IoT-Based System for Improving Vehicular Safety by Continuous Traffic Violation Monitoring
Abstract
1. Introduction
- An IoT-based system for the continuous monitoring of traffic violations, including over-speeding, passenger overloading, and seatbelt unfastening, is presented. This contribution includes both the architecture, consisting of edge computing, fog computing, and cloud computing, and the algorithms used for the monitoring. This system benefits the safety of autonomous vehicles.
- Empirical proof shows that adding a fog layer between the edge and cloud layers improves the estimation accuracy, because the fog layer provides the system with more computational resources for operating the estimation algorithms.
- Empirical proof shows that the sensor-based approach achieves high accuracy in speed estimation, passenger counting, and seatbelt fastening checks, while maintaining a low computational demand on the edge side.
2. Related Work
2.1. Speed Monitoring Systems
2.2. Passenger Number Monitoring Systems
2.3. Seatbelt Monitoring Systems
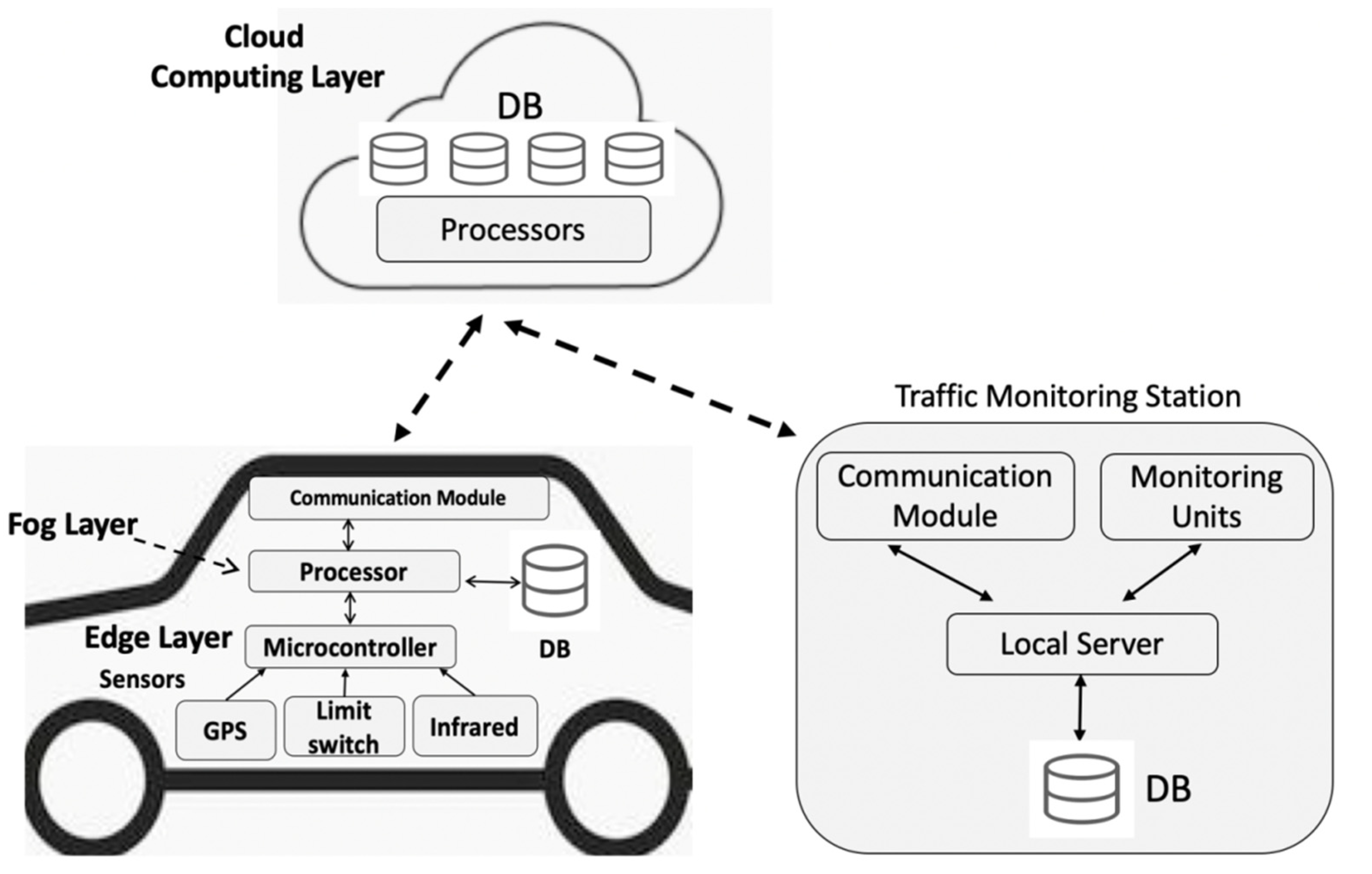
3. Proposed System
3.1. The Edge and Sensor Layer
3.2. The Fog Computing Layer
3.3. The Cloud Computing Layer
3.4. Monitoring Station
4. Experiment and Results
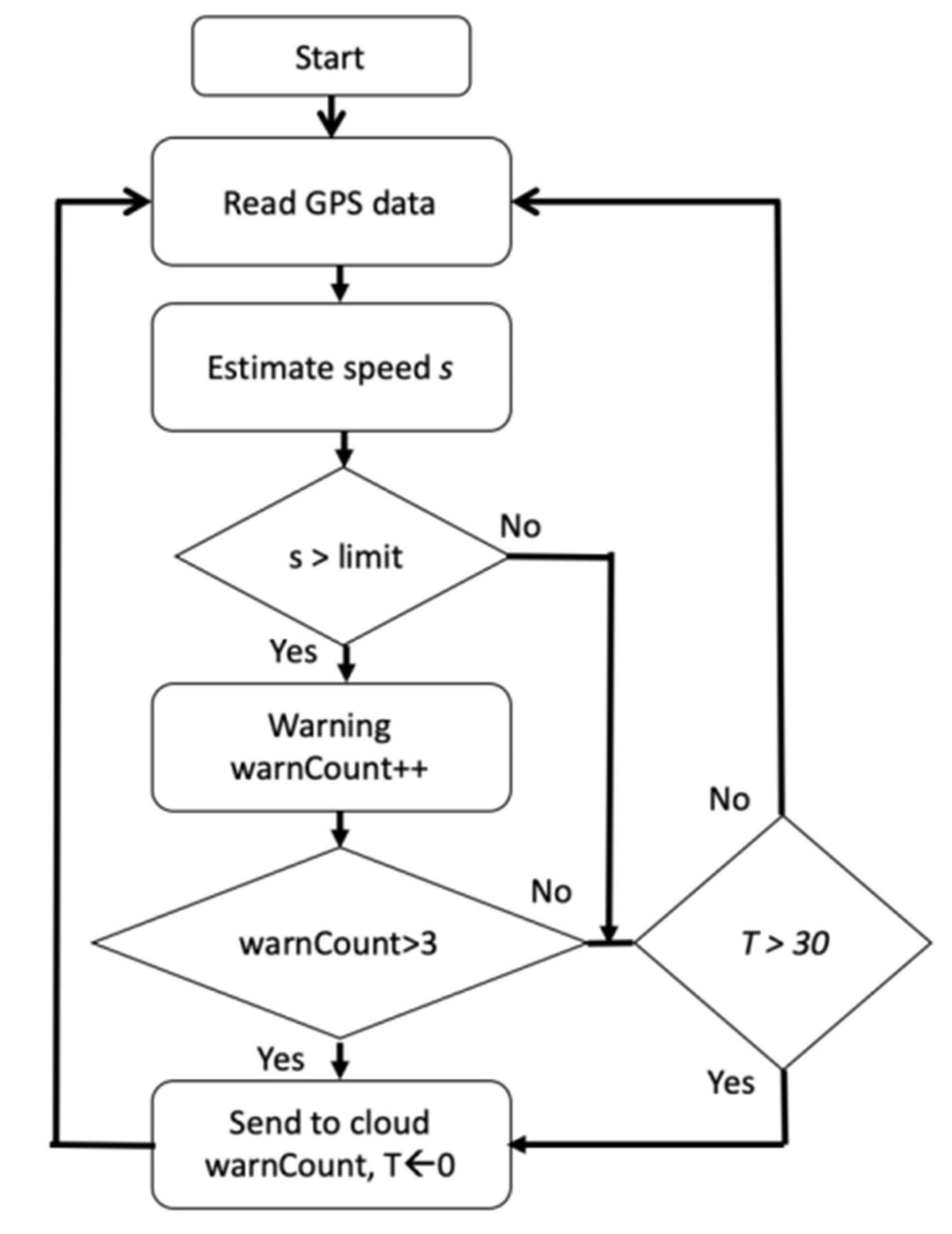
4.1. Speed Estimation Results
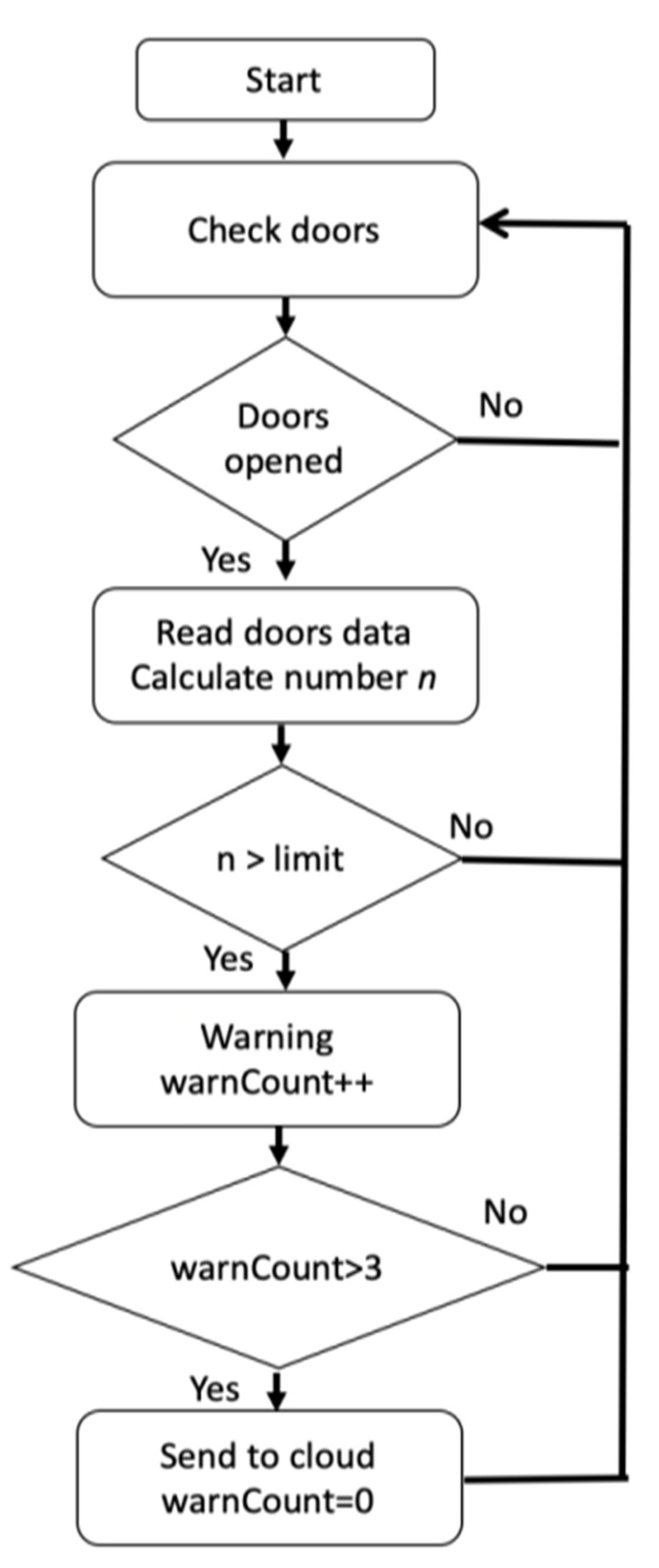
4.2. Passenger Number Monitoring Results
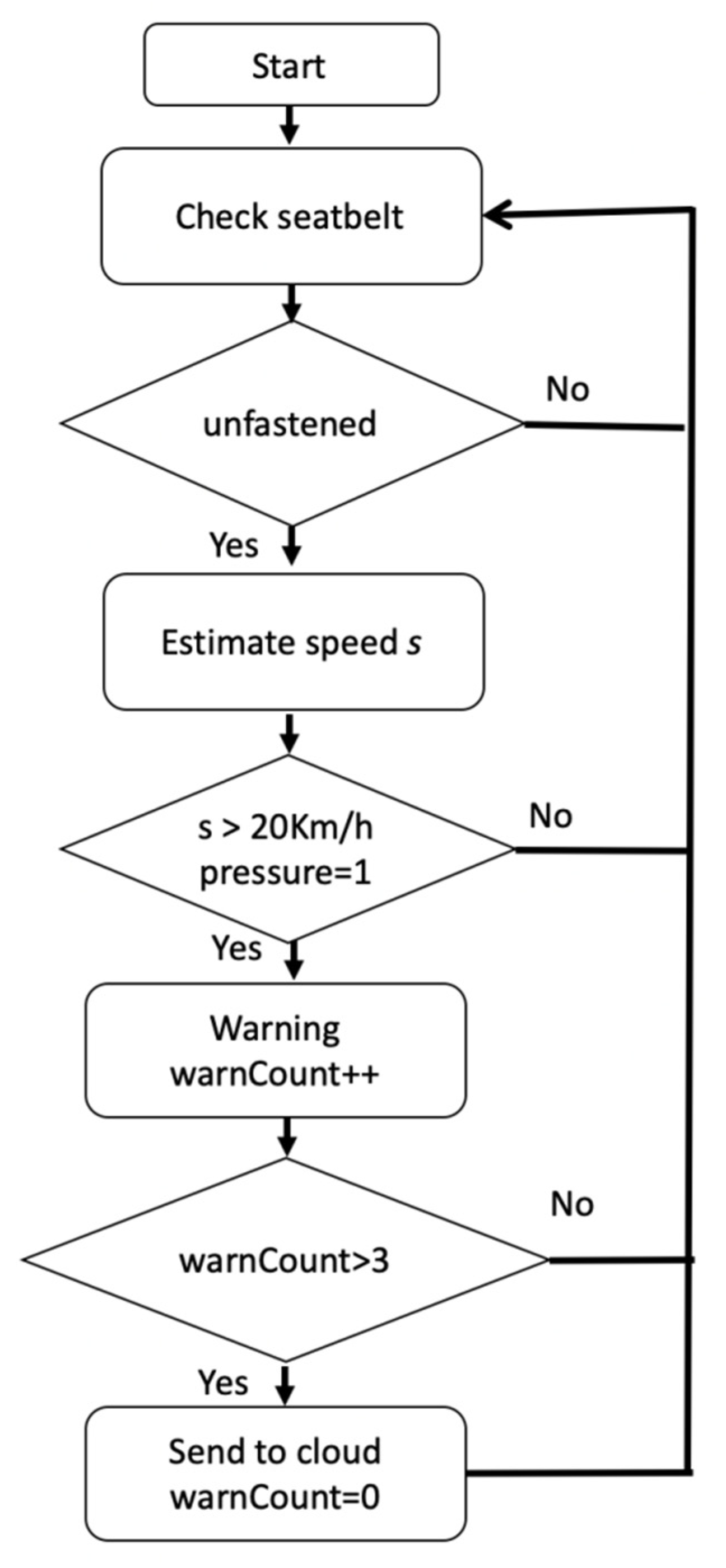
4.3. Seatbelt Monitoring Results
4.4. Latency Analysis
5. Limitations
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Wang, J.; Wu, J.; Li, Y. The Driving Safety Field Based on Driver–Vehicle–Road Interactions. IEEE Trans. Intell. Transp. Syst. 2015, 16, 2203–2214. [Google Scholar] [CrossRef]
- Ashraf, K.; Varadarajan, V.; Rahman, M.R.; Walden, R.; Ashok, A. See-Through a Vehicle: Augmenting Road Safety Information Using Visual Perception and Camera Communication in Vehicles. IEEE Trans. Veh. Technol. 2021, 70, 3071–3086. [Google Scholar] [CrossRef]
- Telawi, S.; Hayek, A.; Borcsok, J. Safe Detection of Wheels Spinning and Sliding in Vehicles. IEEE Trans. Veh. Technol. 2022, 71, 9410–9421. [Google Scholar] [CrossRef]
