Abstract
Recently the Internet of Vehicles (IoV) has become a promising research area in the field of the Internet of Things (IoT), which enables vehicles to communicate and exchange real-time information with each other, as well as with infrastructure, people, and other sensors and actuators through various communication interfaces. The realization of IoV networks faces various communication and networking challenges to meet stringent requirements of low latency, dynamic topology, high data-rate connectivity, resource allocation, multiple access, and QoS. Advances in information-centric networks (ICN), edge computing (EC), and artificial intelligence (AI) will transform and help to realize the Intelligent Internet of Vehicles (IIoV). Information-centric networks have emerged as a paradigm promising to cope with the limitations of the current host-based network architecture (TCP/IP-based networks) by providing mobility support, efficient content distribution, scalability and security based on content names, regardless of their location. Edge computing (EC), on the other hand, is a key paradigm to provide computation, storage and other cloud services in close proximity to where they are requested, thus enabling the support of real-time services. It is promising for computation-intensive applications, such as autonomous and cooperative driving, and to alleviate storage burdens (by caching). AI has recently emerged as a powerful tool to break through obstacles in various research areas including that of intelligent transport systems (ITS). ITS are smart enough to make decisions based on the status of a great variety of inputs. The convergence of ICN and EC with AI empowerment will bring new opportunities while also raising not-yet-explored obstacles to realize Intelligent IoV. In this paper, we discuss the applicability of AI techniques in solving challenging vehicular problems and enhancing the learning capacity of edge devices and ICN networks. A comprehensive review is provided of utilizing intelligence in EC and ICN to address current challenges in their application to IIoV. In particular, we focus on intelligent edge computing and networking, offloading, intelligent mobility-aware caching and forwarding and overall network performance. Furthermore, we discuss potential solutions to the presented issues. Finally, we highlight potential research directions which may illuminate efforts to develop new intelligent IoV applications.
1. Introduction
Advancements in digital infrastructure, computing, and learning algorithms have enabled the emergence of massive connectivity and digital intelligence. In particular, the growth in the Internet of Things (IoT) has facilitated the connection of a number of smart devices, including smart vehicles, vehicles equipped with advanced computing, sensing, networking, and communication technologies, to the Internet in what is known as the Internet of Vehicles (IoV). The original intention of vehicular networking, a key driver for intelligent transport systems (ITS), was to bring connectivity to vehicles [1].
Beyond mere connectivity, however, IoV aims to significantly transform existing ITS by enabling seamless cooperative driving in autonomous vehicles, which reduces the risk of traffic accidents. It also enhances infotainment, real-time tracking, traffic information and parking management, thus reducing commuting time and CO2 emissions [2]. Therefore, the future of IoV in the era of 5G/B5G [3] and artificial intelligence (AI) has attracted attention from both academia and industry as a means to realize the Intelligent Internet of Vehicles (IIoV).
The full scale realization of IoV is challenged by various issues, including the heterogeneity of networking and communications interfaces, the requirements of latency sensitive applications, the heterogeneity of vehicle resources, security concerns, reliability, handling and processing of generated data and the lack of an accepted framework that supports collaborative IoV networks. Moreover, these issues are further exacerbated by frequent changes in network topology as a result of vehicular mobility. Some of these challenges have been addressed using emerging technologies, such as edge computing, information centric networks, multi-access radio technology and AI.
Edge computing [4] is a relatively recent computing paradigm that aims to provide computational, storage, and other cloud services in close proximity to the devices using them, thus achieving low latency, high bandwidth, and location and mobility-aware contextual services. Related edge-computing approaches, such as fog computing [5], cloudlets [6], and mobile edge computing have been proposed. Intelligent caching, intelligent forwarding, and computational offloading are some of the future directions in edge intelligence.
ICN [7] has emerged as a paradigm promising to cope with the limitations of the current host-based network architecture by providing mobility support, efficient content distribution, scalability and security based on content names regardless of the location. The existing host-based network architecture faces significant challenges to meet demands in terms of scalability, mobility, security, and resource utilization [8]. Numerous investigations have confirmed the feasibility of applying ICN in different domains of IoV applications [9]. Ghasemi et al. [10] demonstrated video streaming over ICN/NDN on a global NDN (named data networking) test bed. Other studies [11,12] have investigated the potential of ICN using NDN with IEEE802.15.4 for constrained IoT devices to implement a real-world smart agriculture scenario.
Our paper aims to provide a comprehensive survey of the development and state-of-the-art of the convergence of edge-computing intelligence and ICN for realizing IIoV (Intelligent Internet of Vehicles) solutions. In the past few years, some survey articles have been presented in the context of ICN for IoT summarizing the applicability and potential of information centric networks for the Internet of Things [13,14,15,16,17]. Khelifi et al. [18] carried out a brief survey on named data networking in vehicular ad hoc networks, while Kerrche et al. [19] analyzed IoV and artificial intelligence for information-centric networks [20]. Our survey differs from previous studies in that it examines intelligence computing, edge caching, and networking in the context of ICN-based IoV. Figure 1 shows the converged architecture for IIoV.

Figure 1.
Converged Architecture for IIoV.
To the best of our knowledge, this is the only comprehensive study that discusses AI based solutions for the convergence of ICN-based IoV with edge computing as well as their potential benefits. In this regard, we summarize the major contributions of the paper as follows:
- Presenting a comprehensive review regarding the utilization of edge intelligence and ICN for IoV solutions, addressing existing challenges.
- Performing an in-depth review of the leading enablers of IoV, including wireless communications, mobile edge/fog computing, machine learning/AI, intelligent computing, and information-centric networking.
- Providing a detailed ICN architecture suitable to meet the requirements of IoV networks, such as naming, caching, mobility, and security.
- Highlighting challenges and issues faced by ICN-based IoV, indicating future research directions which may illuminate efforts to develop new intelligent IoV applications.
The rest of the paper is organized as follows: In Section 2, a review of IoV, ICN, EC and AI is presented. Section 3 introduces a general model for ICN and edge computing convergence for IIoV with detailed discussion of the key elements. Section 4 reviews existing research on the application of AI to wireless networks and communication to achieve intelligent networking, intelligent edge computing and caching. Challenges and open issues are identified and highlighted in Section 5. Finally, the conclusions of the paper are provided in Section 6 (Figure 2).
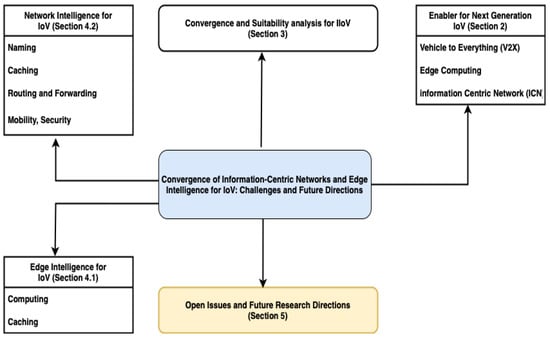
Figure 2.
The organization of the remaining parts of the paper.
2. Internet of Vehicles (IoV)
IoV has attracted a great deal of attention as a useful Internet of Things (IoT) scenario for addressing the grand challenges of modern transportation problems. Connected and fully automated vehicles are expected to revolutionize the transportation systems of the future on a global scale, significantly enhancing road safety, alleviating traffic congestion, reducing fuel consumption, and enhancing driving experience and infotainment. IoV evolved from vehicular ad hoc networks (VANET) which mainly focused on providing road safety applications based on communication between vehicles and roadside units, constituting a special case of mobile ad hoc networks (MANET) [1].
In IoV, vehicles are equipped with computing and storage capabilities, a variety of sensors, including cameras, GPS, RADAR, LIDAR (light detection and ranging), and different communication wireless interfaces, leading to independent autonomous vehicles that can connect and cooperate with each other, with roadside infrastructure, with pedestrians, and with other entities through vehicle-to-everything (V2X) communications.
Several access technologies have already emerged to support V2X communication, such as wireless local area networks (WLAN), including IEEE 802.11p/ WAVE [21,22,23] and its evolution IEEE 802.11bd [24], wireless wide area networks, cellular technologies, such as LTE/5G [21,25,26], as well as LoRa [27,28,29,30] and Bluetooth. These wireless access technologies offer diverse communication options among different smart things. In IoV, each vehicle is envisioned as a smart object having sensing, computing and storage capabilities enabling it to connect with other entities through the vehicle-to-everything (V2X) umbrella, comprising vehicle-to-vehicle (V2V), vehicle-to-infrastructure (V2I), vehicle to sensor (V2S), vehicle to roadside unit (V2R), and vehicle to personal device (V2P).
2.1. IoV Applications
IoV opens up new opportunities and applications and offers many benefits to drivers, pedestrians, society and business. According to the World Health Organization (WHO), every year, approximately 1.3 million people die and 7 million are injured in traffic accidents. Moreover, people waste billions of hours because of traffic problems (e.g., through traffic jams and accidents) [31].
According to the 5G Automotive Association (5GAA), IoV applications are clustered into four categories.
- Safety-based: The primary goal is to reduce the severity and frequency of vehicle crashes. Connected vehicles exchange warning alerts to prevent possible collisions, and provide real-time crash information with location information to emergency teams.
- Traffic efficiency: Traffic efficiency covers a range of applications intended to optimize the flow of road traffic. For instance, scheduling traffic signals at intersections according to the volume of traffic to reduce waiting time.
- Cooperative driving: Cooperative adaptive cruise control (CACC) requires throughput of the order of 5 Mbps and latency of the order of 2–10 ms.
- Infotainment: Efficient provision of non-driving-related information and entertainment to drivers and passengers with stringent QoS is crucial for IoV. Many vehicular users are now interested in accessing HD video streaming and use various latency-sensitive mobile applications, such as real-time online gaming, virtual sports, video streaming, instant messaging among passengers, and geo-specific advertisements. Such services are characterized by relatively short latency.
Typical IoV applications and their requirement are listed and described in Table 1.

Table 1.
IoV applications and characteristics.
2.2. Radio Access Technologies
There is a need to combine short-range technologies, such as Bluetooth, with long-range technologies for seamless network availability. In this section, we describe their basic characteristics, summarized in Table 2.

Table 2.
Comparison of IEEE 802.11p, IEEE 802.11bd, 4G and 5G technologies for IoV.
- IEEE 802.11p/WAVE: The 802.11p (WAVE: wireless access in vehicular environments) protocol adapted the IEEE 802.11 PHY/MAC layer specification to the vehicular environment and termed it dedicated short-range communications (DSRC). It provides V2V and V2I communication using a 10 MHz wide channel at 5.9 GHz. Various regional bodies define spectrum utilization for IoV. In Europe, ITS-G5 allocated a total of 40 MHz in the frequency range of 5875–5915 MHz for safety-related road ITS. In addition, the frequency range 5915–5925 MHz was prioritized for urban rail ITS, but could also be used for road ITS once ETSI establishes polite protocols and proper co-channel sharing mechanisms between road ITS and urban rail ITS [32]. IEEE 802.11p uses binary convolutional coding (BCC) which is weaker than low-density parity-check coding (LDPC) or turbo-coding in higher modulation and coding schemes (MCS). This is addressed in the IEEE 802.11bd amendment which offers twice the performance, supporting speeds up to 500 km/h, and twice the communication range of 802.11p, due to its use of LDPC coding and 256 QAM modulation. 802.11bd is expected to be approved in 2022.Similarly, the US Federal Communication Commission had allocated 75 MHz (frequency range from 5850 MHz to 5925 MHz) for V2X applications. However, on 3 May 2021 it decided to reallocate 45 MHz of the 75 MHz spectrum to unlicensed devices, such as Wi-Fi. As a result, from this date on, only the 30 MHz between 5895 and 5925 will remain for safety applications using vehicle-to-everything (V2X) communication [33].
- LTE Cellular V2X (C-V2X): LTE cellular vehicle-to-everything (C-V2X) is a 3GPP standard that uses the PC5 interface at 5.9 GHz. Employing high capacity, large cell infrastructure, it enables communication between vehicles, humans, and infrastructure. It consists of vehicle-to-vehicle (V2V), vehicle-to-infrastructure (V2I) and vehicle-to-person (V2) communication. It represents an alternative to the IEEE 802.11p standard, that supports direct vehicle-to-vehicle communication even without cellular base station involvement. C-V2X is continually evolving over 3GPP releases. It was introduced in 3GPP release 14, completed in 2017. In Release 15, further enhancements were introduced. In 5G, further performance improvements will be attained, replacing C-V2X with New Radio (NR). It should be noted that C-V2X and DSRC are not compatible with each other.
