A Biologically Inspired Cost-Efficient Zero-Trust Security Approach for Attacker Detection and Classification in Inter-Satellite Communication Networks
Abstract
1. Introduction
- (1)
- Continuous Authentication for ISLs: The MRFCO-ZTS model implements continuous authentication mechanisms specifically tailored for Inter-Satellite Links (ISLs) in LEO networks. This strengthens security by improving data confidentiality, authentication reliability, integrity, and privacy protection, while effectively resisting a wide range of cyber threats.
- (2)
- Bio-Inspired Optimization for Cost Efficiency: MRFCO-ZTS employs the Manta Ray Foraging Optimization (MRFO) algorithm—a bio-inspired technique—to optimize the ZTS cost function. This function considers the likelihood of attacks, potential risk impact, and computational overhead. By integrating a cost-optimized classification system, the model effectively distinguishes between legitimate and malicious nodes, enhancing secure data access in satellite communications.
- (3)
- Balanced Performance and Efficiency: The MRFCO-ZTS framework achieves an optimal balance between satellite network security, communication latency, and resource utilization. Its performance has been validated through extensive simulations, demonstrating improvements over traditional satellite authentication methods in terms of accuracy, speed, and efficiency [3,4,6].
2. Related Works
2.1. Conventional Authentication Techniques
2.2. Conventional Zero-Trust Authentication Techniques
- Proposed MRFCO-ZTS is intended for fast adaptation to new threat patterns and Minimizes system load during detection/classification as where it utilizes Manta Ray Foraging Optimization for learning-based evolution of trust scores, using behaviors.
- Besides to that, proposed MRFCO-ZTS enforces Strict identity validation at every request, Dynamic trust re-evaluation based on behavior and past interaction, No implicit trust for previously authenticated satellite nodes, Trust decay over time in idle or suspicious nodes.
3. LEO Satellite Network Model
