Security in Wireless Sensor Networks: A Cryptography Performance Analysis at MAC Layer
Abstract
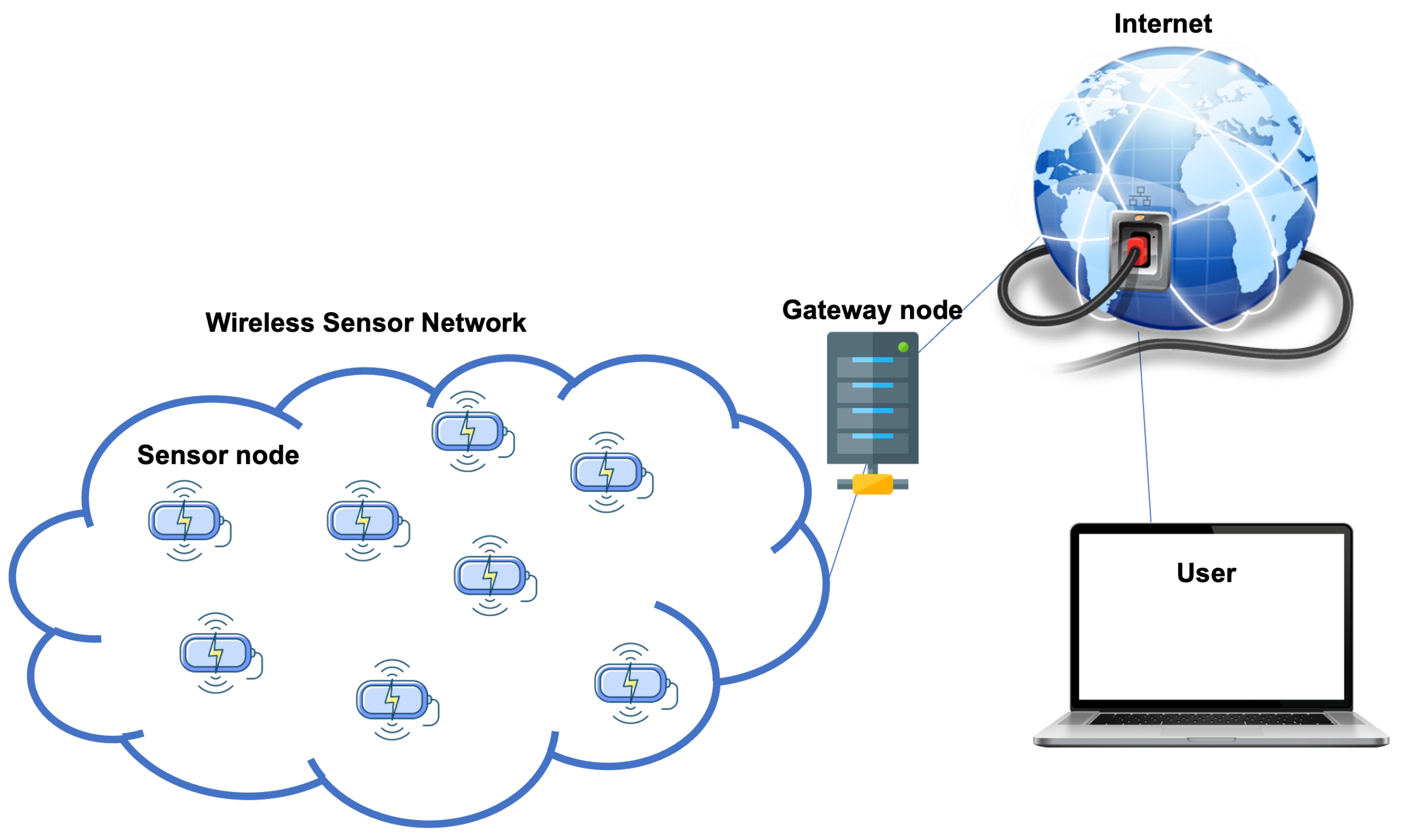
1. Introduction
- Sensing: the measurement of physical quantities (temperature, humidity, etc.);
- Processing: the processing of the acquired measurements;
- Communication: the communication with other nodes, typically through radio frequency (RF) interfaces.
2. Related Work
2.1. MAC Energy Issues on WSNs
2.2. MAC Security Issues on WSNs
2.3. Main Contributions of the Paper
3. Analyzed Cryptographic Methods and Primitives