- 5G and Beyond 5G NR V2X: Some IoV applications, such as self-driving vehicles, require that the transmission delay is less than one millisecond. The IoV of tomorrow will require higher throughput, lower latency, higher reliability and multicast capabilities, while supporting mobility up to 500 km/h and application-aware services. Thus, NR C-V2X in release 16 offers backward compatibility with Rel. 14 and Rel. 15 for safety, multicast messages, and advanced-use-case (transport profile) capabilities. Spectrum and energy efficiencies are improved by deploying massive multi-input multi-output (MIMO) and millimeter-wave technologies.Figure 3 shows the spectrum allocation in Europe and the US. The frequencies from 5945 to 6425 MHz have been assigned to very low power wireless access systems (VLPWAS), including radio local area networks (RLANs) for public and private applications, regardless of the underlying network topology in Europe, with a maximum effective isotropic radiated power (EIRP) of 14 dBm [34]. In the US, FCC has allocated the same band under the control of an automated frequency control (AFC) system to protect incumbent users, at the standard power levels that are currently permitted in the 5 GHz band [35]. More details can be found in [32].
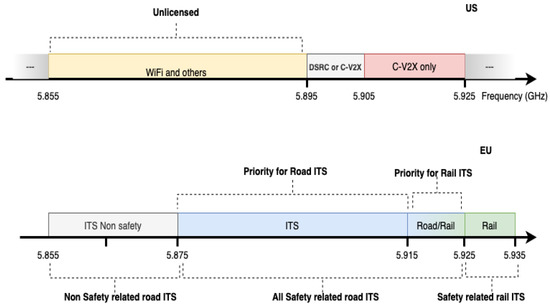 Figure 3. ITS Spectrum allocation in US and Europe.
Figure 3. ITS Spectrum allocation in US and Europe. - Heterogeneous Wireless Access: Combining the strengths of both IEEE802.11p and cellular leverages while tempering their weaknesses. QoS-based service can be provided with cellular networks offering high-throughput entertainment services while DSRC handles vehicle safety.
2.3. Layered Architectures and Standards
Several IoV architectures have been devised by researchers [1,36,37,38,39]. Bonomi [40] proposed a four-layer architecture that includes embedded devices and sensors, multi-service edge, core, data center and cloud. Kaiwartya et al. [1] proposed a five-layer architecture (perception layer, coordination, artificial intelligence, application, business). A 13-layer scheme with three-dimensional system architecture (dimension of IoV, intelligent computing, and real-time big data analytics) has even been proposed [39]. Zhuang et al. [41] presented an SDN/NFV-enabled network architecture for IoV. Chen et al. [42] proposed a Cognitive Internet of Vehicles architecture.
Various researchers and industries are pursuing the development of novel network architectures and solutions that could facilitate IoV implementation [43]. The European Telecommunications Standards Institute (ETSI) in Europe and the Federal Communication Commission (FCC) in the US have proposed architectural standards for IoV. Approaches including cooperative awareness messages (CAMs) for transmitting geographically aware information with relevant data for other vehicles, decentralized environmental notification messages (DENMs), local dynamic maps (LDMs), a key technology for integrating static, temporary, and dynamic information in a geographical context, and geonetworking addressing for geolocation-based routing, have been added to the traditional TCP/IP-based model.
Despite ongoing efforts, there is no universal and comprehensive architecture for IoV. To fully implement IoV, different sectors (researchers, automotive manufacturers, standardization organizations, city planners, etc.) must collaborate.
3. Information Centric Networking (ICN)
Current Internet architecture is a host-centric design based on the TCP/IP protocol which was developed in the 1970s and adopted as the protocol standard for ARPANET (the predecessor of the Internet) in 1983. A great deal of research has been undertaken to address the limitations of TCP/IP networks in terms of scalability, transmission efficiency, mobility, and security.
ICN is an emerging paradigm for the future Internet that involves a radical change. It allows content access regardless of its location by leveraging forwarding, name-based routing, security, and caching. It is proposed to replace the current TCP/IP architecture offering a flexible network structure in the IoT environment.
Many ICN architectures have been proposed over recent years [44], including data-oriented network architecture (DONA) [45], content-centric network (CCN) [7] and named-data networking (NDN) [46]. NDN is one of the four NSF FIA projects aimed at designing the future Internet architectures with the objective of completely overhauling the Internet by replacing IP with content chunks as a universal element of transport. Figure 4 shows the comparison between TCP/IP and NDN.
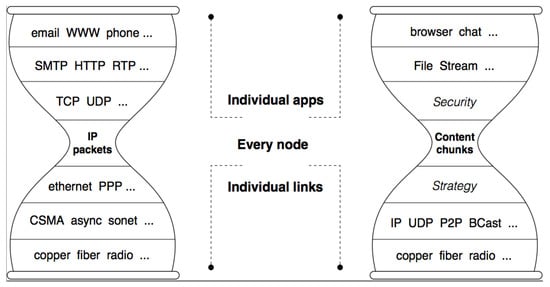
Figure 4.
Comparison of host-centric and information-centric stack [46].
Traditional IP networks need to carry out two operations. The first is performed in the routing (or control) plane, in which the routers communicate routing updates and select the best path for constructing the forwarding information table (FIB). The second operation is performed in the forwarding (or data) plane, and involves following the directives contained in the FIB to perform the forwarding. The routing plane is stateful and can adapt to network changes, including link failure, router crashes, new routes, or alternative better paths. However, the IP forwarding is stateless and cannot adapt to anything without instruction from the routing control plane. This has often been referred to as “smart routing and dumb forwarding”.
NDN replaces the IP dumb-forwarding by stateful forwarding. Instead of distributing IP prefixes, the routing protocols distribute the name prefixes. Stateful forwarding is a process that records incoming interest packets in the PIT and uses the recorded information to forward the retrieved data packets back to the consumers(s). The recorded information can also be used to measure data plane performance, e.g., to adjust interest forwarding strategy decisions. All communication in NDN is performed using two distinct types of packets: interest and data. As shown in Figure 5, each NDN router (vehicles, RSU, BS, MBS, etc.) maintains three major data structures: a content store (CS) for temporary caching of received data packets, a pending interest table (PIT), and a forwarding table (FIB) [47].
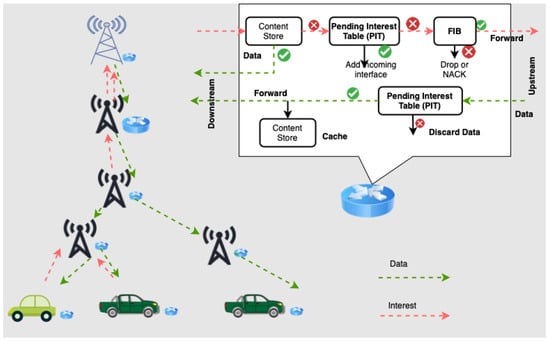
Figure 5.
Typical interest and data communication in NDN communication.
Instead of sending packets between a source and destination devices identified by their numeric IP addresses, NDN disseminates named data at the network level, forwarding names directly that carry application semantics. Moreover, each packet in NDN is secured at the time of production, allowing data replication anywhere in the network and preserving the security properties of the data over its lifetime [48]. The ICN architecture building blocks enabling the shift from a host-centric to a content-centric paradigm are elaborated in the following subsections.
3.1. Content Naming
Content-naming has a direct influence on the other aspects of ICN-based networks, such as routing and forwarding [49]. As ICN changes the focus of traditional networks from host-based to content-based, the data being requested is considered to be an object and given a name that helps users to identify it. Named data objects (NDOs) are the core of addressing and forwarding in the ICN network. NDOs are addressable data units in ICN networks that can represent a collection of bytes or a piece of information. Every NDO, including documents, videos, music, and photos must have a globally unique name.
Four types of naming techniques are used in the ICN literature: hierarchical, flat, attribute-based and hybrid.
- Hierarchical names are given in plain, human-readable components, separated by “/”. CCN and NDN follow this naming convention.
- Flat names are self-certifying and used in ICN architectures such as MobilityFirst [50] and DONA [45]. The content name has two parts of the form and is associated with metadata.
- The attribute-based technique identifies content by attribute-value pairs (AVP). Contents are requested by applying constraints (also called predicates) to the attributes.
- Hybrid-naming combines the previous three techniques.
3.2. Routing and Forwarding
Routing is one of the most critical parts of the ICN/NDN network since it is significantly different from the current Internet architecture. As opposed to routing by the address of a host, ICN routes by the names of the requested data. Two packet types are used in NDN to identify content: interest packets and content packets. Each router maintains three data structures: content store (CS), pending interest table (PIT), and forwarding interest base (FIB). CS stores or caches data, PIT records interest entries and FIB is used to map the outgoing interface for each Interest request. Currently, two approaches are used for routing: name-based and name resolution-based. In name-based routing, the Interest (request for specific content) is routed from the consumer to the producer of the content or cache node using the name of the requested data to resolve the next hop in the network. Name resolution-based routing uses a name-resolution service employing two steps: the consumer node sends messages to the name-resolution server (NRS) with the name of the desired content, and the NRS server resolves the name with a single, or set of, addresses of content producers or caches that have the requested content. NRS provides the name resolution function for translating an object name into some other information, such as a locator, another name, metadata, etc., that is used for forwarding the object requested. More specifically, it is a service that is provided by the ICN infrastructure to help a consumer to reach a specific piece of information. The consumer provides a persistent name and the NRS returns a name or locator that can reach a current instance of the requested object [51].
3.3. Caching
Content caching is one of the fundamental architectural building blocks of ICN networks, enabling fast, reliable, and scalable content delivery. Each NDN node in the network has the capability to cache named content and respond to requests for it. Reacting to a content request, an NDN node either responds directly if it has the content in its local cache, or sends a request message to other nodes. Content is cached once the request is fulfilled. ICN caching democratizes content delivery since caching is implemented by all network routers involved instead of a few specialized cache nodes. Several caching schemes [52] have been proposed for optimal caching and efficient resource utilization.
3.4. Mobility
Mobility refers to the changes in speed and direction of nodes over time. Mobility support at the network layer is a strength of ICN that addresses one of the limitations of IP networks. Consumer mobility is naturally supported in ICN architecture, so a change in the physical location of the consumer node does not affect the delivery of the content. However, producer mobility is more difficult to support as the name resolution system or routing tables in named-based routing need to be updated. To support producer mobility in ICN, different techniques are suggested in the literature [53]. Zafar [54] presented an adaptive content dissemination solution for VANET networks that includes a hierarchical context-aware content naming scheme that enables safety-critical and non-safety applications. Fog-computing-assisted mobility support with information-centric IoV is addressed in [55].
3.5. Security
Data protection and privacy are considered to be fundamental requirements for IoV services. IoV is fundamentally a multi-domain environment with a large number of heterogeneous nodes and services. When designing IoV systems, security and privacy should be carefully considered and integrated. ICN has dramatically changed the traditional security perspective from securing the communication path to securing the content itself. Protection and trust are implemented at the packet level rather than at the communication channel level. As a result, data trust is decoupled from how and where data are stored and no secure connection setup is necessary [56].
4. Edge Computing
Cloud computing began as a solution for the storage and processing of large-scale data. However, in recent years, the massive growth in smart and connected devices, coupled with technologies such as IoT, V2X, augmented reality (AR), etc., has presented challenges to centralized cloud computing. The requirements for ultra-low latency and real-time response, high bandwidth, mobility support, and context-awareness services are the focus of researchers in academia and industry.
According to Gartner, it is estimated that 75% of data in 2025 will be processed outside the traditional data center [57]. Edge computing aims to bring cloud computing services closer to the end-user for a real-time, context-aware response. It comprises a continually expanding set of connected devices and systems that gather and analyze data close to the users. According to Intel predictions, an autonomous vehicle will generate about 4 TB of data in an hour (1 GB of data is generated every second). In the following, we review edge computing approaches including fog computing [5], cloudlets [6], and mobile edge computing (MEC) [58]. A detailed comparison of fog computing, cloudlets, and MEC is presented in [59]. Table 3 shows a comparison of different computing strategies. Various vendors, including Microsoft Azure [60], Cisco Edge Computing [61], and IBM [62] are already employing edge computing. Some approaches to edge computing described in the literature are:

Table 3.
Comparison of Cloud Computing, Fog Computing, Mobile Edge Computing and Cloudlets.
- Fog computing: Fog computing is proposed to address the issue of the large latency between mobile devices and the cloud. Bonomi et al. [5] presented its purpose and key characteristics. It is a highly virtual platform to provide computing, storage, and networking services closer to end devices than the Cloud. In general, it offers the following benefits: quick response to delay-sensitive applications, such as emergency and multimedia applications, data aggregation, data protection and security, context-aware and location-aware service provisioning [63]. Details on fog computing can be found in [64].
- Cloudlets: Cloudlets are a project developed by CMU (Carnegie Mellon Unversity) [6]. They provide the middle tier in a three-tier hierarchy: mobile device–cloudlet–cloud. Their main goal is to merge mobile computing and cloud computing by introducing a middle-tier forming a multi-hierarchical structure. They can be viewed as “data centers in a box”, whose goal is to “bring the cloud closer” by means of low end-to-end latency and high bandwidth. Mobile end devices can offload computational tasks to a cloudlet.