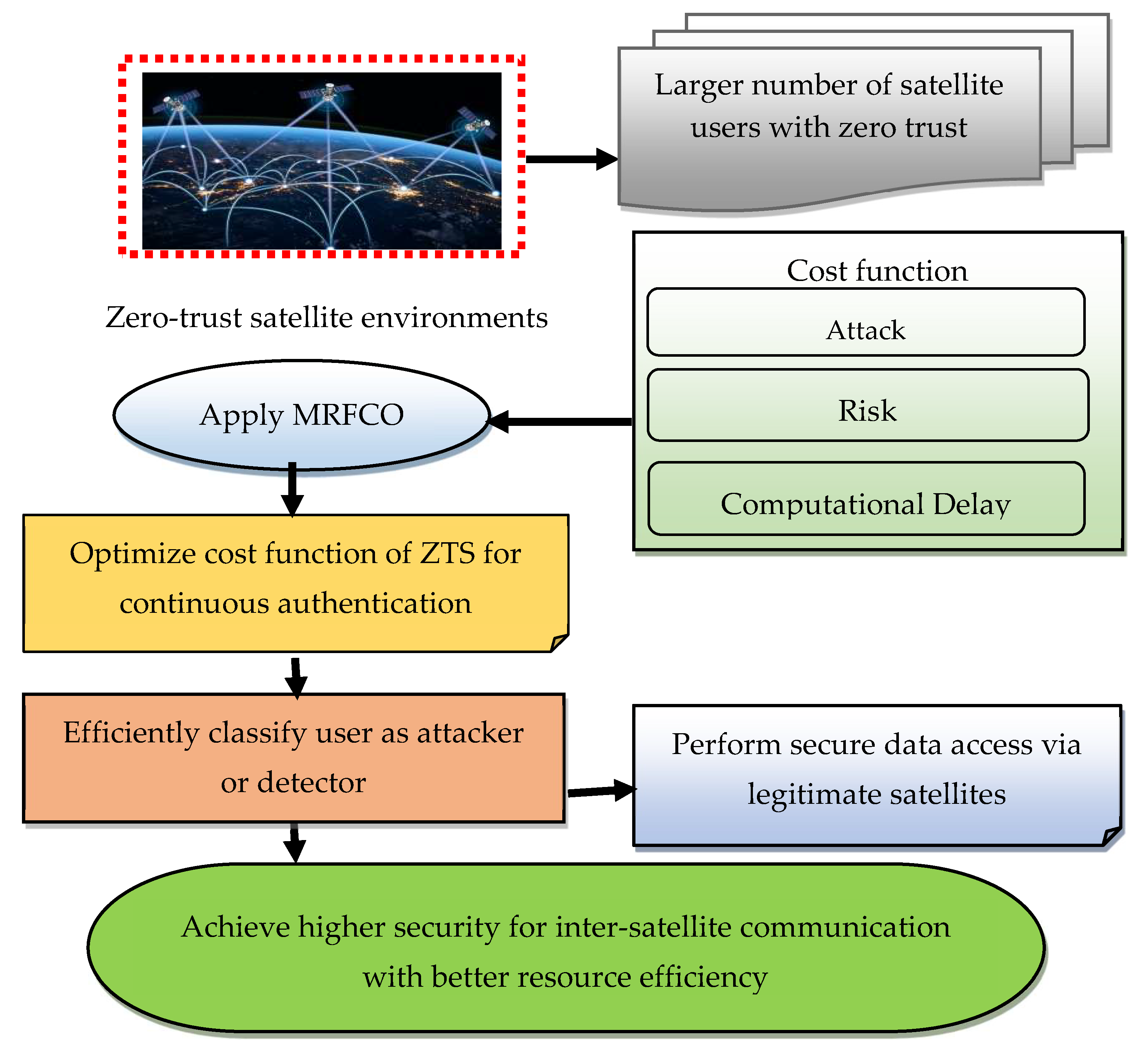
4. The Development of the MRFCO-ZTS Approach
4.1. The Architecture of MRFCO-ZTS-Secured LEO Satellite Network
4.2. MRFCO-ZTS Approach
- (1)
- Chain foraging: Create sequential foraging using the mathematical formulation below:
- (2)
- Cyclone Foraging: Forms circular swimming to encircle, using the formula below:
- (3)
- Somersault Foraging: Local fine-tuning through somersault maneuvers, using the formula below:
| Algorithm 1 Manta ray foraging cost-optimized zero-trust security approach for attacker/detector classification algorithm |
| 1: Input: Number of satellites ’; Behavior logs, access pattern, trust score 2: Output: Minimum-cost classification model (deny, allow) for achieving higher security 3: Begin 4: Number of satellite users ’ 5: For all satellite users in the network 6: Define cost function 7: Determine Attack likelihood score ‘’ 8: Measure cumulative user risk 9: Calculate computational delay 10: Define the Objective Function of optimization 11: Apply MRFCO Concept, initialize population by considering ‘’ 12: For each , Measure fitness 13: While not termination 14: Choose foraging mode (Chain, Cyclone, Somersault) 15: Update position 16: Determine new fitness i.e., Re-evaluate cost, Update if required 17: Return as optimal parameters for ZTS classification 18: Cyclone Foraging 19: Somersault Foraging 20: 21: End While 22: End For 23: End |
5. Simulation
- Security level;
- Latency;
- Efficiency.
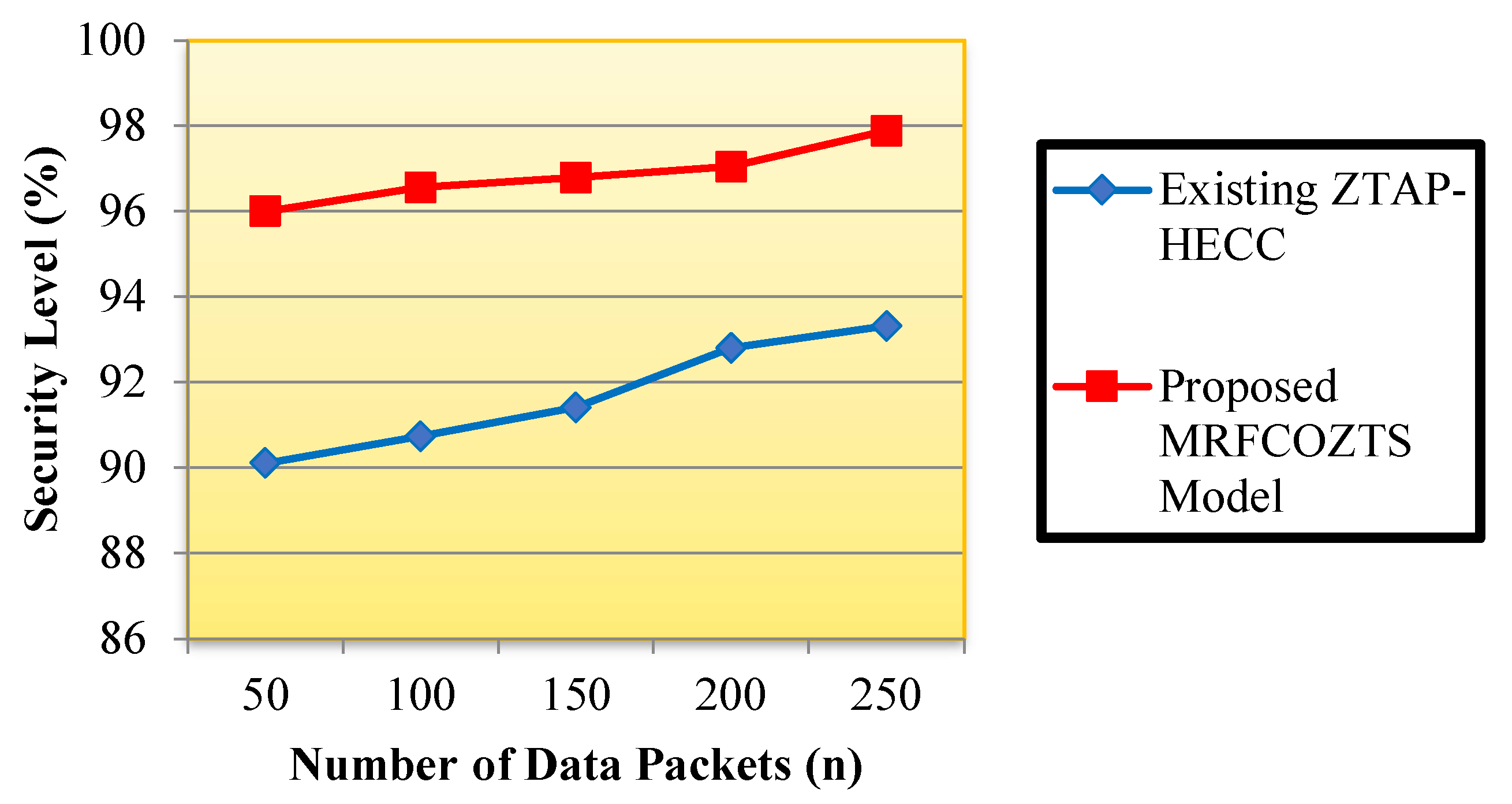
5.1. Performance Measure of Security
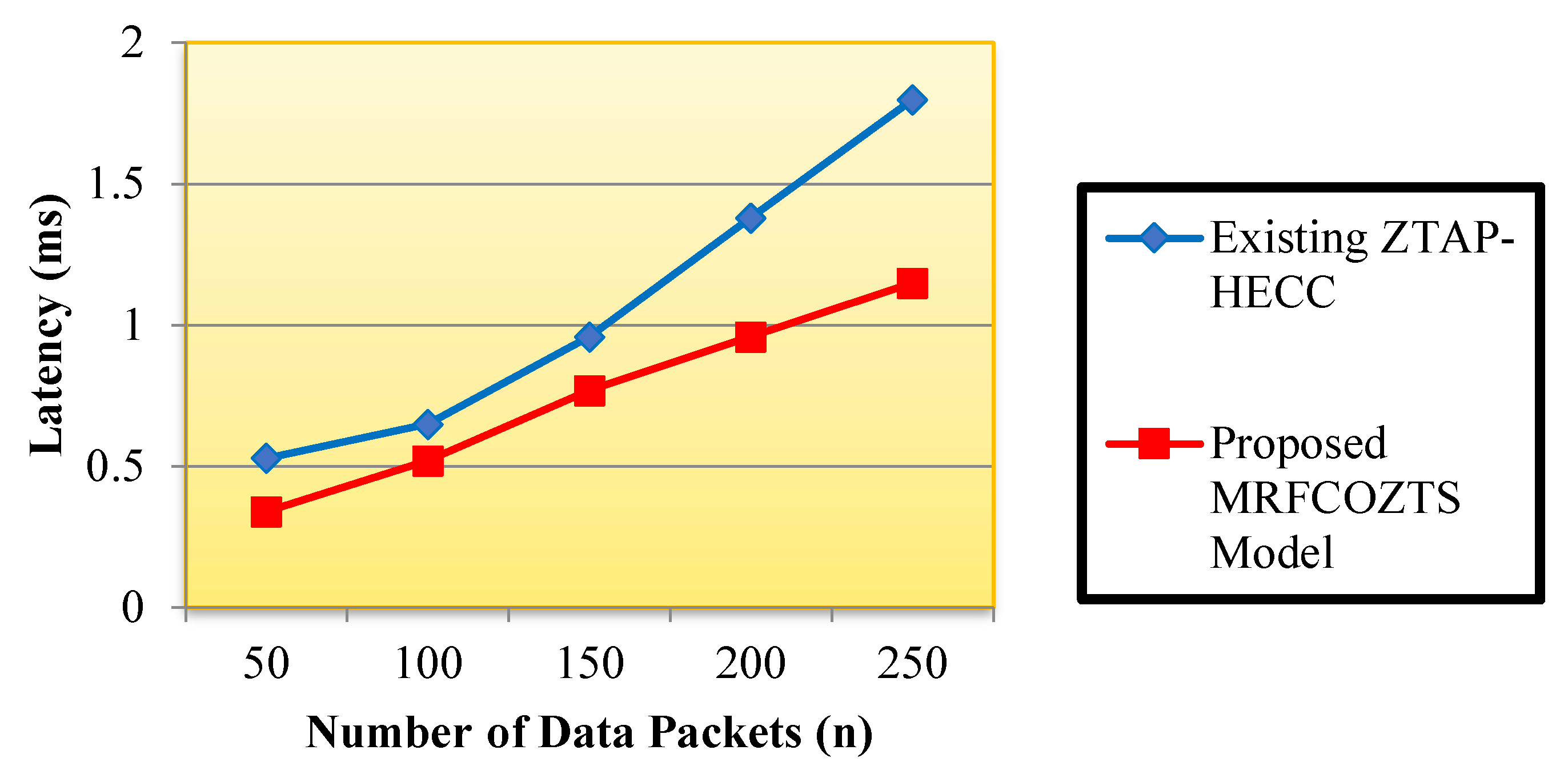
5.2. Performance Measure of Latency
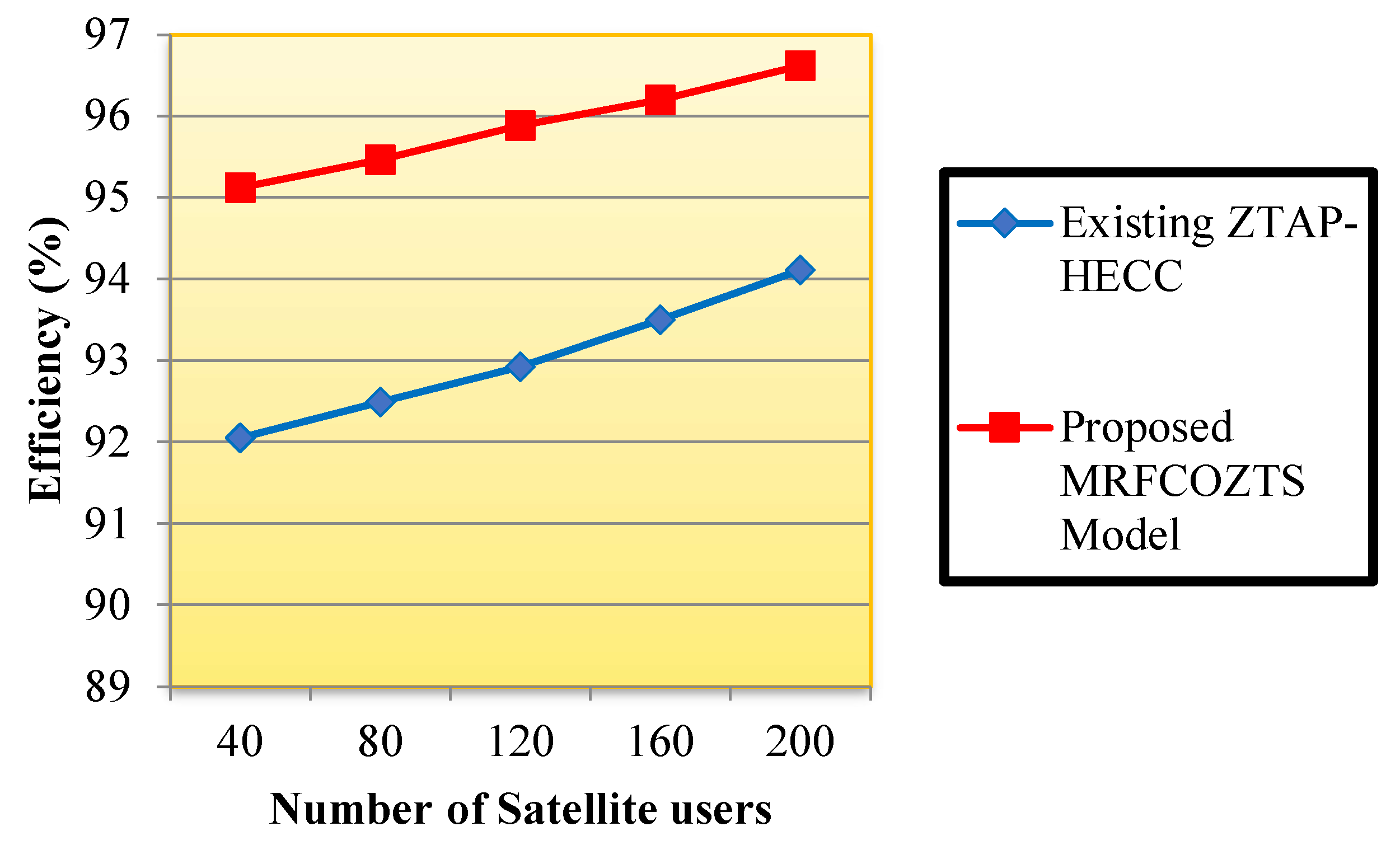
5.3. Performance Measure of Efficiency
5.4. Scalability to Large Satellite Constellations (e.g., 1000+ Nodes)
5.5. Energy/Resource Consumption per Authentication Cycle
5.6. Robustness to Adaptive Attacks (e.g., Mimicry, Distributed Spoofing)
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Farreaa, K.A.; Baig, Z.; Dossa, R.; Liu, D. Zero Trust-Based Authentication for Inter-Satellite Links in NextGen Low Earth Orbit Networks. Ad Hoc Netw. 2025, 174, 103817. [Google Scholar] [CrossRef]
