Abstract
Traditional cyber attack-defense strategies have traditionally focused solely on the attacker and defender, while neglecting the role of government-led system administrators. To address strategic selection challenges in cyber warfare, this study employs an evolutionary game theory framework to construct a tripartite game model involving cyber attackers, defenders, and system administrators. The replicator dynamic equation is utilized for stability analysis of behavioral strategies across stakeholders, with Lyapunov theory applied to evaluate the equilibrium points of pure strategies within the system. MATLAB (2021a) simulations were conducted to validate theoretical findings. Experimental results demonstrate that the model achieves evolutionary stability under various scenarios, yielding optimal defense strategies that provide theoretical support for addressing cybersecurity challenges.
1. Introduction
As cyberspace continues to expand, information technology has been widely adopted across industries, effectively driving societal development in the information age. However, this advancement also brings severe security threats and challenges. The primary form of confrontation among cyberspace entities is cyber warfare. To minimize damage or further reduce losses, it is essential to implement scientifically sound and feasible defense strategies to enhance cybersecurity capabilities [1]. Therefore, applying game theory-based approaches to analyze cybersecurity and strengthening the construction of defensive technology systems hold significant practical importance. Traditional decision-making approaches typically assume a static decision environment where decision-makers independently make choices with minimal consideration for other participants’ reactions. This makes them ill-suited to dynamic environments and struggle to analyze information asymmetry in detail. Decision-makers often focus on optimizing single objectives without mechanisms to predict adversaries’ actions or assess the system’s equilibrium state. Game theory, however, can quantify the impact of strategies between attackers and defenders, enabling analysis and optimization of decision-making processes in uncertain, complex, and interdependent network environments. It helps predict attack behaviors, formulate corresponding defense strategies, and innovatively propose incentive mechanisms to guide specific participant behaviors. These contributions have significantly advanced cybersecurity fields such as network security situation assessment, cyber warfare confrontation, and information warfare.
However, existing studies focus primarily on the attacker–defender dyad, overlooking the critical influence of a third participant: the government-led system administrator. This omission constitutes a significant limitation, as it fails to capture the regulatory dimension that fundamentally shapes real-world cybersecurity ecosystems. The administrator, through mechanisms such as audits, penalties, and rewards, alters the cost–benefit structure for both attackers and defenders, thereby critically changing the game dynamics and resulting equilibria. This intervention breaks the self-reinforcing dynamics of the bilateral game and introduces a feedback and control loop, steering the system towards more desirable equilibria that are unattainable without regulatory oversight. A typical scenario is the protection of Critical Information Infrastructure (e.g., the power grid), where a national regulatory body mandates security standards, penalizes non-compliance, and incentivizes robust defense, thereby fundamentally reshaping the strategic landscape for both utility companies and potential attackers. Therefore, incorporating the regulator as a strategic player is essential for a more accurate and realistic representation of cybersecurity governance.
To bridge this gap, this study constructs a tripartite evolutionary game model incorporating attackers, defenders, and a system administrator. The main contributions of this work are threefold:
- We propose a novel theoretical framework that endogenizes the system administrator as a core decision-maker, moving beyond traditional bilateral models.
- We derive the replicator dynamics and employ Lyapunov stability theory to identify and analyze the Evolutionary Stable Strategies (ESSs) under various realistic conditions.
- We validate our theoretical findings through numerical simulations and translate the equilibrium results into actionable insights for cybersecurity policy and defense strategy selection.
The remainder of this paper is structured as follows: Section 2 reviews related work. Section 3 details the model formulation. Section 4 presents the stability analysis of equilibrium points. Section 5 discusses the simulation results. Finally, Section 6 concludes the study and suggests future research directions.
2. Related Work
Significant progress has been made in cybersecurity through game-theoretic modeling approaches. Specifically, ref. [2] developed a game-theoretic matching optimization model and proposed a distributed algorithm to find Nash equilibria in strategic interactions. The work in [3] proposes a Bayesian-game-driven, charging-guided co-defense framework to enhance the resilience of the coupled transportation–cyber–physical power system against attacks. The study also improved existing strategy evaluation methods by incorporating defender countermeasures and attack success rates. The work in [4] introduced an Adversarial Game Theory (ADGM) model that defines network security status through node density distribution across various security states. This approach analyzes transition paths of cybersecurity conditions, effectively mapping macro-level network dynamics from micro-level adversarial behaviors. The work in [5] developed a signal game model integrating active defense technology, solving and analyzing pure-strategy complete Bayesian Nash equilibrium. Ref. [6] combined qualitative differential analysis with evolutionary game theory to construct a cybersecurity threat dynamic game model featuring continuous attack–defense interactions and bounded rational decision-makers. The study derived the evolution trajectory of cybersecurity states and validated the feasibility of the dynamic threat assessment algorithm. Ref. [7] designs a Bayesian Stackelberg game to optimally allocate IoV security resources against advanced persistent threats. Ref [8] presents a complex-probability attack graph framework to quantify concurrent exploits and backtracking cycles for large-scale IoT risk assessment.
