Knowledge Distillation-Based GPS Spoofing Detection for Small UAV
Abstract
:1. Introduction
2. Related Work
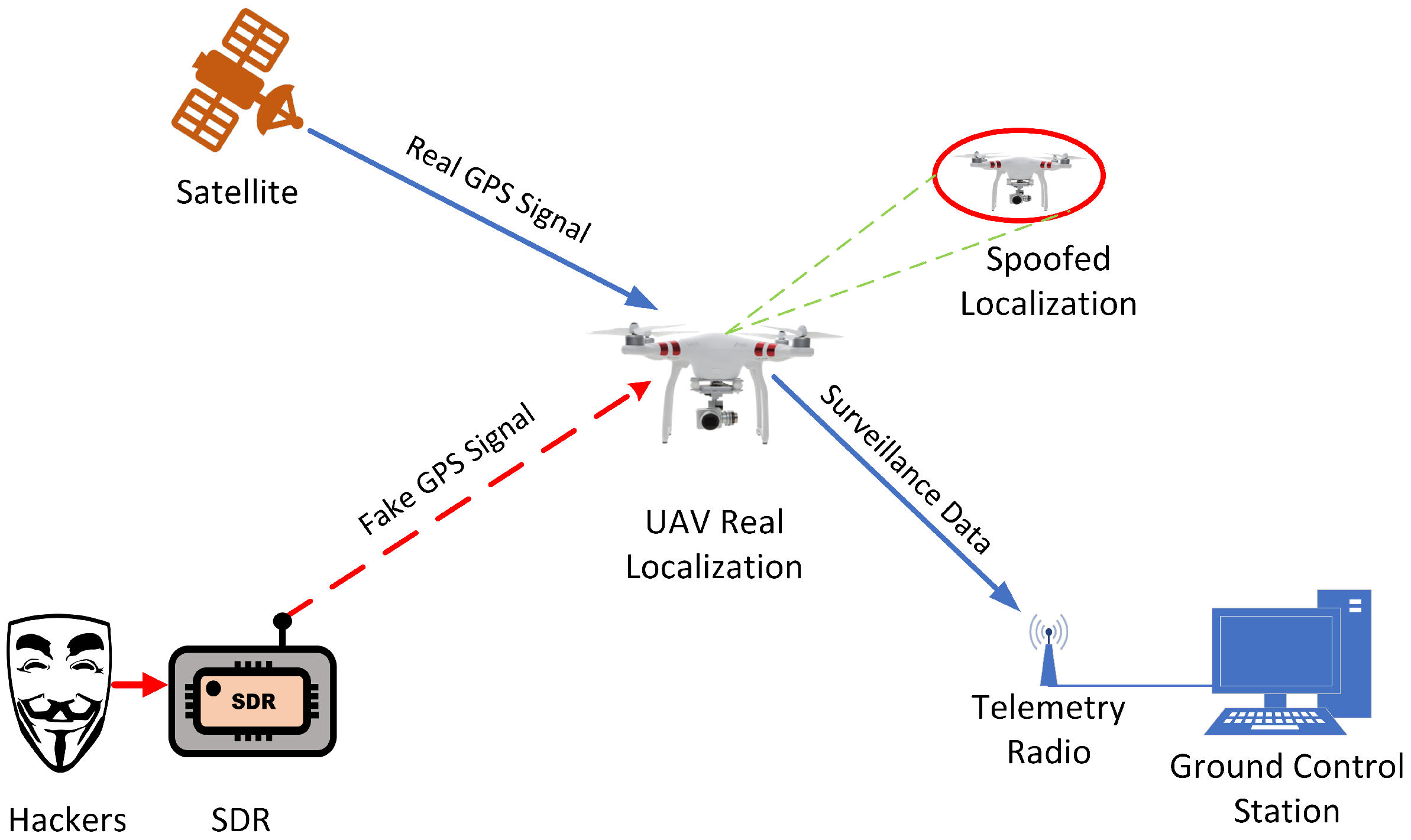
2.1. GPS Spoofing in UAVs
2.2. Knowledge Distillation
3. System Modeling
4. Problem Statement
5. Methodology
5.1. Long-Short Term Memory (LSTM)-Based Detection
| Algorithm 1: GPS spoofing detection |
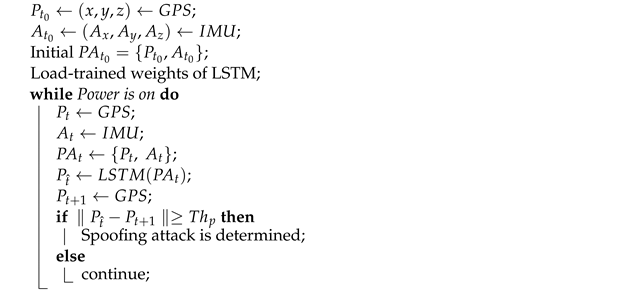 |
5.2. KD-Enabled Lightweight Detection
6. Evaluation
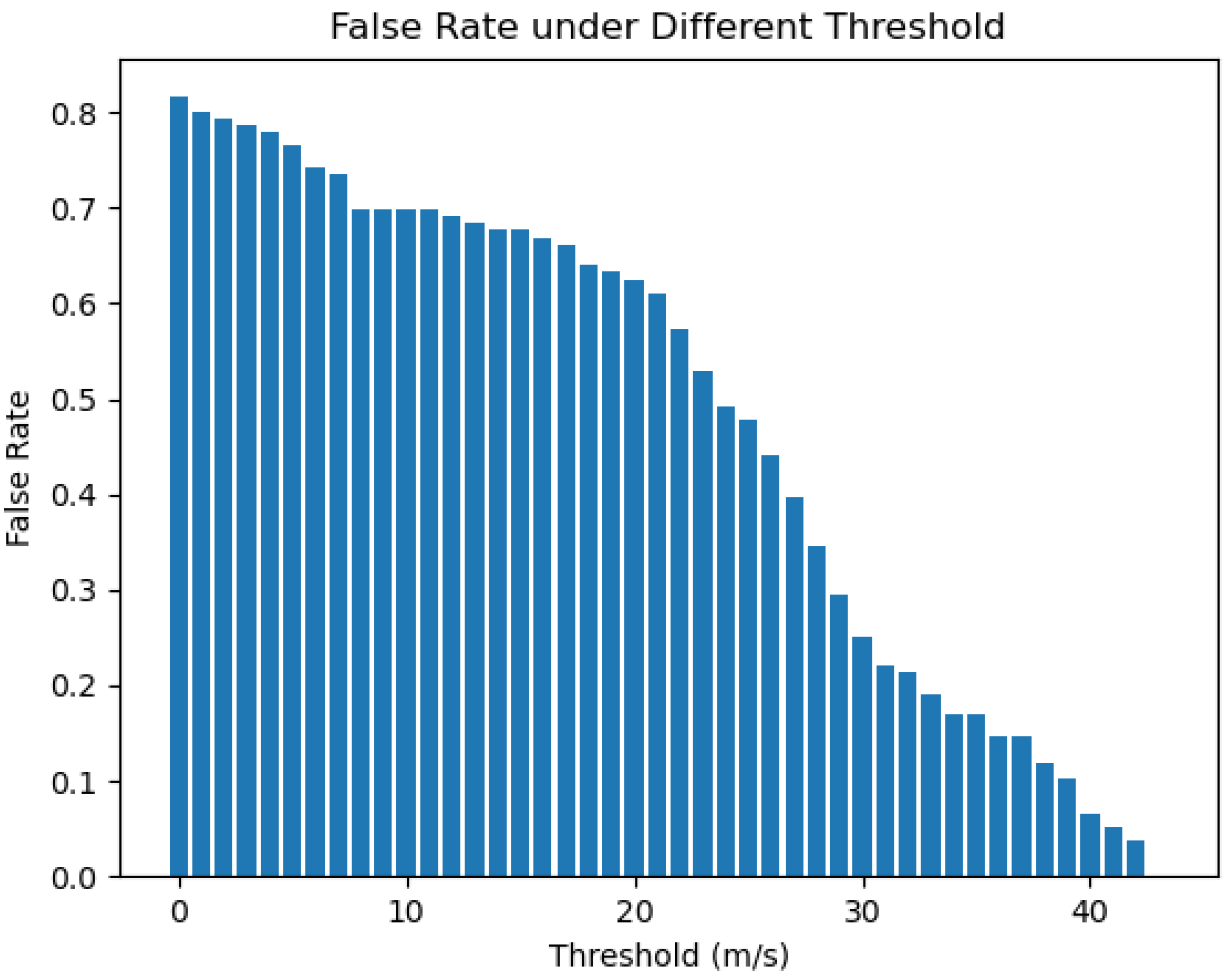
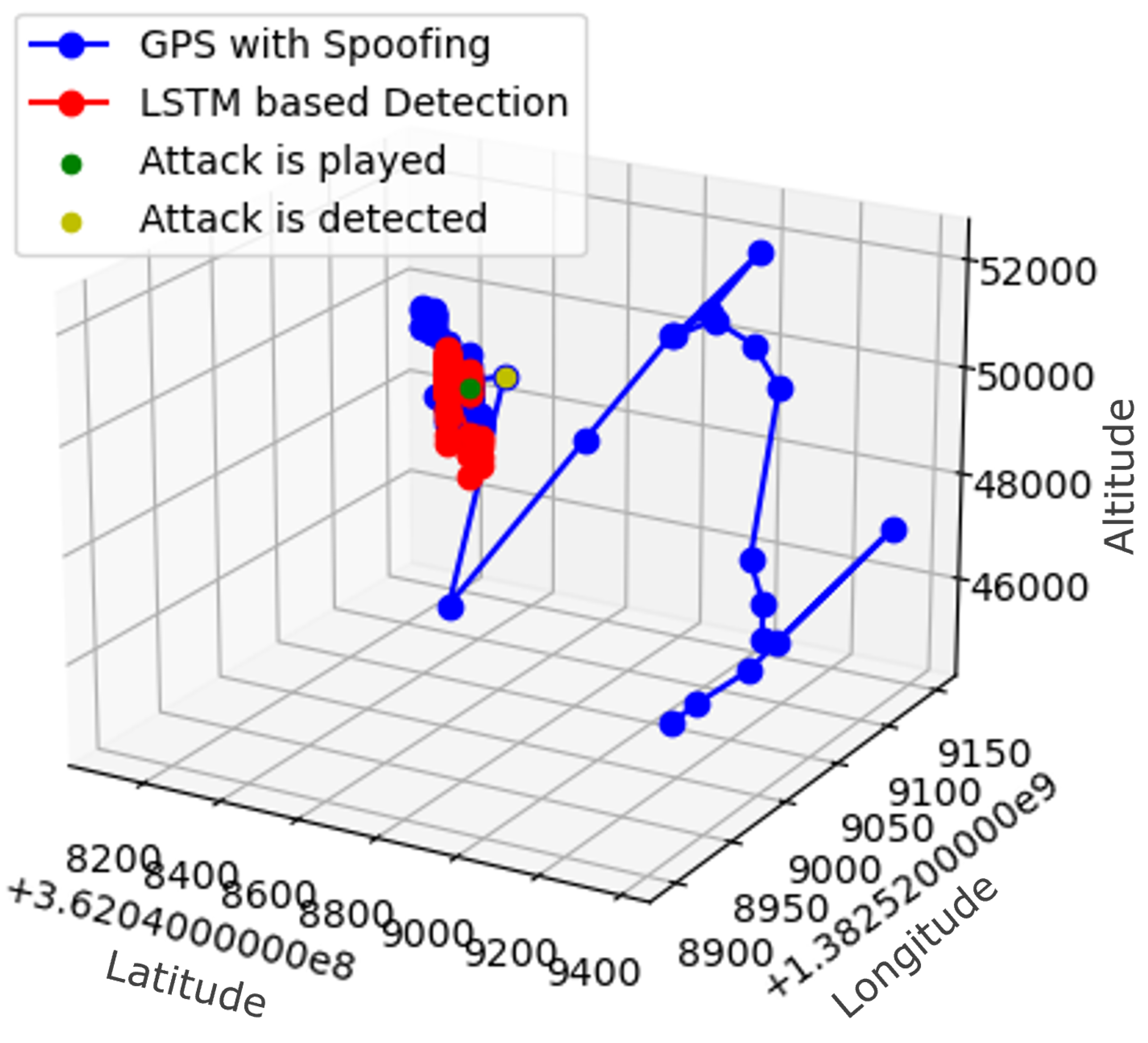
6.1. GPS Spoofing Detection
6.2. Lightweight Detection
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A. Symbol Summary
| Symbols | Definition |
|---|---|
| The signal a GPS module received. | |
| GPS location: . | |
| The forged GPS signal. | |
| Acceleration of UAV at time k. | |
| Acceleration of UAV in x, y, and z axis at time k. | |
| Rotation of UAV at time k. | |
| Rotation of UAV in yaw, pitch, roll at time k. | |
| The received signal strength indicator (RSSI). | |
| Position at time t’ and t. | |
| v | The speed of UAV. |
| A | Acceleration of UAV. |
| N | Thermal noise and zero drift. |
| Threshold of UAV movement. | |
| Combination of and . | |
| , , and | Weight matrices for the input gate. |
| Cell activation vectors. | |
| Cell activation output vector. | |
| Bias for the input layer. | |
| Logistic sigmoid function. | |
| , , and | Weight matrices for the forget gate. |
| Bias for forget layer. | |
| ⊙ | The Hadamard product. |
| g | Cell input activation function. |
| Weight matrices for the cell state. | |
| Bias for cell state. | |
| , , and | Weight matrices for the output gates. |
| Bias for forget layer. | |
| Output activation vector. | |
| Cell output activation function. | |
| Weight matrices for the final result. | |
| The teacher model. | |
| A student model. | |
| The loss functions of the student model vs. the teacher model. | |
| The loss functions of the student model vs. the real positions. |
References
- Qiu, H.; Qiu, M.; Liu, M.; Memmi, G. Secure Health Data Sharing for Medical Cyber-Physical Systems for the Healthcare 4.0. IEEE J. Biomed. Health Inform. 2020, 24, 2499–2505. [Google Scholar] [CrossRef] [PubMed]
