Privacy Framework for the Development of IoT-Based Systems
Abstract
1. Introduction
- Classification of existing research: We categorized articles on IoTS privacy issues into different perspectives, simplifying the topic for readers and providing essential background on its challenges and opportunities.
- Proposal of a methodological approach: A systematic approach is presented to help developers extract privacy requirements during the IoTS development process.
- Improvement of existing privacy guidelines: We have critically reviewed and updated existing privacy guidelines.
- Evaluation of effectiveness: The effectiveness of the newly created and improved privacy guidelines was measured using a questionnaire.
2. Motivation
- Guidelines should be better explained: According to Perera et al. [22], who conducted several experiments based on existing guidelines, there is a need to simplify existing recommendations and present them in a clearer and more accessible way to developers.
- The design of IoTSs by software engineers is influenced by their own expertise: Developers tend to rely on their own background and expertise when selecting and applying privacy policies, which can lead to incorrect design decisions during the development process. To address this issue, it is necessary to establish a comprehensive repository of detailed information on privacy guidelines, their implementation, and best practices. Such a resource could enable developers to search for guidance, ensuring consistency in their design approach and ultimately leading to more robust privacy-enhanced applications.
- Lack of a clear approach to implementing the guidelines: After our analysis of the work presented by Perera et al. [22], it has become clear that developers need a structured roadmap that outlines the necessary steps to be followed to extract privacy concerns during the development phases of IoTS projects. Such a methodological approach should provide a well-defined framework, complete with tools and guidance, to facilitate the integration of privacy principles based on well-established guidelines.
- Minimize the number of privacy guidelines: Reducing the number of privacy policies allows developers to focus on key objectives (i.e., the goals pursued by the respective policies), which should help them to identify and address critical privacy concerns more effectively. The process of policy minimization involves filtering, reviewing, and validating existing privacy policies. This effort should be undertaken by security and privacy experts in the IoTS field, both from academia and industry. Their feedback will be instrumental in refining the current privacy guidelines and presenting a final, curated set of them. In addition, a survey will be conducted to assess the complexity of the current guidelines. The results of this survey will be analyzed and integrated into our research to further refine the guidelines and ensure that they are both practical and understandable for developers.
3. Background
3.1. IoTS Non-Functional Requirements
3.2. Privacy by Design
4. Related Work
4.1. IoTS Security and Privacy Vulnerabilities and Attacks with Countermeasures
4.2. AI-Based Approaches for IoTS Security and Privacy
4.3. Zero Trust Approaches for IoTS Security and Privacy
4.4. Frameworks and Guidelines for IoTS Security and Privacy
4.5. IoTS Privacy
4.6. Comparative Analysis of Existing Approaches
4.7. Positioning Against Existing IoTS Development Methodologies
- Integration of privacy concerns throughout the entire IoTS development lifecycle, addressing gaps present in existing solutions.
- A developer-oriented workflow with clear and practical steps for embedding privacy.
- Support emerging technologies, such as federated learning and zero trust, to enhance adaptability.
- Real-world applicability through actionable guidelines tailored to diverse IoTS environments.
5. Proposed Methodological Approach: Planning, Requirements, and Design (PRD)
5.1. Foundations of PRD
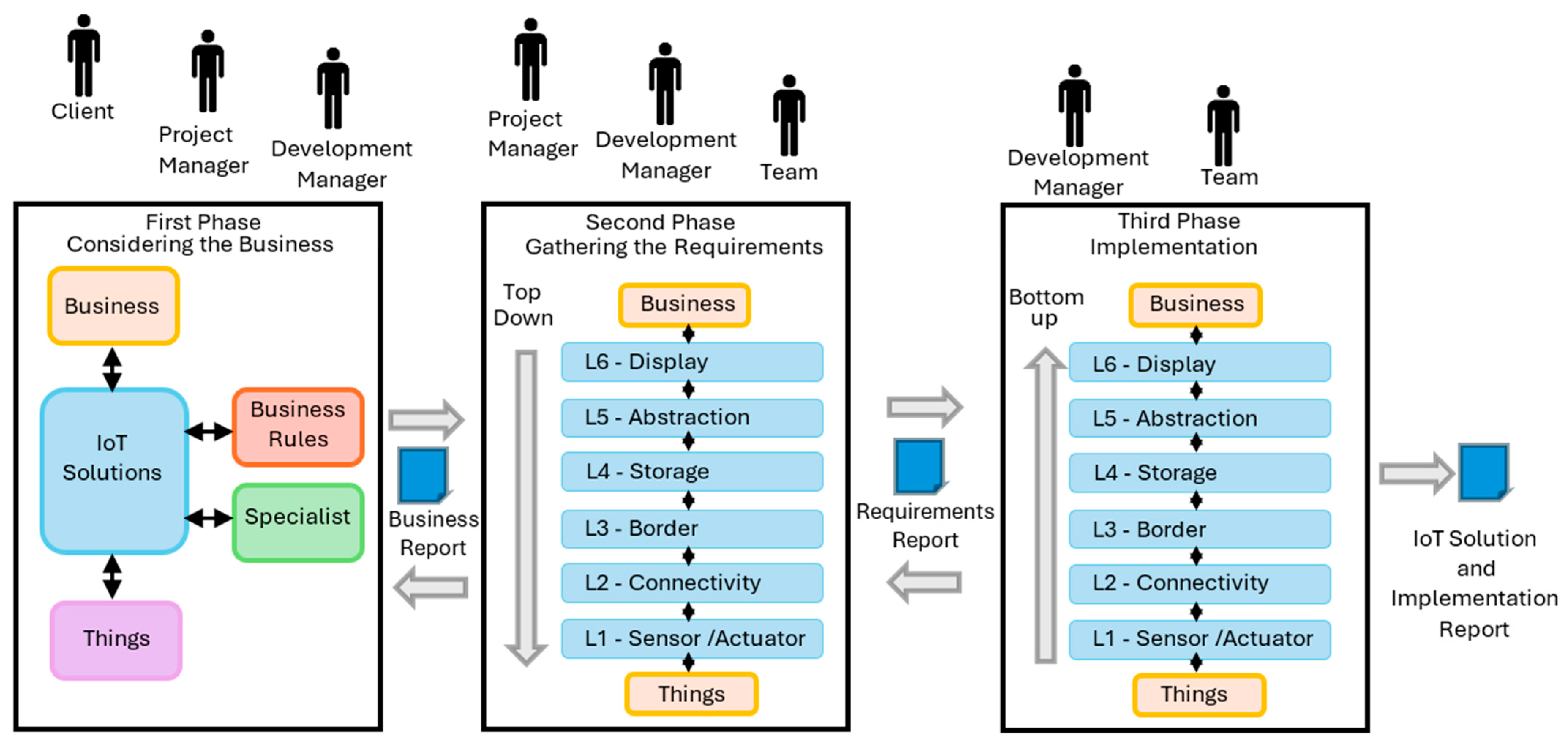
- Considering the Business: In this initial phase, the business context is thoroughly analyzed to identify the key issues the IoT solution aims to address. The TpM-Pro methodology prioritizes a deep understanding of the solution’s business value, ensuring alignment with customer needs. Key considerations during this phase include business requirements, the entities to be measured or controlled, the involvement of specialized expertise, and applicable business rules. To support this process, the TpM-IoT-Canvas tool is used to systematically extract essential requirements and facilitate collaborative planning. This is achieved through a visual model with eight sections: business, justification, benefits, product, things, solution requirements, client, and team. This comprehensive approach ensures that all critical aspects of the business environment are addressed, establishing a strong foundation for the subsequent development phases.
