Abstract
We study the problem of color-avoiding and color-favored percolation in a network, i.e., the problem of finding a path that avoids a certain number of colors, associated with vulnerabilities of nodes or links, or is attracted by them. We investigate here regular (mainly directed) lattices with a fractions of links removed (hence the term “diluted”). We show that this problem can be formulated as a self-organized critical problem, in which the asymptotic phase space can be obtained in one simulation. The method is particularly effective for certain “convex” formulations, but can be extended to arbitrary problems using multi-bit coding. We obtain the phase diagram for some problem related to color-avoiding percolation on directed models. We also show that the interference among colors induces a paradoxical effect in which color-favored percolation is permitted where standard percolation for a single color is impossible.
1. Introduction
Percolation theory concerns the flow and the diffusion of some quantity on lattices or networks, for instance a disease on a human network or a message in a communication one [1,2,3]. It has many applications in the Internet science [4], for instance in the problem of robustness under attack [5], or the resilience after a random failure of nodes and/or links [6]. Classical percolation theory studies the penetration of a scalar quantity on a lattice, but it may be extended to more complex situations [7].
Percolation models have been also widely used to model the spreading of a disease [8]. In such models, nodes correspond to individuals that can be in several states. The simplest situation is with two states, susceptible (healthy) and infectious (ill). In this model infectious individuals recover after some time and become susceptible again (susceptible-infectious-susceptible or SIS model). Alternatively, one can introduce a recovered (or dead) state, which does not spread the disease nor can be infected again (susceptible-infectious-recovered or SIR model), many other possibilities exists [9,10,11]. Links between nodes represent contacts capable of transmitting the disease among individuals: a susceptible individual connected to an infectious one can became infected with a certain probability. The percolation transition represents the outbreak of an epidemic. Similar approaches can be used to model the propagation of computer viruses [12,13].
In many real-world networks, one can identify different classes of nodes that share the same vulnerabilities. For example, one can classify Internet routers that run different software versions in separate classes. Routers that are vulnerable to a certain bug may simultaneously fail and suddenly isolate parts of the network.
In communication networks, vertices can be associated with servers controlled by different companies. Some of them could be interested in eavesdropping information that passes through their servers, which therefore must be avoided for a secure communication. Even if all the companies are dangerous, a secure communication between the source and the receiver can be achieved by splitting messages in pieces by secret-sharing, and sending them through multiple paths, each one avoiding one of the vulnerable classes of nodes.
The color-avoiding percolation (CAP) theory is a recent generalization of the percolation theory, useful to treat these problems [14,15,16,17]. Every node of the network is marked with a one or more colors, associated with the possible vulnerabilities. The goal of CAP is to find whether one or more paths exist between couples of nodes avoiding one or more colors.
Each color can be associated with a layer in a multi-graph, so that the problem of color-avoidance is that of deciding is there exists a path that avoids all nodes or links that are “occupied” in some of the layers.
On the other side, one could profit of nodes that act as gateways towards different companies or alternative networks, seen as connections among layers, and so that in case of failure of one layer they could route the traffic to another one. Associating colors to layers, one could consider the problem of color-favored percolation (CFP), i.e., percolation with the possibility of passing from one layer to another in case of co-occupation. In principle, the two problems could be considered to be dual, by reverting the interpretation of occupation/vacancy of a node for a given color.
In this paper, we show how CAP/CFP problems on direct lattices can be mapped into a self-organized critical (SOC) problem. We study the critical properties of CAP in a direct lattice using different SOC methods, in particular with the fragment method [18].
We also show that the interference among colors in color-favored percolation allows the presence of a percolating cluster that “jumps” among layers where the percolation of a single color is impossible.
We shall deal here with regular lattices with dilution, i.e., with a fraction of links removed. We shall show that the results of simulations on such diluted lattices are very similar to that obtained on random networks, with the same average connectivity.
2. Percolation and Directed Percolation
Let us recall some definitions. We denote by the state of site in position i () at time t (), where one means wet or infected and zero dry or healthy. The index i identifies a site in a given network, connected to other sites j as specified by the adjacency matrix a: if there is a link from site j to site i and zero otherwise. We denote by the (input) connectivity of site i. Let us suppose for the moment that the lattice has constant connectivity k, and take the simplest case , with each site connected to its neighboring two sites and .