- Liu, R.; Zhang, Y.; Ge, Y.; Hu, W.; Sha, B. Precision Regulation Model of Water and Fertilizer for Alfalfa Based on Agriculture Cyber-Physical System. IEEE Access 2020, 8, 38501–38516. [Google Scholar] [CrossRef]
- Wang, K.; Yuan, L.; Miyazaki, T.; Chen, Y.; Zhang, Y. Jamming and Eavesdropping Defense in Green Cyber–Physical Transportation Systems Using a Stackelberg Game. IEEE Trans. Ind. Inform. 2018, 14, 4232–4242. [Google Scholar] [CrossRef]
- Siozios, K.; Soudris, D.; Kosmatopoulos, E. An Overview of Emerging Systems-Related Concepts, Approaches and Technologies Unifying and Advancing S&T Achievements of the Past Decades (e.g., CPS, IoT, I2oT, SoS/E, 5G and Cross-Cutting Decision Making). In Cyber-Physical Systems: Decision Making Mechanisms and Applications; IEEE: Piscataway, NJ, USA, 2017; pp. 1–98. [Google Scholar]
- Lu, H.; Duan, X. Collaborative Computing for Space-Air-Ground Integrated Vehicular Networks. In Proceedings of the 2021 International Conference on Space-Air-Ground Computing (SAGC), Huizhou, China, 23–25 October 2021; pp. 175–177. [Google Scholar] [CrossRef]
- Zhou, Z.; Zhang, C.; Xu, C.; Xiong, F.; Zhang, Y.; Umer, T. Energy-Efficient Industrial Internet of UAVs for Power Line Inspection in Smart Grid. IEEE Trans. Ind. Inform. 2018, 14, 2705–2714. [Google Scholar] [CrossRef]
- Bacco, M.; Berton, A.; Gotta, A.; Caviglione, L. IEEE 802.15.4 Air-Ground UAV Communications in Smart Farming Scenarios. IEEE Commun. Lett. 2018, 22, 1910–1913. [Google Scholar] [CrossRef]
- Eldosouky, A.; Ferdowsi, A.; Saad, W. Drones in Distress: A Game-Theoretic Countermeasure for Protecting UAVs Against GPS Spoofing. IEEE Internet Things J. 2020, 7, 2840–2854. [Google Scholar] [CrossRef]
- Dang, Y.; Benzaïd, C.; Shen, Y.; Taleb, T. GPS Spoofing Detector with Adaptive Trustable Residence Area for Cellular based-UAVs. In Proceedings of the GLOBECOM 2020-2020 IEEE Global Communications Conference, Taipei, Taiwan, 7–11 December 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Ahmad, M.; Farid, M.A.; Ahmed, S.; Saeed, K.; Asharf, M.; Akhtar, U. Impact and Detection of GPS Spoofing and Countermeasures against Spoofing. In Proceedings of the 2019 2nd International Conference on Computing, Mathematics and Engineering Technologies (iCoMET), Sukkur, Pakistan, 30–31 January 2019; pp. 1–8. [Google Scholar] [CrossRef]
