Leveraging Blockchain Technology for Secure 5G Offloading Processes †
Abstract
1. Introduction
- Limited infrastructure: The 5G network requires a dense infrastructure of base stations and antennas to provide adequate coverage within cities. However, existing infrastructure today is not enough for the large number of current and future services.
- Signal interference: 5G signals, especially in the higher frequency bands, are more susceptible to interference from physical obstacles such as buildings, trees, and other urban elements in the city, resulting in shadow areas where coverage is poor or non-existent.
- Upgrade costs: Extending an existing 5G network is costly, as it requires the installation of new base stations and antennas, and can be prohibitive for some cities.
- Regulations: Installing a new 5G infrastructure (base stations or antennas) requires obtaining permits and complying with local regulations. This process can be slow and bureaucratic, delaying the expansion of 5G.
- Coverage disparity: In many cities, 5G coverage is unequal, with central and busy areas receiving better coverage than peripheral or less populated ones.
- Environmental impact: The installation of additional base stations may raise concerns about the environmental impact on cities.
- Improved Coverage: In areas where the 5G signal is weak, intermittent, or inexistent, offloading to other networks provides an additional reliable connection.
- Congestion Reduction: By diverting some traffic to alternative networks, the load on the core 5G network is reduced, improving the quality of service.
- Resource Optimization: Offloading allows for better utilization of available resources, as alternative networks can handle the additional traffic without negatively impacting the core network.
- Cost Savings: For network operators, offloading can be a more cost-effective way to manage data, as it avoids the need to invest in additional 5G infrastructure.
- Flexibility and Scalability: Offloading offers a flexible and scalable solution for managing data traffic in dynamic urban environments, adapting to changing network needs.
2. State-of-the-Art
2.1. Blockchain-Based Marketplaces
- Blockchain removes the need for intermediaries. Unlike traditional marketplaces that rely on a central authority, Blockchain-based marketplaces operate on a decentralized network. This way, costs are usually reduced.
- Transparency is increased as all transactions on a Blockchain are visible to all participants in the network, increasing trust and fairness among users, as they can verify the authenticity and history of transactions.
- Security based on cryptographic techniques used for the link between blocks to provide an immutable ledger. This ensures that all transactions are tamper-proof and verifiable.
- Smart Contracts automatically execute transactions when specific conditions are met, reducing the need for manual interaction and minimizing the risk of fraud [41].
- Public Blockchain networks usually face scalability issues due to the large number of transactions that need to be processed. This often results in longer processing times and higher transaction costs.
- Although transactions on public networks are transparent, the identity of the participants is not always known, which could be an issue within bidding processes.
- Consensus mechanisms in public networks are usually more energy demanding, reducing efficiency and increasing costs.
2.2. Authentication in 5G Networks
- 5G-AKA-FS [62]: This protocol aims to provide both forward secrecy and unlinkability. It introduces modifications to the key generation process and implements additional security measures to prevent active attacks.
- 5G-IPAKA [65]: This improved protocol focuses on mutual authentication between the User Equipment (UE) and the Serving Network (SN), as well as enhanced security for the anchor key and authentication vector.
- SUCI-AKA [66]: This variant reuses the Elliptic Curve Integrated Encryption Scheme (ECIES) secret to address linkability attacks.
2.2.1. Self-Sovereign Identity (SSI)
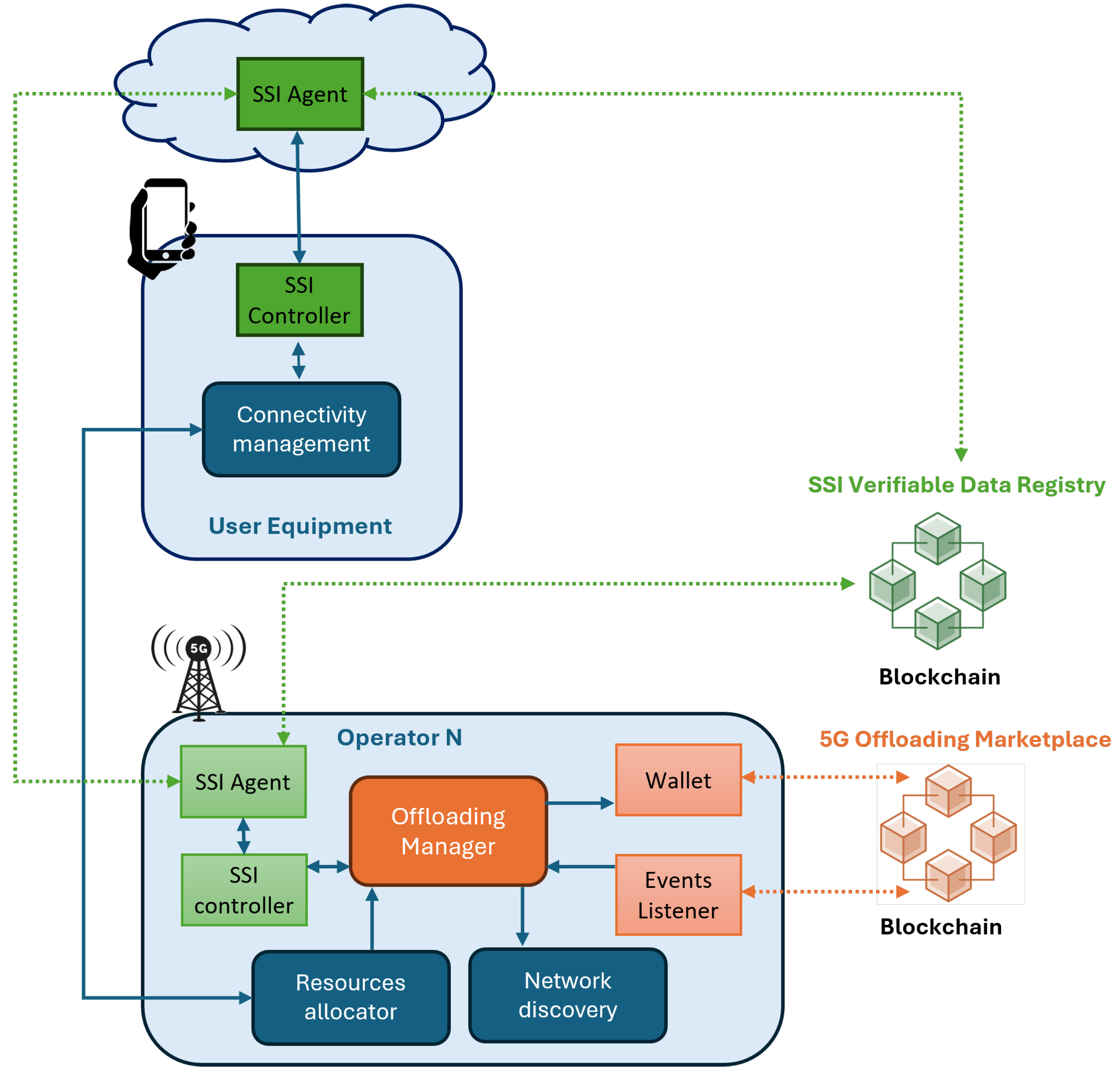
3. Blockchain-Based Secure 5G Offloading Mechanism
- New offloading manager logic which receives the current network state and manages offloading processes when needed. Once an offloading is agreed, it makes a request for resources de-allocation (for primary operator) and allocation (for secondary operator).
- A wallet for the correct Blockchain transactions creation and signature. It will be used by operators for network state updates and secondary operators searching processes.
- Events listener to receive Blockchain events about the new offloading requests. Each registered operator will receive an event with the offloading characteristics.
- SSI controller which will manage the user equipment authentication in any of the operator networks avoiding credentials sharing and identity thefts. The primary operator will issue a credential to the user equipment making the offloading process to the secondary operator, which will verify the identity of the credential prior to the resources allocation.
- SSI agent which will manage the identity of the user equipment through verifiable credentials. The identity issuance (primary operator) and the validation (secondary operator) are executed.
- SSI controller which will manage the user equipment identity received from the primary operator to be offloaded to the secondary operator.
- SSI agent which will manage the reception and secure storage of the received credential from the primary operator as well as the credential sharing for being authenticated in the secondary operator.