- Boujemaa, K.S.; Berrada, I.; Fardousse, K.; Naggar, O.; Bourzeix, F. Toward Road Safety Recommender Systems: Formal Concepts and Technical Basics. IEEE Trans. Intell. Transp. Syst. 2022, 23, 5211–5230. [Google Scholar] [CrossRef]
- Dhulavvagol, P.M.; Desai, A.; Ganiger, R. Vehical Tracking and Speed Estimation of Moving Vehicles for Traffic Surveillance Applications. In Proceedings of the 2017 International Conference on Current Trends in Computer, Electrical, Electronics and Communication (CTCEEC), Mysore, India, 8–9 September 2017; pp. 373–377. [Google Scholar] [CrossRef]
- Roriz, R.; Cabral, J.; Gomes, T. Automotive LiDAR Technology: A Survey. IEEE Trans. Intell. Transp. Syst. 2022, 23, 6282–6297. [Google Scholar] [CrossRef]
- Cui, Y.; Xu, H.; Wu, J.; Sun, Y.; Zhao, J. Automatic Vehicle Tracking with Roadside LiDAR Data for the Connected-Vehicles System. IEEE Intell. Syst. 2019, 34, 44–51. [Google Scholar] [CrossRef]
- Bonyar, A.; Geczy, A.; Harsanyi, G.; Hanak, P. Passenger Detection and Counting Inside Vehicles For eCall- a Review on Current Possibilities. In Proceedings of the 2018 IEEE 24th International Symposium for Design and Technology in Electronic Packaging (SIITME), Iasi, Romania, 25–28 October 2018; pp. 221–225. [Google Scholar] [CrossRef]
- IEE. Seat Belt Reminder Sensors. Available online: https://iee-sensing.com/automotive/safety-and-comfort/seat-belt-reminder/ (accessed on 28 September 2022).
- Standex Electronics. Seat Belt Sensor. Available online: https://standexelectronics.com/applications-markets/seat-belt-sensor/ (accessed on 28 September 2022).
- Beymer, D.; McLauchlan, P.; Coifman, B.; Malik, J. A real-time computer vision system for measuring traffic parameters. In Proceedings of the IEEE Computer Society Conference on Computer Vision and Pattern Recognition, San Juan, PR, USA, 17–19 June 1997; pp. 495–501. [Google Scholar] [CrossRef]
- Jianzhong, X.; Qiuyu, Z.; Sai, Y.; Wenjun, S. Passenger counting based on Kinect. In Proceedings of the 2014 International Conference on Audio, Language and Image Processing, Shanghai, China, 7–9 July 2014; pp. 405–409. [Google Scholar] [CrossRef]