- Gathering the Requirements: In this phase, the process of gathering requirements focuses on breaking down the system into smaller, manageable components to ensure that both business objectives and technical needs are effectively addressed. The business context and the IoT Open-Source Reference Model (IoT-OSRM) serve as foundational frameworks that guide the identification and organization of system elements. The interrelationships among these components are carefully analyzed to ensure coherence and alignment throughout the system architecture. Functional and non-functional requirements are defined using a top-down approach, systematically categorizing them across six levels, beginning with sensor nodes and extending to data presentation. At each level, particular attention is dedicated to addressing security and privacy concerns, ultimately resulting in the creation of a Requirements Report, which consolidates all collected information and provides a solid foundation for stakeholder review and approval before the project progresses to the implementation phase.
- Implementation: In this final phase, developers evaluate and select the most appropriate technologies to fulfill the previously defined requirements, following a bottom-up approach that aligns with the IoT-OSRM reference model. The implementation process is structured in six distinct levels: Level 1 focuses on the selection of components for sensors and actuators, forming the foundation for data collection and interaction with the physical environment. Level 2 involves determining the necessary network infrastructure to ensure reliable and secure communication between devices. Level 3 addresses the selection of the edge element, responsible for local data processing and initial filtering. Level 4 pertains to choosing the most suitable data storage solution, emphasizing scalability, security, and accessibility. Level 5 involves applying appropriate data-handling techniques for processing, analysis, and transformation of raw data into meaningful insights. Finally, Level 6 involves the deployment of user interface tools designed to present processed data to the end user in an intuitive and accessible manner. This structured approach ensures a cohesive and efficient implementation, maintaining consistency with the system’s overall design while addressing critical aspects such as security, privacy, and user experience.
5.1.1. TpM-Pro Agents and Roles
- Clients: Includes all the stakeholders involved in the project.
- Project Manager: Acts as a liaison between the clients and the development manager. This person is responsible for gathering business data and, in collaboration with other participants, confirming the feasibility of the proposed solution.
- Development Manager: Oversees the interdisciplinary team and establishes key considerations for the solution’s development. This role also involves monitoring the project’s progress, assigning tasks across the different IoT-OSRM levels, and ensuring alignment with the overall project goals. Additionally, the development manager is responsible for gathering requirements and acts as a bridge between the project manager and the interdisciplinary team.
- Multidisciplinary Development Team: Consisting of experts with varying levels of IoT-OSRM expertise, this team contributes specialized knowledge throughout the different stages of the development process, ensuring that technical, security, and privacy requirements are effectively addressed.
5.1.2. TpM-Pro Phases
- Phase 1: Considering the Business
- First, the business itself must be evaluated, recognizing that even projects within the same industry can have unique requirements. Overlooking these nuances could lead to solutions misaligned with end-user expectations.
- Second, it is essential to identify the things (whether physical or virtual) that the business seeks to quantify, measure, or control. The project manager plays a key role in clearly defining what these “things” are.
- Third, the involvement of specialists or domain experts, whether internal or external, is crucial as they provide valuable insights that guide informed decision-making.
- Finally, business rules, including any assumptions, constraints, or operational guidelines, must be clearly understood and integrated into the development process to ensure that the solution remains aligned with client needs and complies with regulatory and organizational standards.
- Phase 2: Gathering of Requirements
- Level 1—Sensor/Actuator Node: Focuses on the selection of hardware components, including sensors, actuators, microcontrollers, memory, and processing units. Additional key considerations include the integration of edge/fog computing and local data processing to enhance system responsiveness and reduce network load.
- Level 2—Connectivity: Specifies the type of connection between the “things” and the border element, whether wired, wireless, or hybrid. Developers evaluate variables such as cost, scalability, environmental conditions, bandwidth, and reliability to determine the most effective communication method.
- Level 3—Border: Defines the “border element” that connects the system to the Internet and facilitates communication between IoT devices. This level may incorporate technologies such as network virtualization, middleware, and software-defined networks to optimize data flow and improve network efficiency.
- Level 4—Storage: Determines the most appropriate data storage method, considering options such as cloud-based, on-premises, or hybrid solutions. Key factors include data security, redundancy, scalability, and accessibility to ensure efficient data management and compliance with privacy regulations.
- Level 5—Abstraction: Identifies the processes through which raw data is transformed into meaningful information. This level leverages expert knowledge and advanced AI analytical techniques, such as ML and data mining, to interpret and contextualize complex data streams.
- Level 6—Display: Defines how information is presented to end users, focusing on intuitive and accessible formats, such as tables, graphs, and notifications. Effective data visualization at this level enhances user engagement and decision-making.
- Phase 3: Implementation
- Level 1—Sensor/Actuator Node: Involves the selection of sensors, actuators, microcontrollers, transducers, and memory components. These hardware elements form the foundational layer of the IoT system, enabling data collection and interaction with the physical environment.
- Level 2—Connectivity: Establishes the networking infrastructure required to connect “things” to the edge components. The choice between wired, wireless, or hybrid connections is based on considerations such as bandwidth, latency, environmental factors, and scalability.
- Level 3—Border: Focuses on selecting the appropriate edge element, which may include a single-board computer, an inter-cloud computing system, or a dedicated cloud server. The chosen technology must comply with the requirements outlined in Phase 2, ensuring efficient data routing, pre-processing, and enhanced security.
- Level 4—Storage: Involves choosing the data storage solution that best meets the system’s operational needs, whether through local databases, cloud storage, or a hybrid approach. This selection considers factors such as data security, redundancy, latency, and accessibility, ensuring that stored data remains both reliable and readily available.
- Level 5—Abstraction: Focuses on implementing data-handling techniques to process and transform raw data into actionable insights. This includes employing advanced methods such as big data analytics, ML, and DL to extract meaningful information and support informed decision-making for the end user.
- Level 6—Display: Involves deploying the user interface tools through which end users will interact with the system. This includes developing mobile applications, dashboards, alerts, graphs, and other forms of visual reporting to present data in an intuitive and accessible manner.