Traditional game theory (such as Nash equilibrium analysis) typically focuses on static equilibrium states, assuming that participants select optimal strategies once and for all within a given strategy space and remain unchanged in equilibrium. It fails to account for dynamic adjustments and adaptive changes in participants’ strategies, often assumes complete rationality, neglects learning processes and bounded rationality, emphasizes individual-level equilibrium while ignoring collective behavioral patterns and evolutionary trends, lacks stability and sustainability, and features singular, inflexible strategies. Evolutionary game theory, however, is premised on bounded rationality [9], allowing participants to dynamically evolve based on their specific capabilities and gains from offensive–defensive interactions to select optimal solutions. In the context of cyber warfare, ref. [10] designs an evolutionary-game-based proactive defense to predict and mitigate DoS attacks in islanded microgrid secondary control. Subsequently, ref. [11] builds a three-player evolutionary game to evolve stable strategies for dynamic array–honeypot defense beyond static traps. Ref. [12] proposes a global learning particle swarm optimization algorithm for calculating Nash equilibria and quantifying evolutionary game parameters. Ref. [13] establishes an evolutionary game decision model for cyber attack–defense based on RM algorithms, deriving optimal defense strategies through solving stable equilibrium points and describing evolutionary trajectories of two-sided optimal strategies. Ref. [14] develops an attack–defense evolutionary game model based on network topology learning mechanisms and designs defense strategy selection algorithms. Through research on wireless sensor networks, ref. [15] systematically reviews multiple game-theoretic defense studies, classifying by warfare type, game class, and player structure, and identifies gaps.
To provide a clearer delineation between existing studies and the proposed work, a systematic comparison of related game-theoretic cybersecurity models is presented in Table 1. The table compares key aspects, including the players involved, the game theory type, dynamic nature, and consideration of a regulator. It clearly shows that most existing research is confined to an attacker–defender dyad and generally overlooks the role of an active regulatory third party. Even when a third party is considered, its role typically differs from the system administrator with enforcement power investigated in this study. This comparison highlights a gap in the literature and provides a clear justification for the necessity of our work.

Table 1.
Comparison of related work on game-theoretic cybersecurity models.
3. Methodology
3.1. Basic Concepts
Evolutionary game theory originated from biological evolution theory [16], among which the learning mechanism with replication dynamics as the core is most widely used. Under the condition of bounded rationality, this paper constructs an evolutionary game model of attack, defense, and user in network attack and defense based on evolutionary game theory.
Definition 1.
The three-way evolutionary game model of network attack and defense can be expressed as a four-tuple .
(1) represents the set of three participants in network attack and defense. Here, represents the network attacker, represents the network defender, and represents the system manager.
(2) represents the set of strategy spaces for the evolution game of three-party attack and defense, where is the strategy set of network attacker; is the strategy set of network defender; is the strategy set of system manager. respectively represent the number of strategies of attacker, defender, and system manager; and are all positive integers.
(3) The belief set for the evolution game of attack, defense, and tripartite . Here, represents the probability distribution of the attacker’s strategy set; represents the probability that the attacker chooses to adopt an attack strategy ; represents the probability distribution of the defender’s strategy set; and represents the probability distribution of the system manager’s strategy set.
(4) is the set of payoff functions of the three-party evolutionary game model, which represents the game payoff of each participant. respectively represent the payoff function obtained by network attackers, network defenders, and system managers when choosing strategy sets.
Definition 2.
The payoff matrix of the three-party evolution game of network attack and defense consists of the benefits obtained by the three parties under the three-party strategy , and there are elements in the matrix.
(1) Use ,, respectively represent the total revenue of the implementation actions of network attackers, network defenders, and system managers, and use ,, respectively represent the costs of network attackers, network defenders, and system managers.
(2) Use ,, respectively represent the net benefits of network attackers, network defenders, and system managers, which are shown as follows:
(3) represents a set of three-party benefit matrices for network attack and defense, where represents the benefit matrix of network attackers, represents the benefit matrix of network defenders, and represents the benefit matrix of system managers. Based on the above theory, the benefit matrices of the three parties are shown as follows:
In cyber warfare scenarios, attackers, defenders, and system administrators employ distinct strategies. Through strategic imitation of competitive tactics and adaptive adjustments driven by mutual interests, the confrontation evolves into a dynamic process. To clarify the quantified benefits of each stakeholder in this tripartite framework, we integrate and visualize the attack payoff matrix, defense payoff matrix, and management payoff matrix using game theory diagrams, as illustrated in Figure 1. Each terminal node of the game tree is associated with a payoff vector , where , and represent the payoffs for the attacker, defender, and administrator, respectively, under the corresponding strategy combination . For instance, the vector denotes the payoffs for all parties when the attacker chooses strategy 1, the defender chooses strategy 1, and the administrator chooses strategy 1.
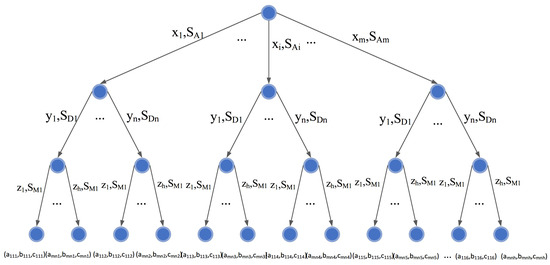
Figure 1.
Three-party subject attack and defense game tree. The ellipsis in the figure indicates that not all strategies are listed.
3.2. Tripartite Evolution Game Model
The network defense strategy constructed in this paper selects the logical relationship between the three parties of evolutionary game subjects as shown in Figure 2:
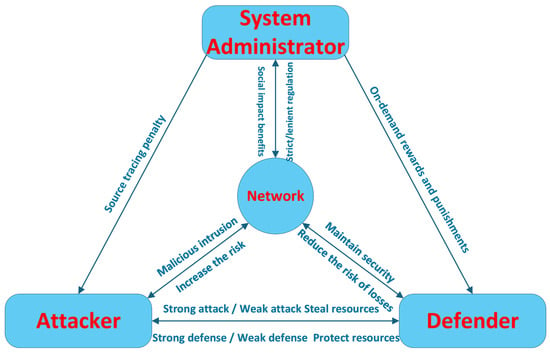
Figure 2.