- Guo, H.; Lin, H.; Zhang, S.; Li, S. Image-based seat belt detection. In Proceedings of the 2011 IEEE International Conference on Vehicular Electronics and Safety, Beijing, China, 10–12 July 2011; pp. 161–164. [Google Scholar] [CrossRef]
- Maduri, P.K.; Singh, G.; Sharma, S.; Mishra, R.K.; Mishra, N.K. Seat Belt And Helmet Detection Using Deep Learning. In Proceedings of the 2021 3rd International Conference on Advances in Computing, Communication Control and Networking (ICAC3N), Greater Noida, India, 17–18 December 2021; pp. 476–480. [Google Scholar] [CrossRef]
- Cui, Y.; Chen, R.; Chu, W.; Chen, L.; Tian, D.; Li, Y.; Cao, D. Deep Learning for Image and Point Cloud Fusion in Autonomous Driving: A Review. IEEE Trans. Intell. Transp. Syst. 2022, 23, 722–739. [Google Scholar] [CrossRef]
- Haydari, A.; Yilmaz, Y. Deep Reinforcement Learning for Intelligent Transportation Systems: A Survey. IEEE Trans. Intell. Transp. Syst. 2022, 23, 11–32. [Google Scholar] [CrossRef]
- Daraghmi, Y.-A. Vehicle Speed Monitoring System Based on Edge Computing. In Proceedings of the International Conference on Promising Electronic Technologies (ICPET), Deir El-Balah, Palestine, 17–18 November 2021. [Google Scholar]
- Islam, M.; Rahman, M.; Chowdhury, M.; Comert, G.; Sood, E.D.; Apon, A. Vision-Based Personal Safety Messages (PSMs) Generation for Connected Vehicles. IEEE Trans. Veh. Technol. 2020, 69, 9402–9416. [Google Scholar] [CrossRef]
- Chen, C.; Liu, B.; Wan, S.; Qiao, P.; Pei, Q. An Edge Traffic Flow Detection Scheme Based on Deep Learning in an Intelligent Transportation System. IEEE Trans. Intell. Transp. Syst. 2021, 22, 1840–1852. [Google Scholar] [CrossRef]
- Chen, X.; Wu, C.; Liu, Z.; Zhang, N.; Ji, Y. Computation Offloading in Beyond 5G Networks: A Distributed Learning Framework and Applications. IEEE Wirel. Commun. 2021, 28, 56–62. [Google Scholar] [CrossRef]
- Du, Z.; Wu, C.; Yoshinaga, T.; Yau, K.-L.A.; Ji, Y.; Li, J. Federated Learning for Vehicular Internet of Things: Recent Advances and Open Issues. IEEE Open J. Comput. Soc. 2020, 1, 45–61. [Google Scholar] [CrossRef] [PubMed]
- Xu, X.; Fang, Z.; Qi, L.; Zhang, X.; He, Q.; Zhou, X. TripRe. ACM Trans. Multimed. Comput. Commun. Appl. 2021, 17, 1–21. [Google Scholar] [CrossRef]
