Securing the SDN Data Plane in Emerging Technology Domains: A Review
Abstract
1. Introduction
2. Motivation and Contributions
- We provide the first in-depth review of existing literature in SDN data plane security, encompassing over 300 relevant and high-quality sources.
- We provide a detailed review of existing reviews, surveys, and equivalents into SDN security, classifying them based on the depth of their examination of SDN data plane security.
- We provide a classification of existing SDN data plane security research into three (3) primary research domains and eleven (11) sub-domains.
- For each domain and sub-domain, we identify research strengths and weaknesses, including gaps.
- We provide a holistic analysis of the body of research to identify promising future directions for research.
- Lastly, we identify and discuss the role of SDN in managing and securing the data planes of emerging technologies.
3. The Software-Defined Networking Data Plane
3.1. Software-Defined Networking
3.2. Data Plane Threats
4. Methodology
4.1. Research Questions
- RQ1. How may existing research into the security of SDN data planes be classified?
- RQ2. Based on this classification, what are the strengths of this research?
- RQ3. Based on this classification, what are the weaknesses of this research?
- RQ4. Based on the identified strengths and weaknesses, what are promising future directions for research?
4.2. Paper Selection
5. Previous Reviews
5.1. Overview
5.2. Data Plane Security
5.3. Stateful Data Plane
5.4. SDN Security
5.5. SDN
5.6. Summary
6. Security Capabilities Within the Data Plane
6.1. Overview
6.2. Programmable Data Plane
6.3. Network Function Virtualization
6.4. Post-Quantum Security
6.5. Traditional Security Capabilities
6.6. Summary
7. Security of the Data Plane Infrastructure
7.1. Overview
7.2. Device Compromise
7.3. Forwarding Anomaly Detection
7.4. Heterogeneous SDN
7.5. Secure Southbound Communication
7.6. Summary
8. Dynamic Routing Within the Data Plane
8.1. Overview
8.2. Multi-Path Routing
8.3. Trust-Based Routing
8.4. Resilient Routing
8.5. Summary
9. Discussion
9.1. Overview
9.2. Hybrid SDN Security and Management
9.3. Heterogeneous SDN Security
9.4. Trust-Based Methods
9.5. Other Issues
10. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| AI | Artificial Intelligence |
| API | Application Programming Interface |
| CNN | Convolutional Neural Network |
| DL | Deep Learning |
| DNN | Deep Neural Network |
| DoS | Denial-of-Service (Attack) |
| DDoS | Distributed-Denial-of-Service (Attack) |
| IoT | Internet of Things |
| MITM | Man-in-the-Middle (Attack) |
| ML | Machine Learning |
| MTD | Moving Target Defense |
| NBI | Northbound Interface |
| NF | Network Function |
| NFV | Network Function Virtualization |
| P4 | Programming Protocol-independent Packet Processors |
| PDP | Programmable Data Plane |
| RL | Reinforcement Learning |
| SBI | Southbound Interface |
| SDN | Software-Defined Networking |
| SDP | Stateful Data Plane |
| SDWN | Software-Defined Wireless Network |
| SIoT | Social Internet of Things |
| VANET | Vehicular Ad Hoc Network |
| VNF | Virtual(-ized) Network Function |
| WSN | Wireless Sensor Network |
References
- Casado, M.; Freedman, M.J.; Pettit, J.; Luo, J.; McKeown, N.; Shenker, S. Ethane: Taking control of the enterprise. In Proceedings of the SIGCOMM ’07: Proceedings of the 2007 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications, Kyoto, Japan, 27–31 August 2007. [Google Scholar]
- McKeown, N.; Anderson, T.; Balakrishnan, H.; Parulkar, G.; Peterson, L.; Rexford, J.; Shenker, S.; Turner, J. OpenFlow: Enabling innovation in campus networks. ACM SIGCOMM Comput. Commun. Rev. 2008, 38, 69–74. [Google Scholar] [CrossRef]
- Open Networking Group. OpenFlow Switch Specification (v 1.5.1). Available online: https://opennetworking.org/wp-content/uploads/2014/10/openflow-switch-v1.5.1.pdf (accessed on 5 April 2025).
- Bosshart, P.; Daly, D.; Gibb, G.; Izzard, M.; McKeown, N.; Rexford, J.; Schlesinger, C.; Talayco, D.; Vahdat, A.; Varghese, G.; et al. P4: Programming protocol-independent packet processors. ACM SIGCOMM Comput. Commun. Rev. 2014, 44, 87–95. [Google Scholar] [CrossRef]
- P4 Language Consortium. P4 Open Source Programming Language. Available online: https://p4.org/ (accessed on 5 April 2025).
- Rahouti, M.; Xiong, K.; Xin, Y.; Jagatheesaperumal, S.; Ayyash, M.; Shaheed, M. SDN security review: Threat taxonomy, implications and open challenges. IEEE Access 2022, 10, 45820–45854. [Google Scholar] [CrossRef]
- Gao, S.; Li, Z.; Xiao, B.; Wei, G. Security threats in the data plane of software-defined networks. IEEE Netw. 2018, 32, 108–113. [Google Scholar] [CrossRef]
- Tankovic, A.; Dervisevic, E.; Mehic, M.; Kaljic, E. A survey on data plane security in software-defined networks: Twoard adaptive security of data planes. IEEE Access 2025, 13, 97058–97093. [Google Scholar] [CrossRef]
- Dargahi, T.; Caponi, A.; Ambrosin, M.; Bianchi, G.; Conti, M. A survey on the security of stateful SDN data planes. IEEE Commun. Surv. Tutor. 2017, 19, 1701–1725. [Google Scholar] [CrossRef]
- Shaghaghi, A.; Kaafar, M.; Buyya, R.; Jha, S. Software-defined network (SDN) data plane security: Issues, solutions and future directions. In Handbook of Computer Networks and Cyber Security; Gupta, B., Perez, G., Agrawal, D., Gupta, D., Eds.; Springer: Cham, Switzerland, 2020. [Google Scholar]
- Zhang, X.; Cui, L.; Wei, K.; Fung Po, T.; Ji, Y.; Jia, W. A survey on stateful data plane in software defined networks. Comput. Netw. 2021, 184, 107597. [Google Scholar] [CrossRef]
- Gao, Y.; Wang, Z. A review of P4 programmable data planes for network security. Mob. Inf. Syst. 2021, 2021, 1257046. [Google Scholar] [CrossRef]
- AlSabeh, A.; Khoury, J.; Kfoury, E.; Crichigno, J.; Bou-Harb, E. A survey on security applications of P4 programmable switches and a STRIDE-based vulnerability assessment. Comput. Netw. 2022, 207, 108800. [Google Scholar] [CrossRef]
- Goswami, B.; Kulkarni, M.; Paulose, J. A survey on P4 challenges in software defined networks: P4 programming. IEEE Access 2023, 11, 54373–54387. [Google Scholar] [CrossRef]
- Kaljic, E.; Maric, A.; Njemcevic, P.; Hadzialic, M. A survey on data plane flexibility and programmability in software-defined networking. IEEE Access 2019, 7, 47804–47840. [Google Scholar] [CrossRef]
- Michel, O.; Bifulco, R.; Rétvári, G.; Schmid, S. The programmable data plane: Abstractions, architectures, algorithms, and applications. ACM Comput. Surv. 2021, 54, 82. [Google Scholar] [CrossRef]
- Kfoury, E.F.; Crichigno, J.; Bou-Harb, E. An exhaustive survey on P4 programmable data plane switches: Taxonomy, applications, challenges, and future trends. IEEE Access 2021, 9, 87094–87155. [Google Scholar] [CrossRef]
- Hauser, F.; Häberle, M.; Merling, D.; Lindner, S.; Gurevich, V.; Zeiger, F.; Frank, R.; Menth, M. A survey on data plane programming with P4: Fundamentals, advances, and applied research. J. Netw. Comput. Appl. 2023, 212, 103561. [Google Scholar] [CrossRef]
- Ahmad, I.; Namal, S.; Ylianttila, M.; Gurtov, A. Security in software defined networks: A survey. IEEE Commun. Surv. Tutor. 2015, 17, 2317–2346. [Google Scholar] [CrossRef]
- Dabbagh, M.; Hamdaoui, B.; Guizani, M.; Rayes, A. Software-defined networking security: Pros and cons. IEEE Commun. Mag. 2015, 53, 73–79. [Google Scholar] [CrossRef]
- Alsmadi, I.; Xu, D. Security of software defined networks: A survey. Comput. Secur. 2015, 53, 79–108. [Google Scholar] [CrossRef]
- Scott-Hayward, S.; Natarajan, S.; Sezer, S. A survey of security in software defined networks. IEEE Commun. Surv. Tutor. 2016, 18, 623–654. [Google Scholar] [CrossRef]
- Dayal, N.; Maity, P.; Srivastava, S.; Khondoker, R. Research trends in security and DDoS in SDN. Secur. Commun. Netw. 2016, 9, 6386–6411. [Google Scholar] [CrossRef]
- Krishnan, P.; Najeem, J.S. A review of security, threats and mitigation approaches for SDN. Int. J. Innov. Technol. Explor. Eng. 2019, 8, 389–393. [Google Scholar]
- Iqbal, M.; Iqbal, F.; Mohsin, F.; Rizwan, M.; Ahmad, F. Security issues in software defined networking (SDN): Risks, challenges and potential solutions. Int. J. Adv. Comput. Sci. Appl. 2019, 10, 298–303. [Google Scholar] [CrossRef]
- Isyaku, B.; Zahid, M.S.M.; Kamat, M.B.; Abu Bakar, K.; Ghaleb, F.A. Software defined networking flow table management of OpenFlow switches performance and security challenges: A survey. Futur. Internet 2020, 12, 147. [Google Scholar] [CrossRef]
- Chica, J.C.C.; Imbachi, J.C.; Vega, J.F.B. Security in SDN: A comprehensive survey. J. Netw. Comput. Appl. 2020, 159, 102595. [Google Scholar] [CrossRef]
- Alhaj, A.N.; Dutta, N. Analysis of security attacks in SDN network: A comprehensive survey. In Contemporary Issues in Communication, Cloud and Big Data Analytics; Springer: Berlin/Heidelberg, Germany, 2021. [Google Scholar]
- Jimenez, M.B.; Fernandez, D.; Rivadeneira, J.E.; Bellido, L.; Cardenas, A. A survey of the main security issues and solutions for the SDN architecture. IEEE Access 2021, 9, 122016–122038. [Google Scholar] [CrossRef]
- Deb, R.; Roy, S. A comprehensive survey of vulnerability and information security in SDN. Comput. Netw. 2022, 206, 108802. [Google Scholar] [CrossRef]
- Hirsi Abdi, A.; Audah, L.; Salh, A.; Alhartomi, M.A.; Rasheed, H.; Ahmed, S.; Tahir, A. Security control and data planes of SDN: A comprehensive review of traditional, AI, and MTD approaches to security solutions. IEEE Access 2024, 12, 69941–69980, Erratum in IEEE Access 2024, 12, 162107–162108. [Google Scholar] [CrossRef]
- Bhuiyan, Z.A.; Islam, S.; Islam, M.; Ullah, A.B.M.A.; Naz, F.; Rahman, M.S. On the (in)security of the control plane of SDN architecture: A survey. IEEE Access 2023, 11, 91550–91582. [Google Scholar] [CrossRef]
- Mahar, I.A.; Libing, W.; Maher, Z.A.; Rahu, G.A. A comprehensive survey of software defined networking and its security threats. In Proceedings of the IEEE 1st Karachi Section Humanitarian Technology Conference (Khi-HTC), Tandojam, Pakistan, 8–9 January 2024. [Google Scholar]
- Farooq, M.S.; Riaz, S.; Alvi, A. Security and privacy issues in software-defined networking (SDN): A systematic literature review. Electronics 2023, 12, 3077. [Google Scholar] [CrossRef]
- Yoon, C.; Lee, S.; Kang, H.; Par, T.; Shin, S.; Yegneswaran, V.; Porras, P.; Gu, G. Flow wars: Systemizing the attack surface and defenses in software-defined networks. IEEE Trans. Netw. 2017, 25, 3514–3530. [Google Scholar] [CrossRef]
- Raghunath, K.; Krishnan, P. Towards a secure SDN architecture. In Proceedings of the 9th International Conference on Computing and Networking Technology (ICCNT), Amsterdam, The Netherlands, 10–12 July 2018. [Google Scholar]
- Nisar, K.; Jimson, E.R.; Hijazi, M.H.A.; Welch, I.; Hassan, R.; Aman, A.H.M.; Sodhro, A.H.; Pirbhulal, S.; Khan, S. A survey on the architecture, application, and security of software defined networking: Challenges and open issues. Internet Things 2020, 12, 100289. [Google Scholar] [CrossRef]
- Gaur, K.; Choudhary, P.; Yadav, P.; Jain, A.; Kumar, P. Software defined networking: A review on architecture, security and applications. In Proceedings of the International Conference on Applied Scientific Computational Intelligence Using Data Science (ASCI 2020), Jaipur, India, 22–23 December 2020. [Google Scholar]
- Sezer, S.; Scott-Hayward, S.; Chouhan, P.K.; Fraser, B.; Lake, D.; Finnegan, J.; Viljoen, N.; Miller, M.; Rao, N. Are we ready for SDN? Implementation challenges for software-defined networks. IEEE Commun. Mag. 2013, 51, 36–43. [Google Scholar] [CrossRef]
- Feamster, N.; Rexford, J.; Zegura, E. The road to SDN: An intellectual history of programmable networks. ACM SIGCOMM Comput. Commun. Rev. 2014, 44, 100289. [Google Scholar] [CrossRef]
- Braun, W.; Menth, M. Software-defined networking using OpenFlow: Protocols, applications and architectural design choices. Futur. Internet 2014, 6, 302–336. [Google Scholar] [CrossRef]
- Xia, W.; Wen, Y.; Foh, C.H.; Niyato, D.; Xie, H. A survey on software-defined networking. IEEE Commun. Surv. Tutor. 2015, 17, 27–51. [Google Scholar] [CrossRef]
- Kreutz, D.; Ramos, F.M.V.; Veríssimo, P.E.; Rothenberg, C.E.; Azodolmolky, S.; Uhlig, S. Software-defined networking: A comprehensive survey. Proc. IEEE 2015, 103, 14–76. [Google Scholar] [CrossRef]
- Benzekki, K.; El Fergougui, A.; Elalaoui, A.E. Software-defined networking (SDN): A survey. Secur. Commun. Netw. 2016, 9, 5803–5833. [Google Scholar] [CrossRef]
- Ali, J.; Lee, G.-M.; Roh, B.-H.; Ryu, D.K.; Park, G. Software-defined networking approaches for link failure recovery: A survey. Sustainability 2020, 12, 4255. [Google Scholar] [CrossRef]
- Isyaku, B.; Bin Abu Bakar, K.; Ghaleb, F.A.; Al-Nahari, A. Dynamic routing and failure recovery approaches for efficient resource utilization in OpenFlow-SDN: A survey. IEEE Access 2022, 10, 121791–121815. [Google Scholar] [CrossRef]
- Kobo, H.I.; Abu-Mahfouz, A.M.; Hancke, G.P., Jr. A survey on software-defined wireless sensor networks: Challenges and design requirements. IEEE Access 2017, 5, 1872–1899. [Google Scholar] [CrossRef]
- Rafique, W.; Qi, L.; Yaqoob, I.; Imran, M.; Rasool, R.U.; Dou, W. Complementing IoT services through software defined networking and edge computing: A comprehensive survey. IEEE Commun. Surv. Tutor. 2020, 22, 1761–1804. [Google Scholar] [CrossRef]
- Zhao, Y.; Li, Y.; Zhang, X.; Geng, G.; Zhang, W.; Sun, Y. A survey of networking applications applying the software defined networking concept based on machine learning. IEEE Access 2019, 7, 95397–95417. [Google Scholar] [CrossRef]
- Xie, J.; Yu, F.R.; Huang, T.; Xie, R.; Liu, J.; Wang, C.; Liu, Y. A Survey of Machine Learning Techniques Applied to Software Defined Networking (SDN): Research Issues and Challenges. IEEE Commun. Surv. Tutor. 2019, 21, 393–430. [Google Scholar] [CrossRef]
- Taheri, R.; Ahmed, H.; Arslan, E. Deep learning for the security of software-defined networks: A review. Clust. Comput. 2023, 26, 3089–3112. [Google Scholar] [CrossRef]
- Shahzad, M.; Rizvi, S.; Khan, T.A.; Ahmad, S.; Ateya, A.A. An exhaustive parametric analysis for securing SDN through traditional, AI/ML, and blockchain approaches: A systematic review. Int. J. Networked Distrib. Comput. 2025, 13, 12. [Google Scholar] [CrossRef]
- Bardhi, E.; Conti, M.; Lazzeretti, R. Is AI a trick or t(h)reat for securing programmable data planes? IEEE Netw. 2024, 38, 146–152. [Google Scholar] [CrossRef]
- Li, Y.; Chen, M. Software-defined network function virtualization: A survey. IEEE Access 2015, 3, 2542–2553. [Google Scholar] [CrossRef]
- Demirci, S.; Demirci, M.; Sagiroglu, S. Virtual security functions and their placement in software defined networks: A survey. GAZI Univ. J. Sci. 2019, 32, 833–851. [Google Scholar] [CrossRef]
- Demirci, S.; Sagiroglu, S. Optimal placement of virtual network functions in software defined networks: A survey. J. Netw. Comput. Appl. 2019, 147, 102424. [Google Scholar] [CrossRef]
- Sengupta, S.; Chowdhary, A.; Sabur, A.; Alshamrani, A.; Huang, D.; Kambhampati, S. A Survey of Moving Target Defenses for network security. IEEE Commun. Surv. Tutor. 2020, 22, 1909–1941. [Google Scholar] [CrossRef]
- Macedo, D.F.; Guedes, D.; Vieira, L.F.M.; Vieira, M.A.M.; Nogueira, M. Programmable networks-from software-defined radio to software-defined networking. IEEE Commun. Surv. Tutor. 2015, 17, 1102–1125. [Google Scholar] [CrossRef]
- Balarezo, J.F.; Wang, S.; Chavez, K.G.; Al-Hourani, A.; Kandeepan, S. A survey on DoS/DDoS attacks mathematical modelling for traditional, SDN and virtual networks. Eng. Sci. Technol. Int. J. 2022, 31, 101065. [Google Scholar] [CrossRef]
- Carrascal, D.; Rojas, E.; Arco, J.M.; Lopez-Pajares, D.; Alvarez-Horcajo, J.; Carral, J.A. A comprehensive survey of in-band control in SDN: Challenges and opportunities. Electronics 2023, 12, 1265. [Google Scholar] [CrossRef]
- Diouf, M.; Ouya, S.; Klein, J.; Bissyandé, T. Software security in software-defined networking: A systematic literature review. arXiv 2025, arXiv:2502.13828. [Google Scholar] [CrossRef]
- Moshref, M.; Bhargava, A.; Gupta, A.; Yu, M.; Govindan, R. Flow-level state transition as a new switch primitive for SDN. In Proceedings of the 2014 ACM conference on SIGCOMM (SIGCOMM14), Chicago, IL, USA, 17–22 August 2014. [Google Scholar]
- Bianchi, G.; Bonola, M.; Capone, A.; Cascone, C. OpenState: Programming platform-independent stateful OpenFlow applications inside the switch. ACM SIGCOMM Comput. Commun. Rev. 2014, 44, 44–51. [Google Scholar] [CrossRef]
- Sun, C.; Bi, J.; Chen, H.; Hu, H.; Zheng, Z.; Zhu, S.; Wu, C. SDPA: Toward a stateful data plane in software-defined networking. IEEE/ACM Trans. Netw. 2017, 25, 3294–3308. [Google Scholar] [CrossRef]
- Scholz, D.; Gallenmuller, S.; Stubbe, H.; Carle, G. SYN flood defense in programmable data planes. In Proceedings of the 3rd P4 Workshop in Europe (EuroP4 2020), Part of CoNEXT 2020, New York, NY, USA, 1–4 December 2020. [Google Scholar]
- Scholz, D.; Gallenmuller, S.; Stubbe, H.; Jaber, B.; Rouhi, M.; Carle, G. Me Love (SYN-) Cookies: SYN Flood Mitigation in Programmable Data Planes. Available online: https://arxiv.org/pdf/2003.03221 (accessed on 18 January 2025).
