Protecting Function Privacy and Input Privacy in the Publicly Verifiable Outsourcing Computation of Polynomial Functions
Abstract
1. Introduction
- We propose the first publicly verifiable outsourcing computation scheme that achieves both function privacy and input privacy for matrix functions, which can be extended to arbitrary polynomial functions (the extension method is provided).
- We additionally provide a faster privately verifiable method, which allows the request user to verify the results more efficiently than with public verification.
- The function owner retains control over the function. If they do not allow a user to use their function model, the cloud server cannot complete the computation.
2. Related Works
3. Preliminaries
3.1. Additive Homomorphic Encryption (Additive HE)
- : The security parameter is taken as input, and two -bit large prime numbers, , are chosen. Then, we have , where p = 2 + 1 and q = 2 + 1. A generator is randomly sampled, and then the public parameters are output.
- : The public parameters are taken as input. According to , is randomly sampled. Then, the public/secret key pair is output.
- : For a message , is sampled. The message m is encrypted with public key and outputs ciphertext , where .
- : For the ciphertext , secret key is used for decryption, and the output message is .
- : For two ciphertexts and , whose corresponding plaintexts are , wherethe additive homomorphism property is described as follows:In particular, given a constant , we have , where
3.2. Linear Homomorphic Encryption (LHE)
- : The security parameter is taken as input. Two -bit large prime numbers q and are chosen. Set , and there is a cyclotomic polynomial . is the discrete Gaussian distribution over the ring . The public parameters ={} are obtained as outputs.
- : The public parameter is taken as input. A ring element is a sample, and the secret key is obtained as an output.
- : For a message , is taken as a sample, and the output ciphertext is .
- : The ciphertext is decrypted with the secret key , and the output is obtained.
- : Given d coefficients and d ciphertexts , the linear homomorphism property is described as follows:
3.3. Homomorphic Proxy Re-Encryption (HPRE)
- : The security parameter is taken as input. is run to generate . Then, the output is obtained.
- : The public parameter is taken as input. is run twice to generate , , which stands for the public/secret key pair of the data owner and data receiver, respectively. Then, the output is obtained.
- : For a message , the data owner runs to output the ciphertext , where . Then, the output is .
- : The data owner’s secret key and the data receiver’s secret key are taken as input, and the re-encryption key = = is the output.
- : The re-encryption key and the ciphertext are taken as inputs, and the re-encryption ciphertext is obtained as the output, where
- : The ciphertext is decrypted with the data receiver’s secret key , and the output is .
3.4. Verifiable Matrix-Vector Multiplication (VerM)
- : The security parameter is taken as input, and a -bit large prime number q is chosen. Let be a finite field and be a cyclic group of generator g and order q. Let be integers, and then output .
- : The function owner takes their matrix , where is the set of all matrices over as input to generate the public verification data (once and for all). A vector is uniformly sampled, and is computed. The obtained output is , where , .
- : The function and the input are taken as inputs. The result is obtained.
- : The public verification data , the input and the result are taken as input. This convinces the user to accept the result if and only ifIf the equation is valid, then the output is 1; otherwise, the output is 0.