Tripartite evolution of the main logical relationship between the subject.
Assuming the three parties have distinct strategy sets: (1) Strong Attack vs. Weak Attack , (2) Strong Defense vs. Weak Defense , (3) Strict vs. Lenient Regulation . Strong Attack denotes sophisticated, resource-intensive offensive actions (e.g., Advanced Persistent Threats), modeled by a substantial cost . Weak Attack refers to simple, low-effort opportunistic attacks, whose cost is assumed to be negligible. Strong Defense represents the deployment of proactive and advanced security measures (e.g., threat intelligence platforms and automated incident response systems), incurring a cost . Weak Defense implies relying only on basic, foundational security controls (e.g., conventional firewalls, basic patch management), with assumed negligible cost but resulting in reduced defense effectiveness. Strict supervision means the administrator enforces high-intensity oversight, including mandatory audits, forensic investigation, and the imposition of rewards/penalties, at a cost . Loose Regulation describes a basic, reactive supervisory approach, with assumed negligible cost. V represents the value of defensive resources, E represents the fixed returns generated by these defenses. When attackers employ strong strategies, defenders adopt weak defenses and administrators implement lenient regulation, resulting in continuous ransomware intrusions causing losses L (L increasing with V). During network attacks, strict regulation administrators conduct traceability investigations and impose penalties on attackers. If defenders adopt strong defense strategies, they receive administrative rewards ; otherwise, penalties apply. Implementing strong defense strategies yields positive benefits for system administrators, whereas adopting weak defenses under lenient regulation leads to negative outcomes .
When attackers employ strong attacks with defenders implementing robust defenses, or when attackers use weak attacks with defenders adopting inadequate defenses, the probability of successful cyberattacks remains constant ∂. Specifically, (1) when attackers launch strong attacks against defenders using weak defenses, the success rate of cyberattacks equals . (2) When attackers employ weak attacks against defenders with strong defenses, the probability of successful cyberattacks becomes negligible.
Based on the above assumptions, the payoff matrix of a mixed strategy game between network attackers, network defenders, and system managers is shown in Table 2.

Table 2.
Setting of relevant parameters of the three parties in the game model.
Based on the above benefit matrix, we can obtain the expected benefit matrix and average benefit matrix under different strategy combinations of the three parties. Among them, the benefit of strong attack strategy of network attackers is , the benefit of weak attack is , and the average benefit of selected strategies is :
The benefits of the strong defense strategy for network defenders are , and the benefits of the weak defense strategy are . The average benefits of the selected strategies are :
The returns of the system regulator’s strict supervision strategy are , the returns of the loose supervision strategy are , and the average returns of the selected strategies are :
3.3. Analysis of Three-Way Evolution Path
3.3.1. Analysis of Network Attacker Strategy Evolution Path
According to Equation (1), the dynamic equation of attack replication and its first partial derivative can be obtained as follows:
If . According to the stability theorem of differential equations, if a cyber attacker chooses to launch a strong attack, they must satisfy the following conditions to maintain stability: and . Since is an increasing function of y, we have that when , , and thus the attacker cannot determine a stable strategy; when , , and becomes the attacker’s evolutionary stable strategy; conversely, when , it represents the Evolutionarily Stable State (ESS). The phase diagram of the attacker’s strategy evolution is shown in Figure 3.
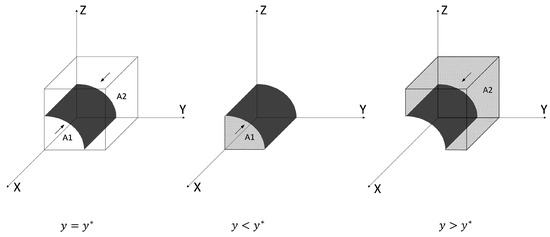
Figure 3.
Phase diagram of network attacker strategy evolution.
The volume in the figure is , where is the probability that the attacker chooses a strong attack, and the volume is , where is the probability that the attacker chooses a weak attack. Calculations can be obtained as follows:
According to the expression of the probability that network attackers adopt strong attack strategy, the first-order partial derivatives of each element are obtained: , , , , . It is also found that the probability of adopting strong attack is positively correlated with and negatively correlated with .
When the attacker is analyzed for strategic stability, is an evolutionally stable strategy when . As gradually increased, the attacker’s stable strategy gradually changed from (taking a strong attack strategy) to (taking a weak attack strategy).
3.3.2. Analysis of Evolution Path of Network Defender Strategy
According to Equation (2), the dynamic equation of attack replication and its first partial derivative are obtained as follows:
If . According to the stability theorem of differential equations, if a network defender chooses to implement strong defense, they must satisfy the following conditions to maintain stability: and . Since is a decreasing function of z, we have that when , , , indicating the defender cannot determine a stable strategy; when , , in which becomes the defender’s final stable strategy; conversely, when , it represents an Equilibrium Stable State (ESS). The phase diagram of the defender’s strategy evolution is shown in Figure 4.