- Farreaa, K.A.; Baig, Z.; Doss, R.R.M.; Liu, D. Provably Secure Optimal Homomorphic Signcryption for Satellite-Based Internet of Things. Comput. Netw. 2024, 250, 110516. [Google Scholar] [CrossRef]
- Qi, M.; Chen, J.; Chen, Y. A Secure Authentication with Key Agreement Scheme Using ECC for Satellite Communication Systems. Int. J. Satell. Commun. Netw. 2024, 42. In Press. [Google Scholar] [CrossRef]
- Abdrabou, M.; Gulliver, T.A. Authentication for Satellite Communication Systems Using Physical Characteristics. IEEE Open J. Veh. Technol. 2022, 4, 48–60. [Google Scholar] [CrossRef]
- Murtaza, A.; Xu, T.; Pirzada, S.J.H.; Jianwei, L. A Lightweight Authentication and Key Sharing Protocol for Satellite Communication. Int. J. Comput. Commun. Eng. 2020, 9, 1–6. [Google Scholar] [CrossRef]
- Huang, C.; Zhang, Z.; Li, M.; Zhu, L.; Zhu, Z.; Yang, X. A Mutual Authentication and Key Update Protocol in Satellite Communication Network. Automatika 2020, 61, 334–344. [Google Scholar] [CrossRef]
- Pokhrel, S.R. Poster: Orbital ZTA! Secure Satellite Communication Networks with Zero Trust Architecture. In Proceedings of the ACM SIGCOMM 2024 Conference: Posters and Demos, New York, NY, USA, 4–8 August 2024; pp. 33–35. [Google Scholar] [CrossRef]
- Guo, Y.; Wang, J.; Geng, K.; Li, Z.; Li, F.; Fang, L. SEHAP: Secure and Efficient Handover Authentication Protocol in LEO Satellite Non-Terrestrial Networks. In Proceedings of the IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Hyderabad, India, 3–7 March 2025; pp. 1–5. [Google Scholar] [CrossRef]
- Ostad-Sharif, A.; Abbasinezhad-Mood, D.; Nikooghadam, M. Efficient Utilization of Elliptic Curve Cryptography in Design of a Three-Factor Authentication Protocol for Satellite Communications. Comput. Commun. 2019, 147, 85–97. [Google Scholar] [CrossRef]
- Chen, Y.; Chen, J. Robust Three-Factor Authentication Protocol for Satellite Communication Systems. Int. J. Commun. Syst. 2020, 33, 1–12. [Google Scholar] [CrossRef]