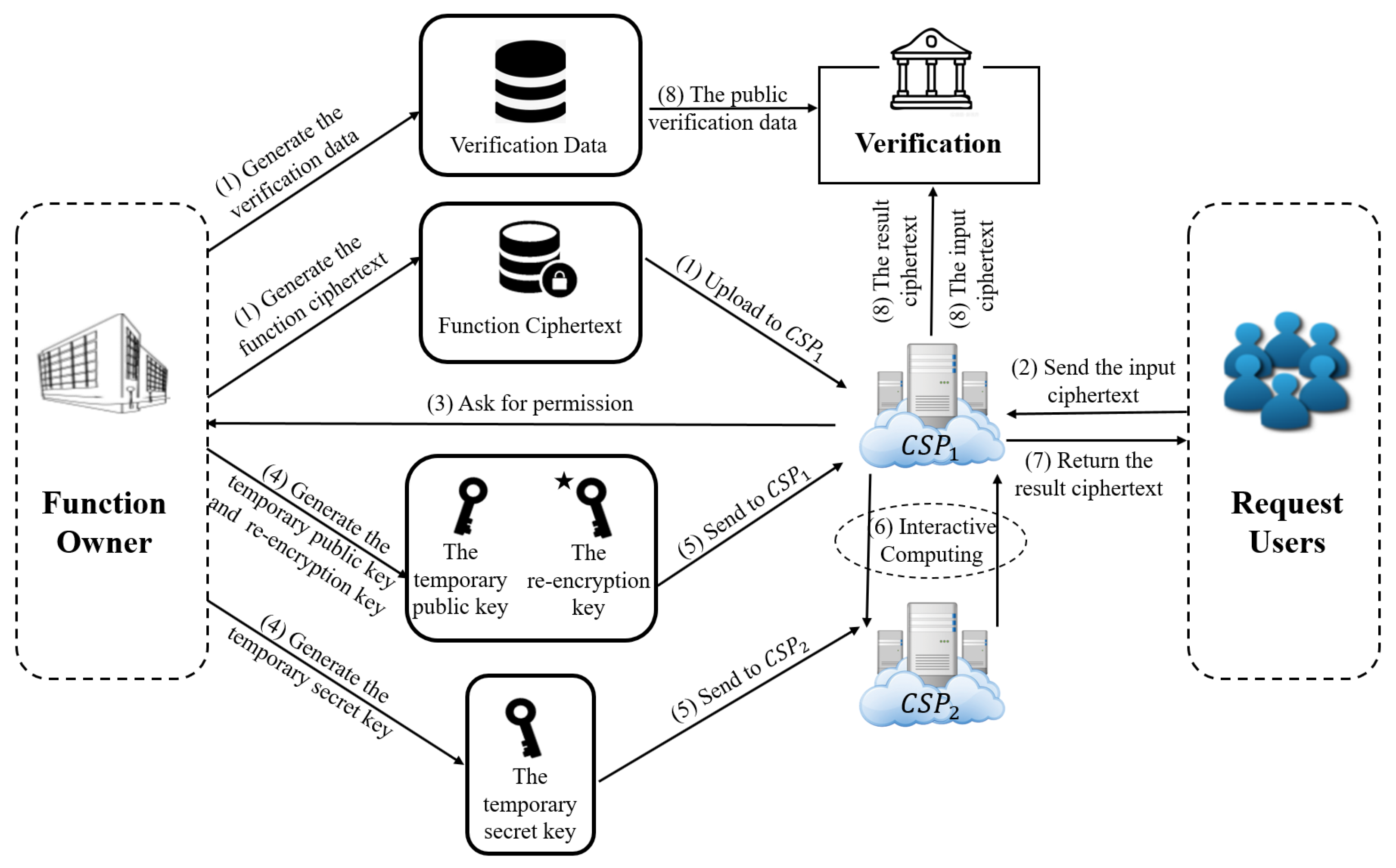
4. System Model and Design Goals
4.1. System Model
- Preparation:
- (1)
- The function owner encrypts the function parameters and prepares the public verification data. Then, they upload the function’s ciphertext to the cloud service provider .
- (2)
- A request user encrypts their input when they request to perform the computation.
- (3)
- When receives the request from the user, it asks the function owner for permission.
- (4)
- The function owner generates a temporary public/secret key pair and a re-encryption key when they permit the use of their function.
- (5)
- The function owner sends the temporary public key and the re-encryption key to and sends the temporary secret key to .
- Computation:
- (6)
- re-encrypts the original function ciphertext with a mask. Then, the new ciphertext can be decrypted by with the temporary secret key. then collaborates with to complete the computation.
- (7)
- returns the result ciphertext to the user.
- Verification:
- (8)
- The public verification is performed using the public verification data, the input ciphertext and the result ciphertext. Simultaneously, the user decrypts the result ciphertext and verifies the result privately in a fast way with the public verification data and the plaintexts of their input and result.
4.2. Design Goals
- Maintain function privacy: The function ciphertext and public verification data cannot reveal any information about the function, so the encryption schemes that we use should be semantically secure so that no adversary can infer any information from the obtained ciphertext.
- Maintain input privacy. Similarly, the input ciphertext must not reveal information about the input. The encryption scheme for the input, thus, needs to be semantically secure.
- Maintain result privacy. No one should be able to obtain information about the result plaintext except for the request user. The result ciphertext cannot be distinguished from the random elements.
- Achieve public verification. Anyone can complete the verification with the publicly available information, and there is no malicious CSP that can persuade the public to accept an incorrect result with a non-negligible probability. We assume that the public has limited computational resources, and so verification must be efficient.
