Improved DDoS Detection Utilizing Deep Neural Networks and Feedforward Neural Networks as Autoencoder
Abstract
:1. Introduction
2. Related Works
3. The Concept of Detection DDoS Attacks in SDN
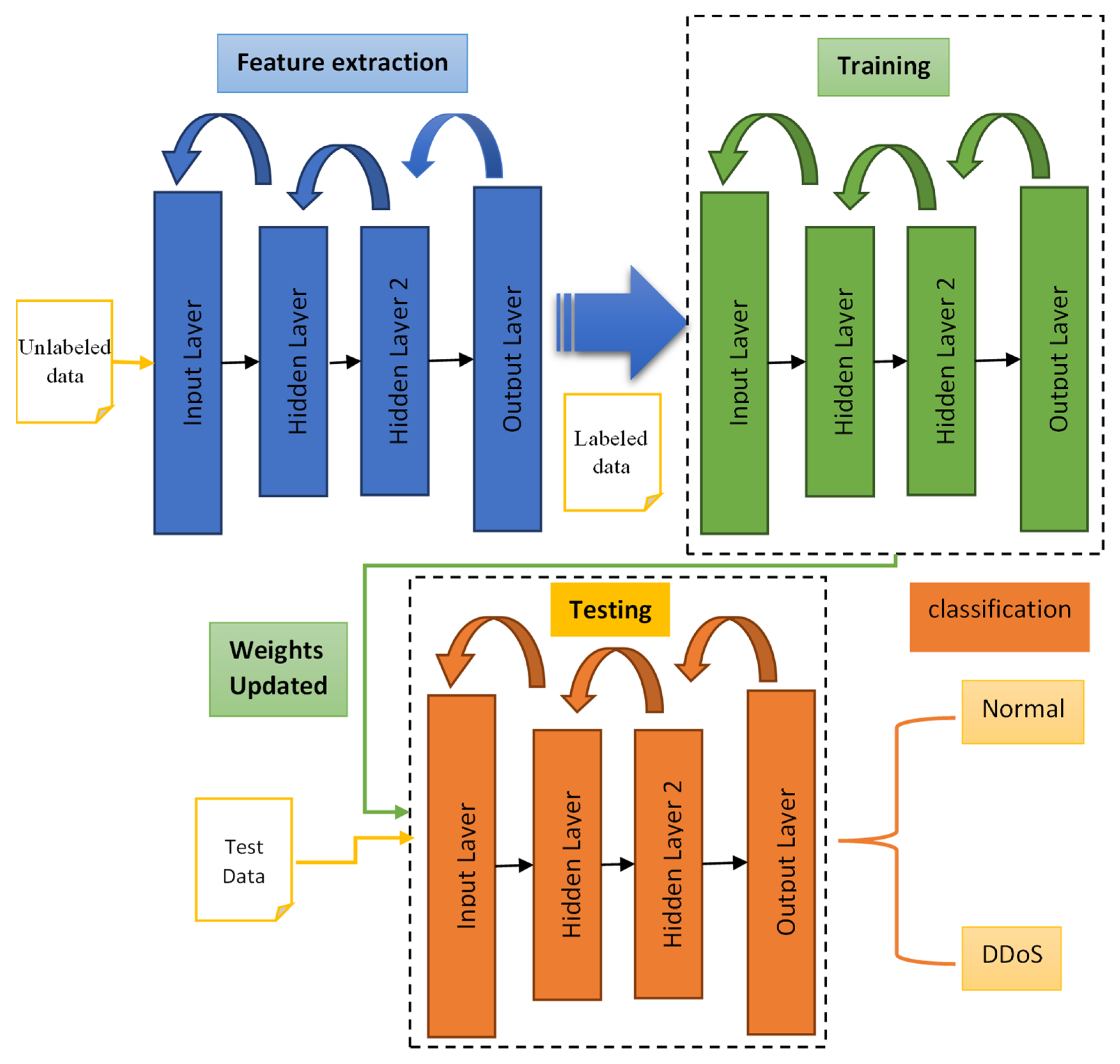
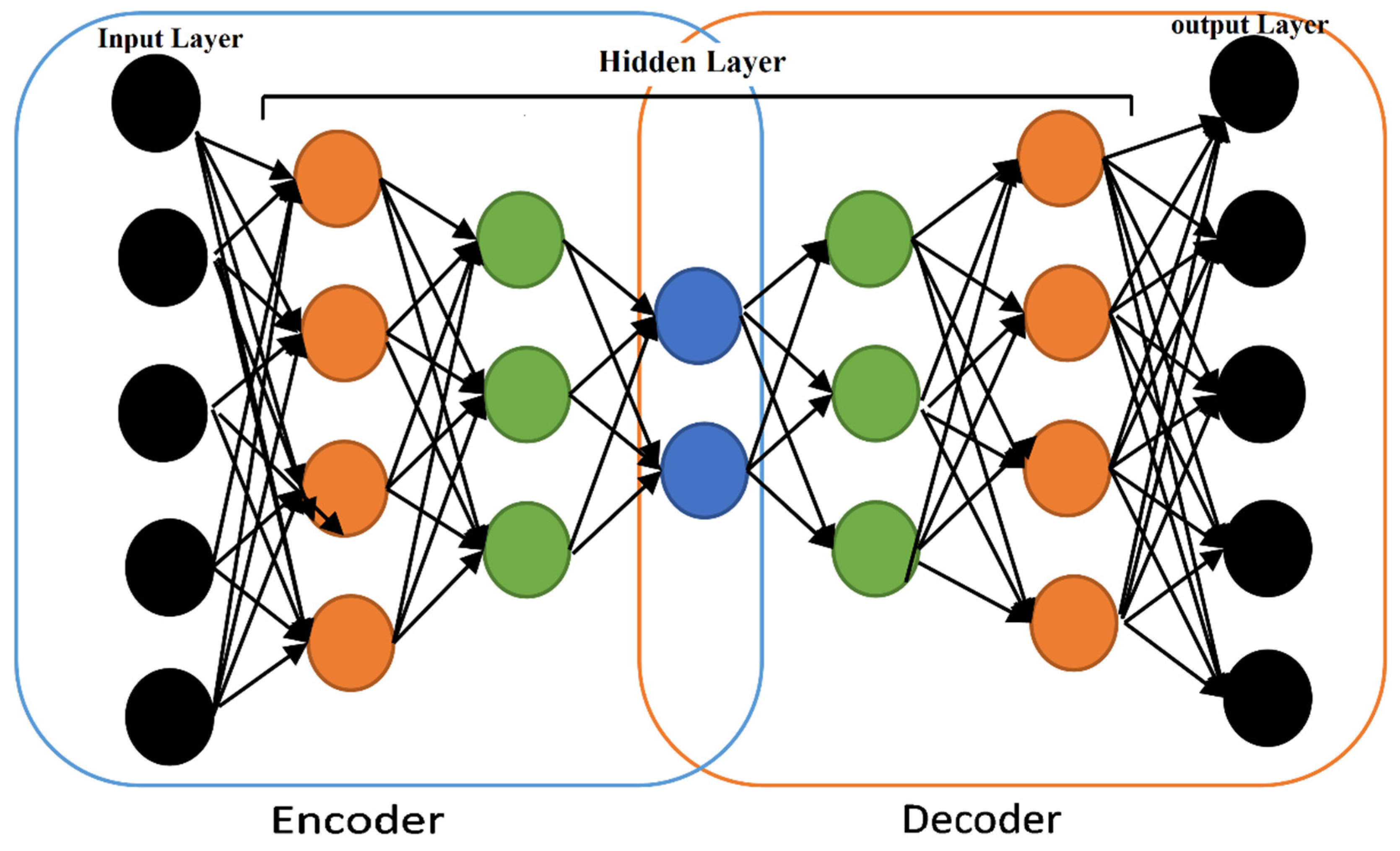
4. Proposed Model Structure
- Source IP, as well as destination IP along with port number;
- The protocol type (TCP, UDP, or ICMP) and header length;
- The number of packets transmitted at every switch;
- The number of packets received at each switch;
- The packet count (the number of packets within each flow).