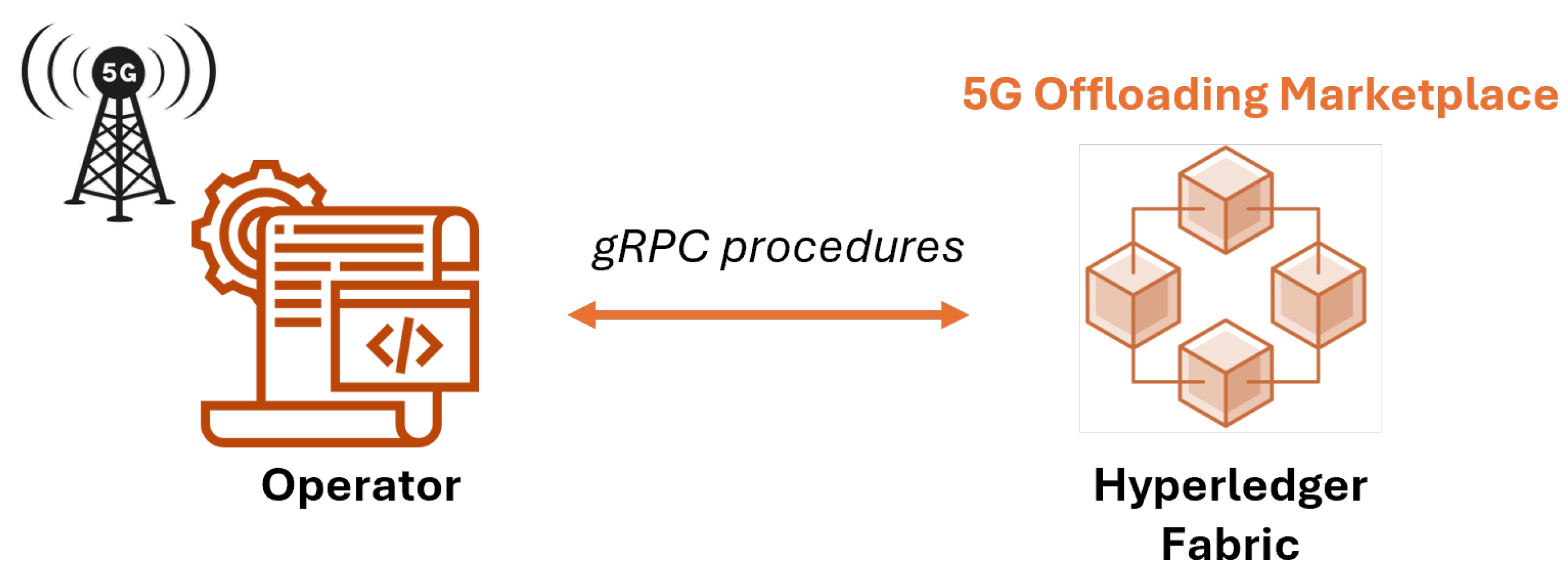
3.1. Blockchain for a Secure Marketplace
- Resource optimization: A marketplace allows operators to select the best available options for offloading (i.e., right capacity, optimal location, lower costs, etc.). By having access to a variety of options, operators can make informed decisions that maximize performance and minimize costs.
- Flexibility: A marketplace allows operators to adapt to fluctuations in data and processing demand. This is crucial in situations where workloads can vary significantly (i.e., mass events).
- Competition: A marketplace promotes competition among operators as other operators can compare prices, which incentivizes providers to improve their offerings and reduce costs. This healthy competition results in better services and lower prices.
- Ease of integration: Operators can access a centralized platform where they can find and offloading services without the need for complex individual negotiations, improving operational efficiency.
- Innovation: The presence of a marketplace encourages the development of new technologies and solutions as operators have an incentive to develop and offer new capabilities and improvements (i.e., better energy efficiency) to attract more users.
- Improved satisfaction: A marketplace allows the definition of filters in order to make the operators to select services that best meet their performance, cost, and location requirements, resulting in improved satisfaction.
3.1.1. Architecture and Components
3.1.2. Data Models and Operations
- The Operator endpoints, which refer to the logic related to each operator identity as well as available resources. Each operator has a unique identifier id, a name (for identification purposes), and a type that categorizes its role within the marketplace. In addition, a percentage of available resources is also included in terms of RAM, CPU, and storage. The following operations related to the operator are available as follows:
- -
- Create: Registers a new operator in the system;
- -
- Update: Modifies an existing operator information. This must be done periodically to keep the marketplace updated;
- -
- Get: Retrieves the information-related to a given operator;
- -
- Delete: Removes an operator from the marketplace;
- -
- List: Retrieves a list of all registered operators.
- The Service endpoints, which refer to the logic related to the services offered by different operators. Each service has a unique identifier id, an operator id (identifying the operator offering the service), the price, the location, the uplink throughput, downlink throughput, and the status, which refers to the availability status. In addition, the requirements in terms of RAM, CPU, and storage are also indicated. The following operations related to the operator are available as follows:
- -
- Create: Registers a new service of an operator;
- -
- Update: Modifies existing service-related information. This must be done periodically to keep the marketplace updated;
- -
- Get: Retrieves the information related to a specific service;
- -
- Delete: Removes a service from the marketplace;
- -
- List: Retrieves a list of all available services.
- The Consumption endpoints, which refer to the logic which allows an operator to search for additional suitable services from other registered operators and be able to proceed with an offloading process. The consumption request includes a unique identifier id, the identifier of the requester operator requester id, and a list of minimum requirements to be fulfilled by the selected service and related operator. This list is variable and refers to the information related to the operator and service data models (i.e., location should be Paris, UL throughput should be higher than 33 Mbps, etc.). There are only two related operations:
- -
- Search: Initiates a new search of suitable services in the marketplace according to the defined requirements.
- -
- Get Result: It provides the result of the search request. It can indicate it is still an ongoing process or it can provide the selected service as a result when the process has finished. This operation has been included for developers, as the result of the search operation will be notified to the involved primary and secondary operators through Blockchain events.
- Initiate Consumption Request. The primary operator makes a search request in the marketplace specifying the minimum desired service requirements.
- Service Evaluation Phase. From all registered services whose status is available, the marketplace identifies the suitable services that meet the given requirements.
- Operator Evaluation Phase. For each of the identified services, the marketplace checks if the associated operator has the minimum required resources in terms of RAM, CPU, and storage available.
- Service selection. From the identified services, the marketplace will choose that with the better price.
- Completion of Consumption Process. The marketplace emits a Blockchain event confirming that the process has been successfully completed and indicating the following information:
- The identifier of the consumption request the answer refers to;
- The identifier of the primary operator making the request;
- The identifiers of the selected secondary operator and service;
- The identifier of the UE whose required resources will be offloaded;
- A list with the minimum requirements specified in the request by the primary operator;
- A list of the actual values provided by the selected secondary operator and service for the defined requirements;
- The price of the offloading process for the selected secondary operator and service.
This event will be received by the primary and secondary selected operators to indicate that they should proceed with the offloading process according to Figure 2.
- The marketplace sends a new Blockchain event with the information (identifier) about the operators of the suitable identified services after the three previous steps.
- The oracle receives the event, processes it and extracts the list of operators identifiers whose rating values are needed. It also makes a request to the external service with the list of operators.
- The external service operation happens and, as a result, the rating value for each operator in the list is obtained and sent back to the oracle as response.
- The oracle processes the received information and creates and signs the suitable transaction to invoke the new method to update the rating internal information to be considered by the marketplace most suitable service selection.
- The new method in the marketplace smart contract will be executed providing as a result the most suitable service in terms of associated operator rating values.
- Step 5 is then executed in the same way as explained, resulting in a Blockchain event to notify the primary and secondary selected operators.