- Lin, T.-Y.; Wu, J.-P.; Hung, P.-H.; Shao, C.-H.; Wang, Y.-T.; Cai, Y.-Z.; Tsai, M.-H. Mitigating SYN flooding Attack and ARP Spoofing in SDN Data Plane. In Proceedings of the 21st Asia-Pacific Network Operations and Management Symposium (APNOMS), Daegu, Republic of Korea, 22–25 September 2020. [Google Scholar]
- Khooi, X.Z.; Csikor, L.; Divakaran, D.M.; Kang, M.S. DIDA: Distributed in-network defense architecture against amplified reflection DDoS attacks. In Proceedings of the 6th IEEE International Conference on Network Softwarization (NetSoft), Ghent, Belgium, 29 June–3 July 2020. [Google Scholar]
- Friday, K.; Kfoury, E.; Bou-Harb, E.; Crichigno, J. Towards a Unified In-Network DDoS Detection and Mitigation Strategy. In Proceedings of the 6th IEEE International Conference on Network Softwarization (NetSoft), Ghent, Belgium, 29 June–3 July 2020. [Google Scholar]
- Simsek, G.; Bostan, H.; Sarica, A.K.; Sarikaya, E.; Keles, A.; Angin, P.; Alemdar, H.; Onur, E. DroPPPP: A P4 Approach to Mitigating DoS Attacks in SDN. In Proceedings of the International Workshop on Information Security Applications, Jeju Island, Republic of Korea, 26–28 August 2020. [Google Scholar]
- Dimolianis, M.; Pavlidis, A.; Maglaris, V. A multi-feature DDoS detection schema on P4 network hardware. In Proceedings of the 1st Workshop on Flexible Network Data Plane Processing (NETPROC@ICIN2020), Paris, France, 24–27 February 2020. [Google Scholar]
- Zhang, M.; Li, G.; Wang, S.; Liu, C.; Chen, A.; Hu, H.; Gu, G.; Li, Q.; Xu, M.; Wu, J. Poseidon: Mitigating volumetric DDoS attacks with programmable switches. In Proceedings of the Network and Distributed Systems Security (NDSS) Symposium, San Diego, CA, USA, 23–26 February 2020. [Google Scholar]
- Liu, Z.; Namkung, H.; Nikolaidis, G.; Lee, J.; Kim, C.; Jin, X.; Braverman, V.; Yu, M.; Sekar, V. Jaqen: A High-Performance Switch-Native Approach for Detecting and Mitigating Volumetric DDoS Attacks with Programmable Switches. In Proceedings of the 30th USENIX Security Symposium, Online, 11–13 August 2021. [Google Scholar]
- Xing, J.; Wu, W.; Chen, A. Ripple: A programmable, decentralized link-flooding defense against adaptive adversaries. In Proceedings of the 30th USENIX Security Symposium, Online, 11–13 August 2021. [Google Scholar]
- Kuka, M.; Vojanec, K.; Kucera, J.; Benacek, P. Accelerated DDoS attacks mitigation using programmable data plane. In Proceedings of the ACM/IEEE Symposium on Architectures for Networking and Communications Systems (ANCS), Cambridge, UK, 24–25 September 2019. [Google Scholar]
- Lapolli, A.C.; Marques, J.A.; Gaspary, L.P. Offloading real-time DDoS attack detection to programmable data planes. In Proceedings of the IFIP/IEEE Symposium on Integrated Network and Service Management (IM), Arlington, WA, USA, 8–12 April 2019. [Google Scholar]
- Ding, D.; Savi, M.; Pederzolli, F.; Campanella, M.; Siracusa, D. In-network volumetric DDoS victim identification using programmable commodity switches. IEEE Trans. Netw. Serv. Manag. 2021, 18, 1191–1202. [Google Scholar] [CrossRef]
- Ding, D.; Savi, M.; Siracusa, D. Tracking normalized network traffic entropy to detect DDoS attacks in P4. IEEE Trans. Dependable Secur. Comput. 2022, 19, 4019–4031. [Google Scholar] [CrossRef]
- Sivaraman, V.; Narayana, S.; Rottenstreich, O.; Muthukrishnan, S.; Rexford, J. Heavy-hitter detection entirely in the data plane. In Proceedings of the Symposium on SDN Research (SOSR17), Santa Clara, CA, USA, 3–4 April 2017. [Google Scholar]
- Febro, A.; Xiao, H.; Spring, J. Telephony denial of service defense at data plane (TDoSD@DP). In Proceedings of the 2018 IEEE/IFIP Network Operations and Management Symposium, Taipei, Taiwan, 23–27 April 2018. [Google Scholar]
- Febro, A.; Xiao, H.; Spring, J. Distributed SIP DDoS defense with P4. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), Marrakesh, Morocco, 15–18 April 2019. [Google Scholar]
- Mi, Y.; Wang, A. ML-Pushback: Machine learning based pushback defense against DDoS. In Proceedings of the 15th International Conference on Emerging Networking EXperiments and Technologies (CoNEXT19), Orlando, FL, USA, 9–12 December 2019. [Google Scholar]
- González, L.A.Q.; Castanheira, L.; Marques, J.A.; Schaeffer-Filho, A. BUNGEE: An adaptive pushback mechanism for DDoS detection and mitigation in P4 data planes. In Proceedings of the IFIP/IEEE International Symposium on Integrated Network Management (IM), Bordeaux, France, 16–21 May 2021. [Google Scholar]
- Yue, M.; Wang, H.; Liu, L.; Wu, Z. Detecting DoS attacks based on multi-features in SDN. IEEE Access 2020, 8, 104688–104700. [Google Scholar] [CrossRef]
- Musumeci, F.; Ionata, V.; Paolucci, F.; Cugini, F.; Tornatore, M. Machine-learning-assisted DDoS attack detection with P4 language. In Proceedings of the IEEE International Conference on Communications (ICC) (ICC2020), Dublin, Ireland, 7–11 June 2020. [Google Scholar]
- Zhang, W.; Jing, S.; Zhao, C. Anti-DDoS attacks strategy of SDN data plane with data augmentation based on P4. In Proceedings of the International Conference on High Performance Computing & Communications, Data Science & Systems, Smart City & Dependability in Sensor, Cloud & Big Data Systems & Application (HPCC/DSS/SmartCity/DependSys), Melbourne, Australia, 17–21 December 2023. [Google Scholar]
- Ndonda, G.K.; Sadre, R. A two-level intrusion detection system for industrial control system networks using P4. In Proceedings of the 5th International Symposium for ICS & SCADA Cyber Security Research 2018 (ICS-CSR 2018), Hamburg, Germany, 29–30 August 2018. [Google Scholar]
- Lewis, B.; Broadbent, M.; Race, N. P4ID: P4 enhanced intrusion detection. In Proceedings of the IEEE Conference on Network Function Virtualization and Software Defined Networks (NFV-SDN), Dallas, TX, USA, 12–14 November 2019. [Google Scholar]
- Cai, Y.-Z.; Lin, T.-Y.; Wang, Y.-T.; Tuan, Y.-P. E-Replacement: Efficient scanner data collection method in P4-based software-defined networks. Int. J. Netw. Manag. 2021, 31, e2162. [Google Scholar] [CrossRef]
- Golchin, P.; Zhou, C.; Agnihotri, P.; Agnihotri, P.; Hajizadeh, M.; Kundel, R.; Steinmetz, R. CML-IDS: Enhancing intrusion detection in SDN through collaborative machine learning. In Proceedings of the 19th International Conference on Network and Service Management (CNSM 2023), Niagara Falls, ON, Canada, 30 October–2 November 2023. [Google Scholar]
- Doriguzzi-Corin, R.; Knob, L.A.D.; Mendozzi, L.; Siracusa, D.; Savi, M. Introducing packet-level analysis in programmable data planes to advance network intrusion detection. Comput. Netw. 2024, 239, 110162. [Google Scholar] [CrossRef]
- Sanghi, A.; Kadiyala, K.P.; Tammana, P.; Joshi, S. Anomaly detection in data plane systems using packet execution paths. In Proceedings of the ACM SIGCOMM 2021 Workshop on Secure Programmable Network Infrastructure, New York, NY, USA, 27 August 2021. [Google Scholar]
- Qin, Q.; Poularakis, K.; Leung, K.K.; Tassiulas, L. Line-speed and scalable intrusion detection at the network edge via federated learning. In Proceedings of the IFIP Networking Conference (Networking), Paris, France, 22–25 June 2020. [Google Scholar]
- Gutierrez, S.A.; Branch, J.W.; Gaspary, L.P.; Botero, J.F. Watching Smartly from the Bottom: Intrusion Detection Revamped Through Programmable Networks and Artificial Intelligence. Available online: https://arxiv.org/pdf/2106.00239 (accessed on 18 January 2025).
- Brandino, B.; Casas, P.; Grampín, E. Detecting attacks at switching speed: AI/ML and active learning for in-network monitoring in data planes. In Proceedings of the IEEE 32nd International Conference on Network Protocols (ICNP 2024), Charleroi, Belgium, 28–31 October 2024. [Google Scholar]
- Brandino, B.; Grampin, E.; Dietz, K.; Wehner, N.; Seufert, M.; Hoßfeld, T.; Casas, P. HALIDS: A hardware-assisted machine learning IDS for in-network monitoring. In Proceedings of the 8th Network Traffic Measurement and Analysis Conference (TMA 2024), Dresden, Germany, 21–24 May 2024. [Google Scholar]
- Maheswaran, N.; Bose, S.; Gokulraj, G.; Anitha, T.; Shruthi, T.; Vijayaraj, G. Intrusion prevention system in SDN environment for 6G networks using deep learning. In Proceedings of the 6th International Conference on Mobile Computing and Sustainable Informatics (ICMCSI-2025), Lalitpur, Nepal, 7–8 January 2025. [Google Scholar]
- Spina, M.G.; DeRango, F.; Scalzo, E.; Guerriero, F.; Iera, A. Distributing intelligence in 6G programmable data planes for effective in-network intrusion prevention. IEEE Netw. 2025, 39, 319–325. [Google Scholar] [CrossRef]
- Seufert, M.; Dietz, K.; Wehner, N.; Geißler, S.; Schüler, J.; Wolz, M.; Hotho, A.; Casas, P.; Hoßfeld, T.; Feldmann, A. Marina: Realizing ML-driven real-time network traffic monitoring at terabit scale. IEEE Trans. Netw. Serv. Manag. 2024, 21, 2773–2790. [Google Scholar] [CrossRef]
- Wang, H.; Tan, X.; Yuan, S.; Li, M.; Wu, J.; Zheng, Q. A two-phase encrypted traffic classification scheme in programmable data plane. In Proceedings of the IEEE International Symposium on Parallel and Distributed Processing with Applications (ISPA), Kaifeng, China, 30 October–2 November 2024. [Google Scholar]
- Sanvito, D.; Moro, D.; Capone, A. Towards traffic classification offloading to stateful SDN data planes. In Proceedings of the IEEE Conference on Network Softwarization (NetSoft 2017), Bologna, Italy, 3–7 July 2017. [Google Scholar]
- Hypolite, J.; Sonchack, J.; Hershkop, S.; Dautenhahn, N.; DeHon, A.; Smith, J.M. DeepMatch: Practical deep packet inspection in the data plane using network processors. In Proceedings of the 16th International Conference on Emerging Networking EXperiments and Technologies (CoNEXT20), Barcelona, Spain, 1–4 December 2020. [Google Scholar]
- AlSabeh, A.; Kfoury, E.; Crichigno, J.; Bou-Harb, E. P4DDPI: Securing P4-programmable data plane networks via DNS deep packet inspection. In Proceedings of the Workshop on Measurements, Attacks, and Defenses for the Web (MADWeb), San Diego, CA, USA, 28 April 2022; pp. 1–7. [Google Scholar]
- Gupta, S.; Gosain, D.; Kwon, M.; Acharya, H.B. DeeP4R: Deep packet inspection in P4 using packet recirculation. In Proceedings of the IEEE Conference on Computer Communications (INFOCOM 2023), New York, NY, USA, 17–20 May 2023. [Google Scholar]
- Voros, P.; Kiss, A. Security middleware programming using P4. In International Conference on Human Aspects of Information Security, Privacy, and Trust; Tryfonas, T., Ed.; Springer: Berlin/Heidelberg, Germany, 2016. [Google Scholar]
- Cao, J.; Bi, J.; Zhou, Y.; Zhang, C. CoFilter: A high-performance switch-assisted stateful packet filter. In Proceedings of the ACM SIGCOMM 2018 Conference on Posters and Demos, Budapest, Hungary, 20–25 August 2018. [Google Scholar]
- Datta, R.; Choi, S.; Chowdhary, A.; Park, Y. P4Guard: Designing P4 based firewall. In Proceedings of the 2018 IEEE Military Communications Conference (MILCOM), Los Angeles, CA, USA, 29–31 October 2018. [Google Scholar]
- Ricart-Sanchez, R.; Malagon, P.; Alcarez-Calero, J.M.; Wang, Q. NetFPGA-based firewall solution for 5G multi-tenant architectures. In Proceedings of the 2019 IEEE International Conference on Edge Computing (EDGE), Milan, Italy, 8–13 July 2019. [Google Scholar]
- Afek, Y.; Bremler-Barr, A.; Shafir, L. Network anti-spoofing with SDN data plane. In Proceedings of the IEEE Conference on Computer Communications (INFOCOM 2017), Atlanta, CA, USA, 1–4 May 2017. [Google Scholar]
- Gondaliya, H.; Sankaran, G.C.; Sivalingam, K.M. Comparative Evaluation of IP Address Anti-Spoofing Mechanisms Using a P4/NetFPGA-Based Switch. In Proceedings of the 3rd P4 Workshop in Europe (EuroP4 2020), Part of CoNEXT 2020, Barcelona, Spain, 1 December 2020. [Google Scholar]
- Kuang, P.; Liu, Y.; He, L. P4DAD: Securing duplicate address detection using P4. In Proceedings of the IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020. [Google Scholar]
- Li, G.; Zhang, M.; Liu, C.; Kong, X.; Chen, A.; Gu, G.; Duan, H. NetHCF: Enabling Line-Rate and Adaptive Spoofed IP Traffic Filtering. In Proceedings of the IEEE 27th International Conference on Network Protocols (ICNP), Chicago, IL, USA, 8–10 October 2019. [Google Scholar]
- Datta, T.; Feamster, N.; Rexford, J.; Wang, L. SPINE: Surveillance protection in the network elements. In Proceedings of the 9th USENIX Workshop on Free and Open Communications on the Internet (FOCI 19), Santa Clara, CA, USA, 13 August 2019. [Google Scholar]
- Chang, D.; Sun, W.; Yang, Y. A SDN proactive defense mechanism based on IP transformation. In Proceedings of the 2nd International Conference on Safety Produce Informatization (IICSPI), Chongqing, China, 28–30 November 2019. [Google Scholar]
- Govil, Y.; Wang, L.; Rexford, J. MIMIQ: Masking IPs with migration in QUIC. In Proceedings of the USENIX Workshop on Free and Open Communications on the Internet (FOCI), Austin, TX, USA, 11 August 2020. [Google Scholar]
- Liu, G.; Quan, W.; Cheng, N.; Lu, N.; Zhang, H.; Shen, X. P4NIS: Improving network immunity against eavesdropping with programmable data planes. In Proceedings of the IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Vancouver, BC, Canada, 20 May 2020. [Google Scholar]
- Liu, G.; Quan, W.; Cheng, N.; Gao, D.; Lu, N.; Zhang, H.; Shen, X. Softwarized IoT network immunity against eavesdropping with programmable data planes. IEEE Internet Things 2021, 8, 6578–6590. [Google Scholar] [CrossRef]
- Meier, R.; Tsankov, P.; Lenders, V.; Vanbever, L.; Vechev, M. NetHide: Secure and practical network topology obfuscation. In Proceedings of the 27th USENIX Security Symposium, Baltimore, MD, USA, 15–17 August 2018. [Google Scholar]
- Moghaddam, H.M.; Mosenia, A. Anonymizing Masses: Practical Light-Weight Anonymity at the Network Level. Available online: https://arxiv.org/abs/1911.09642 (accessed on 17 January 2025).