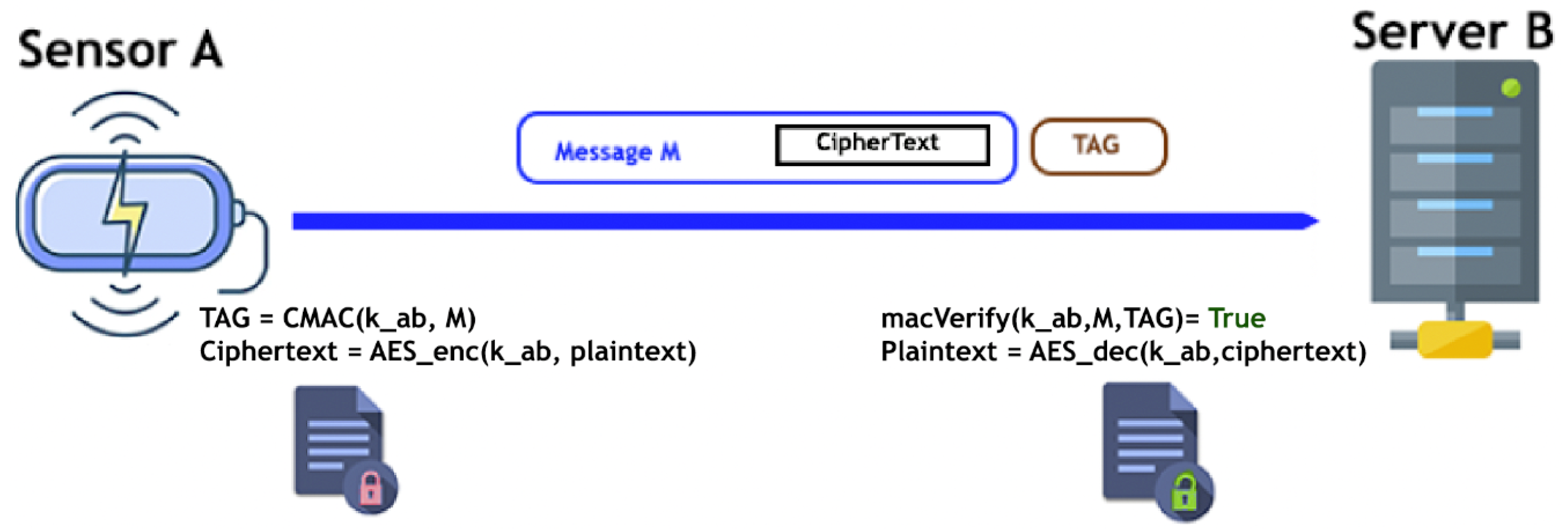
3.1. Advanced Encryption Standard (AES)
3.1.1. Confidentiality in AES
3.1.2. Integrity and Authentication in AES
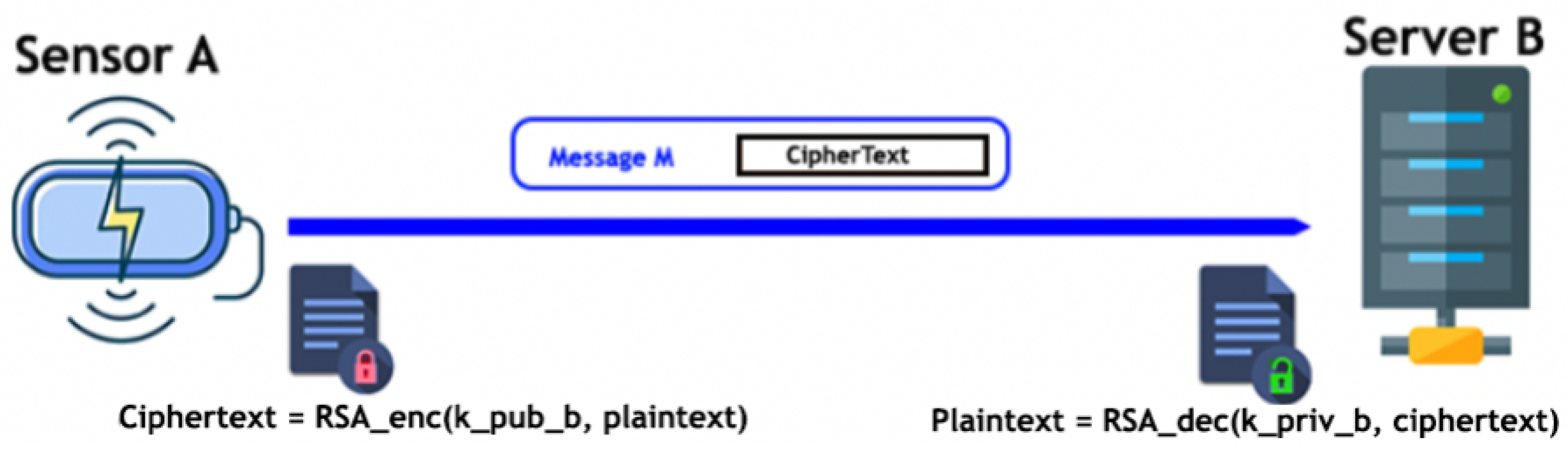
3.2. Rivest Shamir Adelman (RSA)
3.2.1. Confidentiality in RSA
3.2.2. Integrity and Authentication in RSA
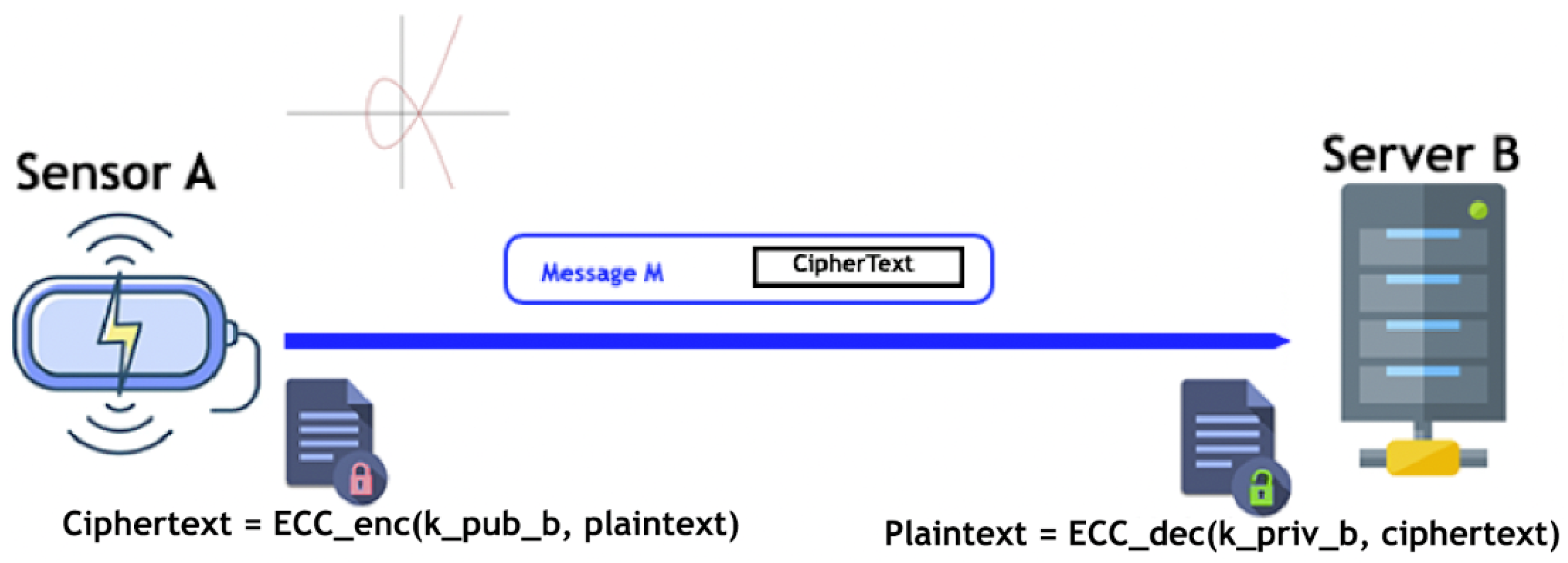
3.3. Elliptic Curve Criptography (ECC)
3.3.1. Confidentiality in ECC
3.3.2. Integrity and Authentication in ECC and ECDSA
4. Implemented Attacks and Relative Mitigations
- energy drain attack;
- impersonation attack.