5.2. PRD Phases
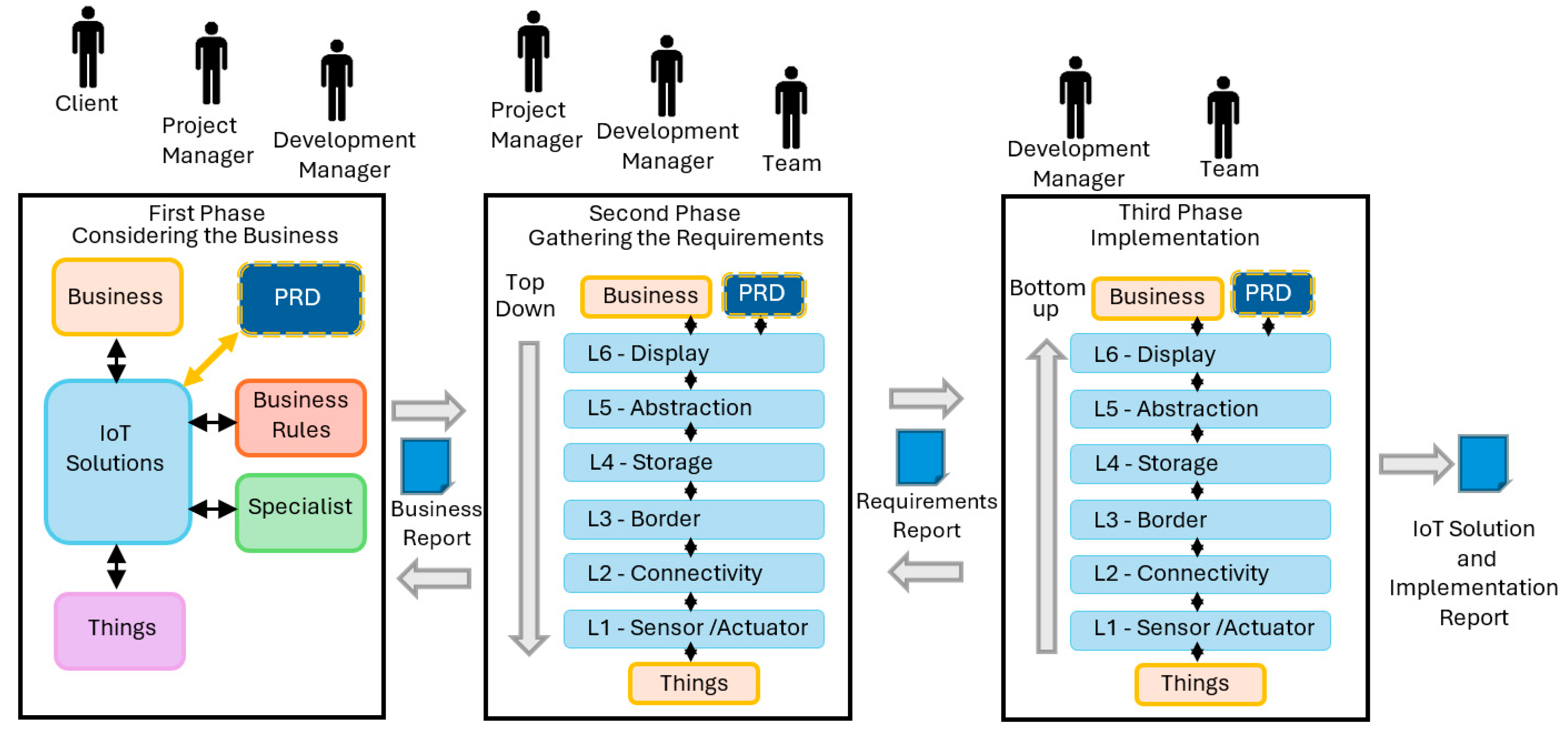
5.2.1. Phase 1—Planning
5.2.2. Phase 2—Requirements Elicitation
5.2.3. Phase 3—Design
- Considering the Business: Aligns privacy goals with business objectives, ensuring that privacy considerations are integrated from the outset and remain consistent and aligned with the overall strategic vision.
- Gathering the Requirements: Defines privacy-specific requirements, such as data anonymization, encryption, and access control, and ensures their seamless integration into the system specifications, laying a solid foundation for a secure and compliant system architecture.
- Implementation: Provides a detailed system blueprint that guides developers in the effective implementation of privacy mechanisms. This includes outlining security best practices, testing procedures, and regulatory compliance checks to ensure the system meets all necessary privacy standards.
5.3. Brief Application Steps of the PRD Framework Integrated with TpM-Pro
- 1.
- Planning
- Identify stakeholders and core privacy requirements.
- Set clear privacy objectives aligned with business and regulatory needs.
- Conduct an initial Privacy Impact Assessment (PIA).
- Select and tailor relevant privacy guidelines to the project domain
- 2.
- Requirements Gathering
- Translate privacy objectives into specific technical and operational requirements.
- Use tools such as user stories and use cases to clarify requirements.
- Integrate the selected privacy guidelines into the requirement specifications.
- Continuously refine requirements based on feedback during development.
- 3.
- Design
- Integrate privacy-preserving mechanisms (encryption, access control, anonymization) based on the privacy guidelines.
- Develop a detailed blueprint guiding implementation while ensuring regulatory compliance.
- Perform privacy testing and validation before final deployment.
6. Proposal of Privacy Guidelines
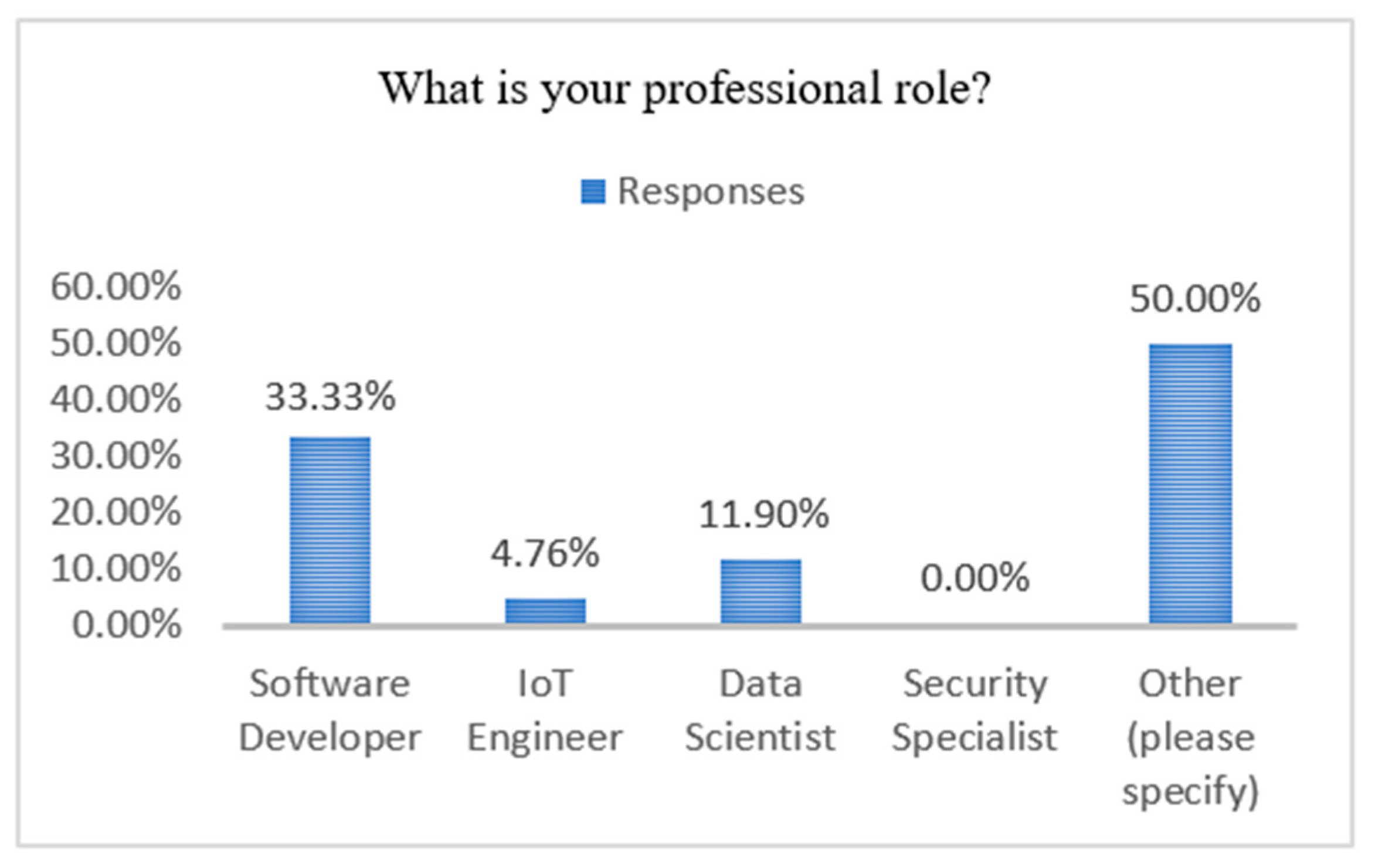
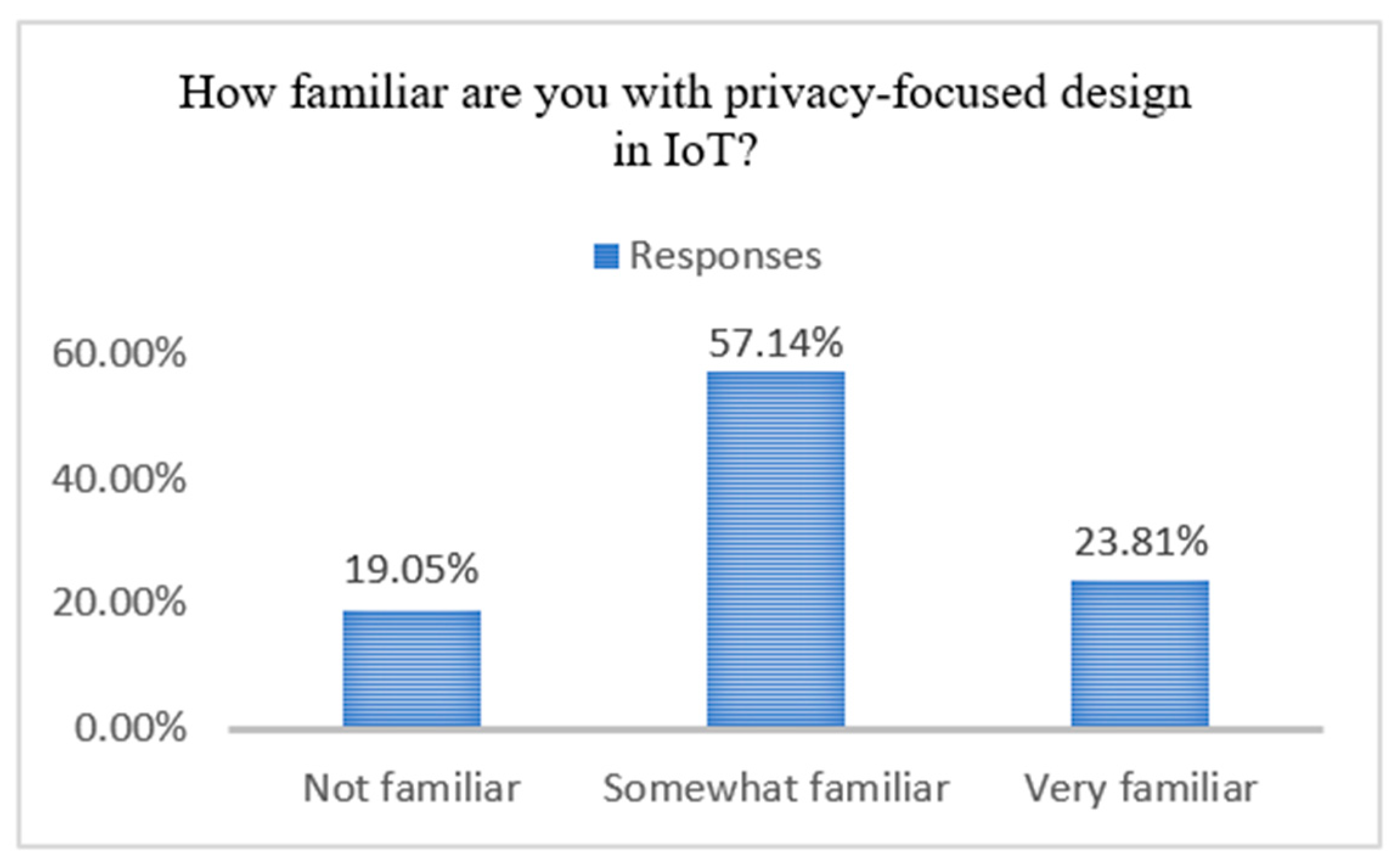
6.1. Survey Design and Implementation
- Clarity: The ease of understanding the guideline.
- Practicality: The feasibility of implementing the guideline.
- Relevance: The significance of the guideline in ensuring privacy in IoTSs.
- Demographic Information: Collected data on participants’ backgrounds and assessed their general understanding of IoTS privacy.
- Guideline Evaluation: Asked participants to evaluate the 30 privacy guidelines based on their clarity, practicality, and relevance.
- Feedback and Suggestions: Provided space for participants to offer additional comments, suggestions, and potential improvements to further refine the guidelines.