- Ensure the function owner’s control over the function. CSPs cannot complete the computation if the function owner does not allow the user to use their function model.
5. The Proposed Solution
5.1. Preparation
- The key pair of preparation steps for the function owner:
- -
- Run to generate .
- -
- Run to generate =.
- The function owner encrypts the matrix and uploads it to :
- -
- For each element in the matrix , , runto generate , where .
- -
- Upload to .
- The function owner generates the verification data :
- -
- Run to generate . It holds that,,where and .
- The request user encrypts the input vector and sends it to :
- -
- Run to generate the public parameters for the request user.
- -
- Run to generate the secret key for the request user.
- -
- For each in the input vector , , run to generate the ciphertext , where and .
- -
- The user sends the ciphertext to and requests computation.
- asks the function owner for permission.
- The function owner will generate a temporary key pair and a re-encryption key if permission is granted:
- -
- The function owner runs again to generate a temporary public/secret key pair .
- -
- Run to generate a re-encryption key .
- -
- The function owner sends and to and sends to .
5.2. Computation
- re-encrypts the matrix ciphertext:
- -
- For each element in the matrix ciphertext , , runs to re-encrypt into , where, .Then, .
- sends the re-encryption ciphertext with a mask to :
- -
- For each element in , , samples as the mask.
- -
- For each mask , run with the temporary key to generate , where .
- -
- For , run to generate the masked ciphertext .
- -
- sends the masked ciphertext and the user’s input ciphertext to .
- computes the final result’s first part :
- -
- Parse as a -size matrix and write to index the -th element.
- -
- For , run to generate . The first part of the final result is .
- performs the decryption for the masked ciphertext:
- -
- After receiving the masked ciphertext , for , runs to generate the masked matrix parameters .
- -
- Parse as an -size matrix and write to index the -th element. It holds that =.
- computes the second part of the final result :
- -
- For , run to generate . Then, send the second part of the final result to .
- computes the final result and returns it to the user:
- -
- For computes . Then, the final result = is returned to the user.
5.3. Verification
- Public Verification:
- -
- The public runs . It outputs 1 if and only if
- Private Verification:
- -
- After the user receives the result ciphertext =, for , they run to generate the plaintext , where . The final result plaintext is .
- -
- Run . It outputs 1 if and only if
5.4. The Extension Method for Arbitrary Polynomial Functions
5.4.1. Univariate Polynomials
5.4.2. Multivariate Polynomials
6. Results
6.1. Correctness Analysis
- Correctness of the result ciphertext from . Given the ciphertexts of the result and the input vector , for , it holds that:Let and , such that the following holds:We can see that the result corresponds to the multiplication of matrix and vector in plaintext.
- Correctness of decryption for the result ciphertext . Given the ciphertext of the result , wherefor , it holds that:We can see that the decryption for the result ciphertext is correct.
- Correctness of public verification.Given the input vector ciphertext , the result ciphertext and the public verification data , wherefor , it convinces the public to accept the result if and only if:The left side is:and the right side is:If , then Equation (22) holds.
- Correctness of private verification.The correctness of private verification is consistent with the description provided in Section 3.4.
6.2. Security Analysis
- HE. The scheme is based on the hardness of the Decisional Composite Residuosity Assumption and Decisional Diffie–Hellman Assumption, which is stated below:Definition 1.(Decisional Composite Residuosity Problem [26]) Given a composite n and an integer z, decide if z is an modulo or not, namely, if there exists y such that .Definition 2.(Decisional Diffie–Hellman Problem [24]) Let g be an element of prime order in a cyclic group . Given , decide whether or not .Theorem 1.The scheme is semantically secure if and only if the Decisional Composite Residuosity Assumption and Decisional Diffie–Hellman Assumption hold.
- LHE. The security is established in [3], and we state it below:Theorem 2.LHE is linearly homomorphic as long as .Theorem 3.Let and for some . The scheme is semantically secure under the worst-case hardness of approximating the shortest vectors on ideal lattices to within a factor of .
- HPRE. It is based on the security of HE.
- VerM. It is based on the hardness of the Discrete Logarithm Assumption [9]. It will pass the verification by mistake with a probability of at most, which is negligible when q is a -bit prime. It is stated below:Definition 3.(Discrete Logarithm Problem) Let g be an element of prime order in a cyclic group . Given , compute x such that .Theorem 4.The scheme is semantically secure if and only if the Discrete Logarithm Assumption holds.
