Interest Flooding Attacks in Named Data Networking and Mitigations: Recent Advances and Challenges
Abstract
1. Introduction
- Establishing a comprehensive taxonomy of IFA variants that categorizes attacks in multiple dimensions, including source origin, intensity patterns, and target layers, and examining how attack sophistication has evolved from simple flooding to advanced collusive models over the past five years. This taxonomy framework enables systematic analysis of attack characteristics and facilitates the development of targeted countermeasures for specific threat scenarios.
- Performing a critical evaluation of the seven detection and mitigation strategies published between 2013 and 2024, organizing these approaches into five primary categories based on their core methodologies. Our analysis goes beyond simple cataloging by assessing the effectiveness, computational overhead, and deployment feasibility of rate-limiting strategies, PIT management techniques, machine learning approaches, reputation systems, and blockchain-based solutions. The evaluation includes performance comparisons where quantitative data is available and identifies the operational trade-offs inherent in each approach.
- Examining domain-specific adaptations of IFA countermeasures for resource-constrained environments, with particular focus on IoT deployments, wireless sensor networks (WSNs), and vehicular networking scenarios. This analysis addresses the practical challenges of implementing security mechanisms within computational and energy limitations while maintaining real-time performance requirements.
- Analyzing the evaluation methodologies and performance metrics employed in the reviewed literature, by identifying inconsistencies in benchmarking approaches, and highlighting the need for standardized testing frameworks. Our examination includes the evaluation of simulation environments, experimental parameters, and real-world deployment considerations that affect the practical applicability of the proposed solutions.
- Identifying five critical research directions that address current limitations in IFA defense mechanisms. These directions encompass the development of adaptive countermeasures against evolving attack strategies, integration of privacy-preserving detection techniques for encrypted content scenarios, optimization for real-time constraints in edge computing environments, establishment of standardized evaluation frameworks for reproducible research, and design of hybrid defense approaches that combine multiple mitigation strategies for enhanced effectiveness.
2. NDN Architecture and Vulnerability to Interest Flooding
2.1. NDN Architecture Fundamentals
2.2. Interest Flooding Attack Vulnerability Analysis
- PIT Resource Exhaustion Mechanisms: The finite capacity of PIT represents the main vulnerability target in IFA. Each interest packet consumes a PIT entry until either a corresponding data packet arrives or the entry is canceled due to unfilled requests. Attackers can exploit the PIT consuming mechanism by generating large volumes of interest packets for non-existent or deliberately unsatisfiable content, causing PIT entries to accumulate until router memory resources are exhausted [11,16]. The packet exhaustion prevents legitimate interest packets from receiving PIT entries, effectively denying service to legitimate users without requiring the high bandwidth consumption typically associated with traditional flooding attacks.
- Pull-Based Communication Exploitation: NDN’s pull-based model ensures that data flows through the network only upon explicit request through interest packets. Although this design improves control over data dissemination and mitigates specific unsolicited data delivery attacks, it creates opportunities for abuse through interest manipulation [17]. Attackers can generate high volumes of interest packets for non-existent or rarely accessed content, knowing these requests cannot be satisfied with existing data packets. The resulting accumulation of unsatisfiable interests leads to resource exhaustion and degraded service for legitimate network users [18].
- Stateful Forwarding Vulnerabilities: The distinction between NDN’s stateful forwarding and traditional IP routing creates unique attack opportunities. Conventional IP networks maintain minimal per-packet state, making them less susceptible to state exhaustion attacks. NDN routers must maintain detailed information about each forwarded interest packet, including content names and interface mappings, until the corresponding data packet completes the transaction [19,20]. The persistent state maintenance requirement enables attackers to consume router resources through coordinated interest flooding without requiring successful data retrieval or high bandwidth utilization.