4.1. Energy Drain Attack
4.1.1. Energy Drain Attack Targeting a Specific Sensor
4.1.2. Energy Drain Attack: Mitigation
4.2. Impersonation Attack
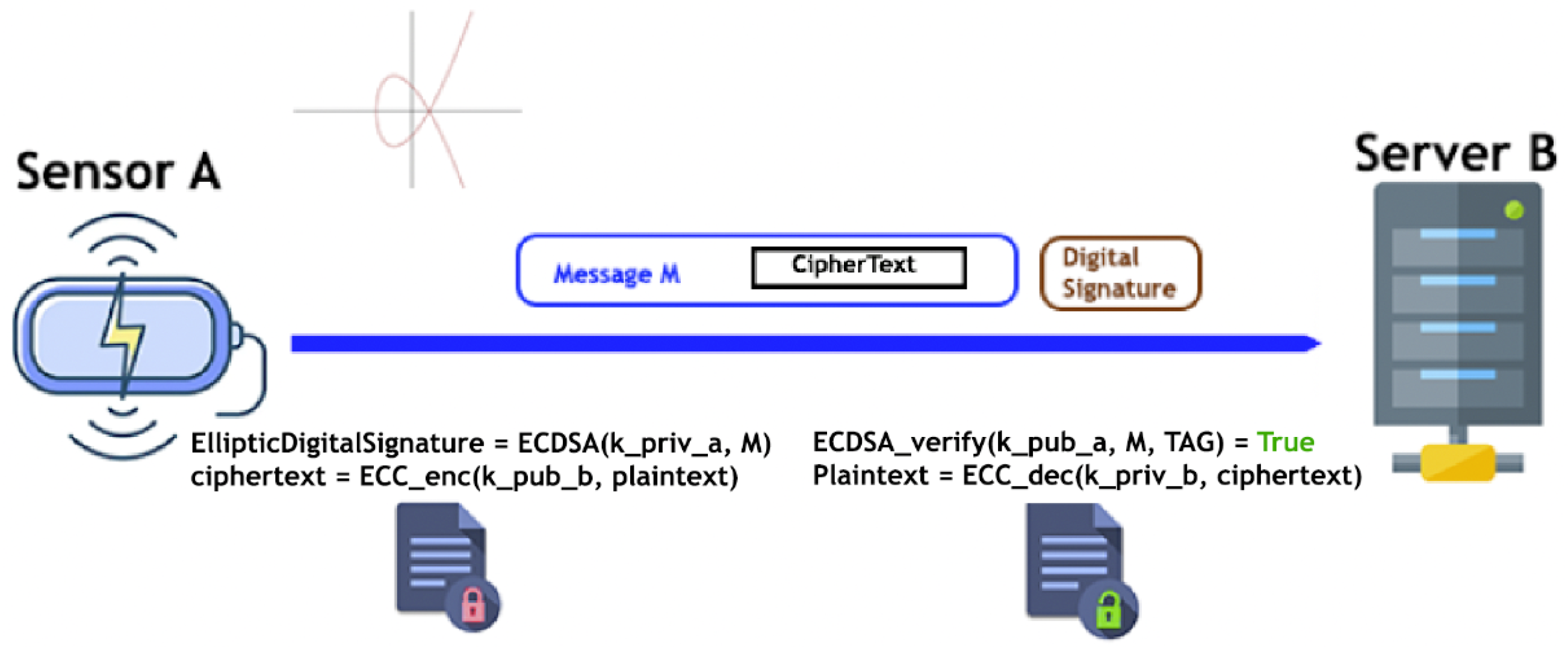
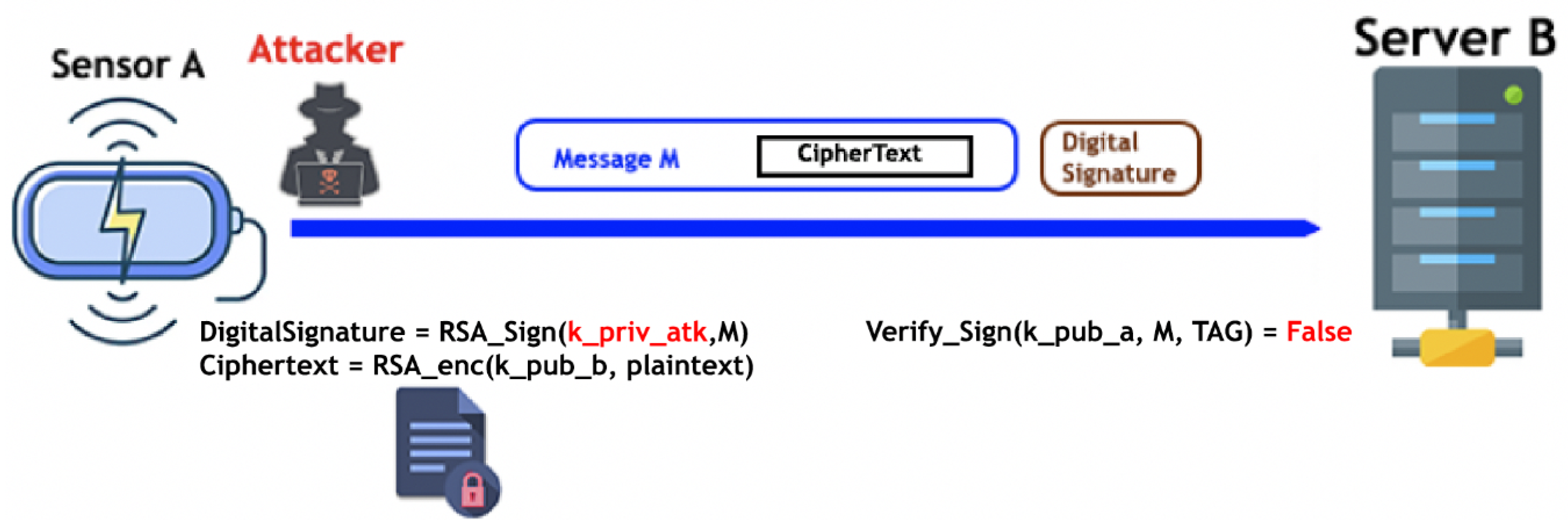
4.2.1. Impersonation Attack: Impersonating a Sensor Node against the Legacy Server
4.2.2. Impersonation Attack: Proposed Mitigation
- 1.
- Symmetric cryptography;
- 2.
- Public key cryptography.
4.2.3. Use of Symmetric Cryptography
4.2.4. Use of Asymmetric Cryptography
5. Performance Evaluation
5.1. Experimental Setup
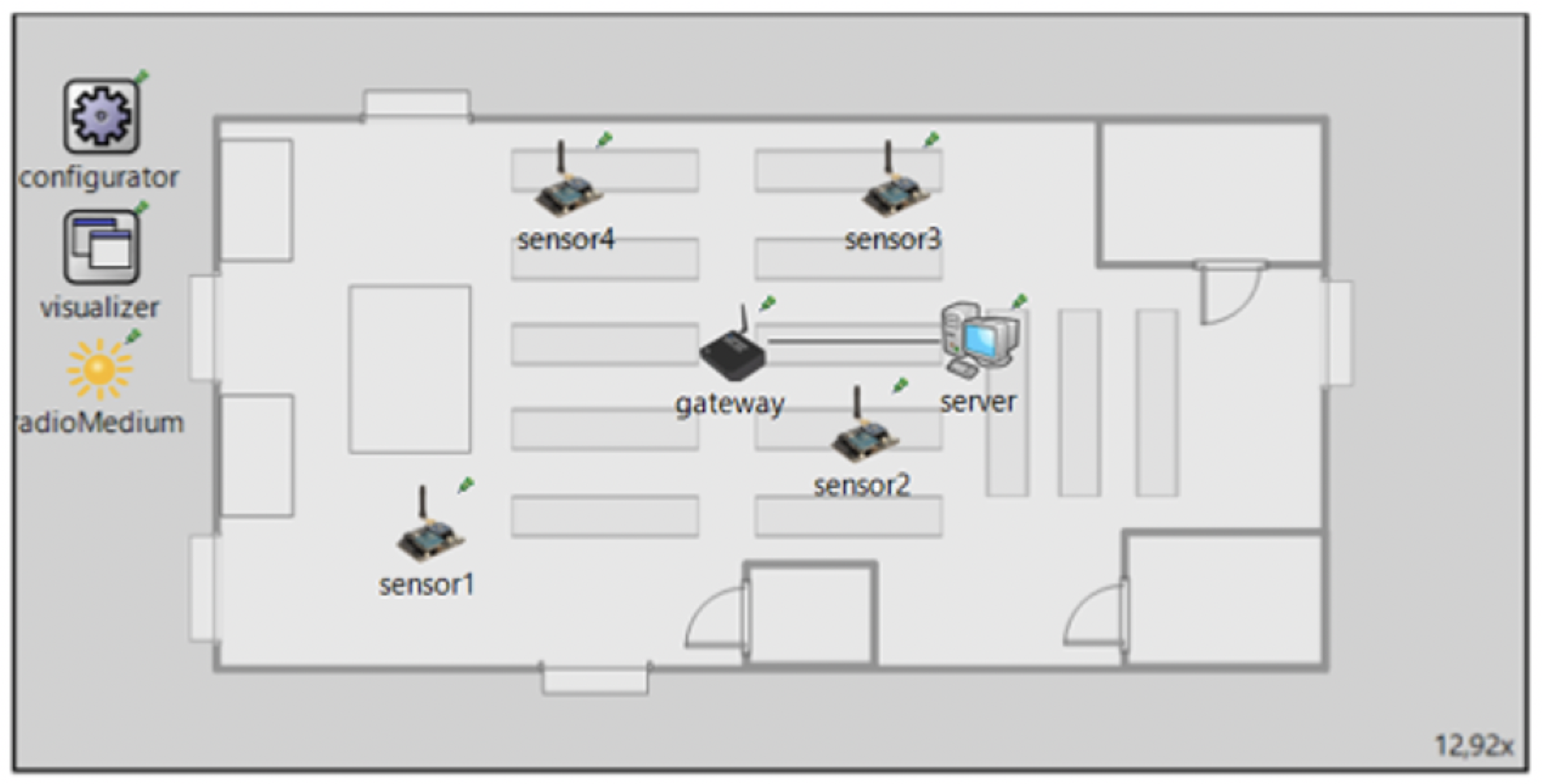
5.2. Network Configuration: Sensors, Gateway and Server
- A network composed of 4 sensors, a gateway and a server: in this setting, each sensor will send 100 packets during a simulation time of 100 s. So, considering four sensors, 400 packets will be sent.