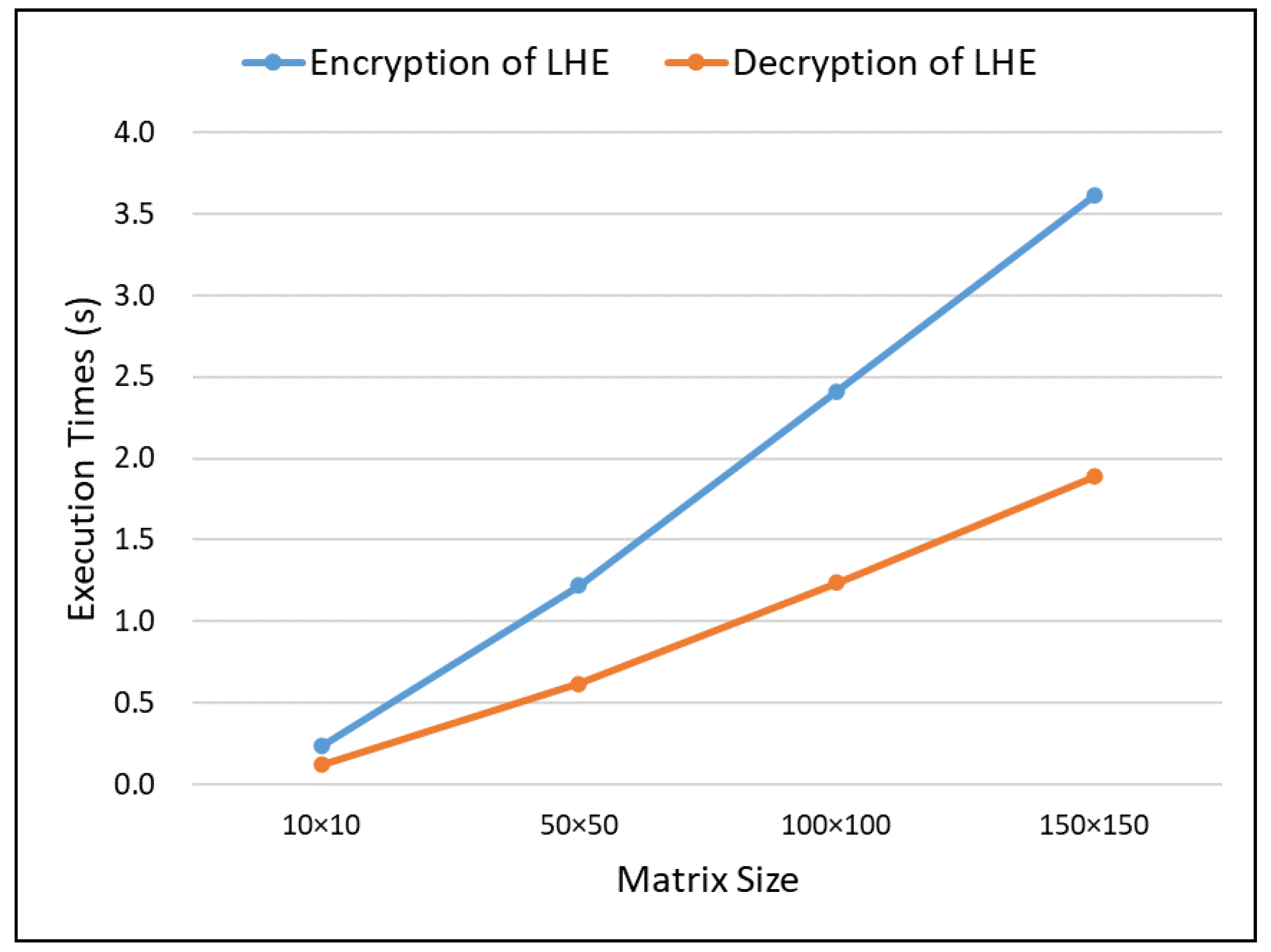
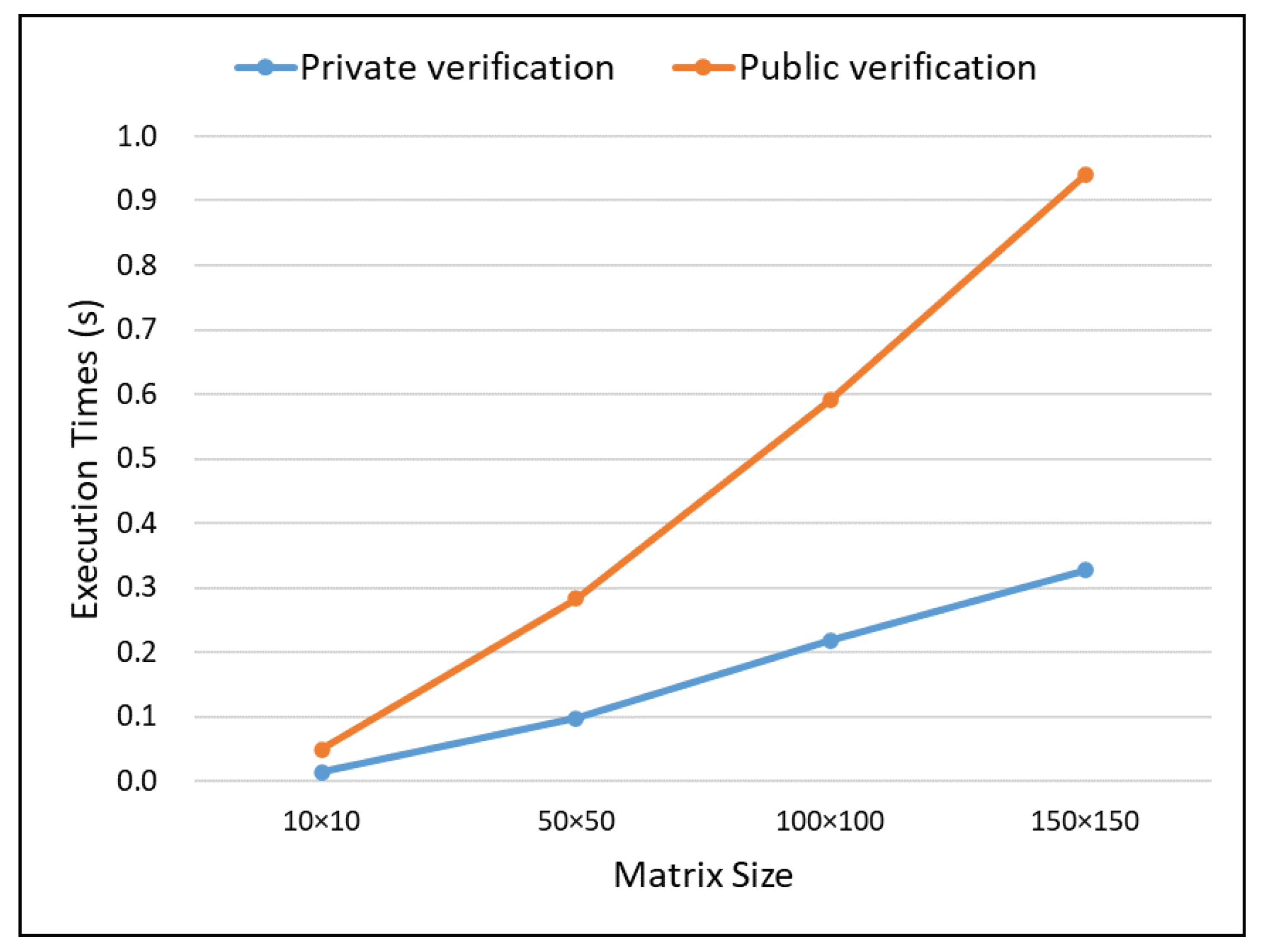
6.3. Experimental Results
7. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Rivest, R.L.; Adleman, L.; Dertouzos, M.L. On data banks and privacy homomorphisms. Found. Secur. Comput. 1978, 4, 169–180. [Google Scholar]
- Gentry, C. Fully homomorphic encryption using ideal lattices. In Proceedings of the 41st Annual ACM Symposium on Theory of Computing, STOC 2009, Bethesda, MD, USA, 31 May–2 June 2009; Mitzenmacher, M., Ed.; ACM: New York, NY, USA, 2009; pp. 169–178. [Google Scholar]
- Brakerski, Z.; Vaikuntanathan, V. Fully Homomorphic Encryption from Ring-LWE and Security for Key Dependent Messages. In Proceedings of the Advances in Cryptology—CRYPTO 2011—31st Annual Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2011; Rogaway, P., Ed.; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2011; Volume 6841, pp. 505–524. [Google Scholar] [CrossRef]
- Yao, C.C. How to generate and exchange secrets. In Proceedings of the 27th Annual Symposium on Foundations of Computer Science, Toronto, ON, Canada, 27–29 October 1986; IEEE Computer Society: Washington, DC, USA, 1986; pp. 162–167. [Google Scholar]
- Demmler, D.; Schneider, T.; Zohner, M. ABY—A Framework for Efficient Mixed-Protocol Secure Two-Party Computation. In Proceedings of the 22nd Annual Network and Distributed System Security Symposium, NDSS 2015, San Diego, CA, USA, 8–11 February 2015; The Internet Society: Reston, VA, USA, 2015. [Google Scholar]
- Feng, D.; Yang, K. Concretely efficient secure multi-party computation protocols: Survey and more. Secur. Saf. 2022, 1, 2021001. [Google Scholar] [CrossRef]
- Papamanthou, C.; Shi, E.; Tamassia, R. Signatures of Correct Computation. In Proceedings of the Theory of Cryptography—10th Theory of Cryptography Conference, TCC 2013, Tokyo, Japan, 3–6 March 2013; Volume 7785, pp. 222–242. [Google Scholar]
- Parno, B.; Raykova, M.; Vaikuntanathan, V. How to Delegate and Verify in Public: Verifiable Computation from Attribute-Based Encryption. In Proceedings of the Theory of Cryptography—9th Theory of Cryptography Conference, TCC 2012, Taormina, Italy, 19–21 March 2012; Volume 7194, pp. 422–439. [Google Scholar]
- Zhang, L.F.; Safavi-Naini, R. Protecting data privacy in publicly verifiable delegation of matrix and polynomial functions. Des. Codes Cryptogr. 2020, 88, 677–709. [Google Scholar] [CrossRef]