- Mobile edge computing (MEC). Mobile edge computing is a European Telecommunications Standards Institute (ETSI) initiative to provide IT and cloud-computing capabilities within the RAN (radio area network) in close proximity to mobile subscribers. The RAN edge offers a service environment with ultra-low latency and high bandwidth, as well as direct access to real-time RAN information (subscriber location, cell load, channel load, etc.) and is well-suited to provide context-related services.
5. Machine Learning, Deep Learning and Artificial Intelligence
AI is a discipline inspired by human intelligence used to predict, automate, and optimize tasks that humans have historically performed, such as speech and vision recognition, and decision-making. Application areas include computer vision and natural language processing (NLP). Machine learning, deep learning, generative adversarial networks (GAN) [65] and federated learning are some of the AI methods used.
Machine learning (ML) allows machines to become more accurate at prediction or classification without explicitly being programmed to do so. Machine learning algorithms use training data to build a model. There are three broad classes of ML: supervised learning, unsupervised learning and reinforcement learning. It leverages tagged data sets to build a model that is then applied to a specific inference task.
Deep learning is a subset of machine learning that uses several layers of artificial neural networks (ANN), such as convolutional neural networks (CNN), recurrent neural networks (RNN) and deep reinforcement learning (DRL). In recent years it has advanced significantly in the performance of classification and prediction tasks.
5.1. Convolutional Neural Networks
The CNN-based model led to a breakthrough in object detection and recognition. This development made CNNs attractive for entirely novel application domains in IIoV. Intelligent vehicles rely heavily on object detectors for perception, pathfinding and other decision-making. CNNs are mainly applied to analyze image-based applications. Since 2012, several CNN algorithms and architectures have been proposed, such as R-CNN and its variants, as well as YOLO. R-CNN is a region-based CNN, proposed in [66], which combines region-based algorithms with CNN. The purpose of R-CNN is to extract 2000 regions through selective search, then, instead of working on the whole image, classification is performed on the selected regions. YOLO was introduced in 2016 using an approach known as, “You only look once” [67]. In contrast to region-based approaches, YOLO passes the n-by-n image only once in a fully convolutional neural network (FCNN), which makes it quite fast. It splits the image into grids of dimension m-by-m and generates bounding boxes and their class probabilities. Figure 6 shows a typical CNN learning process and object detection (e.g., vehicle, pedestrian, RSU).
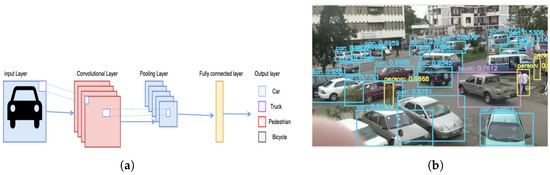
Figure 6.
CNN and example of object-detection application of autonomous vehicle in IoV (a) Typical CNN learning process. (b) Object detection in IoV context.
5.2. Recurrent Neural Networks
Recurrent neural networks (RNN) employ sequential or time-series data and are distinguished by their “memory” elements, which aid in the storage of earlier knowledge and influence the present input and output of the network. Unlike traditional deep neural networks, in which inputs are independent of outputs, RNN output is dependent on the sequence’s preceding parts. Variant RNN architectures proposed include vanilla recurrent neural networks, long short-term memory (LSTM), and gated recurrent units (GRU). RNN in IoV can be used to predict the future position and velocity of each of the dynamic objects detected in the scene (for example, vehicles and pedestrians) and thus provide essential input information, such as autonomous cruise control and autonomous emergency braking. Figure 7 shows a typical computational graph of a basic RNN and its application in vehicle positioning and speed prediction.
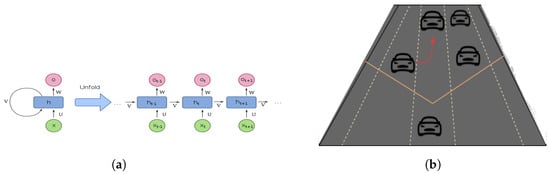
Figure 7.
RNN and example of position prediction application of autonomous vehicle in IoV [68]. (a) Typical RNN. (b) Position prediction.
5.3. Reinforcement Learning
Reinforcement learning is a special type of machine learning in which the learner (agent) interacts with the environment to learn optimal policies required to map states to actions. The agent senses the current status of the environment and takes the corresponding action, after which it earns a reward, while the environment changes to a new state. The goal of RL is to create an intelligent agent that can perform efficient policies to maximize the rewards. Figure 8 demonstrates the general RL framework.
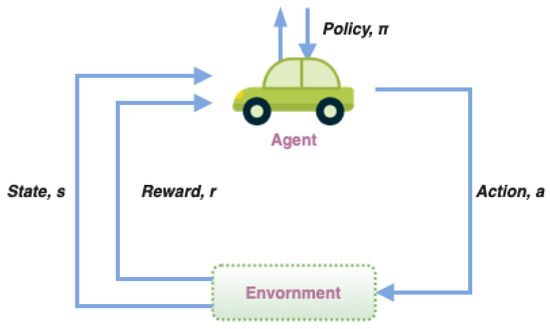
Figure 8.
Typical reinforcement learning process.
5.4. Federated Learning
Federated learning, also known as collaborative learning, trains an algorithm across multiple decentralized devices without sharing training data samples. Federated learning allows numerous players to develop a common, strong machine learning model addressing crucial issues such as data privacy, security, data access rights, and access to heterogeneous data. Figure 9 shows a typical federating learning IoV scenario; in Figure 9a, the RSU enabled the aggregation of federated learning, and in Figure 9b, the selected vehicle enabled the model aggregation.
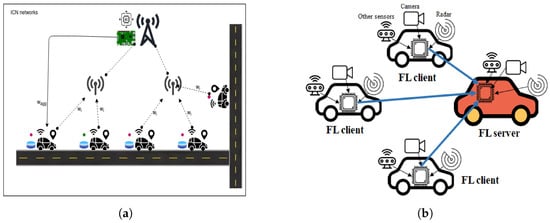
Figure 9.
IoV FL process [69]. (a) Federated learning performed on RSU (V2I). (b) Federated learning among vehicles (V2V).
5.5. TinyML
TinyML is a growing field of machine learning technologies and applications, comprising hardware, algorithms and software, which are capable of processing sensor data at low power, thus enabling a variety of applications. TinyML enables application of deep learning models to micro controllers, allowing machine learning models to run on embedded systems that have limited computing and storage resources [70]. TinyML has enormous potential in the context of IoV. For example, the authors of [71] utilized TinyML for IoV in anomaly detection. Similarly, [72] proposed autonomous driving for mini-vehicles considering limited onboard storage and computing capabilities. Figure 10 shows TinyML applied in an IOV environment.
Figure 10.
Typical IoV TinyML.
6. ICN and Edge Computing Convergence Suitability Analysis for IIoV
In this section, we present a convergence and suitability analysis of ICN, edge computing and AI for existing and future IoV applications that require efficient, reliable, secure and scalable communication infrastructure and architecture for seamless integration, and cooperation among entities in IoV networks.
6.1. Converged IoV Infrastructure
The benefits of ICN for IoV stem from the fact that a requested content might be located in a server far away from the current vehicle position, but it also might have been cached in a closer repository, easily accessed by its named content, thus reducing the latency and backhaul traffic. This is particularly relevant due to the dynamic aspect of IoV; the content might even be cached in a nearby vehicle. ICN promises efficient content delivery, and supports mobility, scalability, and security. It allows Internet applications to be developed based on named requests, caching, and any-casting. Because of its various advantages, ICN offers an interesting solution for IoV communications and seems to fit perfectly with many IoV applications [18,19]. Its in-network content caching and forwarding methods enable the dissemination of information between different vehicles in the network. In the ICN context, vehicles can be consumers, producers, and data forwarders at the same time; RSUs, BSs, and core network elements can provide NDN forwarding and caching capability. For an efficient ICN-based IoV network, all ICN core elements described in Section II should be optimized to meet the frequent topology changes of IoV networks. Intelligent and adaptive naming, routing/forwarding, security/privacy, and mobility-aware design are necessary to provide efficient IoV applications and services, as described in the following section.
Edge computing is another enabling technology that meets the time-sensitive requirements of IoV to offer pervasive services for massive numbers of connected vehicles with low latency and very large bandwidth. Traditionally, cloud computing offered computational, storage, and on-demand services to a far away user. However, as many IoV applications require low latency and high bandwidth, edge computing provides services in close proximity to end-users. Future Internet applications require low latency, high security, mobility, and scalable content distribution. Edge computing for IoV is an ideal solution to remove the burden on backhaul networks. However, existing TCP/IP-based edge computing solutions have some weaknesses when applied to support cloud services at the edge of the network. Edge computing offers many benefits associated with latency challenges, as it provides high bandwidth close to the user. In addition, advanced computing enables the processing of real-time tasks closer to the source or even on it.
In recent years, the marriage of edge computing and AI has spawned a new research area called edge intelligence [70]. Similarly, the marriage of ICN and AI has spawned intelligent networking. Recent advances in deep learning have accelerated the realization of autonomous vehicles. Edge computing, which is one of the strategies of 5G, provides an optimal service for real-time access and high bandwidth. ICN and edge computing can be combined, resulting in synergistic benefits for IoV. Several AI approaches have been used for solving problems in IoV and autonomous vehicles. Table 4 shows the mutual benefits of the synergy of ICN and edge computing. Figure 11 shows the convergence of ICN, edge computing and AI for IIoV.

Table 4.
Role of AI in mutual benefits of ICN and edge computing for IIoV.

Figure 11.
The convergence of ICN-Edge Computing-AI for IIoV.
ICN and edge computing are essential for achieving this goal. By leveraging the ICN perspective, vehicular users can obtain multimedia chunks via the vehicle-edge-cloud approach to improve the delivery quality. ICN with edge computing is an excellent fit and allows adaptive video delivery optimization. This enables traffic optimization on the edge, in addition to backhaul and core networks using in-network caching. Caching multimedia content, based on popularity, request pattern, and quality awareness (e.g., user device capability and type, available bandwidth, etc.), is possible through ICN and edge computing. Moreover, with the prevalence of content caching in edge computing, it is possible to have multiple active links and load balancing on dynamics and mobile conditions.
Figure 12 shows the proposed IIoV layered protocol stack. It consists of different layers, such as physical, access, edge, ICN, and application, as well as security, AI, and intelligence dimensions. The ICN layer is an intermediate layer that provides core NDN aspects (naming, forwarding/routing, mobility, caching). The physical layer encompasses the various wireless communication interfaces (Wi-Fi, 4G/5G) employed by the ICN node for better availability of content and its distribution.
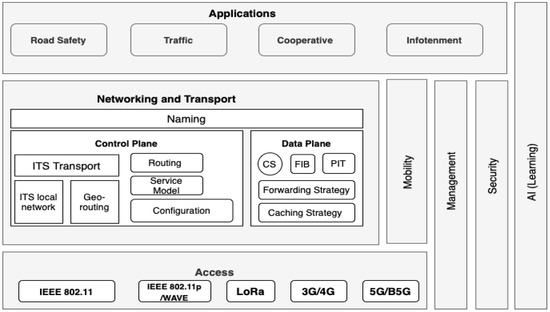
Figure 12.
Protocol stack of converged architecture for ICN IIoV.
6.2. Collaborative Perception and Driving: Use Case
To demonstrate the potential of ICN and EC convergence in the realization of IIoV, we conducted a suitability analysis by exploring enabling technologies and considering cooperative perception and driving as a use case. In the cooperative driving use case, large vehicles, such as trucks and minivans, share camera views of road conditions ahead of them with lagging vehicles. A driver in front might warn the lagging driver intending to pass about an oncoming vehicle in the passing lane with the goal of preventing catastrophic head-on collisions during overtaking. Consider the scenario shown in Figure 13, where two connected autonomous vehicles are moving one behind the other, in the same lane, while engaged in cooperative collaborative perception to improve their individual capabilities and exchange safety information through V2X communications. The driver of vehicle A in front spots a pedestrian ahead on the adjacent lane, which is not in the field of view of vehicle B in the rear, as vehicle A has obstructed the view. Vehicle B is planning to make a passing/overtaking maneuver, but it is unaware of the pedestrian. The knowledge about the pedestrian becomes crucial for vehicle B, as it would not have enough time to avoid colliding with the pedestrian after the lane change. The remedy would be to avoid performing the lane change at this time. Accurate perception of the surrounding environment is a vital requirement for safety. In cooperative driving, vehicles exchange safety information in a variety of ways—vehicles could share raw sensor data; however it would require significant communication bandwidth which cannot always be guaranteed. Another option is to exchange information about the detected objects including their position, speed, etc., as cooperative awareness messages (CAMs). Thus, cooperative and autonomous driving is one application of IoV that should benefit from the synergy of ICN and edge computing. The content distribution and caching capability of ICN networks can be leveraged to share cooperative awareness messages (CAMs) among vehicles. On the other hand, edge computing enables services to be deployed and provides local computing and storage. For instance, by caching and reusing computation results, other consumers can avoid repeating computations. Interests aggregation can also be performed on edge nodes thus avoiding duplicates of interests for the same content from multiple consumers. Therefore, ICN and edge computing share complementary properties, local storage, and the ability to reduce latency, enhance mobility, and ensure scalability.