- Kim, H.; Gupta, A. ONTAS: Flexible and scalable online network traffic anonymization system. In Proceedings of the 2019 Workshop on Network Meets AI & ML (NetAI19), Beijing, China, 23 August 2019. [Google Scholar]
- Almaini, A.; Al-Dubai, A.; Romdhani, I.; Schramm, M. Delegation of authentication to the data plane in software-defined networks. In Proceedings of the 2019 IEEE International Conferences on Ubiquitous Computing & Communications (IUCC) and Data Science and Computational Intelligence (DSCI) and Smart Computing, Networking and Services (SmartCNS), Shenyang, China, 21–23 October 2019. [Google Scholar]
- Almaini, A.; Al-Dubai, A.; Romdhani, I.; Schramm, M.; Alsarhan, A. Lightweight edge authentication for software defined networks. Computing 2021, 103, 291–311. [Google Scholar] [CrossRef]
- Zaballa, E.O.; Franco, D.; Zhou, Z.; Berger, M.S. P4Knocking: Offloading host-based firewall functionalities to the network. In Proceedings of the 1st Workshop on Flexible Network Data Plane Processing (NETPROC@ICIN2020), Paris, France, 24–27 February 2020. [Google Scholar]
- Qin, Y.; Quan, W.; Song, F.; Zhang, L.; Liu, G.; Liu, M. Flexible encryption for reliable transmission based on the P4 programmable platform. In Proceedings of the Information Communication Technologies Conference, Nanjing, China, 29–31 May 2020. [Google Scholar]
- Chen, X. Implementing AES encryption on programmable switches via scrambled lookup tables. In Proceedings of the 2020 ACM SIGCOMM Workshop on Secure Programmable Network Infrastructure (SPIN20), Online, 10 August 2020. [Google Scholar]
- Oliveira, I.; Neto, E.; Immich, R.; Fontes, R.; Neto, A.; Rodriguez, F.; Rothenberg, C.E. Dh-aes-p4: On-premise encryption and in-band key-exchange in P4 fully programmable data planes. In Proceedings of the 4th Workshop on Mobility Support in Slice-Based Network Control for Heterogeneous Environments (IEEE NFV-SDN 2021), Heraklion, Greece, 9 November 2021. [Google Scholar]
- Hauser, F.; Schmidt, M.; Haberle, M.; Menth, M. P4-MACsec: Dynamic topology monitoring and data layer protection with MACsec in P4-based SDN. IEEE Access 2020, 8, 58845–58858. [Google Scholar] [CrossRef]
- Hauser, F.; Haberle, M.; Menth, M. P4-IPsec: Site-to-site and host-to-site VPN with IPsec in P4-based SDN. IEEE Access 2020, 8, 139567–139586. [Google Scholar] [CrossRef]
- Scholz, D.; Oeldemann, A.; Geyer, F.; Gallenmüller, S.; Stubbe, H.; Wild, T.; Herkersdorf, A.; Carle, G. Cryptographic hashing in P4 data planes. In Proceedings of the ACM/IEEE Symposium on Architectures for Networking and Communications Systems (ANCS 2019), Cambridge, UK, 24–25 September 2019. [Google Scholar]
- Narayanan, N.; Sankaran, G.; Sivalingam, K. Mitigation of security attacks in the SDN data plane using P4-enabled switches. In Proceedings of the 2019 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), Goa, India, 16–19 December 2019. [Google Scholar]
- Liu, M.; Gao, D.; Liu, G.; He, J.; Jin, L.; Zhou, C.; Yang, F. Learning based adaptive network immune mechanism to defense eavesdropping attacks. IEEE Access 2019, 7, 182814–182826. [Google Scholar] [CrossRef]
- Xing, J.; Wu, W.; Chen, A. Architecting programmable data plane defenses into the network with FastFlex. In Proceedings of the 18th ACM Workshop on Hot Topics in Networks (HotNets 2019), Princeton, NJ, USA, 13–15 November 2019. [Google Scholar]
- Castanheira, L.; Parizotto, R.; Schaeffer-Filho, A.E. FlowStalker: Comprehensive traffic flow monitoring on the data plane using P4. In Proceedings of the 2019 IEEE International Conference on Communications (ICC 2019), Shanghai, China, 20–24 May 2019. [Google Scholar]
- Gori, G.; Rinieri, L.; Sadi, A.A.; Melis, A.; Callegati, F.; Prandini, M. GRAPH4: A security monitoring architecture based on data plane anomaly detection metrics calculated over attack graphs. Future Internet 2023, 15, 368. [Google Scholar] [CrossRef]
- Ganesan, A.; Sarac, K. Attack detection and mitigation using intelligent data planes in SDNs. In Proceedings of the IEEE Global Communications Conference: Communication & Information Systems Security (GLOBECOM 2022), Rio de Janeiro, Brazil, 4–8 December 2022. [Google Scholar]
- Smyth, D.; Scott-Hayward, S.; Cionca, V.; McSweeney, S.; O’Shea, D. SECAP switch–defeating topology poisoning attacks using P4 data planes. J. Netw. Syst. Manag. 2023, 31, 28. [Google Scholar] [CrossRef]
- Zhou, G.; Liu, Z.; Fu, C.; Li, Q.; Xu, K. An efficient design of intelligent network data plane. In Proceedings of the 32nd USENIX Security Symposium, Anaheim, CA, USA, 9–11 August 2023. [Google Scholar]
- Nascimento, A.; Abreu, D.; Riker, A.; Abelém, A. AID-SDN: Advanced intelligent defense for SDN using P4 and machine learning. In Proceedings of the IEEE Latin-American Conference on Communications (LATINCOM), Panama City, Panama, 15–17 November 2023. [Google Scholar]
- Paolucci, F.; Civerchia, F.; Sgambelluri, A.; Giorgetti, A.; Cugini, F.; Castoldi, P. P4 edge node enabling stateful traffic engineering and cyber security. J. Opt. Commun. Netw. 2019, 11, A84–A95. [Google Scholar] [CrossRef]
- Hwang, R.-H.; Nguyen, V.-L.; Lin, P.-C. StateFit: A security framework for SDN programmable data plane model. In Proceedings of the 15th International Symposium on Pervasive Systems, Algorithms and Networks, Yichang, China, 16–18 October 2018. [Google Scholar]
- Grigoryan, G.; Liu, Y. LAMP: Prompt Layer 7 attack mitigation with programmable data planes. In Proceedings of the IEEE 17th International Symposium on Network Computing and Applications (NCA), Cambridge, MA, USA, 1–3 November 2018. [Google Scholar]
- Kang, Q.; Xue, L.; Morrison, A.; Tang, Y.; Chen, A.; Luo, X. Programmable in-network security for context-aware BYOD policies. In Proceedings of the 29th USENIX Security Symposium, Boston, MA, USA, 12–14 August 2020. [Google Scholar]
- Yang, S.; Bai, L.; Cui, L.; Ming, Z.; Wu, Y.; Yu, S.; Shen, H.; Pan, Y. An efficient pipeline processing scheme for programming Protocol-independent Packet Processors. J. Netw. Comput. Appl. 2020, 171, 102806. [Google Scholar] [CrossRef]
- Xing, J.; Kang, Q.; Chen, A. NetWarden: Mitigating network covert channels while preserving performance. In Proceedings of the 29th USENIX Security Symposium, San Diego, CA, USA, 12–14 August 2020. [Google Scholar]
- Laraba, A.; Francois, J.; Chrisment, I.; Chowdhury, S.R.; Boutaba, R. Defeating protocol abuse with P4: Application to explicit congestion notification. In Proceedings of the IFIP Networking Conference (Networking), Paris, France, 22–26 June 2020. [Google Scholar]
- Barradas, D.; Santos, N.; Rodrigues, L.; Signorello, S.; Ramos, F.M.V.; Madeira, A. FlowLens: Enabling Efficient Flow Classification for ML-based Network Security Applications. In Proceedings of the Network and Distributed Systems Security (NDSS) Symposium, Online, 21–25 February 2021. [Google Scholar]
- Bai, S.; Kim, H.; Rexford, J. Passive OS Fingerprinting on Commodity Switches. In Proceedings of the IEEE 8th International Conference on Network Softwarization (NetSoft), Milan, Italy, 27 June–1 July 2022. [Google Scholar]
- Yazdinejad, A.; Parizi, R.M.; Dehghantanha, A.; Choo, K.-K.R. P4 to-blockchain: A secure blockchain-enabled packet parser for software defined networking. Comput. Secur. 2020, 88, 101629. [Google Scholar] [CrossRef]
- Moro, D.; Verticale, G.; Capone, A. Network function decomposition and offloading on heterogeneous networks with programmable data planes. IEEE Open J. Commun. Soc. 2021, 2, 1874–1885. [Google Scholar] [CrossRef]
- Internet Engineering Task Force. Request for Comments (RFC) 9000 QUIC: A UDP-Based Multiplexed and Secure Transport; RFC Editor: Marina del Rey, CA, USA, 2021. [Google Scholar]
- Bouet, M.; Leguay, J.; Conan, V. Cost-based placement of virtualized deep packet inspection functions in SDN. In Proceedings of the IEEE Military Communications Conference (MILCOM-IEEE 2013), San Diego, CA, USA, 18–20 November 2013. [Google Scholar]
- Cerrato, I.; Jungel, T.; Palesandro, A.; Risso, F.; Sune, M.; Woesner, H. User-specific network service functions in an SDN-enabled network node. In Proceedings of the Third European Workshop on Software-Defined Networks, Budapest, Hungary, 1–3 September 2014. [Google Scholar]
- Lin, Y.-D.; Lin, P.-C.; Yeh, C.-H.; Wang, Y.-C.; Lai, Y.-C. An extended SDN architecture for network function virtualization with a case study on intrusion prevention. IEEE Netw. 2015, 29, 48–53. [Google Scholar] [CrossRef]
- Bu, C.; Wang, X.; Cheng, H.; Huang, M.; Li, K.; Das, S.K. Enabling adaptive routing service customization via the integration of SDN and NFV. J. Netw. Comput. Appl. 2017, 93, 123–136. [Google Scholar] [CrossRef]
- Schulz-Zander, J.; Mayer, C.; Ciobotaru, B.; Lisicki, R.; Schmid, S.; Feldmann, A. Unified programmability of virtualized network functions and software-defined wireless networks. IEEE/ACM Trans. Netw. 2017, 14, 1046–1060. [Google Scholar] [CrossRef]
- Tian, C.; Munir, A.; Liu, A.; Yang, J.; Zhao, Y. OpenFunction: An extensible data plane abstraction protocol for platform-independent software-defined middleboxes. IEEE/ACM Trans. Netw. 2018, 26, 1488–1501. [Google Scholar] [CrossRef]
- Park, T.; Kim, Y.; Yegneswaran, V.; Porras, P.; Xu, Z.; Park, K.; Shin, S. DPX: Data-plane extensions for SDN security service instantiation. In Proceedings of the International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, Gothenburg, Sweden, 19–20 June 2019. [Google Scholar]
- Kim, J.; Kim, Y.; Yegneswaran, V.; Porras, P.; Shin, S.; Park, T. Extended data plane architecture for in-network security services in software-defined networks. Comput. Secur. 2023, 124, 102976. [Google Scholar] [CrossRef]
- Deng, J.; Hu, H.; Li, H.; Pan, Z.; Wang, K.-C.; Ahn, G.-J.; Bi, J.; Park, Y. VNGuard: An NFV/SDN combination framework for provisioning and managing virtual Firewalls. In Proceedings of the IEEE Conference on Network Function Virtualization and Software Defined Network (NFV-SDN), San Francisco, CA, USA, 18–21 November 2015. [Google Scholar]
- Thang, N.; Park, M.; Joo, Y.-I. Elastic Virtual Honeypot System for SDNFV-based networks. Int. J. Commun. Netw. Inf. Secur. 2020, 12, 295–301. [Google Scholar] [CrossRef]
- Paolucci, F.; Cugini, F.; Castoldi, P.; Osinski, T. Enhancing 5G SDN/NFV edge with P4 data plane programmability. IEEE Netw. 2021, 35, 154–160. [Google Scholar] [CrossRef]
- Das, D.; Banerjee, S.; Dasgupta, K.; Chatterjee, P.; Ghosh, U.; Biswas, U. Blockchain enabled SDN framework for security management in 5G applications. In Proceedings of the 24th International Conference on Distributed Computing and Networking, Kharagpur, India, 4–7 January 2023. [Google Scholar]
- Aguado, A.; Hugues-Salas, E.; Haigh, P.A.; Marhuenda, J.; Price, A.B.; Sibson, P.; Kennard, J.E.; Erven, C.; Rarity, J.G.; Thompson, M.G.; et al. First experimental demonstration of secure NFV orchestration over an SDN-controlled optical network with time-shared quantum key distribution. In Proceedings of the 42nd European Conference and Exhibition on Optical Communications, Düsseldorf, Germany, 18–22 September 2016. [Google Scholar]
- Aguado, A.; Hugues-Salas, E.; Haigh, P.A.; Marhuenda, J.; Price, A.B.; Sibson, P.; Kennard, J.E.; Erven, C.; Rarity, J.G.; Thompson, M.G.; et al. Secure NFV orchestration over an SDN-controlled optical network with time-shared quantum key distribution resources. J. Lightwave Technol. 2017, 35, 1357–1362. [Google Scholar] [CrossRef]
- Aguado, A.; Lopez, V.; Lopez, D.; Peev, M.; Poppe, A.; Pastor, A.; Folgueira, J.; Martin, V. The engineering of software-defined quantum key distribution networks. IEEE Commun. Mag. 2019, 57, 20–26. [Google Scholar] [CrossRef]