6.2. Survey Results
6.2.1. Analysis Part 1: Categorization of Guidelines Based on Importance and User Feedback
- (a)
- High-Importance GuidelinesThese guidelines consistently received high ratings across all three dimensions, with a mean score of 4.0 and above, signifying their critical role in safeguarding IoTS privacy.
- Encrypted Data Communication (4.51)
- Encrypted Data Storage (4.44)
- Data Anonymization (4.42)
- Minimize Data Storage (4.23)
- Information Disclosure (4.40)
- Compliance with Regulations (4.35)
- Logging (4.30)
- Auditing (4.30)
- Minimize Raw Data Intake (4.0)
- (b)
- Medium-Importance GuidelinesThese guidelines, with scores between 3.7 and 3.99, were considered valuable but may require refinement or be context-dependent, affecting their applicability across different IoT scenarios.
- Minimize Data Acquisition (3.86)
- Minimize Number of Data Sources (3.79)
- Reduce Data Granularity (3.88)
- Knowledge Discovery-Based Aggregation (3.91)
- Distributed Data Storage (3.88)
- Category-Based Aggregation (3.79)
- Query Answering Without Raw Data (3.95)
- (c)
- Low-Importance GuidelinesThese guidelines received scores below 3.7, indicating limited practical implementation or a lack of clarity.
- Minimize Knowledge Discovery (3.16)
- Open-Source Policy for Transparency (3.37)
- Hidden Data Routing (3.49)
- Chain Aggregation (3.21)
- Minimize Data Retention Period (3.5)
- Repeated Query Blocking (3.0)
- Distributed Data Processing (3.0)
- Geography-Based Aggregation (3.5)
- Time-Period Based Aggregation (3.0)
- Control (3.5)
- Data Flow Diagrams (3.5)
- Certification (3.0)
- Standardization (3.0)
- Encrypted Data Processing (3.5)
- Key Findings and Reflections
6.2.2. Analysis Part 2: Detailed Analysis of Participant Recommendations
- 1.
- Need for More Precise Definitions and ExamplesA recurring concern among respondents was the ambiguity in certain guideline definitions. Participants pointed out that terms such as “minimizing data acquisition” and “minimizing knowledge discovery” are vague and context-dependent. To address this, they suggested the following:
- (a)
- Incorporating specific use-case examples for each guideline to illustrate its practical applications more clearly.
- (b)
- Aligning definitions with established privacy frameworks, such as GDPR and the National Institute of Standards and Technology (NIST), to ensure consistency with regulatory standards.
- (c)
- Providing clear thresholds for implementation, such as specifying what constitutes “excessive data retention”.
- 2.