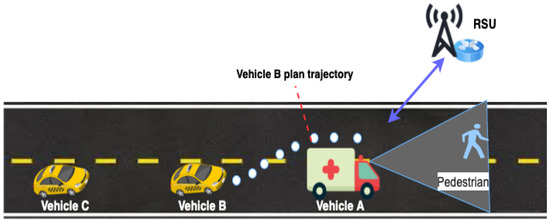
Figure 13.
Collaborative driving—see through.
7. Edge Intelligence and Networking for IoV
With the goal of providing intelligent AI applications, a new computing and networking paradigm named Edge AI has been introduced. In the following, we present recent research on intelligent edge networking, edge computing, and caching in the context of the IoV domain. Table 5 summarizes the area where AI/ML/DL techniques solve bottleneck problems and realize converged IIoV.

Table 5.
Summary of AI techniques in different aspects of ICN and edge computing.
7.1. Edge Computing Intelligence for IoV
Intelligent IoV should use a variety of intelligent computing platforms, such as cloud computing intelligence, edge computing, and on-vehicle intelligence. Providing intelligence at each layer of the IoV network architecture helps to meet the different requirements of IoV applications. IIoV will facilitate urban traffic management, vehicle insurance, road infrastructure building and repair, logistics and transit, in addition to vehicle driving and safety. IoV must be interconnected with other systems, such as Smart City, as a special case of the Internet of Things (IoT). Cloud computing and intelligence are mostly employed in this scenario for training and inference of AI models with massive datasets, as well as aggregating non-real-time data for wide-area networks deployed on the cloud.
To overcome excessive latency in cloud computing, edge computing and intelligence can support IoV for processing delay-sensitive computational tasks, such as road-side image processing, aggregating, and storing local information. Edge computing devices can be deployed on different edge nodes, such as on the RSU, BS, and vehicles having powerful onboard processing capabilities. Edge nodes provide computational services. The vehicle can offload tasks using either binary offloading or partial offloading schemes. Binary offloading is when the device determines whether the task is to be executed locally or to be offloaded to the edge server, depending on the workload of the server and the QoS requirements. In partial offloading the computational task is partitioned and executed on both the local device and an edge server. In [73], an edge learning framework is proposed and is demonstrated to reduce network traffic by 80% and running time by 69% over state-of-the-art cloud-based solutions. The author of [74] proposes edge-based data analysis and task allocation. Edge computing resources are utilized and task distribution for edge nodes based on game theory is applied. In [75], a novel real-time video analytics process is demonstrated using low-cost IoT devices and LoRaWAN networks to realize new services and applications that include traffic management through IoT edge computing.
Edge computing and intelligence also support privacy-aware services employing federated learning at the edge. Edge devices provide a communication efficient and privacy-preserving federated learning framework for enhancing the performance of IoV, whereby in-vehicle learning models are trained by exchanging inputs, outputs, and their learning parameters locally, as described in [22]. Vehicles can transform into mobile data centers, perform federated learning to enhance transmission control protocol (TCP) performance over WiFi, and react in a timely way to the Internet to meet vehicles’ needs.
An energy-efficient computational offloading scheme employing deep reinforcement learning for the Intelligent Internet of Vehicles is discussed in [76].
Addressing the issue of running DNN, which require tremendous computational resources, high energy consumption and significant latency, the authors of [70] propose a collaborative framework for DNN co-inference between edge and end devices. The effectiveness of the framework was tested on a Raspberry Pi.
Newer vehicles are equipped with a powerful onboard unit that can provide computing capabilities for other sensors in the vehicle or cooperate with other vehicles. On-vehicle intelligence is an approach for processing high delay-sensitive tasks, such as real-time decision-making for vehicle control. Intelligent sensors utilize advanced signal processing techniques, data fusion, intelligent algorithms, and AI to understand sensor data, for better integration of sensors and feature extraction, leading to measures that can be used in smart sensing applications. In [77], a vehicle vibration sensor is used to classify and monitor road conditions. TinyML is a novel paradigm that enables low-end client devices to leverage machine learning techniques by deploying lean models previously developed on freely available cloud platforms [78]. It enables the performance of predictive maintenance by monitoring certain parameters and drawing conclusions based on ML to predict future faults.
7.2. Intelligent Edge Caching for IoV
The contents of IoV applications, either safety or non-safety, are likely to be transient, characterized by a limited lifespan and to become invalid after a certain period of time. Information, such as traffic conditions of certain road segments, will change after a few minutes after being reported by the source (producer) [79]. Thus, these transient contents have an impact on in-networking caching and forwarding decisions for NDN-based networks.
A comprehensive literature review on caching transient contents in vehicular NDN is provided in [80].
Caching improves the distribution and availability of contents and services in ICN [14]. It enhances the network performance by storing contents or services that are frequently used, to improve retrieval time and throughput, thus guaranteeing the quality of user experience (QoE). Cache management is one of the essential elements of NDN. Routing and forwarding are supported since nodes can cache content and interests. Content-caching issues include cache placement and cache replacement. Cache placement refers to which content and where to cache, while cache replacement refers to how long to cache in order to maximize the long-term average hit ratio. Traditional cache replacements include FIFO, LRU, and LFU. Content caching is challenging because of the dynamic and high mobility nature of IoV networks, content growth and sporadic demand of content, delay-sensitive applications, and limited cache capacity.
In IoV networks, caching can be performed on vehicles, on RSUs, on BSs, or jointly. For example, RSU caching minimizes the latency of retrieving contents and increases the cache hit ratio. Quick response time and storage efficiency are the two main factors to be considered for the cache management scheme. Caching popular content near the user improves efficiency.
Several cache management methods have been proposed to improve the efficiency of NDN. In the vehicular context they include: mobility-aware caching, delay-aware caching, proactive caching, probabilistic caching, and cooperative caching. For example, The authors of [81] proposed a limited domain cache (LdC), which simultaneously considers cache hit rate and the popularity of contents factors.
Recently, learning-based approaches have been used to design and optimize edge caching. In the following, we discuss representative studies that employ intelligent caching for IoV. The authors of [82] propose a cooperative edge caching framework which aims to exploit cooperation among BSs, RSUs, and connected vehicles. In [83], joint task caching and computational offloading for vehicular edge computing are proposed.
Performance evaluation and applicability analysis of different machine learning models for caching and routing have been addressed in [84]. Content popularity and request stream correlation are factors that affect cache performance and routing.
In [85], a deep-learning-based content caching framework, DeepCache, is proposed. The popularity of the content is predicted using an LSTM-based model. Similarly, [86] uses content popularity and user location to create an intelligent cache for content-centric networks. The approach is that of an optimization problem to determine which type of content should be cached in which router at a given time, thus classifying it as either normal or popular.
Content replacement is also an important issue in content caching. In [87], a dueling deep-q-network-based delay-aware cache update policy for fog radio access is employed and compared with the traditional caching replacement policies, i.e, FIFO, LRU, and LFU. The paper considers user mobility and time-varying channel states to improve the performance of the caching strategy.
7.3. Edge Network Intelligence for IoV
An edge network, in the context of IoV, can be defined as an autonomous network consisting of smart vehicles, a set of RSUs and BSs offering services without any prior configuration. The nodes in the network should have computation and caching capabilities. Each node in the network could have a multi-wireless interface to access services (e.g., 4G/5G, Wi-Fi) single-hop or multi-hop.
Network intelligence should allow autonomous devices to join edge networks, discover the services offered, gain seamless access to the services, and be coordinated with other entities in the network. Thus, edge networks need to have built-in embedded intelligence to allow better agility, resiliency, faster customization, and security. Indeed, embedding intelligence into the network will provide a much higher level of automation, enabling faster deployment, dynamic provisioning adapted to the nature of network functions, and end-to-end orchestration for coherent deployment of network infrastructures and service chains. It will also result in enhanced resilience and improved availability of future networks and services. In the next subsection, we review some of the latest research on this topic.
7.3.1. ICN-Based Naming and Resource Discovery for IoV Networks
Naming is one of the most significant networking aspects in NDN networks, used to identify the contents, as well as other network functionalities, including forwarding, caching, mobility, security, etc. [88]. ICN decouples content from its location and enables it to be easily retrieved, not only from the original server (producer), but also from the in-network caching nodes in the subsequent content request. Furthermore, it also provides interest aggregation for the requests from different consumers for common content, which, in turn, reduces interest packet traffic. ICN naming brings significant help to IoV communications by allowing vehicles to cache content, and also to forward interest, based on the content name instead of the address of the host, as the IoV environment is characterized by rapid changes and short connectivity duration.
However, NDN-based naming for IoV is challenging and most existing ICN frameworks assume that consumers are ex ante aware of the service and resource name. The consumer node sends out an interest packet that carries a name that identifies the desired content. However, vehicular users connecting to the network may not be aware of the name of the content or service of interest. A robust content naming design is needed to allow producers to describe precisely what it has and consumers to express which information they need. Existing research attempts to design content names for the IoV are based on specific use cases.
In [54], a hierarchical context-aware content naming scheme for NDN-based VANET, that enables naming of both safety and non-safety application contents, is proposed. It exploits the coding scheme to represent most of the content names. It follows the following naming scheme: content type (1 bit, safety or non-safety), content scope (1 bit, local or global), content format (2 bits, 00 for text, 11 for video, 01 for picture, and 10 for audio), application types (4 bits for main type + 4 bits subtype ), to represent 32 different applications, timestamps, GPS locations, content sizes, and content file types.
In [89], a naming scheme for a vehicular content-centric network is proposed with the purpose of uniquely identifying the content generated by vehicles using a hierarchical and hash-based naming scheme. The hierarchical naming scheme is partly used for content name prefix aggregation and as an aid for a routing and hash-based naming scheme to help maintain content integrity.
In [90], the authors argue that the existing conventional hierarchical or hybrid NDN naming schema are inefficient to extract contents that are transient in nature and present instead a named-based query and command mechanism (NINQ) framework for ICN-based IoT. The authors of [54] present an adaptive content dissemination solution for VANET networks that includes hierarchical context-aware content naming schemes that enable both safety-critical and non-safety applications. To guarantee that the forwarding and processing rules of the packets are correct, [91] proposes a name space analysis framework to model and analyze NDN data planes using header space analysis.
Another challenge with NDN naming is the issue of name lookup in a large-scale namespace in the forwarding plane of the content router. Managing FIBs at an NDN router is challenging having long content names or name prefixes. In [92], a method is proposed to compress FIB with the goals of reducing the required router storage space and meeting the demands of routing efficiently
The authors of [93] propose a neural network-based solution named Pyramid-NN, which builds an index with the aim of reducing memory consumption and false positive rates while increasing the lookup speed.
Thus, an adaptive naming mechanism that exploits AI techniques is required to help vehicular nodes to identify available resources and to provide seamless service and resource discovery. For example, a naming technique based on natural language processing (NLP) is proposed in [94]. In this study, an AI-based application module assigns names for the content based on the event captured by cameras and sensors that describe the types of events and their geographical locations.
7.3.2. Intelligent Forwarding and Routing for IIoV
The named-data link state routing (NLSR) protocol [95] is one of the routing protocols for ICN networks that allows the router to return the content if it exists in the cache or to forward the interest packets to the nearest content router without predicting the probable location of the content. The same protocol was evaluated in [96] to test its real-world performance in a test-bed. Multipath forwarding and in-network caching (MUCA), proposed in [97], is an intra-domain name-based routing protocol that utilizes multi-path forwarding, link state database synchronization and in-network caching. The paper claims that MUCA outperforms the existing named-data link-state routing protocol (NLSR) [95]; however, according to [98] it is obsolete. The authors of [99] propose instead a multi-criteria decision-making (MCDM) approach based on interest forwarding and cooperative data caching.
Recently some research has been undertaken in designing an intelligent forwarding strategy. For example, [100] used a support vector machine (SVM) to forecast the success of interest packets in predicting content cached locations with the aim of minimizing the content search time and to maximize throughput. As an NDN-forwarding plane enables choosing the next forwarding hop independently, without relying on routing, an intelligent forwarding strategy can be designed for adaptive and intelligent data forwarding [101]. Similarly, [101] proposed FS-RL, an intelligent forwarding strategy based on RL in named-data networking. Moreover, the authors of [102] considered the feasibility of using reinforcement learning, specifically Q-learning for efficient and adaptive forwarding in NDN networks. They achieved higher interest satisfaction and shorter delay compared with the existing BestRoute and Flooding strategies. In [103], a random neural-network-based reinforcement learning interest forwarding scheme was proposed. The forwarding scheme takes advantage of the in-network caching capability of NDN architecture.
