A Three-Party Evolutionary Game Model and Stability Analysis for Network Defense Strategy Selection
Abstract
1. Introduction
- We propose a novel theoretical framework that endogenizes the system administrator as a core decision-maker, moving beyond traditional bilateral models.
- We derive the replicator dynamics and employ Lyapunov stability theory to identify and analyze the Evolutionary Stable Strategies (ESSs) under various realistic conditions.
- We validate our theoretical findings through numerical simulations and translate the equilibrium results into actionable insights for cybersecurity policy and defense strategy selection.
2. Related Work
3. Methodology
3.1. Basic Concepts
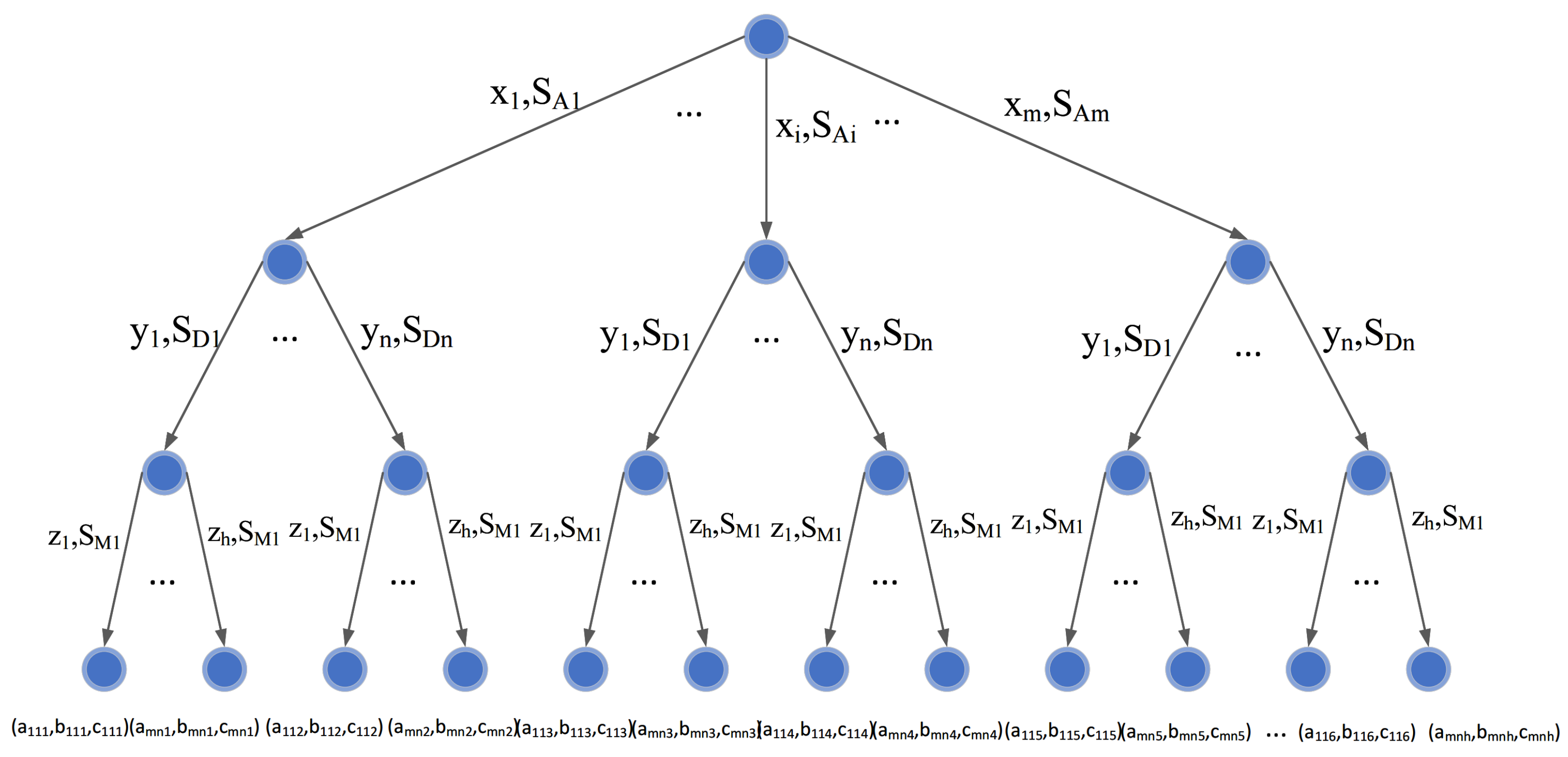
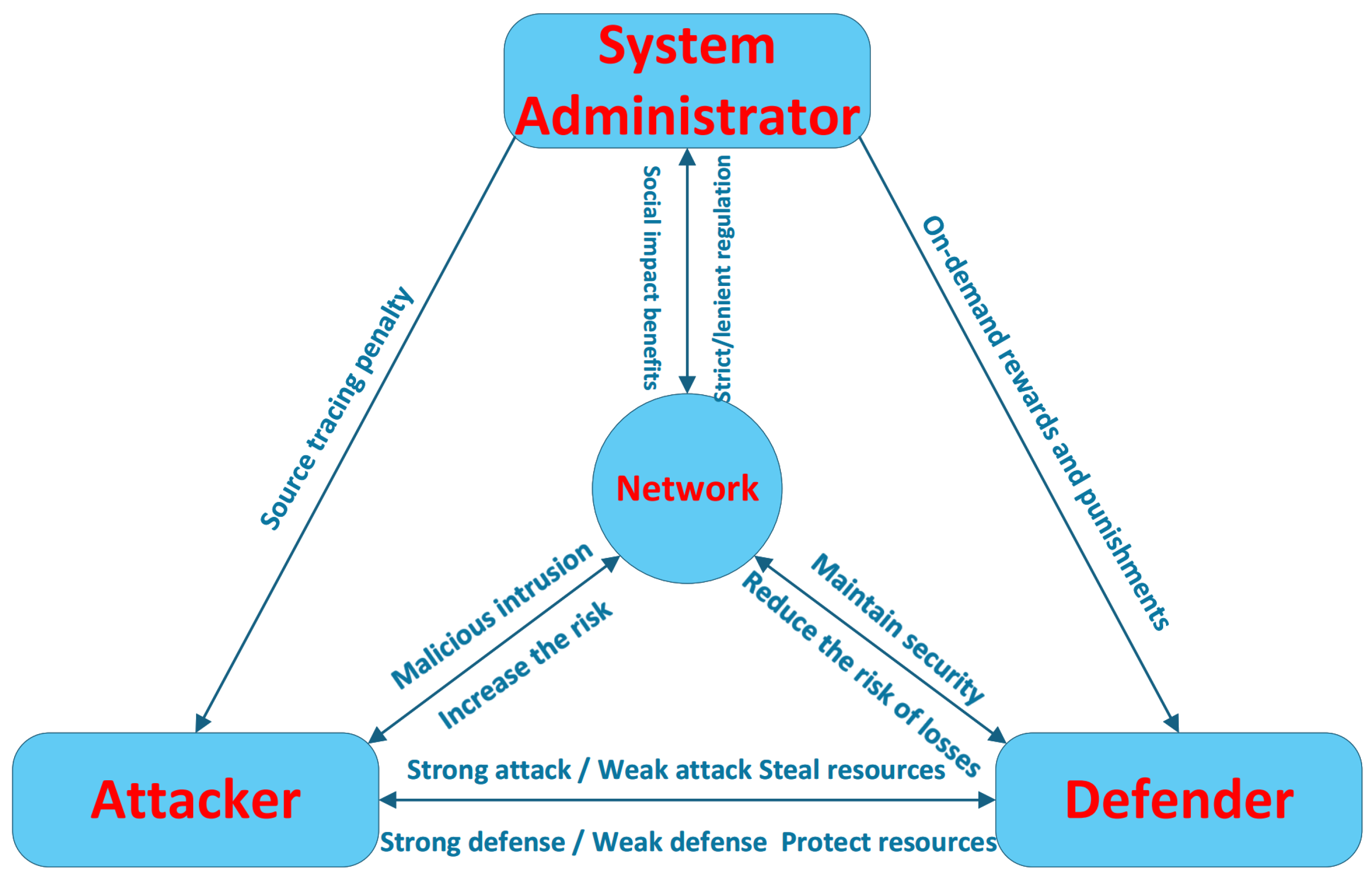
3.2. Tripartite Evolution Game Model
3.3. Analysis of Three-Way Evolution Path
3.3.1. Analysis of Network Attacker Strategy Evolution Path
3.3.2. Analysis of Evolution Path of Network Defender Strategy
3.3.3. Analysis of Evolution Path of System Manager Strategy
4. Model Solution and Analysis
4.1. Solving the Three-Party Evolutionary Game Model
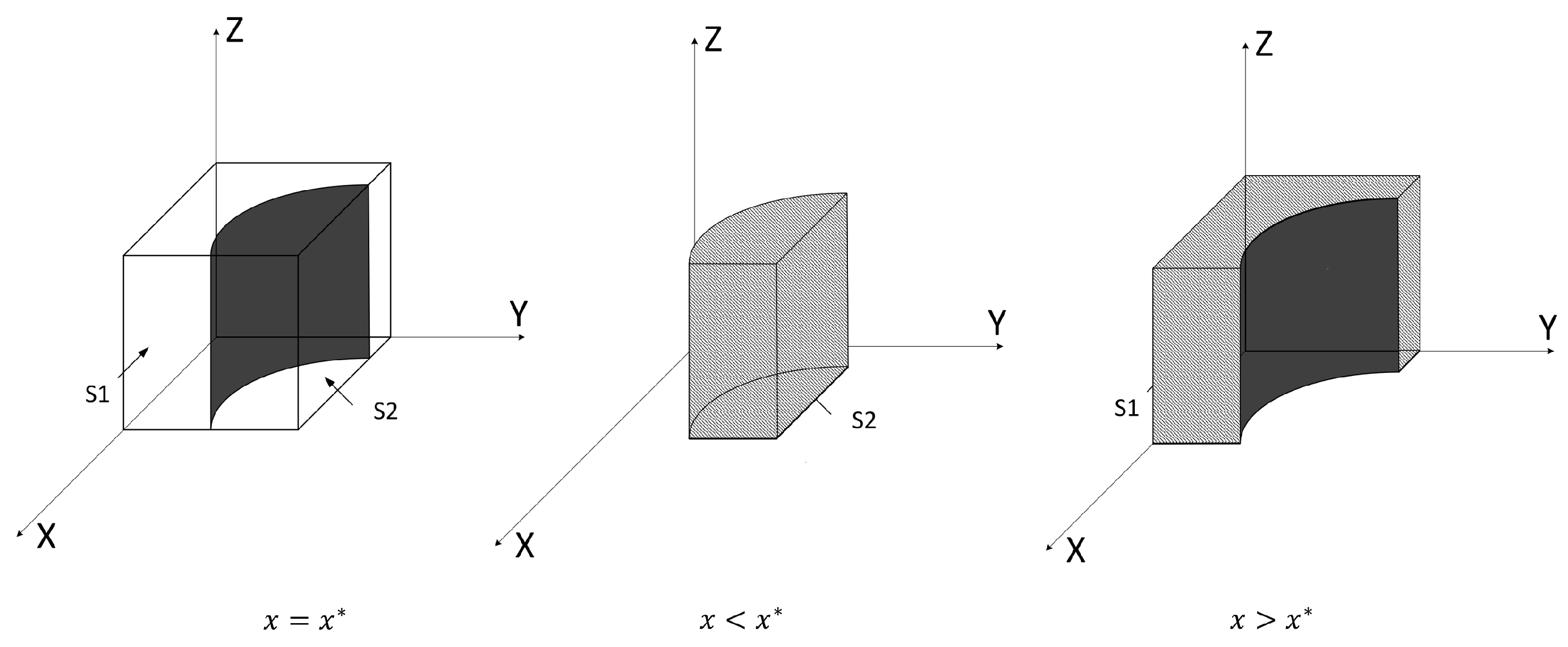
4.2. Stability Analysis of Balance Point
4.3. Optimal Strategy Selection Algorithm
| Algorithm 1. Algorithm for deriving the optimal network defense strategy | |
| 1 | Input the initial three-party evolutionary game model . |
| Construct the attacker’s strategy set and belief set | |
| 2 | , where is the probability that the attacker adopts attack strategy . |