- Dang, Y.; Benzaïd, C.; Yang, B.; Taleb, T. Deep Learning for GPS Spoofing Detection in Cellular-Enabled UAV Systems. In Proceedings of the 2021 International Conference on Networking and Network Applications (NaNA), Lijiang, China, 29 October–1 November 2021; pp. 501–506. [Google Scholar] [CrossRef]
- Dey, V.; Pudi, V.; Chattopadhyay, A.; Elovici, Y. Security Vulnerabilities of Unmanned Aerial Vehicles and Countermeasures: An Experimental Study. In Proceedings of the 2018 31st International Conference on VLSI Design and 2018 17th International Conference on Embedded Systems (VLSID), Pune, India, 6–10 January 2018; pp. 398–403. [Google Scholar] [CrossRef]
- Ranyal, E.; Jain, K. Unmanned Aerial Vehicle’s Vulnerability to GPS Spoofing a Review. J. Indian Soc. Remote Sens. 2020, 49, 585–591. [Google Scholar] [CrossRef]
- Kerns, A.J.; Shepard, D.P.; Bhatti, J.A.; Humphreys, T.E. Unmanned Aircraft Capture and Control Via GPS Spoofing. J. Field Robot. 2014, 31, 617–636. [Google Scholar] [CrossRef]
- Qiao, Y.; Zhang, Y.; Du, X. A Vision-Based GPS-Spoofing Detection Method for Small UAVs. In Proceedings of the 2017 13th International Conference on Computational Intelligence and Security (CIS), Hong Kong, 15–17 December 2017; pp. 312–316. [Google Scholar] [CrossRef]
- Zou, Q.; Huang, S.; Lin, F.; Cong, M. Detection of GPS spoofing based on UAV model estimation. In Proceedings of the IECON 2016-42nd Annual Conference of the IEEE Industrial Electronics Society, Florence, Italy, 24–27 October 2016; pp. 6097–6102. [Google Scholar] [CrossRef]
- Gasimova, A.; Khoei, T.T.; Kaabouch, N. A Comparative Analysis of the Ensemble Models for Detecting GPS Spoofing attacks on UAVs. In Proceedings of the 2022 IEEE 12th Annual Computing and Communication Workshop and Conference (CCWC), Virtual Conference, 26–29 January 2022; pp. 0310–0315. [Google Scholar] [CrossRef]