- Wan, S.; Ding, S.; Chen, C. Edge computing enabled video segmentation for real-time traffic monitoring in internet of vehicles. Pattern Recognit. 2022, 121, 108146. [Google Scholar] [CrossRef]
- Meghana, V.; Anisha, B.S.; Kumar, P.R. IOT based Smart Traffic Signal Violation Monitoring System using Edge Computing. In Proceedings of the 2021 2nd Global Conference for Advancement in Technology (GCAT), Bangalore, India, 1–3 October 2021; pp. 1–5. [Google Scholar] [CrossRef]
- Chen, N.; Chen, Y. Anomalous Vehicle Recognition in Smart Urban Traffic Monitoring as an Edge Service. Future Internet 2022, 14, 54. [Google Scholar] [CrossRef]
- Khan, O.; Ibrahim, A.; Mamlook, R. Fog Computing-Based Model for Mitigation of Traffic Congestion. Int. J. Simul. Syst. Sci. Technol. 2019, 19, 5.1–5.7. [Google Scholar] [CrossRef]
- Vergis, S.; Komianos, V.; Tsoumanis, G.; Tsipis, A.; Oikonomou, K. A Low-Cost Vehicular Traffic Monitoring System Using Fog Computing. Smart Cities 2020, 3, 138–156. [Google Scholar] [CrossRef]
- Ding, X.; Wang, Z.; Zhang, L.; Wang, C. Longitudinal Vehicle Speed Estimation for Four-Wheel-Independently-Actuated Electric Vehicles Based on Multi-Sensor Fusion. IEEE Trans. Veh. Technol. 2020, 69, 12797–12806. [Google Scholar] [CrossRef]
- Tan, G.; Gao, H. Vehicle state estimation of steer by wire system based on multi sensor fusion. In Proceedings of the 2017 Chinese Automation Congress (CAC), Jinan, China, 20–22 October 2017; pp. 6329–6333. [Google Scholar] [CrossRef]
- Xue, W.; Wang, D.; Wang, L. Monitoring the Speed, Configurations, and Weight of Vehicles Using an In-Situ Wireless Sensing Network. IEEE Trans. Intell. Transp. Syst. 2015, 16, 1667–1675. [Google Scholar] [CrossRef]
- Daraghmi, Y.-A.; Wu, T.-H.; Ik, T.-U. Crowdsourcing-Based Road Surface Evaluation and Indexing. IEEE Trans. Intell. Transp. Syst. 2022, 23, 4164–4175. [Google Scholar] [CrossRef]
- Singla, L.; Bhatia, P. GPS based bus tracking system. In Proceedings of the 2015 International Conference on Computer, Communication and Control (IC4), Indore, India, 10–12 September 2015; pp. 1–6. [Google Scholar] [CrossRef]
- Wei, J.; Chiu, C.-H.; Huang, F.; Zhang, J.; Cai, C. A cost-effective decentralized vehicle remote positioning and tracking system using BeiDou Navigation Satellite System and Mobile Network. EURASIP J. Wirel. Commun. Netw. 2019, 2019, 112. [Google Scholar] [CrossRef]