In classical percolation, the evolution of the state of the whole system is given by the parallel application of the rule
where is a random number uniformly distributed in the interval , ∨ is the OR operation, ∧ the AND one (equivalent to the multiplication) and is the truth function which takes the value one if · is true, and zero otherwise.
Equation (1) essentially says that if a site is wet, it stays wet, and that a dry site can become wet with probability p if at least one of neighbors is so ( gives the probability that the “pore” is open).
The connected wet sites form a percolation cluster. When the probability p goes beyond a critical value , a giant percolation cluster appears, spanning the systems, while small isolated clusters are still present. This is the percolation transition.
For modeling a disease spreading, one needs a modification, since the infection is a random event that can occur at every time step, so we modify Equation (1) as
where now is independently extracted for each site and each time step. In the language of disease spreading, it is an SIR (Susceptible-Infected-Recovered) model. Since in this and the following cases the “properties” of the lattice (the random numbers) are changing in time, they are also denoted “directed” percolation models [19] (time is the “directed” direction). A given set of random numbers is also called a “realization” of the disorder in the lattice.
Finally, as happens in some disease and in many computer cases, the “ineffectiveness” or misbehaving can be only transient, so after some time a node returns to the initial state, i.e., a SIS (Susceptible-Infected-Susceptible) model. This has the following implementation,
We shall deal here essentially with similar SIS models. They can be generalized, for instance, one can have an infection probability that increases with the number of infected neighbors, or even cases in which there is an interference effect among them, such as in the Domany–Kinzel (DK) model [20,21],
where now the probabilities , (number of ones in the neighborhood) define the model. In the example of Equation (3), ; .
In general, one assumes , so that the configuration becomes an absorbing state [22]. In the DK model, one defines and (Figure 1). The order parameter is the asymptotic “density” of active (non-zero) () sites, where
which is zero below and greater than zero above.

Figure 1.
The phase diagram of the DK model, marks the critical line separating the active and inactive (or absorbing) phase, marks the “chaotic” phase near the corner . The simplest mean-field approximation gives independently of q.
Let us introduce some useful terms. We refer to the progress of the percolation process with the term “infection” and to the region of phase space where in the long-time limit there is a finite probability of survival for the percolation process as the “active” region (), see Figure 1.
One can show that the standard site (directed) percolation corresponds to the line and that the bond (directed) percolation corresponds to the curve , but other interesting behaviors occurs in the phase space, in particular near the corner , (chaotic phase, Figure 1) that corresponds to a disruptive interference for which percolation can happen more easily if there is just one “infected” neighbors than if there are two [23,24].
Other extensions are possible, for instance the infection process may depend on the perception of the risk of being infected [25], which has application to computer networks [26].
3. Self-organized Criticality and the Fragment Method
In systems showing a continuous phase transition, like the percolation ones, order parameters such as the asymptotic density of active sites show a power-law behavior in the vicinity of the critical value :
which is a mark of the self-similar (scale-free) character of the transition.
While in “standard” critical systems this power-law behavior can be observed only via a fine triggering of parameters, the so-called auto-critical systems self-organizes into a critical state, which is therefore denoted as “self-organized criticality”, to underline their ability to “go freely” to the critical point.
Known examples of auto-critical systems have been used for modeling earthquakes [27] and evolution [28], and the invasion percolation model [29].
Some classic percolation problems can be reformulated as SOC system [30], and the evolution of certain quantities can be used to obtain information on the criticality of the systems, such as the critical values of their control parameters.
We shall illustrate this idea for the simple directed site percolation problem with . Let us introduce the quantity , which is the minimum value of p for which the giant percolation cluster includes site i at time t. The quantity can therefore be written as , and Equation (3) as
The expression can be rewritten as and is equivalent to . Equation (5) becomes
We can therefore extract the evolution rule for the :
which has a sort of magic: automatically (or self-critically) the ’s evolve so that all of them are above the critical value , for the given lattice and the set of random number used, since, by definition, the critical percolation probability is the smallest value of p for which there is a giant percolation cluster, spanning the whole system.
Thus, can be approximated by
This estimation is just an approximation, since one should consider the thermodynamic () limit. Moreover, the previous result depends on the realization of the disorder, i.e., the set of random numbers used for the simulation, and one should average over different realizations. In practice, the variance of the critical values of obtained in different realizations always drops to zero when increasing the system size, showing the presence of strong self-averaging in these systems [31].