- Panice, G.; Luongo, S.; Gigante, G.; Pascarella, D.; Di Benedetto, C.; Vozella, A.; Pescapè, A. A SVM-based detection approach for GPS spoofing attacks to UAV. In Proceedings of the 2017 23rd International Conference on Automation and Computing (ICAC), Huddersfield, UK, 7–8 September 2017; pp. 1–11. [Google Scholar] [CrossRef]
- Agyapong, R.A. Efficient Detection of GPS Spoofing Attacks on Unmanned Aerial Vehicles Using Deep Learning. In Proceedings of the 2021 IEEE Symposium Series on Computational Intelligence (SSCI), Orlando, FL, USA, 5–7 December 2021. [Google Scholar]
- Chen, X.; Li, T.; Liu, H.; Huang, Q.; Gan, X. A GPS Spoofing Detection Algorithm for UAVs Based on Trust Evaluation. In Proceedings of the 2023 IEEE 13th International Conference on CYBER Technology in Automation, Control, and Intelligent Systems (CYBER), Qinhuangdao, China, 11–14 July 2023; pp. 315–319. [Google Scholar] [CrossRef]
- Dang, Y.; Karakoc, A.; Norshahida, S.; Jäntti, R. 3D Radio Map-Based GPS Spoofing Detection and Mitigation for Cellular-Connected UAVs. IEEE Trans. Mach. Learn. Commun. Netw. 2023, 1, 313–327. [Google Scholar] [CrossRef]
- Demir, M.Ö.; Kurt, G.K.; Pusane, A.E. A Pseudorange-Based GPS Spoofing Detection Using Hyperbola Equations. IEEE Trans. Veh. Technol. 2023, 72, 10770–10783. [Google Scholar] [CrossRef]
- Gou, J.; Yu, B.; Maybank, S.J.; Tao, D. Knowledge Distillation: A Survey. Int. J. Comput. Vis. 2021, 129, 1789–1819. [Google Scholar] [CrossRef]
- Chen, P.; Liu, S.; Zhao, H.; Jia, J. Distilling Knowledge via Knowledge Review. In Proceedings of the 2021 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR), Los Alamitos, CA, USA, 20–25 June 2021; pp. 5006–5015. [Google Scholar] [CrossRef]
- Peng, B.; Jin, X.; Li, D.; Zhou, S.; Wu, Y.; Liu, J.; Zhang, Z.; Liu, Y. Correlation Congruence for Knowledge Distillation. In Proceedings of the 2019 IEEE/CVF International Conference on Computer Vision (ICCV), Los Alamitos, CA, USA, 27 October–2 November 2019; pp. 5006–5015. [Google Scholar] [CrossRef]