- Luo, Y.; Cao, J.; Shang, C.; Ma, R.; Niu, B.; Zhang, Y.; Li, H. NSAA: A Network Slice Access Authentication and Service Authorization Scheme for Integrated Satellite-Terrestrial Network. IEEE Internet Things J. 2024, 12, 7636–7651. [Google Scholar] [CrossRef]
- Suhaimi, N.H.S.; Kamarudin, N.H.; Khalid, M.N.A.; Tahir, I.; Mohamed, M.A.A. State-of-the-Art Authentication Measures in Satellite Communication Networks: A Comprehensive Analysis. IEEE Access 2024, 12, 142241–142264. [Google Scholar] [CrossRef]
- Gautam, D.; Kanwar, S.; Prajapat, S.; Kumar, P.; Chen, C. A Robust ECC-Based Authentication Protocol for Satellite-to-Satellite Communication Network. Telecommun. Syst. 2024, 87, 541–559. [Google Scholar] [CrossRef]
- Prajapat, S.; Kumar, P.; Kumar, S.; Das, A.K.; Shetty, S.; Hossain, M.S. Designing High-Performance Identity-Based Quantum Signature Protocol with Strong Security. IEEE Access 2024, 12, 14647–14658. [Google Scholar] [CrossRef]
- Guo, J.; Du, Y.; Zhang, D.; Wu, R. PSEEMV: Provably Secure and Efficient Emergency Message Verification Scheme Based on ECC and CRT for Space Information Network. J. Inf. Secur. Appl. 2023, 73, 103437. [Google Scholar] [CrossRef]
- Yang, Y.; Cao, J.; Ren, X.; Niu, B.; Zhang, Y.; Li, H. LK-AKA: A Lightweight Location Key-Based Authentication and Key Agreement Protocol for S2S Communication. Comput. Commun. 2023, 197, 214–229. [Google Scholar] [CrossRef]
- Liu, Y.; Ni, L.; Peng, M. A Secure and Efficient Authentication Protocol for Satellite-Terrestrial Networks. IEEE Internet Things J. 2023, 10, 5810–5822. [Google Scholar] [CrossRef]
- Guo, J.; Du, Y. A Secure Three-Factor Anonymous Roaming Authentication Protocol Using ECC for Space Information Networks. Peer Peer Netw. Appl. 2021, 14, 898–916. [Google Scholar] [CrossRef]