This method is powerful and elegant, but it can be used only if the rule can be expressed using the AND and OR operation.
It is possible to think to sites as segments initially marking all values of p, from zero to one. Since site i can be wet only for , the associated segment can be painted with white (dry) from zero to , and black (wet) above it. At beginning, all segments are black, meaning that initially all are wet.
The AND operation is similar to taking the intersection of the black parts of the segments, and the OR to the union of them. Since these operations keep the black part contiguous, one has only to keep track of the lower boundary, which is exactly [18].
Clearly, if the rule includes also other operations like NOT or XOR, the black part of the segment is no more compact.
We can however approximate the evolution of a system by iterating segments (now called fragments) sampled at many values of p, using a multi-bit technique. In this way we can compute the parallel evolution of the system for many values of p over the random field determined by the random numbers , as shown in Ref. [18] (the fragment method).
This method can be applied to any system that can be described as a probabilistic cellular automaton (PCA). In a network we can describe the evolution of the states of the nodes with the local evolution rule
in which time t is a discrete variable, and f is a function of the set of states of the nodes connected to node i and of the set of random numbers confronted with the control parameters.
The important aspect of this procedure is that the evolution of the fragments is independent of the values of the control parameter p. The parameter is reintroduced in the problem only in the final step of the procedure, to pass from the fragment configuration to the phase-space configuration.
The evolution of the fragments can be seen as the evolution in parallel of different copies of the original system over the same disordered field (the random numbers). The different values of the control parameter correspond to copies of the system sharing the same initial configuration and the same set of random numbers. The bits of the multi-bit representation of fragments are the values of the variables s for each of the values of the control parameter. The percolation cluster for those systems with control parameter less than the critical value is finite (does not reach a large time), so that what happens is that fragments self-organize so that (for large enough systems) they are zero for and different from zero above. By inspecting the fragments, one can get an approximate value of .
One can also consider a probabilistic system characterized by m control parameters , with . In this case, the fragment method consists of assigning a fragment in m dimensions to every node. The fragments in m dimensions are defined as subsets of m-dimensional unit hypercube. A fragment in 2 dimensions, for example, is a subset of the unit square .
4. Color-Avoiding Percolation
The idea of color-avoiding percolation is that of assigning one or more colors (exclusive or co-present) to sites and/or bonds, and searching for a path that avoids them.
Site and Bond Color-Avoiding Percolation
Let us assign a color to each vertex i of a network. The quantity C denotes the total number of colors. Assuming that the sets of nodes with a certain color are disjoint, we can define the probabilities that a node has the color c, such that .
There are two possibilities:
- Independent colors: nodes can have at the same time more than one vulnerability/color;
- Exclusive colors: every node can assume only one color (cases studied in Refs. [14,15,16]).
We assume that nodes with the same color fail together and that those with different colors unlikely fail at the same time. Some colors can be considered trusted, and it is not necessary to avoid them for sending, receiving or transmitting some information.
We then define a pair of nodes as color-avoiding connected (CAC) if there are paths between them avoiding nodes carrying untrusted colors, with each path avoiding a different color (the same path can be used to avoid more than one color).
We can also define the color-avoiding giant cluster (CAGC) as the maximal set of nodes that are mutually CAC, i.e., the largest set of nodes connected to each other and such that any pair of vertices belonging to the set is CAC. A method to extract this set from the network can be found in Ref. [14].
As with site color-avoiding percolation, two nodes can be defined as pair CAC if they are connected through paths that avoid edges of a certain color, thus defining a bond CAP problem.
5. Applications
Simulations have been made on lattices with N sites in their directed formulation, i.e., with random variables renewed at each time step. A site i is connected to k other sites.
Basic results obtained by means of the SOC method are reported in Ref. [17].
Let us report first the most important results on bond CAP with exclusive colors. We consider a network in which edges are colored with one of two colors, for example red (r) and blue (b). We also considered a dilution of the network with the parameter , the probability that an edge is not removed from the network. The local evolution rule can be written as
where the states and are one if the site i is not red (resp. not blue). They evolve at the same time with the same random variables and , associated with the edges connecting node j to node i. The dilution parameter is confronted with in the first truth function of the two equations to determine whether the connection is removed or not, while p is the probability that a node is red (otherwise it is blue), the control parameter to be compared with .