3. Interest Flooding Attack: Concept and Taxonomy
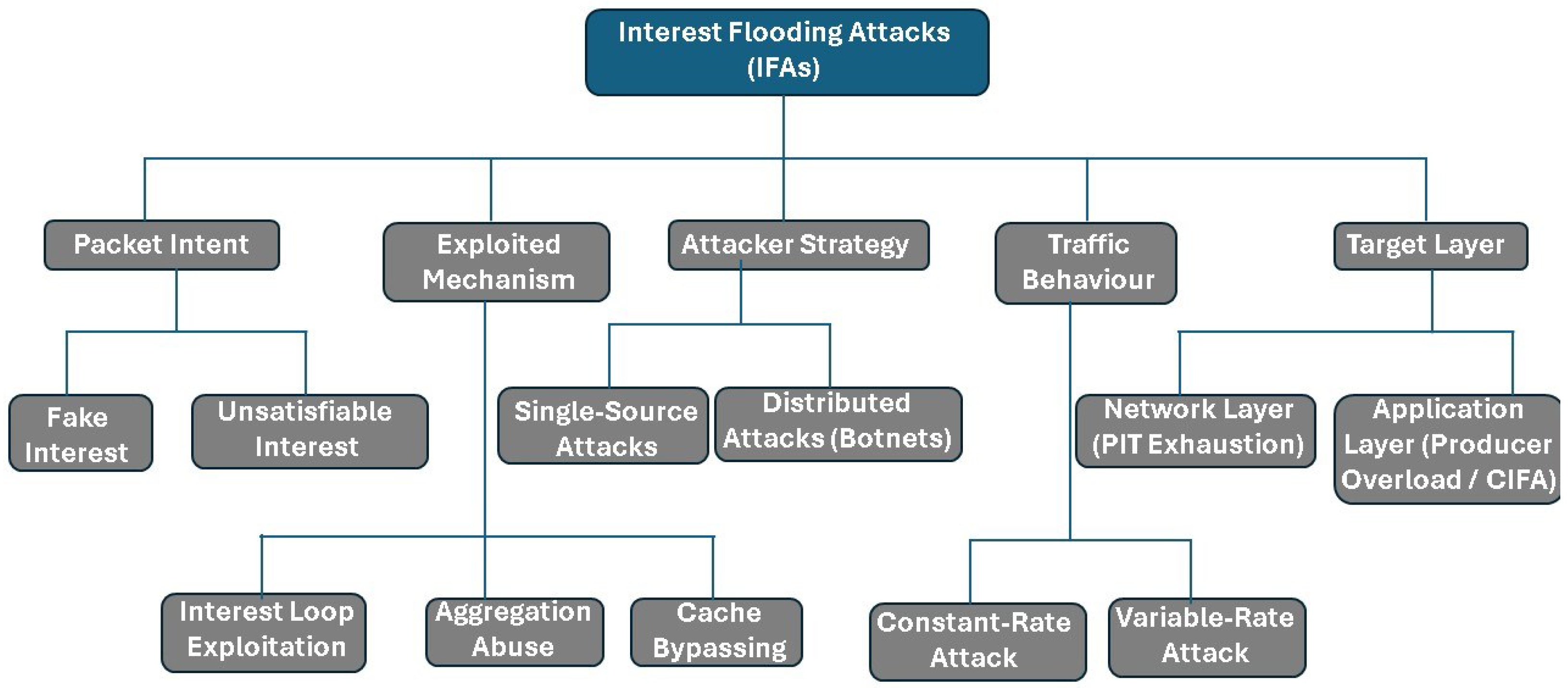
3.1. Types of IFAs
3.1.1. Fake Interest Attacks
3.1.2. Unsatisfiable Interests
3.1.3. Interest Loops or Aggregation Abuse
3.2. Taxonomy of IFA
3.2.1. Source of the Attack
- Single-Source Attacks: In these scenarios, a single adversary sends a large number of malicious-interest packets with the intent of overconsuming network resources. This method resembles traditional DoS attacks, in which a single system inundates a target with excessive traffic, leading to service degradation or unavailability [18].
- Distributed Attacks: Distributed attacks involve multiple compromised nodes, often orchestrated as a botnet, to flood the network from various points [28]. The botnet approach mirrors DDoS attacks, where numerous systems coordinate to overwhelm a target, complicating detection and mitigation due to the dispersed nature of attack vectors and the increased volume of malicious traffic [29].