- Balancing Privacy and Performance in Encrypted Data ProcessingAlthough encryption was among the highest-rated guidelines, several respondents raised concerns about its computational cost. Advanced encryption methods, such as homomorphic encryption and multi-party computation, can introduce latency and processing overhead, making them impractical for resource-constrained IoT devices. Participants recommended the following:
- (a)
- Adopting hybrid encryption models that combine end-to-end encryption with selective decryption to enhance efficiency.
- (b)
- Utilizing lightweight cryptographic approaches, such as differential privacy and zero-knowledge proofs, to reduce processing demands.
- (c)
- Implementing adaptive encryption policies that dynamically adjust encryption levels based on data sensitivity and device capabilities.
- 3.
- Importance of Automated Privacy EnforcementSeveral participants emphasized the need for automated privacy mechanisms, arguing that privacy policies should not depend solely on manual configurations. Key recommendations included:
- (a)
- Developing real-time privacy risk assessment tools to proactively identify potential violations before they occur.
- (b)
- Establishing automated data expiration policies to ensure compliance with minimal human intervention.
- (c)
- Leveraging ML-based anomaly detection to dynamically monitor and address privacy threats.
- 4.
- Improving Data Aggregation and Query AnsweringAggregation-based guidelines, such as Geography-Based Aggregation and Time-Based Aggregation, received moderate ratings, suggesting that their effectiveness is highly dependent on the specific use case. Respondents suggested the following:
- (a)
- Designing context-sensitive aggregation strategies that balance data usability with privacy protection.
- (b)
- Refining query-answering models to ensure differential privacy, preventing the exposure of individual data points.
- (c)
- Introducing threshold-based aggregation policies to limit the risk of sensitive data overexposure.
- 5.
- Expanding Privacy Guidelines to Cover Emerging ChallengesSeveral participants identified gaps in the current privacy guidelines, particularly in relation to emerging technologies and evolving privacy challenges. They proposed expanding the guidelines to address:
- (a)
- AI and Privacy: Strategies to ensure that AI-driven analytics handle IoTS data responsibly while preserving user privacy.
- (b)
- Edge Computing Privacy: Approaches for securing decentralized data processing at the network edge.
- (c)
- User-Controlled Privacy Mechanisms: The need for greater transparency and user-accessible privacy settings in IoTSs to empower end users.
6.2.3. Analysis Part 3: Exploring the Influence of Developers’ Backgrounds on Their Interpretation of Privacy Guidelines
6.2.4. Summary
- Clarity and precision are crucial: Ambiguous guidelines hinder adoption. Definitions should be clear and grounded in real-world scenarios to ensure practical applicability.
- Performance constraints must be addressed: Encryption and data processing techniques should be designed using lightweight and adaptive solutions to accommodate the resource limitations typical of IoT environments.
- Automation is the future of IoT privacy: Privacy protection should move beyond manual enforcement, relying instead on intelligent, automated systems for greater efficiency and reliability.
- Aggregation strategies need flexibility: Rather than rigid aggregation policies, a context-driven approach should be adopted to balance data usability and privacy protection.
- Emerging threats require new guidelines: Future privacy frameworks must evolve to address challenges posed by AI, edge computing, and the increasing demand for user autonomy in IoTSs.
6.3. Proposal
6.3.1. Proposal Part 1: Proposed Privacy Guidelines for IoTS
- 1.
- Data Collection and Processing
- Minimize Data Acquisition: Collect only the data that is essential for the intended purpose, reducing unnecessary data collection.
- Reduce Data Granularity: Limit the level of detail in collected data to the minimum required, avoiding excessive precision where it is not needed.
- Query Answering Without Raw Data: Provide analytical insights without exposing complete raw datasets, ensuring sensitive data remains protected.
- 2.
- Data Security and Protection
- Encrypted Data Communication: Apply strong encryption protocols to secure all data transmissions and prevent unauthorized access.
- Encrypted Data Storage: Store data using strong encryption methods to safeguard it against breaches and unauthorized retrieval.
- Data Anonymization: Implement techniques such as pseudonymization and k-anonymity to protect user identities and reduce re-identification risks.
- 3.
- Data Storage and Retention
- Minimize Data Storage: Retain only data that is necessary for operational or legal purposes, reducing the risk of data exposure.
- Automated Data Deletion: Establish automated processes to delete data once it is no longer required, ensuring compliance with data retention policies.
- 4.
- Aggregation and Decentralization
- Knowledge Discovery-Based Aggregation: Aggregate data to extract meaningful insights while ensuring privacy is maintained.
- Distributed Data Storage: Implement decentralized storage solutions to avoid single points of failure and enhance data resilience.
- 5.
- User Control and Transparency
- Information Disclosure: Clearly inform users when their data is collected, ensuring transparency in data-handling practices.
- User Privacy Controls: Provide users with flexible, dynamic privacy settings, empowering them to control how their data is used.
- Logging and Auditing: Maintain comprehensive records of data activities to facilitate regular security audits and ensure accountability.
- 6.
- Regulatory Compliance and Best Practices
- Compliance with Privacy Regulations: Ensure alignment with established privacy laws and standards, including GDPR, the California Consumer Data Privacy Act (CCPA), and International Organization for Standardization (ISO) frameworks.
- Privacy by Design and Default: Integrate privacy considerations from the initial design phase and enforce them as the default operating standard.
- Comparison of the Proposed Privacy guidelines with LINDDUN Privacy ThreatsTable 4 provides a detailed comparison between the 15 proposed privacy guidelines and the 14 privacy threats from the LINDDUN framework [41], corresponding to the purple, orange, and red categories, which were identified as most relevant and aligned with the focus of our study. This mapping reveals varying degrees of overlap: several guidelines directly address known threats, either by reframing them as proactive design recommendations or by enhancing or extending them through more actionable, developer-focused implementation strategies. Notably, four of the proposed guidelines represent novel contributions that are not explicitly covered by the LINDDUN threat model. Specifically, these guidelines are as follows:
- Guideline 3: Query Answering Without Raw Data. This guideline supports privacy-preserving data querying by enabling analytical responses without exposing raw data. While LINDDUN highlights risks associated with personal data overexposure, it does not address mechanisms such as federated queries or privacy-preserving statistical summaries. Our approach empowers developers to provide meaningful insights while minimizing privacy risks.
- Guideline 9: Knowledge Discovery-Based Aggregation. This guideline promotes aggregation techniques aligned with privacy-preserving data mining principles. While LINDDUN warns against unnecessary data analysis, it does not propose practical methods for safely extracting knowledge from aggregated data. Our approach bridges this gap by offering developer-oriented strategies that enable useful analytics without compromising individual privacy.
- Guideline 10: Distributed Data Storage. This guideline encourages distributed data storage architectures to minimize single points of failure and increase resilience, thereby enhancing privacy protection. While LINDDUN addresses insufficient processing security, it lacks specific guidance on decentralization as a privacy-preserving architectural strategy. Our proposal introduces this concept as a concrete privacy-preserving design pattern tailored to IoT environments, helping developers adopt modern, resilient system architectures that support privacy goals.
- Guideline 15: Privacy by Design and Default. This guideline advocates for the proactive integration of privacy principles from the earliest stages of system design, ensuring that privacy protections are embedded by default. Unlike LINDDUN, which refers to general compliance with privacy standards, our approach provides explicit guidance for developers to integrate privacy throughout the entire system development lifecycle, enabling comprehensive and effective enforcement of privacy requirements.
- Transformation into developer-oriented recommendations: While LINDDUN offers valuable theoretical descriptions of privacy threats, our guidelines build upon these concepts and introduce additional, original elements to deliver concrete, actionable practices for developers. For example, whereas LINDDUN identifies Insufficient Security of Processing, our guideline goes further by recommending Encrypted Data Communication as a practical and developer-friendly mitigation strategy.