In this case, the product (AND) between the two states and is of particular interest. Indeed, the product can be equal to 1 only if the node i is reached through at least two paths, one that avoids the red edges, and one avoiding the blue ones. Since each link carries one of the two colors, the two paths have no links in common.
Imposing as initial condition that the states and are equal to 1 for all the nodes, after a sufficient amount of time the product will be non-zero only for a fraction of the nodes of the network that can be interpreted as elements of the CAGC (Figure 2).
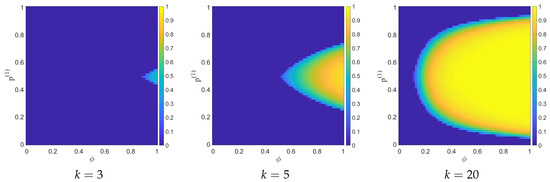
Figure 2.
Phase planes of the bond CAP for two exclusive colors (denoted color 1 and 2). assigned to sites with probability and and different dilutions (different connectivities).
We have studied the value that assumes this product in the parameter space, as shown in Figure 2. The phase planes were in this case obtained with a single simulation of the evolution of the fragments in a lattice with , at the asymptotic time , and varying the connectivity k of the nodes.
If the connectivity k is lower than 3, it is not possible to find nodes such that at large times, regardless of the values of the control parameters. Instead, for there are certain values of and for which undergoes a phase transition and passes from 0 to a non-null-value. Increasing the value of k, the region in the graph in which increases its size, and for example with , as shown in Figure 2, it includes the majority of the phase plane.
These figures are very similar to those reported in Ref. [15], obtained using an Erdős–Rényi network, showing that indeed in these cases the relevant parameter is the average connectivity.
The Equation (7) can be generalized to describe the evolution of networks with a generic number of exclusive colors C. In this case, it is useful to define the random variables
where is the probability of having color c () and .
Considering a random variable r, associated with and edge connecting two nodes, and a color c, the variable is equal to 1 with probability and equal to 0 with probability , thus allowing us to determine if the edge is colored with color i, or another color.
In addition, if for a certain value of r, i.e., the edge has the color c, then for every other color , hence the edge cannot have two different colors at the same time.
Therefore, for a generic network with C exclusive colors, and some color c to be avoided, the bond color-avoiding percolation can be studied with the following local evolution rule
where
is the negation of .
As for the case of the bond CAP with two exclusive colors, the random variable is confronted with the dilution parameter to determine whether the connection between node i and j is removed or not, while determines the color of the edge. We can consider again the product of the states associated with all the colors c to be avoided, which is equal to one only if node i can be reached avoiding every untrusted color, and the fraction of nodes for which this product is equal to one, denoted as
Imposing as initial condition for all nodes and all colors, the asymptotic value can be interpreted as the relative size of the CAGC.
Using Equation (9), we studied the bond CAP in the case of three exclusive colors, and obtained the phase planes shown in Figure 3 and Figure 4. The phase planes were obtained with a single simulation of the evolution of the fragments in a lattice with N = 10,000, at the asymptotic time t = 100,000.

Figure 3.
Phase planes of the bond CAP for three exclusive colors, in networks with average connectivity , at different values of the dilution parameter .
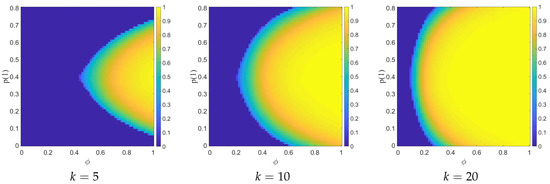
Figure 4.
Phase planes of the bond CAP for three exclusive colors, with one trusted color with fixed probability , varying the average connectivity k of the network.
For the phase planes shown in Figure 3 we considered the case in which the tree colors () are untrusted, and we studied the values of in the parameter space, that can be represented as the set of allowed values of the color probabilities and such that , and (the probability for the third color, , is fixed given the values of and since ), in networks with average connectivity , at different values of the dilution parameter .
As it can be seen, near the three vertices of the “triangle” of the allowed values of and , that corresponds to the situations in which one of the three colors prevails in the network and is hard to avoid, and the other two are less present, as for example for , , while .
Far from the vertices, the system can be in the active phase with , and its size in the phase plane depends on the connectivity of the network, as it can be seen considering different values of the dilution parameter.