3.2.2. Attack Intensity
3.2.3. Target Layer
- Network-Layer IFAs (PIT Exhaustion Attacks): NDN routers maintain per-packet state in the PIT, which records each unsatisfied interest’s name and incoming interface until a matching data is returned. This stateful design, while enabling robust multipath forwarding and loop prevention, is a double-edged sword: the PIT has a finite size and can be overwhelmed. Attackers exploit this by sending spoofed interests for non-existent content names (or otherwise unsatisfiable requests) at high rates, filling PIT entries and consuming bandwidth [33], while enabling robust multipath forwarding and loop prevention. As a result, the router’s memory is exhausted, and new interests (even from legitimate users) cannot be added to the PIT. In essence, the PIT exhaustion attack targets the availability of the network layer by incapacitating the ability of the routers to forward requests [18,33]. The malicious consumers flood the network with unsatisfiable interest packets, exhausting router resources. Attackers request non-existing content, causing PITs to fill up, leading to packet drops and service disruptions. Distributed and slow-start IFAs worsen detection challenges, severely degrading NDN performance.
- Application Layer (Producer-Targeted Attacks): Traditional IFAs primarily target routers; however, attackers can also exploit the application layer by overwhelming content producers. In NDN, producers generate data packets upon receiving interest requests. Attackers flood a producer with interests, exhausting its computational and storage resources. Even if PITs remain stable, excessive processing loads can cause service disruption [8,34]. Two primary vulnerabilities facilitate producer-targeted IFAs:
- Computational Overhead: Every data packet requires cryptographic signing, making dynamic content especially vulnerable.
- Cache Bypassing: Attackers manipulate interest names to prevent caching, forcing producers to serve every request. An attacker can append random components to a popular content name (e.g., /news/video.mp4?session=XYZ), ensuring each request reaches the producer instead of being satisfied by caches.
4. State of the Art Detection and Mitigation Strategies
4.1. Rate-Limiting Strategies
4.2. PIT Management Strategies
4.3. Machine Learning and AI-Based Techniques
4.4. Reputation and Trust-Based Systems
4.5. Blockchain-Based Approaches
4.6. Performance Evaluation
5. Applications and Use Cases of NDN
5.1. IFA Defense in IoT Networks (NDN of Things)
5.1.1. Smart Home
5.1.2. Healthcare IoT
5.1.3. Industrial IoT (IIoT)
5.2. Wireless Sensor Networks and NDN
6. Open Challenges and Future Research Directions
6.1. High False Positive Rates
6.2. NDN Privacy
6.3. Real-Time Constraints in IoT and Edge Computing
6.4. Resource Constraints of IoT Devices
6.5. Energy-Efficient
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| AI | Artificial Intelligence |
| ANN | Artificial Neural Network |
| CHOKe | CHOose and Keep for responsive flows |
| CS | Content Store |
| CUSUM | Cumulative Sum |
| DoS | Denial of Service |
| DDoS | Distributed Denial of Service |
| DPE | Decoupling Pending Entries |
| EWMA | Exponential Weighted Moving Average |
| FIB | Forwarding Information Base |
| GNN | Graph Neural Network |
| HSL | Hash-based Security Label |
| ICN | Information-Centric Networking |
| IFA | Interest Flooding Attack |
| IfNoT | Interest flooding mitigation for NDNoT |
| IIoT | Industrial Internet of Things |
| IoT | Internet of Things |
| ISR | Interest Satisfaction Ratio |