- Feature extraction through normalization and autoencoder;
- Training the model using deep neural network;
- Classifying the traffic for one of the two classes: Normal and DDoS.
5. Evaluation Metrics
- Training/validation accuracy: This metric measures the percentage of true detections through total traffic trace. It is computed as follows:where TP is the (true positive), which is the number of anomaly records that is correctly classified. TN is the (true negative), which represents the number of normal records that is correctly classified. FP is the (false positive), which is the number of normal records that is incorrectly classified. FN is the (true negative), which represents the number of anomaly records that is incorrectly classified.
- Recall: This metric is used to show the percentage of predicted intrusions against all intrusions presented. The aim is to achieve higher recall values. It is computed using the following equation:
- Precision: This metric is used to show the many intrusions predicted by the intrusion detection system (NIDS), which are actual intrusions. The aim is to achieve higher precisions than the lower false alarms. It is computed using the following equation:
- F1-score: This metric attempts to better measure the accuracy of an intrusion detection system (NIDS) by considering both the precision and recall. The aim is to achieve higher F1-scores. It is computed as follows:
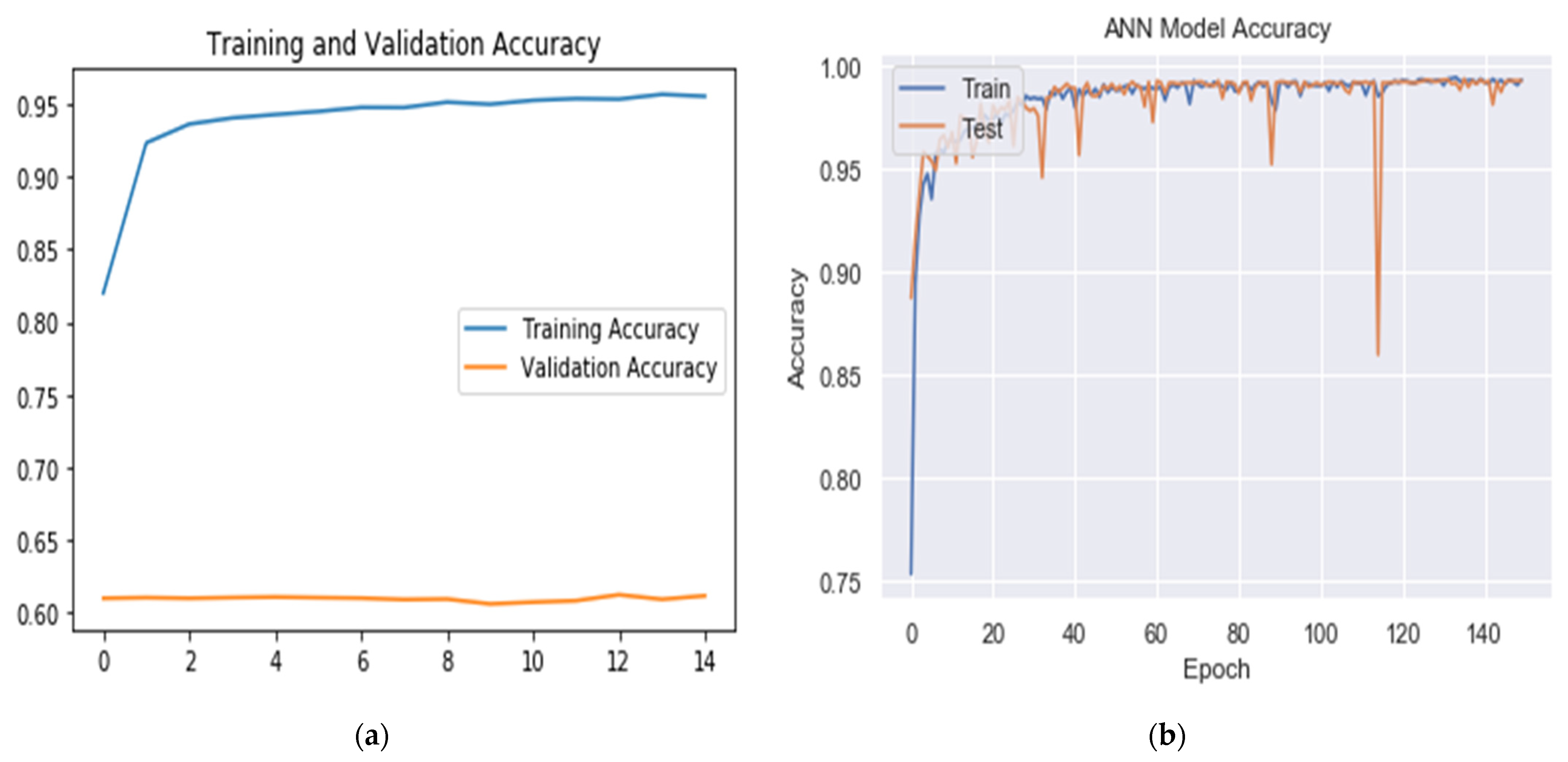
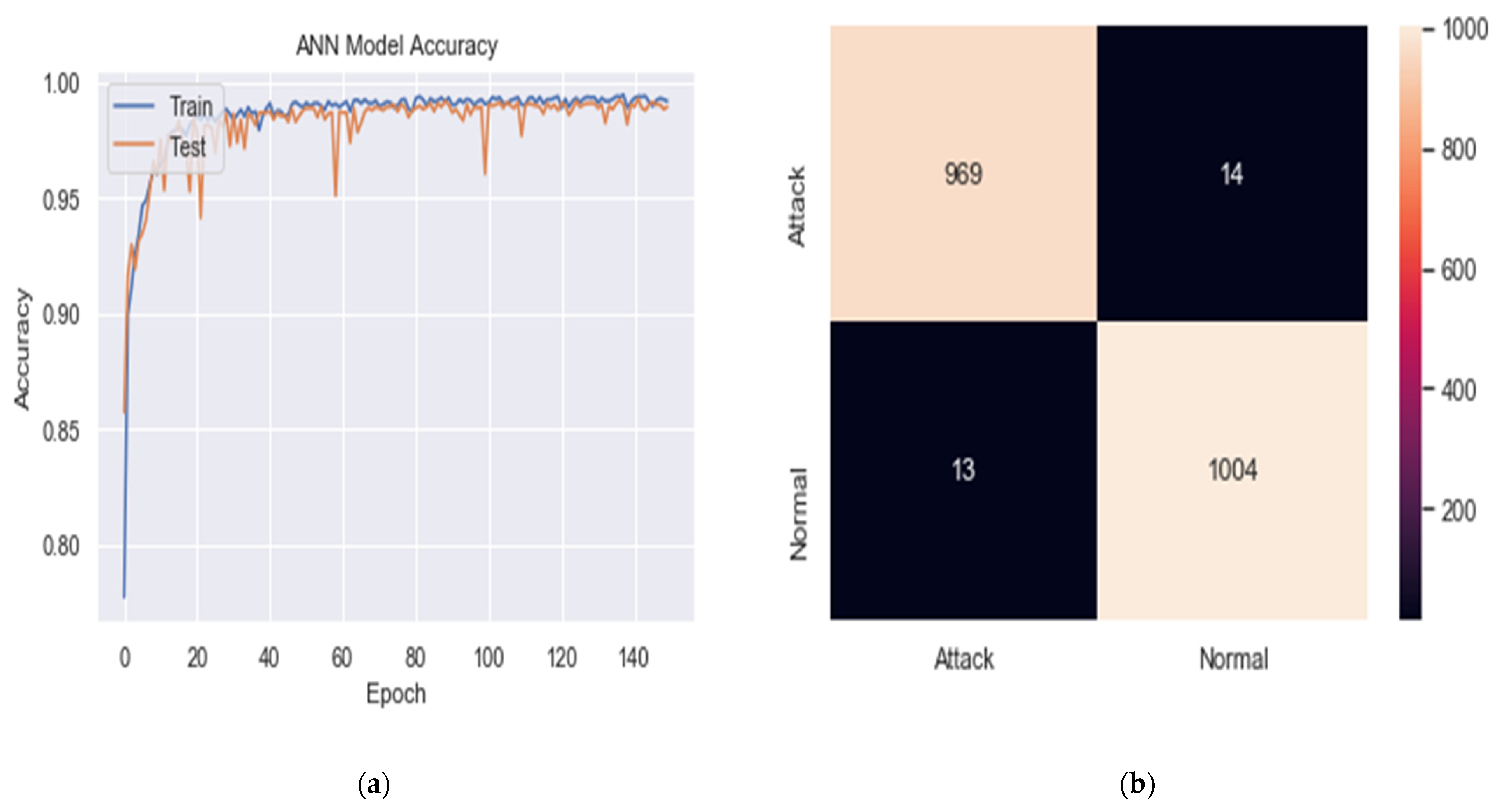
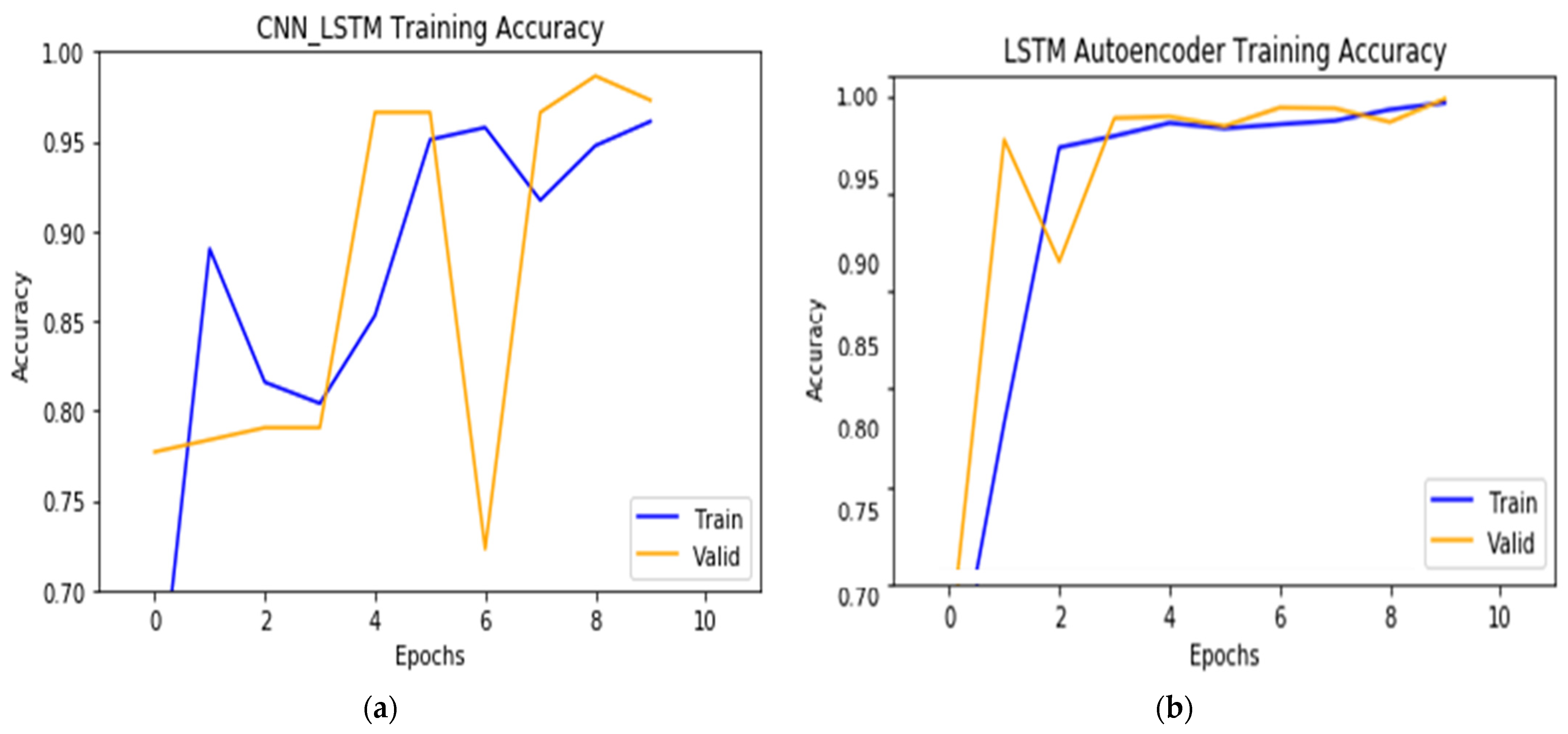
6. Results and Discussion
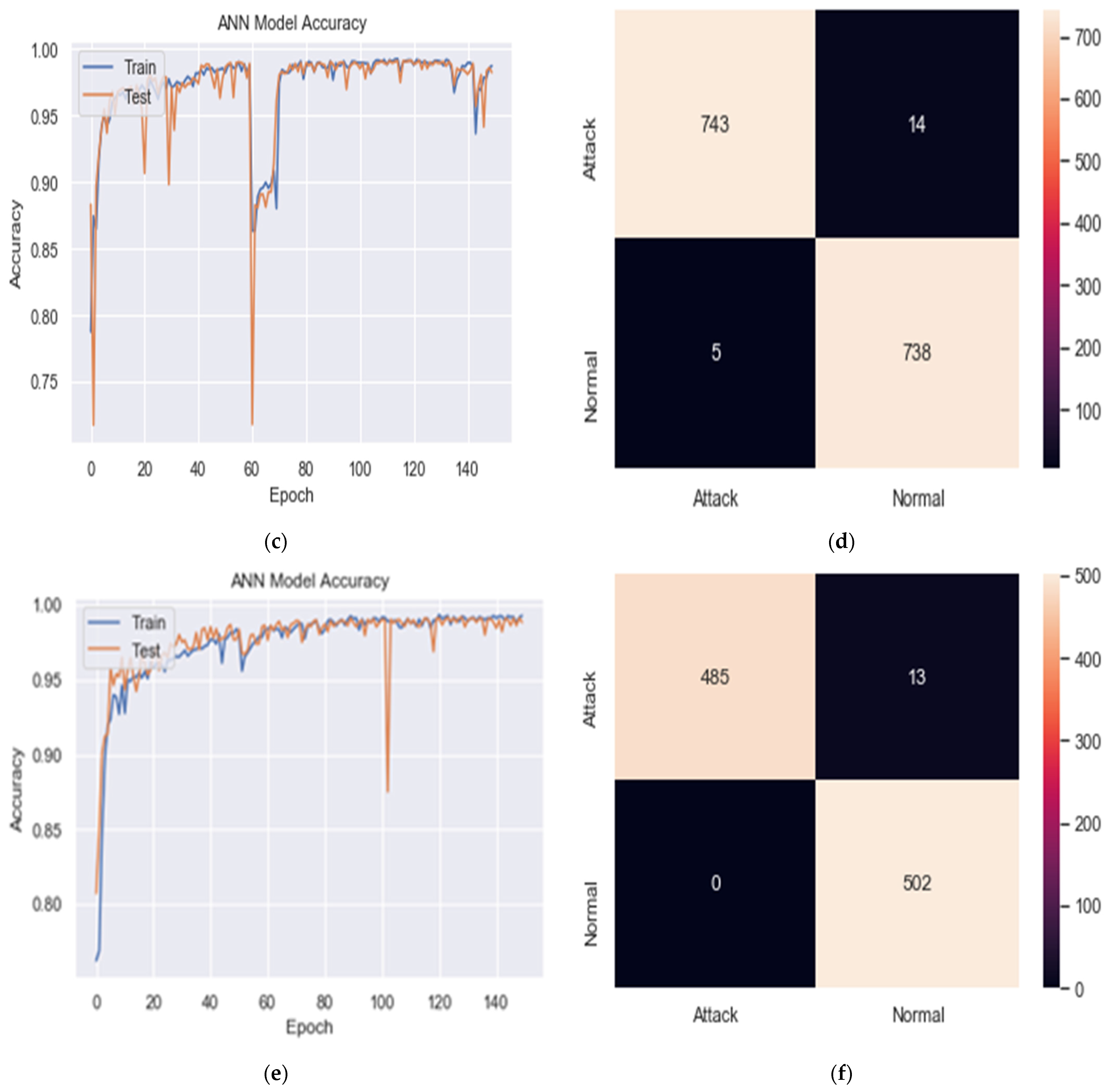
6.1. Test Using ISCXIDS2012
6.1.1. Effect of Data Splitting
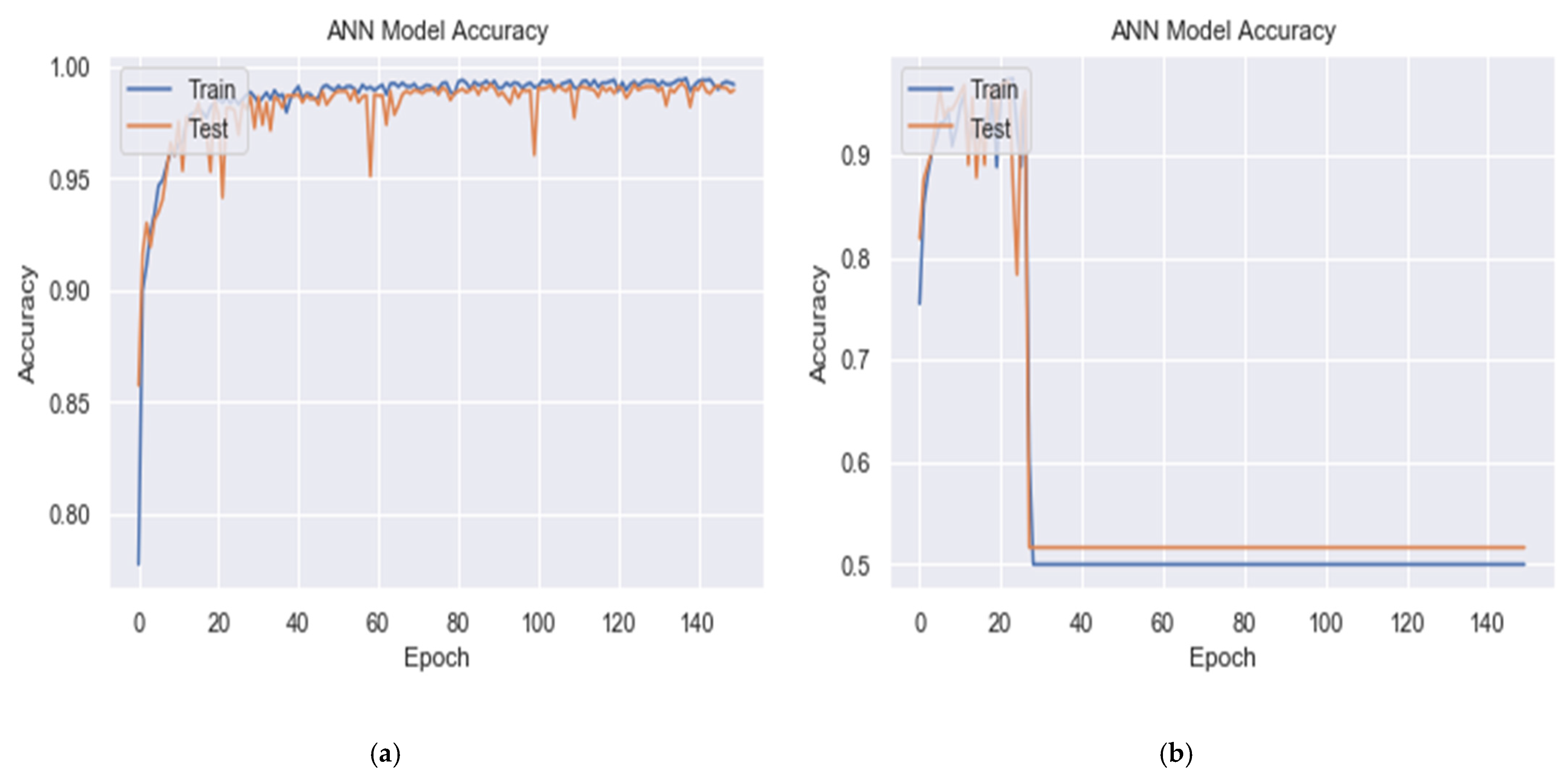
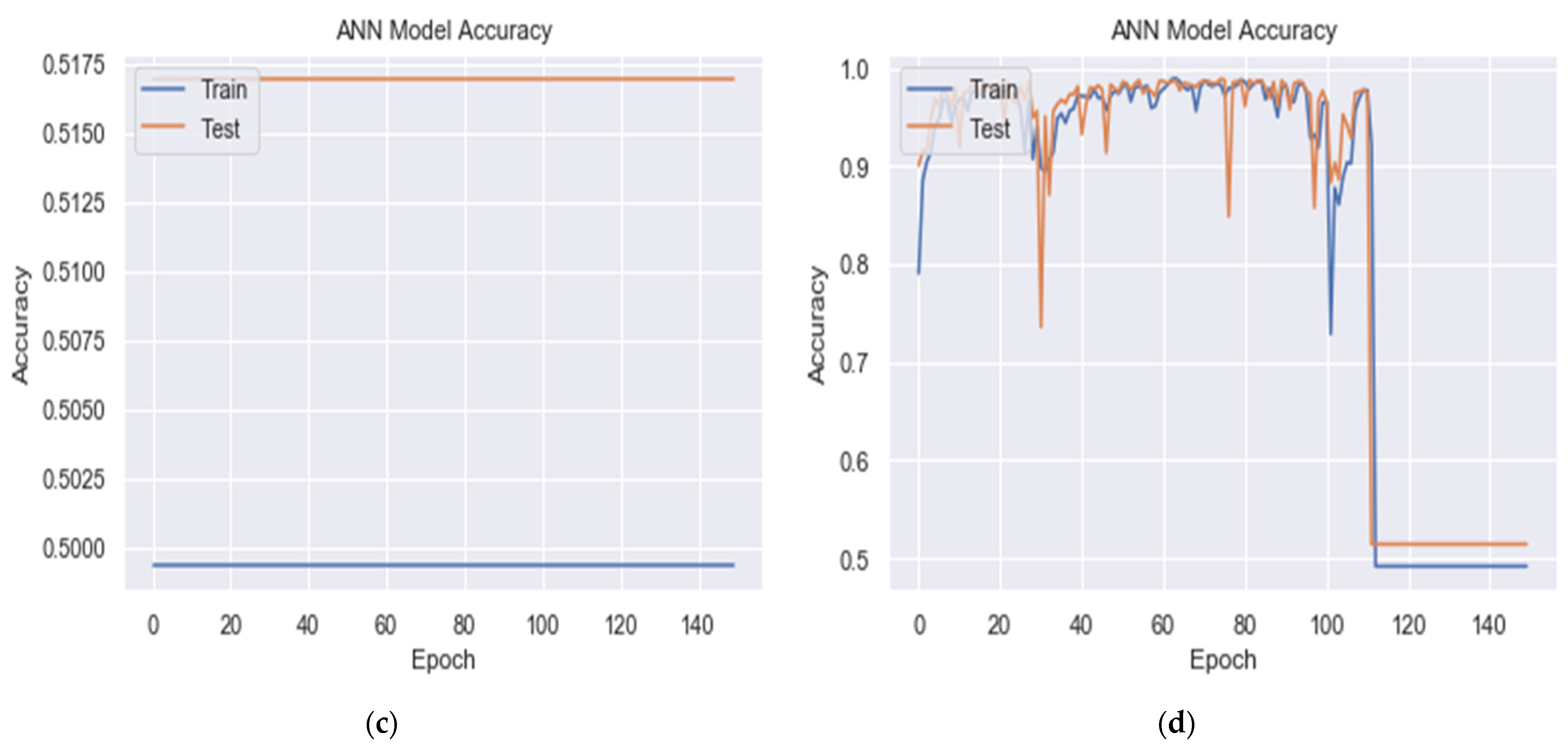
6.1.2. Effect of Activation Function in Output Layer Neurons
6.2. Test Using UNSW2018
6.3. Comparison with Previous Work
6.4. Test Using Dynamic Value
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Adekunle, O.O.; Oluwaseyitan, O. A Security Architecture for Software Defined Networks (SDN). Int. J. Comput. Sci. Inf. Secur. 2015, 13, 56. [Google Scholar]
- Kreutz, D.; Ramos, F.M.; Verissimo, P.E.; Rothenberg, C.E.; Azodolmolky, S.; Uhlig, S. Software-defined networking: A comprehensive survey. Proc. IEEE 2014, 103, 14–76. [Google Scholar] [CrossRef]