- Gunn, L.; Smet, P.; Arbon, E.; McDonnell, M.D. Anomaly Detection in Satellite Communications Systems Using LSTM Networks. In Proceedings of the 2018 Military Communications and Information Systems Conference (MilCIS), Canberra, Australia, 13–15 November 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Tedeschi, P.; Sciancalepore, S.; Di Pietro, R. Satellite-Based Communications Security: A Survey of Threats, Solutions, and Research Challenges. Comput. Netw. 2022, 216, 109246. [Google Scholar] [CrossRef]
- Ramezanpour, K.; Jagannath, J. Intelligent Zero Trust Architecture for 5G/6G Networks: Principles, Challenges, and the Role of Machine Learning in the Context of O-RAN. Comput. Netw. 2022, 217, 109299. [Google Scholar] [CrossRef]
- Peng, C.; Zhou, Q.; Shen, Y.; He, K.; Lian, Z.; Shuai, Z. Zero-Trust Security Strategy for Renewable Power Plant Clusters Under Integrated Satellite-Terrestrial Networks. IEEE Trans. Ind. Appl. 2025; In Press. [Google Scholar] [CrossRef]
- Annabi, M.; Zeroual, A.; Messai, N. Towards Zero Trust Security in Connected Vehicles: A Comprehensive Survey. Comput. Secur. 2024, 145, 104018. [Google Scholar] [CrossRef]
- Fu, P.; Wu, J.; Lin, X.; Shen, A. ZTEI: Zero-Trust and Edge Intelligence Empowered Continuous Authentication for Satellite Networks. In Proceedings of the IEEE Global Communications Conference (GLOBECOM), Rio de Janeiro, Brazil, 5–9 December 2022; pp. 2376–2381. [Google Scholar] [CrossRef]
- Lin, C.-L.; Hsu, T.-E. A Multi-Factor Authentication Scheme Based on Zero Trust Network Access for LEO Satellite Communication Systems. In Proceedings of the 2024 International Conference on Intelligent Computing and Next Generation Networks (ICNGN), Bangkok, Thailand, 23–25 November 2024; pp. 1–5. [Google Scholar] [CrossRef]
- Wang, Y.; Gong, J.; Zhang, J.; Han, X. A Deep Learning Anomaly Detection Framework for Satellite Telemetry with Fake Anomalies. Int. J. Aerosp. Eng. 2022, 2022, 1–9. [Google Scholar] [CrossRef]
- Sadr, M.A.M.; Zhu, Y.; Hu, P. Satellite Anomaly Detection Using Variance Based Genetic Ensemble of Neural Networks. In Proceedings of the IEEE International Conference on Communications (ICC 2023), Rome, Italy, 28 May–1 June 2023; pp. 4070–4075. [Google Scholar] [CrossRef]