- Added technical and architectural contributions: Several guidelines extend beyond LINDDUN’s scope by introducing technical implementation patterns and architectural solutions specifically tailored to IoT environments and their constraints. For instance, Distributed Data Storage and Knowledge Discovery-Based Aggregation explicitly address resilience and privacy-preserving analytics in distributed IoT architectures, areas not explicitly covered in LINDDUN’s original formulation.
- Objective prioritization: The scoring-based approach guarantees that the guidelines align with stakeholder priorities in terms of clarity, practicality, and relevance, thereby reinforcing their applicability to real-world IoT systems.
- Avoiding developer overload: We have considered the cognitive burden placed on developers, recognizing that an excessive number of guidelines can lead to developer fatigue, reducing their ability to effectively implement privacy protections.
6.3.2. Proposal Part 2: Balancing Security and Performance in IoTS
6.3.3. Proposal Part 3: Automated Privacy Enforcement in IoTS
- AI-Based Privacy Preservation
- Context-Awareness and Privacy
- Blockchain for Privacy Management
7. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Samizadeh Nikoui, T.; Rahmani, A.M.; Balador, A.; Haj Seyyed Javadi, H. Internet of Things architecture challenges: A systematic review. Int. J. Commun. Syst. 2021, 34, 1–42. [Google Scholar] [CrossRef]
- Lin, H.; Bergmann, N.W. IoT Privacy and Security Challenges for Smart Home Environments. Information 2016, 7, 44. [Google Scholar] [CrossRef]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Himeur, Y.; Sohail, S.S.; Bensaali, F.; Amira, A.; Alazab, M. Latest trends of security and privacy in recommender systems: A comprehensive review and future perspectives. Comput. Secur. 2022, 118, 102746. [Google Scholar] [CrossRef]
- Ismail, S.; Dawoud, D.W. Software Development Models for IoT. In Proceedings of the 2022 IEEE 12th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 26–29 January 2022; IEEE: New York, NY, USA, 2022; pp. 0524–0530. [Google Scholar] [CrossRef]
- Reinsel, D. IDC Blog. 2019 [cited 2023 Mar 4]. How You Contribute to Today’s Growing DataSphere and Its Enterprise Impact. Available online: https://blogs.idc.com/2019/11/04/how-you-contribute-to-todays-growing-datasphere-and-its-enterprise-impact/ (accessed on 4 March 2023).
- Greenberg, P. 2021 Consumer Data Privacy Legislation. National Conference of State Legislatures [Internet]. Available online: https://www.ncsl.org/technology-and-communication/2021-consumer-data-privacy-legislation (accessed on 10 November 2024).
- Hornos, M.J.; Quinde, M. Development methodologies for IoT-based systems: Challenges and research directions. J. Reliab. Intell. Environ. 2024, 10, 215–244. [Google Scholar] [CrossRef]
- Guerrero-Ulloa, G.; Rodríguez-Domínguez, C.; Hornos, M.J. Agile Methodologies Applied to the Development of Internet of Things (IoT)-Based Systems: A Review. Sensors 2023, 23, 790. [Google Scholar] [CrossRef] [PubMed]
- Nakagawa, H.; Ogata, S.; Aoki, Y.; Kobayashi, K. A model transformation approach to constructing agent-oriented design models for CPS/IoT systems. In Proceedings of the 35th Annual ACM Symposium on Applied Computing, Brno, Czech Republic, 30 March–3 April 2020; Association for Computing Machinery: New York, NY, USA, 2020; pp. 815–822. [Google Scholar] [CrossRef]
- Shaheen, Y.; Hornos, M.J.; Rodríguez-Domínguez, C. IoT Security and Privacy Challenges from the Developer Perspective. In Ambient Intelligence—Software and Applications—14th International Symposium on Ambient Intelligence; Springer Nature: Cham, Switzerland, 2023; pp. 13–21. [Google Scholar] [CrossRef]
- Jacobson, I.; Spence, I.A.N.; Ng, P.-W. Is There a Single Method for the Internet of Things? Commun. ACM 2017, 60, 46–53. [Google Scholar] [CrossRef]
- Patel, P.; Cassou, D. Enabling high-level application development for the Internet of Things. J. Syst. Softw. 2015, 103, 62–84. [Google Scholar] [CrossRef]
- Guerrero-Ulloa, G.; Hornos, M.J.; Rodríguez-Domínguez, C. TDDM4IoTS: A Test-Driven Development Methodology for Internet of Things (IoT)-Based Systems. In Applied Technologies; Springer International Publishing: Cham, Switzerland, 2020; pp. 41–55. [Google Scholar] [CrossRef]
- Ferreira, L.C.B.C.; Yamaguti, R.; Branquinho, O.C.; Cardieri, P. A TpM-based collaborative system to teach IoT. Comput. Appl. Eng. Educ. 2022, 30, 292–303. [Google Scholar] [CrossRef]
- Bucher, T.; Klesse, M.; Kurpjuweit, S.; Winter, R. Situational Method Engineering BT—Situational Method Engineering: Fundamentals and Experiences; Ralyté, J., Brinkkemper, S., Henderson-Sellers, B., Eds.; Springer: Boston, MA, USA, 2007; pp. 33–48. [Google Scholar] [CrossRef]
- Ferreira, L.C.B.C.; Chaves, P.R.; Assumpção, R.M.; Branquinho, O.C.; Fruett, F.; Cardieri, P. The Three-Phase Methodology for IoT Project Development. Internet Things 2022, 20, 100624. [Google Scholar] [CrossRef]
- Valacich, J.S.; George, J.F.; Hoffer, J.A. Modern Systems Analysis and Design; Pearson Eudcation: London, UK, 2017. [Google Scholar]
- Alhirabi, N.; Rana, O.; Perera, C. Security and Privacy Requirements for the Internet of Things: A Survey. ACM Trans. Internet Things 2021, 2, 1–37. [Google Scholar] [CrossRef]
- Shaheen, Y.Y.; Hornos, M.J.; Rodríguez-Domínguez, C. Addressing Privacy Challenges in Internet of Things (IoT) Applications. In Ambient Intelligence—Software and Applications—15th International Symposium on Ambient Intelligence; Novais, P., Parameshachari, B.D., Satoh, I., Inglada, V.J., González, S.R., Jove Pérez, E., Domínguez, J.P., Chamoso, P., Alonso, R.S., Eds.; Springer Nature: Cham, Switzerland, 2025; pp. 45–54. [Google Scholar] [CrossRef]
- Dias, J.P.; Ferreira, H.S. State of the Software Development Life-Cycle for the Internet-of-Things. arXiv 2018, arXiv:1811.04159. [Google Scholar]
- Perera, C.; Barhamgi, M.; Bandara, A.K.; Ajmal, M.; Price, B.; Nuseibeh, B. Designing privacy-aware internet of things applications. Inf. Sci. 2020, 512, 238–257. [Google Scholar] [CrossRef]
- Cavoukian, A. Privacy by design: The definitive workshop. A foreword by Ann Cavoukian, Ph.D. Identity Inf. Soc. 2010, 3, 247–251. [Google Scholar] [CrossRef]
- European Parliament and of the Council. Regulation (EU) 2016/679 of 27 April 2016 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data, and repealing Directive 95/46/EC (General Data Protection Regulation). Off. J. Eur. Union 2016, OJ L 119/1, 1–88. Available online: https://eur-lex.europa.eu/eli/reg/2016/679/oj/eng (accessed on 10 July 2025).