| Construct the defender policy set and belief set | |
| 3 | , where is the probability that the defender adopts defense strategy . |
| Construct the system manager’s strategy set and belief set | |
| 4 | , where is the probability that the system manager adopts supervision strategy . |
| 5 | /* Calculate the attack and defense benefit matrices for each strategy combination */ |
| 6 | for i←1 to m do |
| 7 | for j←1 to n do |
| 8 | for k←1 to h do |
| 9 | |
| 10 | |
| 11 | |
| 12 | end for |
| 13 | end for |
| 14 | end for |
| 15 | /* Complex dynamic equations are constructed*/ |
| 16 | for i←1 to m do |
| 17 | |
| 18 | end for |
| 19 | for j←1 to n do |
| 20 | |
| 21 | end for |
| 22 | for k←1 to h do |
| 23 | |
| 24 | Solve |
| 25 | Output the optimal network defense strategy |
| 26 | end |
5. Results and Discussion
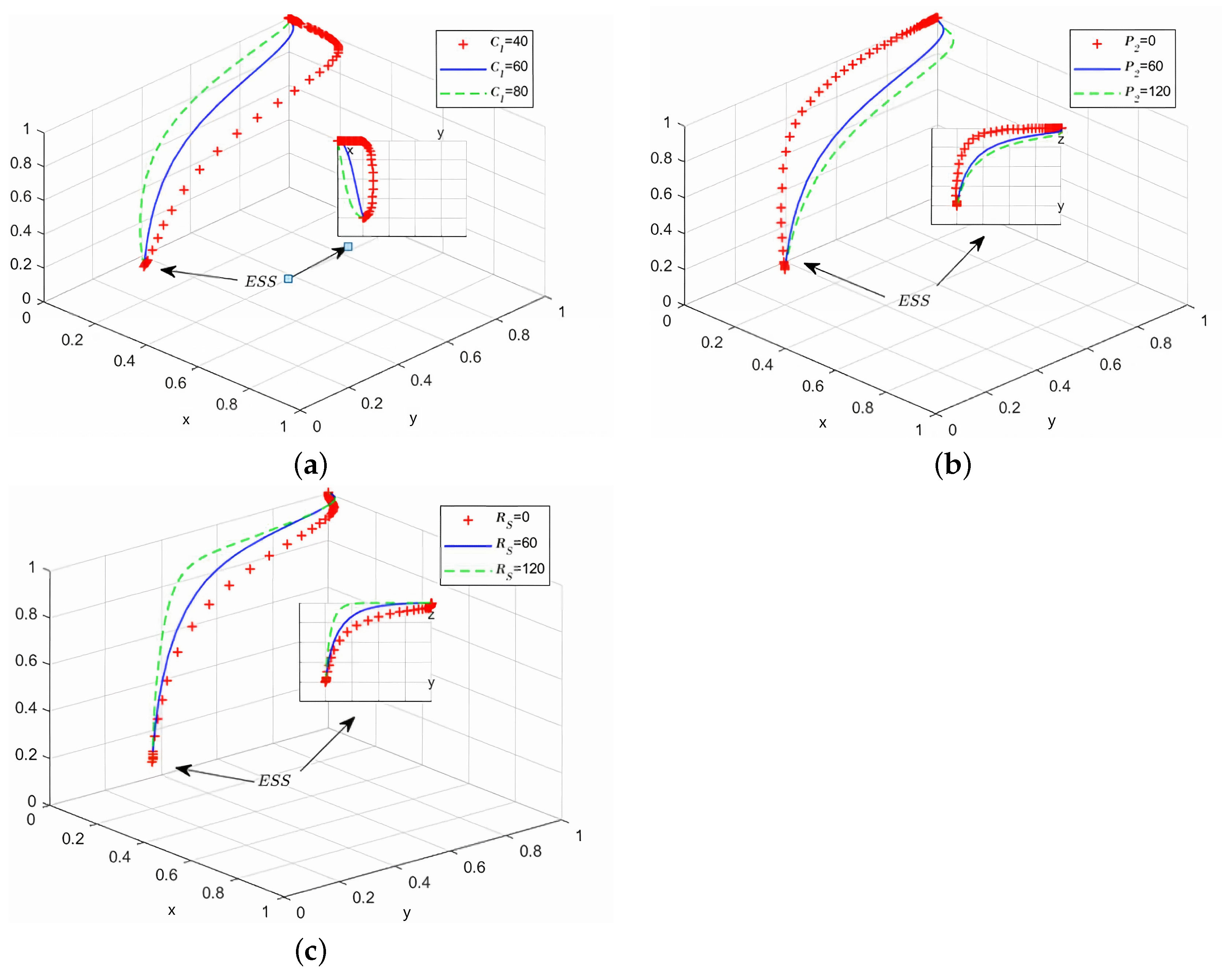
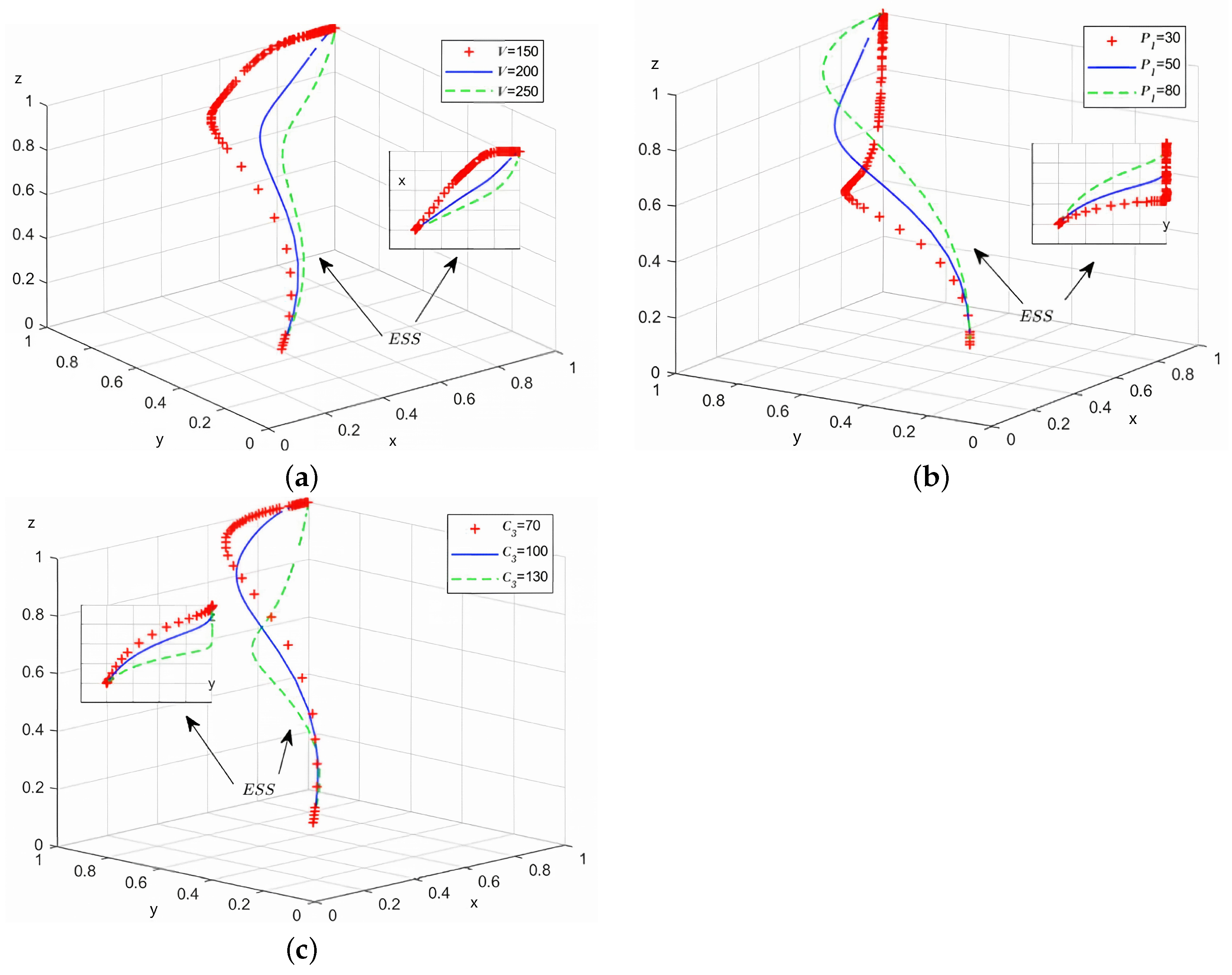
5.1. Simulation Result Analysis of the Evolution Process of Key Influence Parameters
5.1.1. Simulation Analysis of Strategy Point (1,1,0)
5.1.2. Simulation Analysis of Strategy Point (0,1,1)
5.1.3. Strategy Point (1,1,1) Simulation Analysis
5.2. Analysis of Simulation Results of Evolution Process Under Different Initial Probabilities
5.3. Discussion and Implications
6. Conclusions
- Incorporating Complex Attack Models: Future work will align attack strategies with frameworks like MITRE ATT&CK to model multi-stage and adaptive attack behaviors, alongside investigating the dynamic, stage-dependent responses of defenders and administrators.