- Wu, X.; Zheng, T.; Wu, R.; Zhou, H.; Huang, Y.; Zhang, J. Hi-SAM: A High-Scalable Authentication Model for Satellite-Ground Zero-Trust System Using Mean Field Game. J. Netw. Syst. Manag. 2025, 33, 72. [Google Scholar] [CrossRef]
- Wang, Z.; Cao, J.; Di, X. Anomaly Detection Method for Satellite Networks Based on Genetic Optimization Federated Learning. Expert Syst. Appl. 2025, 295, 128627. [Google Scholar] [CrossRef]
- Yang, Y.; Wang, L.; Xu, F. Secure and Energy-Efficient Beamforming for LEO Satellite Downlink via Intelligent Surfaces. IEEE Trans. Commun. 2024, 72, 1234–1246. [Google Scholar] [CrossRef]

| Symbol | Meaning |
|---|---|
| Attack likelihood score for user/session (0 to 1) | |
| Risk impact if misclassification occurs (0 to 1) | |
| Computational delay or verification latency for (in milliseconds) | |
| Misclassification penalty, 1 if misclassified, 0 otherwise | |
| Tunable weights for security, performance, accuracy |
| Detector Action | |
|---|---|
| = Legitimate | Give full access to all services |
| = Attacker | Immediate block, alert, forensic log |
| Component | Specification |
|---|---|
| Processor (CPU) | Intel Core i5-11400F @ 2.60 GHz (6 cores, 12 threads) (Intel Corporation, Santa Clara, CA, USA) |
| RAM | 16 GB DDR4 @ 3200 MHz (MHzKingston Technology, Fountain Valley, CA, USA) |
| Storage | 512 GB NVMe SSD (Kingston Technology, Fountain Valley, CA, USA) |
| GPU (optional use) | NVIDIA GTX 1650 (4 GB GDDR6, CUDA-capable) (NVIDIA Corporation, Santa Clara, CA, USA) |
| Power Supply | 500 W PSU, consistent 220 V input (Corsair Components, Fremont, CA, USA) |
| Operating System | Windows 10 Pro (64-bit), version 22H2 (Microsoft Corporation, Redmond, WA, USA) |
| Category | Configuration |
|---|---|
| Simulation Platform | MATLAB R2024b (64-bit) |
| MATLAB Toolboxes | Optimization Toolbox; Statistics and Machine Learning Toolbox |
| Programming Language | MATLAB scripting (M-code) |
| Execution Mode | Script and function-based batch simulations |
| Parallel Computing | Disabled (single-node simulation) |
| Function | Description |
|---|---|