- Makori, D.O. Machine Learning Based Ddos Attack Detection for Software-Defined Networks: Yazılım Tanımlı Ağlar Için Makine Öğrenme Esaslı Ddos Attack Algılama. M.Sc. Thesis, Akarya Üniversitesi, Sakarya, Turkey, 2018. [Google Scholar]
- Weekes, J. Towards Smarter SDN Switches: Revisiting the Balance of Intelligence in SDN Networks; Lancaster University (United Kingdom): Lancaster, UK, 2019. [Google Scholar]
- El Mrabet, Z.; Kaabouch, N.; El Ghazi, H.; El Ghazi, H. Cyber-security in smart grid: Survey and challenges. Comput. Electr. Eng. 2018, 67, 469–482. [Google Scholar] [CrossRef]
- Potluri, S.; Diedrich, C. Accelerated deep neural networks for enhanced intrusion detection system. In Proceedings of the 2016 IEEE 21st International Conference on Emerging Technologies and Factory Automation (ETFA), Berlin, Germany, 6–9 September 2016; pp. 1–8. [Google Scholar]
- Nam, T.M.; Phong, P.H.; Khoa, T.D.; Huong, T.T.; Nam, P.N.; Thanh, N.H.; Thang, L.X.; Tuan, P.A.; Loi, V.D. Self-organizing map-based approaches in DDoS flooding detection using SDN. In Proceedings of the 2018 International Conference on Information Networking (ICOIN), Chiang Mai, Thailand, 10–12 January 2018; pp. 249–254. [Google Scholar]