- Wang, L.; Yoon, K. Knowledge Distillation and Student-Teacher Learning for Visual Intelligence: A Review and New Outlooks. IEEE Trans. Pattern Anal. Mach. Intell. 2022, 44, 3048–3068. [Google Scholar] [CrossRef] [PubMed]
- Guo, J.; Chen, M.; Hu, Y.; Zhu, C.; He, X.; Cai, D. Reducing the Teacher-Student Gap via Spherical Knowledge Disitllation. arXiv 2020, arXiv:2010.07485. [Google Scholar] [CrossRef]
- Monti, A.; Porrello, A.; Calderara, S.; Coscia, P.; Ballan, L.; Cucchiara, R. How many Observations are Enough? Knowledge Distillation for Trajectory Forecasting. In Proceedings of the 2022 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR), Los Alamitos, CA, USA, 18–24 June 2022; pp. 6543–6552. [Google Scholar] [CrossRef]
- Luo, H.; Chen, T.; Li, X.; Li, S.; Zhang, C.; Zhao, G.; Liu, X. KeepEdge: A Knowledge Distillation Empowered Edge Intelligence Framework for Visual Assisted Positioning in UAV Delivery. IEEE Trans. Mob. Comput. 2022, 4729–4741. [Google Scholar] [CrossRef]
- Wang, Z.; Wei, Y.; Wu, F. Knowledge Distillation based Cooperative Reinforcement Learning for Connectivity Preservation in UAV Networks. In Proceedings of the 2021 International Conference on UK-China Emerging Technologies (UCET), Chengdu, China, 4–6 November 2021; pp. 171–176. [Google Scholar] [CrossRef]
- Yu, G. Data-Free Knowledge Distillation for Privacy-Preserving Efficient UAV Networks. In Proceedings of the 2022 6th International Conference on Robotics and Automation Sciences (ICRAS), Wuhan, China, 9–11 June 2022; pp. 52–56. [Google Scholar] [CrossRef]
- Nuand. bladeRF 2.0. Available online: https://github.com/Nuand/bladeRF.git (accessed on 8 November 2023).
- Martoyo, I.; Setiasabda, P.; Kanalebe, H.Y.; Uranus, H.P.; Pardede, M. Software Defined Radio for Education: Spectrum Analyzer, FM Receiver/Transmitter and GSM Sniffer with HackRF One. In Proceedings of the 2018 2nd Borneo International Conference on Applied Mathematics and Engineering (BICAME), Balikpapan, Indonesia, 10–11 December 2018; pp. 188–192. [Google Scholar] [CrossRef]
- Ebinuma, T. Gps-sdr-sim. Github. 2018. Available online: https://github.com/osqzss/gps-sdr-sim (accessed on 23 May 2021).