- A network composed of 8 sensors, a gateway and a server: also in this case, in 100 s of simulation time, each sensor sent 100 packets so 800 packets will be sent.
5.3. Network Configuration: BMAC and LMAC Setting
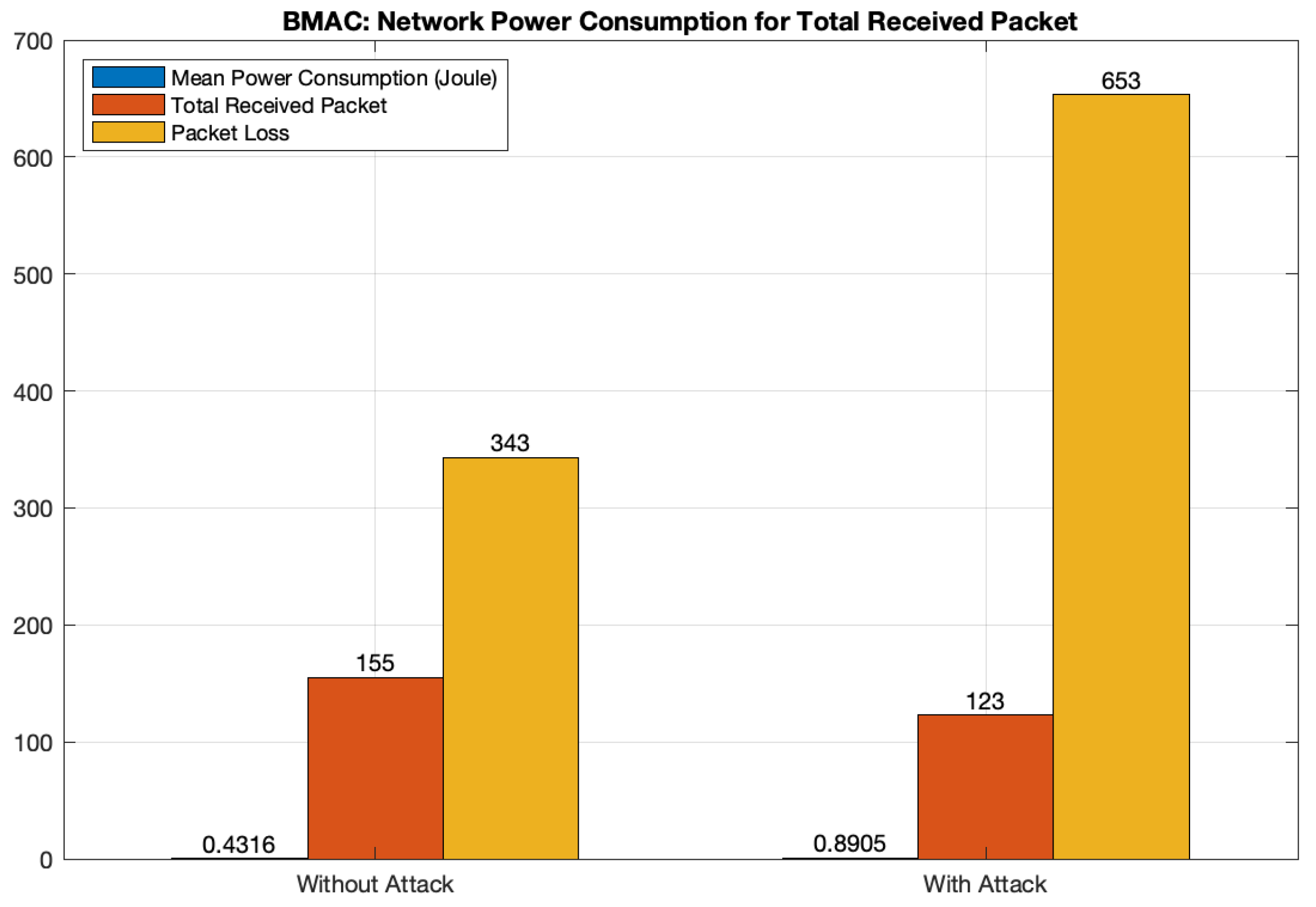
5.4. Performance Evaluation: Energy Drain Attack
- Total energy consumption over the total number of received packets;
- Total number of received packets;
- Number of packets lost.