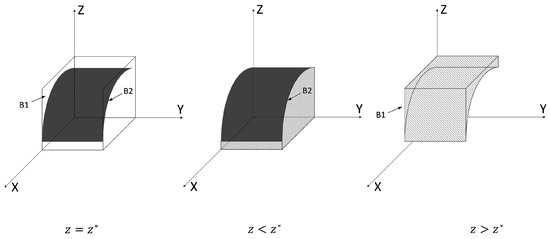
Figure 4.
Evolution phase diagram of network defender strategy.
In the figure, the volume is , the probability of the defender choosing strong defense is , and the volume is , the probability of the defender choosing weak defense is . Calculations can be obtained as follows:
According to the expression of the probability of network defenders adopting strong defense strategy, the first-order partial derivatives of each element are obtained as , , , , , and . Therefore, the probability of adopting strong defense is positively correlated with and negatively correlated with .
When the defender is analyzed for strategic stability, is an evolutionally stable strategy when , . As gradually increases, the defender’s stable strategy changes from (taking a weak defense strategy) to (taking a strong defense strategy).
3.3.3. Analysis of Evolution Path of System Manager Strategy
According to Equation (2), the dynamic equation of attack replication and its first partial derivative are obtained as follows:
if . According to the stability theorem of differential equations, if a system manager adopts a strict supervision strategy x, the system must satisfy the following conditions to maintain stability: and
Since is a decreasing function of x, we have that when
, and the system manager cannot determine a stable strategy; when , , becomes the final stable strategy for the system manager; conversely, when , it reaches ESS. The phase diagram of the system manager’s strategy evolution is shown in Figure 5:
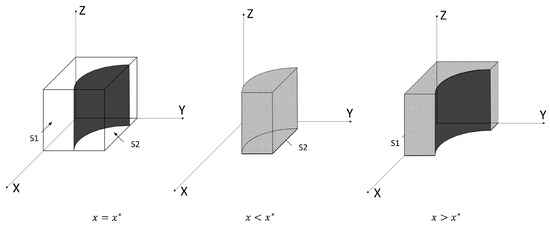
Figure 5.
Phase diagram of system manager strategy evolution.
The volume in the figure is, where is the probability that the system administrator chooses strong defense, and the volume of is , where is the probability that the system administrator chooses weak defense. Calculations can be obtained as follows:
According to the expression of the probability of system managers adopting strict supervision strategies, the first-order partial derivatives of each element are obtained as , , , , , . The probability of adopting strict supervision is positively correlated with and negatively correlated with . When the system manager conducts a stability analysis of strategies, when
and , , is considered an evolutionary stable strategy; when and ,, becomes a final stable strategy. Therefore, as x increases and y decreases, the system manager’s strategy gradually shifts from (loose regulation) to (strict regulation).
4. Model Solution and Analysis
4.1. Solving the Three-Party Evolutionary Game Model
According to Lyapunov stability theory, the equilibrium point of the system , , , can be calculated with . The Jacobian matrix of the three-party evolutionary game is as follows:
The eigenvalues at each equilibrium point are solved, as shown in Table 3:

Table 3.
Payoff matrix of the three-party mixed-strategy game.
4.2. Stability Analysis of Balance Point
According to the first law of Lyapunov, when the corresponding eigenvalues of each equilibrium point are negative, the equilibrium point is stable; when there is at least one positive eigenvalue, the equilibrium point is unstable. The corresponding eigenvalues of each equilibrium point are analyzed under different circumstances, according to Table 4.

Table 4.
Payoff matrix of three-party mixed-strategy game (order as original).
Scenario 1. When the conditions are met , the stable strategies of the three parties are strong attack, strong defense, and loose supervision, and the stability determination is shown in Table 5.

Table 5.
Stability analysis of .
In Scenario 1, cyber attackers derive far greater benefits from launching aggressive attacks than the costs incurred in implementing strong countermeasures. When an attack occurs, system administrators fail to impose retrospective penalties, leading attackers to adopt aggressive strategies. For network defenders facing frequent and highly sophisticated cyberattacks, the perceived risk of losses far outweighs the costs of proactive defense measures, making aggressive defense strategies nearly inevitable. When all defenders implement rigorous protective measures during cyberattacks, the overall network environment remains largely intact. System administrators not only avoid negative consequences but also gain positive returns, resulting in a near-zero probability of adopting strict supervision. When all three parties reach equilibrium, the optimal defensive strategy becomes aggressive defense.
Scenario 2. When the conditions are met , the three-party evolutionary stable strategy is (weak attack, strong defense, strict supervision), and the stability determination situation is shown in Table 6.

Table 6.
Stability analysis of .
In Scenario 2, cyber attackers face significantly higher costs than potential gains from adopting aggressive attack strategies, coupled with traceability penalties imposed by system administrators. This incentivizes attackers to adopt passive defense tactics. Conversely, when system administrators implement strict oversight and provide corresponding rewards for defenders adopting robust defenses, it substantially reduces defensive losses, thereby encouraging stronger protective measures. The dynamic between defenders’ aggressive strategies and attackers’ passive approaches generates substantial positive social benefits for system administrators, driving them to enforce stricter regulations. When all three stakeholders reach equilibrium, the optimal defense strategy becomes aggressive defense.
Scenario 3. When the conditions are met , the stable strategies of the three parties are (strong attack, strong defense, strict supervision), and the stability determination is shown in Table 7.

Table 7.
Stability analysis of .