| ML | Machine Learning |
| NACK | Negative Acknowledgment |
| NCR | Named Content Retrieval |
| NDN | Named Data Networking |
| NDNoT | Named Data Networking of Things |
| PIT | Pending Interest Table |
| PSO | Particle Swarm Optimization |
| RBF | Radial Basis Function |
| RTOS | Real-Time Operating System |
| SBF | Stable Bloom Filter |
| S-PIT | Stable Bloom Filter–enhanced PIT |
| WSN | Wireless Sensor Network |
References
- Ahlgren, B.; Dannewitz, C.; Imbrenda, C.; Kutscher, D.; Ohlman, B. A survey of information-centric networking. IEEE Commun. Mag. 2012, 50, 26–36. [Google Scholar] [CrossRef]
- Cisco. Cisco Annual Internet Report (2018–2023) White Paper; Cisco: San Jose, CA, USA, 2020; Volume 10, pp. 1–35. [Google Scholar]
- Xylomenos, G.; Ververidis, C.N.; Siris, V.A.; Fotiou, N.; Tsilopoulos, C.; Vasilakos, X.; Katsaros, K.V.; Polyzos, G.C. A survey of information-centric networking research. IEEE Commun. Surv. Tutor. 2013, 16, 1024–1049. [Google Scholar] [CrossRef]
- Baccelli, E.; Mehlis, C.; Hahm, O.; Schmidt, T.C.; Wählisch, M. Information centric networking in the IoT: Experiments with NDN in the wild. In Proceedings of the 1st ACM Conference on Information-Centric Networking, Paris, France, 24–26 September 2014; pp. 77–86. [Google Scholar]
- Jacobson, V.; Smetters, D.K.; Thornton, J.D.; Plass, M.F.; Briggs, N.H.; Braynard, R.L. Networking named content. In Proceedings of the 5th International Conference on Emerging Networking Experiments and Technologies, Rome, Italy, 1–4 December 2009; pp. 1–12. [Google Scholar]
- Zhang, L.; Afanasyev, A.; Burke, J.; Jacobson, V.; Claffy, K.; Crowley, P.; Papadopoulos, C.; Wang, L.; Zhang, B. Named data networking. ACM SIGCOMM Comput. Commun. Rev. 2014, 44, 66–73. [Google Scholar] [CrossRef]
- Zhu, K.; Chen, Z.; Yan, W.; Zhang, L. Security attacks in named data networking of things and a blockchain solution. IEEE Internet Things J. 2018, 6, 4733–4741. [Google Scholar] [CrossRef]
- Benmoussa, A.; Kerrache, C.A.; Lagraa, N.; Mastorakis, S.; Lakas, A.; Tahari, A.E.K. Interest flooding attacks in named data networking: Survey of existing solutions, open issues, requirements, and future directions. ACM Comput. Surv. 2022, 55, 1–37. [Google Scholar] [CrossRef]
- Al-Share, R.A.; Shatnawi, A.S.; Al-Duwairi, B. Detecting and mitigating collusive interest flooding attacks in named data networking. IEEE Access 2022, 10, 65996–66017. [Google Scholar] [CrossRef]
- Pu, C.; Zhu, P. Defending against flooding attacks in the internet of drones environment. In Proceedings of the 2021 IEEE Global Communications Conference (GLOBECOM), Madrid, Spain, 7–11 December 2021; pp. 1–6. [Google Scholar]
- Lee, R.T.; Leau, Y.B.; Park, Y.J.; Anbar, M. A survey of interest flooding attack in named-data networking: Taxonomy, performance and future research challenges. IETE Tech. Rev. 2022, 39, 1027–1045. [Google Scholar] [CrossRef]
- Alubady, R.; Hassan, S.; Habbal, A. Pending interest table control management in Named Data Network. J. Netw. Comput. Appl. 2018, 111, 99–116. [Google Scholar] [CrossRef]
- Sucipto, A.; Ahdan, S.; Syambas, N.R. PIT Performance Measurement using NFD Pipeline Parameters in Named Data Networking (NDN). In Proceedings of the 2024 10th International Conference on Wireless and Telematics (ICWT), Batam, Indonesia, 4–5 July 2024; pp. 1–5. [Google Scholar]
- Kaur, R.; Singh, A.; Singh, A.; Goyal, A.; Singh, A.; Batra, S. An efficient pending interest table content search in NDN through stable bloom filter. Comput. J. 2024, 67, 941–946. [Google Scholar] [CrossRef]