5.5. Performance Evaluation: Impersonation Attack
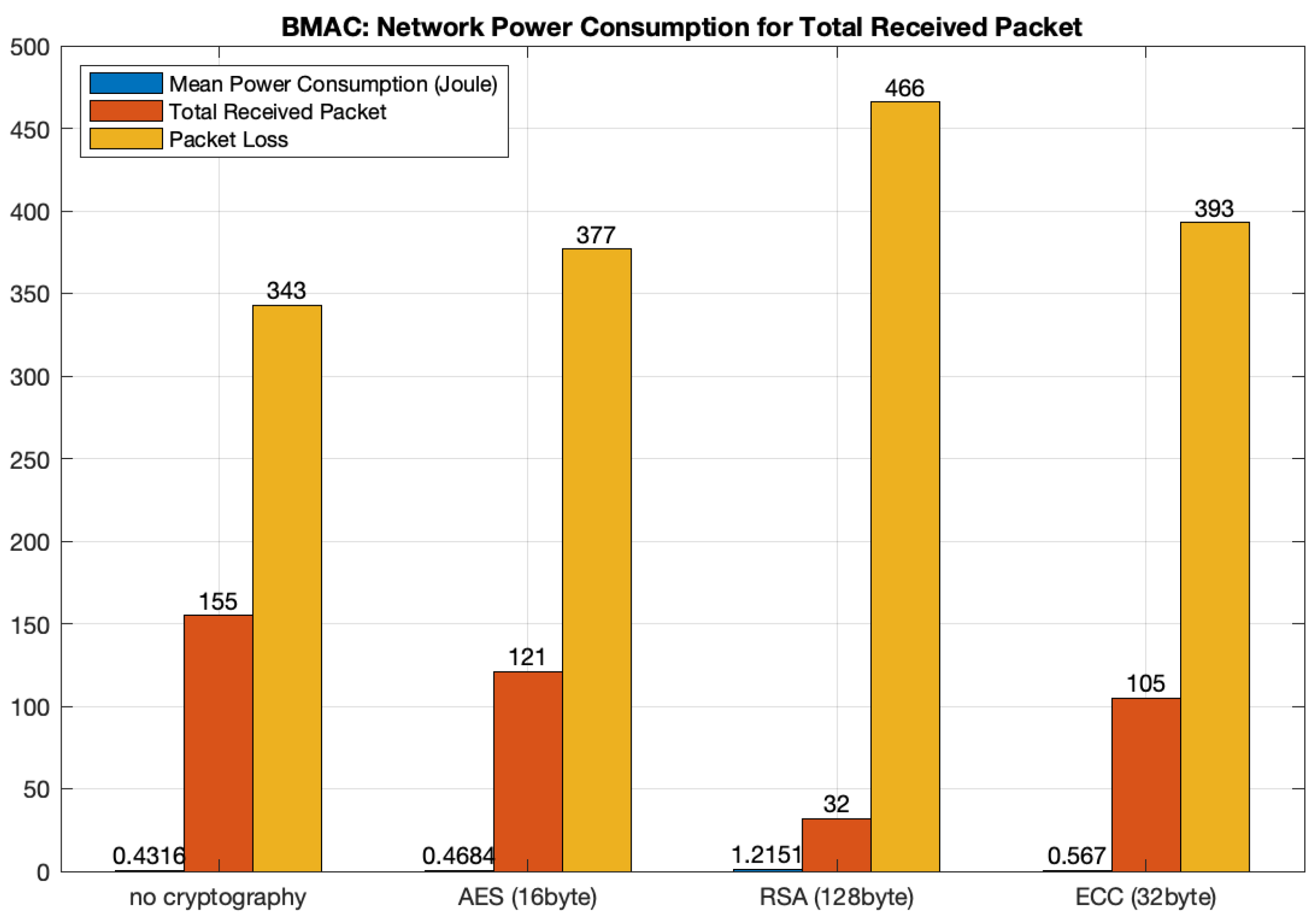
5.5.1. Impersonation Attack with BMAC
Using AES
- The total received packet number is equal to 121 and there are 34 packets less than the initial setup described earlier.
- The energy consumption is equal to 0.46844 J and it is greater than the initial setup.
Using RSA
- The total number of received packets in this case is equal to 32, so 123 packets less than the initial setup and 89 packets with respect to the scenario with AES. This is due to two factors: firstly, the ability of the server to discard the tampered and forged packets and, secondly, the low number of packets sent by sensor nodes since the packets with RSA have a greater length (128 bytes).
- The energy consumption is equal to 1.21514 J and it is greater than the initial setup, AES and even ECC. Since sensor nodes are equipped with limited power and computing resources, they are not able to handle packets which are characterized by a high size, and thus the network will experiment a bottleneck. As a consequence, a large number of packets gets lost.
Using ECC
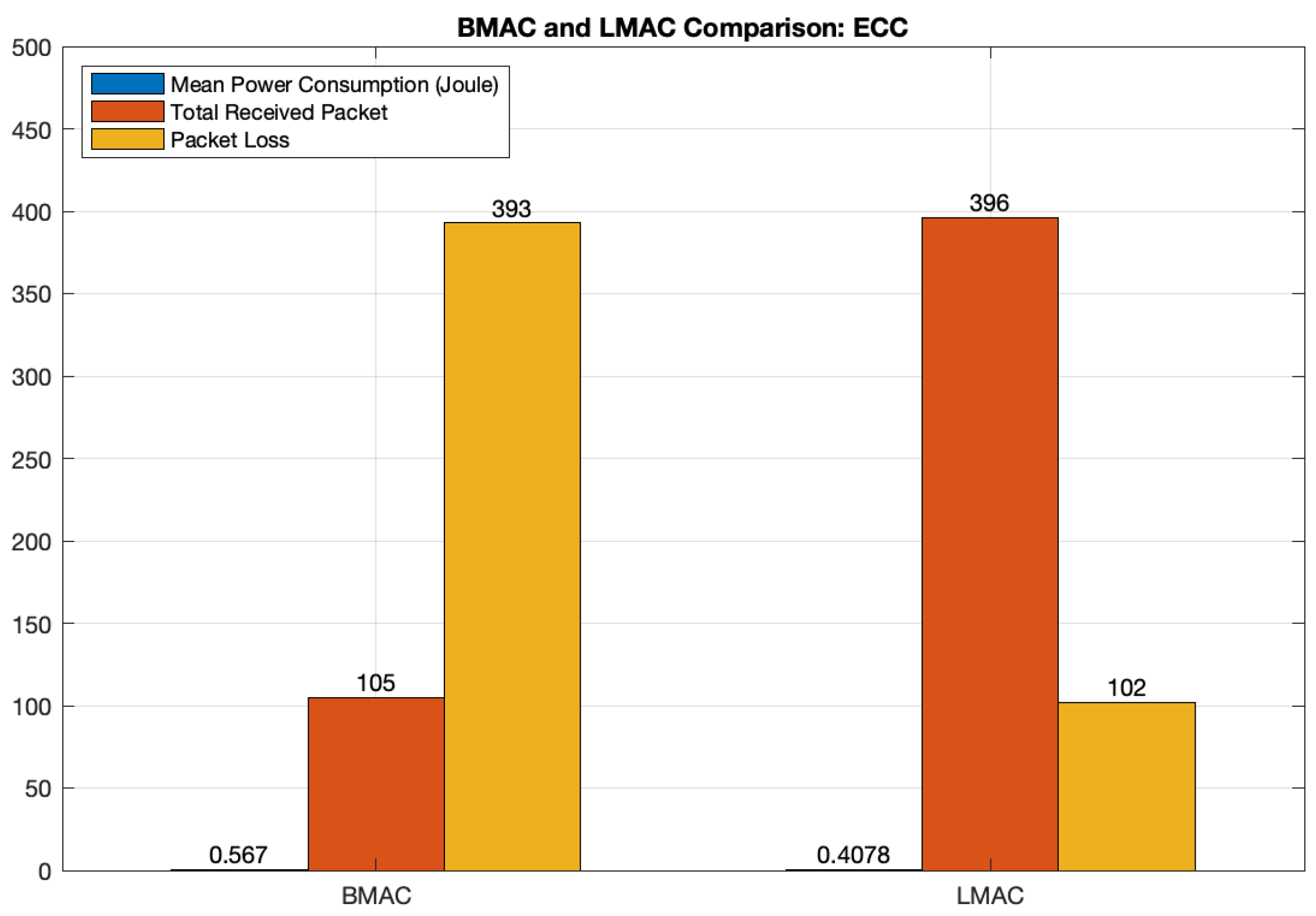
- The total number of received packets is equal to 105, so 50 packets less than the initial setup, 16 less than AES and 73 less than RSA.
- The energy consumption is equal to 0.567043 J and it is greater than all other scenarios.