A routing protocol for vehicular named data networking was proposed in [104] to address the problem of reverse path partitioning (RPP) during consumer mobility. The mechanism, auxiliary forwarding set (AFS), considers mobility factors to identify and select forwarding nodes. The authors of [105] proposed a new method using Bloom filters which combine routing of network connectivity with a building and forwarding engine. A fuzzy interest forwarding approach that exploits semantic similarities between the names carried in interest packets and the names of potentially matching data in CS and entries in FIB is proposed in [106]. These are promising initiatives but they do not evaluate large-scale, highly dynamic, and frequently changing topologies which are a primary characteristic of IoV networks.
7.3.3. Mobility Support for IIoV
Mobility is an integral part of IoV. Thus, mobility management is an important network function, which still presents a challenge. Mobility management should support continuous user communication while on the move without interruption. Different mobility types and scenarios should be considered when developing mobility support solutions for IIoV [107]. In an ICN/NDN-based IoV environment, each vehicle might operate simultaneously as an information producer and consumer. Vehicular consumers send their requests directly to the next NDN router mentioning the content name, but they do not know the location of the content in which they are interested. The NDN router is then responsible for forwarding the consumer’s interest to the node where the content is stored. Experimental-based NDN solutions for VANET supporting various communications categories (V2V, V2I, and V2R) have been produced and have demonstrated their potential to improve the QoS of VANETs [108]. Furthermore, the authors of [109] examined the promising potential of NDN for connected vehicle applications. However, the support of fast mobility and a large number of vehicle-aware solutions and frameworks needs to be improved. Most ICN architecture designs claim to inherently support consumer mobility; however, the challenge is when the producer node also moves. Recent studies, such as [110], argue that the existing schemes to address consumer mobility have shortcomings as they waste bandwidth and mobile consumers may miss real-time content during handover. The paper proposes a softwarized and MEC-enabled protocol architecture supporting consumer mobility in ICN and claims improvement in the communication overhead by 99.93%.
Producer mobility is more complicated since the NDN naming scheme does not include location information. A number of studies, such as those of [111,112,113,114,115], address producer mobility. Four producer mobility approaches have been presented in the literature: location resolution, triangular, locator/identifier separation, and routing-based. They can be divided into two categories: anchor-based and anchorless schemes. Most approaches utilize anchor nodes to hide the producer node movement. These use an anchor node or rendezvous server to track the current locations of contents. The anchor node holds the binding information for content and its location. It always interacts with the mobile producer to maintain updated binding information. This is a similar approach to that of home agent mobility in IP networks. However, such an approach causes suboptimal routing problems and signaling overhead. In the anchor-less scheme [112], mobile producers send special announcements to the previously contacted NDN access router (NAR) whenever it changes the point of attachment.
Recently, intelligent mechanisms have been proposed to address producer mobility in the ICN context. In [116] a proxy-based mobility support approach called PMNDN is proposed. The proxy entity is responsible for maintaining the reachability of the user. The authors of [113] present producer mobility solutions using NDN in an IoT context. Seamless service-driven mobility support, as a service that caters to both host-driven and network driven mobility, is considered in [117]. In [118], anchor-less producer mobility management in named data networking for real-time multimedia is proposed. Similarly, in [119], the authors proposed supporting producer mobility via named data networking in an integrated space-terrestrial scheme. The optimal producer mobility support solution (OPMSS) [111] is proposed to minimize unnecessary interest packet losses and delay, while providing an optimization path for data when the mobile producer relocates. In [115], the authors propose a lightweight machine-learning-based strategy to predict the position of the producer in advance and to determine whether or not handover occurs. It uses an echo state network (ESN), which is a type of fast converging recurrent neural network that uses simple linear regression.
7.3.4. Security and Privacy for IIoV
Security and privacy concerns are still challenging for NDN-based IoV networks [2]. In a non-trustable distributed environment, blockchain technology is being used to establish a creditworthy ecosystem among independent participants. IoV networks can leverage the potential of blockchain technology in IoV environments. Researchers discuss different solutions to utilize blockchain technology. For example, [120] proposes blockchain-based security architecture for NDN-based IoV networks using consensus algorithms and performance evaluations of its effectiveness in key management, cache positioning defense, and access control. In [121], the authors also propose a protocol for secure and privacy-friendly service provisioning at the mobile edge that provides a security service between the consumers and producers based on the NDN paradigm. In [122], the researchers apply communication sequential processes (CSP) modeling and verification tools for NDN-based IoV networks to verify vital properties, including deadlock freedom, data availability, PIT deletion faking, and CS caching pollution. The model fails to ensure the security of data in the presence of an intruder, so the authors utilized blockchain to guarantee the security of NDN-based IoV. Recently, machine-learning-based security and privacy solutions have been introduced for intrusion detection in IoT networks to reduce smart vehicle accidents and to detect malicious attacks in vehicular networks. RNN-based solutions might help to detect malicious attacks in IoV. For example, [123] proposes a hybrid deep learning (DL) model based on LSTM and GRU-based solutions for cyber-attack detection in IoV.
8. Issues and Recommendations for Future Research
In spite of the developments discussed, there are still open issues and challenges that need to be addressed to realize the advantages of IIoV. The main purpose of this section is to stimulate the interest of the ICN, Edge, IoV, and AI research communities in the requirements of future intelligent IoV networks. The challenges still to be addressed include: how to build an efficient network framework with edge computing and ICN in IoVs; how and where to place edge servers to service a large and dynamic number of vehicular users; and, how to design efficient caching, offloading, and communication strategies for IoV to provide intelligent services.
8.1. Intelligent Connected Platform
Following the success of cloud-based AI services, products such as Google’s Cloud IoT Edge, Amazon Edge, and Azure IoT Edge, are being provided which extend data processing, analysis, and storage close to endpoints and provide edge computing services. Thus, 5GAA was established with the aim of bringing the automotive and telecommunication industries together to develop end-to-end solutions for future mobility and transportation services. Further partnering has occurred with standardization organizations, such as ETSI. Thus, edge intelligence can become a pervasive paradigm allowing edge devices to develop powerful edge AI functionalities. IIoV as an intelligent connected platform relies on the support of high-tech technologies, such as mobile internet, edge computing, cloud clouting, big data, and AI. The platform should support flexible service deployment, splitting and deploying independently as needed to meet the needs of specific vendors. To fully harness the potential of edge intelligence in IoV, several key challenges must be overcome. Intelligent connected platforms should be compatible with heterogeneous systems. The market potential of this technology will attract many vehicle manufacturers and IT vendors in the future. Thus, a common open standard should be set such that IoV stakeholders can enjoy seamless and smooth services across heterogeneous intelligent connected platforms anytime and anywhere.
8.2. Architecture and Network Heterogeneity Issues
Designing a universal network architecture that encompasses the heterogeneity of IoV is a challenging task. Mobile cloud services can be integrated with the ICN-based IoV to provide access to the information. However, this creates several challenges. Edge nodes execute a considerable amount of computational tasks, including content caching and networking. Using edge nodes, the processing burden and latency are significantly decreased. Furthermore, future smart vehicles will be equipped with various wireless interfaces that should be supported, including WAVE, LTE, 5G, and even satellite-based ones. For efficient content retrieval and communication, the network stack should exploit these multiple wireless interfaces. Interoperability between different variants of ICN, and with existing TCP/IP architecture, must be maintained as IP is currently the dominant protocol on the Internet. Supporting heterogeneity and interoperability is the major challenge.
8.3. Intelligent Distributed Computing and Autonomous Networking
An important aspect of intelligent IoV is the training and deployment of deep learning models. It may be too difficult to model and run computationally intensive deep learning models directly on vehicles. Directly moving data to a central server for training, e.g., at a cloud server, will introduce prohibitive communication overheads. Offloading them to the edge server may cause impairments due to time-varying wireless fading channels and lead to excessive latency when the offloaded data size is large. Besides enjoying the general benefits of edge intelligence, various challenges are presented, such as meeting the QoS requirements of applications, including real time requirements, such as 20–100 ms latency in safety application, high level accuracy and reliability for autonomous vehicles in 3D object detection and inference. Various techniques have been proposed to improve the performance of edge intelligence to enable inferences in IoV networks. Model compression is one enabling technique to alleviate the issue of resource-intensive deep learning models and resource-constrained edge devices. Model partition is another technique to alleviate the burden of executing deep learning models on vehicles, offloading the computational intensive tasks to the edge node (RSU) or other vehicles to obtain models to perform inference. Model partitions can be between vehicle and edge nodes or among vehicles for vehicle-edge node collaboration, according to the current system environment factors, such as network bandwidth, device resource and edge-server load.
Autonomous networking design is important to achieve efficient edge intelligence service provisioning under dynamic heterogeneous wireless network coexistence (e.g., LTE/5G/Wi-Fi/Bluetooth), allowing newly added edge devices to self-configure in a plug-and-play manner. Furthermore, ultra-reliable low-latency communication (URLLC) has been defined in 5G new radio for mission-critical application scenarios that demand low delay and high reliability. Thus, it will be valuable to integrate 5G URLLC capability with edge computing to provide ultra-reliable and low-latency edge services.
8.4. Smart Naming and Discovery
As IoV networks are distributed, intelligent IoV applications will be available in multiple vehicles and edge devices. Vehicles and edge nodes may run different IoV services and generate content. Content- and service-naming enable addressing and identification of content and services. Thus, it is critical to design efficient service- and content-naming schemes and also to service discovery protocols so that consumers can identify and locate the relevant content/service in a timely manner. However, naming in a dynamic environment is challenging due to intermittent connectivity caused by rapid mobility and topology changes. Solutions such as intelligent attribute-value-based naming can help. An adaptive encoding technique would be a viable option to tackle the issue of associating names. However, much more research is needed on this topic.
8.5. Mobility and Context Awareness Issues
In IoV, a thorough knowledge of vehicle mobility is a crucial aspect of continuous IoV services and network management. As vehicles move, the link condition between them and the RSU can change quickly and become intermittent. More significantly, an urban environment can be highly dynamic and complex with many unpredictable factors, such as time-varying traffic densities, buildings, and other structures affecting the V2V and V2I link performance. ICN was considered an alternative to bypass the limitations imposed by traditional IP networks, especially those relating to mobility. Even so, several research challenges remain unresolved, including frequent handovers that may degrade QoS and QoE. ICN supports consumer mobility natively. However, it becomes more complex if the producer also moves. A potential solution could be to locate mobile producers by flooding them with interest packets for path discovery. However, this would increase network traffic and the likelihood of network congestion. Vehicle contextual information, including position, speed, direction, acceleration, road traffic, road condition, and weather information can be effectively obtained from onboard sensors and shared among vehicles to design intelligent context-aware IoV protocols.
8.6. Security and Privacy Preservation
As a result of IoV’s open deployment nature, it could be intercepted by potential attackers resulting in degradation of IoV services. We need to revise security and privacy at different layers (e.g., physical, link, network, session, and application). Blockchain-based solutions are used to provide security and are a suitable fit due to their decentralized nature, as mentioned in Section 7.3.4. However, in specific use cases, such as in connected and autonomous vehicles, vehicles perform collaborative perception and collaborate using collective perception messages (CPMs) to improve road safety and efficiency. Attackers may target CPMs and send false information that jeopardizes safety. Current standardization efforts do not yet include vehicle misbehavior specifications for advanced V2X services, such as collaborative perception (CP) [126].
8.7. Deployment and Orchestration
The IoV network entities, including vehicles, RSUs, and BSs, have heterogeneous storage, computing, routing, and forwarding capabilities. The ideal edge intelligence deployment technique to support as many vehicles as possible to meet the coverage, connectivity, and support of various intelligent services is still a research problem. Thus, the placement of edge intelligence is of paramount importance to improve communication, computing, and caching performance in terms of optimizing the resource allocation with minimal deployment costs and message exchange overheads. Given the large scale of physical IoV networks, we need to determine the minimum number of edge nodes, their location placement, network topology, and their association with BS and MBS to achieve an optimal allocation of resources. An intelligent optimization solution that considers the types, amount, and update frequency of information and available underlying network elements is needed. A clean-slate deployment requires all the network entities to support name-based routing and intelligent forwarding strategies.
9. Conclusions
Due to the fast growth of IoT and IoV, the conventional host-based networking paradigm faces a number of issues, including those related to scalability, mobility, addressing and security. Furthermore, recent applications demand real-time data which necessitates the rethinking of network models. The Internet of Vehicles (IoV) is different from the traditional Internet and other IoT networks, such as weather monitoring, due to the highly dynamic nature, mobility and high density of vehicles, and thus requires special attention. Security is a major concern in vehicle communication. In this paper, we have presented detailed reviews of the convergence of various technologies supporting IIoV, including ICN, edge computing, and AI. Edge intelligence accelerates V2X communication, vehicular edge computing, and intelligent networking, We also analyzed different techniques reported in the literature that use ICN-based communications for IoV networks. Lastly, we presented the requirements and challenges of building an intelligent communication networks architecture and intelligent computation for IoV. We hope that this work will serve as a useful reference in the area of intelligent IoV and inspire new topics of research.