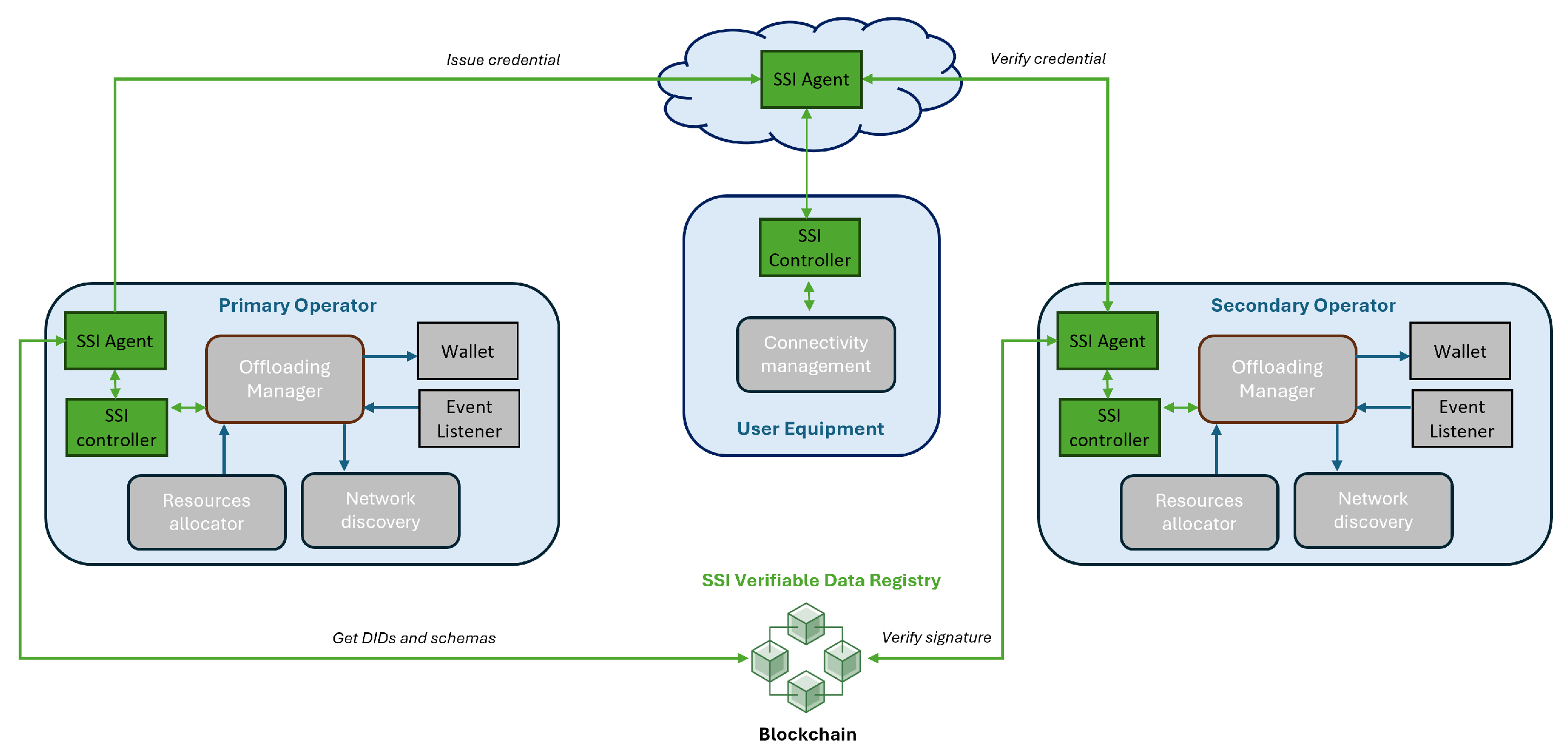
3.2. Blockchain for Secure Authentication Among Operators
3.2.1. Architecture and Components
- Automatic mode. ACA-Py agents might be configured in an automatic mode that implies that there is no need to ask the controller what to do. In this case, the Arduino SSI agent would always automatically accept all the received credentials and would always automatically respond with a proof from the credential to every verification request. This would release the SSI controller of the 5G user equipment (Arduino) of any control action. However, this approach is very limited, as the user equipment could not take any decision.
- Polling. In this case, the controller would periodically poll the ACA-Py agent to check if any action needs to be performed. This would allow the SSI controller (Arduino) to make decisions according to any specified authentication logic. This includes that it could decide whether to accept or not a credential and if sending or not proof as a response to a verification request.
3.2.2. Operation
- The SSI controller of the primary operator receives the information by the offloading event with all the information required to issue the identity credential.
- The SSI controller of the primary operator notifies the SSI agent to create the credential with the required attributes.
- The SSI agent obtains the schema and DID information of the UE from the Hyperledger Indy Blockchain network.
- The SSI agent of the primary operator issues the identity credential to the UE SSI agent.
- Periodically, the SSI controller of the UE is polling the SSI agent for news.
- For the polling request in which the SSI agent of the UE has already received the credential, the UE SSI controller decides to accept or not the credential.
- If the credential is accepted, the SSI agent locally stores it and the release of resources can happen in the primary operator.
- The SSI controller of the secondary operator receives the information from the offloading event with all the information required to request an identity proof to the particular UE (UE identifier).
- The SSI controller of the secondary operator notifies the SSI agent to create an identity proof request to the UE.
- The SSI agent obtains the schema and DID information of the UE from the Hyperledger Indy Blockchain network.
- The SSI agent of the secondary operator sends the identity proof request to the UE SSI agent.
- Periodically, the SSI controller of the UE is polling the SSI agent for news.
- For the polling request in which the SSI agent of the UE has already received the identity proof request, the UE SSI controller decides to accept or not the issuance of a proof response.
- If the proof request is accepted, the SSI agent lof the UE sends the associated proof response to the SSI agent of the secondary operator.
- Periodically, the SSI controller of the secondary operator is polling the SSI agent for news.
- For the polling request in which the SSI agent of the secondary operator has already received the proof response, the SSI controller decides to accept or not it.
- If the proof response is accepted, the SSI agent of the secondary operator verifies the signatures of the received proof response against the Hyperledger Indy Blockchain network to be sure of its authenticity.
- The SSI controller of the secondary operator continues polling its agent periodically.
- For the polling request in which the SSI agent has already verified the proof response, the SSI agent sends the verification result to the SSI controller, which analyses the offloading parameters and provides the required and agreed resources to the UE.
4. Performance Evaluation
4.1. Blockchain-Based Operators Marketplace
- Prior to the offloading process:
- -
- An operator registration process. The Create operation from the Operator endpoints is executed by an operator administrator. This process execution time is negligible in comparison with the time required for one block to be aggregated to the Blockchain network, which is variable according to some configuration parameters. In the considered example Blockchain network, this time is around 2 s. It is an example value that could be optimized in a real deployment. Anyway, the impact of this time is not relevant as it will happen only once, when the operator decides to participate in the marketplace, prior to any offloading process.
- -
- A service registration process. The Create operation from the Service endpoints is executed for each available service by an operator administrator. As in the previous case, this process execution time is also negligible in comparison with the time required for the block aggregation in the Blockchain, which takes also around 2 s. This process will also happen only once per service, when the operator decides to participate in the marketplace, prior to any offloading process. Different services could be registered in the same Blockchain block, reducing and optimizing the services required registration time.
- Periodically and for each offloading process:
- -
- Each operator inside the marketplace must periodically update the percentage of available resources as well as the availability status of its services. The Update operation from the Operator and Service endpoints is executed, respectively. As in previous cases, this process takes also around 2 s due to the block aggregation time to the example Blockchain network as the operation time is negligible. This process will happen periodically and in parallel to other activities of the operator, so the offloading process quality is not degraded as the cut-off time is not increased.
- For each offloading process:
- -
- The primary operator in the offloading process makes a search request to the marketplace of the most suitable secondary operator. The Search operation from the Consumption endpoints is executed. This process happens just before the release and new provision of resources happen so the quality of service is not affected. Table 2 gathers the execution time for the search for different registered services in the marketplace, different requirements in the search request and different simultaneous search requests from different operators. The search time column refers to the average time per request taking into account that simultaneous requests can be included in the same block to be aggregated to the Blockchain network. In addition, the associated event generation time is also considered inside the search time.
- *
- It is important to notice that in the case of a single request, the search time is mainly influenced by the time required by a block to be aggregated to the example Fabric network. The number of requirements considered in the request or the number of already registered services on which to search has a low impact on the search time.
- *
- When 10 simultaneous requests are considered, around 0.4–0.5 s average search time is obtained, as the block aggregation time is shared by all the requests. Anyway, the number of requirements and the number of registered services still have no significant impact on the search time, which is still more influenced by the block aggregation time.
- *
- The situation starts to look different for 100 simultaneous requests. On the one side, the average search time for 50 and 100 registered services is around 0.15–0.19 s. However, the number of registered services starts to influence the search time with 1000 registered service, which increases the average search time up to 0.41–0.47 s. On the other hand, the situation for 10 registered services is different, as it requires a higher average search time of 0.3 s, which is higher than for 50 and 100 registered services. This could be because the search time is still mainly influenced by the time required by a block to be aggregated to the example Fabric network.
- *
- Finally, the parameters start to influence the search time when 1000 simultaneous search requests are considered. In this case, as in the previous case, the search time for 10 registered is higher than for 50 and 100 registered operators, probably due to the higher influence of the block aggregation time. However, the search time slightly increases with the number of requirements defined in the request, moving from 0.35 s for two requirements up to 0.45 s for seven requirements. The search time increases also with the number of requirements as well as with the number of registered services for 50, 100, and 1000 registered services.
- *
- As a summary, for a maximum number of 100 simultaneous requests, the search time is mainly influence by the block aggregation time to the particular Blockchain network, which can be optimized as required. However, for a higher number of simultaneous requests, such as 1000, the search time increases with the number of requirements and the number of existing registered services in the marketplace.