- Meng, X.; Fu, H.; Peng, L.; Liu, G.; Yu, Y.; Wang, Z.; Chen, E. D-LSTM: Short-Term Road Traffic Speed Prediction Model Based on GPS Positioning Data. IEEE Trans. Intell. Transp. Syst. 2022, 23, 2021–2030. [Google Scholar] [CrossRef]
- Kim, J.; Lee, H.; Kim, S.; Park, J.H. Real-Time Power System Transient Stability Prediction Using Convolutional Layer and Long Short-Term Memory. J. Electr. Eng. Technol. 2023, 18, 2723–2735. [Google Scholar] [CrossRef]
- Ludwig, N. 14 CFR Part 107 (UAS)–Drone Operators Are Not Pilots 14. Available online: https://www.suasnews.com/wp-content/uploads/2017/12/AS480-Research-Paper.pdf (accessed on 8 November 2023).
- Sak, H.; Senior, A.; Beaufays, F. Long Short-Term Memory Based Recurrent Neural Network Architectures for Large Vocabulary Speech Recognition. arXiv 2014, arXiv:1402.1128. [Google Scholar] [CrossRef]
- Whelan, J.; Sangarapillai, T.; Minawi, O.; Almehmadi, A.; El-Khatib, K. UAV Attack Dataset. IEEE Dataport 2020. [Google Scholar] [CrossRef]
- Liu, H.; Wu, H.; Sun, W.; Lee, I. Spatio-Temporal GRU for Trajectory Classification. In Proceedings of the 2019 IEEE International Conference on Data Mining (ICDM), Beijing, China, 8–11 November 2019; pp. 1228–1233. [Google Scholar] [CrossRef]