- Pektaş, A.; Acarman, T. A deep learning method to detect network intrusion through flow-based features. Int. J. Netw. Manag. 2019, 29, e2050. [Google Scholar] [CrossRef]
- Elsayed, M.S.; Le-Khac, N.-A.; Soumyabrata, D.; Jurcut, A.D. Machine-Learning Techniques for detecting Attacks in SDN. In Proceedings of the 2019 IEEE 7th International Conference on Computer Science and Network Technology (ICCSNT), Dalian, China, 19–20 October 2019. [Google Scholar]
- Sindian, S.; Samer, S. An enhanced deep autoencoder-based approach for DDoS attack detection. Wseas Trans. Syst. Control 2020, 15, 716–725. [Google Scholar] [CrossRef]
- DDoS Evaluation Dataset (CIC-DDoS2019). Available online: https://www.unb.ca/cic/datasets/ddos-2019.html (accessed on 30 June 2022).
- Radanliev, P.; De Roure, D.; Page, K.; Van Kleek, M.; Santos, O.; Maddox, L.T.; Burnap, P.; Anthi, E.; Maple, C. Design of a dynamic and self-adapting system, supported with artificial intelligence, machine learning and real-time intelligence for predictive cyber risk analytics in extreme environments–cyber risk in the colonisation of Mars. Saf. Extrem. Environ. 2020, 2, 219–230. [Google Scholar] [CrossRef]