In Scenario 3, when the network defender possesses sufficiently high resource value, attackers may still opt for aggressive attack strategies to maximize gains despite facing traceability penalties from system regulators. When both resource value and regulatory incentives are sufficient, defenders tend to adopt strong defense strategies over time to minimize losses. Meanwhile, system regulators implement strict oversight policies that increase rewards for defenders while intensifying penalties against attackers. Given that the costs of rigorous supervision and reward expenditures are lower than fines and positive benefits from penalties, the probability of adopting strict supervision approaches tends toward 1. When all three parties reach equilibrium, the optimal defense strategy becomes aggressive defense.
4.3. Optimal Strategy Selection Algorithm
In the process of a three-party game of network attack and defense, each subject can maximize its expected benefit by constantly learning, adjusting, and improving its strategy selection, and gradually tend to a certain equilibrium state. At this time, the strategy selected by each subject is the optimal strategy.
In the initial phase of a three-party evolutionary game, participants fully utilize available information resources to assess expected economic returns from their strategies. Subsequently, they employ evolutionary dynamic equations to precisely calculate optimal defensive strategies that maximize benefits, continuously refining and optimizing their choices to achieve better outcomes. This ongoing process of information gathering and strategy adjustment forms the cornerstone enabling the three-party evolutionary game model to operate effectively and sustainably. See Algorithm 1.
| Algorithm 1. Algorithm for deriving the optimal network defense strategy | |
| 1 | Input the initial three-party evolutionary game model . |
| Construct the attacker’s strategy set and belief set | |
| 2 | , where is the probability that the attacker adopts attack strategy . |
| Construct the defender policy set and belief set | |
| 3 | , where is the probability that the defender adopts defense strategy . |
| Construct the system manager’s strategy set and belief set | |
| 4 | , where is the probability that the system manager adopts supervision strategy . |
| 5 | /* Calculate the attack and defense benefit matrices for each strategy combination */ |
| 6 | for i←1 to m do |
| 7 | for j←1 to n do |
| 8 | for k←1 to h do |
| 9 | |
| 10 | |
| 11 | |
| 12 | end for |
| 13 | end for |
| 14 | end for |
| 15 | /* Complex dynamic equations are constructed*/ |
| 16 | for i←1 to m do |
| 17 | |
| 18 | end for |
| 19 | for j←1 to n do |
| 20 | |
| 21 | end for |
| 22 | for k←1 to h do |
| 23 | |
| 24 | Solve |
| 25 | Output the optimal network defense strategy |
| 26 | end |
5. Results and Discussion
To validate the aforementioned analysis, we conducted simulation experiments using a tripartite cyber attack–defense model based on evolutionary game theory proposed in this paper. Through deploying network information systems, we used Matlab R2020b to analyze the evolutionary patterns and behavioral tendencies of three stakeholders in cyber warfare scenarios, while exploring how critical influencing parameters affect the strategic models.
This study analyzes the evolution process of key influencing parameters for three strategic equilibrium points, with all initial values set to 0.2. The ode 45 function was employed to solve differential equations over a time range from 0 to 50, where different parameter values were assigned to each dataset and plotted using distinct colors and line types. Subsequent analyses examined evolutionary processes under varying initial probabilities while keeping other parameters constant. A three-layer nested loop was implemented to modify initial strategy combinations of , with variables within each iteration ranging from 0.1 to 1 at 0.2-step intervals. This resulted in 125 datasets, which were analyzed through ode45 to determine system state evolution over time. The plot3 function transformed these results into visual 3D graphics, enabling observation of evolutionary trajectories under different initial strategies and facilitating deeper understanding of system behavior patterns.
5.1. Simulation Result Analysis of the Evolution Process of Key Influence Parameters
5.1.1. Simulation Analysis of Strategy Point (1,1,0)
Select the data that meet the conditions to form array 1, and analyze the influence of the process and results of the three-party evolutionary game under this situation, and analyze the influence brought by the change of the core influence parameter value .
Analyze the correlation between variable changes and evolutionary game process and results, assign parameters , , , respectively, while keeping other parameters unchanged. During the simulation evolution process, 50 iterative operations are carried out to obtain the simulation results of the replication dynamic equation, as shown in Figure 6a–c:
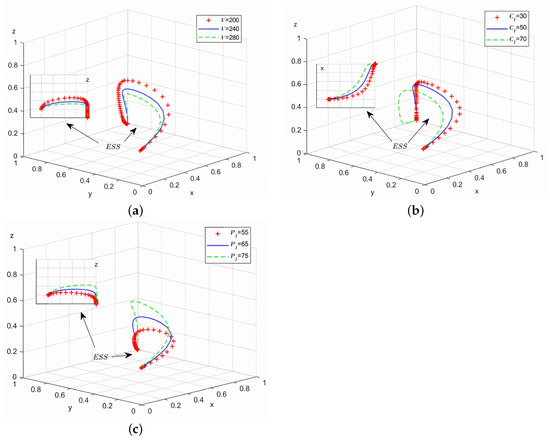
Figure 6.
Simulation analysis of strategy point (1,1,0).