- Khelifi, H.; Luo, S.; Nour, B.; Shah, S.C. Security and privacy issues in vehicular named data networks: An overview. Mob. Inf. Syst. 2018, 2018, 5672154. [Google Scholar] [CrossRef]
- Jeet, R.; Arun Raj Kumar, P. A survey on interest packet flooding attacks and its countermeasures in named data networking. Int. J. Inf. Secur. 2022, 21, 1163–1187. [Google Scholar] [CrossRef]
- Ullah, S.S.; Hussain, S.; Ali, I.; Khattak, H.; Mastorakis, S. Mitigating content poisoning attacks in named data networking: A survey of recent solutions, limitations, challenges and future research directions. Artif. Intell. Rev. 2024, 58, 42. [Google Scholar] [CrossRef]
- Afanasyev, A.; Mahadevan, P.; Moiseenko, I.; Uzun, E.; Zhang, L. Interest flooding attack and countermeasures in named data networking. In Proceedings of the 2013 IFIP Networking Conference, Brooklyn, NY, USA, 22–24 May 2013; pp. 1–9. [Google Scholar]
- Theeranantachai, S.; Zhang, B.; Zhang, L. NDN’s Stateful Forwarding Plane in the Presence of Ground-Satellite Handovers. In Proceedings of the 2024 IEEE 32nd International Conference on Network Protocols (ICNP), Charleroi, Belgium, 28–31 October 2024; pp. 1–11. [Google Scholar]
- Yi, C.; Afanasyev, A.; Moiseenko, I.; Wang, L.; Zhang, B.; Zhang, L. A case for stateful forwarding plane. Comput. Commun. 2013, 36, 779–791. [Google Scholar] [CrossRef]
- Shi, Z.; Xu, Y.; Ma, M.; Zhang, Y. An EWMA-Based Mitigation Scheme Against Interest Flooding Attacks in Named Data Networks. In Proceedings of the International Conference on Intelligent Computing, Tianjin, China, 5–8 August 2024; pp. 158–167. [Google Scholar]
- Benarfa, A.; Hassan, M.; Losiouk, E.; Compagno, A.; Yagoubi, M.B.; Conti, M. ChoKIFA+: An early detection and mitigation approach against interest flooding attacks in NDN. Int. J. Inf. Secur. 2021, 20, 269–285. [Google Scholar] [CrossRef]
- Kumar, N.; Singh, A.K.; Srivastava, S. Fast Detection and Traceback-based Mitigation of Interest Flooding Attack. SN Comput. Sci. 2025, 6, 1–15. [Google Scholar] [CrossRef]
- Buragohain, M.; Nandi, S. Demystifying security on NDN: A survey of existing attacks and open research challenges. In The “Essence” of Network Security: An End-to-End Panorama; Springer: Singapore, 2021; pp. 241–261. [Google Scholar]
- Yu, L.; Ai, H.; Choi, D.O. Countermeasures of interest flooding attack in named data networking: A survey. Int. J. Electr. Eng. Educ. 2023, 60, 279–295. [Google Scholar] [CrossRef]
- Zhao, L.; Cheng, G.; Hu, X.; Wu, H.; Gong, J.; Yang, W.; Fan, C. An insightful experimental study of a sophisticated interest flooding attack in NDN. In Proceedings of the 2018 1st IEEE International Conference on Hot Information-Centric Networking (HotICN), Shenzhen, China, 15–17 August 2018; pp. 121–127. [Google Scholar]
- Rahman, M.A.; Liang, T.; Zhang, B. BLEnD: Improving NDN performance over wireless links using interest bundling. In Proceedings of the MILCOM 2021-2021 IEEE Military Communications Conference (MILCOM), San Diego, CA, USA, 29 November–2 December 2021; pp. 432–437. [Google Scholar]
- Compagno, A.; Conti, M.; Gasti, P.; Tsudik, G. Poseidon: Mitigating interest flooding DDoS attacks in named data networking. In Proceedings of the 38th Annual IEEE Conference on Local Computer Networks, Sydney, Australia, 21–24 October 2013; pp. 630–638. [Google Scholar]
- Wah, C.H.; Chang, R.K.C. Defending against flooding-based distributed denial-of-service attacks: A tutorial. IEEE Commun. Mag. 2002, 40, 42–51. [Google Scholar]
