.; Kasmier, D. Ontology Foundation for the Self-Driving Software Stack. Social Science Research Network: Rochester, NY, USA, 2025; p. 5129199. [Google Scholar] [CrossRef]
- Lee, H.; Jeong, S.H.; Kim, H.K. OTIDS: A Novel Intrusion Detection System for In-vehicle Network by Using Remote Frame. In Proceedings of the 2017 15th Annual Conference on Privacy, Security and Trust (PST), Calgary, AB, Canada, 28–30 August 2017; pp. 57–66. [Google Scholar] [CrossRef]



| Security Technique | Security Measure | Security Requirement | ||
|---|---|---|---|---|
| Confidentiality | Integrity | Availability | ||
| Authentication & Access Control | Multi-factor authentication (MFA) | * | * | * |
| Multi-factor authentication (MFA) | * | * | * | |
| Secure Communication | End-to-end encryption (E2EE) | * | * | |
| Intrusion Prevention Systems (IPS) | * | * | ||
| Blockchain for V2X security | * | * | ||
| AI-Based Intrusion Detection Systems (IDS) | Anomaly-based detection | * | * | |
| Adversarial ML defense techniques | * | * | ||
| Secure Software & Hardware | Secure booting and code signing | * | * | |
| Hardware Security Modules (HSM) | * | * | ||
| Resilience & Recovery Mechanisms | Safety mechanisms | * | * | |
| Redundant systems | * | |||
| Specification Aspect | Description | Justification and Delimitation |
| Knowledge Domain | Cyber security for Autonomous Vehicles (AVs), integrating concepts from general computer security (threats, vulnerabilities, countermeasures). | Focuses the model on the unique communication protocols and layered architectures of modern vehicles. |
| Main Objective | To conceal security heterogeneity and enable automated semantic reasoning for selecting the most appropriate mitigation strategy against identified threats. | Guarantees better interoperability of security policies and decreases risk severity through knowledge-driven defense. |
| Users | Autonomous Vehicle embedded security systems (IDS, Security Managers), security analysts, and researchers in VANETs. | Provides a common, exploitable vocabulary and a formal reasoning engine for real-time applications. |
| Information Sources | Technical documentation on AV security standards, established cyber security taxonomies, and expert knowledge. | Ensures the validity and practical relevance of the concepts and relationships modeled. |
| Scope of the Ontology | Vehicle (Asset types, Components), Threat (Attacks by Layer, Characteristics), Countermeasure (Mitigation techniques), and Risk Level. | Excludes details on raw sensor data, non-security-related driver behavior, and general traffic flow models. |
| Attack Type | Description |
| Fuzzy Attacks | Injecting messages of spoofed random CAN ID and DATA values |
| Impersonation Attacks | Injecting messages of Impersonating node, arbitration ID = ‘0 × 164’. |
| Dos Attack | Message injection with CAN identifier “0 × 000” in a short cycle |
| Non-Attack Conditions | Normal CAN messages. |
| Ontologies | Domain | Granularity | Orientation IDS/Security | Reasoning/Decision | Selection of Mitigation Techniques |
|---|---|---|---|---|---|
| [8] | General security | Average—generic primitives | Conceptual IDS | No decision-making reasoning related to the attack | No |
| [9] | Authentication/Integrity | Low—web service security only | No | Semantic matchmaking | No |
| [10] | Wired network | Average—threats/vulnerabilities | IDS (attack catalog) | Description only | No |
| [11] | Driving assistance/alerts | High—driving context | No IDS | Context-dependent alert messages | No |
| [13] | Traffic Infrastructure | Average | No | No | No |
| [14] | Vehicle context/sensors | Average—scenes, lanes, sensors | No | No | No |
| [17,18] | Network anomalies | Average—network anomalies | Baseline IDS | Anomalies Detection | No |
| [21] | CAN Attack | High—signals and frames | IDS-oriented CAN attack | Reasoning on CAN Bus | No |
| Proposed Ontology | Autonomous vehicle safety + IDS | High—attacks, intrusion characteristics, methods, and countermeasures | IDS ML + ontological reasoning | decision engine (SPARQL reasoning) | Automatic selection of optimal mitigation |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Published by MDPI on behalf of the World Electric Vehicle Association. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Boughanja, M.; Bakraouy, Z.; Mazri, T.; Srhir, A. Enhancing Intrusion Detection in Autonomous Vehicles Using Ontology-Driven Mitigation. World Electr. Veh. J. 2025, 16, 642. https://doi.org/10.3390/wevj16120642
Boughanja M, Bakraouy Z, Mazri T, Srhir A. Enhancing Intrusion Detection in Autonomous Vehicles Using Ontology-Driven Mitigation. World Electric Vehicle Journal. 2025; 16(12):642. https://doi.org/10.3390/wevj16120642
Chicago/Turabian StyleBoughanja, Manale, Zineb Bakraouy, Tomader Mazri, and Ahmed Srhir. 2025. "Enhancing Intrusion Detection in Autonomous Vehicles Using Ontology-Driven Mitigation" World Electric Vehicle Journal 16, no. 12: 642. https://doi.org/10.3390/wevj16120642
APA StyleBoughanja, M., Bakraouy, Z., Mazri, T., & Srhir, A. (2025). Enhancing Intrusion Detection in Autonomous Vehicles Using Ontology-Driven Mitigation. World Electric Vehicle Journal, 16(12), 642. https://doi.org/10.3390/wevj16120642