- Exploring Advanced Learning Mechanisms: Going beyond replicator dynamics, investigating learning rules based on historical actions or belief updates (e.g., reinforcement learning) would capture more sophisticated strategic adaptation.
- Extending Model Assumptions: Incorporating continuous strategy spaces and scenarios with incomplete information would enhance the model’s realism and generalizability.
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Alese, B.K.; Ibidunmoye, E.O.; Haruna, D.I. Game-based analysis of the network attack-defense interaction. In Proceedings of the World Congress on Engineering, London, UK, 2–4 July 2014; Volume 1. [Google Scholar]
- Xu, Y.; Liu, J.; Cong, L.; Di, X.; Xie, N.; Xing, Z.; Qi, H. Game theory-based switch migration strategy for satellite networks. Comput. Commun. 2024, 221, 10–18. [Google Scholar] [CrossRef]
- Yang, Z.; Xiang, Y.; Liao, K.; Yang, J. Research on security defense of coupled transportation and cyber-physical power system based on the static Bayesian game. IEEE Trans. Intell. Transp. Syst. 2022, 24, 3571–3583. [Google Scholar] [CrossRef]
- Sun, H.; Shao, C.; Zhang, J.; Wang, K.; Huang, W. Evolution analysis of network attack and defense situation based on game theory. Comput. Mater. Contin. 2025, 83, 1451–1470. [Google Scholar] [CrossRef]