- Daraghmi, Y.-A.; Daadoo, M. Intelligent Smartphone based system for detecting speed bumps and reducing car speed. MATEC Web Conf. 2016, 77, 09006. [Google Scholar] [CrossRef]
- Koubaa, A.; Qureshi, B. DroneTrack: Cloud-Based Real-Time Object Tracking Using Unmanned Aerial Vehicles Over the Internet. IEEE Access 2018, 6, 13810–13824. [Google Scholar] [CrossRef]
- Kanhere, N.K.; Birchfield, S.T. A Taxonomy and Analysis of Camera Calibration Methods for Traffic Monitoring Applications. IEEE Trans. Intell. Transp. Syst. 2010, 11, 441–452. [Google Scholar] [CrossRef]
- Yabo, A.; Arroyo, S.; Safar, F.G.; Oliva, D. Vehicle classification and speed estimation using Computer Vision techniques. In Proceedings of the XXV Congreso Argentino de Control Automático, Buenos Aires, Argentina, 19–22 September 2016. [Google Scholar]
- Barth, V.; de Oliveira, R.; de Oliveira, M.; Nascimento, V.d. Vehicle Speed Monitoring using Convolutional Neural Networks. IEEE Lat. Am. Trans. 2019, 17, 1000–1008. [Google Scholar] [CrossRef]
- Luvizon, D.C.; Nassu, B.T.; Minetto, R. A Video-Based System for Vehicle Speed Measurement in Urban Roadways. IEEE Trans. Intell. Transp. Syst. 2016, 18, 1393–1404. [Google Scholar] [CrossRef]
- Zhong, G.; Wan, X.; Zhang, J.; Yin, T.; Ran, B. Characterizing Passenger Flow for a Transportation Hub Based on Mobile Phone Data. IEEE Trans. Intell. Transp. Syst. 2016, 18, 1507–1518. [Google Scholar] [CrossRef]
- Yuen, J.K.K.; Lee, E.W.M.; Lo, S.M.; Yuen, R.K.K. An Intelligence-Based Optimization Model of Passenger Flow in a Transportation Station. IEEE Trans. Intell. Transp. Syst. 2013, 14, 1290–1300. [Google Scholar] [CrossRef]
- Seidel, R.; Jahn, N.; Seo, S.; Goerttler, T.; Obermayer, K. NAPC: A Neural Algorithm for Automated Passenger Counting in Public Transport on a Privacy-Friendly Dataset. IEEE Open J. Intell. Transp. Syst. 2022, 3, 33–44. [Google Scholar] [CrossRef]
- Janitzek, T.; Achterberg, F. Seat Belt Reminders, Implementing Advanced Safety Technology in Europe’s Cars. ETC. 2006. Available online: https://etsc.eu/seat-belt-reminders/ (accessed on 6 October 2022).