- Mhamdi, L.; McLernon, D.; El-Moussa, F.; Zaidi, S.A.R.; Ghogho, M.; Tang, T. A deep learning approach combining autoencoder with one-class SVM for DDoS attack detection in SDNs. In Proceedings of the 2020 IEEE Eighth International Conference on Communications and Networking (ComNet), Hammamet, Tunisia, 27–30 October 2020; pp. 1–6. [Google Scholar]
- Kushwah, G.S.; Ranga, V. Distributed denial of service attack detection in cloud computing using hybridextreme learning machine. Turk. J. Electr. Eng. Comput. Sci. 2021, 29, 1852–1870. [Google Scholar] [CrossRef]
- Gadze, J.D.; Bamfo-Asante, A.A.; Agyemang, J.O.; Nunoo-Mensah, H.; Opare, K.A.-B. An investigation into the application of deep learning in the detection and mitigation of DDOS attack on SDN controllers. Technologies 2021, 9, 14. [Google Scholar] [CrossRef]
- Singh, A.; Jang-Jaccard, J. Autoencoder-based Unsupervised Intrusion Detection using Multi-Scale Convolutional Recurrent Networks. arXiv 2022, arXiv:2204.03779. [Google Scholar]
- The UNSW-NB15 Dataset. Available online: https://research.unsw.edu.au/projects/unsw-nb15-dataset (accessed on 26 May 2022).
- NSL-KDD Dataset. Available online: https://www.unb.ca/cic/datasets/nsl.html (accessed on 12 June 2022).