- Pawlick, J.; Zhu, Q. Quantitative models of imperfect deception in network security using signaling games with evidence. In Proceedings of the 2017 IEEE Conference on Communications and Network Security (CNS), Las Vegas, NV, USA, 9–11 October 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 394–395. [Google Scholar]
- Zhang, H.; Tan, J.; Liu, X.; Huang, S.; Hu, H.; Zhang, Y. Cybersecurity threat assessment integrating qualitative differential and evolutionary games. IEEE Trans. Netw. Serv. Manag. 2022, 19, 3425–3437. [Google Scholar] [CrossRef]
- Halabi, T.; Wahab, O.A.; Mallah, R.A.; Zulkernine, M. Protecting the internet of vehicles against advanced persistent threats: A Bayesian Stackelberg game. IEEE Trans. Reliab. 2021, 70, 970–985. [Google Scholar] [CrossRef]
- Younang, V.C.W.; Sen, A. Security Risk Assessment Using Bayesian Attack Graphs and Complex Probabilities for Large Scale IoT Applications. IEEE Trans. Dependable Secur. Comput. 2025; Early Access. [Google Scholar]
- Tosh, D.; Sengupta, S.; Kamhoua, A.C.; Kwiat, K.A. Establishing evolutionary game models for CYBer security information EXchange (CYBEX). J. Comput. Syst. Sci. 2016, 98, 27–52. [Google Scholar] [CrossRef]
- Zhang, B.; Dou, C.; Yue, D.; Park, J.H.; Zhang, Z. Attack-defense evolutionary game strategy for uploading channel in consensus-based secondary control of islanded microgrid considering DoS attack. IEEE Trans. Circuits Syst. Regul. Pap. 2021, 69, 821–834. [Google Scholar] [CrossRef]
- Shi, L.; Wang, X.; Hou, H. Research on optimization of array honeypot defense strategies based on evolutionary game theory. Mathematics 2021, 9, 805. [Google Scholar] [CrossRef]