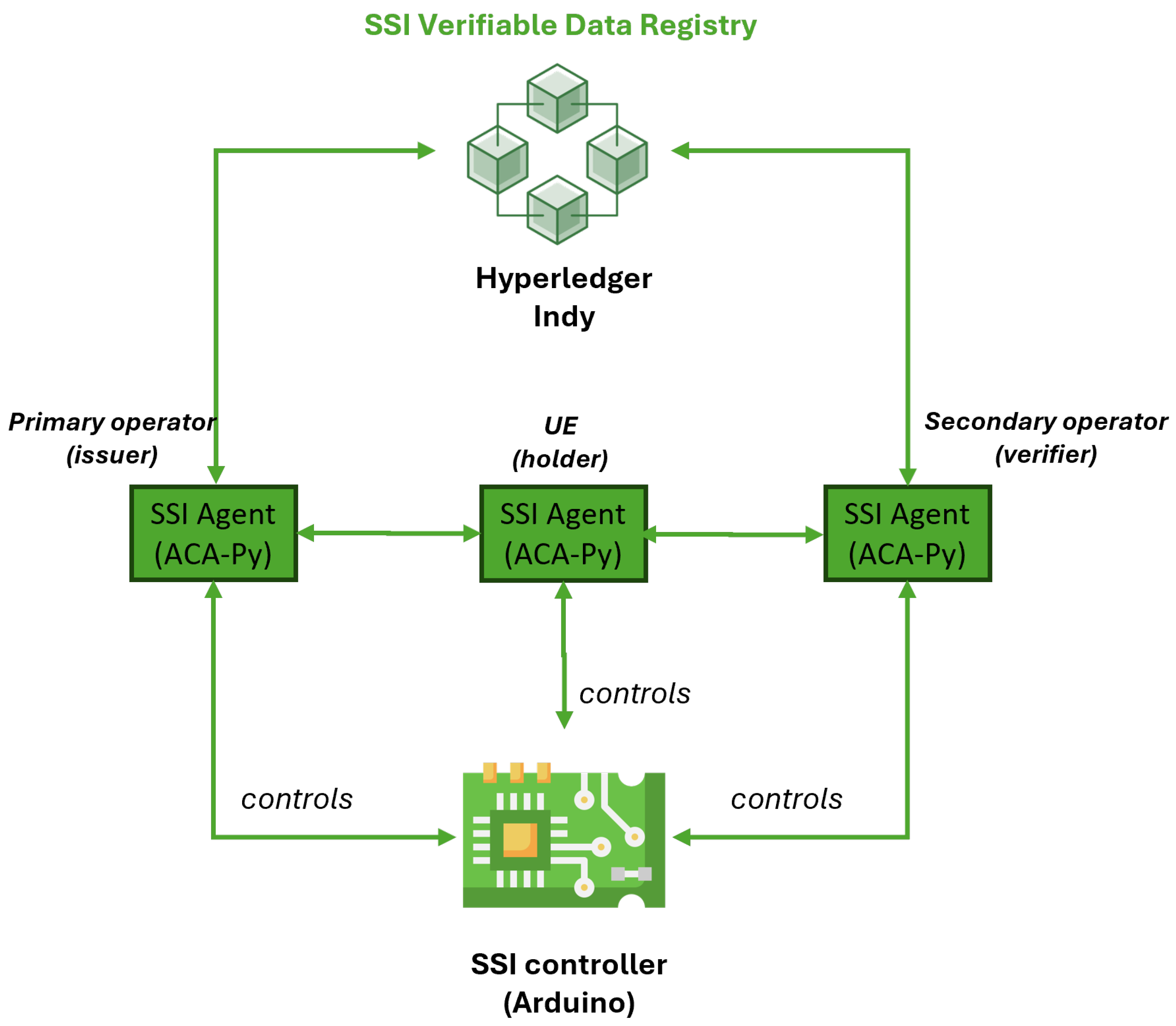
4.2. SSI-Based Authentication of UEs
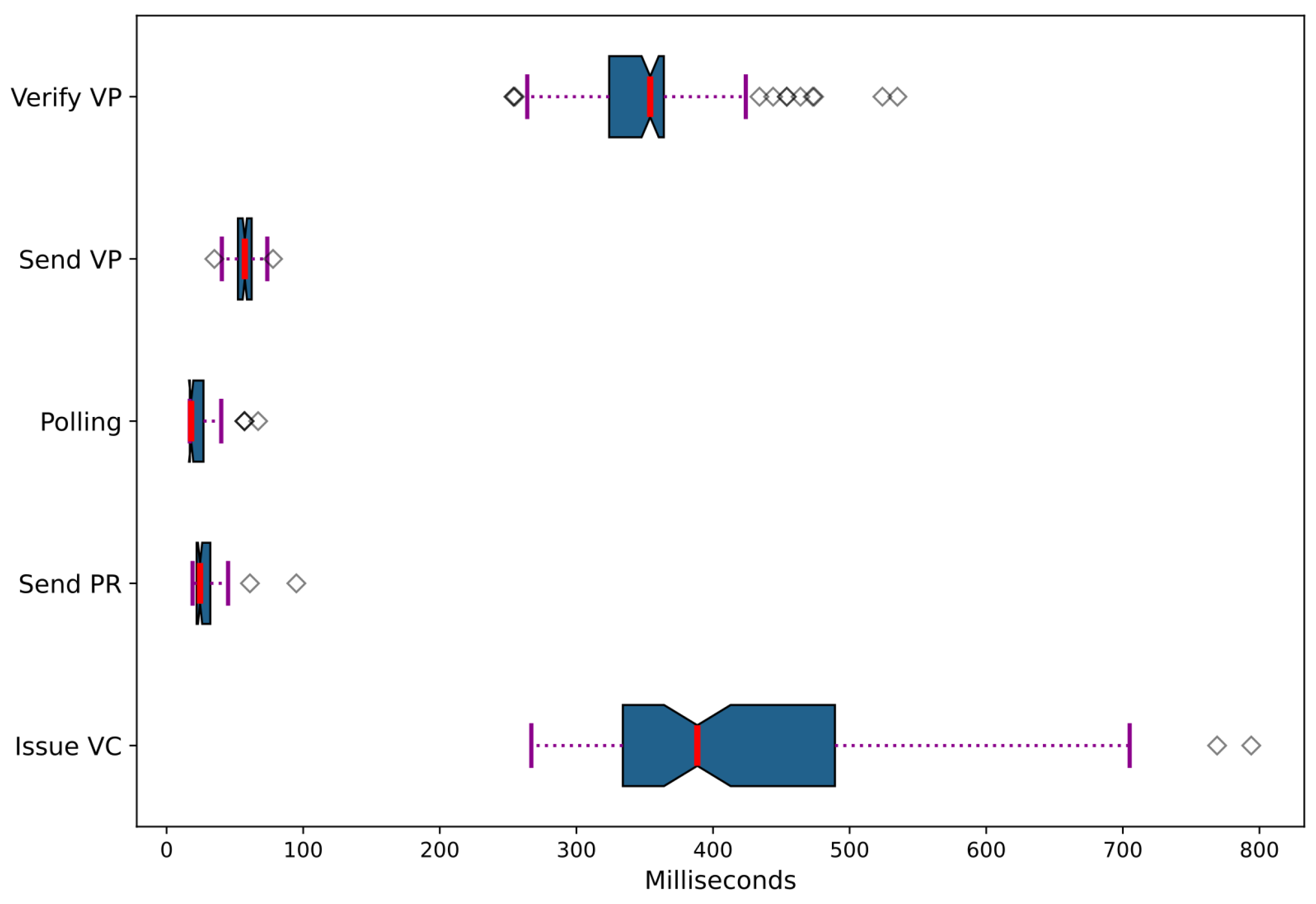
- Issue verifiable credential (Issue VC). The Arduino SSI controller invokes the ACA-Py issuer SSI agent (simulating the primary operator) to issue a credential to the holder SSI agent (simulating the UE).
- Send a proof request (Send PR). The Arduino SSI controller invokes the ACA-Py verifier SSI agent (simulating the secondary operator) to send a proof request to the holder SSI agent (simulating the UE), asking for the credential issued in the step 1.
- Polling. The Arduino SSI controller polls the ACA-Py holder agent (simulating the UE) for an incoming proof request. This polling activity is the same in other points of the SSI operation flow from Section 3.2.2.
- Send a verifiable proof response (Send VP). The Arduino SSI controller invokes the ACA-Py holder SSI agent (simulating the UE) to generate a proof response that match the received proof request from step 2 and sends it to the verifier SSI agent (simulating the secondary operator).
- Verify the verifiable proof response (Verify VP). Arduino invokes the ACA-Py verifier SSI agent (simulating the secondary operator) and verifies the received proof response from step 4.