- Signorello, S.; Marchal, S.; Francois, J.; Festor, O.; State, R. Advanced interest flooding attacks in named-data networking. In Proceedings of the 2017 IEEE 16th International Symposium on Network Computing and Applications (NCA), Cambridge, MA, USA, 30 October–1 November 2017; pp. 1–10. [Google Scholar]
- Wang, K.; Guo, D.; Quan, W. Analyzing NDN NACK on interest flooding attack via SIS epidemic model. IEEE Syst. J. 2019, 14, 1862–1873. [Google Scholar] [CrossRef]
- Kumari, M.K.; Tripathi, N. Detecting interest flooding attacks in NDN: A probability-based event-driven approach. Comput. Secur. 2025, 148, 104124. [Google Scholar] [CrossRef]
- Cheng, G.; Zhao, L.; Hu, X.; Zheng, S.; Wu, H.; Fan, C. A network-wide view-based detection and mitigation of a sophisticated Interest Flooding Attack. EURASIP J. Wirel. Commun. Netw. 2020, 2020, 1–18. [Google Scholar] [CrossRef]
- Karami, A.; Guerrero-Zapata, M. A hybrid multiobjective rbf-pso method for mitigating dos attacks in named data networking. Neurocomputing 2015, 151, 1262–1282. [Google Scholar] [CrossRef]
- Hidouri, A.; Hajlaoui, N.; Touati, H.; Hadded, M.; Muhlethaler, P. A survey on security attacks and intrusion detection mechanisms in named data networking. Computers 2022, 11, 186. [Google Scholar] [CrossRef]
- Named Data Networking Project. Named Data Networking (NDN) Project FAQ. 2025. Available online: https://named-data.net/project/faq/ (accessed on 3 April 2025).
- Dong, J.; Wang, K.; Quan, W.; Yin, H. InterestFence: Simple but efficient way to counter interest flooding attack. Comput. Secur. 2020, 88, 101628. [Google Scholar] [CrossRef]
- Wang, Y.; Rozhnova, N.; Narayanan, A.; Oran, D.; Rhee, I. An improved hop-by-hop interest shaper for congestion control in named data networking. ACM SIGCOMM Comput. Commun. Rev. 2013, 43, 55–60. [Google Scholar] [CrossRef]
- Alston, A.; Refaei, T. Neutralizing interest flooding attacks in named data networks using cryptographic route tokens. In Proceedings of the 2016 IEEE 15th International Symposium on Network Computing and Applications (NCA), Cambridge, MA, USA, 31 October–2 November 2016; pp. 85–88. [Google Scholar]
- Ghali, C.; Tsudik, G.; Uzun, E. Needle in a haystack: Mitigating content poisoning in named-data networking. In Proceedings of the NDSS Workshop on Security of Emerging Networking Technologies (SENT), San Diego, CA, USA, 23 February 2014; pp. 1–10. [Google Scholar]
- Magsi, A.H.; Mohsan, S.A.H.; Muhammad, G.; Abbasi, S. A machine learning-based interest flooding attack detection system in vehicular named data networking. Electronics 2023, 12, 3870. [Google Scholar] [CrossRef]
- Rabari, J.; Kumar, A.R.P. FIFA: Fighting against interest flooding attack in NDN-based VANET. In Proceedings of the 2021 International Wireless Communications and Mobile Computing (IWCMC), Harbin, China, 28 June–2 July 2021; pp. 1539–1544. [Google Scholar]
- Liang, H.; Burgess, L.; Liao, W.; Wang, Q.; Yu, W. On detecting interest flooding attacks in named data networking (ndn)–based iot searches. In AI, Machine Learning and Deep Learning; CRC Press: Boca Raton, FL, USA, 2023; pp. 259–276. [Google Scholar]
- Ogunbunmi, S.; Chen, Y.; Blasch, E.; Chen, G. A survey on reputation systems for uav networks. Drones 2024, 8, 253. [Google Scholar] [CrossRef]
- Ogunbunmi, S.; Hatmai, M.; Xu, R.; Chen, Y.; Blasch, E.; Ardiles-Cruz, E.; Aved, A.; Chen, G. A lightweight reputation system for uav networks. In Proceedings of the International Conference on Security and Privacy in Cyber-Physical Systems and Smart Vehicles, Chicago, IL, USA, 12–16 October 2023; pp. 114–129. [Google Scholar]