- Liu, N.; Liu, S.; Zheng, W.-M. Evolutionary game and LGPSO for attack-defense confrontation analysis in WSN from macro perspective. Expert Syst. Appl. 2025, 264, 125815. [Google Scholar] [CrossRef]
- Jin, H.; Zhang, S.; Zhang, B.; Dong, S.; Liu, X.; Zhang, H.; Tan, J. Evolutionary game decision-making method for network attack and defense based on regret minimization algorithm. J. King Saud Univ.—Comput. Inf. Sci. 2023, 35, 292–302. [Google Scholar] [CrossRef]
- Liu, X.; Zhang, H.; Zhang, Y.; Shao, L. Optimal network defense strategy selection method based on evolutionary network game. Secur. Commun. Netw. 2020, 2020, 5381495. [Google Scholar] [CrossRef]
- Ho, E.; Rajagopalan, A.; Skvortsov, A.; Arulampalam, S.; Piraveenan, M. Game theory in defence applications: A review. Sensors 2022, 22, 1032. [Google Scholar] [CrossRef] [PubMed]
- Ruan, G. The evolutionary game simulation on knowledge sharing among innovation network members. J. Intell. 2011, 30, 100–104. [Google Scholar]




| Reference | Players | Game Theory Type | Dyn/ Evol | Regulator | Key Findings/ Focus |
|---|---|---|---|---|---|
| Yang et al. [3] | Attacker, Defender | Static Bayesian Game | No | No | Security defense of coupled transportation and cyber–physical power system. |
| Halabi et al. [7] | Attacker, Defender | Bayesian Stackelberg Game | No | No | Optimal resource allocation against advanced persistent threats in IoV. |