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Suffredini, G. Smart Cities as Ecosystems-What Will Be the Impact of 5G? Master Thesis, University of Gothenburg, Gothenburg, Sweden, 2020. Available online: https://gupea.ub.gu.se/bitstream/handle/2077/65782/gupea_2077_65782_1.pdf?sequence=1&isAllowed=y (accessed on 20 January 2025).
- Majeed, A. Comparative studies of 3G, 4G & 5G mobile network & data offloading method a survey. Int. J. Res. Inf. Technol. 2015, 3, 421–427. Available online: https://www.researchgate.net/publication/277817220_Comparative_Studies_of_3G_4G_5G_Mobile_Network_Data_Offloading_Method_a_Survey (accessed on 1 April 2025).
- Salman, H.A.; Alsajri, A.; Kalakech, A.; Steiti, A. Difference Between 4G and 5G Networks. Babylon. J. Netw. 2023, 2023, 41–54. [Google Scholar] [CrossRef]
- Gohar, A.; Nencioni, G. The role of 5G technologies in a smart city: The case for intelligent transportation system. Sustainability 2021, 13, 5188. [Google Scholar] [CrossRef]
- Yang, C.; Liang, P.; Fu, L.; Cui, G.; Huang, F.; Teng, F.; Bangash, Y.A. Using 5G in smart cities: A systematic mapping study. Intell. Syst. Appl. 2022, 14, 200065. [Google Scholar] [CrossRef]
- Shehab, M.J.; Kassem, I.; Kutty, A.A.; Kucukvar, M.; Onat, N.; Khattab, T. 5G networks towards smart and sustainable cities: A review of recent developments, applications and future perspectives. IEEE Access 2021, 10, 2987–3006. [Google Scholar] [CrossRef]
- Chrysikos, T.; Gourna, S.; Skouroliakou, A. RF Coverage Design for the Implementation of a Broadband Monitoring Service in the Context of 5G-Enabled Smart Cities. Information 2023, 14, 156. [Google Scholar] [CrossRef]
- Sudhamani, C.; Roslee, M.; Tiang, J.J.; Rehman, A.U. A survey on 5G coverage improvement techniques: Issues and future challenges. Sensors 2023, 23, 2356. [Google Scholar] [CrossRef]
- Elgendi, I.; Munasinghe, K.S.; Jamalipour, A. Traffic offloading for 5G: L-LTE or Wi-Fi. In Proceedings of the 2017 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Atlanta, GA, USA, 1–4 May 2017; IEEE: New York, NY, USA, 2017; pp. 748–753. [Google Scholar]
- Damigos, G.; Lindgren, T.; Sandberg, S.; Nikolakopoulos, G. Performance of sensor data process offloading on 5g-enabled uavs. Sensors 2023, 23, 864. [Google Scholar] [CrossRef]
- Aujla, G.S.; Chaudhary, R.; Kumar, N.; Rodrigues, J.J.; Vinel, A. Data offloading in 5G-enabled software-defined vehicular networks: A Stackelberg-game-based approach. IEEE Commun. Mag. 2017, 55, 100–108. [Google Scholar] [CrossRef]
- Muhamad, W.N.W.; Aris, S.S.M.; Dimyati, K.; Javed, M.A.; Idris, A.; Ali, D.M.; Abdullah, E. Energy-efficient task offloading in fog computing for 5G cellular network. Eng. Sci. Technol. Int. J. 2024, 50, 101628. [Google Scholar] [CrossRef]
- Ebrahimi, A.; Afghah, F. Intelligent Task Offloading: Advanced MEC Task Offloading and Resource Management in 5G Networks. arXiv 2025, arXiv:2501.06242. [Google Scholar]
- Wang, F.; Diao, B.; Sun, T.; Xu, Y. Data security and privacy challenges of computing offloading in FINs. IEEE Netw. 2020, 34, 14–20. [Google Scholar] [CrossRef]
- Li, T.; He, X.; Jiang, S.; Liu, J. A survey of privacy-preserving offloading methods in mobile-edge computing. J. Netw. Comput. Appl. 2022, 203, 103395. [Google Scholar] [CrossRef]
- Xiao, J.; Xu, W.; Cai, Y. Task Offloading and Resource Allocation with Reliability Guarantee in 5G-WiFi Heterogeneous Networks. In Proceedings of the 2024 IEEE Wireless Communications and Networking Conference (WCNC), Dubai, United Arab Emirates, 21–24 April 2024; IEEE: New York, NY, USA, 2024; pp. 1–6. [Google Scholar]
- Bouras, C.; Kollia, A.; Papazois, A. SDN & NFV in 5G: Advancements and challenges. In Proceedings of the 2017 20th Conference on Innovations in Clouds, Internet and Networks (ICIN), Paris, France, 7–9 March 2017; IEEE: New York, NY, USA, 2017; pp. 107–111. [Google Scholar]
- Zhuang, W.; Ye, Q.; Lyu, F.; Cheng, N.; Ren, J. SDN/NFV-empowered future IoV with enhanced communication, computing, and caching. Proc. IEEE 2019, 108, 274–291. [Google Scholar] [CrossRef]
- Shilpa, V.; Ranjan, R. SDN Based Data Offloading and Load Balancing Techniques for Applications in 5G. Int. J. Recent Technol. Eng. (IJRTE) 2019, 8, 6353–6358. [Google Scholar]
- Zhou, H.; Wang, H.; Li, X.; Leung, V.C. A survey on mobile data offloading technologies. IEEE Access 2018, 6, 5101–5111. [Google Scholar] [CrossRef]
- Xu, D.; Li, Y.; Chen, X.; Li, J.; Hui, P.; Chen, S.; Crowcroft, J. A survey of opportunistic offloading. IEEE Commun. Surv. Tutor. 2018, 20, 2198–2236. [Google Scholar] [CrossRef]
- Elgendi, I.; Munasinghe, K.S.; Sharma, D.; Jamalipour, A. Traffic offloading techniques for 5G cellular: A three-tiered SDN architecture. Ann. Telecommun. 2016, 71, 583–593. [Google Scholar] [CrossRef]
- Liyanage, M.; Dananjaya, M.; Okwuibe, J.; Ylianttila, M. SDN based operator assisted offloading platform for multi-controller 5G networks. In Proceedings of the 2017 IEEE International Symposium on Local and Metropolitan Area Networks (LANMAN), Osaka, Japan, 12–14 June 2017; IEEE: New York, NY, USA, 2017; pp. 1–3. [Google Scholar]
- Paris, S.; Martisnon, F.; Filippini, I.; Chen, L.; Martignon, F. A bandwidth trading marketplace for mobile data offloading. In Proceedings of the 2013 Proceedings IEEE INFOCOM, Turin, Italy, 14–19 April 2013; IEEE: New York, NY, USA, 2013; pp. 430–434. [Google Scholar]
- Gao, L.; Iosifidis, G.; Huang, J.; Tassiulas, L. Economics of mobile data offloading. In Proceedings of the 2013 Proceedings IEEE INFOCOM, Turin, Italy, 14–19 April 2013; IEEE: New York, NY, USA, 2013; pp. 3303–3308. [Google Scholar]
- Ramachandran, G.S.; Radhakrishnan, R.; Krishnamachari, B. Towards a decentralized data marketplace for smart cities. In Proceedings of the 2018 IEEE International Smart Cities Conference (ISC2), Kansas City, MO, USA, 16–19 September 2018; IEEE: New York, NY, USA, 2018; pp. 1–8. [Google Scholar]
- Aljohani, M.; Mukkamala, R.; Olariu, S.; Kalari, S.; Sunkara, M. SmartReview: A Blockchain-based Transaction Review System for Decentralized Marketplaces. In Proceedings of the 2024 6th International Conference on Blockchain Computing and Applications (BCCA), Dubai, United Arab Emirates, 26–29 November 2024; IEEE: New York, NY, USA, 2024; pp. 108–115. [Google Scholar]
- Christidis, J.; Karkazis, P.A.; Papadopoulos, P.; Leligou, H.C. Decentralized blockchain-based iot data marketplaces. J. Sens. Actuator Netw. 2022, 11, 39. [Google Scholar] [CrossRef]
- Qureshi, M.B.; Qureshi, M.S.; Tahir, S.; Anwar, A.; Hussain, S.; Uddin, M.; Chen, C.L. Encryption techniques for smart systems data security offloaded to the cloud. Symmetry 2022, 14, 695. [Google Scholar] [CrossRef]
- Ji, X.; Huang, K.; Jin, L.; Tang, H.; Liu, C.; Zhong, Z.; You, W.; Xu, X.; Zhao, H.; Wu, J.; et al. Overview of 5G security technology. Sci. China Inf. Sci. 2018, 61, 081301. [Google Scholar] [CrossRef]
- Basin, D.; Dreier, J.; Hirschi, L.; Radomirovic, S.; Sasse, R.; Stettler, V. A formal analysis of 5G authentication. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018; pp. 1383–1396. [Google Scholar]
- Dwiputriane, D.B.; Heng, S.H. Authentication for 5G Mobile Wireless Networks. J. Eng. Technol. Appl. Phys. 2022, 4, 16–24. [Google Scholar] [CrossRef]
- DIF—Decentralized Identity Foundation. Principles and Characteristics of Self Sovereign Identity. Available online: https://decentralized-id.com/self-sovereign-identity/characteristics/ (accessed on 20 January 2025).