- Peng, Y.; Wu, C.; Zhao, B.; Yu, W.; Liu, B.; Qiao, S. QKDFlow: QKD based secure communication towards the OpenFlow interface in SDN. In Proceedings of the 4th International Conference on Geo-Informatics in Resource Management and Sustainable Ecosystem (GRMSE2016), Hong Kong, China, 18–20 November2016. [Google Scholar]
- Lopez, D.R.; Martin, V.; Lopez, V.; Iglesia, F.d.l.; Pastor, A.; Brunner, H.; Aguado, A.; Bettelli, S.; Fung, F.; Hillerkuss, D.; et al. Demonstration of software defined network services utilizing quantum key distribution fully integrated with standard telecommunication network. Quantum Rep. 2020, 2, 453–458. [Google Scholar] [CrossRef]
- Lopez, V.; Pastor, A.; Lopez, D.; Aguado, A.; Martin, V. MadQCI: A heterogeneous and scalable SDN QKD network deployed in production facilities. arXiv 2023, arXiv:2311.12791. [Google Scholar] [CrossRef]
- Tessinari, R.S.; Arabul, E.; Alia, O.; Muqaddas, A.S.; Kanellos, G.T.; Nejabati, R.; Simeonidou, D. Demonstration of a dynamic QKD network control using a QKD-aware SDN application over a programmable hardware encryptor. In Proceedings of the Optical Fiber Communication Conference (OFC2021), Washington, DC, USA, 6–11 June 2021. [Google Scholar]
- Arabul, E.; Tessinari, R.S.; Alia, O.; Hugues-Salas, E.; Kanellos, G.T.; Nejabati, R.; Simeonidou, D. Experimental demonstration of programmable 100 Gb/s SDN-enabled encryptors/decryptors for QKD networks. In Proceedings of the Optical Fiber Communication Conference (OFC 2021), Washington, DC, USA, 6–11 June 2021. [Google Scholar]
- Arabul, E.; Tessinari, R.S.; Alia, O.; Oliveira, R.; Kanellos, G.T.; Nejabati, R.; Simeonidou, D. 100 Gb/s dynamically programmable SDN-enabled hardware encryptor for optical networks. J. Opt. Commun. Netw. 2022, 14, A50–A60. [Google Scholar] [CrossRef]
- Mahdi, S.S.; Abdullah, A.A. Enhanced security of software-defined network and network slice through hybrid quantum key distribution protocol. Infocommun. J. 2022, 14, 9–15. [Google Scholar] [CrossRef]
- Tessinari, R.S.; Woodward, R.I.; Shields, A.J. Software-defined quantum network using a QKD-secured SDN controller and encrypted messages. In Proceedings of the Optical Fiber Communication Conference (OFC 2023), San Diego, CA, USA, 5–9 March 2023. [Google Scholar]
- García, C.R.; Rommel, S.; Olmos, J.J.V.; Monroy, I.T. Enhancing the security of software defined networks via quantum key distribution and post-quantum cryptography. In Proceedings of the Distributed Computing and Artificial Intelligence, Special Sessions I, 20th International Conference (DCAI2023), Guimarães, Portugal, 12–14 July 2023. [Google Scholar]
- Rempola, M.H.; Smith, A.; Li, Y.; Du, L. Securing SDN communication through quantum key distribution. In Proceedings of the Distributed Computing and Artificial Intelligence, Special Sessions I, 20th International Conference (DCAI2023), Guimarães, Portugal, 12–14 July 2023. [Google Scholar]
- Satasiya, D.; Rupal, D.R. Analysis of software defined network firewall (SDF). In Proceedings of the International Conference on Wireless Communications, Signal Processing and Networking (WiSPNET), Chennai, India, 23–25 March 2016; pp. 228–231. [Google Scholar]
- Nife, F.; Kotulski, Z. Application—Aware firewall mechanism for software defined networks. J. Netw. Syst. Manag. 2020, 28, 605–626. [Google Scholar] [CrossRef]
- Huang, H.; Li, P.; Guo, S. Traffic scheduling for deep packet inspection in software-defined networks. Concurr. Comput. Pract. Exp. 2017, 29, e3967. [Google Scholar] [CrossRef]
- Yu, C.; Lan, J.; Xie, J.; Hu, Y. QoS-aware traffic classification architecture using machine learning and deep packet inspection in SDNs. In Proceedings of the 8th International Congress of Information and Communication Technology (ICICT 2018), Xiamen, China, 23–25 March 2018. [Google Scholar]
- Cheng, Q.; Wu, C.; Zhou, H.; Kong, D.; Zhang, D.; Xing, J.; Ruan, W. Machine learning based malicious payload identification in software defined networking. J. Netw. Comput. Appl. 2021, 192, 103186. [Google Scholar] [CrossRef]
- Sainz, M.; Garitano, I.; Iturbe, M.; Zurutuza, U. Deep packet inspection for intelligent intrusion detection in software-defined industrial networks: A proof of concept. Log. J. IGPL 2020, 28, 461–472. [Google Scholar] [CrossRef]
- Wu, X.; Liu, M.; Dou, W.; Yu, S. DDoS attacks on data plane of software-defined network: Are they possible? Secur. Commun. Netw. 2016, 9, 5444–5459. [Google Scholar] [CrossRef]
- Durner, R.; Lorenz, C.; Wiedemann, M.; Kellerer, W. Detecting and mitigating denial of service attacks against the data plane in software defined networks. In Proceedings of the IEEE Conference on Network Softwarization (NetSoft 2017), Bologna, Italy, 3–7 July 2017. [Google Scholar]
- Shang, G.; Zhe, P.; Bin, X.; Aiqun, H.; Kui, R. FloodDefender: Protecting data and control plane resources under SDN-aimed DoS attacks. In Proceedings of the IEEE Conference on Computer Communications (IEEE INFOCOM 2017), Atlanta, GA, USA, 1–4 May 2017. [Google Scholar]
- Ambrosin, M.; Conti, M.; Gaspari, F.D.; Poovendran, R. LineSwitch: Tackling control plane saturation attacks in software-defined networking. IEEE/ACM Trans. Netw. 2017, 25, 1206–1219. [Google Scholar] [CrossRef]
- Sahoo, K.; Puthal, D. SDN-assisted DDoS defense framework for the Internet of Multimedia Things. ACM Trans. Multimed. Comput. Commun. Appl. 2020, 98, 98. [Google Scholar] [CrossRef]
- Ujjan, R.; Pervez, Z.; Dahal, K.; Khan, W.; Khattak, A.; Hayat, B. Entropy Based Features Distribution for Anti-DDoS Model in SDN. Sustainability 2021, 13, 1522. [Google Scholar] [CrossRef]
- Sumantra, I.; Ghandi, S. DDoS attack detection and mitigation in software defined networks. In Proceedings of the International Conference on System, Computation, Automation and Networking (ICSCAN), Pondicherry, India, 3–4 July 2020. [Google Scholar]
- Carvalho, R.N.; Bordim, J.L.; Alchieri, E.A.P. Entropy-based DoS attack identification in SDN. In Proceedings of the IEEE International Parallel and Distributed Processing Symposium Workshops (IPDPSW 2019), Rio de Janeiro, Brazil, 20–24 May 2019. [Google Scholar]
- Wang, S.; Chandrasekharan, S.; Gomez, K.; Kandeepan, S.; Al-Hourani, A.; Asghar, M.R.; Russello, G.; Zanna, P. SECOD: SDN sEcure control and data plane algorithm for detecting and defending against DoS attacks. In Proceedings of the IEEE/IFIP Network Operations and Management Symposium (NOMS 2018), Taipei, Taiwan, 23–27 April 2018. [Google Scholar]
- Kaljic, E.; Maric, A.; Njemcevic, P. DoS attack mitigation in SDN networks using a deeply programmable packet-switching node based on a hybrid FPGA/CPU data plane architecture. In Proceedings of the XXVII International Conference on Information, Communication and Automation Technologies (ICAT 2019), Sarajevo, Bosnia and Herzegovina, 20–23 October 2019. [Google Scholar]
- Mahrach, S.; Haqiq, A. DDoS flooding attack mitigation in software defined networks. Int. J. Adv. Comput. Sci. Appl. 2020, 11, 693–700. [Google Scholar] [CrossRef]
- Carvalho, R.N.; Costa, L.R.; Bordim, J.L.; Alchieri, E.A.P. Enhancing an SDN architecture with DoS attack detection mechanisms. Adv. Sci. Technol. Eng. Syst. 2020, 5, 215–224. [Google Scholar] [CrossRef]
- Liu, Y.; Wang, Y.; Feng, H. POAGuard: A defense mechanism against preemptive table overflow attack in software-defined networks. IEEE Access 2023, 11, 123659–123676. [Google Scholar] [CrossRef]
- Niyaz, Q.; Sun, W.; Javaid, A.Y. A deep learning based DDoS detection system in software-defined networking (SDN). arXiv 2016, arXiv:1611.07400. [Google Scholar] [CrossRef]
- Alshamrani, A.; Chowdhary, A.; Pisharody, S.; Lu, D.; Huang, D. A defense system for defeating DDoS attacks in SDN based networks. In Proceedings of the 15th ACM International Symposium on Mobility Management and Wireless Access (MobiWac 2017), Miami, FL, USA, 21–25 November 2017. [Google Scholar]
- Prakash, A.; Priyadarshini, R. An intelligent software defined network controller for preventing Distributed Denial of Service (DDoS) attacks. In Proceedings of the Second International Conference on Inventive Communication and Computational Technologies (ICICCT 2018), Coimbatore, India, 20–21 April 2018. [Google Scholar]
- Krishnan, P.; Duttagupta, S.; Achuthan, K. VARMAN: Multi-plane security framework for software defined networks. Comput. Commun. 2019, 148, 215–239. [Google Scholar] [CrossRef]
- Swami, R.; Dave, M.; Ranga, V. Software-defined networking-based DDoS defense mechanisms. ACM Comput. Surv. 2019, 52, 28. [Google Scholar] [CrossRef]
- Abhiroop, T.; Babu, S.; Manoj, B.S. A machine learning approach for detecting DoS attacks in SDN switches. In Proceedings of the 24th National Conference on Communications (NCC), Hyderabad, India, 25–28 February 2018. [Google Scholar]
- Ahmad, A.; Harjula, E.; Ylianttila, M.; Ahmad, I. Evaluation of machine learning techniques for security in SDN. In Proceedings of the IEEE Globecom Workshops (GC Workshops 2020), Taipei, Taiwan, 7–11 December 2020. [Google Scholar]
- Elsayed, M.S.; Le-Khac, N.-A.; Dev, S.; Jurcut, A.D. DDoSNet: A deep-learning model for detecting network attacks. In Proceedings of the IEEE 21st International Symposium on “A World of Wireless, Mobile and Multimedia Networks” (WoWMoM), Cork, Ireland, 31 August–3 September 2020. [Google Scholar]
- Ahuja, N.; Singal, G.; Mukhopadhyay, D. DLSDN: Deep learning for DDOS attack detection in software defined networking. In Proceedings of the 11th International Conference on Cloud Computing, Data Science & Engineering (Confluence 2021), Noida, India, 28–29 January 2021. [Google Scholar]
- Dimolianis, M.; Pavlidis, A.; Maglaris, V. Signature-based traffic classification and mitigation for DDoS attacks using programmable network data planes. IEEE Access 2021, 9, 113061–113076. [Google Scholar] [CrossRef]
- Yu, S.; Zhang, J.; Liu, J.; Zhang, X.; Li, Y.; Xu, T. A cooperative DDoS attack detection scheme based on entropy and ensemble learning in SDN. Wirel. Commun. Netw. 2021, 90, 90. [Google Scholar] [CrossRef]
- Dehkordi, A.; Soltanaghaei, M.; Boroujeni, F. A hybrid mechanism to detect DDoS attacks in software defined networks. Majlesi J. Electr. Eng. 2021, 15, 1–8. [Google Scholar] [CrossRef]
- Liu, Y.; Zhi, T.; Shen, M.; Wang, L.; Li, Y.; Wan, M. Software-defined DDoS detection with information entropy analysis and optimized deep learning. Future Gener. Comput. Syst. 2022, 129, 99–114. [Google Scholar] [CrossRef]
- Gadallah, W.G.; Ibrahim, H.M.; Omar, N.M. A deep learning technique to detect distributed denial of service attacks in software defined networks. Comput. Secur. 2024, 137, 103588. [Google Scholar] [CrossRef]
- Cao, J.; Xu, M.; Li, Q.; Sun, K.; Yang, Y.; Zheng, J. Disrupting SDN via the data plane: A low-rate flow table overflow attack. In Proceedings of the 13th International Conference on Security and Privacy in Communications Networks (SECURECOMM17), Niagara Falls, ON, Canada, 22–25 October 2017. [Google Scholar]
- Cao, J.; Xu, M.; Li, Q.; Sun, K.; Yang, Y. The LOFT attack: Overflowing SDN flow tables at a low rate. IEEE/ACM Trans. Netw. 2023, 31, 1416–1431. [Google Scholar] [CrossRef]
- Tang, D.; Yan, Y.; Gao, C.; Liang, W.; Jin, W. LtRFT: Mitigate the low-rate data plane DDoS attack with learning-to-rank enabled flow tables. IEEE Trans. Inf. Forensics Secur. 2023, 18, 3143–3157. [Google Scholar] [CrossRef]
- Tang, D.; Gao, C.; Liang, W.; Zhang, J.; Li, K. FTMaster: A detection and mitigation system of low-rate flow table overflow attacks via SDN. IEEE Trans. Netw. Serv. Manag. 2023, 20, 5073–5084. [Google Scholar] [CrossRef]