| Zhang et al. [10] | Attacker, Defender | Evolutionary Game Theory | Yes | No | Evolutionary strategy for DoS attack in islanded microgrid. |
| Shi et al. [11] | Attacker, Defender | Evolutionary Game Theory | Yes | No | Optimization of array honeypot defense strategies. |
| Jin et al. [13] | Attacker, Defender | Evolutionary Game Theory (Regret Minimization) | Yes | No | Network attack–defense decision-making based on regret minimization. |
| Tosh et al. [9] | Attacker, Defender, Info Exchange Center | Evolutionary Game Theory | Yes | Yes (diff. role) | Establishing evolutionary game models for cybersecurity information exchange. |
| Our Work | Attacker, Defender, System Admin | Evolutionary Game Theory | Yes | Yes (Core) | Analyzes tripartite stable strategies under regulation, providing quantitative basis for cybersecurity policy. |
| Main Body | Parameter | Meaning |
|---|---|---|
| Cyber attackers | x | The probability of choosing a strong attack strategy |
| The cost of choosing a strong attack strategy | ||
| Cyber defenders | y | The probability of choosing a strong defense strategy |
| The cost of choosing a strong defense strategy | ||
| V | Value of owned data assets | |
| E | Resources provide a fixed benefit to the defensive side | |
| L | The loss incurred when a resource attack is successful | |
| System Administrator | z | Choose the probability of strict supervision |
| Choose the cost of strict regulation | ||
| Strictly regulate the punishment of cyber attackers | ||