- Applebaum, B.; Ishai, Y.; Kushilevitz, E. From Secrecy to Soundness: Efficient Verification via Secure Computation. In Proceedings of the 37th International Colloquium Conference on Automata, Languages and Programming, ICALP 2010, Bordeaux, France, 6–10 July 2010; Springer: Berlin/Heidelberg, Germany, 2010. Part I. Volume 6198, pp. 152–163. [Google Scholar]
- Barbosa, M.; Farshim, P. Delegatable Homomorphic Encryption with Applications to Secure Outsourcing of Computation. In Proceedings of the Topics in Cryptology—CT-RSA 2012—The Cryptographers’ Track at the RSA Conference 2012, San Francisco, CA, USA, 27 February–2 March 2012; Springer: Berlin/Heidelberg, Germany, 2012; Volume 7178, pp. 296–312. [Google Scholar]
- Chung, K.M.; Kalai, Y.T.; Vadhan, S.P. Improved Delegation of Computation using Fully Homomorphic Encryption. In Advances in Cryptology—CRYPTO 2010, Proceedings of the 30th Annual Cryptology Conference, Santa Barbara, CA, USA, 15–19 August 2010; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2010; Volume 6223, pp. 483–501. [Google Scholar]
- Fiore, D.; Gennaro, R.; Pastro, V. Efficiently Verifiable Computation on Encrypted Data. In Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security, Scottsdale, AZ, USA, 3–7 November 2014; ACM: New York, NY, USA, 2014; pp. 844–855. [Google Scholar]
- Joo, C.; Yun, A. Homomorphic authenticated encryption secure against chosen-ciphertext attack. In Proceedings of the Advances in Cryptology–ASIACRYPT 2014: 20th International Conference on the Theory and Application of Cryptology and Information Security, Kaoshiung, Taiwan, 7–11 December 2014; Springer: Berlin/Heidelberg, Germany, 2014. Part II 20. pp. 173–192. [Google Scholar]
- Libert, B.; Peters, T.; Joye, M.; Yung, M. Linearly Homomorphic Structure-Preserving Signatures and Their Applications. In Proceedings of the Advances in Cryptology—CRYPTO 2013—33rd Annual Cryptology Conference, Santa Barbara, CA, USA, 18–22 August 2013; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2013. Part II. Volume 8043, pp. 289–307. [Google Scholar]
- Zhang, L.F. Multi-server verifiable delegation of computations: Unconditional security and practical efficiency. Inf. Comput. 2021, 281, 104740. [Google Scholar] [CrossRef]