- Adam, M.; Hammoudeh, M.; Alrawashdeh, R.; Alsulaimy, B. A Survey on Security, Privacy, Trust, and Architectural Challenges in IoT Systems. IEEE Access 2024, 12, 57128–57149. [Google Scholar] [CrossRef]
- Pourrahmani, H.; Yavarinasab, A.; Monazzah, A.M.H.; van Herle, J. A review of the security vulnerabilities and countermeasures in the Internet of Things solutions: A bright future for the Blockchain. Internet Things 2023, 23, 100888. [Google Scholar] [CrossRef]
- Hossain, M.; Kayas, G.; Hasan, R.; Skjellum, A.; Noor, S.; Islam, S.M.R. A Holistic Analysis of Internet of Things (IoT) Security: Principles, Practices, and New Perspectives. Future Internet 2024, 16, 40. [Google Scholar] [CrossRef]
- Swessi, D.; Idoudi, H. A Survey on Internet-of-Things Security: Threats and Emerging Countermeasures. Wirel. Pers. Commun. 2022, 124, 1557–1592. [Google Scholar] [CrossRef]
- Kaushal, N.; Singh, G.; Singh, J. An Addressing Techniques for Maintaining Security and Privacy Framework for Internet of Things. In Proceedings of the 2023 3rd International Conference on Intelligent Technologies (CONIT), Hubli, India, 23–25 June 2023; pp. 1–7. [Google Scholar] [CrossRef]
- Nazir, A.; He, J.; Zhu, N.; Wajahat, A.; Ma, X.; Ullah, F.; Qureshi, S.; Pathan, M.S. Advancing IoT security: A systematic review of machine learning approaches for the detection of IoT botnets. J. King Saud Univ.-Comput. Inf. Sci. 2023, 35, 101820. [Google Scholar] [CrossRef]
- Qureshi, S.U.; He, J.; Tunio, S.; Zhu, N.; Nazir, A.; Wajahat, A.; Ullah, F.; Wadud, A. Systematic review of deep learning solutions for malware detection and forensic analysis in IoT. J. King Saud Univ.-Comput. Inf. Sci. 2024, 36, 102164. [Google Scholar] [CrossRef]
- Li, J.; Lyu, L.; Liu, X.; Zhang, X.; Lyu, X. FLEAM: A Federated Learning Empowered Architecture to Mitigate DDoS in Industrial IoT. IEEE Trans. Ind. Inform. 2022, 18, 4059–4068. [Google Scholar] [CrossRef]
- Alahmari, S.; Alkharashi, A. Privacy-Aware Federated Learning Framework for IoT Security Using Chameleon Swarm Optimization and Self-Attentive Variational Autoencoder. Comput. Model. Eng. Sci. 2025, 143, 849–873. [Google Scholar] [CrossRef]
- Zhao, B.; Ji, Y.; Shi, Y.; Jiang, X. Design and implementation of privacy-preserving federated learning algorithm for consumer IoT. Alex. Eng. J. 2024, 106, 206–216. [Google Scholar] [CrossRef]
- Dhar, S.; Bose, I. Securing IoT Devices Using Zero Trust and Blockchain. J. Organ. Comput. Electron. Commer. 2021, 31, 18–34. [Google Scholar] [CrossRef]
- Liu, C.; Tan, R.; Wu, Y.; Feng, Y.; Jin, Z.; Zhang, F.; Liu, Y.; Liu, Q.X. Dissecting zero trust: Research landscape and its implementation in IoT. Cybersecurity 2024, 7, 20. [Google Scholar] [CrossRef]
- Paul, P.C.; Loane, J.; McCaffery, F.; Regan, G. Towards Design and Development of a Data Security and Privacy Risk Management Framework for WBAN Based Healthcare Applications. Appl. Syst. Innov. 2021, 4, 76. [Google Scholar] [CrossRef]
- Abdul-Ghani, H.A.; Konstantas, D. A Comprehensive Study of Security and Privacy Guidelines, Threats, and Countermeasures: An IoT Perspective. J. Sens. Actuator Netw. 2019, 8, 22. [Google Scholar] [CrossRef]
- Hoepman, J.H. Privacy design strategies. In ICT Systems Security and Privacy Protection; Springer: Berlin/Heidelberg, Germany, 2014; pp. 446–459. [Google Scholar] [CrossRef]
- Perera, C.; McCormick, C.; Bandara, A.K.; Price, B.A.; Nuseibeh, B. Privacy-by-design framework for assessing internet of things applications and platforms. In Proceedings of the 6th International Conference on the Internet of Things, Stuttgart, Germany, 7–9 November 2016; Association for Computing Machinery: New York, NY, USA, 2016; pp. 83–92. [Google Scholar] [CrossRef]
- Consortium, L. LINDDUN GO Threat Modeling Tool [Internet]. 2024. Available online: https://downloads.linddun.org/linddun-go/cardbrowser/v241203/index.html (accessed on 20 June 2025).
- Deb, S.; Bhuyan, B. Performance analysis of current lightweight stream ciphers for constrained environments. Sādhanā 2020, 45, 256. [Google Scholar] [CrossRef]
- Abosata, N.; Al-Rubaye, S.; Inalhan, G.; Emmanouilidis, C. Internet of Things for System Integrity: A Comprehensive Survey on Security, Attacks and Countermeasures for Industrial Applications. Sensors 2021, 21, 3654. [Google Scholar] [CrossRef] [PubMed]
- Thabit, F.; Can, O.; Aljahdali, A.O.; Al-Gaphari, G.H.; Alkhzaimi, H.A. Cryptography Algorithms for Enhancing IoT Security. Internet Things 2023, 22, 100759. [Google Scholar] [CrossRef]
- El-hajj, M.; Mousawi, H.; Fadlallah, A. Analysis of Lightweight Cryptographic Algorithms on IoT Hardware Platform. Future Internet 2023, 15, 54. [Google Scholar] [CrossRef]
- Halgamuge, M.N.; Niyato, D. Adaptive edge security framework for dynamic IoT security policies in diverse environments. Comput. Secur. 2025, 148, 104128. [Google Scholar] [CrossRef]
- Kounoudes, A.D.; Kapitsaki, G.M. A mapping of IoT user-centric privacy preserving approaches to the GDPR. Internet Things 2020, 11, 100179. [Google Scholar] [CrossRef]
- Sun, P.; Wan, Y.; Wu, Z.; Fang, Z.; Li, Q. A survey on privacy and security issues in IoT-based environments: Technologies, protection measures and future directions. Comput. Secur. 2025, 148, 104097. [Google Scholar] [CrossRef]
- Schilit, B.N.; Theimer, M.M. Disseminating active map information to mobile hosts. IEEE Netw. 1994, 8, 22–32. [Google Scholar] [CrossRef]
- Alotaibi, A.I.; Oracevic, A. Context-Aware Security in the Internet of Things: What We Know and Where We are Going. In Proceedings of the 2023 International Symposium on Networks, Computers and Communications (ISNCC), Doha, Qatar, 23–26 October 2023; pp. 1–8. [Google Scholar] [CrossRef]
- Bou Chaaya, K.; Barhamgi, M.; Chbeir, R.; Arnould, P.; Benslimane, D. Context-aware System for Dynamic Privacy Risk Inference: Application to smart IoT environments. Future Gener. Comput. Syst. 2019, 101, 1096–1111. [Google Scholar] [CrossRef]
- Wang, T.; Yang, Q.; Shen, X.; Gadekallu, T.R.; Wang, W.; Dev, K. A Privacy-Enhanced Retrieval Technology for the Cloud-Assisted Internet of Things. IEEE Trans. Ind. Inform. 2022, 18, 4981–4989. [Google Scholar] [CrossRef]
- Saha, R.; Kumar, G.; Conti, M.; Devgun, T.; Kim, T.H.; Alazab, M. DHACS: Smart Contract-Based Decentralized Hybrid Access Control for Industrial Internet-of-Things. IEEE Trans. Ind. Inform. 2022, 18, 3452–3461. [Google Scholar] [CrossRef]



| Guideline Name | |
|---|---|