| Strict regulation and strong defense strategies reward the defender | ||
| Strict regulation and lax regulation are the punishment for defenders | ||
| The positive benefits of strong defense for system managers | ||
| Weak defense brings negative benefits to system managers | ||
| The probability of success of a network attacker when the network defender takes strong defense measures, and the network attacker carries out weak attack while the network defender takes weak defense | ||
| The probability of success of a network attacker when the network attacker adopts a strong attack and the network defender adopts a weak defense |
| Cyber Attackers | Defender | System Administrator | Payoff Vector (Attacker, Defender, SysAdmin) |
|---|---|---|---|
| x | y | Strict supervision (z) | |
| Loose regulation () | |||
| Strict supervision (z) | |||
| Loose regulation () | |||
| y | Strict supervision (z) | ||
| Loose regulation () | |||
| Strict supervision (z) | |||
| Loose regulation () |
| Equilibrium | |||
|---|---|---|---|
| Equilibrium | ESS | |||
|---|---|---|---|---|
| + | + | Instability point | ||
| − | + | Instability point | ||
| + | − | − | Instability point | |
| + | + | Instability point | ||
| − | − | − | ESS | |
| − | + | Instability point | ||
| + | − | + | Instability point | |
| − | + | − | Instability point |
| Equilibrium | ESS | |||
|---|---|---|---|---|
| + | + | Instability point | ||
| − | + | Instability point | ||
| + | − | − | Instability point | |
| + | + | Instability point | ||