As shown in Figure 6a, the enhancement of network users’ resource value accelerates attackers’ evolution toward sustained use of aggressive strategies. With increasing risks V, both attackers’ probability of adopting aggressive tactics and defenders’ probability of implementing robust defenses rise simultaneously, while system administrators’ adoption of strict monitoring decreases. In this scenario, defenders invest more resources to protect their assets, aiming to minimize losses during large-scale aggressive attacks. Figure 6b reveals that as risks escalate, attackers’ probability of choosing aggressive strategies declines while defenders’ probability of adopting strong defense measures increases. By continuously upgrading cybersecurity technologies, updating security protocols, and implementing robust defense strategies, defenders significantly increase the difficulty of attacks and raise the costs of aggressive tactics, ultimately reducing attackers’ propensity to use aggressive approaches. Figure 6c indicates that as risks grow, attackers’ probability of using aggressive strategies decreases while system administrators’ preference for strict monitoring intensifies. Therefore, to curb cyberattacks, system administrators should enhance cybersecurity frameworks by increasing penalties, establishing comprehensive governance regulations, developing efficient incident response mechanisms, and improving regulatory oversight capabilities. These measures combined with stricter enforcement can effectively reduce attackers’ reliance on aggressive tactics.
5.1.2. Simulation Analysis of Strategy Point (0,1,1)
Select the data that meet the conditions to form array 2, analyze the process and results of the three-party evolutionary game under this situation, and analyze the influence brought by the change of the core influencing parameter value .
Analyze the correlation between variable changes and evolutionary game process and results, assign parameters , , , respectively, while keeping other parameters unchanged. During the simulation evolution process, 50 iterative operations are carried out to obtain the simulation results of the replication dynamic equation, as shown in Figure 7a–c:
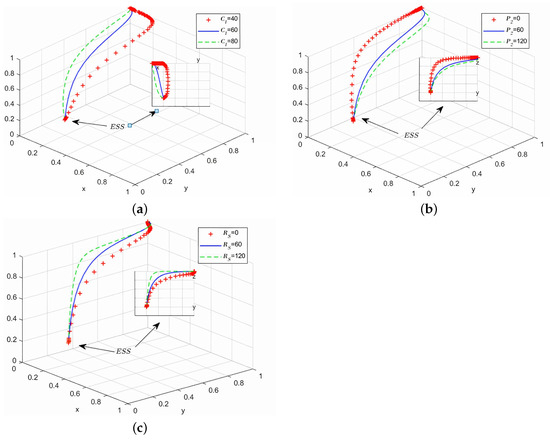
Figure 7.
Simulation analysis of strategy point (0,1,1).
As shown in Figure 7a, as the value of increases, both the probability of cyber attackers adopting aggressive attack strategies and the probability of defenders implementing robust defense measures decrease. In such scenarios, attackers may opt for more cost-effective, covert, and harder-to-detect tactics to reduce operational costs and enhance attack success rates. This necessitates system administrators to adopt stricter regulatory policies. Consequently, defenders must intensify research and monitoring of emerging attack patterns while promptly adjusting their defense strategies. Continuous enhancement of cybersecurity expertise and vigilance is essential to maintain sensitivity to evolving threats and respond effectively to dynamic security environments. Figure 7b reveals that as the value of rises, the probability of attackers choosing aggressive strategies and defenders implementing strong defenses increases simultaneously, while the probability of administrators adopting strict oversight decreases. The graph indicates that to strengthen overall network security, administrators should focus on technical enhancements that increase attackers’ intrusion difficulty rather than merely raising penalties for non-compliant defenders. Figure 7c demonstrates that as the value of grows, administrators’ adoption of strict supervision intensifies. Strengthening public recognition and awareness of administrators’ roles through transparent regulatory frameworks and accountability mechanisms will ensure fair enforcement practices, thereby collectively advancing cybersecurity development and maximizing regulatory effectiveness and social benefits.
5.1.3. Strategy Point (1,1,1) Simulation Analysis
Select the data that meet the conditions to form array 3, and analyze the process and results of the three-party evolutionary game under this situation, and analyze the influence brought by the change of the core influencing parameter value.
Analyze the correlation between variable changes and evolutionary game process and results, assign parameters
and , respectively, while keeping other parameters unchanged. During the simulated evolution process, 50 iterative operations are carried out to obtain simulation results of the replication dynamic equation, as shown in Figure 8a–c.
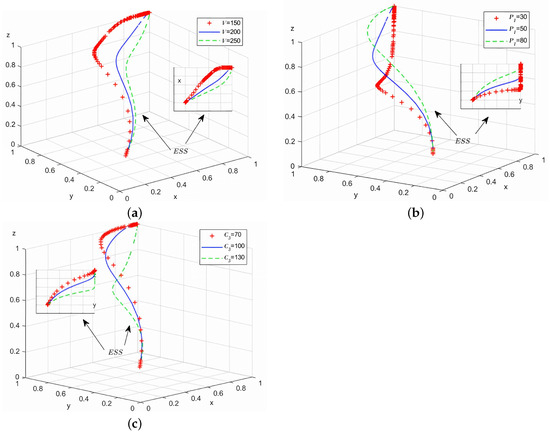
Figure 8.
Simulation analysis of strategy point (1,1,1).
As shown in Figure 8a, as the value of V increases, cyber attackers’ probability of adopting aggressive attack strategies rises, while both defenders’ adoption of robust defense measures and system administrators’ implementation of strict supervision decrease. To curb attacks and enhance cybersecurity, system administrators should proactively fulfill their supervisory responsibilities by providing technical support subsidies to defenders. This reduces the resource costs for defenders, elevates overall network security, and consequently decreases attackers’ propensity to employ aggressive tactics. Figure 8b demonstrates that increased penalties incentivize administrators to maintain rigorous oversight. As the value of rises, the probability of strict supervision intensifies, making attacks more costly and reducing aggressive strategy adoption, thereby strengthening network security. Figure 8c reveals that higher increases attackers’ probability of using aggressive strategies while decreasing administrators’ adoption of strict supervision. By establishing innovative regulatory frameworks and implementing cutting-edge cybersecurity technologies, we can reduce administrative and human resource costs associated with strict supervision, effectively lowering attackers’ probability of choosing aggressive tactics.