- Tang, D.; Zhang, D.; Qin, Z.; Yang, Q.; Xiao, S. SFTO-guard: Real time detection and mitigation system for slow-rate flow table overflow attacks. J. Netw. Comput. Appl. 2023, 213, 103597. [Google Scholar] [CrossRef]
- Tang, D.; Zheng, Z.; Li, K.; Yin, C.; Liang, W.; Zhang, J. FTOP: An efficient flow table overflow preventing system for switches in SDN. IEEE Trans. Netw. Sci. Eng. 2024, 11, 2524–2536. [Google Scholar] [CrossRef]
- Tang, D.; Zheng, Z.; Yin, C.; Xiong, B.; Qin, Z.; Yang, Q. FTODefender: An efficient flow table overflow attacks defending system in SDN. Expert Syst. Appl. 2024, 237, 12146. [Google Scholar] [CrossRef]
- Mudgal, A.; Verma, A.; Singh, M.; Sahoo, K.S.; Elmroth, E.; Bhuyan, M. FloRa: Flow table low-rate overflow reconnaissance and detection in SDN. IEEE Trans. Netw. Serv. Manag. 2024, 21, 6670–6683. [Google Scholar] [CrossRef]
- Zeng, Y.; Wang, Y.; Liu, Y. Research on detection and mitigation methods of adaptive flow table overflow attacks in software-defined networks. IEEE Access 2024, 12, 48830–48845. [Google Scholar] [CrossRef]
- Jain, L.; Venkanna, U.; Vollala, S. FTSheild: An intelligent framework for LOFT attack detection and mitigation with programmable data plane. Expert Syst. Appl. 2025, 265, 125865. [Google Scholar] [CrossRef]
- Riggio, R.; Marina, M.; Schulz-Zander, J.; Kuklinski, S.; Rasheed, T. Programming abstractions for software-defined wireless networks. IEEE Trans. Netw. Serv. Manag. 2015, 12, 146–162. [Google Scholar] [CrossRef]
- Celesova, B.; Val’ko, J.; Grezo, R.; Helebrandt, P. Enhancing security of SDN focusing on control plane and data plane. In Proceedings of the International Symposium on Digital Forensic and Security (ISDFS), Barcelos, Portugal, 10–12 June 2019. [Google Scholar]
- Ibrahim, O.; Bhaya, W. Intrusion detection system for cloud based software-defined networks. In Proceedings of the International Conference of Modern Applications on Information and Communication Technology (ICMAICT), Hilla, Iraq, 22–23 October 2020. [Google Scholar]
- Sebbar, A.; Cherqi, O.; Chougdali, K.; Boulmalf, M. Real time anomaly detection in SDN architecture using integrated SIEM and machine learning for enhancing network security. In Proceedings of the IEEE Global Communications Conference: Communications Software and Multimedia (GLOBECOM-IEEE 2023), Kuala Lumpur, Malaysia, 4–8 December 2023. [Google Scholar]
- Wang, P.; Ye, F.; Chen, X.; Qian, Y. Datanet: Deep learning based encrypted network traffic classification in SDN home gateway. IEEE Access 2018, 6, 55380–55391. [Google Scholar] [CrossRef]
- Malik, A.; Frein, R.d.; Al-Zeyadi, M.; Andreu-Perez, J. Intelligent SDN traffic classification using deep learning: Deep-SDN. In Proceedings of the 2nd International Conference on Computer Communication and the Internet (ICCCI 2020), Nagoya, Japan, 26–29 June 2020. [Google Scholar]
- Serag, R.H.; Abdalzaher, M.S.; Elsayed, H.A.E.A.; Sobh, M.; Krichen, M.; Salim, M.M. Machine-learning-based traffic classification in software-defined networks. Electronics 2024, 13, 1108. [Google Scholar] [CrossRef]
- Koerner, M.; Kao, O. MAC based dynamic VLAN tagging with OpenFlow for WLAN access networks. In Proceedings of the International Workshop on Applications of Software-Defined Networking in Cloud Computing (SDNCC), Montreal, QC, Canada, 15–18 August 2016. [Google Scholar]
- Zhong, Y.; Li, Z.; Liao, L. A privacy-preserving caching scheme for device-to-device communications. Secur. Commun. Netw. 2021, 2021, 6696149. [Google Scholar] [CrossRef]
- Wang, T.; Chen, H. A lightweight SDN fingerprint attack defense mechanism based on probabilistic scrambling and controller dynamic scheduling strategies. Secur. Commun. Netw. 2021, 1, 6688489. [Google Scholar] [CrossRef]
- Ye, R.; Ouyang, Y.; Che, X. Security and attack prevention in software-defined network. In Proceedings of the International Conference on Telecommunications and Power Electronics (TELEPE 2024), Frankfurt, Germany, 29–31 May 2024. [Google Scholar]
- Alkhamisi, A.; Katib, I.; Buhari, S.M. Federated learning-based security attack detection for multi-controller software-defined networks. Algorithms 2024, 17, 290. [Google Scholar] [CrossRef]
- Hyder, M.F.; Ismail, M.A. Securing control and data planes from reconnaissance attacks using distributed shadow controllers, reactive and proactive approaches. IEEE Access 2021, 9, 21881–21894. [Google Scholar] [CrossRef]
- Lam, J.H.; Lee, S.; Lee, H.-J.; Oktian, Y.E. Securing distributed SDN with IBC. In Proceedings of the 2015 Seventh International Conference on Ubiquitous and Future Networks (ICUFN), Sapporo, Japan, 7–10 July 2015. [Google Scholar]
- Adhikari, T.; Kule, M.; Khan, A.K. An ECDH and AES based encryption approach for prevention of MiTM in SDN southbound communication interface. In Proceedings of the 13th International Conference on Computing Communication and Networking Technologies (ICCCNT 2022), Kharagpur, India, 3–5 October 2022. [Google Scholar]
- Buzura, S.; Lehene, M.; Iancu, B.; Dadarlat, V. An extendable software architecture for mitigating ARP spoofing-based attacks in SDN data plane layer. Electronics 2022, 11, 1965. [Google Scholar] [CrossRef]
- Guo, X.; Wang, C.; Cao, L.; Jiang, Y.; Yan, Y. A novel security mechanism for software defined network based on blockchain. Comput. Sci. Inf. Syst. 2022, 19, 523–545. [Google Scholar] [CrossRef]
- Chi, P.-W.; Kuo, C.-T.; Guo, J.-W.; Lei, C.-L. How to detect a compromised SDN switch. In Proceedings of the 2015 1st IEEE Conference on Network Softwarization (NetSoft), London, UK, 13–17 April 2015. [Google Scholar]
- Chao, T.-W.; Ke, Y.-M.; Chen, B.-H.; Chen, J.-L.; Hsieh, C.J.; Lee, S.-C.; Hsiao, H.-C. Securing data planes in software-defined networks. In Proceedings of the IEEE Conference on Network Softwarization (NetSoft), Seoul, Republic of Korea, 6–10 June 2016. [Google Scholar]
- Zhou, H.; Wu, C.; Yang, C.; Wang, P.; Yang, Q.; Lu, Z.; Cheng, Z. SDN-RDCD: A real-time and reliable method for detecting compromised SDN devices. IEEE/ACM Trans. Netw. 2018, 26, 2048–2061. [Google Scholar] [CrossRef]
- Pattanaik, A.; Gupta, A.; Kanavalli, A. Early detection and diminution of DDoS attack instigated by compromised switches on the controller in software defined networks. In Proceedings of the IEEE International Conference on Distributed Computing, VLSI, Electrical Circuits and Robotics (DISCOVER), Manipal, India, 11–12 August 2019. [Google Scholar]
- Sanjeetha, R.; Srivastava, S.; Pokharna, R.; Shafiq, S.; Kanavalli, A. Mitigation of DDoS attack instigated by compromised switches on SDN controller by analyzing the flow rule request traffic. Int. J. Eng. Technol. 2018, 7, 46–49. [Google Scholar] [CrossRef][Green Version]
- Shaghaghi, A.; Kaafar, M.A.; Jha, S. WedgeTail: An intrusion prevention system for the data plane of software defined networks. In Proceedings of the Asia Conference on Computer and Communications Security (ASIA CCS17), Abu Dhabi, United Arab Emirates, 2 April 2017. [Google Scholar][Green Version]
- Dinh, P.T.; Lee, T.; Canh, T.N.; Dang, S.P.; Noh, S.C.; Park, M. Abnormal SDN switches detection based on chaotic analysis of network traffic. In Proceedings of the 25th Asia-Pacific Conference on Communications (APCC), Ho Chi Minh City, Vietnam, 6–8 November 2019. [Google Scholar][Green Version]
- Dinh, P.T.; Park, M. ECSD: Enhanced compromised switch deteciton in an SDN-based cloud through multivariate time-series analysis. IEEE Access 2020, 8, 119346–119360. [Google Scholar] [CrossRef]
- Hessam, G.; Saba, G.; Alkhayat, M.I. A new approach for detecting violation of data plane integrity in software defined networks. J. Comput. Secur. 2021, 29, 341–358. [Google Scholar] [CrossRef]
- Reddy, B.A.; Sahoo, K.S.; Bhuyan, M. Securing P4-SDN data plane against flow table modification attack. In Proceedings of the IEEE Symposium on Network Operations and Management, Seoul, Republic of Korea, 6–10 May 2024. [Google Scholar]
- Deng, S.; Gao, X.; Lu, Z.; Gao, X. Packet injection attack and its defense in software-defined networks. IEEE Trans. Inf. Forensics Secur. 2018, 13, 695–705. [Google Scholar] [CrossRef]
- Alshra’a, A.S.; Seitz, J. Using INSPECTOR device to stop packet injection attack in SDN. IEEE Commun. Lett. 2019, 33, 1174–1177. [Google Scholar] [CrossRef]
- Antikainen, M.; Aura, T.; Särelä, M. Spook in your network: Attacking an SDN with a compromised OpenFlow switch. In Proceedings of the Nordic Conference on Secure IT Systems (NordSec 2014), Tromsø, Norway, 15–17 October 2014. [Google Scholar]
- Zhou, Y.; Chen, K.; ZHang, J.; Leng, J.; Tang, Y. Exploiting the vulnerability of flow table overflow in software-defined network: Attack model, evaluation and defense. Secur. Commun. Netw. 2018, 2018, 4760632. [Google Scholar] [CrossRef]
- Sathya, R.; Thangarajan, R. Efficient anomaly detection and mitigation in software defined networking environment. In Proceedings of the 2nd International Conference on Electronics and Communication Systems (ICECS), Coimbatore, India, 26–27 February 2015. [Google Scholar]
- Pang, C.; Jiang, Y.; Li, Q. FADE: Detecting forwarding anomaly in software-defined networks. In Proceedings of the IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 22–27 May 2016. [Google Scholar]
- Li, Q.; Liu, Y.; Liu, Z.; Zhang, P.; Pang, C. Efficient forwarding anomaly detection in software-defined networks. IEEE Trans. Parallel Distrib. Syst. 2021, 32, 2676–2690. [Google Scholar] [CrossRef]
- Aryan, R.; Yazidi, A.; Engelstad, P.E.; Kure, O. A general formalism for defining and detecting OpenFlow rule anomalies. In Proceedings of the IEEE 42nd Conference on Local Computer Networks (LCN), Singapore, 9–12 October 2017. [Google Scholar]
- Aryan, R.; Yazidi, A.; Engelstad, P.E. An incremental approach for swift OpenFlow anomaly detection. In Proceedings of the IEEE 43rd Conference on Local Computer Networks (LCN), Chicago, IL, USA, 1–4 October 2018. [Google Scholar]
- Zhang, P.; Xu, S.; Yang, Z.; Li, H.; Li, Q.; Wang, H.; Hu, C. FOCES: Detecting forwarding anomalies in software defined networks. In Proceedings of the IEEE International Conference on Distributed Computing Systems (ICDCS 2018), Vienna, Austria, 2–6 July 2018. [Google Scholar]
- Zhang, P.; Zhang, F.; Xu, S.; Yang, Z.; Li, H.; Li, Q.; Wang, H.; Shen, C.; Hu, C. Network-wide forwarding anomaly detection and localization in software-defined networks. IEEE/ACM Trans. Netw. 2021, 29, 332–345. [Google Scholar] [CrossRef]
- Li, Q.; Zou, X.; Huang, Q.; Zheng, J.; Lee, P.P.C. Dynamic packet forwarding verification in SDN. IEEE Trans. Dependable Secur. Comput. 2019, 16, 915–929. [Google Scholar] [CrossRef]
- Kausar, N.; Latif, Z.; Lee, C.; Iqbal, U. Towards Detection and Mitigation of Traffic Anomalies in SDN. In Proceedings of the International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Republic of Korea, 20–22 October 2021. [Google Scholar]
- Xi, S.; Bu, K.; Mao, W.; Zhang, X.; Ren, K.; Ren, X. RuleOut forwarding anomalies for SDN. IEEE/ACM Trans. Netw. 2022, 31, 395–407. [Google Scholar] [CrossRef]
- Zhibin, Z.; Chang, C.; Zhu, X. A software-defined networking packet forwarding verification mechanism based on programmable data plane. J. Electron. Inf. Technol. 2020, 42, 1110–1117. [Google Scholar]
- Zhang, W.; Jing, S.; Guo, L.; Zhao, C. P4-DVPF: Dynamic Verification of Packets Forwarding Based on P4 for SDN. In Proceedings of the International Conference on Intelligent Computing and Next Generation Networks (ICNGN), Singapore, 12–14 December 2023. [Google Scholar]