The size of the active phase decreases lowering the value of , and for small enough values as , if one color is nearly absent from the network and easy to avoid, as for example for , the other colors become harder to avoid, and for all the values of and .
We also studied a different problem for the phase planes, considering networks with one trusted color and two untrusted ones. In this case, colors 1 and 2 are to be avoided, while it is not necessary to avoid the third color, therefore is dependent on the product of the states associated with only the first two colors, Figure 4.
The phase planes have been obtained by fixing the value of the probability of the third color to , considering different values of the average connectivity k, and studying the value of in the parameter space of the dilution parameter and the allowed values of the color probability (that cannot be greater than 0.8, because of the presence of the third color, while the probability for the second color is fixed as ).
This phase planes are clearly similar to those in Figure 2, as the exchange symmetry of the two untrusted colors is preserved by the presence of the third color, and the smaller critical value of is still obtained for . However, while in the case of two exclusive colors it is not possible to have if one of the untrusted colors is nearly absent from the lattice, as the other untrusted one becomes impossible to avoid, even for great values of k, in the case of three exclusive colors, the presence of a trusted color can allow for or , if the connectivity k is large enough.
6. Multilayer Model
We can have an alternative view of color-avoiding percolation by mapping it onto a multilayer directed process.
Let us consider two (or more) layers, defined by an index c, , so that now the equations concerns quantities such as and random numbers . We can assume that each layer corresponds to a given color. Let us first discuss the color-favored situation, in which the percolation clusters are composed by sites carrying at least one color. Equation (4) becomes
where for color-favored percolation,
Sites with more than one color act as gateways among layers.
For color-avoiding percolation and not-exclusive colors, Equation (4) becomes
where now denotes the presence of color c and the absence of other colors at site i and time t,
where the overbar denotes the negation. For exclusive colors, is simply , since the presence of one color c implies the absence of other colors in that site.
In the following, we shall use the terminology of color-favored percolation, i.e., we shall say that the system percolates when there is activity in the phase space.
Up to now we described the situation in which colors do not interact, so that the color-avoiding percolation phase just corresponds to the absorbing () state of the standard DK model of Figure 1.
What happens when colors interfere? To reduce the number of parameters we assume that the model is symmetric among colors. For two colors () we have now that the transition probability for layer 1 is , (and symmetrically for layer 2 is ). We again assume that the empty state is absorbing, so that .
If we assume that the presence of a color is sufficient to stop percolation on that layer, we have the same model as before except for the case in which there is no color on one layer but there is one on the other: and . We are left with two free parameters: and , which express the “interference” for which a color on a layer can affect the percolation on the other layer.
We studied two cases: and , . The first case (a) is similar to site percolation, while the other (b) reminds the “disruptive interference” of the DK model.
For small enough values of nothing new happens, since in the absorbing phase the “activity” on both layers goes to zero, and in the “active” phase, the influence of the interference term is small. The only influence of is that of shifting the border of the active phase (the simplest mean-field analysis predicts that the threshold for the DK model now becomes ).
However, when is about , one can see that the phase boundary becomes more complex: an active phase appears near the corner for case (a), and this extend to the whole side for case (b).
What happens here is that the “percolation paths” jump from one layer to the other. Indeed, the value is near the site percolation threshold for the standard DK model, so that even an isolated infected site on a layer can propagate to the other layer, although is almost-immediately disappearing on the original layer due to the small values of p and q. Actually, the survival on the original layer is detrimental for percolation, as shown by the appearance of an active island near the corner in Figure 5 and Figure 6.
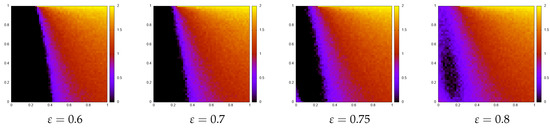
Figure 5.
Phase space of directed percolation with interacting colors, case (a). The vertical axes is p and the horizontal one is q. For moderate values of one simply has a shift of the critical line, but for a region near the corner becomes active.

Figure 6.
Phase space of directed percolation with interacting colors, case (b). The vertical axes is p and the horizontal one is q. In this case, (disruptive interference among layers) the active region tends to occupy the whole line .