- Ivanova, V.; Tashev, T.; Draganov, I. Detection of IoT based DDoS Attacks by Network Traffic Analysis using Feedforward Neural Networks. Int. J. Circuits Syst. Sign. Proc. 2022, 16, 653–662. [Google Scholar] [CrossRef]
- Prasad, A.; Chandra, S. VMFCVD: An Optimized Framework to Combat Volumetric DDoS Attacks using Machine Learning. Arab. J. Sci. Eng. 2022, 47, 9965–9983. [Google Scholar] [CrossRef] [PubMed]
- Khalaf, B.A.; Mostafa, S.A.; Mustapha, A.; Mohammed, M.A.; Abduallah, W.M. Comprehensive review of artificial intelligence and statistical approaches in distributed denial of service attack and defense methods. IEEE Access 2019, 7, 51691–51713. [Google Scholar] [CrossRef]
- Mirkovic, J.; Reiher, P. A taxonomy of DDoS attack and DDoS defense mechanisms. ACM SIGCOMM Comput. Commun. Rev. 2004, 34, 39–53. [Google Scholar] [CrossRef]
- Khraisat, A.; Gondal, I.; Vamplew, P.; Kamruzzaman, J. Survey of intrusion detection systems: Techniques, datasets and challenges. Cybersecurity 2019, 2, 20. [Google Scholar] [CrossRef]
- Sahri, N.; Okamura, K. Protecting DNS services from IP spoofing: SDN collaborative authentication approach. In Proceedings of the 11th International Conference on Future Internet Technologies, Nanjing, China, 15–17 June 2016; pp. 83–89. [Google Scholar]
- Fatima, M.; Pasha, M. Survey of machine learning algorithms for disease diagnostic. J. Intell. Learn. Syst. Appl. 2017, 9, 73781. [Google Scholar] [CrossRef]
- Gupta, C.; Johri, I.; Srinivasan, K.; Hu, Y.-C.; Qaisar, S.M.; Huang, K.-Y. A Systematic Review on Machine Learning and Deep Learning Models for Electronic Information Security in Mobile Networks. Sensors 2022, 22, 2017. [Google Scholar] [CrossRef] [PubMed]
- Intrusion Detection Evaluation Dataset (ISCXIDS2012). Available online: https://www.unb.ca/cic/datasets/ids.html (accessed on 15 May 2022).
- Tang, T.A.; McLernon, D.; Mhamdi, L.; Zaidi, S.A.R.; Ghogho, M. Intrusion detection in sdn-based networks: Deep recurrent neural network approach. In Deep Learning Applications for Cyber Security; Springer: Berlin, Germany, 2019; pp. 175–195. [Google Scholar]
- Raikar, M.M.; Meena, S.; Mulla, M.M.; Shetti, N.S.; Karanandi, M. Data traffic classification in software defined networks (SDN) using supervised-learning. Proc. Comput. Sci. 2020, 171, 2750–2759. [Google Scholar] [CrossRef]
- Sugomori, Y.; Kaluza, B.; Soares, F.M.; Souza, A.M. Deep Learning: Practical Neural Networks with Java; Packt Publishing Ltd.: Birmingham, UK, 2017. [Google Scholar]
- Meng, Q.; Catchpoole, D.; Skillicom, D.; Kennedy, P.J. Relational autoencoder for feature extraction. In Proceedings of the 2017 International Joint Conference on Neural Networks (IJCNN), Anchorage, AK, USA, 14–19 May 2017; pp. 364–371. [Google Scholar]
- Charu, C.A. Neural Networks and Deep Learning: A Textbook; An Giang University: An Giang, Vietnam, 2018. [Google Scholar]
- Xu, Z.; Wang, Y.; Long, M.; Wang, J.; KLiss, M. PredCNN: Predictive Learning with Cascade Convolutions. In Proceedings of the Twenty-Seventh International Joint Conference on Artificial Intelligence, Stockholm, Sweden, 13–19 July 2018; pp. 2940–2947. [Google Scholar]
- Chu, W.; Cai, D. Stacked Similarity-Aware Autoencoders. In Proceedings of the Twenty-Sixth International Joint Conference on Artificial Intelligence, Melbourne, Australia, 19–25 August 2017; pp. 1561–1567. [Google Scholar]
- Liu, G.; Bao, H.; Han, B. A stacked autoencoder-based deep neural network for achieving gearbox fault diagnosis. Math. Probl. Eng. 2018, 2018, 5105709. [Google Scholar] [CrossRef]
- ElSayed, M.S.; Le-Khac, N.-A.; Albahar, M.A.; Jurcut, A. A novel hybrid model for intrusion detection systems in SDNs based on CNN and a new regularization technique. J. Netw. Comput. Appl. 2021, 191, 103160. [Google Scholar] [CrossRef]
- Perez-Diaz, J.A.; Valdovinos, I.A.; Choo, K.-K.R.; Zhu, D. A flexible SDN-based architecture for identifying and mitigating low-rate DDoS attacks using machine learning. IEEE Access 2020, 8, 155859–155872. [Google Scholar] [CrossRef]
- Soltanaghaei, M. A New DDoS Detection Method in Software Defined Network; Research Square: Durham, NC, USA, 2020. [Google Scholar]



| Layer (Type) | Output Shape |
|---|---|
| Conv 2D | (None, 48, 48, 50) |
| Max Pooling | (None, 24, 24, 50) |
| Conv 2D | (None, 22, 22, 64) |
| Max Pooling | (None, 11, 11, 64) |
| Conv 2D | (None, 9, 9, 64) |
| flatten (Flatten) | (None, 5184) |
| Dense | (None, 64) |
| Dense | (None, 1) |