| fmincon() | Constrained optimization (baseline comparison) |
| Custom mrfo_cost_function() | Implements MRFO-based attacker classification |
| rand(), normrnd() | Random-number generation for synthetic user behavior |
| surf(), plot3(), bar() | Visualization of cost landscapes and classification results |
| Custom trust-score module | Rule-based and probabilistic trust-score evaluation |
| tic; toc; | Used for measuring simulation time |
| Element | Value/Description |
|---|---|
| User Sessions Simulated | 250 to 1200 dynamic users per run |
| Session Duration | 600 s (10 min real-time simulation) |
| Cost Function Range | 0.1 to 4.8 |
| Authentication Cycle | Every 1.5–3 s (configurable interval) |
| Attack Behavior | Injected synthetic mimicry, burst, and random attacks |
| Trust Score Model | Probabilistic model based on user activity logs |
| Classification Output | Binary (Legitimate, Attacker), with risk tagging |
| User_ID | Sessions | Avg_Risk_Score | Suspicious_Sessions | Total_Cost | User_Type |
|---|---|---|---|---|---|
| “User_1” | 39 | 0.82 | 27 | 318.82 | “Attacker” |
| “User_2” | 43 | 0.62 | 22 | 268.25 | “Detector” |
| “User_3” | 37 | 0.63 | 16 | 223.85 | “Detector” |
| “User_4” | 34 | 0.63 | 17 | 214.93 | “Detector” |
| “User_5” | 32 | 0.7 | 18 | 253.74 | “Attacker” |
| Number of Data | Security Level (%) | |
|---|---|---|
| Packets | Existing ZTAP-HECC | Proposed MRFCO-ZTS Mode |
| 50 | 90.11 | 96 |
| 100 | 90.73 | 96.55 |
| 150 | 91.41 | 96.79 |
| 200 | 92.80 | 97.04 |
| 250 | 93.32 | 97.88 |
| Number of Data | Latency (ms) | |
|---|---|---|
| Packets | Existing ZTAP-HECC | Proposed MRFCO-ZTS Model |
| 50 | 0.53 | 0.34 |
| 100 | 0.65 | 0.52 |
| 150 | 0.96 | 0.77 |
| 200 | 1.38 | 0.96 |
| 250 | 1.80 | 1.15 |
| Number of Satellite | Efficiency (%) | |
|---|---|---|
| Users | Existing ZTAP-HECC | Proposed MRFCO-ZTS Model |
| 40 | 92.05 | 95.12 |
| 80 | 92.49 | 95.46 |
| 120 | 92.92 | 95.88 |
| 160 | 93.50 | 96.20 |
| 200 | 94.11 | 96.62 |
| Satellites | Authentication Accuracy (%) | Average Latency (ms) | Average MRFO Iterations | Peak Memory Per Node (MB) |