Author Contributions
Conceptualization, S.S.M. and M.Z.; methodology, M.Z.; investigation, S.S.M., M.Z., M.L. and E.P.; resources, S.S.M.; writing—original draft preparation, S.S.M. and E.P.; writing—review and editing, E.P.; visualization, S.S.M.; supervision, M.Z. and M.L.; project administration, M.Z.; funding acquisition, M.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Acknowledgments
The authors would like to thank the STEP and TRIL programmes of the Abdus Salam International Centre for Theoretical Physics (ICTP).
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| AI | Artificial Intelligence | LRU | Least Recently Used |
| ANN | Artificial Neural Network | LSTM | Long Short-Term Memory |
| APU | AI Processing Unit | MANET | Mobile Ad Hoc Networks |
| BS | Base Station | MDP | Markov Decision Process |
| C-RAN | Cloud-Radio Access Networks | MEC | Mobile (Multi-access) Edge Computing |
| CDN | Content Delivery Network | ML | Machine Learning |
| CNN | Convolutional Neural Network | MLP | Multi-Layer Perceptron |
| CAM | Cooperative Awareness Message | NDN | Named Data Networking |
| CS | Content Store | NFV | Network Function Virtualization |
| CV | Computer Vision | NLP | Natural Language Processing |
| D2D | Device to Device | NPU | Neural Processing Unit |
| DNN | Deep Neural Network | PIT | Pending Interest Table |
| DQL | Deep Q-Networks | QoE | Quality of Experience |
| DRL | Deep Reinforcement Learning | QoS | Quality of Service |
| EC | Edge Computing | RL | Reinforcement Learning |
| ETSI | European Telecommunication | RSU | Roadside Unit |
| Standardization Institute | |||
| FCNN | Fully Connected Neural Network | SDN | Software Defined Network |
| FIB | Forwarding Interest Table | SGD | Stochastic Gradient Descent |
| FIFO | First In First Out | TL | Transfer Learning |
| FL | Federated Learning | V2I | Vehicle to Infrastructure |
| GAN | Generative Adversarial Network | V2V | Vehicle to Vehicle |
| GNNs | Graph Neural Networks | V2X | Vehicle to Everything |
| ICN | Information Centric Networks | VANET | Vehicular Ad Hoc Networks |
| IIoV | Intelligent Internet of Vehicles | VR | Virtual Reality |
| IoV | Internet of Vehicle | WAVE | Wireless Access Vehicular Environment |
| ITS | Intelligent Transport Systems |
References
- Kaiwartya, O.; Abdullah, A.H.; Cao, Y.; Altameem, A.; Prasad, M.; Lin, C.T.; Liu, X. Internet of Vehicles: Motivation, Layered Architecture, Network Model, Challenges, and Future Aspects. IEEE Access 2016, 4, 5356–5373. [Google Scholar] [CrossRef]
- Contreras-Castillo, J.; Zeadally, S.; Guerrero-Ibanez, J.A. Internet of Vehicles: Architecture, Protocols, and Security. IEEE Internet Things J. 2018, 5, 3701–3709. [Google Scholar] [CrossRef]
- Storck, C.R.; Duarte-Figueiredo, F. A 5G V2X ecosystem providing internet of vehicles. Sensors 2019, 19, 550. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Shi, W.; Cao, J.; Zhang, Q.; Li, Y.; Xu, L. Edge Computing: Vision and Challenges. IEEE Internet Things J. 2016, 3, 637–646. [Google Scholar] [CrossRef]
- Bonomi, F.; Milito, R.; Zhu, J.; Addepalli, S. Fog computing and its role in the internet of things. In Proceedings of the 1st ACM Mobile Cloud Computing Workshop, Helsinki, Finland, 17 August 2012; pp. 13–15. [Google Scholar] [CrossRef]
- Satyanarayanan, M.; Chen, Z.; Ha, K.; Hu, W.; Richter, W.; Pillai, P. Cloudlets: At the leading edge of mobile-cloud convergence. In Proceedings of the 6th International Conference on Mobile Computing, Applications and Services, Austin, TX, USA, 6–7 November 2014; pp. 1–9. [Google Scholar] [CrossRef] [Green Version]
- Jacobson, V.; Smetters, D.K.; Briggs, N.H.; Thornton, J.D.; Plass, M.F.; Braynard, R.L. Networking Named Data. In Proceedings of the ACM CoNEXT, Rome, Italy, 1–4 December 2009; pp. 1–12. [Google Scholar]
- Sabir, Z.; Amine, A. NDN vs TCP/IP Which One Is the Best Suitable for Connected Vehicles. In Recent Advances in Mathematics and Technology; Springer: Berlin/Heidelberg, Germany, 2020. [Google Scholar]
- Afanasyev, A.; Burke, J.; Refaei, T.; Wang, L.; Zhang, B.; Zhang, L. A Brief Introduction to Named Data Networking. In Proceedings of the IEEE Military Communications Conference MILCOM, Los Angeles, CA, USA, 29–31 October 2018; pp. 605–611. [Google Scholar] [CrossRef]
- Ghasemi, C.; Yousefi, H.; Zhang, B. Internet-Scale Video Streaming over NDN. IEEE Netw. 2021, 35, 174–180. [Google Scholar] [CrossRef]
- Abane, A.; Daoui, M.; Muhlethaler, P.; Afifi, H. A down-to-earth integration of Named Data Networking in the real-world IoT. In Proceedings of the 2018 6th International Conference on Future Internet of Things and Cloud Workshops (FiCloudW), Barcelona, Spain, 6–8 August 2018. [Google Scholar]
- Abane, A.; Daoui, M.; Bouzefrane, S.; Banerjee, S.; Muhlethaler, P. A realistic deployment of named data networking in the internet of things. J. Cyber Secur. Mobil. 2020, 9, 1–27. [Google Scholar] [CrossRef]
- Arshad, S.; Azam, M.A.; Rehmani, M.H.; Loo, J. Recent advances in information-centric networking-based internet of things (ICN-IoT). IEEE Internet Things J. 2019, 6, 2128–2158. [Google Scholar] [CrossRef] [Green Version]
- Din, I.U.; Asmat, H.; Guizani, M. A review of information centric network-based internet of things: Communication architectures, design issues, and research opportunities. Multimed. Tools Appl. 2018, 30241–30256. [Google Scholar] [CrossRef]
- Mars, D.; Gammar, S.M.; Lahmadi, A.; Azouz, L.; Mars, D.; Gammar, S.M.; Lahmadi, A.; Azouz, L.; Using, S. Using Information Centric Networking in Internet of Things: A Survey. Wirel. Pers. Commun. 2019, 10, 87–103. [Google Scholar] [CrossRef]
- Nour, B.; Sharif, K.; Li, F.; Biswas, S.; Moungla, H.; Guizani, M.; Wang, Y. A survey of Internet of Things communication using ICN: A use case perspective. Comput. Commun. 2019, 142–143, 95–123. [Google Scholar] [CrossRef]
- Hail, M.A. IoT-NDN: An IoT architecture via named data netwoking (NDN). In Proceedings of the 2019 IEEE International Conference on Industry 4.0, Artificial Intelligence, and Communications Technology, IAICT 2019, Bali, Indonesia, 1–3 July 2019; pp. 74–80. [Google Scholar] [CrossRef]
- Khelifi, H.; Luo, S.; Nour, B.; Moungla, H.; Faheem, Y.; Hussain, R.; Ksentini, A. Named Data Networking in Vehicular Ad Hoc Networks: State-of-the-Art and Challenges. IEEE Commun. Surv. Tutor. 2020, 22, 320–351. [Google Scholar] [CrossRef] [Green Version]
- Kerrche, C.A.; Ahmad, F.; Elhoseny, M.; Adnane, A.; Ahmad, Z.; Nour, B. Internet of Vehicles Over Named Data Networking: Current Status and Future Challenges; Springer International Publishing: Berlin/Heidelberg, Germany, 2020; Volume 242, pp. 83–99. [Google Scholar] [CrossRef]
- Yao, H.; Li, M.; Du, J.; Zhang, P.; Jiang, C.; Han, Z. Artificial Intelligence for Information-Centric Networks. IEEE Commun. Mag. 2019, 57, 47–53. [Google Scholar] [CrossRef]
- Hameed Mir, Z.; Filali, F. LTE and IEEE 802.11p for vehicular networking: A performance evaluation. Eurasip J. Wirel. Commun. Netw. 2014, 2014. [Google Scholar] [CrossRef] [Green Version]
- Pokhrel, S.R.; Choi, J. Improving TCP Performance over WiFi for Internet of Vehicles: A Federated Learning Approach. IEEE Trans. Veh. Technol. 2020, 69, 6798–6802. [Google Scholar] [CrossRef]
- Bazzi, A.; Masini, B.M.; Zanella, A.; Thibault, I. On the performance of IEEE 802.11p and LTE-V2V for the cooperative awareness of connected vehicles. IEEE Trans. Veh. Technol. 2017, 66, 10419–10432. [Google Scholar] [CrossRef]
- Naik, G.; Choudhury, B.; Park, J.M. IEEE 802.11bd amp; 5G NR V2X: Evolution of Radio Access Technologies for V2X Communications. IEEE Access 2019, 7, 70169–70184. [Google Scholar] [CrossRef]
- Singh, A.; Singh, B. A Study of the IEEE802.11p (WAVE) and LTE-V2V Technologies for Vehicular Communication. In Proceedings of the International Conference on Computation, Automation and Knowledge Management, ICCAKM 2020, Dubai, United Arab Emirates, 9–10 January 2020; pp. 157–160. [Google Scholar] [CrossRef]
- Amadeo, M.; Campolo, C.; Molinaro, A.; Harri, J.; Rothenberg, C.E.; Vinel, A. Enhancing the 3GPP V2X architecture with information-centric networking. Future Internet 2019, 11, 199. [Google Scholar] [CrossRef] [Green Version]
- Murillo, F.J.; Yoshioka, J.S.Q.; López, A.D.V.; Salazar-Cabrera, R.; de la Cruz, Á.P.; Molina, J.M.M. Experimental evaluation of lora in transit vehicle tracking service based on intelligent transportation systems and IoT. Electronics 2020, 9, 1950. [Google Scholar] [CrossRef]
- Arena, F.; Pau, G.; Severino, A. A review on IEEE 802.11p for intelligent transportation systems. J. Sens. Actuator Netw. 2020, 9, 22. [Google Scholar] [CrossRef]
- Ferrari, P.; Sisinni, E.; Carvalho, D.F.; Depari, A.; Signoretti, G.; Silva, M.; Silva, I.; Silva, D. On the use of LoRaWAN for the Internet of Intelligent Vehicles in Smart City scenarios. In Proceedings of the 2020 IEEE Sensors Applications Symposium, SAS, Kuala Lumpur, Malaysia, 9–11 March 2020; pp. 6–11. [Google Scholar] [CrossRef]
- Haque, K.F.; Abdelgawad, A.; Yanambaka, V.P.; Yelamarthi, K. Lora architecture for v2x communication: An experimental evaluation with vehicles on the move. Sensors 2020, 20, 6876. [Google Scholar] [CrossRef]
- World Health Organization (WHO). Road Traffic Injuries: The Facts; World Health Organization: Geneva, Switzerland, 2018; pp. 1–32. [Google Scholar]
- ETSI TR 103 667 Intelligent Transport Systems (ITS); Study on Spectrum Sharing between ITS-G5 and LTE-V2X Technologies in the 5 855 MHz–5 925 MHz Band. Technical Report. 2021. Available online: https://www.etsi.org/deliver/etsi_tr/103600_103699/103667/01.01.01_60/tr_103667v010101p.pdf (accessed on 19 March 2022).
- Use of the 5.850-5.925 GHz Band. Technical Report. 2021. Available online: https://www.federalregister.gov/documents/2021/05/03/2021-08802/use-of-the-5850-5925-ghz-band (accessed on 19 March 2022).
- Official Journal of the European Union, L232. Technical Report. 2021. Available online: https://eur-lex.europa.eu/legal-content/EN/TXT/PDF/?uri=OJ:L:2021:232:FULL&from=EN (accessed on 20 March 2022).
- FCC Adopts New Rules For The 6 GHz Band, Unleashing 1,200 Megahertz Of Spectrum For Unlicensed Use. Technical Report. 2020. Available online: https://www.fcc.gov/document/fcc-opens-6-ghz-band-wi-fi-and-other-unlicensed-uses (accessed on 20 March 2022).