| Layer (Type) | Output Shape |
|---|---|
| Dense | (None, 18, 64) |
| Bidirectional | (None, 128) |
| Dense | (None, 32) |
| Dense | (None, 16) |
| Dense | (None, 12) |
| Dense | (None, 1) |
| Network | Loss | Accuracy | Val. Loss | Val. Accuracy |
|---|---|---|---|---|
| ANN-Autoencoder | 0.5842 | 0.6612 | 0.5641 | 0.6484 |
| CNN-Autoencoder | 0.1027 | 0.9554 | 0.5907 | 0.6279 |
| BDLSTM-Autoencoder | 0.0388 | 0.9935 | 0.0624 | 0.9930 |
| Network | Accuracy | Val. Accuracy | Precision | Recall | F1-Score |
|---|---|---|---|---|---|
| (60, 20, 20) splitting | 0.9935 | 0.9930 | 0.99 N 0.99 At | 0.99 N 0.99 At | 0.99 N 0.99 At |
| (70, 15, 15) splitting | 0.9875 | 0.9826 | 0.98 N 0.99 At | 0.99 N 0.98 At | 0.99 N 0.99 At |
| (80, 10, 10) splitting | 0.9927 | 0.9884 | 0.97 N 1.0 At | 1.0 N 0.97 At | 0.99 N 0.99 At |
| Network | Accuracy | Val. Accuracy | Precision | Recall | F1-Score |
|---|---|---|---|---|---|
| Proposed model | 0.9935 | 0.9930 | 0.99 N 0.99 At | 0.99 N 0.99 At | 0.99 N 0.99 At |
| ReLU | 0.9554 | 0.6114 | 0.00 N 0.49 At | 0.00 N 1.00 At | 0.00 N 0.65 At |
| SoftMax | 0.9935 | 0.9930 | 0.00 N 0.48 At | 0.00 N 1.00 At | 0.00 N 0.65 At |
| tanh | 0.4920 | 0.5148 | 0.51 N 0.00 At | 1.00 N 0.00 At | 0.68 N 0.00 At |
| Network | Loss | Accuracy | Val. Loss | Val. Accuracy |
|---|---|---|---|---|
| ANN-Autoencoder | 0.5746 | 0.6453 | 0.5787 | 0.6512 |
| CNN-Autoencoder | 0.1338 | 0.9611 | 0.0880 | 0.986 |
| BDLSTM-Autoencoder | 0.0020 | 0.9995 | 4.9197 × 10−4 | 0.9994 |
| Ref | Dataset | Algorithm | Accuracy | Val. Accuracy | Precision | Recall | F1-Score |
|---|---|---|---|---|---|---|---|
| Proposed model | ISCXIDS2012 | BDLSTM-Autoencoder | 0.9935 | 0.9930 | 0.9978 N 0.9991 At | 0.99 N 0.99 At | 0.9981 N 0.9987 At |
| Dehkordi et al. [38] | Model | 0. 8711 | ---- | 0. 3708 N 0. 3574 At | --- | 0.4580 N 0.5266 At | |
| Naive Bayes | 0.9584 | ----- | 0.9156 | ---- | 0.9116 | ||
| Random Tree | 0.9984 | ----- | 0.9966 | ---- | 0.9967 | ||
| Proposed model | UNSW2018 | BDLSTM-Autoencoder | 0.9995 | 0.9994 | 0.95 N 0.99 At | 0.94 N 0.99 At | 0.95 N 0.99 At |
| Ivanova et al. [19] | Model | 0.9999 | 0.9999 | 0.8255 N 0.9999 At | 0.6635 N 0.9999 At | 0.7357 N 0.9987 At | |
| Prasad et al. [20] | Model | 0.9999 | 0.9999 | 0.8772 N 0.9999 At | 0.8255 N 0.9999 At | 0.8197 N 0.9999 At |
| Switch | Src | Dst | Pktcount | Bytecount | Dur | Dur_Nsec | Tot_Dur | Flows | … | Pktrate | Pairflow | Protocol | Port_No | Tx_Bytes | Rx_Bytes | Tx_Kbps |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 7 | 10.0.0.3 | 10.0.0.10 | 247 | 24,206 | 535 | 41,000,000 | 2.53 × 1011 | 13 | … | 0 | 1 | ICMP | 2 | 35,897 | 31,370 | 0 |
| 7 | 10.0.0.12 | 10.0.0.17 | 122,751 | 7,119,558 | 410 | 808,000,000 | 4.11 × 1011 | 3 | … | 251 | 1 | TCP | 2 | 33,018,521 | 470,020,975 | 0 |
| 5 | 10.0.0.16 | 10.0.0.3 | 168,663 | 91,078,202 | 322 | 297,000,000 | 3.22 × 1011 | 5 | … | 545 | 1 | TCP | 1 | 6,115,457 | 144,666,612 | 0 |
| 6 | 10.0.0.12 | 10.0.0.7 | 605 | 59,290 | 620 | 214,000,000 | 6.20 × 1011 | 3 | … | 0 | 1 | ICMP | 3 | 65,744 | 135,525,618 | 0 |
| 4 | 10.0.0.2 | 10.0.0.8 | 35,970 | 38,344,020 | 78 | 820,000,000 | 7.882 × 1011 | 6 | … | 451 | 0 | UDP | 3 | 3236 | 3404 | 0 |
| 4 | 10.0.0.9 | 10.0.0.2 | 792 | 77,616 | 811 | 590,000,000 | 8.12 × 1011 | 5 | … | 0 | 0 | ICMP | 2 | 105,851 | 135,561,984 | 0 |
| Network | Accuracy | Val. Accuracy | Precision | Recall | F1-Score |
|---|---|---|---|---|---|
| Proposed model | 0.9762 | 0.9768 | 0.98 N 0.88 At | 0.92 N 0.97 At | 0.95 N 0.93 At |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yaser, A.L.; Mousa, H.M.; Hussein, M. Improved DDoS Detection Utilizing Deep Neural Networks and Feedforward Neural Networks as Autoencoder. Future Internet 2022, 14, 240. https://doi.org/10.3390/fi14080240
Yaser AL, Mousa HM, Hussein M. Improved DDoS Detection Utilizing Deep Neural Networks and Feedforward Neural Networks as Autoencoder. Future Internet. 2022; 14(8):240. https://doi.org/10.3390/fi14080240
Chicago/Turabian StyleYaser, Ahmed Latif, Hamdy M. Mousa, and Mahmoud Hussein. 2022. "Improved DDoS Detection Utilizing Deep Neural Networks and Feedforward Neural Networks as Autoencoder" Future Internet 14, no. 8: 240. https://doi.org/10.3390/fi14080240
APA StyleYaser, A. L., Mousa, H. M., & Hussein, M. (2022). Improved DDoS Detection Utilizing Deep Neural Networks and Feedforward Neural Networks as Autoencoder. Future Internet, 14(8), 240. https://doi.org/10.3390/fi14080240