- BuckleMeUp. Buckle Me Up Seatbelt Reminder and Alert. Available online: https://www.bucklemeup.com/ (accessed on 28 September 2022).
- FEI. Seat Belt Sensors. Available online: https://www.fab-ent.com/adl/alarms-sensors/seat-belt-sensors (accessed on 28 September 2022).
- Kashevnik, A.; Ali, A.; Lashkov, I.; Shilov, N. Seat Belt Fastness Detection Based on Image Analysis from Vehicle In-abin Camera. In Proceedings of the 2020 26th Conference of Open Innovations Association (FRUCT), Yaroslavl, Russia, 20–24 April 2020; pp. 143–150. [Google Scholar] [CrossRef]
- Ren, S.; He, K.; Girshick, R.; Sun, J. Faster R-CNN: Towards Real-Time Object Detection with Region Proposal Networks. IEEE Trans. Pattern Anal. Mach. Intell. 2017, 39, 1137–1149. [Google Scholar] [CrossRef]
- Wu, T.; Zhang, Z.; Liu, Y.; Guo, W.; Wang, Z. Driver Seat Belt Detection Based on YOLO Detection and Semantic Segmentation. J. Comput.-Aided Des. Comput. Graph. 2019, 31, 126. [Google Scholar] [CrossRef]
- Yang, D.; Zang, Y.; Liu, Q. Study of Detection Method on Real-time and High Precision Driver Seatbelt. In Proceedings of the 2020 Chinese Control And Decision Conference (CCDC), Hefei, China, 22–24 August 2020; pp. 79–86. [Google Scholar] [CrossRef]
- Artan, Y.; Bulan, O.; Loce, R.P.; Paul, P. Passenger Compartment Violation Detection in HOV/HOT Lanes. IEEE Trans. Intell. Transp. Syst. 2016, 17, 395–405. [Google Scholar] [CrossRef]
- Korn, G.A.; Korn, T.M. Appendix b: B9. plane and spherical trigonometry: Formulas expressed in terms of the haversine function. In Mathematical Handbook for Scientists and Engineers: Definitions, Theorems, and Formulars for Reference and Review, 3rd ed.; Mineola: New York, NY, USA, 2000. [Google Scholar]
- OpenStreetBrowser. Available online: https://www.openstreetbrowser.org/#map=13/32.2668/35.1126&categories=car_maxspeed (accessed on 22 October 2022).
- Buyya, R.; Ranjan, R.; Calheiros, R.N. Modeling and Simulation of Scalable Cloud Computing Environments and the CloudSim Toolkit: Challenges and Opportunities. Available online: https://arxiv.org/ftp/arxiv/papers/0907/0907.4878.pdf (accessed on 29 September 2022).