- Qu, Q.; Ogunbunmi, S.; Hatami, M.; Xu, R.; Chen, Y.; Chen, G.; Blasch, E. A digital twins enabled reputation system for microchain-based uav networks. In Proceedings of the 2023 IEEE 12th International Conference on Cloud Networking (CloudNet), Hoboken, NJ, USA, 1–3 November 2023; pp. 428–432. [Google Scholar]
- Sivaganesan, D. A data driven trust mechanism based on blockchain in IoT sensor networks for detection and mitigation of attacks. J. Trends Comput. Sci. Smart Technol. (TCSST) 2021, 3, 59–69. [Google Scholar]
- Bilgili, S.; Demir, A.K.; Alam, S. Ifnot: An approach towards mitigating interest flooding attacks in named data networking of things. Internet Things 2024, 25, 101076. [Google Scholar] [CrossRef]
- He, Y.; Ma, Y.; Hu, Q.; Zhou, Z.; Xiao, K.; Wang, C. Lightweight transmission behavior audit scheme for NDN Industrial Internet identity resolution and transmission based on blockchain. Electronics 2023, 12, 2538. [Google Scholar] [CrossRef]
- Din, M.S.U.; Rehman, M.A.U.; Kim, B.S. CIDF-WSN: A collaborative interest and data forwarding strategy for named data wireless sensor networks. Sensors 2021, 21, 5174. [Google Scholar] [CrossRef]
- Bukhowah, R.; Aljughaiman, A.; Rahman, M.H. Detection of dos attacks for IoT in information-centric networks using machine learning: Opportunities, challenges, and future research directions. Electronics 2024, 13, 1031. [Google Scholar] [CrossRef]
- Dong, J.; Wang, K.; Lyu, Y.; Jiao, L.; Yin, H. InterestFence: Countering interest flooding attacks by using hash-based security labels. In Proceedings of the Algorithms and Architectures for Parallel Processing: 18th International Conference, ICA3PP 2018, Guangzhou, China, 15–17 November 2018; Proceedings, Part IV 18. Springer: Berlin/Heidelberg, Germany, 2018; pp. 527–537. [Google Scholar]
- Oikonomou, G.; Duquennoy, S.; Elsts, A.; Eriksson, J.; Tanaka, Y.; Tsiftes, N. The Contiki-NG open source operating system for next generation IoT devices. SoftwareX 2022, 18, 101089. [Google Scholar] [CrossRef]
- Wang, X.; Cai, S. Edge-assisted NDN-based IoT framework with provider and consumer mobility support. IEEE Trans. Netw. Sci. Eng. 2022, 9, 1713–1725. [Google Scholar] [CrossRef]
- Wang, X.; Cai, S. Secure healthcare monitoring framework integrating NDN-based IoT with edge cloud. Future Gener. Comput. Syst. 2020, 112, 320–329. [Google Scholar] [CrossRef]
- Habibzadeh, H.; Dinesh, K.; Shishvan, O.R.; Boggio-Dandry, A.; Sharma, G.; Soyata, T. A survey of healthcare Internet of Things (HIoT): A clinical perspective. IEEE Internet Things J. 2019, 7, 53–71. [Google Scholar] [CrossRef] [PubMed]
- Dhingra, S.; Madda, R.B.; Gandomi, A.H.; Patan, R.; Daneshmand, M. Internet of Things mobile–air pollution monitoring system (IoT-Mobair). IEEE Internet Things J. 2019, 6, 5577–5584. [Google Scholar] [CrossRef]
- Askar, N.A.; Habbal, A. RLEAFS: Reinforcement Learning based Energy Aware Forwarding Strategy for NDN based IoT Networks. IEEE Access 2024, 12, 177173–177188. [Google Scholar] [CrossRef]
- Karim, S.M.; Habbal, A.; Chaudhry, S.A.; Irshad, A. BSDCE-IoV: Blockchain-based secure data collection and exchange scheme for IoV in 5G environment. IEEE Access 2023, 11, 36158–36175. [Google Scholar] [CrossRef]


| Attack Type | Description | Target | Source | Rate |
|---|---|---|---|---|
| Fake Interest | Requests for non-existent content | Network layer | Single/Distributed | Constant/Variable |
| Unsatisfiable Interest | Exploits filters to block matching data | Network layer | Distributed | Constant |