- Catalano, D.; Fiore, D.; Gennaro, R.; Vamvourellis, K. Algebraic (trapdoor) one-way functions and their applications. In Proceedings of the Theory of Cryptography: Tenth Theory of Cryptography Conference, TCC 2013, Tokyo, Japan, 3–6 March 2013; Springer: Berlin/Heidelberg, Germany, 2013; pp. 680–699. [Google Scholar]
- Elkhiyaoui, K.; Önen, M.; Azraoui, M.; Molva, R. Efficient Techniques for Publicly Verifiable Delegation of Computation. In Proceedings of the 11th ACM on Asia Conference on Computer and Communications Security, AsiaCCS 2016, Xi’an, China, 30 May–3 June 2016; ACM: New York, NY, USA, 2016; pp. 119–128. [Google Scholar]
- Fiore, D.; Gennaro, R. Publicly verifiable delegation of large polynomials and matrix computations, with applications. In Proceedings of the ACM Conference on Computer and Communications Security, CCS’12, Raleigh, NC, USA, 16–18 October 2012; ACM: New York, NY, USA, 2012; pp. 501–512. [Google Scholar] [CrossRef]
- Beimel, A. Secure Schemes for Secret Sharing and Key Distribution. Ph.D. Thesis, Technion—Israel Institute of Technology, Haifa, Israel, 1996. [Google Scholar]
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute-based encryption for fine-grained access control of encrypted data. In Proceedings of the 13th ACM Conference on Computer and Communications Security, CCS 2006, Alexandria, VA, USA, 30 October–3 November 2006; ACM: New York, NY, USA, 2006; pp. 89–98. [Google Scholar]
- Peter, A.; Tews, E.; Katzenbeisser, S. Efficiently Outsourcing Multiparty Computation Under Multiple Keys. IEEE Trans. Inf. Forensics Secur. 2013, 8, 2046–2058. [Google Scholar] [CrossRef]
- Liu, X.; Robert, H.; Deng, K.K.R.C.; Weng, J. An Efficient Privacy-Preserving Outsourced Calculation Toolkit With Multiple Keys. IEEE Trans. Comput. 2016, 65, 3567–3579. [Google Scholar] [CrossRef]
- Bresson, E.; Catalano, D.; Pointcheval, D. A Simple Public-Key Cryptosystem with a Double Trapdoor Decryption Mechanism and Its Applications. In Proceedings of the Advances in Cryptology—ASIACRYPT 2003, Ninth International Conference on the Theory and Application of Cryptology and Information Security, Taipei, Taiwan, 30 November–4 December 2003; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2003; Volume 2894, pp. 37–54. [Google Scholar]
- Kawai, Y.; Matsuda, T.; Hirano, T.; Koseki, Y.; Hanaoka, G. Proxy Re-Encryption That Supports Homomorphic Operations for Re-Encrypted Ciphertexts. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 2019, 102-A, 81–98. [Google Scholar] [CrossRef]