- Daraghmi, E.-Y.; Daraghmi, Y.-A.; Yuan, S.-M. MedChain: A design of blockchain-based system for medical records access and permissions management. IEEE Access 2019, 7, 164595–164613. [Google Scholar] [CrossRef]
- Daraghmi, E.Y.; Daraghmi, Y.A.; Yuan, S.M. UniChain: A Design of Blockchain-Based System for Electronic Academic Records Access and Permissions Management. Appl. Sci. 2019, 9, 4966. [Google Scholar] [CrossRef]
- Daraghmi, E.-Y.; Helou, M.A.; Daraghmi, Y.-A. A Blockchain-Based Editorial Management System. Secur. Commun. Netw. 2021, 2021, 9927640. [Google Scholar] [CrossRef]
- Daraghmi, Y.-A.; Yi, C.-W.; Chiang, T.-C. Negative Binomial Additive Models for Short-Term Traffic Flow Forecasting in Urban Areas. IEEE Trans. Intell. Transp. Syst. 2014, 15, 784–793. [Google Scholar] [CrossRef]
- Ali, F.; Ali, A.; Imran, M.; Naqvi, R.A.; Siddiqi, M.H.; Kwak, K.-S. Traffic accident detection and condition analysis based on social networking data. Accid. Anal. Prev. 2021, 151, 105973. [Google Scholar] [CrossRef]
- Bag, S.; Pretorius, J.H.C.; Gupta, S.; Dwivedi, Y.K. Role of institutional pressures and resources in the adoption of big data analytics powered artificial intelligence, sustainable manufacturing practices and circular economy capabilities. Technol. Forecast. Soc. Chang. 2021, 163, 120420. [Google Scholar] [CrossRef]
- Khasawneh, A.M.; Helou, M.A.; Khatri, A.; Aggarwal, G.; Kaiwartya, O.; Altalhi, M.; Abu-ulbeh, W.; AlShboul, R. Service-Centric Heterogeneous Vehicular Network Modeling for Connected Traffic Environments. Sensors 2022, 22, 1247. [Google Scholar] [CrossRef]

| Sensor-Based Approach | Computer-Vision-Based Approach | |
|---|---|---|
| Speed estimation | Proposed system [5,6,7,15,30,33,34] | [36,37,38,39] |
| Passenger counting | Proposed system [8] | [12,42] |
| Seatbelt detection | Proposed system [43,44,45] | [13,14,46,48,49,50] |
| Smartphones | CPU | GPU (Adreno) | Memory (GB) |
|---|---|---|---|
| s1 | Octa-core (2 × 2.3 GHz Kryo 465 Gold 6 × 1.8 GHz Kryo 465 Silver) | 618 | 128 |
| s2 | Octa-core (4 × 2.2 GHz Kryo 260 Gold 4 × 1.8 GHz Kryo 260 Silver) | 512 | 64 |
| s3 | Hexa-core (4 × 1.4 GHz Cortex-A53 2 × 1.8 GHz Cortex-A72) | 510 | 16 |
| Parameter | Value |
|---|---|
| Number of data centers | 1 |
| Number of hosts | 1 |
| Number of data center brokers | 1 |