| Interest Loops | Abuses aggregation/routing to create loops | Network layer | Single | Variable |
| Collusive IFA (CIFA) | Producer cooperates with attacker | Application layer | Distributed | Variable |
| Cache Bypassing Attack | Uses unique suffixes to bypass cache | Application layer | Single | Constant |
| Technique | Main Idea | Strengths | Weaknesses | Computing Complexity |
|---|---|---|---|---|
| Rate Limiting | Throttle interfaces based on unsatisfied interest rate | Simple, lightweight, easy to deploy | May penalize legitimate bursts of traffic | Low |
| PIT Management | Modify or bypass PIT storage to reduce overload | Targets core vulnerability directly | Risks breaking interest–data matching semantics | Medium |
| ML/AI-Based | Learn and classify traffic patterns as normal or malicious | Adaptive to evolving attacks, detects stealthy behavior | Requires training data, high resource usage | High |
| Trust/Reputation | Score consumers based on behavior history | Gradual mitigation, works in distributed settings | Cold-start problem, susceptible to Sybil or collusion | Medium |
| Blockchain-Based | Use shared ledgers or smart contracts to validate behavior | Tamper-proof, ensures accountability and traceability | High latency, storage, and consensus overhead | High |
| Application Domain | Recommended Mitigation Approaches |
|---|---|
| Smart Homes | Rate limiting, PIT management, content-agnostic filtering |
| Healthcare IoT | Lightweight ML detection, trust/reputation scoring, flow-based filtering |
| Industrial IoT (IIoT) | Stateless detection, adaptive rate control, collaborative trust systems |
| NDNoT (NDN over IoT) | ML + caching strategies, low-latency interest shaping, PIT pruning |
| Wireless Sensor Networks | Rule-based detection, periodic PIT flushing, constrained rate-limiting |
| Challenge | Why It Matters | What’s Needed | Future Direction |
|---|---|---|---|
| High False Positives | Can block legitimate users | Adaptive thresholding, behavior modeling | Adaptive baselines |
| NDN Privacy vs. Detection | Encrypted names hide attacker behavior | Content-agnostic or zero-knowledge detection | Cryptographic techniques |
| Real-Time IoT Constraints | Slow methods can not run on microcontrollers | RTOS-compatible lightweight algorithms | Interrupt-driven detection mechanisms |
| Lack of Evaluation Standards | No uniform metrics across studies | Shared testbeds, benchmark datasets | Edge-assisted NDN-based IoT framework |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ogunbunmi, S.; Chen, Y.; Zhao, Q.; Nagothu, D.; Wei, S.; Chen, G.; Blasch, E. Interest Flooding Attacks in Named Data Networking and Mitigations: Recent Advances and Challenges. Future Internet 2025, 17, 357. https://doi.org/10.3390/fi17080357
Ogunbunmi S, Chen Y, Zhao Q, Nagothu D, Wei S, Chen G, Blasch E. Interest Flooding Attacks in Named Data Networking and Mitigations: Recent Advances and Challenges. Future Internet. 2025; 17(8):357. https://doi.org/10.3390/fi17080357
Chicago/Turabian StyleOgunbunmi, Simeon, Yu Chen, Qi Zhao, Deeraj Nagothu, Sixiao Wei, Genshe Chen, and Erik Blasch. 2025. "Interest Flooding Attacks in Named Data Networking and Mitigations: Recent Advances and Challenges" Future Internet 17, no. 8: 357. https://doi.org/10.3390/fi17080357
APA StyleOgunbunmi, S., Chen, Y., Zhao, Q., Nagothu, D., Wei, S., Chen, G., & Blasch, E. (2025). Interest Flooding Attacks in Named Data Networking and Mitigations: Recent Advances and Challenges. Future Internet, 17(8), 357. https://doi.org/10.3390/fi17080357