| 1-Minimize data acquisition 2-Minimize the number of data sources 3-Minimize raw data intake 4-Minimize knowledge discovery 5-Minimize data storage 6-Minimize data retention period 7-Hidden data routing 8-Data anonymization 9-Encrypted data communication 10-Encrypted data processing 11-Encrypted data storage 12-Data granularity reduction 13-Query response 14-Repeated query blocking 15-Distributed data processing | 16-Distributed data storage 17-Knowledge discovery-based aggregation 18-Geography-based aggregation 19-Chain aggregation 20-Time period-based aggregation 21-Category-based aggregation 22-Information disclosure 23-Control 24-Logging 25-Auditing 26-Open source 27-Data flow diagrams 28-Certification 29-Standardisation 30-Compliance |
| Aspect | Security-Focused Approaches | AI-Based Detection | Zero Trust Models | Frameworks and Guidelines | Privacy-by-Design Frameworks | Proposed Framework |
|---|---|---|---|---|---|---|
| Main Focus | Vulnerabilities and countermeasures | Threat detection via ML/DL/FL | Access control and continuous verification | Regulatory compliance and policies | Developer privacy guidelines | Systematic privacy integration |
| Privacy-by-Design Integration | Limited or absent | Partial, privacy-preserving techniques | Limited privacy focus | Limited developer-focused integration | Strong focus on PbD | Core element throughout development |
| Developer Support | Minimal procedural guidance | Focus on detection, not development | Complex implementation | Limited developer methodology | Guidelines but limited tooling | Stepwise, developer-friendly tools |
| Alignment with IoTS Development | Limited | Limited relevance | Operational focus | Limited lifecycle integration | Design-phase focused | Full lifecycle integration |
| Resource Suitability | Moderate to high resource demands | Computationally intensive | Challenging for constrained devices | Domain-specific, variable | Lightweight | Lightweight and scalable |
| Privacy Risk Handling | General or minimal | Privacy-preserving ML techniques | Mainly access control | Limited beyond compliance | Emphasis on privacy protection | Adaptive risk management and enforcement |
| Phase | Objective | Key Activities | Output |
|---|---|---|---|
| Planning | Define strategic privacy goals | Stakeholder analysis, Privacy Impact Assessment (PIA) | Strategic privacy framework, Aligned goals |
| Requirements elicitation | Translate goals into actionable requirements | Data flow mapping, Technical/operational requirement definition | Comprehensive requirements report |
| Design | Build and validate privacy mechanisms | Privacy by Design (PbD), Testing privacy features | Validated system design with embedded privacy tools |
| Proposed Guideline | Mapped LINDDUN Threat(s) | Novelty/Comment | Contribution | |
|---|---|---|---|---|
| 1 | Minimize Data Acquisition | Excessive Amount of Data Collected | Same objective, rephrased as a positive design principle | Direct Mapping |
| 2 | Reduce Data Granularity | Excessively Sensitive Data Collected | Emphasizes data precision control, not explicitly covered in LINDDUN | Enhanced |
| 3 | Query Answering Without Raw Data | Overexposure of Personal Data | Proposes concrete privacy-preserving querying mechanisms absent in LINDDUN | New |
| 4 | Encrypted Data Communication | Insufficient Security of Processing | Standard mitigation directly aligned with LINDDUN | Direct Mapping |
| 5 | Encrypted Data Storage | Insufficient Security of Processing | Standard mitigation directly aligned with LINDDUN | Direct Mapping |
| 6 | Data Anonymization | Excessively Sensitive Data Collected | Adds specific anonymization strategies | Enhanced |
| 7 | Minimize Data Storage | Unnecessary Data Retention | Same goal expressed as a design principle | Direct Mapping |
| 8 | Automated Data Deletion | Insufficient Rectification or Erasure | Adds automation aspects not explicitly covered by LINDDUN | Enhanced |
| 9 | Knowledge Discovery-Based Aggregation | Unnecessary Data Analysis | Suggests novel aggregation for privacy-preserving analytics absent in LINDDUN | New |
| 10 | Distributed Data Storage | Insufficient Security of Processing (Resilience Dimension) | Introduces architectural decentralization absent in LINDDUN | New |
| 11 | Information Disclosure | Insufficient Transparency | Same goal rephrased positively | Direct Mapping |
| 12 | User Privacy Controls | Insufficient Privacy Controls, Insufficient Access | Emphasizes user-centric, dynamic control mechanisms | Enhanced |
| 13 | Logging and Auditing | Improper Data Lifecycle Management | Adds concrete mechanisms for traceability and accountability | Enhanced |
| 14 | Compliance with Privacy Regulations | Non-Compliance of Processing with Applicable Regulations, Non-Adherence to Privacy Standards | Provides explicit reference to current regulations (e.g., GDPR), extending LINDDUN’s approach | Enhanced |
| 15 | Privacy by Design and Default | Non-Adherence to Privacy Standards | Introduces proactive privacy integration across the lifecycle | New |
| IoT Domain | Recommended Algorithm | Performance/Rational |
|---|---|---|
| Smart Home | PICCOLO, SIMON, SPECK, TWINE | Low memory and processing requirements |
| RFID/Logistics | SPECK, PICCOLO, SIMON | Limited space, no power backup |
| Smart Agriculture | TWINE, SIMON, SPECK, PRESENT | Energy efficiency, minimal processing, remote deployment |
| Healthcare | SIMON, SPECK, PICCOLO, PRESENT, MIDORI | Privacy, real-time response, low resources |
| Industrial Systems | MIDORI, PRINCE | Wireless communication, hard-to-access sensors |
| 5G World | PRINCE, PRESENT, SIMON, MIDORI | Secure real-time communication |
| Remote Keyless Entry | KEELOQ | Secure lightweight cipher for cars and buildings |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shaheen, Y.Y.; Hornos, M.J.; Rodríguez-Domínguez, C. Privacy Framework for the Development of IoT-Based Systems. Future Internet 2025, 17, 322. https://doi.org/10.3390/fi17080322
Shaheen YY, Hornos MJ, Rodríguez-Domínguez C. Privacy Framework for the Development of IoT-Based Systems. Future Internet. 2025; 17(8):322. https://doi.org/10.3390/fi17080322
Chicago/Turabian StyleShaheen, Yaqin Y., Miguel J. Hornos, and Carlos Rodríguez-Domínguez. 2025. "Privacy Framework for the Development of IoT-Based Systems" Future Internet 17, no. 8: 322. https://doi.org/10.3390/fi17080322
APA StyleShaheen, Y. Y., Hornos, M. J., & Rodríguez-Domínguez, C. (2025). Privacy Framework for the Development of IoT-Based Systems. Future Internet, 17(8), 322. https://doi.org/10.3390/fi17080322