- Mosavi, M.R.; Sorkhi, M. An efficient method for optimum selection of GPS satellites set using Recurrent Neural Network. In Proceedings of the 2009 IEEE/ASME International Conference on Advanced Intelligent Mechatronics, Singapore, 14–17 July 2009; pp. 245–249. [Google Scholar] [CrossRef]
- Niu, S.; Liu, Y.; Wang, J.; Song, H. A Decade Survey of Transfer Learning (2010–2020). IEEE Trans. Artif. Intell. 2020, 1, 151–166. [Google Scholar] [CrossRef]
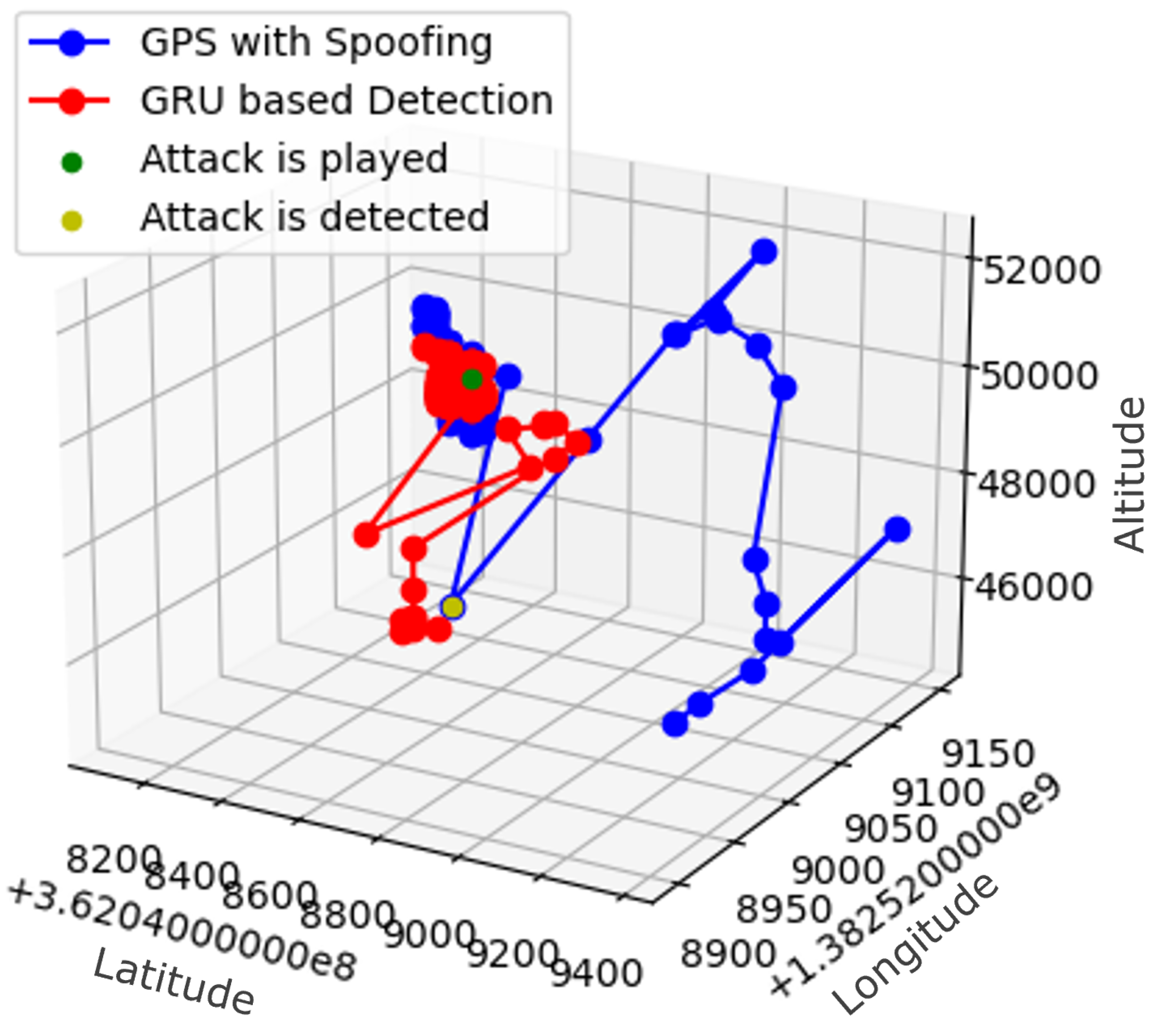
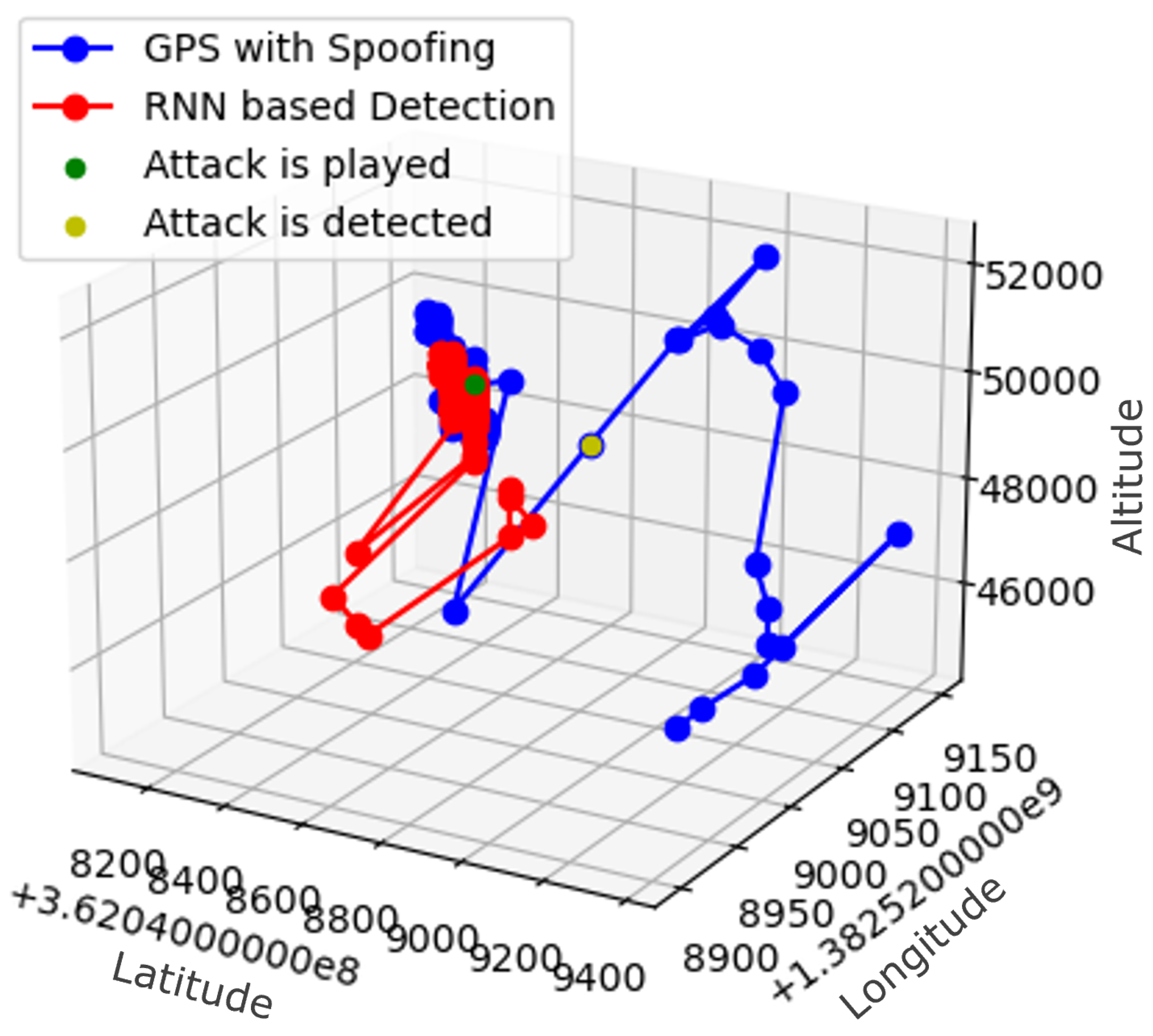
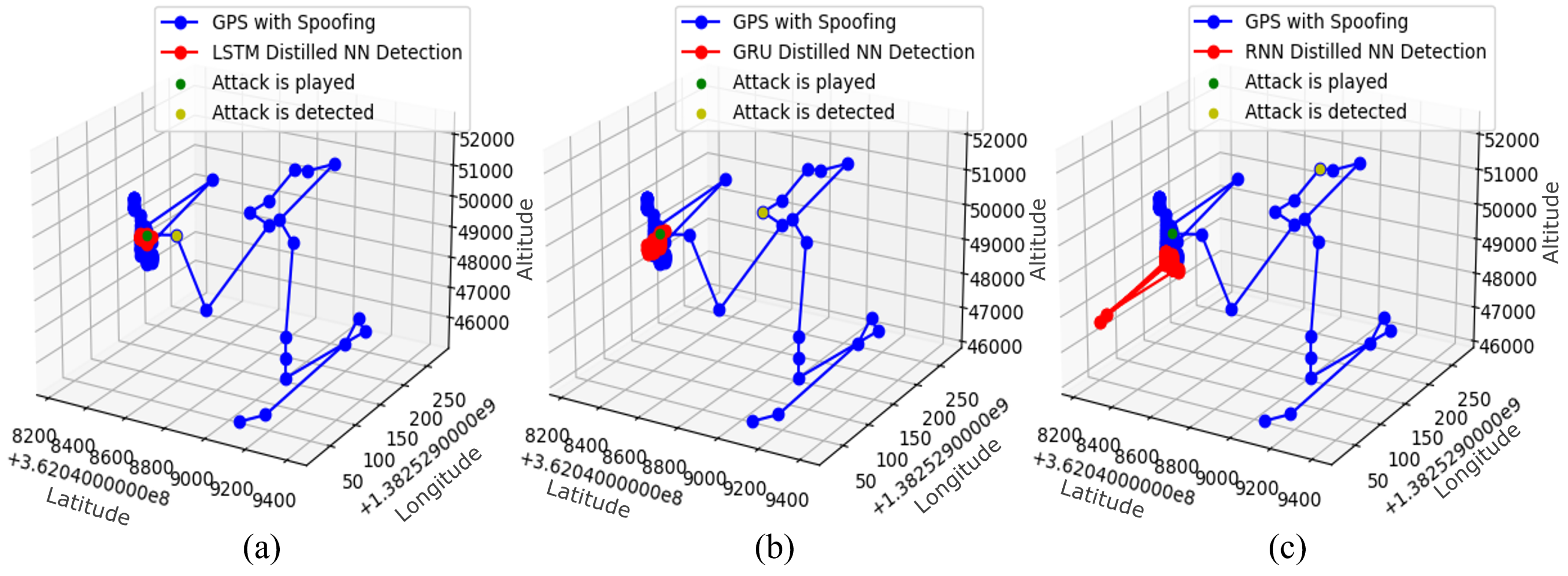
| Parameters | LSTM | GRU | RNN |
|---|---|---|---|
| Input Size | 6 | 6 | 6 |
| Hidden Size | 12 | 12 | 12 |
| Number of Layers | 12 | 12 | 12 |
| Number of Classes | 1 | 1 | 1 |
| Output Size | 3 | 3 | 3 |
| Learning Rate | 0.001 | 0.001 | 0.001 |
| Input Size | Output Size | Hidden Layer |
|---|---|---|
| 6 | 3 | (16, 8) |
| Models | LSTM | GRU | RNN |
|---|---|---|---|
| Model Size | 72.7 kb | 57.8 kb | 27.7 kb |
| NN Model Size | 3.0 kb | 3.0 kb | 3.0 kb |
| NN Model Overhead | 266.88 Mb | 266.88 Mb | 266.88 Mb |
| Overhead | 390.37 Mb | 391.29 Mb | 389.84 Mb |