- Wan, J.; Zhang, D.; Zhao, S.; Yang, L.T.; Lloret, J. Context-aware vehicular cyber-physical systems with cloud support: Architecture, challenges, and solutions. IEEE Commun. Mag. 2014, 52, 106–113. [Google Scholar] [CrossRef]
- Raza, S.; Wang, S.; Ahmed, M.; Anwar, M.R. A survey on vehicular edge computing: Architecture, applications, technical issues, and future directions. Wirel. Commun. Mob. Comput. 2019, 2019, 3159762. [Google Scholar] [CrossRef]
- Contreras-Castillo, J.; Zeadally, S.; Ibáñez, J.A.G. A seven-layered model architecture for internet of vehicles. J. Inf. Telecommun. 2017, 1, 4–22. [Google Scholar] [CrossRef] [Green Version]
- Darwish, T.S.; Abu Bakar, K. Fog Based Intelligent Transportation Big Data Analytics in The Internet of Vehicles Environment: Motivations, Architecture, Challenges, and Critical Issues. IEEE Access 2018, 6, 15679–15701. [Google Scholar] [CrossRef]
- Bonomi, F. The Smart and Connected Vehicle and the Internet of Things; WSTS: San Jose, CA, USA, 2013. [Google Scholar]
- Zhuang, W.; Ye, Q.; Lyu, F.; Cheng, N.; Ren, J. SDN/NFV-Empowered Future IoV With Enhanced Communication, Computing, and Caching. Proc. IEEE 2020, 108, 274–291. [Google Scholar] [CrossRef]
- Chen, M.; Tian, Y.; Fortino, G.; Zhang, J.; Humar, I. Cognitive Internet of Vehicles. Comput. Commun. 2018, 120, 58–70. [Google Scholar] [CrossRef]
- Tuyisenge, L.; Ayaida, M.; Tohme, S.; Afilal, L.E. Network Architectures in Internet of Vehicles (IoV): Review, Protocols Analysis, Challenges and Issues. In Proceedings of the 5th International Conference, IOV 2018, Paris, France, 20–22 November 2018; pp. 3–13. [Google Scholar] [CrossRef]
- Yu, K.; Eum, S.; Kurita, T.; Hua, Q.; Sato, T.; Nakazato, H.; Asami, T.; Kafle, V.P. Information-Centric Networking: Research and Standardization Status. IEEE Access 2019, 7, 126164–126176. [Google Scholar] [CrossRef]
- Koponen, T.; Chawla, M.; Chun, B.G.; Ermolinskiy, A.; Kim, K.H.; Shenker, S.; Stoica, I. A data-oriented (and Beyond) network architecture. Comput. Commun. Rev. 2007, 37, 181–192. [Google Scholar] [CrossRef]
- Zhang, L.; Afanasyev, A.; Burke, J.; Jacobson, V.; Claffy, K.; Crowley, P.; Papadopoulos, C.; Wang, L.; Zhang, B. Named Data Networking. SIGCOMM Comput. Commun. Rev. 2014, 44, 66–73. [Google Scholar] [CrossRef]
- Yi, C.; Afanasyev, A.; Moiseenko, I.; Wang, L.; Zhang, B.; Zhang, L. A case for stateful forwarding plane. Comput. Commun. 2013, 36, 779–791. [Google Scholar] [CrossRef] [Green Version]
- Singh, V.P.; Ujjwal, R.L. A walkthrough of name data networking: Architecture, functionalities, operations and open issues. Sustain. Comput. Inform. Syst. 2020, 28, 100419. [Google Scholar] [CrossRef]
- Bari, M.F.; Chowdhury, S.R.; Ahmed, R.; Boutaba, R.; Mathieu, B. A survey of naming and routing in information-centric networks. IEEE Commun. Mag. 2012, 50, 44–53. [Google Scholar] [CrossRef]
- Seskar, I.; Nagaraja, K.; Sam, N.; Raychaudhuri, D. MobilityFirst Future Internet Architecture project. In Proceedings of the Asian Internet Engineeering Conference, AINTEC 2011, Bangkok Thailand, 9–11 November 2011; pp. 1–3. [Google Scholar] [CrossRef] [Green Version]
- Hong, J. Design Guidelines for Name Resolution Service in ICN. Available online: https://tools.ietf.org/id/draft-irtf-icnrg-nrs-requirements-03.html (accessed on 19 March 2022).
- Yu, M.; Li, R.; Liu, Y.; Li, Y. A caching strategy based on content popularity and router level for NDN. In Proceedings of the 2017 IEEE 7th International Conference on Electronics Information and Emergency Communication, ICEIEC 2017, Macau, China, 21–23 July 2017; pp. 195–198. [Google Scholar] [CrossRef]
- Tyson, G.; Sastry, N.; Rimac, I.; Cuevas, R.; Mauthe, A. A survey of mobility in information-centric networks: Challenges and research directions. In Proceedings of the International Symposium on Mobile Ad Hoc Networking and Computing (MobiHoc), Hilton Head, SC, USA, 11 June 2012; pp. 1–6. [Google Scholar] [CrossRef]
- Zafar, W.U.I.; Rehman, M.A.U.; Jabeen, F.; Kim, B.S.; Rehman, Z. Context-aware naming and forwarding in ndn-based vanets. Sensors 2021, 21, 4629. [Google Scholar] [CrossRef] [PubMed]
- Wang, M.; Wu, J.; Li, G.; Li, J.; Li, Q.; Wang, S. Toward mobility support for information-centric IoV in smart city using fog computing. In Proceedings of the 2017 5th IEEE International Conference on Smart Energy Grid Engineering, SEGE 2017, Oshawa, ON, Canada, 14–17 August 2017; pp. 357–361. [Google Scholar] [CrossRef]
- Yu, Y.; Li, Y.; Du, X.; Chen, R.; Yang, B. Content Protection in Named Data Networking: Challenges and Potential Solutions. IEEE Commun. Mag. 2018, 56, 82–87. [Google Scholar] [CrossRef]
- What Edge Computing Means for Infrastructure and Operations Leaders. Available online: https://www.gartner.com/smarterwithgartner/what-edge-computing-means-for-infrastructure-and-operations-leaders (accessed on 28 March 2022).
- Patel, M.; Naughton, B.; Chan, C.; Sprecher, N.; Abeta, S.; Neal, A. Mobile-edge computing introductory technical white paper. White Pap.-Mob.-Edge Comput. (Mec) Ind. Initiat. 2014, 29, 854–864. [Google Scholar]
- Muniswamaiah, M.; Agerwala, T.; Tappert, C.C. A Survey on Cloudlets, Mobile Edge, and Fog Computing. In Proceedings of the 2021 8th IEEE International Conference on Cyber Security and Cloud Computing (CSCloud)/2021 7th IEEE International Conference on Edge Computing and Scalable Cloud (EdgeCom), Washington, DC, USA, 26–28 June 2021; pp. 139–142. [Google Scholar] [CrossRef]
- Azure IoT Edge. Available online: https://azure.microsoft.com/it-it/services/iot-edge/ (accessed on 28 March 2022).
- Edge Computing Solutions. Available online: https://www.cisco.com/c/en/us/solutions/service-provider/edge-computing.html. (accessed on 28 March 2022).
- IBM Solutions for 5G and Edge Computing. Available online: https://www.ibm.com/cloud/edge-computing. (accessed on 28 March 2022).
- Aazam, M.; Zeadally, S.; Harras, K.A. Fog Computing Architecture, Evaluation, and Future Research Directions. IEEE Commun. Mag. 2018, 56, 46–52. [Google Scholar] [CrossRef]
- Mukherjee, M.; Shu, L.; Wang, D. Survey of fog computing: Fundamental, network applications, and research challenges. IEEE Commun. Surv. Tutor. 2018, 20, 1826–1857. [Google Scholar] [CrossRef]
- Goodfellow, I.J.; Pouget-Abadie, J.; Mirza, M.; Xu, B.; Warde-Farley, D.; Ozair, S.; Courville, A.; Bengio, Y. Generative Adversarial Networks. arXiv 2014, arXiv:1406.2661. [Google Scholar] [CrossRef]
- Girshick, R.; Donahue, J.; Darrell, T.; Malik, J. Rich Feature Hierarchies for Accurate Object Detection and Semantic Segmentation. In Proceedings of the 2014 IEEE Conference on Computer Vision and Pattern Recognition, Columbus, OH, USA, 23–28 June 2014; pp. 580–587. [Google Scholar] [CrossRef] [Green Version]
- Redmon, J.; Divvala, S.; Girshick, R.; Farhadi, A. You Only Look Once: Unified, Real-Time Object Detection. In Proceedings of the 2016 IEEE Conference on Computer Vision and Pattern Recognition (CVPR), Las Vegas, NV, USA, 27–30 June 2016; pp. 779–788. [Google Scholar] [CrossRef] [Green Version]
- Kim, B.; Kang, C.M.; Lee, S.H.; Chae, H.; Kim, J.; Chung, C.C.; Choi, J.W. Probabilistic Vehicle Trajectory Prediction over Occupancy Grid Map via Recurrent Neural Network. In Proceedings of the 2017 IEEE 20th International Conference on Intelligent Transportation Systems (ITSC), Yokohama, Japan, 16–19 October 2017. [Google Scholar]
- Du, Z.; Wu, C.; Yoshinaga, T.; Yau, K.; Ji, Y.; Li, J. Federated Learning for Vehicular Internet of Things: Recent Advances and Open Issues. IEEE Open J. Comput. Soc. 2020, 1, 45–61. [Google Scholar] [CrossRef]
- Li, E.; Zhou, Z.; Chen, X. Edge Intelligence: On-Demand Deep Learning Model Co-Inference with Device-Edge Synergy. In Proceedings of the 2018 Workshop on Mobile Edge Communications, Budapest, Hungary, 20 August 2018; Association for Computing Machinery: New York, NY, USA, 2018; pp. 31–36. [Google Scholar] [CrossRef]
- Andrade, P.; Silva, I.; Signoretti, G.; Silva, M.; Dias, J.; Marques, L.; Costa, D.G. An Unsupervised TinyML Approach Applied for Pavement Anomalies Detection Under the Internet of Intelligent Vehicles. In Proceedings of the 2021 IEEE International Workshop on Metrology for Industry 4.0 IoT (MetroInd4.0 IoT), Rome, Italy, 7–9 June 2021; pp. 642–647. [Google Scholar] [CrossRef]
- de Prado, M.; Rusci, M.; Capotondi, A.; Donze, R.; Benini, L.; Pazos, N. Robustifying the Deployment of tinyML Models for Autonomous Mini-Vehicles. Sensors 2021, 21, 1339. [Google Scholar] [CrossRef]
- Huang, Y.; Ma, X.; Fan, X.; Liu, J.; Gong, W. When deep learning meets edge computing. In Proceedings of the 2017 IEEE 25th International Conference on Network Protocols (ICNP), Toronto, ON, Canada, 10–13 October 2017; pp. 1–2. [Google Scholar] [CrossRef]
- Zhao, C.; Dong, M.; Ota, K.; Li, J.; Wu, J. Edge-MapReduce-Based Intelligent Information-Centric IoV: Cognitive Route Planning. IEEE Access 2019, 7, 50549–50560. [Google Scholar] [CrossRef]
- Seid, S.; Zennaro, M.; Libsie, M.; Pietrosemoli, E.; Manzoni, P. A Low Cost Edge Computing and LoRaWAN Real Time Video Analytics for Road Traffic Monitoring. In Proceedings of the 2020 16th International Conference on Mobility, Sensing and Networking (MSN), Tokyo, Japan, 17–19 December 2020; pp. 762–767. [Google Scholar] [CrossRef]
- Ning, Z.; Dong, P.; Wang, X.; Guo, L.; Rodrigues, J.J.P.C.; Kong, X.; Huang, J.; Kwok, R.Y.K. Deep Reinforcement Learning for Intelligent Internet of Vehicles: An Energy-Efficient Computational Offloading Scheme. IEEE Trans. Cogn. Commun. Netw. 2019, 5, 1060–1072. [Google Scholar] [CrossRef]
- Seid, S.; Zennaro, M.; Libse, M.; Pietrosemoli, E. Mobile Crowdsensing Based Road Surface Monitoring Using Smartphone Vibration Sensor and Lorawan. In Proceedings of the 1st Workshop on Experiences with the Design and Implementation of Frugal Smart Objects, London, UK, 21 September 2020; Association for Computing Machinery: New York, NY, USA, 2020; pp. 36–41. [Google Scholar] [CrossRef]
- Ray, P.P. A review on TinyML: State-of-the-art and prospects. J. King Saud Univ.-Comput. Inf. Sci. 2021, 34, 1595–1623. [Google Scholar] [CrossRef]
- Zhang, J.; Letaief, K.B. Mobile Edge Intelligence and Computing for the Internet of Vehicles. Proc. IEEE 2020, 108, 246–261. [Google Scholar] [CrossRef] [Green Version]
- Amadeo, M. A Literature Review on Caching Transient Contents in Vehicular Named Data Networking. Telecom 2021, 2, 75–92. [Google Scholar] [CrossRef]