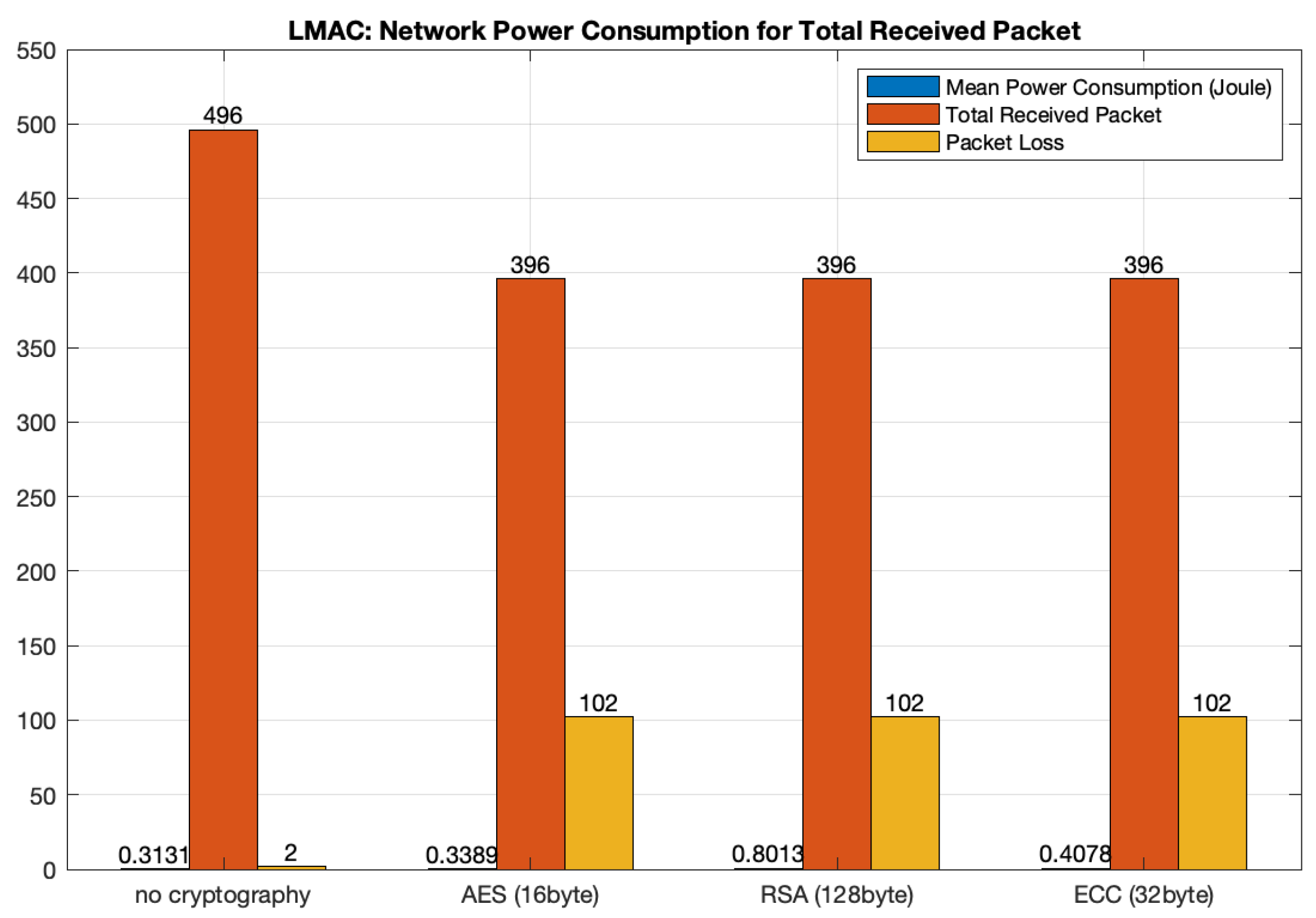
5.5.2. Impersonation Attack with LMAC
Using AES
- The energy consumption is equal to 0.338924 J and it is greater than the initial setup.
Using RSA
- The energy consumption is equal to 0.801263 J and it is greater than the initial setup and the setup with AES and ECC.
Using ECC
- Finally, in this setting, the energy consumption is equal to 0.407812 J, and therefore it is greater than AES and less than RSA.
5.6. BMAC vs. LMAC: Overall Comparison
5.6.1. Bmac and LMAC Comparison Using AES
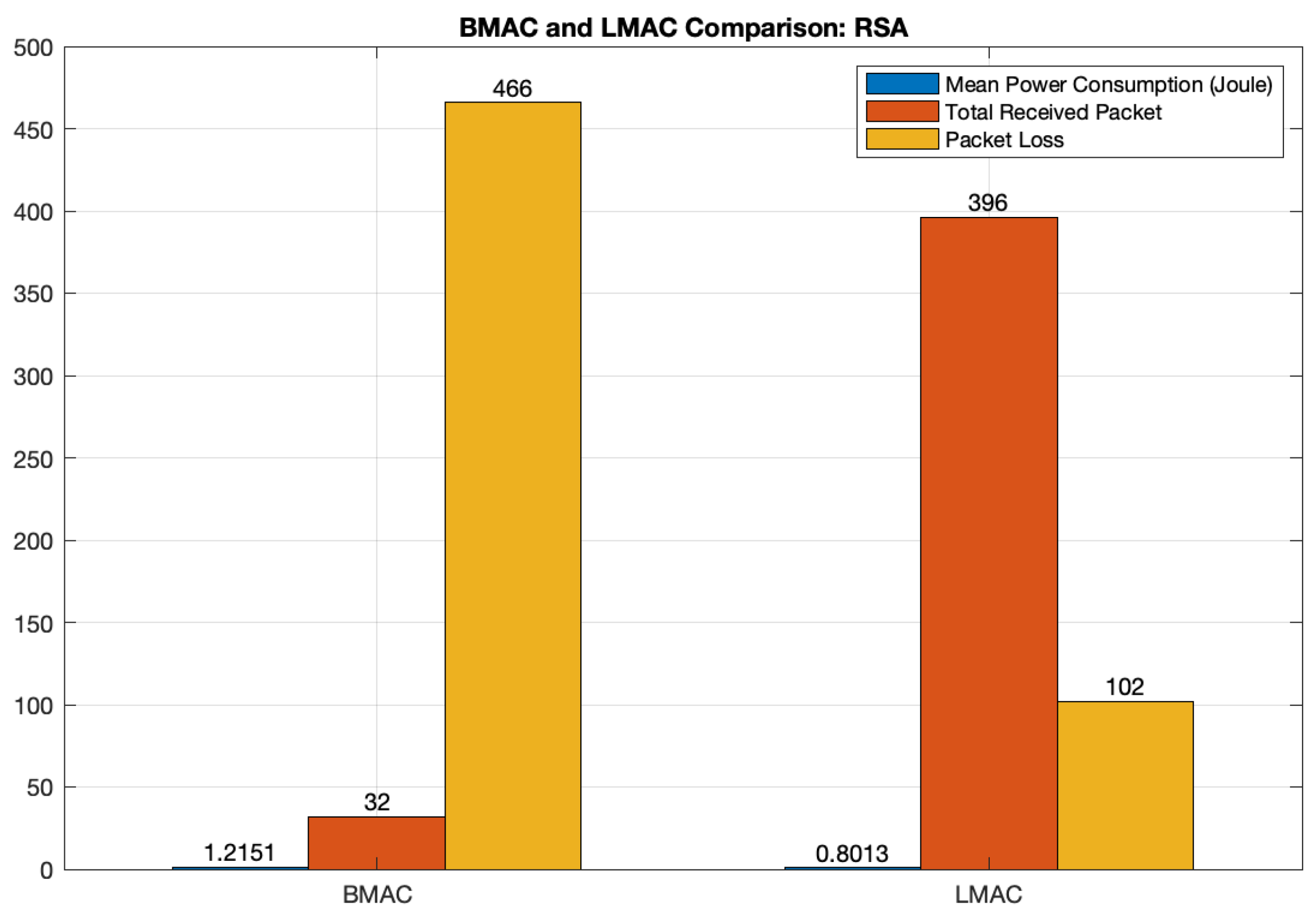
5.6.2. Bmac and LMAC Comparison Using RSA
5.6.3. Bmac and LMAC Comparison Using ECC
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| AES | Advanced Encryption Standard |
| BMAC | Berkeley MAC |
| DES | Data Encryption Standard |
| DLP | Discrete Logarithmic Problem |
| DSA | Digital Signature Algorithm |
| ECC | Elliptic Curve Cryptography |
| ECDH | Elliptic Curve Diffie-Hellman |
| ECDSA | Elliptic Curve DSA |
| LMAC | Lightweight MAC |
| MAC | Medium Access Control |
| NIST | National Institute of Standards and Technology |
| RSA | Rivest Shamir Adelman |
| SMAC | Sensor MAC |
References
- Matin, M.A.; Islam, M. Overview of wireless sensor network. Wirel. Sens.-Netw.-Technol. Protoc. 2012, 1, 3. [Google Scholar] [CrossRef]
- Dhunna, G.S. Low Power MAC Security Mechanisms for WSNs in a Smart Grid Environment. Ph.D. Thesis, The University of Regina, Regina, SK, Canada, 2017. [Google Scholar]
- Chowdhury, S.M.; Hossain, A. Different energy saving schemes in wireless sensor networks: A survey. Wirel. Pers. Commun. 2020, 114, 2043–2062. [Google Scholar] [CrossRef]
- Othman, A.; Maga, D. Relation between security and energy consumption in wireless sensor network (WSN). In Proceedings of the 2018 New Trends in Signal Processing (NTSP), Liptovský Mikuláš, Slovakia, 10–12 October 2018; pp. 1–8. [Google Scholar]
- Afroz, F.; Braun, R. Energy-efficient MAC protocols for wireless sensor networks: A survey. Int. J. Sens. Netw. 2020, 32, 150–173. [Google Scholar] [CrossRef]
- Samara, G. Wireless Sensor Network MAC Energy-efficiency Protocols: A Survey. In Proceedings of the 2020 21st International Arab Conference on Information Technology (ACIT), Giza, Egypt, 28–30 November 2020; pp. 1–5. [Google Scholar]
- Olakanmi, O.O.; Dada, A. Wireless sensor networks (WSNs): Security and privacy issues and solutions. In Wireless Mesh Networks-Security, Architectures and Protocols; IntechOpen: London, UK, 2020; p. 13. [Google Scholar]
- Azzedin, F.; Albinali, H. Security in Internet of Things: RPL Attacks Taxonomy. In Proceedings of the 5th International Conference on Future Networks & Distributed Systems, Dubai, United Arab Emirates, 15–16 December 2021; pp. 820–825. [Google Scholar]
- Khanam, S.; Ahmedy, I.B.; Idris, M.Y.I.; Jaward, M.H.; Sabri, A.Q.B.M. A survey of security challenges, attacks taxonomy and advanced countermeasures in the internet of things. IEEE Access 2020, 8, 219709–219743. [Google Scholar] [CrossRef]
- De Rango, F.; Marano, S. Trust-based SAODV protocol with intrusion detection and incentive cooperation in MANET. In Proceedings of the 2009 International Conference on Wireless Communications and Mobile Computing: Connecting the World Wirelessly, Leipzig, Germany, 21–24 June 2009; pp. 1443–1448. [Google Scholar]