- Di Pierro, M. What is the blockchain? Comput. Sci. Eng. 2017, 19, 92–95. [Google Scholar] [CrossRef]
- Kodra, F.; Cangu, B. Blockchain Revolution in Accounting: Transparency, Efficiency, and Costs. IJAME 2025, 1. Available online: https://app.ijame.org/index.php/v1/article/view/5 (accessed on 1 April 2025).
- Mijwil, M.M.; Aljanabi, M.; Abotaleb, M.; Shukur, B.S.; Al Sailawi, A.S.A.; Bala, I.; Hiran, K.K.; Doshi, R.; Dhoska, K. Exploring the Impact of Blockchain Revolution on the Healthcare Ecosystem: A Critical Review. Mesopotamian J. Cybersecur. 2025, 5, 78–89. [Google Scholar] [CrossRef]
- Kadam, S.; Senta, R.; Sah, R.K.; Sawant, A.; Jain, S. Blockchain revolution: A new horizon for supply chain management in hotel industry. In Proceedings of the 2024 International Conference on Emerging Smart Computing and Informatics (ESCI), Pune, India, 5–7 March 2024; IEEE: New York, NY, USA, 2024; pp. 1–8. [Google Scholar]
- Maher, M.A.; Khan, I.A. From sharing to selling: Challenges and opportunities of establishing a digital health data marketplace using blockchain technologies. Blockchain Healthc. Today 2022, 5, 10-30953. [Google Scholar] [CrossRef]
- Sober, M.; Scaffino, G.; Schulte, S.; Kanhere, S.S. A blockchain-based IoT data marketplace. Clust. Comput. 2023, 26, 3523–3545. [Google Scholar] [CrossRef]
- Tan, Y. Implications of blockchain-powered marketplace of preowned virtual goods. Prod. Oper. Manag. 2024, 33, 1393–1409. [Google Scholar] [CrossRef]
- Taherdoost, H. Smart contracts in blockchain technology: A critical review. Information 2023, 14, 117. [Google Scholar] [CrossRef]
- Dolhopolov, A.; Castelltort, A.; Laurent, A. Exploring the benefits of blockchain-powered metadata catalogs in data mesh architecture. In Proceedings of the International Conference on Management of Digital, Heraklion, Greece, 5–7 May 2023; Springer Nature: Cham, Switzerland, 2023; pp. 32–40. [Google Scholar]
- Golightly, L.; Modesti, P.; Garcia, R.; Chang, V. Securing distributed systems: A survey on access control techniques for cloud, blockchain, IoT and SDN. Cyber Secur. Appl. 2023, 1, 100015. [Google Scholar] [CrossRef]
- Sarfaraz, A.; Chakrabortty, R.K.; Essam, D.L. A tree structure-based improved blockchain framework for a secure online bidding system. Comput. Secur. 2021, 102, 102147. [Google Scholar] [CrossRef]
- Yakubu, B.M.; Ahmad, M.M.; Sulaiman, A.B.; Kazaure, A.S.; Khan, M.I.; Javaid, N. Blockchain based smart marketplace for secure internet bandwidth trading. In Proceedings of the 2021 1st International Conference on Multidisciplinary Engineering and Applied Science (ICMEAS), Abuja, Nigeria, 15–16 July 2021; IEEE: New York, NY, USA, 2021; pp. 1–6. [Google Scholar]
- Al-Khatib, A.; Hadi, H.; Timinger, H.; Moessner, K. Blockchain-empowered resource trading for optimizing bandwidth reservation in vehicular networks. IEEE Access 2024, 12, 90084–90098. [Google Scholar] [CrossRef]
- Yousafzai, A.; Khan, L.U.; Majeed, U.; Hakeem, O.; Hong, C.S. FedMarket: A cryptocurrency driven marketplace for mobile federated learning services. IEEE Access 2022, 10, 87602–87616. [Google Scholar] [CrossRef]
- Tkachuk, R.V.; Ilie, D.; Tutschku, K.; Robert, R. A survey on blockchain-based telecommunication services marketplaces. IEEE Trans. Netw. Serv. Manag. 2021, 19, 228–255. [Google Scholar] [CrossRef]
- Fernando, P.; Gunawardhana, L.; Rajapakshe, W.; Dananjaya, M.; Gamage, T.; Liyanage, M. Blockchain-Based Wi-Fi Offloading Platform for 5G. In Proceedings of the 2020 IEEE International Conference on Communications Workshops (ICC Workshops), Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar]
- Mohan, C. State of public and private blockchains: Myths and reality. In Proceedings of the 2019 international Conference on Management of Data, Amsterdam, The Netherlands, 30 June–5 July 2019; pp. 404–411. [Google Scholar]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger fabric: A distributed operating system for permissioned blockchains. In Proceedings of the Thirteenth EuroSys Conference, Porto, Portugal, 23–26 April 2018; pp. 1–15. [Google Scholar]
- Mohanty, D. R3 Corda for Architects and Developers: With Case Studies in Finance, Insurance, Healthcare, Travel, Telecom, and Agriculture; Apress: New York, NY, USA, 2019. [Google Scholar]
- Melissari, F.; Papadakis, A.; Chatzitheodorou, D.; Tran, D.; Schouteten, J.; Athanasiou, G.; Zahariadis, T. Experiences using ethereum and quorum blockchain smart contracts in dairy production. J. Sens. Actuator Netw. 2024, 13, 6. [Google Scholar] [CrossRef]
- Capocasale, V.; Gotta, D.; Perboli, G. Comparative analysis of permissioned blockchain frameworks for industrial applications. Blockchain: Res. Appl. 2023, 4, 100113. [Google Scholar] [CrossRef]
- Abang, J.E.; Takruri, H.; Al-Zaidi, R.; Al-Khalidi, M. Latency performance modelling in hyperledger fabric blockchain: Challenges and directions with an IoT perspective. Internet Things 2024, 26, 101217. [Google Scholar] [CrossRef]
- Li, D.; Wong, W.E.; Guo, J. A survey on blockchain for enterprise using hyperledger fabric and composer. In Proceedings of the 2019 6th International Conference on Dependable Systems and Their Applications (DSA), Harbin, China, 3–6 January 2020; IEEE: New York, NY, USA, 2020; pp. 71–80. [Google Scholar]
- Vera-Rivera, A.; Hossain, E. Decentralizing Trust: Consortium Blockchains and Hyperledger Fabric Explained. arXiv 2025, arXiv:2502.06540. [Google Scholar]
- Ahmad, I.; Shahabuddin, S.; Kumar, T.; Okwuibe, J.; Gurtov, A.; Ylianttila, M. Security for 5G and beyond. IEEE Commun. Surv. Tutor. 2019, 21, 3682–3722. [Google Scholar] [CrossRef]
- Schneider, P.; Horn, G. Towards 5G security. In Proceedings of the 2015 IEEE Trustcom/BigDataSE/ISPA, Helsinki, Finland, 20–22 August 2015; IEEE: New York, NY, USA, 2015; Volume 1, pp. 1165–1170. [Google Scholar]
- Javed, M.A.; khan Niazi, S. 5G security artifacts (DoS/DDoS and authentication). In Proceedings of the 2019 International Conference on Communication Technologies (ComTech), Rawalpindi, Pakistan, 20–21 March 2019; IEEE: New York, NY, USA, 2019; pp. 127–133. [Google Scholar]
- 3Gpp. Technical Specification Group Services and System Aspects, Release 15. 2018. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3144 (accessed on 1 April 2025).