|---|---|---|---|---|
| 250 | 96.6 | 1.10 | 42 | 4.2 |
| 500 | 95.8 | 1.35 | 45 | 5.3 |
| 750 | 94.7 | 1.72 | 48 | 6.1 |
| 1000 | 93.4 | 2.08 | 52 | 6.9 |
| 1200 | 91.9 | 2.46 | 57 | 7.5 |
| Action Phase | Avg CPU Time (ms) | Energy Consumption (mJ) | Comm Overhead (Bytes/Session) |
|---|---|---|---|
| Trust Score Calculation | 3.5 | 12.2 | 250 |
| Cost Function Evaluation | 2.8 | 10.5 | — |
| MRFO-Based Optimization | 5.2 | 19.1 | — |
| Final Classification and Action | 1.1 | 3.8 | 150 (alert or grant signal) |
| Total per Cycle | 12.6 ms | 45.6 mJ | ~400 bytes |
| Attack Type | Detection Rate (%) | False Negative Rate (%) | Avg Detection Delay (ms) | Remarks |
|---|---|---|---|---|
| Baseline Random Attack | 97.4 | 2.6 | 1.3 | High sensitivity maintained |
| Mimicry Behavior Attack | 89.5 | 10.5 | 2.4 | Delay increases; cost function less discriminative |
| Distributed Coordinated | 91.8 | 8.2 | 2.1 | MRFO adaptation helps isolate spatial patterns |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Varadala, S.; Xu, H. A Biologically Inspired Cost-Efficient Zero-Trust Security Approach for Attacker Detection and Classification in Inter-Satellite Communication Networks. Future Internet 2025, 17, 304. https://doi.org/10.3390/fi17070304
Varadala S, Xu H. A Biologically Inspired Cost-Efficient Zero-Trust Security Approach for Attacker Detection and Classification in Inter-Satellite Communication Networks. Future Internet. 2025; 17(7):304. https://doi.org/10.3390/fi17070304
Chicago/Turabian StyleVaradala, Sridhar, and Hao Xu. 2025. "A Biologically Inspired Cost-Efficient Zero-Trust Security Approach for Attacker Detection and Classification in Inter-Satellite Communication Networks" Future Internet 17, no. 7: 304. https://doi.org/10.3390/fi17070304
APA StyleVaradala, S., & Xu, H. (2025). A Biologically Inspired Cost-Efficient Zero-Trust Security Approach for Attacker Detection and Classification in Inter-Satellite Communication Networks. Future Internet, 17(7), 304. https://doi.org/10.3390/fi17070304