- Kim, D.Y.; Lee, J. An NDN cache management for MEC. Appl. Sci. 2020, 10, 896. [Google Scholar] [CrossRef] [Green Version]
- Qiao, G.; Leng, S.; Maharjan, S.; Zhang, Y.; Ansari, N. Deep Reinforcement Learning for Cooperative Content Caching in Vehicular Edge Computing and Networks. IEEE Internet Things J. 2020, 7, 247–257. [Google Scholar] [CrossRef]
- Tang, C.; Wu, H. Joint optimization of task caching and computation offloading in vehicular edge computing. Peer-to-Peer Netw. Appl. 2021, 15, 854–869. [Google Scholar] [CrossRef]
- Kulkarni, A.; Seetharam, A. Model and Machine Learning based Caching and Routing Algorithms for Cache-enabled Networks. arXiv 2020, arXiv:2004.06787. [Google Scholar] [CrossRef]
- Ndikumana, A.; Ullah, S.; Kim, D.H.; Hong, C.S. Deepauc: Joint deep learning and auction for congestion-aware caching in Named Data Networking. PLoS ONE 2019, 14, e0220813. [Google Scholar] [CrossRef] [Green Version]
- Wu, H.T.; Cho, H.H.; Wang, S.J.; Tseng, F.H. Intelligent data cache based on content popularity and user location for Content Centric Networks. Hum.-Centric Comput. Inf. Sci. 2019, 9, 44. [Google Scholar] [CrossRef] [Green Version]
- Guo, B.; Zhang, X.; Sheng, Q.; Yang, H. Dueling deep-q-network based delay-aware cache update policy for mobile users in fog radio access networks. IEEE Access 2020, 8, 7131–7141. [Google Scholar] [CrossRef]
- Serhane, O.; Yahyaoui, K.; Nour, B.; Moungla, H. A Survey of ICN Content Naming and In-Network Caching in 5G and beyond Networks. IEEE Internet Things J. 2021, 8, 4081–4104. [Google Scholar] [CrossRef]
- Bouk, S.H.; Ahmed, S.H.; Kim, D. Hierarchical and hash based naming with Compact Trie name management scheme for Vehicular Content Centric Networks. Comput. Commun. 2015, 71, 73–83. [Google Scholar] [CrossRef]
- Rehman, M.A.U.; Ullah, R.; Kim, B.S. NINQ: Name-integrated query framework for named-data networking of things. Sensors 2019, 19, 2906. [Google Scholar] [CrossRef] [Green Version]
- Jahanian, M.; Ramakrishnan, K.K. Name space analysis: Verification of named data network data planes. In Proceedings of the ICN ’19:2019 Conference on Information-Centric Networking, Macao, China, 24–26 September 2019; pp. 44–54. [Google Scholar] [CrossRef] [Green Version]
- Karrakchou, O.; Samaan, N.; Karmouch, A. FCTree: A Space Efficient FIB Data Structure for NDN Routers. In Proceedings of the 2018 IEEE 43rd Conference on Local Computer Networks (LCN), Chicago, IL, USA, 1–4 October 2018; pp. 589–596. [Google Scholar] [CrossRef]
- Li, Z.; Liu, J.; Yan, L.; Zhang, B.; Luo, P.; Liu, K. Smart Name Lookup for NDN Forwarding Plane via Neural Networks. In IEEE/ACM Transactions on Networking; IEEE: Piscataway, NJ, USA, 2021. [Google Scholar] [CrossRef]
- Mochida, T.; Nozaki, D.; Okamoto, K.; Qi, X.; Wen, Z.; Sato, T.; Yu, K. Naming scheme using NLP machine learning method for network weather monitoring system based on ICN. In Proceedings of the 2017 20th International Symposium on Wireless Personal Multimedia Communications (WPMC), Bali, Indonesia, 17–20 December 2017; pp. 428–434. [Google Scholar] [CrossRef]
- Hoque, A.K.M.M.; Amin, S.O.; Alyyan, A.; Zhang, B.; Zhang, L.; Wang, L. NLSR: Named-data Link State. In Proceedings of the 3rd ACM SIGCOMM workshop on Information-centric networking-ICN ’13, New York, NY, USA, 12 August 2013; p. 15. [Google Scholar]
- Friyanto, A.; Ariefianto, W.T.; Syambas, N.R. Analysis Operation NLSR with Ubuntu as NDN Router. In Proceedings of the 2019 5th International Conference on Wireless and Telematics, ICWT 2019, Yogyakarta, Indonesia, 25–26 July 2019; pp. 20–23. [Google Scholar] [CrossRef]
- Ghasemi, C.; Yousefi, H.; Shin, K.G.; Zhang, B. MUCA: New Routing for Named Data Networking. In Proceedings of the 2018 IFIP Networking Conference IFIP Networking and Workshops, IFIP Networking 2018-Proceedings, Zurich, Switzerland, 14–16 May 2018; pp. 289–297. [Google Scholar] [CrossRef]
- Wang, L.; Lehman, V.; Mahmudul Hoque, A.K.; Zhang, B.; Yu, Y.; Zhang, L. A Secure Link State Routing Protocol for NDN. IEEE Access 2018, 6, 10470–10482. [Google Scholar] [CrossRef]
- Pu, C. Pro NDN: MCDM-Based Interest Forwarding and Cooperative Data. J. Comput. Netw. Commun. 2021, 2021, 1–16. [Google Scholar] [CrossRef]
- Dutta, N.; Tanwar, S.; Patel, S.K.; Ghinea, G. SVM-based Analysis for Predicting Success Rate of Interest Packets in Information Centric Networks. Appl. Artif. Intell. 2021, 1–22. [Google Scholar] [CrossRef]
- Zhang, Y.; Xu, K.; Bai, B.; Lei, K. IFS-RL: An intelligent forwarding strategy based on reinforcement learning in named-data networking. In Proceedings of the 2018 Workshop on Network Meets AI and ML, Part of SIGCOMM 2018, Budapest, Hungary, 24 August 2018; pp. 54–59. [Google Scholar] [CrossRef]
- Fu, B.; Qian, L.; Zhu, Y.; Wang, L. Reinforcement learning-based algorithm for efficient and adaptive forwarding in named data networking. In Proceedings of the 2017 IEEE/CIC International Conference on Communications in China, ICCC 2017, Qingdao, China, 22–24 October 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Akinwande, O. Interest forwarding in named data networking using reinforcement learning. Sensors 2018, 18, 3354. [Google Scholar] [CrossRef] [Green Version]
- Duarte, J.M.; Braun, T.; Villas, L.A. Receiver mobility in vehicular named data networking. In Proceedings of the 2017 Workshop on Mobility in the Evolving Internet Architecture, Part of SIGCOMM 2017, Los Angeles, CA, USA, 25 August 2017; pp. 43–48. [Google Scholar] [CrossRef] [Green Version]
- Mun, J.H.; Lim, H. On Sharing an FIB Table in Named Data Networking. Appl. Sci. 2019, 9, 3178. [Google Scholar] [CrossRef] [Green Version]
- Mastorakis, S.; Chan, K.; Ko, B.; Afanasyev, A.; Zhang, L. Experimentation With Fuzzy Interest Forwarding in Named Data Networking. arXiv 2018, arXiv:2010.07832. [Google Scholar]
- Sofia, R.C. Guidelines towards information-driven mobility management. Future Internet 2019, 11, 111. [Google Scholar] [CrossRef] [Green Version]
- Chen, M.; Ong Mau, D.; Zhang, Y.; Taleb, T.; Leung, V.C. VENDNET: VEhicular Named Data NETwork. Veh. Commun. 2014, 1, 208–213. [Google Scholar] [CrossRef]
- Yang, N.; Chen, K.; Liu, Y. Towards Efficient NDN Framework for Connected Vehicle Applications. IEEE Access 2020, 8, 60850–60866. [Google Scholar] [CrossRef]
- Benedetti, P.; Piro, G.; Grieco, L.A. A softwarized and MEC-enabled protocol architecture supporting consumer mobility in Information-Centric Networks. Comput. Netw. 2021, 188, 107867. [Google Scholar] [CrossRef]
- Hussaini, M.; Naeem, M.A.; Kim, B.S. Opmss: Optimal producer mobility support solution for named data networking. Appl. Sci. 2021, 11, 4064. [Google Scholar] [CrossRef]
- Choi, J.H.; Cha, J.H.; Han, Y.H.; Min, S.G. A dual-connectivity mobility link service for producer mobility in the named data networking. Sensors 2020, 20, 4859. [Google Scholar] [CrossRef]
- Meddeb, M.; Dhraief, A.; Belghith, A.; Monteil, T.; Drira, K. Producer Mobility support in Named Data Internet of Things Network. Procedia Comput. Sci. 2017, 109, 1067–1073. [Google Scholar] [CrossRef]
- Augé, J.; Carofiglio, G.; Grassi, G.; Muscariello, L.; Pau, G.; Zeng, X. MAP-Me: Managing Anchor-Less Producer Mobility in Content-Centric Networks. IEEE Trans. Netw. Serv. Manag. 2018, 15, 596–610. [Google Scholar] [CrossRef] [Green Version]
- Li, Y.; Piao, X.; Zhang, H.; Lei, K. NDN Producer Mobility Management Based on Echo State Network: A Lightweight Machine Learning Approach. In Proceedings of the International Conference on Parallel and Distributed Systems-ICPADS, Singapore, 11–13 December 2018; pp. 275–282. [Google Scholar] [CrossRef]
- Rao, Y.; Gao, D.; Zhang, H.; Foh, C.H. Mobility support for the user in NDN-based cloud storage service. In Proceedings of the 2015 IEEE Globecom Workshops, GC Wkshps, San Diego, CA, USA, 6–10 December 2015; pp. 1–6. [Google Scholar] [CrossRef]
- Azgin, A.; Ravindran, R.; Chakraborti, A.; Wang, G.Q. Seamless producer mobility as a service in information centric networks. In Proceedings of the 2016 3rd ACM Conference on Information-Centric Networking, Kyoto, Japan, 26–28 September 2016; pp. 243–248. [Google Scholar] [CrossRef]
- Ali, I.; Lim, H. Anchor-Less Producer Mobility Management in Named Data Networking for Real-Time Multimedia. Mob. Inf. Syst. 2019, 2019, 3531567. [Google Scholar] [CrossRef]
- Liu, D.; Huang, C.; Chen, X.; Jia, X. Supporting producer mobility via named data networking in space-terrestrial integrated networks. In Proceedings of the 12th International Conference, WASA 2017, Guilin, China, 19–21 June 2017; pp. 829–841. [Google Scholar] [CrossRef]
- Lei, K.; Fang, J.; Zhang, Q.; Lou, J.; Du, M.; Huang, J.; Wang, J.; Xu, K. Blockchain-Based Cache Poisoning Security Protection and Privacy-Aware Access Control in NDN Vehicular Edge Computing Networks. J. Grid Comput. 2020, 18, 593–613. [Google Scholar] [CrossRef]
- Amadeo, M.; Campolo, C.; Molinaro, A.; Rottondi, C.; Verticale, G. Securing the mobile edge through named data networking. In Proceedings of the IEEE World Forum on Internet of Things, WF-IoT 2018, Singapore, 5–8 February 2018; pp. 80–85. [Google Scholar] [CrossRef] [Green Version]
- Chen, N.; Zhu, H.; Yin, J.; Fei, Y.; Xiao, L.; Zhu, M. Modeling and verifying NDN-based IoV using CSP. J. Softw. Evol. Process 2021, e2371. [Google Scholar] [CrossRef]
- Ullah, S.; Khan, M.A.; Ahmad, J.; Jamal, S.S.; e Huma, Z.; Hassan, M.T.; Pitropakis, N.; Arshad; Buchanan, W.J. HDL-IDS: A Hybrid Deep Learning Architecture for Intrusion Detection in the Internet of Vehicles. Sensors 2022, 22, 1340. [Google Scholar] [CrossRef] [PubMed]
- Hao, B.; Wang, G.; Zhang, M.; Zhu, J.; Xing, L.; Wu, Q. Stochastic Adaptive Forwarding Strategy Based on Deep Reinforcement Learning for Secure Mobile Video Communications in NDN. Secur. Commun. Netw. 2021, 2021, 6630717. [Google Scholar] [CrossRef]
- Sena, Y.A.B.D.; Dias, K.L.; Zanchettin, C. DQN-AF: Deep Q-Network based Adaptive Forwarding Strategy for Named Data Networking. In Proceedings of the 2020 IEEE Latin-American Conference on Communications, LATINCOM 2020, Santo Domingo, Dominican Republic, 18–20 November 2020. [Google Scholar] [CrossRef]
- Ansari, M.R.; Monteuuis, J.P.; Petit, J.; Chen, C. V2X Misbehavior and Collective Perception Service: Considerations for Standardization. In Proceedings of the 2021 IEEE Conference on Standards for Communications and Networking (CSCN), Thessaloniki, Greece, 15–17 December 2021; pp. 1–6. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).