- Dey, S.K.; Rahman, M.M. Flow based anomaly detection in software defined networking: A deep learning approach with feature selection method. In Proceedings of the 4th International Conference on Electrical Engineering and Information & Communication Technology (iCEEiCT), Dhaka, Bangladesh, 13–15 September 2018. [Google Scholar]
- Sridharan, V.; Gurusamy, M.; Leon-Garcia, A. Anomalous rule detection using machine learning in software defined networks. In Proceedings of the IEEE Conference on Network Function Virtualization and Software Defined Networks (NFV-SDN), Dallas, TX, USA, 12–14 November 2019. [Google Scholar]
- Lai, Y.-C.; Zhou, K.-Z.; Lin, S.-R.; Lo, N.-W. F1ow-based anomaly detection using multilayer perceptron in software defined networks. In Proceedings of the 42nd International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 20–24 May 2019. [Google Scholar]
- Phan, T.V.; Nguyen, T.G.; Dao, N.-N.; Huong, T.T.; Thanh, N.H.; Bauschert, T. DeepGuard: Efficient anomaly detection in SDN with fine-grained traffic flow monitoring. IEEE Trans. Netw. Serv. Manag. 2020, 17, 1349–1362. [Google Scholar] [CrossRef]
- Khurshid, A.; Zhou, W.; Caesar, M.; Godfrey, B. VeriFlow: Verifying network-wide invariants in real time. In Proceedings of the 1st ACM International Workshop on Hot Topics in Software Defined Networks (HotSDN12), Helsinki, Finland, 13 August 2012. [Google Scholar]
- Dhawan, M.; Poddar, R.; Mahajan, K.; Mann, V. SPHINX: Detecting security attacks in software-defined networks. In Proceedings of the Network and Distributed System Security Symposium, San Diego, CA, USA, 8–11 February 2015. [Google Scholar]
- Chaudhary, R.; Kumar, N. LOADS: Load optimisation and anomaly detection scheme for software-defined networks. IEEE Trans. Veh. Technol. 2019, 68, 12329–12344. [Google Scholar] [CrossRef]
- Flauzac, O.; González, C.; Hachani, A.; Nolot, F. SDN based architecture for IoT and improvement of the security. In Proceedings of the 29th International Conference on Advanced Information Networking and Applications Workshops, Gwangju, Republic of Korea, 24–27 March 2015. [Google Scholar]
- Qin, Q.; Poularakis, K.; Tassiulas, L. A learning approach with programmable data plane towards IoT security. In Proceedings of the IEEE 40th International Conference on Distributed Computing Systems (ICDCS 2020), Singapore, 29 November–1 December 2020; pp. 410–420. [Google Scholar]
- Guo, X.; Lin, H.; Li, Z.; Peng, M. Deep-reinforcement-learning based QoS-aware secure routing for SDN-IoT. IEEE Internet Things 2020, 7, 6242–6251. [Google Scholar] [CrossRef]
- Cui, L.; Yu, F.R.; Yan, Q. When big data meets software-defined networking: SDN for big data and big data for SDN. IEEE Netw. 2016, 30, 58–65. [Google Scholar] [CrossRef]
- Yao, J.; Han, Z.; Sohail, M.; Wang, L. A robust security architecture for SDN-based 5G networks. Future Internet 2019, 11, 85. [Google Scholar] [CrossRef]
- Han, B.; Yang, X.; Sun, Z.; Huang, J.; Su, J. OverWatch: A cross-plane DDoS attack defense framework with collaborative intelligence in SDN. Secur. Commun. Netw. 2018, 2018, 9649643. [Google Scholar] [CrossRef]
- Yang, X.; Wang, D.; Tang, W.; Feng, W.; Zhu, C. IPsec cryptographic algorithm invocation considering performance and security for SDN southbound interface communication. IEEE Access 2020, 8, 181782–181795. [Google Scholar] [CrossRef]
- Salman, F.; Jedidi, A. Trust-aware security system for dynamic southbound communication in software defined network. In Proceedings of the International Conference on Innovation and Intelligence for Informatics, Computing, and Technologies (3ICT), Sakheer, Bahrain, 20–21 November 2022. [Google Scholar]
- Sebbar, A.; Zkik, K.; Baddi, Y.; Boulmalf, M.; Kettani, M.D.E.-C.E. MitM detection and defense mechanism CBNA-RF based on machine learning for large-scale SDN context. J. Ambient Intell. Humaniz. Comput. 2022, 11, 5875–5894. [Google Scholar] [CrossRef]
- Silva, E.G.d.; Knob, L.A.D.; Wickboldt, J.A.; Gaspary, L.P.; Granville, L.Z.; Schaeffer-Filho, A. Capitalizing on SDN based SCADA systems: An anti-eavesdropping case-study. In Proceedings of the IFIP/IEEE International Symposium on Integrated Network Management (IM2015), Ottawa, ON, Canada, 11–15 May 2015. [Google Scholar]
- Mohan, P.; Gurusamy, M.; Lim, T. Dynamic attack-resilient routing in software defined networks. IEEE Trans. Netw. Serv. Manag. 2018, 15, 1146–1160. [Google Scholar] [CrossRef]
- Tapolcai, J.; Retvari, G.; Babarczi, P.; Berczi-Kovacs, E. Scalable and efficient multipath routing via redundant trees. IEEE J. Sel. Areas Commun. 2019, 37, 982–996. [Google Scholar] [CrossRef]
- Wang, Z.; Lu, Z.; Li, C. Research on deep reinforcement learning multi-path routing planning in SDN. In Proceedings of the 2nd International Conference on Electronic Engineering and Informatics, Lanzhou, China, 17–19 July 2020. [Google Scholar]
- Chiu, K.-C.; Liu, C.-C.; Chou, L.-D. Reinforcement learning-based service-oriented dynamic multipath routing in SDN. Wirel. Commun. Mob. Comput. 2022, 2022, 1330993. [Google Scholar] [CrossRef]
- Zhang, Y.; Qiu, L.; Xu, Y.; Wang, X.; Wang, S.; Paul, A.; Wu, Z. Multi path routing algorithm based on deep reinforcement learning for SDN. Appl. Sci. 2023, 13, 12520. [Google Scholar] [CrossRef]
- Sanchez, L.P.A.; Shen, Y.; Guo, M. MDQ: A QoS-congestion aware deep reinforcement learning approach for multi-path routing in SDN. J. Netw. Comput. Appl. 2025, 235, 104082. [Google Scholar] [CrossRef]
- Yin, S.; Huang, S.; Liu, H.; Guo, B.; Gao, T.; Li, W. Survivable multipath virtual network embedding against multiple failures for SDN/NFV. IEEE Access 2018, 6, 76909–76923. [Google Scholar] [CrossRef]
- Wang, Q.; Shou, G.; Liu, Y.; Hu, Y.; Guo, Z.; Chang, W. Implementation of multipath network virtualization with SDN and NFV. IEEE Access 2018, 6, 32460–32470. [Google Scholar] [CrossRef]
- Xiaolong, X.; Yun, C.; Liuyun, H.; Anup, K. MTSS: Multi-path traffic scheduling mechanism based on SDN. J. Syst. Eng. Electron. 2019, 30, 974–984. [Google Scholar] [CrossRef]
- Zhou, C.; Quan, W.; Gao, D.; Liu, Z.; Yu, C.; Liu, M.; Xu, Z. AMS: Adaptive Multipath Scheduling Mechanism against Eavesdropping Attacks with Programmable Data Planes. In Proceedings of the IEEE Advanced Information Technology, Electronic and Automation Control Conference (IAEAC), Chongqing, China, 12–14 March 2021. [Google Scholar]
- Qi, H.; Guo, Y.; Hou, D.; Xing, Z.; Ren, W.; Cong, L.; Di, X. SDN-based dynamic multi-path routing strategy for satellite networks. Future Gener. Comput. Syst. 2022, 133, 254–265. [Google Scholar] [CrossRef]
- Ma, H.; Wang, M.; Lv, H.; Liu, J.; Di, X.; Qi, H. A SDN improvement scheme for multi-path QUIC transmission in satellite networks. Comput. Intell. 2024, 40, e12650. [Google Scholar] [CrossRef]
- Cheng, Y.; Jia, X. NAMP: Network-aware multipathing in software-defined data center networks. IEEE/ACM Trans. Netw. 2020, 28, 846–859. [Google Scholar] [CrossRef]
- Amaral, P.; Pinto, P.; Bernardo, L. Achieving correct hop-by-hop forwarding on multiple policy-based routing paths. IEEE Trans. Netw. Sci. Eng. 2020, 7, 1226–1238. [Google Scholar] [CrossRef]
- Betge-Brezetz, S.; Kamga, G.-B.; Joutei, A.; Maalmi, O. Control of sensitive traffic in the cloud based on OpenFlow. In Proceedings of the IEEE Third International Conference on Cloud Networking (CloudNet), Luxembourg, Luxembourg, 8–10 October 2014. [Google Scholar]
- Betgé-Brezetz, S.; Kamga, G.-B.; Tazi, M. Trust support for SDN controllers and virtualized network applications. In Proceedings of the IEEE Conference on Network Softwarization (NetSoft), London, UK, 13–17 April 2015. [Google Scholar]
- Betge-Brezetz, S.; Kamga, G.-B.; Balla, M.; Criton, T.; Jebalia, H. SDN-based trusted path in a multi-domain network. In Proceedings of the IEEE International Conference on Cloud Engineering Workshop, Berlin, Germany, 4–8 April 2016. [Google Scholar]
- Ermis, O.; Bahtiyar, S.; Caglayan, M.; Bulbul, N.; Alagoz, F. Trust Enhanced Security for Routing in SDN. In Proceedings of the 2022 1st International Conference on 6G Networking (6GNet), Paris, France, 6–8 July 2022. [Google Scholar]
- Kalkan, K. SUTSEC: SDN utilized trust based secure clustering in IoT. Comput. Netw. 2020, 178, 107328. [Google Scholar] [CrossRef]
- Raschella, A.; Eiza, M.H.; Mackay, M.; Shi, Q.; Banton, M. A trust-based cooperative system for efficient Wi-Fi radio access networks. IEEE Access 2023, 11, 136136–136149. [Google Scholar] [CrossRef]
- Quinn, T.; Shah, S.D.A.; Bouhafs, F.; den Hartog, F. Towards trust-based routing for data plane security in heterogeneous Software-Defined Wireless Networks. In Proceedings of the IEEE Conference on Network Softwarization (NetSoft), Saint Louis, MO, USA, 24–28 June 2024. [Google Scholar]
- Kreutz, D.; Ramos, F.M.V.; Veríssimo, P. Towards secure and dependable software-defined networks. In Proceedings of the Second ACM SIGCOMM Workshop on Hot Topics in Software Defined Networking (HotSDN ’13), Hong Kong, China, 16 August 2013. [Google Scholar]
- Darabseh, A.; Al-Ayyoub, M.; Jararweh, Y.; Benkhelifa, E.; Vouk, M.; Rindos, A. SDSecurity: A software defined security experimental framework. In Proceedings of the Workshop on Cloud Computing Systems, Networks, and Applications (CCSNA) (IEEE ICC 2015), London, UK, 8–12 June 2015. [Google Scholar]
- Chowdhary, A.; Huang, D.; Alshamrani, A.; Kang, M.; Kim, A.; Velazquez, A. TRUFL: Distributed trust management framework in SDN. In Proceedings of the IEEE International Conference on Communications (ICC), Seoul, Republic of Korea, 20–24 May 2019. [Google Scholar]
- Tan, S.; Li, X.; Dong, Q. A trust management system for securing data plane of ad-hoc networks. IEEE Trans. Veh. Technol. 2016, 65, 7579–7592. [Google Scholar] [CrossRef]
- Mao, M.; Yi, P.; Hu, T.; Zhang, Z.; Lu, X.; Lei, J. Hierarchical hybrid trust management scheme in SDN-enabled VANETs. Mob. Inf. Syst. 2021, 2021, 7611619. [Google Scholar] [CrossRef]
- Yan, Z.; Zhang, P.; Vasilakos, A.V. A security and trust framework for virtualized networks and software-defined networking. Secur. Commun. Netw. 2016, 9, 3059–3069. [Google Scholar] [CrossRef]
- Karmakar, K.K.; Varadharajan, V.; Hitchens, M.; Tupakula, U.; Sariputra, P. A trust-aware OpenFlow switching framework for software defined networks (SDN). Comput. Netw. 2023, 237, 110109. [Google Scholar] [CrossRef]
- Wang, L.; Ma, H.; Jiang, Y.; Tang, Y.; Zu, S.; Hu, T. A data plane security model of segmented routing based on SDP trust enhancement architecture. Sci Rep 2022, 12, 8762. [Google Scholar] [CrossRef]
- Ashraf, U.; Al-Naeem, M.; Bhutta, M.N.M.; Yuen, C. ZFort: A scalable zero-trust approach for trust management and traffic engineering in SDN based IoTs. Internet Things 2024, 28, 101419. [Google Scholar] [CrossRef]
- Yao, G.; Bi, J.; Xiao, P. Source address validation solution with OpenFlow/NOX architecture. In Proceedings of the 19th IEEE International Conference on Network Protocols, Vancouver, BC, Canada, 17 October 2011. [Google Scholar]
- Liu, J.; Zhang, H.; Guo, Z. A defense mechanism of random routing mutation in SDN. IEICE Trans. Inf. Syst. 2017, 100, 1046–1054. [Google Scholar] [CrossRef]
- Wang, M.; Liu, J.; Mao, J.; Cheng, H.; Chen, J.; Qi, C. RouteGuardian: Constructing secure routing paths in software-defined networking. Tsinghua Sci. Technol. 2017, 22, 400–412. [Google Scholar] [CrossRef]
- Albu-Salih, A.T.; Mohammed, S.J.; Seno, S.A.H. Dynamic routing method over hybrid SDN for flying ad hoc networks. Baghdad Sci. J. 2018, 15, 361–368. [Google Scholar] [CrossRef]