- De Rango, F.; Lentini, D.C.; Marano, S. Static and dynamic 4-way handshake solutions to avoid denial of service attack in Wi-Fi protected access and IEEE 802.11 i. EURASIP J. Wirel. Commun. Netw. 2006, 2006, 47453. [Google Scholar] [CrossRef][Green Version]
- Sergi, C.; Turiaco, N.; De Rango, F. MAC protocols in Wireless Sensor Network: A Energy Comparison Analysis. In Proceedings of the 29th Telecommunications Forum (TELFOR), Belgrade, Serbia, 23–24 November 2021; pp. 1–4. [Google Scholar]
- Li, C.T. Security of wireless sensor networks: Current status and key issues. In Smart Wireless Sensor Networks; IntechOpen: London, UK, 2010; pp. 299–313. [Google Scholar]
- Abdulghani, S.; Shukur, S. A Literature Survey of Energy-Efficient Medium Access Control Protocols for Wireless Sensor Networks. In Proceedings of the 2004 IEEE International Symposium on Industrial Electronics, Ajaccio, France, 4–7 May 2020. [Google Scholar]
- Quintero, V.L.; Estevez, C.; Orchard, M.E.; Pérez, A. Improvements of energy-efficient techniques in WSNs: A MAC-protocol approach. IEEE Commun. Surv. Tutor. 2018, 21, 1188–1208. [Google Scholar] [CrossRef]
- Abrar, E.; Hassan, M.N.; Biswas, M.A.; Jahid, M.S.; Mazid-Ul-Haque, M.; Islam, M.S. Analysis of Micro Duty Cycle Techniques for Efficient SMAC. In Proceedings of the 2021 2nd International Conference on Robotics, Electrical and Signal Processing Techniques (ICREST), Dhaka, Bangladesh, 5–7 January 2021; pp. 433–438. [Google Scholar]
- Munadi, R.; Sulistyorini, A.E.; Adiprabowo, T. Simulation and analysis of energy consumption for S-MAC and T-MAC protocols on wireless sensor network. In Proceedings of the 2015 IEEE Asia Pacific Conference on Wireless and Mobile (APWiMob), Bandung, Indonesia, 27–29 August 2015; pp. 142–146. [Google Scholar]
- Udoh, E.; Getov, V. Proactive energy-efficiency: Evaluation of duty-cycled MAC protocols in wireless sensor networks. In Proceedings of the 2018 International Conference on Computer, Information and Telecommunication Systems (CITS), Colmar, France, 11–13 July 2018; pp. 1–5. [Google Scholar]
- Rehman, M.U.; Uddin, I.; Adnan, M.; Tariq, A.; Malik, S. VTA-SMAC: Variable traffic-adaptive duty cycled sensor MAC protocol to enhance overall QoS of S-MAC protocol. IEEE Access 2021, 9, 33030–33040. [Google Scholar] [CrossRef]
- Punia, S.K.; Ziya, F. Study on MAC Protocols and Attacks: A Review. In Proceedings of the 2019 6th International Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 13–15 March 2019; pp. 621–625. [Google Scholar]
- Ekong, V.; Ekong, U. A survey of security vulnerabilities in wireless sensor networks. Niger. J. Technol. 2016, 35, 392–397. [Google Scholar] [CrossRef][Green Version]
- Tomić, I.; McCann, J.A. A survey of potential security issues in existing wireless sensor network protocols. IEEE Internet Things J. 2017, 4, 1910–1923. [Google Scholar] [CrossRef]
- Tiwari, A.; Varma, R.; Rauthan, M.S.; Barthwal, V. Analysis of Security Attacks and Security Protocols of Wireless Sensor Network: Review. Available online: http://www.ijstr.org/final-print/jan2020/Analysis-Of-Security-Attacks-And-Security-Protocols-Of-Wireless-Sensor-Network-Review.pdf (accessed on 5 May 2022).