- You, I.; Kim, G.; Shin, S.; Kwon, H.; Kim, J.; Baek, J. 5G-AKA-FS: A 5G Authentication and Key Agreement Protocol for Forward Secrecy. Sensors 2024, 24, 159. [Google Scholar] [CrossRef]
- Gupta, S.; Parne, B.L.; Chaudhari, N.S. Security vulnerabilities in handover authentication mechanism of 5G network. In Proceedings of the 2018 First International Conference on Secure Cyber Computing and Communication (ICSCCC), Jalandhar, India, 15–17 December 2018; IEEE: New York, NY, USA, 2018. [Google Scholar]
- Ko, Y.; Pawana, I.W.A.J.; You, I. Formal Security Reassessment of the 5G-AKA-FS Protocol: Methodological Corrections and Augmented Verification Techniques. Sensors 2024, 24, 7979. [Google Scholar] [CrossRef] [PubMed]
- Xiao, Y.; Wu, Y. 5g-ipaka: An improved primary authentication and key agreement protocol for 5g networks. Information 2022, 13, 125. [Google Scholar] [CrossRef]
- Køien, G.M. The SUCI-AKA Authentication Protocol for 5G Systems. In Norsk IKT-Konferanse for Forskning og Utdanning; NIKT: Notodden, Norway, 2020; Available online: https://www.ntnu.no/ojs/index.php/nikt/article/view/5550/5022 (accessed on 1 April 2025).
- Yadav, A.K.; Misra, M.; Pandey, P.K.; Ranaweera, P.; Liyanage, M.; Kumar, N. A Secure Authentication Protocol for IoT-WLAN Using EAP Framework. IEEE Trans. Dependable Secur. Comput. 2024, 22, 49–65. [Google Scholar] [CrossRef]
- Dawar, A.D.A. Enhancing Wireless Security and Privacy: A 2-Way Identity Authentication Method for 5G Networks. Int. J. Math. Stat. Comput. Sci. 2024, 2, 183–198. [Google Scholar] [CrossRef]
- Fang, H.; Wang, X.; Tomasin, S. Machine learning for intelligent authentication in 5G and beyond wireless networks. IEEE Wirel. Commun. 2019, 26, 55–61. [Google Scholar] [CrossRef]
- Li, X.; Wang, C.; Zou, X.; Wang, S. A Secure and Effective Authentication Method in 5G. In Proceedings of the 2023 4th International Seminar on Artificial Intelligence, Networking and Information Technology (AINIT), Nanjing, China, 16–18 June 2023; IEEE: New York, NY, USA, 2023; pp. 243–246. [Google Scholar]
- Khan, N.A. PKI-Based security enhancement for IoT in 5G networks. In Proceedings of the Inventive Computation and Information Technologies: Proceedings of ICICIT 2021, Coimbatore, India, 12–13 August 2022; Springer Nature: Singapore, 2022; pp. 217–225. [Google Scholar]
- Boubakri, W.; Abdallah, W.; Boudriga, N. Access control in 5G communication networks using simple PKI certificates. In Proceedings of the 2017 13th International Wireless Communications and Mobile Computing Conference (IWCMC), Valencia, Spain, 26–30 June 2017; IEEE: New York, NY, USA, 2017; pp. 2092–2097. [Google Scholar]
- Bala, R.; Manoharan, R. Secure and effective authentication for 5G networks (SEA-5G) using blockchain. J. Ambient. Intell. Humaniz. Comput. 2025, 16, 51–66. [Google Scholar] [CrossRef]
- Weingaertner, T.; Camenzind, O. Identity of things: Applying concepts from self sovereign identity to IoT devices. J. Br. Blockchain Assoc. 2021, 4, 1–7. [Google Scholar] [CrossRef]
- De Diego, S.; Regueiro, C.; Maciá-Fernández, G. Enabling identity for the IoT-as-a-service business model. IEEE Access 2021, 9, 159965–159975. [Google Scholar] [CrossRef]
- Salleras, X.; Daza, V. SANS: Self-Sovereign Authentication for Network Slices. Secur. Commun. Netw. 2020, 2020, 8823573. [Google Scholar] [CrossRef]
- Fiege, U.; Fiat, A.; Shamir, A. Zero knowledge proofs of identity. In Proceedings of the Nineteenth Annual ACM Symposium on Theory of Computing, New York, NY, USA, 25–27 May 1987; pp. 210–217. [Google Scholar]
- Song, W.; Nokhbeh Zaeem, R.; Liau, D.; Chang, K.C.; Lamison, M.R.; Khalil, M.M.; Barber, K.S. Self-sovereign identity and user control for privacy-preserving contact tracing. In Proceedings of the IEEE/WIC/ACM International Conference on Web Intelligence and Intelligent Agent Technology, Melbourne, Australia, 14–17 December 2021; pp. 438–445. [Google Scholar]
- Foytik, P.; Bouk, S.H.; Anderson, G.; Shetty, S. Self-Sovereign Identity Management in Ship-Based 5G-Devices Use Case. In Proceedings of the 2024 IEEE 21st Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 6–9 January 2024; IEEE: New York, NY, USA, 2024; pp. 650–651. [Google Scholar]
- Aruna, M.G.; Hasan, M.K.; Islam, S.; Mohan, K.G.; Sharan, P.; Hassan, R. Cloud to cloud data migration using self sovereign identity for 5G and beyond. Clust. Comput. 2022, 25, 2317–2331. [Google Scholar] [CrossRef]
- Küpper, A. Decentralized identifiers and self-sovereign identity-a new identity management for 6G integration?: Mobilecloud 2021 invited talk. In Proceedings of the 2021 IEEE International Conference on Joint Cloud Computing (JCC), Oxford, UK, 23–26 August 2021; IEEE: New York, NY, USA, 2021; p. 71. [Google Scholar]
- Reed, D.; Sporny, M.; Longley, D.; Allen, C.; Grant, R.; Sabadello, M.; Holt, J. Decentralized Identifiers (dids) v1.0. Draft Community Group Report. 2020. Available online: https://www.w3.org/TR/2020/WD-did-core-20201108/ (accessed on 1 April 2025).
- Lage, O.; de Diego, S.; Urkizu, B.; Gómez, E.; Gutiérrez, I. Blockchain applications in cybersecurity. In Computer Security Threats; IntechOpen: London, UK, 2019; pp. 76–86. [Google Scholar]
- World Wide Web Consortium. Verifiable Credentials Data Model 2.0. 2024. Available online: https://www.w3.org/TR/vc-data-model-2.0/ (accessed on 20 January 2025).
- Gebresilassie, S.K.; Rafferty, J.; Morrow, P.; Chen, L.L.; Abu-Tair, M.; Cui, Z. Distributed, Secure, Self-Sovereign Identity for IoT Devices. In Proceedings of the 2020 IEEE 6th World Forum on Internet of Things (WF-IoT), New Orleans, LA, USA, 2–16 June 2020; IEEE: New York, NY, USA, 2020; pp. 1–6. [Google Scholar]
- Mahalle, P.N.; Shinde, G.; Shafi, P.M. Rethinking decentralised identifiers and verifiable credentials for the Internet of Things. In Internet of Things, Smart Computing and Technology: A Roadmap Ahead; Springer: Cham, Switzerland, 2020; pp. 361–374. [Google Scholar]
- Hyperledger Aries. Available online: https://github.com/hyperledger/aries (accessed on 20 January 2025).
- Veramo—Performant and Modular APIs for Verifiable Data and SSI. Available online: https://veramo.io/ (accessed on 22 April 2025).
- Ali, M.; Shea, R.; Nelson, J.; Freedman, M.J. Blockstack Technical Whitepaper; Blockstack PBC: New York, NY, USA, 2017. [Google Scholar]
- Veres One—A Globally Interoperable Blockchain for Identity. Available online: https://veres.one/ (accessed on 22 April 2025).
- Jolocom—A Decentralized, Open Source Solution for Digital Identity and Access Management. Available online: https://www.alchemy.com/dapps/jolocom (accessed on 22 April 2025).
- Hyperledger Indy. Available online: https://github.com/hyperledger/indy-sdk (accessed on 20 January 2025).
- Hyperledger Aries Cloud Agent. Available online: https://github.com/hyperledger/aries-cloudagent-python (accessed on 20 January 2025).
- Davie, M.; Gisolfi, D.; Hardman, D.; Jordan, J.; O’Donnell, D.; Reed, D. The trust over ip stack. IEEE Commun. Stand. Mag. 2019, 3, 46–51. [Google Scholar] [CrossRef]
- Curren, S.; Looker, T.; Terbu, O. DIDComm Messaging v2.x Editor’s Draft. 2022. Available online: https://identity.foundation/didcomm-messaging/spec/ (accessed on 20 January 2025).