- Xu, X.; Hu, H.; Liu, Y.; Tan, J.; Zhang, H.; Song, H. Moving target defense of routing randomization with deep reinforcement learning against eavesdropping attack. Digit. Commun. Netw. 2022, 8, 373–387. [Google Scholar] [CrossRef]
- Cascone, C.; Sanvito, D.; Pollini, L.; Capone, A.; Sanso, B. Fast failure detection and recovery in SDN with stateful data plane. Int. J. Netw. Manag. 2017, 27, e1957. [Google Scholar] [CrossRef]
- Li, Z.; Hu, Y.; Wu, J.; Lu, J. P4Resilience: Scalable resilience for multi-failure recovery in SDN with programmable data plane. Comput. Netw. 2022, 208, 108896. [Google Scholar] [CrossRef]
- Li, L.; Li, K.; Meng, X.; Wang, Y.; Wang, X. Dynamic weight routing and optical-code algorithm based on SDN. Heliyon 2023, 9, e12407. [Google Scholar] [CrossRef]
- Santana, P.; Moura, J. A Bayesian Multi-Armed Bandit algorithm for dynamic end-to-end routing in SDN-based networks with piecewise-stationary rewards. Algorithms 2023, 16, 233. [Google Scholar] [CrossRef]
- Becherer, M.; Hussain, O.K.; Zhang, Y.; den Hartog, F.; Chang, E. On trust recommendations in the social Internet of Things—A survey. ACM Comput. Surv. 2024, 56, 1–35. [Google Scholar] [CrossRef]
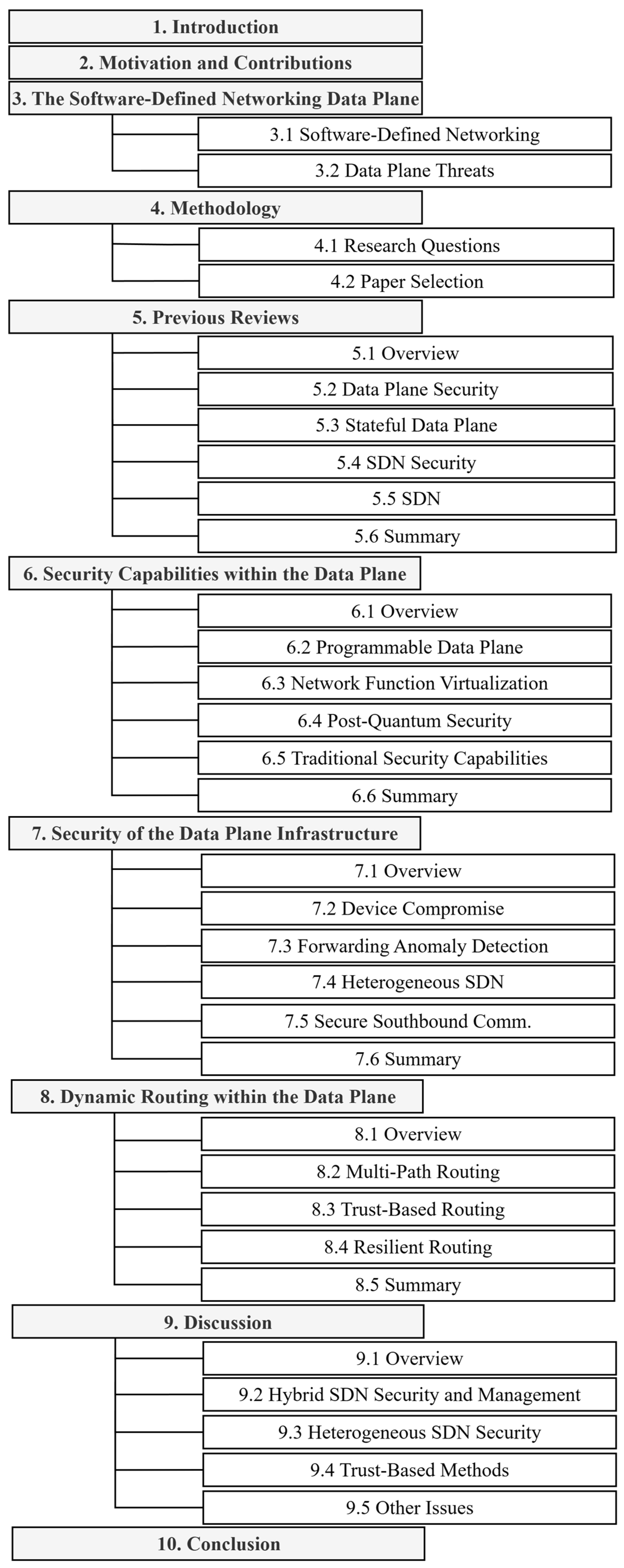
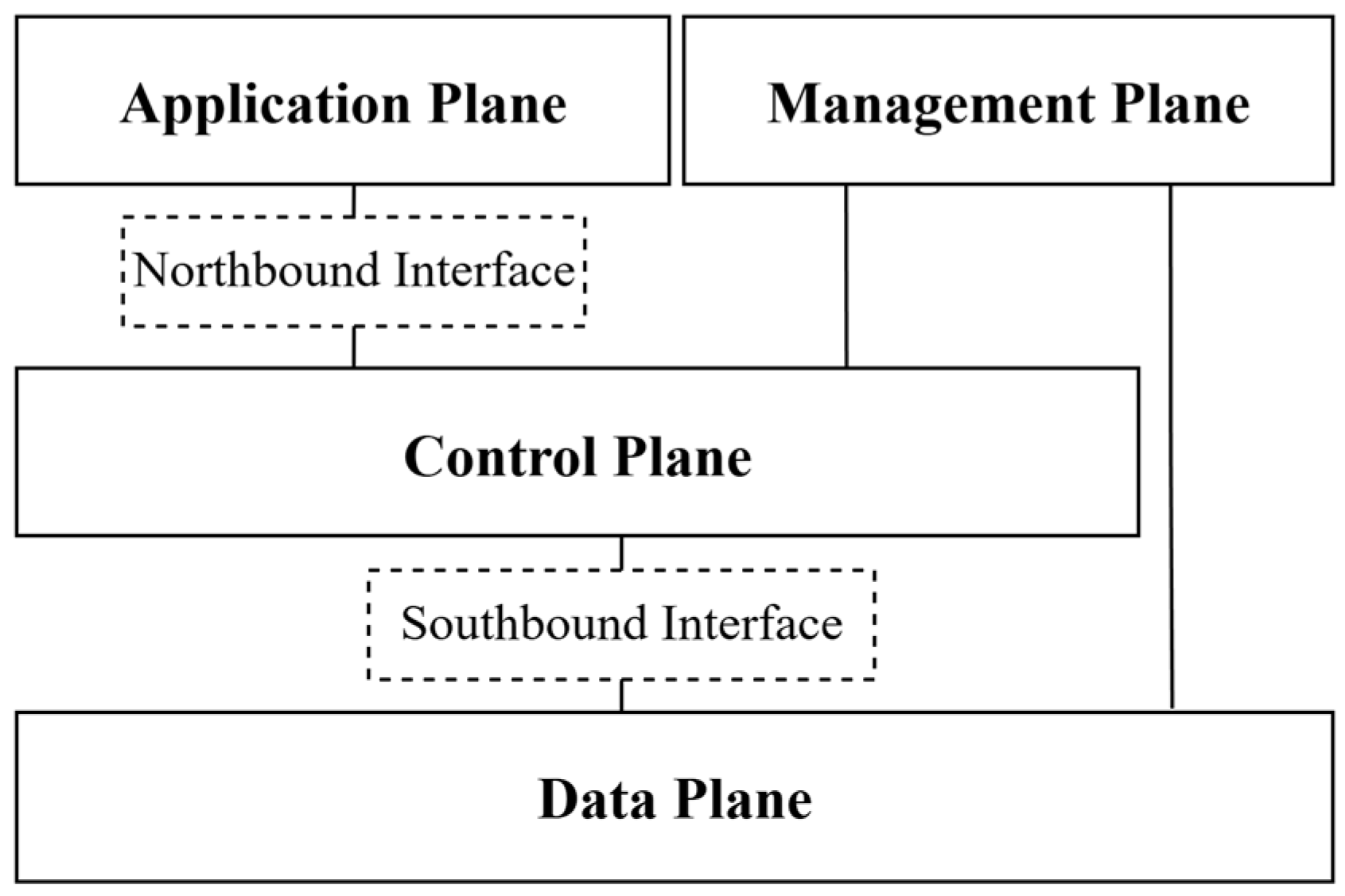
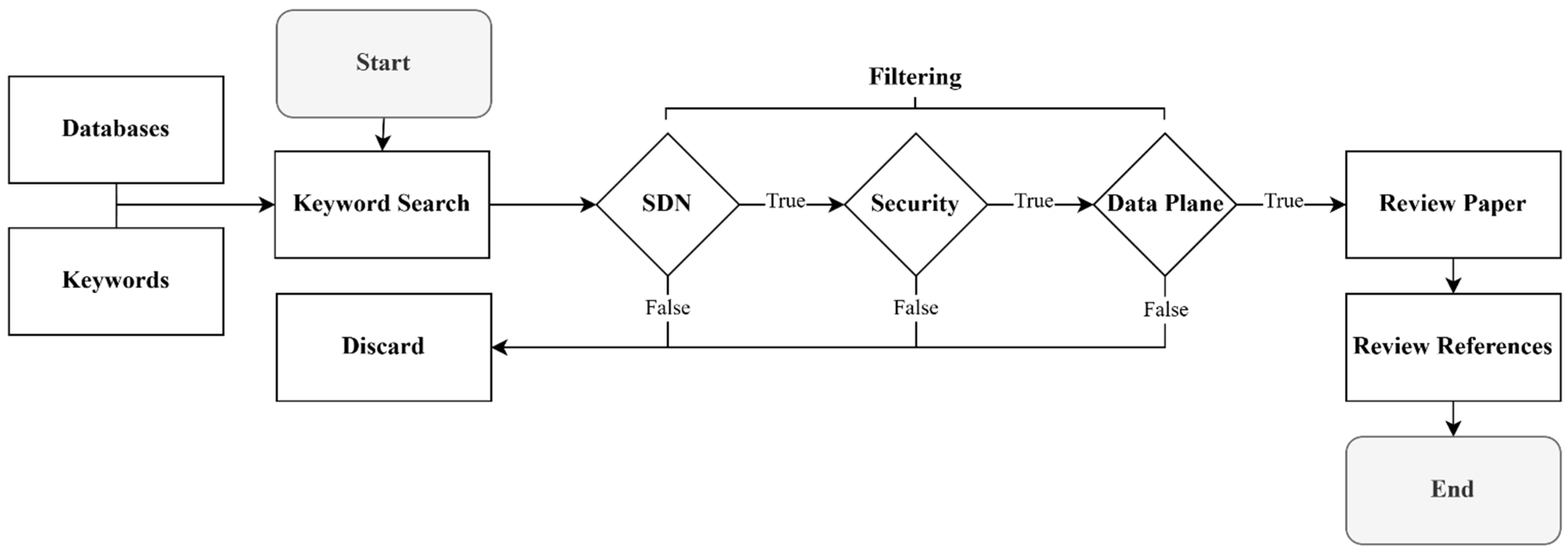


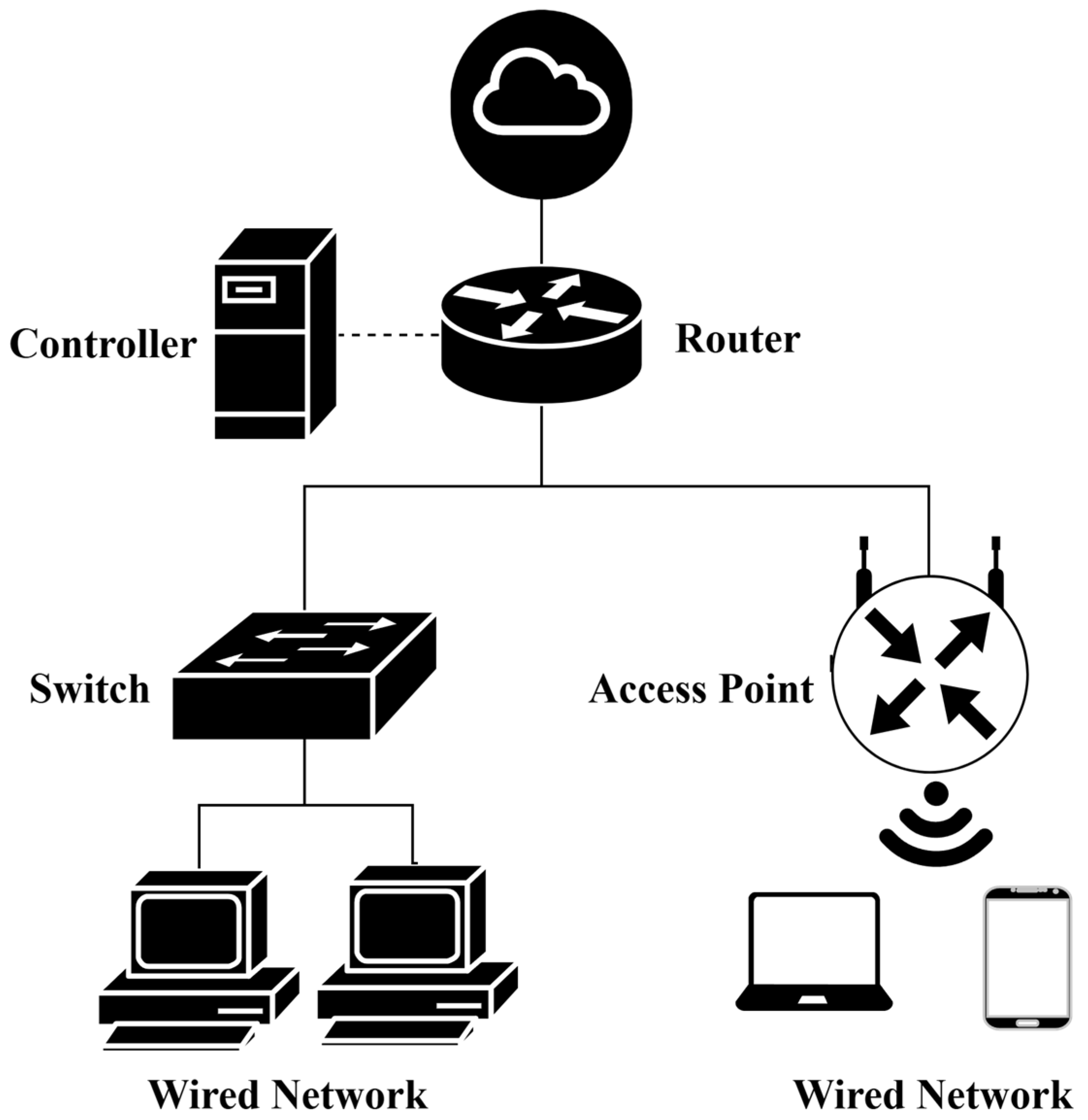




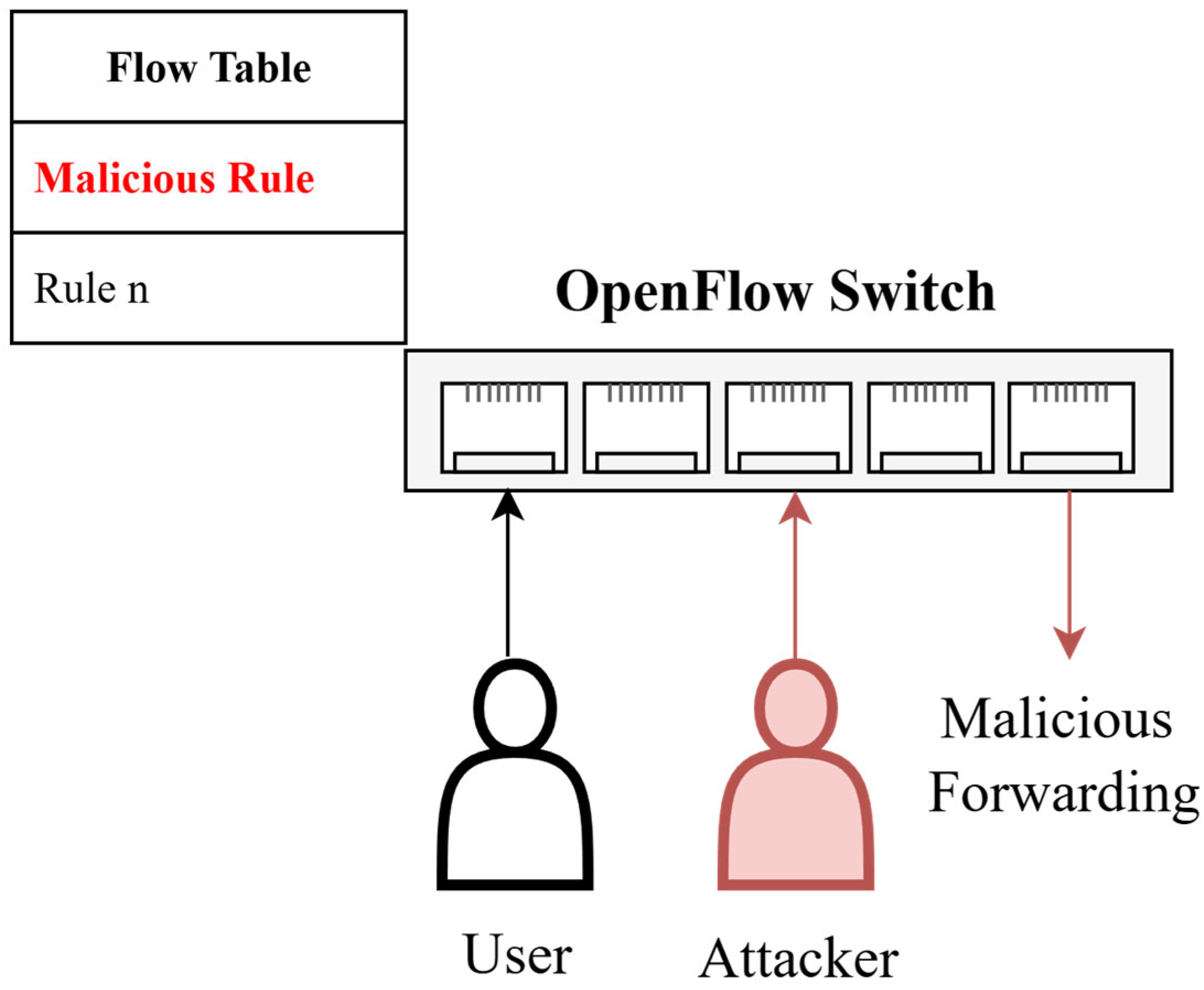
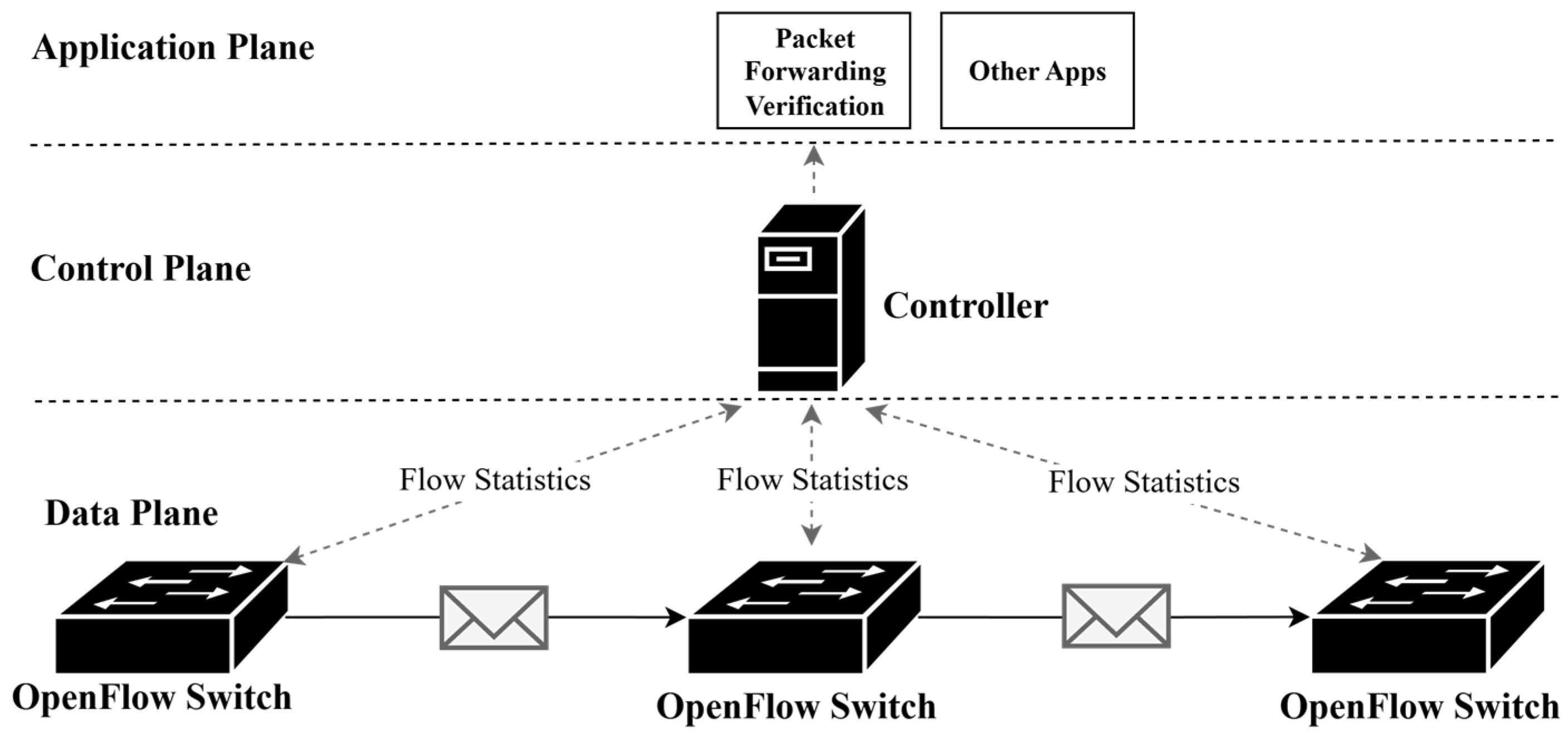
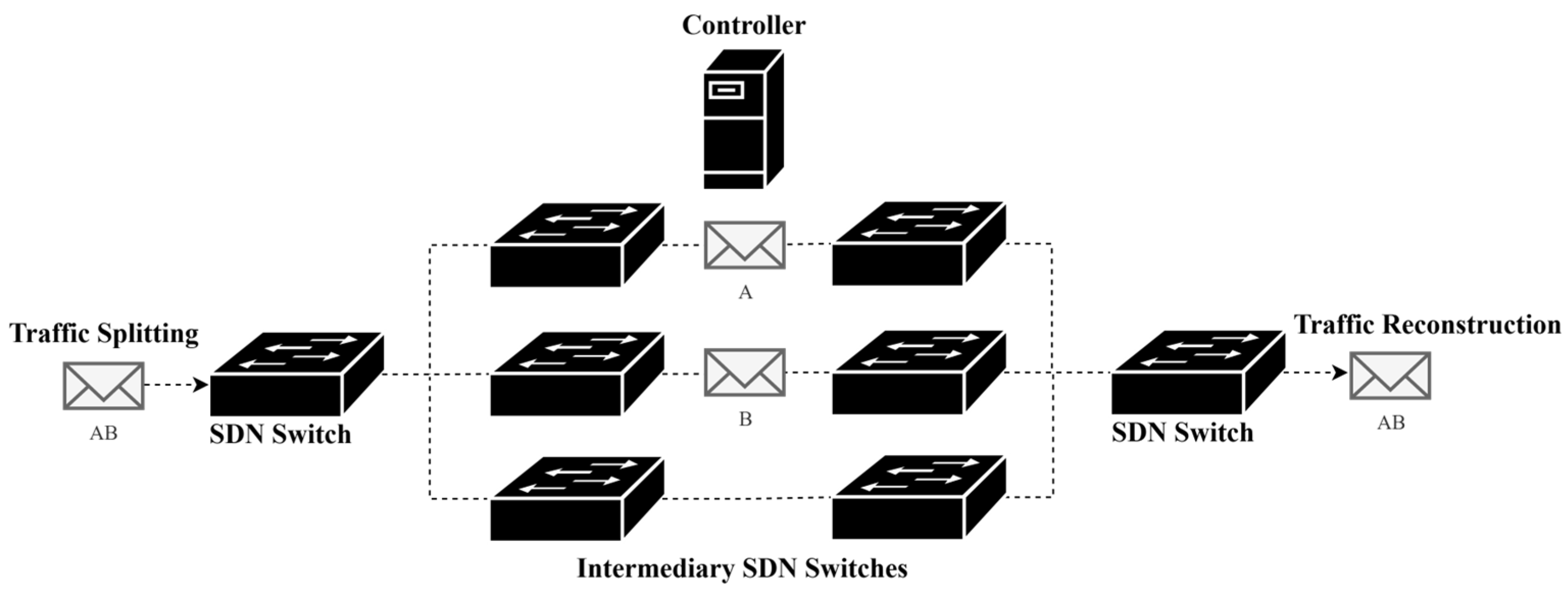
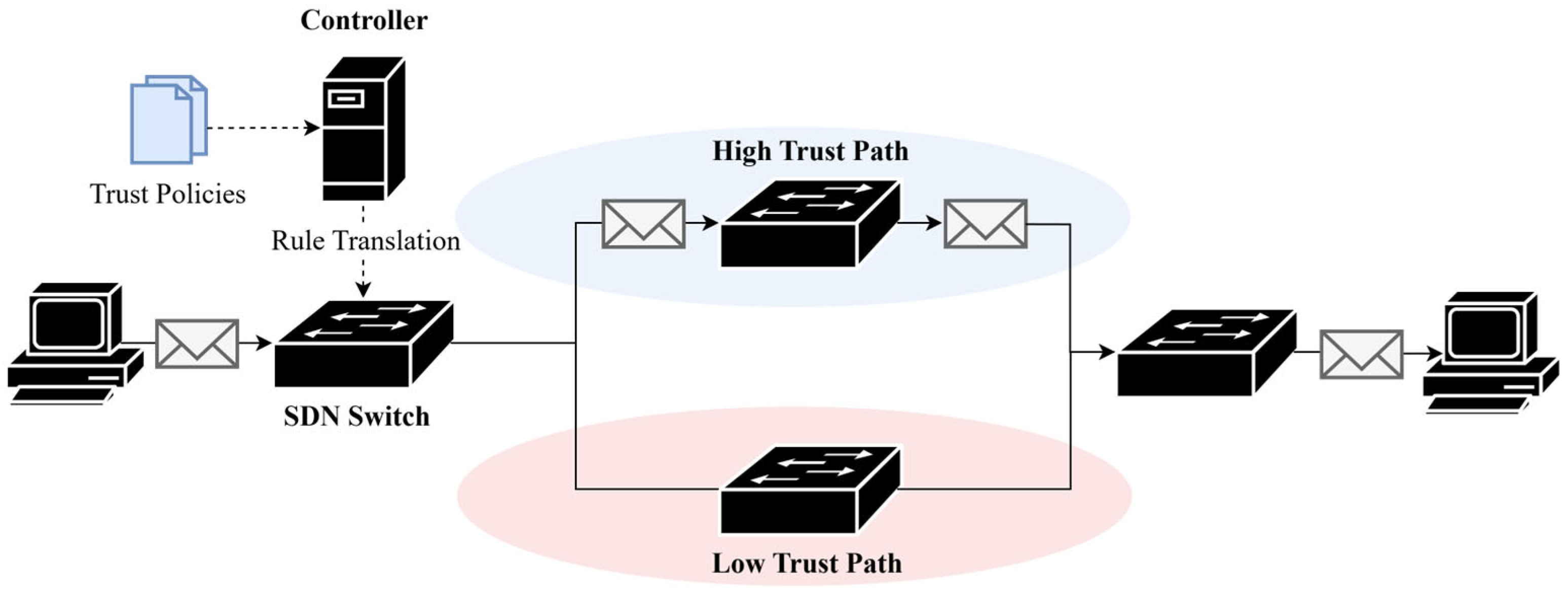
| Plane Component | Threats | Mitigations |
|---|---|---|
| Southbound Interface | Side-channel vulnerabilities | Monitoring and logging |
| Data spill (data leak) | Monitoring and logging; data loss prevention; traffic filtering (firewall, intrusion detection, and prevention) | |
| Malicious software (malware) | Monitoring and logging | |
| Eavesdropping | Traffic encryption; secure routing | |
| Man-in-the-middle | Traffic encryption; secure routing | |
| Replay attacks | Session and token management; monitoring and logging; traffic filtering (firewall, intrusion detection, and prevention) | |
| Switch Software | Side-channel vulnerabilities | Monitoring and logging |
| Data spill (data leak) | Secure programming; patching; adherence to standards; monitoring and logging | |
| Malicious software (malware) | Monitoring and logging | |
| Switch Firmware | Side-channel vulnerabilities | Monitoring and logging |
| Malicious software (malware) | Forwarding anomaly detection; exclusionary routing for malicious or compromised nodes | |
| Switches | Malicious infrastructure | Forwarding anomaly detection; exclusionary routing for malicious or compromised nodes; authentication; network access control |
| Side-channel vulnerabilities | Monitoring and logging | |
| Poisoned forwarding rules | Forwarding rule auditing; forwarding anomaly detection | |
| Denial-of-service/Distributed denial-of-service | Exclusionary routing for malicious or compromised nodes; traffic filtering (firewall, intrusion detection, and prevention) | |
| Communications Links | Man-in-the-middle | Traffic encryption; forwarding anomaly detection; secure routing |
| Eavesdropping | Traffic encryption; secure routing | |
| Replay attacks | Session and token management; monitoring and logging; traffic filtering (firewall, intrusion detection, and prevention) | |
| Endpoints | Malicious infrastructure | Forwarding anomaly detection; exclusionary routing for malicious or compromised nodes; authentication; network access control |
| Denial-of-service/Distributed denial-of-service | Exclusionary routing for malicious or compromised nodes; traffic filtering (firewall, intrusion detection, and prevention) |
| Reference | Year | Topic | Data Plane Security |
|---|---|---|---|
| [8] | 2025 | Data plane security | ● |
| [9] | 2017 | Stateful data plane security | ◉ |
| [10] | 2020 | Stateful data plane security | ◉ |
| [11] | 2021 | Stateful data plane | ◉ |
| [12] | 2021 | P4 security | ◉ |
| [13] | 2022 | P4 security | ◉ |
| [14] | 2023 | P4 | ◉ |
| [15] | 2019 | Programmable data planes | ◉ |
| [16] | 2021 | Programmable data planes | ◉ |
| [17] | 2021 | P4 switches | ◉ |
| [18] | 2023 | P4 applications | ○ |
| [19,20,21] | 2015 | SDN security | ◉ |
| [22,23] | 2016 | SDN security | ◉ |
| [24,25] | 2019 | SDN security | ◉ |
| [26,27] | 2020 | SDN security | ◉ |
| [28] | 2021 | SDN security | ◉ |
| [29] | 2021 | SDN security | ◉ |
| [6] | 2022 | SDN security | ◉ |
| [30] | 2022 | SDN security | ◉ |
| [31] | 2024 | SDN security | ◉ |
| [32] | 2023 | SDN security | ◉ |
| [33] | 2024 | SDN security | ◉ |
| [34] | 2023 | SDN security and privacy | ◉ |
| [35] | 2017 | SDN security architecture | ◉ |
| [36] | 2018 | SDN security architecture | ◉ |
| [37] | 2020 | SDN security architecture | ◉ |
| [38] | 2020 | SDN security architecture | ◉ |
| [39] | 2013 | SDN | ◉ |
| [40,41] | 2014 | SDN | ◉ |
| [42,43] | 2015 | SDN | ◉ |
| [44] | 2016 | SDN | ◉ |
| [45] | 2020 | SDN for resilient networking | ○ |
| [46] | 2022 | SDN for resilient networking | ○ |
| [47] | 2017 | Heterogeneous SDN | ◉ |
| [48] | 2020 | Heterogeneous SDN | ○ |
| [49] | 2019 | ML applications in SDN | ○ |
| [50] | 2019 | ML applications in SDN | ◉ |
| [51] | 2023 | ML applications in SDN | ◉ |
| [52] | 2025 | AI, ML and blockchain in SDN | ○ |
| [53] | 2024 | AI for programmable data planes | ◉ |
| [54] | 2015 | SDN-NFV | ◉ |
| [55,56] | 2019 | SDN-NFV | ◉ |
| [57] | 2020 | MTD | ◉ |
| [58] | 2015 | Programmable networks | ◉ |
| [59] | 2022 | Denial-of-service attacks | ◉ |
| [60] | 2023 | In-band control for SDN | ◉ |
| Identifier | Summary | References |
|---|---|---|
| RSTR-1 | P4 security applications have been subject to significant investigation. | [12,13,14,15,16,17,18,53] |
| RSTR-2 | Cross-plane security for SDN has been subject to significant investigation. | [19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,61] |
| RWKN-1 | No comprehensive review exists for SDN data plane security research. | [8] |
| RWKN-2 | Security of the P4 architecture is underinvestigated. | [9,10] |
| RWKN-3 | Heterogeneous SDN is underinvestigated. | [26,47,48] |
| Reference | Year | Implementation | Application |
|---|---|---|---|
| [4] | 2014 | P4 | Novel language and compiler |
| [62] | 2014 | FAST | Novel architecture |
| [63] | 2014 | OpenState (OpenFlow) | Novel architecture |
| [64] | 2017 | SDPA (OpenFlow) | Novel architecture |
| [65,66,67,68,69,70,71,72] | 2020 | P4 | DoS mitigation |
| [73,74] | 2021 | P4 | DoS mitigation |
| [75,76] | 2019 | P4 | DoS mitigation |
| [77] | 2021 | P4 | DoS mitigation |
| [78] | 2022 | P4 | DoS mitigation |
| [79] | 2017 | P4 | Heavy-hitter detection |
| [80] | 2018 | P4 | Telephony DoS mitigation |
| [81] | 2019 | P4 | Telephony DoS mitigation |
| [82] | 2019 | P4 | ML-based DoS mitigation |
| [83] | 2021 | P4 | ML-based DoS mitigation |
| [84,85] | 2020 | P4 | ML-based DoS mitigation |
| [86] | 2023 | P4 | ML-based DoS mitigation |
| [87] | 2018 | OpenFlow, P4 | Intrusion detection |
| [88] | 2019 | P4 | Intrusion detection |
| [89] | 2021 | P4 | Intrusion detection |
| [90] | 2023 | P4 | Intrusion detection |
| [91] | 2024 | P4 | Intrusion detection |
| [92] | 2021 | P4 | Anomaly detection |
| [93] | 2020 | P4 | ML-based intrusion detection |
| [94] | 2021 | P4 | ML-based intrusion detection |
| [95,96] | 2024 | P4 | ML-based intrusion detection |
| [97,98] | 2025 | P4 | ML-based intrusion detection |
| [99] | 2024 | OpenFlow | ML-based network monitoring |
| [100] | 2024 | P4 | ML-based traffic classification |
| [101] | 2017 | P4 | Deep packet inspection |
| [102] | 2020 | P4 | Deep packet inspection |
| [103] | 2022 | P4 | Deep packet inspection |
| [104] | 2023 | P4 | Deep packet inspection |
| [105] | 2016 | P4 | Firewall |
| [106] | 2018 | Novel (CoFilter) | Packet filtering |
| [107] | 2018 | P4 | Firewall |
| [108] | 2019 | P4 | 5G firewall |
| [109] | 2017 | OpenFlow, P4 | Anti-spoofing |
| [110,111] | 2020 | P4 | Anti-spoofing |
| [112] | 2019 | P4 | Anti-spoofing |
| [113] | 2019 | P4 | Anti-eavesdropping |
| [114] | 2019 | OpenFlow, P4 | Anti-eavesdropping |
| [115,116] | 2020 | P4 | Anti-eavesdropping |
| [117] | 2021 | P4 | Anti-eavesdropping |
| [118] | 2018 | P4 | Topology obfuscation |
| [119,120] | 2019 | P4 | Network anonymity |
| [121] | 2019 | P4 | Data plane authentication |
| [122] | 2021 | P4 | Data plane edge authentication |
| [123] | 2020 | P4 | Data plane authentication |
| [124] | 2020 | OpenFlow, P4 | Encryption |
| [125] | 2020 | P4 | Encryption |
| [126] | 2021 | P4 | Encryption |
| [127] | 2020 | P4 | MACsec |
| [128] | 2020 | P4 | IPsec |
| [129] | 2019 | P4 | Cryptographic hashing |
| [130,131,132,133] | 2019 | P4 | Network defense |
| [134] | 2023 | P4 | Network defense |
| [135] | 2022 | P4 | Network defense |
| [136,137,138] | 2023 | P4 | Network defense |
| [139] | 2019 | P4 | Edge network defense |
| [140] | 2018 | OpenFlow, P4 | Security framework |
| [141] | 2018 | P4 | Application layer security |
| [142] | 2020 | P4 | BYOD |
| [143] | 2020 | P4 | P4 performance |
| [144] | 2020 | P4 | Covert channel defense |
| [145] | 2020 | P4 | Explicit congestion notification |
| [146] | 2021 | P4 | ML-based network defense |
| [147] | 2022 | P4 | OS fingerprinting |
| [148] | 2020 | P4 | Blockchain |
| [149] | 2021 | OpenFlow, P4 | Distributed network functions |
| Reference | Year | Implementation | Application |
|---|---|---|---|
| [151] | 2013 | OpenFlow | Cost-based placement |
| [152] | 2014 | OpenFlow | Secure routing |
| [153] | 2015 | OpenFlow | Intrusion detection |
| [154] | 2017 | OpenFlow | Adaptive routing |
| [155] | 2017 | Novel (OpenSDWN) | SDWN |
| [156] | 2018 | Novel (OpenFunction) | Middleboxes |
| [157] | 2019 | OpenFlow | Data plane functions |
| [158] | 2023 | OpenFlow | Data plane functions |
| [159] | 2015 | Novel (VNGuard) | Firewall management |
| [160] | 2020 | OpenFlow | Network deception |
| [161] | 2021 | OpenFlow, P4 | Programmable edge networking in 5G |
| [162] | 2023 | OpenFlow | Blockchain in 5G |
| Reference | Year | Implementation | Application |
|---|---|---|---|
| [176] | 2016 | OpenFlow | Firewall |
| [177] | 2020 | OpenFlow | Firewall |
| [178] | 2017 | OpenFlow | Deep packet inspection |
| [179] | 2018 | OpenFlow | Deep packet inspection |
| [180] | 2021 | OpenFlow | Deep packet inspection |
| [181] | 2020 | OpenFlow | Deep packet inspection |
| [182] | 2016 | OpenFlow | DoS mitigation |
| [183,184] | 2017 | OpenFlow | DoS mitigation |
| [185] | 2017 | OpenFlow | Entropy-based DoS mitigation |
| [186] | 2020 | OpenFlow | Entropy-based DoS mitigation |
| [187] | 2021 | OpenFlow | Entropy-based DoS mitigation |
| [188] | 2020 | OpenFlow | Entropy-based DoS mitigation |
| [189] | 2019 | OpenFlow | DoS mitigation |
| [190] | 2018 | OpenFlow | DoS mitigation |
| [191] | 2019 | OpenFlow | DoS mitigation |
| [192,193] | 2020 | OpenFlow | DoS mitigation |
| [194] | 2023 | OpenFlow | DoS mitigation |
| [195] | 2016 | OpenFlow | ML-based DoS mitigation |
| [196] | 2017 | OpenFlow | ML-based DoS mitigation |
| [197] | 2018 | OpenFlow | ML-based DoS mitigation |
| [198,199] | 2019 | OpenFlow | ML-based DoS mitigation |
| [200] | 2018 | OpenFlow | ML-based DoS mitigation |
| [201,202] | 2020 | OpenFlow | ML-based DoS mitigation |
| [203,204] | 2021 | OpenFlow | ML-based DoS mitigation |
| [205,206] | 2021 | OpenFlow | ML-based DoS mitigation |
| [207] | 2022 | OpenFlow | ML-based DoS mitigation |
| [208] | 2024 | OpenFlow | ML-based DoS mitigation |
| [209] | 2018 | OpenFlow | Low-rate DoS mitigation |