| − | − | − | ESS | |
| − | + | Instability point | ||
| + | − | + | Instability point | |
| − | + | − | Instability point |
| Equilibrium | ESS | |||
|---|---|---|---|---|
| + | + | + | Instability point | |
| − | + | + | Instability point | |
| + | − | + | Instability point | |
| + | − | + | Instability point | |
| − | − | + | Instability point | |
| − | − | + | Instability point | |
| + | − | − | Instability point | |
| − | − | − | ESS |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Qian, Z.; Liu, F.; He, M.; Li, B.; Li, X.; Zhao, C.; Fu, G.; Hu, Y. A Three-Party Evolutionary Game Model and Stability Analysis for Network Defense Strategy Selection. Future Internet 2025, 17, 499. https://doi.org/10.3390/fi17110499
Qian Z, Liu F, He M, Li B, Li X, Zhao C, Fu G, Hu Y. A Three-Party Evolutionary Game Model and Stability Analysis for Network Defense Strategy Selection. Future Internet. 2025; 17(11):499. https://doi.org/10.3390/fi17110499
Chicago/Turabian StyleQian, Zhenghao, Fengzheng Liu, Mingdong He, Bo Li, Xuewu Li, Chuangye Zhao, Gehua Fu, and Yifan Hu. 2025. "A Three-Party Evolutionary Game Model and Stability Analysis for Network Defense Strategy Selection" Future Internet 17, no. 11: 499. https://doi.org/10.3390/fi17110499
APA StyleQian, Z., Liu, F., He, M., Li, B., Li, X., Zhao, C., Fu, G., & Hu, Y. (2025). A Three-Party Evolutionary Game Model and Stability Analysis for Network Defense Strategy Selection. Future Internet, 17(11), 499. https://doi.org/10.3390/fi17110499