- Paillier, P. Public-Key Cryptosystems Based on Composite Degree Residuosity Classes. In Proceedings of the Advances in Cryptology—EUROCRYPT ’99, International Conference on the Theory and Application of Cryptographic Techniques, Prague, Czech Republic, 2–6 May 1999; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 1999; Volume 1592, pp. 223–238. [Google Scholar] [CrossRef]
- Gamal, T.E. A public key cryptosystem and a signature scheme based on discrete logarithms. IEEE Trans. Inf. Theory 1985, 31, 469–472. [Google Scholar] [CrossRef]
- Goldwasser, S.; Micali, S. Probabilistic Encryption. J. Comput. Syst. Sci. 1984, 28, 270–299. [Google Scholar] [CrossRef]
- Brakerski, Z.; Gentry, C.; Vaikuntanathan, V. (Leveled) Fully Homomorphic Encryption without Bootstrapping. ACM Trans. Comput. Theory 2014, 6, 1–36. [Google Scholar]
- Zhou, H.; Wornell, G.W. Efficient homomorphic encryption on integer vectors and its applications. In Proceedings of the 2014 Information Theory and Applications Workshop, ITA 2014, San Diego, CA, USA, 9–14 February 2014; pp. 1–9. [Google Scholar]
- Blaze, M.; Bleumer, G.; Strauss, M. Divertible Protocols and Atomic Proxy Cryptography. In Proceedings of the Advances in Cryptology—EUROCRYPT ’98, International Conference on the Theory and Application of Cryptographic Techniques, Espoo, Finland, 31 May–4 June 1998; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 1998; Volume 1403, pp. 127–144. [Google Scholar]
- Blum, M.; Luby, M.; Rubinfeld, R. Self-Testing/Correcting with Applications to Numerical Problems. In Proceedings of the 22nd Annual ACM Symposium on Theory of Computing, Baltimore, MD, USA, 13–17 May 1990; ACM: New York, NY, USA, 1990; pp. 73–83. [Google Scholar] [CrossRef]
- Blum, M.; Wasserman, H. Program Result-Checking: A Theory of Testing Meets a Test of Theory. In Proceedings of the 35th Annual Symposium on Foundations of Computer Science, Santa Fe, NM, USA, 20–22 November 1994; IEEE Computer Society: Washington, DC, USA, 1994; pp. 382–392. [Google Scholar] [CrossRef]




| Study Ref./No | Function Privacy/Input Privacy | Private Verification | Public Verification |
|---|---|---|---|
| [10,11,12] | ✓/✓ | ✓ | × |
| [13,14,15] | ✓/✓ | ✓ | × |
| [16] | ✓/✓ | ✓ | × |
| [7,8,17,18,19] | ×/× | ✓ | ✓ |
| [9] | ✓/× or ×/✓ | ✓ | ✓ |
| Our scheme | ✓/✓ | ✓ | ✓ |
| Notations | Descriptions |
|---|---|
| The lowercase bold letters denote vectors where indexes the i-th element | |