| [210,211,212,213] | 2023 | OpenFlow | Low-rate DoS mitigation |
| [214,215,216,217] | 2024 | OpenFlow | Low-rate DoS mitigation |
| [218] | 2025 | OpenFlow | Low-rate DoS mitigation |
| [219] | 2015 | Novel (EmPOWER) | Wireless monitoring |
| [220] | 2019 | OpenFlow | Intrusion detection |
| [221] | 2020 | OpenFlow | Intrusion detection |
| [222] | 2023 | OpenFlow | Intrusion detection |
| [223] | 2018 | OpenFlow | Traffic classification |
| [224] | 2020 | OpenFlow | Traffic classification |
| [203] | 2021 | OpenFlow | Traffic classification |
| [225] | 2024 | OpenFlow | Traffic classification |
| [226] | 2016 | OpenFlow | Network access control |
| [227] | 2021 | OpenFlow | Device-to-device |
| [228] | 2021 | OpenFlow | Network defense |
| [229,230] | 2024 | OpenFlow | Network defense |
| [231] | 2021 | OpenFlow | Moving target defense |
| [232] | 2016 | OpenFlow | Encryption |
| [233] | 2022 | OpenFlow | Encryption |
| [234] | 2022 | OpenFlow | Anti-spoofing |
| [235] | 2022 | OpenFlow | Blockchain |
| Identifier | Summary | References |
|---|---|---|
| RSTR-3 | A range of security applications have been implemented using a programmable data plane. | [12,13,14,15,16,17,18,65,66,67,68,69,70,71,72,73,74,75,76,77,78,79,80,81,82,83,84,85,86,87,88,89,90,91,92,93,94,95,96,97,98,99,100,101,102,103,104,105,106,107,108,109,110,111,112,113,114,115,116,117,118,119,120,121,122,123,124,125,126,127,128,129,130,131,132,133,134,135,136,137,138,139,140,141,142,143,144,145,146,147,148,149] |
| RSTR-4 | Programmable data planes may support mitigation of DoS and DDoS attacks at line rate. | [69] |
| RWKN-4 | There is a disproportionate focus on availability in SDN security. | [65,66,67,68,69,70,71,72,73,74,75,76,77,78,79,80,81,82,83,84,85,86,182,183,184,185,186,187,188,189,190,191,192,193,194,195,196,197,198,199,200,201,202,203,204,205,206,207,208,209,210,211,212,213,214,215,216,217,218] |
| RWKN-5 | There is disproportionate focus on DoS and DDoS attacks on SDN. | [182,183,184,185,186,187,188,189,190,191,192,193,194,195,196,197,198,199,200,201,202,203,204,205,206,207,208,209,210,211,212,213,214,215,216,217,218] |
| RWKN-6 | Weaknesses of the decentralized model in programmable data planes are underinvestigated. | Nil |
| RWKN-7 | Hybrid SDN is underinvestigated. | [75,87,97,109,123] |
| RWKN-8 | In-network (in-band) control is underinvestigated. | [60] |
| RWKN-9 | Novel attacks on P4 switches are underinvestigated. | Nil |
| RWKN-10 | Software security for SDN and programmable data planes is underinvestigated. | Nil |
| Reference | Year | Implementation | Application |
|---|---|---|---|
| [236] | 2015 | OpenFlow | Compromise detection |
| [237] | 2016 | OpenFlow | Compromise detection |
| [238,239,240,241] | 2017 | OpenFlow | Compromise detection |
| [242] | 2019 | OpenFlow | Compromise detection |
| [243] | 2020 | OpenFlow | Compromise detection |
| [244] | 2021 | OpenFlow | Compromise detection |
| [245] | 2024 | P4 | Compromise detection |
| [246] | 2018 | OpenFlow | Anti-packet injection |
| [247] | 2019 | OpenFlow | Anti-packet injection |
| [248] | 2014 | OpenFlow | Novel attacks |
| [249] | 2018 | OpenFlow | Novel attacks |
| Reference | Year | Implementation | Application |
|---|---|---|---|
| [250] | 2015 | OpenFlow | Forwarding anomaly detection |
| [251] | 2016 | OpenFlow | Forwarding anomaly detection |
| [252] | 2021 | OpenFlow | Forwarding anomaly detection |
| [253] | 2017 | OpenFlow | Forwarding anomaly detection |
| [254,255] | 2018 | OpenFlow | Forwarding anomaly detection |
| [256] | 2021 | OpenFlow | Forwarding anomaly detection |
| [257] | 2019 | OpenFlow | Forwarding anomaly detection |
| [258] | 2021 | OpenFlow | Forwarding anomaly detection |
| [259] | 2022 | OpenFlow | Forwarding anomaly detection |
| [260] | 2020 | OpenFlow, P4 | Forwarding anomaly detection |
| [261] | 2023 | P4 | Forwarding anomaly detection |
| [262] | 2018 | OpenFlow | ML-based forwarding anomaly detection |
| [263,264] | 2019 | OpenFlow | ML-based forwarding anomaly detection |
| [265] | 2020 | OpenFlow | ML-based forwarding anomaly detection |
| [266] | 2012 | OpenFlow | Network invariant detection |
| [267] | 2015 | OpenFlow | Network defense |
| [268] | 2019 | OpenFlow | Load optimization and anomaly detection |
| Reference | Year | Implementation | Application |
|---|---|---|---|
| [269] | 2015 | OpenFlow | IoT and ad hoc networks |
| [270,271] | 2020 | OpenFlow | IoT |
| [272] | 2016 | OpenFlow | Big Data |
| [273] | 2019 | OpenFlow | 5G |
| Reference | Year | Implementation | Application |
|---|---|---|---|
| [274] | 2018 | OpenFlow | Cross-plane defense |
| [275] | 2020 | OpenFlow | IPsec for SDN security |
| [276] | 2022 | OpenFlow | Trust-aware security |
| [277] | 2022 | OpenFlow | MITM mitigation |
| Identifier | Summary | References |
|---|---|---|
| RSTR-5 | Device compromise in SDN has been the subject of significant investigation. | [236,237,238,239,240,241,242,243,244,245,246,247,248,249] |
| RSTR-6 | Forwarding anomaly detection in SDN has been the subject of significant investigation. | [250,251,252,253,254,255,256,257,258,259,260,261,262,263,264,265,266,267,268] |
| RWKN-11 | Security of the SBI is underinvestigated. | [274,275,276,277] |
| RWKN-12 | There are no widely accepted security frameworks for the SDN data plane. | Nil |
| RWKN-13 | There is a lack of SDN mechanisms for data plane monitoring and observability. | Nil |
| RWKN-14 | SDN-based MTD is underinvestigated. | [31,57,231] |
| RWKN-15 | Trust management for SDN data plane devices is underinvestigated. | [276] |
| Reference | Year | Implementation | Application |
|---|---|---|---|
| [278] | 2015 | OpenFlow | Multi-path routing |
| [279] | 2018 | OpenFlow | Multi-path routing |
| [280] | 2019 | OpenFlow | Multi-path routing |
| [281] | 2020 | OpenFlow | ML-based multi-path routing |
| [282] | 2022 | OpenFlow | ML-based multi-path routing |
| [283] | 2023 | OpenFlow | ML-based multi-path routing |
| [284] | 2025 | OpenFlow | ML-based multi-path routing |
| [285,286] | 2018 | OpenFlow | Multi-path routing using SDN-NFV |
| [287] | 2019 | OpenFlow | Multi-path scheduling |
| [288] | 2021 | P4 | Multi-path scheduling |
| [289] | 2022 | OpenFlow | Multi-path for satellite networks |
| [290] | 2024 | OpenFlow | Multi-path for satellite networks |
| [291] | 2020 | OpenFlow | Multi-path routing for datacenters |
| [292] | 2020 | OpenFlow | Multi-path hop-by-hop forwarding |
| Reference | Year | Implementation | Application |
|---|---|---|---|
| [293] | 2014 | OpenFlow | Trust-based routing for cloud |
| [294] | 2015 | OpenFlow | Multi-controller trust-based routing |
| [295] | 2016 | OpenFlow | Trust-based routing for multi-domain networks |
| [296] | 2022 | OpenFlow | Trust-based routing |
| [297] | 2020 | OpenFlow | Trust-based clustering in IoT |
| [298] | 2023 | OpenFlow | Trust-based cooperative system for Wi-Fi |
| [299] | 2024 | OpenFlow | Trust-based routing for heterogeneous networks |
| [300] | 2013 | Nil | Trust management |
| [301] | 2015 | OpenFlow | Security framework |
| [302] | 2019 | OpenFlow | Trust management |
| [303] | 2016 | OpenFlow | Trust management for heterogeneous networks |
| [304] | 2021 | OpenFlow | Trust management for VANETs |
| [305] | 2016 | OpenFlow | Trust for virtualized and software-defined networks |
| [306] | 2023 | OpenFlow | Trust-aware switching framework |
| [307] | 2022 | OpenFlow | Segment routing |
| [308] | 2024 | OpenFlow | Zero-trust-based trust and traffic engineering |
| Reference | Year | Implementation | Application |
|---|---|---|---|
| [309] | 2011 | OpenFlow | Source address validation |
| [310] | 2017 | OpenFlow | Random route mutation |
| [311] | 2017 | OpenFlow | Capability-based routing |
| [312] | 2018 | OpenFlow | Dynamic routing for VANETs |
| [313] | 2022 | OpenFlow | ML-based moving target defense |
| [314] | 2017 | OpenFlow | Fast failure recovery |
| [315] | 2022 | P4 | Fast failure recovery |
| [316] | 2023 | OpenFlow | Optical transport networking |
| [317] | 2023 | OpenFlow | ML-based routing optimization |
| Identifier | Summary | References |
|---|---|---|
| RSTR-7 | Dynamic routing in SDN, including multi-path routing, has been the subject of significant investigation. | [278,279,280,281,282,283,284,285,286,287,288,289,290,291,292,309,310,311,312,313,314,315,316,317] |
| RWKN-16 | Trust-based routing is underinvestigated. | [293,294,295,296,297,298,299,301,302,303,304] |
| RWKN-17 | Dynamic routing in heterogeneous SDN is underinvestigated. | [26,47,48,299,303] |
| RWKN-18 | Capability-based routing is underinvestigated. | Nil |
| RWKN-19 | Time-sensitive routing is underinvestigated. | Nil |
| Identifier | Research Strengths |
|---|---|
| RSTR-1 | P4 security applications have been subject to significant investigation. |
| RSTR-2 | Cross-plane security for SDN has been subject to significant investigation. |
| RSTR-3 | A range of security applications have been implemented using a programmable data plane. |
| RSTR-4 | Programmable data planes may support mitigation of DoS and DDoS attacks at line rate. |
| RSTR-5 | Device compromise in SDN has been the subject of significant investigation. |
| RSTR-6 | Forwarding anomaly detection in SDN has been the subject of significant investigation. |
| RSTR-7 | Dynamic routing in SDN, including multi-path routing, has been the subject of significant investigation. |
| Identifier | Research Weaknesses |
|---|---|
| RWKN-1 | No comprehensive review exists for SDN data plane security research. |
| RWKN-2 | Security of the P4 architecture is underinvestigated. |
| RWKN-3 | Heterogeneous SDN is underinvestigated. |
| RWKN-4 | There is a disproportionate focus on availability in SDN security. |
| RWKN-5 | There is disproportionate focus on DoS and DDoS attacks on SDN. |
| RWKN-6 | Weaknesses of the decentralized (control) model in programmable data planes are underinvestigated. |
| RWKN-7 | Hybrid SDN is underinvestigated. |
| RWKN-8 | In-network (in-band) control is underinvestigated. |
| RWKN-9 | Novel attacks on P4 switches are underinvestigated. |
| RWKN-10 | Software security for SDN and programmable data planes is underinvestigated. |
| RWKN-11 | Security of the SBI is underinvestigated. |
| RWKN-12 | There are no widely accepted security frameworks for the SDN data plane. |
| RWKN-13 | There is a lack of SDN mechanisms for data plane monitoring and observability. |
| RWKN-14 | SDN-based MTD is underinvestigated. |
| RWKN-15 | Trust management for SDN data plane devices is underinvestigated. |
| RWKN-16 | Trust-based routing is underinvestigated. |
| RWKN-17 | Dynamic routing in heterogeneous SDN is underinvestigated. |
| RWKN-18 | Capability-based routing is underinvestigated. |
| RWKN-19 | Time-sensitive routing is underinvestigated. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Quinn, T.; Bouhafs, F.; den Hartog, F. Securing the SDN Data Plane in Emerging Technology Domains: A Review. Future Internet 2025, 17, 503. https://doi.org/10.3390/fi17110503
Quinn T, Bouhafs F, den Hartog F. Securing the SDN Data Plane in Emerging Technology Domains: A Review. Future Internet. 2025; 17(11):503. https://doi.org/10.3390/fi17110503
Chicago/Turabian StyleQuinn, Travis, Faycal Bouhafs, and Frank den Hartog. 2025. "Securing the SDN Data Plane in Emerging Technology Domains: A Review" Future Internet 17, no. 11: 503. https://doi.org/10.3390/fi17110503
APA StyleQuinn, T., Bouhafs, F., & den Hartog, F. (2025). Securing the SDN Data Plane in Emerging Technology Domains: A Review. Future Internet, 17(11), 503. https://doi.org/10.3390/fi17110503