| Number of virtual machines (VM) | 4 |
| Number of processing elements (PE) | 1 |
| MIPS of PE | 4000 |
| MIPS of each VM | 400 |
| VM RAM | 2048 MB |
| Data center scheduling | Space-shared |
| VM scheduling | Space-shared |
| Bandwidth | 1000 |
| Number of cloudlets | 10 |
| Cloudlet scheduling | Space-shared |
| CPU, RAM, BW | Full utilization |
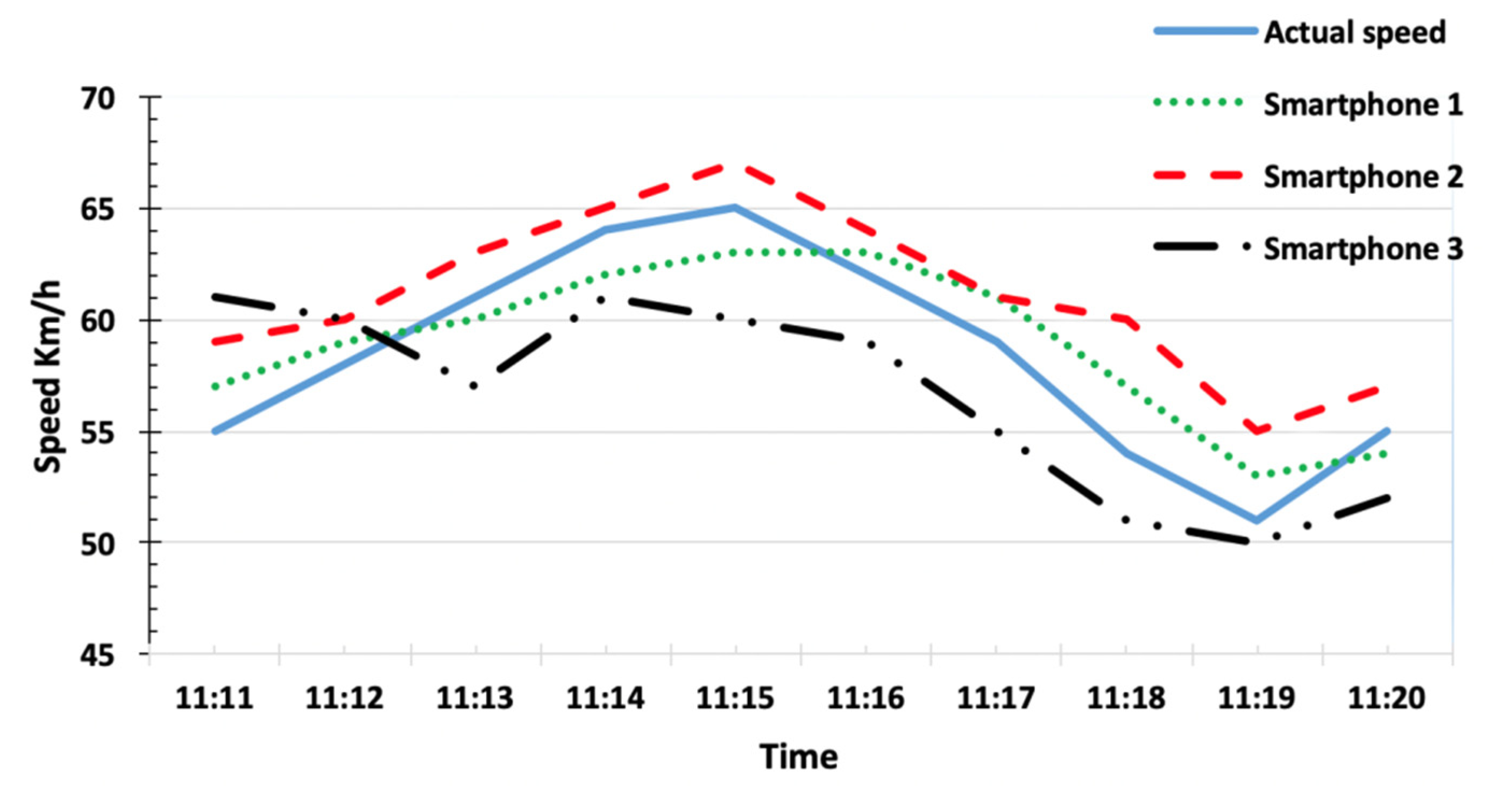
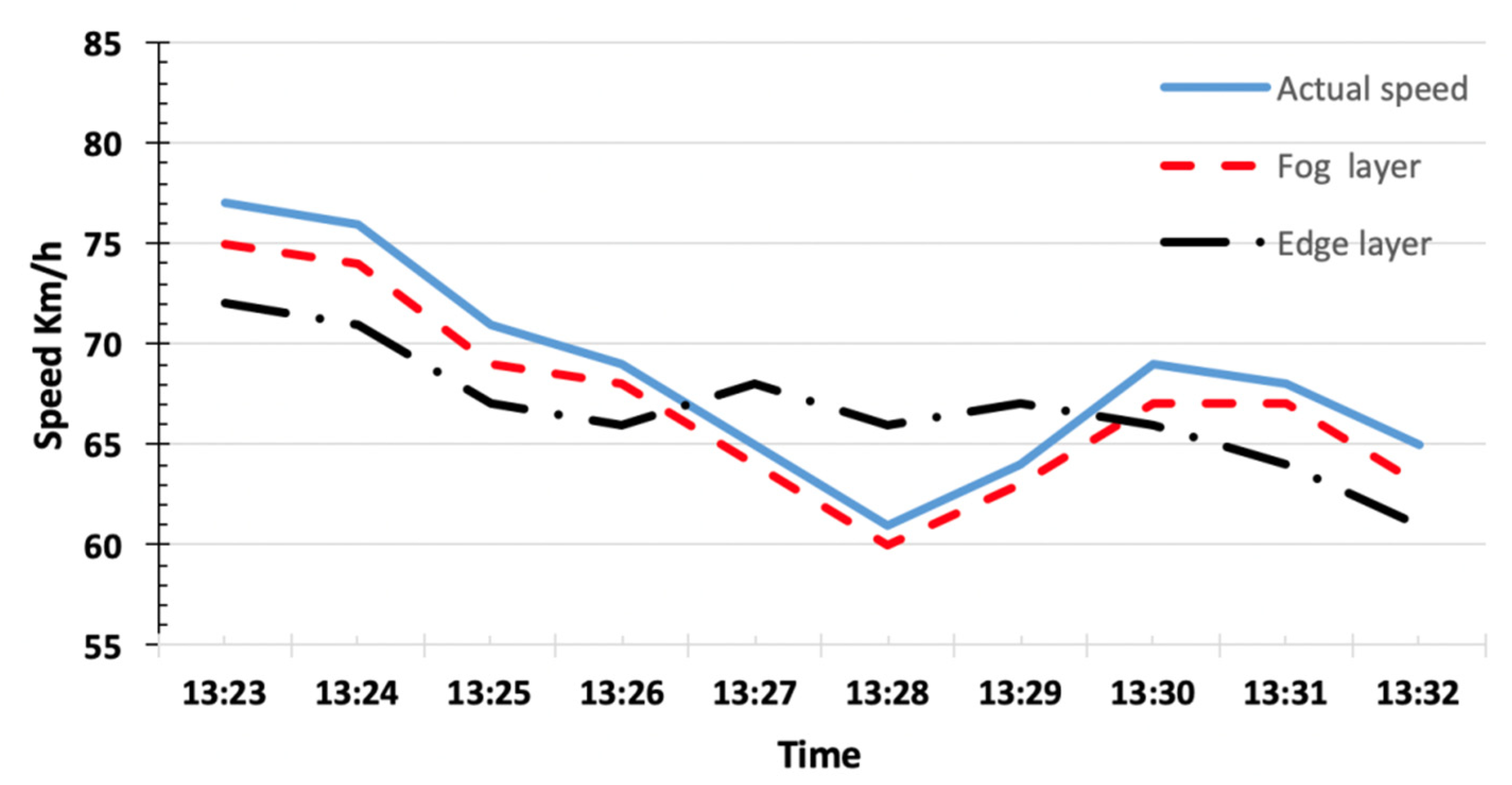
| Smartphone | RMSE without Fog Layers | RMSE with Fog Layers |
|---|---|---|
| s1 | 2.09 | 1.54 |
| s2 | 2.79 | 1.82 |
| s3 | 3.06 | 2.27 |
| Average | 2.64 | 1.87 |
| Accuracy | ||
|---|---|---|
| Door | without Fog Layer | with Fog Layer |
| Front left | 95% | 98% |
| Front right | 94% | 97% |
| Rear left | 93% | 98% |
| Rear right | 94% | 94% |
| Average | 94% | 97% |
| Correct Detection | Incorrect Detection | Accuracy | ||||
|---|---|---|---|---|---|---|
| Door | without Fog Layer | with Fog Layer | without Fog Layer | with Fog Layer | without Fog Layer | with Fog Layer |
| Front left | 47 | 49 | 3 | 1 | 94% | 98% |
| Front right | 48 | 50 | 2 | 0 | 96% | 100% |
| Rear left | 47 | 49 | 3 | 1 | 94% | 98% |
| Rear right | 48 | 50 | 2 | 0 | 96% | 100% |
| Average | 95% | 99% | ||||
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Daraghmi, Y.-A.; Helou, M.A.; Daraghmi, E.-Y.; Abu-ulbeh, W. IoT-Based System for Improving Vehicular Safety by Continuous Traffic Violation Monitoring. Future Internet 2022, 14, 319. https://doi.org/10.3390/fi14110319
Daraghmi Y-A, Helou MA, Daraghmi E-Y, Abu-ulbeh W. IoT-Based System for Improving Vehicular Safety by Continuous Traffic Violation Monitoring. Future Internet. 2022; 14(11):319. https://doi.org/10.3390/fi14110319
Chicago/Turabian StyleDaraghmi, Yousef-Awwad, Mamoun Abu Helou, Eman-Yasser Daraghmi, and Waheeb Abu-ulbeh. 2022. "IoT-Based System for Improving Vehicular Safety by Continuous Traffic Violation Monitoring" Future Internet 14, no. 11: 319. https://doi.org/10.3390/fi14110319
APA StyleDaraghmi, Y.-A., Helou, M. A., Daraghmi, E.-Y., & Abu-ulbeh, W. (2022). IoT-Based System for Improving Vehicular Safety by Continuous Traffic Violation Monitoring. Future Internet, 14(11), 319. https://doi.org/10.3390/fi14110319