| The uppercase bold letters denote matrices where indexes the -th element | |
| The transpose of vector | |
| The dot product of two vectors, and , where | |
| The matrix–vector multiplication of and | |
| Uniformly sample x from a set S at random. | |
| The set of all natural numbers | |
| The set , where | |
| The security parameter | |
| The odd primes | |
| A group under addition modulo N | |
| A group satisfies , where | |
| The set of all matrices over | |
| The cyclic group with generator g | |
| The m-th cyclotomic polynomial, where | |
| The ring of integer polynomials modulo | |
| The ring R with coefficients modulo p | |
| The discrete Gaussian distribution over the ring | |
| The key pair of public key and secret key |
| Data | Size |
|---|---|
| Matrix | |
| Verification data | |
| Verification data | |
| Vector | |
| The final result |
| Sender | Receiver | Phase | Communication Cost |
|---|---|---|---|
| Function owner | Preparation | (Once for all) | |
| Function owner | The public | Preparation | (Once for all) |
| Function owner | Preparation | ||
| Function owner | Preparation | ||
| Request User | Preparation | ||
| Function owner | Preparation | Permission Message | |
| Computation | |||
| Request User | Computation | ||
| The public | Verification | ||
| Computation |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Song, B.; Zhou, D.; Wu, J.; Yuan, X.; Zhu, Y.; Wang, C. Protecting Function Privacy and Input Privacy in the Publicly Verifiable Outsourcing Computation of Polynomial Functions. Future Internet 2023, 15, 152. https://doi.org/10.3390/fi15040152
Song B, Zhou D, Wu J, Yuan X, Zhu Y, Wang C. Protecting Function Privacy and Input Privacy in the Publicly Verifiable Outsourcing Computation of Polynomial Functions. Future Internet. 2023; 15(4):152. https://doi.org/10.3390/fi15040152
Chicago/Turabian StyleSong, Beibei, Dehua Zhou, Jiahe Wu, Xiaowei Yuan, Yiming Zhu, and Chuansheng Wang. 2023. "Protecting Function Privacy and Input Privacy in the Publicly Verifiable Outsourcing Computation of Polynomial Functions" Future Internet 15, no. 4: 152. https://doi.org/10.3390/fi15040152
APA StyleSong, B., Zhou, D., Wu, J., Yuan, X., Zhu, Y., & Wang, C. (2023). Protecting Function Privacy and Input Privacy in the Publicly Verifiable Outsourcing Computation of Polynomial Functions. Future Internet, 15(4), 152. https://doi.org/10.3390/fi15040152