5.2. Analysis of Simulation Results of Evolution Process Under Different Initial Probabilities
Figure 9a–c respectively illustrate the results after 125 iterations of Array 1, Array 2, and Array 3. As shown in Figure 9a, when the conditions are met, the system exhibits a uniquely stable strategy combination (strong attack, strong defense, lenient supervision). Network defenders should strengthen cybersecurity measures by conducting regular vulnerability scans and repairs, establishing backup systems and emergency response mechanisms. Simultaneously, they should actively foster public awareness to encourage system administrators to fulfill their duties diligently, thereby enhancing overall network security.
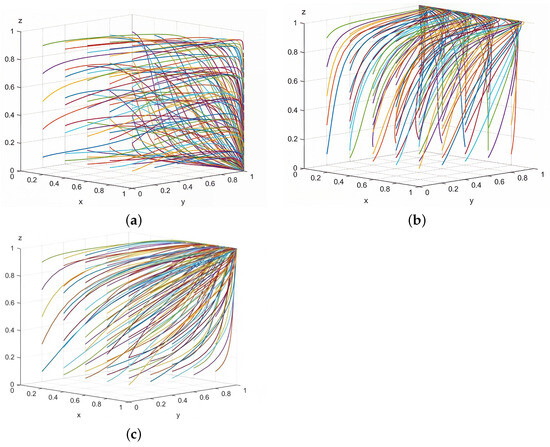
Figure 9.
Results of 125 iterations of the group evolution. Lines of different colors represent different initial conditions.
As shown in Figure 9b, when the conditions are met, the system exhibits a unique evolutionary stable strategy combination (weak attack, strong defense, strict supervision). System administrators must establish comprehensive legal frameworks, enhance reward and penalty mechanisms for both attackers and defenders, and spearhead the development of network defense systems. Through systematic defensive measures, this approach not only reduces the operational costs for defenders implementing robust defenses but also boosts their motivation to strengthen cybersecurity, thereby effectively curbing cyber intrusions to the greatest extent possible.
As shown in Figure 9c, when the conditions are met, the system exhibits a unique evolutionary stable strategy combination (strong attack, strong defense, strict supervision). Under this configuration, defenders hold higher resource value while system administrators impose relatively low penalties on attackers. Given that attackers perceive higher returns than risks, they tend to adopt aggressive offensive measures. Frequent cyberattacks drive defenders and administrators to actively implement defensive and regulatory measures. This can enhance traceability capabilities for cyberattacks and increase penalty, while boosting rewards for defenders. Consequently, more resources will be allocated to accelerate technological research in areas like intrusion detection systems and information security defenses. These efforts aim to maintain network environment security through more efficient and rapid methods.
In conclusion, the results obtained through numerical simulation analysis align with theoretical analyses of strategy stability, thereby validating the effectiveness of the analysis. This discovery holds significant practical implications and guiding value for cybersecurity regulation, helping us better understand and address challenges posed by cyber attacks.
5.3. Discussion and Implications
To fully demonstrate the practical value of our model, we take Scenario 2 (Weak Attack, Strong Defense, Strict Supervision) as an example and delve into a concrete case study of Critical Information Infrastructure protection (e.g., a smart grid). In this case, the defender is a grid operator protecting high-value assets V; the attacker is a hostile entity aiming to disrupt the infrastructure; and the administrator is a national cybersecurity regulatory agency.
Our model analysis reveals that to achieve and maintain this ideal state, the regulator must implement a precise combination of policies: First, it must ensure, through robust threat attribution and law enforcement capabilities, that the penalty is high enough to make the cost of a strong attack significantly exceed its expected gain . Second, it needs to provide adequate rewards or subsidies for the operator to deploy strong defense measures (e.g., advanced threat detection systems), while simultaneously imposing clear fines for security negligence, thereby making “strong defense” the only rational choice for the operator both economically and compliantly.
The unique value of our model lies in its transformation of qualitative goals, such as “effective deterrence,” into quantitative relationships among key parameters like , , and . Policymakers can use our stability conditions (e.g., ) to calculate the minimum threshold for required regulatory intensity (e.g., ), thereby advancing cybersecurity governance from experience-based to scientifically quantitative.
6. Conclusions
Cyber warfare constitutes a dynamic and complex process. This study employs bounded rationality theory to construct a tripartite evolutionary game model for attackers, defenders, and system administrators, grounded in practical cyber defense scenarios. Through replicating dynamic equations, we comprehensively analyze the strategic evolution of all parties’ behaviors and their ultimate stable states under different conditions, thereby identifying optimal defensive strategies for each scenario. By simulating key variable control at three strategic equilibrium points, the analysis reveals critical factors influencing behavioral patterns across stakeholders. These findings provide actionable insights for evolving cyber defense strategies, ultimately contributing to the development of more secure cyberspace environments.
This study establishes a foundational tripartite evolutionary game model, providing a theoretical cornerstone for understanding the regulator’s role in cybersecurity. Future research can be pursued in the following directions to extend this work:
- Incorporating Complex Attack Models: Future work will align attack strategies with frameworks like MITRE ATT&CK to model multi-stage and adaptive attack behaviors, alongside investigating the dynamic, stage-dependent responses of defenders and administrators.