- Liu, Y.; Li, C.; Zhang, J.; Liu, Q. A Homomorphic MAC-based Secure Data Aggregation Scheme for Wireless Sensor Networks. J. Internet Technol. 2018, 19, 2069–2077. [Google Scholar]
- Elshrkawey, M.; Al-Mahdi, H. Sda-sm: An efficient secure data aggregation scheme using separate mac across wireless sensor networks. Int. J. Comput. Commun. Control. 2021, 16, 4xyz. [Google Scholar] [CrossRef]
- Almansoori, M.N.; Elshamy, A.A.; Mustafa, A.A.M. Secure Z-MAC Protocol as a Proposed Solution for Improving Security in WSNs. Information 2022, 13, 105. [Google Scholar] [CrossRef]
- Hoesel, L.V. A lightweight medium access protocol (LMAC) for wireless sensor networks: Reducing preamble transmissions and transceiver state switches. In Proceedings of the 1st International Workshop on Networked Sensing Systems, Toronto, ON, Canada, 30 August 2004. [Google Scholar]
- Dinh, T.; Kim, Y.; Gu, T.; Vasilakos, A.V. L-MAC: A wake-up time self-learning MAC protocol for wireless sensor networks. Comput. Netw. 2016, 105, 33–46. [Google Scholar] [CrossRef]
- Polastre, J.; Hill, J.; Culler, D. Versatile low power media access for wireless sensor networks. In Proceedings of the 2nd International Conference on Embedded Networked Sensor Systems, Baltimore, MD, USA, 3–5 November 2004; pp. 95–107. [Google Scholar]
- Khan, M.U.; Ahmed, S.; Khan, Z.A.; Ullah, Z.; Ahmed, I. Various node mobility scenarios of wireless sensor networks based on B-MAC protocol. In Proceedings of the 2017 Fourth HCT Information Technology Trends (ITT), Al Ain, United Arab Emirates, 25–26 October 2017; pp. 61–66. [Google Scholar]
- Chaouch, A.; Bouallegue, B.; Bouraoui, O. Software application for simulation-based AES, RSA and elliptic-curve algorithms. In Proceedings of the 2016 2nd International Conference on Advanced Technologies for Signal and Image Processing (ATSIP), Monastir, Tunisia, 21–23 March 2016; pp. 77–82. [Google Scholar]
- Hwang, M.S.; Cahyadi, E.F.; Yang, C.Y.; Chiou, S.F. An improvement of the remote authentication scheme for anonymous users using an elliptic curve cryptosystem. In Proceedings of the 2018 IEEE 4th International Conference on Computer and Communications (ICCC), Chengdu, China, 7–10 December 2018; pp. 1872–1877. [Google Scholar]
- De Rango, F.; Potrino, G.; Tropea, M.; Fazio, P. Energy-aware dynamic Internet of Things security system based on Elliptic Curve Cryptography and Message Queue Telemetry Transport protocol for mitigating Replay attacks. Pervasive Mob. Comput. 2020, 61, 101105. [Google Scholar] [CrossRef]
- De Rango, F.; Tropea, M.; Fazio, P. Mitigating DoS attacks in IoT EDGE Layer to preserve QoS topics and nodes’ energy. In Proceedings of the IEEE INFOCOM 2020-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Toronto, ON, Canada, 6–9 July 2020; pp. 842–847. [Google Scholar]
- Odlyzko, A. Discrete logarithms: The past and the future. In Towards a Quarter-Century of Public Key Cryptography; Springer: Berlin/Heidelberg, Germany, 2000; pp. 59–75. [Google Scholar]
- Vo, S.C. A Survey of Elliptic Curve Cryptosystems, Part I: Introductory; NAS Technical Report—NAS-03-012; NASA Advanced Supercomputing Division, NASA: Washington, DC, USA, 2003.
- Sun, J.; Lin, S.; Hwang, M. Cryptanalysis and improvement of a directed digital signature scheme using a non-interactive public-key distribution system. In Future Communication Technology and Engineering, Proceedings of the 2014 International Conference on Future Communication Technology and Engineering (FCTE 2014), Shenzhen, China, 16–17 November 2014; CRC Press: Boca Raton, FL, USA, 2015; p. 99. [Google Scholar]
- Tsai, C.S.; Hwang, M.S.; Sung, P.C. Blind Signature Scheme Based on Elliptic Curve Cryptography; National Chung Hsing University: Taichung, Taiwan, 2012. [Google Scholar]
- Keerthika, M.; Shanmugapriya, D. Wireless Sensor Networks: Active and Passive attacks-Vulnerabilities and Countermeasures. Glob. Trans. Proc. 2021, 2, 362–367. [Google Scholar] [CrossRef]
- Nguyen, V.L.; Lin, P.C.; Hwang, R.H. Energy depletion attacks in low power wireless networks. IEEE Access 2019, 7, 51915–51932. [Google Scholar] [CrossRef]
- Butun, I.; Österberg, P.; Song, H. Security of the Internet of Things: Vulnerabilities, attacks, and countermeasures. IEEE Commun. Surv. Tutor. 2019, 22, 616–644. [Google Scholar] [CrossRef]
- Zhang, Y.; Liu, W.; Fang, Y. Secure localization in wireless sensor networks. In Proceedings of the MILCOM 2005—2005 IEEE Military Communications Conference, Atlantic City, NJ, USA, 17–20 October 2005; pp. 3169–3175. [Google Scholar]
- Regan, R.; Manickam, J.; Leo, M. A survey on impersonation attack in wireless networks. Int. J. Secur. Its Appl. 2017, 11, 39–48. [Google Scholar] [CrossRef]
- OMNeT++. Available online: https://omnetpp.org// (accessed on 19 July 2021).
- INET Framework. Available online: https://inet.omnetpp.org// (accessed on 19 July 2021).




Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tropea, M.; Spina, M.G.; De Rango, F.; Gentile, A.F. Security in Wireless Sensor Networks: A Cryptography Performance Analysis at MAC Layer. Future Internet 2022, 14, 145. https://doi.org/10.3390/fi14050145
Tropea M, Spina MG, De Rango F, Gentile AF. Security in Wireless Sensor Networks: A Cryptography Performance Analysis at MAC Layer. Future Internet. 2022; 14(5):145. https://doi.org/10.3390/fi14050145
Chicago/Turabian StyleTropea, Mauro, Mattia Giovanni Spina, Floriano De Rango, and Antonio Francesco Gentile. 2022. "Security in Wireless Sensor Networks: A Cryptography Performance Analysis at MAC Layer" Future Internet 14, no. 5: 145. https://doi.org/10.3390/fi14050145
APA StyleTropea, M., Spina, M. G., De Rango, F., & Gentile, A. F. (2022). Security in Wireless Sensor Networks: A Cryptography Performance Analysis at MAC Layer. Future Internet, 14(5), 145. https://doi.org/10.3390/fi14050145