| Learning Rate | 0.001 | 0.001 | 0.001 |
| Balance Factor | 0.45 | 0.45 | 0.45 |
| Model Reduced | 95.74% | 94.80% | 89.17% |
| Overhead Reduced | 31.63% | 31.79% | 31.54% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ren, Y.; Restivo, R.D.; Tan, W.; Wang, J.; Liu, Y.; Jiang, B.; Wang, H.; Song, H. Knowledge Distillation-Based GPS Spoofing Detection for Small UAV. Future Internet 2023, 15, 389. https://doi.org/10.3390/fi15120389
Ren Y, Restivo RD, Tan W, Wang J, Liu Y, Jiang B, Wang H, Song H. Knowledge Distillation-Based GPS Spoofing Detection for Small UAV. Future Internet. 2023; 15(12):389. https://doi.org/10.3390/fi15120389
Chicago/Turabian StyleRen, Yingying, Ryan D. Restivo, Wenkai Tan, Jian Wang, Yongxin Liu, Bin Jiang, Huihui Wang, and Houbing Song. 2023. "Knowledge Distillation-Based GPS Spoofing Detection for Small UAV" Future Internet 15, no. 12: 389. https://doi.org/10.3390/fi15120389
APA StyleRen, Y., Restivo, R. D., Tan, W., Wang, J., Liu, Y., Jiang, B., Wang, H., & Song, H. (2023). Knowledge Distillation-Based GPS Spoofing Detection for Small UAV. Future Internet, 15(12), 389. https://doi.org/10.3390/fi15120389