- Jamil, F.; Cheikhrouhou, O.; Jamil, H.; Koubaa, A.; Derhab, A.; Ferrag, M.A. PetroBlock: A blockchain-based payment mechanism for fueling smart vehicles. Appl. Sci. 2021, 11, 3055. [Google Scholar] [CrossRef]
- Saputhanthri, A.; De Alwis, C.; Liyanage, M. Survey on blockchain-based IoT payment and marketplaces. IEEE Access 2022, 10, 103411–103437. [Google Scholar] [CrossRef]
- Alotaibi, F.; Hosny, S.; Tadrous, J.; Gamal, H.E.; Eryilmaz, A. Towards a marketplace for mobile content: Dynamic pricing and proactive caching. arXiv 2015, arXiv:arXiv:1511.07573. [Google Scholar]
- Sund, T.; Lööf, C.; Nadjm-Tehrani, S.; Asplund, M. Blockchain-based event processing in supply chains—A case study at IKEA. Robot. -Comput.-Integr. Manuf. 2020, 65, 101971. [Google Scholar] [CrossRef]
- Saharan, S.; Bawa, S.; Kumar, N. Dynamic pricing techniques for Intelligent Transportation System in smart cities: A systematic review. Comput. Commun. 2020, 150, 603–625. [Google Scholar] [CrossRef]
- Pasdar, A.; Lee, Y.C.; Dong, Z. Connect API with blockchain: A survey on blockchain oracle implementation. ACM Comput. Surv. 2023, 55, 1–39. [Google Scholar] [CrossRef]
- Boi, B.; De Santis, M.; Esposito, C. Self-Sovereign Identity (SSI) Attribute-Based Web Authentication. In Proceedings of the SECRYPT, Rome, Italy, 10–12 July 2023; pp. 758–763. [Google Scholar]
- Montero, F.; Ramón, H.D.; Pousa, A. Self-sovereign Identity Model in a Higher Education Institution. In Proceedings of the XII Jornadas de Cloud Computing, Big Data & Emerging Topics, La Plata, Argentina, 25–27 June 2024. [Google Scholar]
- Zhou, W.; Jia, Y.; Peng, A.; Zhang, Y.; Liu, P. The effect of IoT new features on security and privacy: New threats, existing solutions, and challenges yet to be solved. IEEE Internet Things J. 2018, 6, 1606–1616. [Google Scholar] [CrossRef]
- Kortesniemi, Y.; Lagutin, D.; Elo, T.; Fotiou, N. Improving the privacy of IoT with decentralised identifiers (DIDs). J. Comput. Netw. Commun. 2019, 2019, 8706760. [Google Scholar] [CrossRef]
- Berzin, O.; Ansay, R.; Kempf, J.; Sheikh, I.; Hendel, D. The IoT Exchange. 2021. Available online: https://arxiv.org/abs/2103.12131 (accessed on 24 March 2024).
- Stokkink, Q.; Pouwelse, J. Deployment of a blockchain-based self-sovereign identity. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; IEEE: New York, NY, USA, 2018; pp. 1336–1342. [Google Scholar]
- Siqueira, A.; Da Conceição, A.F.; Rocha, V. Performance Evaluation of Self-Sovereign Identity Use Cases. In Proceedings of the 2023 IEEE International Conference on Decentralized Applications and Infrastructures (DAPPS), Athens, Greece, 17–20 July 2023; IEEE: New York, NY, USA, 2023; pp. 135–144. [Google Scholar]
- Yusop, N.; Moketar, N.A.; Sadikan, S.F.N. Development of Arduino applications for IoT applications in software engineering education: A systematic literature review. Bull. Electr. Eng. Inform. 2024, 13, 1824–1831. [Google Scholar] [CrossRef]
- Hyperledger Fabric v2.4.8 Release Notes. 2023. Available online: https://github.com/hyperledger/fabric/releases/tag/v2.4.8 (accessed on 1 April 2025).
- Wang, X.; Zhao, H.; Zhu, J. GRPC: A communication cooperation mechanism in distributed systems. ACM SIGOPS Oper. Syst. Rev. 1993, 27, 75–86. [Google Scholar] [CrossRef]
- Patnaik Patnaikuni, D.R. A Comparative Study of Arduino, Raspberry Pi and ESP8266 as IoT Development Board. Int. J. Adv. Res. Comput. Sci. 2017, 8, 2350. [Google Scholar]
- Kumar, N.S.; Vuayalakshmi, B.; Prarthana, R.J.; Shankar, A. IOT based smart garbage alert system using Arduino UNO. In Proceedings of the 2016 IEEE region 10 conference (TENCON), Singapore, 22–25 November 2016; IEEE: New York, NY, USA, 2016; pp. 1028–1034. [Google Scholar]
- Wadhwani, S.; Singh, U.; Singh, P.; Dwivedi, S. Smart home automation and security system using Arduino and IOT. Int. Res. J. Eng. Technol. (IRJET) 2018, 5, 1357–1359. [Google Scholar]
- de Diego, S.; Regueiro, C.; Maciá-Fernández, G. An Authentication System Based on Self-sovereign Identity for Vehicle-to-Vehicle (V2V) Communications. In Proceedings of the International Congress on Blockchain and Applications, Salamanca, Spain, 26–28 June 2024; Springer Nature: Cham, Switzerland, 2024; pp. 13–22. [Google Scholar]




| Issues from [23,49] | Proposed Solutions |
|---|---|
| It does not really deep into the technical details of using Blockchain for offloading processes. | This paper includes deep technical details about Blockchain and SSI techniques considered for enhanced security of the offloading process. |
| It considers an InterPlanetary File System (IPFS) decentralized storage where private information is stored without guaranteeing its privacy. | The information required for the offloading process is stored in a permissioned Blockchain, taking advantage of its inherent security features. |
| Lateral communications among different operators are required, meaning that a prior mutual relationship is needed. | Prior communication among operators is not needed as it is orchestrated through Blockchain transactions and events. |
| The validation is done in an Ethereum public network, where throughput, latency, scalability, and privacy are not optimized. | Hyperledger permissioned network is considered for enhanced throughput, latency, and scalability. |
| User authentication credentials need to be shared among operators, which increases the likelihood of interception and thus problems of unauthorized access or exposure of private information. | SSI-based authentication will be considered avoiding authentication credentials sharing and letting the user to totally control and manage its identity. |
| Simultaneous Requests | Requirements | Registered Services | Search Time (s) |
|---|---|---|---|
| 1 | 2 | 10 | 2.18 |
| 50 | 2.25 | ||
| 100 | 2.21 | ||
| 1000 | 2.30 | ||
| 4 | 10 | 2.17 | |
| 50 | 2.21 | ||
| 100 | 2.22 | ||
| 1000 | 2.43 | ||
| 7 | 10 | 2.17 | |
| 50 | 2.21 | ||
| 100 | 2.22 | ||
| 1000 | 2.57 | ||
| 10 | 2 | 10 | 0.44 |
| 50 | 0.49 | ||
| 100 | 0.45 | ||
| 1000 | 0.41 | ||
| 4 | 10 | 0.44 | |
| 50 | 0.47 | ||
| 100 | 0.48 | ||
| 1000 | 0.47 | ||
| 7 | 10 | 0.44 | |
| 50 | 0.48 | ||
| 100 | 0.49 | ||
| 1000 | 0.46 | ||
| 100 | 2 | 10 | 0.29 |
| 50 | 0.18 | ||
| 100 | 0.15 | ||
| 1000 | 0.47 | ||
| 4 | 10 | 0.30 | |
| 50 | 0.18 | ||
| 100 | 0.15 | ||
| 1000 | 0.41 | ||
| 7 | 10 | 0.31 | |
| 50 | 0.19 | ||
| 100 | 0.15 | ||
| 1000 | 0.44 | ||
| 1000 | 2 | 10 | 0.35 |
| 50 | 0.26 | ||
| 100 | 0.28 | ||
| 1000 | 0.89 | ||
| 4 | 10 | 0.41 | |
| 50 | 0.39 | ||
| 100 | 0.46 | ||
| 1000 | 0.90 | ||
| 7 | 10 | 0.49 | |
| 50 | 0.53 | ||
| 100 | 0.51 | ||
| 1000 | 1.00 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Regueiro, C.; de Diego, S.; Urkizu, B. Leveraging Blockchain Technology for Secure 5G Offloading Processes. Future Internet 2025, 17, 197. https://doi.org/10.3390/fi17050197
Regueiro C, de Diego S, Urkizu B. Leveraging Blockchain Technology for Secure 5G Offloading Processes. Future Internet. 2025; 17(5):197. https://doi.org/10.3390/fi17050197
Chicago/Turabian StyleRegueiro, Cristina, Santiago de Diego, and Borja Urkizu. 2025. "Leveraging Blockchain Technology for Secure 5G Offloading Processes" Future Internet 17, no. 5: 197. https://doi.org/10.3390/fi17050197
APA StyleRegueiro, C., de Diego, S., & Urkizu, B. (2025). Leveraging Blockchain Technology for Secure 5G Offloading Processes. Future Internet, 17(5), 197. https://doi.org/10.3390/fi17050197