- Exploring Advanced Learning Mechanisms: Going beyond replicator dynamics, investigating learning rules based on historical actions or belief updates (e.g., reinforcement learning) would capture more sophisticated strategic adaptation.
- Extending Model Assumptions: Incorporating continuous strategy spaces and scenarios with incomplete information would enhance the model’s realism and generalizability.
Author Contributions
Z.Q.: Conceptualization, Formal analysis, Methodology, Validation, Writing—original draft, Writing—review and editing. F.L.: Funding acquisition, Validation, Writing—review and editing. M.H.: Project administration, Writing—review and editing. B.L.: Funding acquisition, Project administration, Supervision, Writing—review & editing. X.L.: Supervision, Writing—review and editing. C.Z.: Supervision, Writing—review and editing. G.F.: Supervision, Writing—review and editing, Methodology. Y.H.: Supervision, Writing—review and editing. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by China Southern Power Grid’s major network-level scientific and technological project “Research and Application of Multi-dimensional Active Defense Technology for Digital Grid”, project number 037800KC24040002 (GDKJXM20240428).
Data Availability Statement
No new data were created or analyzed in this study. Data sharing is not applicable to this article.
Acknowledgments
The author thanks all reviewers who reviewed this manuscript.
Conflicts of Interest
All authors were employed by the company Guangdong Power Grid Co., Ltd. The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
References
- Alese, B.K.; Ibidunmoye, E.O.; Haruna, D.I. Game-based analysis of the network attack-defense interaction. In Proceedings of the World Congress on Engineering, London, UK, 2–4 July 2014; Volume 1. [Google Scholar]
- Xu, Y.; Liu, J.; Cong, L.; Di, X.; Xie, N.; Xing, Z.; Qi, H. Game theory-based switch migration strategy for satellite networks. Comput. Commun. 2024, 221, 10–18. [Google Scholar] [CrossRef]
- Yang, Z.; Xiang, Y.; Liao, K.; Yang, J. Research on security defense of coupled transportation and cyber-physical power system based on the static Bayesian game. IEEE Trans. Intell. Transp. Syst. 2022, 24, 3571–3583. [Google Scholar] [CrossRef]
- Sun, H.; Shao, C.; Zhang, J.; Wang, K.; Huang, W. Evolution analysis of network attack and defense situation based on game theory. Comput. Mater. Contin. 2025, 83, 1451–1470. [Google Scholar] [CrossRef]
- Pawlick, J.; Zhu, Q. Quantitative models of imperfect deception in network security using signaling games with evidence. In Proceedings of the 2017 IEEE Conference on Communications and Network Security (CNS), Las Vegas, NV, USA, 9–11 October 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 394–395. [Google Scholar]
- Zhang, H.; Tan, J.; Liu, X.; Huang, S.; Hu, H.; Zhang, Y. Cybersecurity threat assessment integrating qualitative differential and evolutionary games. IEEE Trans. Netw. Serv. Manag. 2022, 19, 3425–3437. [Google Scholar] [CrossRef]
- Halabi, T.; Wahab, O.A.; Mallah, R.A.; Zulkernine, M. Protecting the internet of vehicles against advanced persistent threats: A Bayesian Stackelberg game. IEEE Trans. Reliab. 2021, 70, 970–985. [Google Scholar] [CrossRef]
- Younang, V.C.W.; Sen, A. Security Risk Assessment Using Bayesian Attack Graphs and Complex Probabilities for Large Scale IoT Applications. IEEE Trans. Dependable Secur. Comput. 2025; Early Access. [Google Scholar]
- Tosh, D.; Sengupta, S.; Kamhoua, A.C.; Kwiat, K.A. Establishing evolutionary game models for CYBer security information EXchange (CYBEX). J. Comput. Syst. Sci. 2016, 98, 27–52. [Google Scholar] [CrossRef]
- Zhang, B.; Dou, C.; Yue, D.; Park, J.H.; Zhang, Z. Attack-defense evolutionary game strategy for uploading channel in consensus-based secondary control of islanded microgrid considering DoS attack. IEEE Trans. Circuits Syst. Regul. Pap. 2021, 69, 821–834. [Google Scholar] [CrossRef]
- Shi, L.; Wang, X.; Hou, H. Research on optimization of array honeypot defense strategies based on evolutionary game theory. Mathematics 2021, 9, 805. [Google Scholar] [CrossRef]
- Liu, N.; Liu, S.; Zheng, W.-M. Evolutionary game and LGPSO for attack-defense confrontation analysis in WSN from macro perspective. Expert Syst. Appl. 2025, 264, 125815. [Google Scholar] [CrossRef]
- Jin, H.; Zhang, S.; Zhang, B.; Dong, S.; Liu, X.; Zhang, H.; Tan, J. Evolutionary game decision-making method for network attack and defense based on regret minimization algorithm. J. King Saud Univ.—Comput. Inf. Sci. 2023, 35, 292–302. [Google Scholar] [CrossRef]
- Liu, X.; Zhang, H.; Zhang, Y.; Shao, L. Optimal network defense strategy selection method based on evolutionary network game. Secur. Commun. Netw. 2020, 2020, 5381495. [Google Scholar] [CrossRef]
- Ho, E.; Rajagopalan, A.; Skvortsov, A.; Arulampalam, S.; Piraveenan, M. Game theory in defence applications: A review. Sensors 2022, 22, 1032. [Google Scholar] [CrossRef] [PubMed]
- Ruan, G. The evolutionary game simulation on knowledge sharing among innovation network members. J. Intell. 2011, 30, 100–104. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).