What happens here is that an isolated active site can percolate on the other layer, but can also survive on the original layer, according to the values of p and q. However, as far as it survives, the two layers are decoupled, while if it immediately disappears the layer can be re-infected by the other layer (where also the survival probability depends on p and q. Therefore, we obtain the paradoxical result that in the case of enough interfering colors, color-favored percolation is favored where single-color percolation is least surviving. Clearly, the opposite happens for color-avoiding percolation.
7. Conclusions
We investigated the problem of color-avoiding and color-favored percolation on a diluted lattice [14,15,16], i.e., the problem of finding a path that avoids a certain number of colors, associated with vulnerabilities of nodes or links.
We have shown that this problem can be formulated as a self-organized critical problem, in which the asymptotic phase space can be obtained in one simulation, analogous to Invasion percolation [29].
By means of the fragment method [18], we obtained the phase diagram for many problems related to color-avoiding percolation, showing in particular that results obtained for Erdős–Rényi networks can be recovered using the dilution of the rule on regular lattices.
We investigated directed models, and we have shown that the interference among colors in color-favored percolation nor only allows the survival of a percolating cluster that continuously “jumps” among layers where the percolation of a single color is impossible, but even that increasing the survival probability of a cluster of a single color results in lowering the survival probability of the “jumping” cluster.
Author Contributions
Conceptualization, F.B. and M.G.; formal analysis, F.B.; methodology, investigation and software, M.G. and F.B.; supervision, F.B.; writing, M.G. and F.B. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Acknowledgments
The present version is an extension of Ref. [17]. In this version we added more results on color-avoiding percolation, and the part about color-favored percolation.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Broadbent, S.R.; Hammersley, J.M. Percolation processes: I. Crystals and mazes. In Mathematical Proceedings of the Cambridge Philosophical Society; Cambridge University Press: Cambridge, UK, 1957; Volume 53, pp. 629–641. [Google Scholar] [CrossRef]
- Stauffer, D. Scaling theory of percolation clusters. Phys. Rep. 1979, 54, 1–74. [Google Scholar] [CrossRef]
- Stauffer, D.; Aharony, A. Introduction to Percolation Theory; Taylor and Francis: Abingdon, UK, 1992. [Google Scholar]
- Bellini, E.; Bagnoli, F.; Massaro, E.; Rechtman, R. Percolation and Internet Science. Future Internet 2019, 11, 35. [Google Scholar] [CrossRef] [Green Version]
- Albert, R.; Jeong, H.; Barabási, A.L. Error and attack tolerance of complex networks. Nature 2000, 406, 378–382. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Callaway, D.S.; Newman, M.E.; Strogatz, S.H.; Watts, D.J. Network robustness and fragility: Percolation on random graphs. Phys. Rev. Lett. 2000, 85, 5468. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Newman, M.E.; Watts, D.J. Scaling and percolation in the small-world network model. Phys. Rev. E 1999, 60, 7332. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Cardy, J.L.; Grassberger, P. Epidemic models and percolation. J. Phys. Math. Gen. 1985, 18, L267. [Google Scholar] [CrossRef]
- Kermack, W.O.; McKendrick, A.G. A contribution to the mathematical theory of epidemics. Proc. R. Soc. Lond. 1927, 115, 700–721. [Google Scholar] [CrossRef] [Green Version]
- Brauer, F.; Castillo-Chavez, C.; Castillo-Chavez, C. Mathematical Models in Population Biology and Epidemiology; Springer: Berlin/Heidelberg, Germany, 2012; Volume 2. [Google Scholar] [CrossRef]
- Murray, J.D. Mathematical Biology: I. An introduction; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2007; Volume 17. [Google Scholar]
- Kephart, J.; White, S. Directed-graph epidemiological models of computer viruses; IEEE computer society symposium on research in security and privacy. In Proceedings of the IEEE Computer Society Symposium on Research in Security and Privacy, Oakland, CA, USA, 20–22 May 1991; pp. 343–359. [Google Scholar] [CrossRef]
- Pastor-Satorras, R.; Vespignani, A. Epidemic Spreading in Scale-Free Networks. Phys. Rev. Lett. 2001, 86. [Google Scholar] [CrossRef] [Green Version]
- Krause, S.M.; Danziger, M.M.; Zlatić, V. Hidden Connectivity in Networks with Vulnerable Classes of Nodes. Phys. Rev. X 2016, 6, 041022. [Google Scholar] [CrossRef] [Green Version]
- Krause, S.M.; Danziger, M.M.; Zlatić, V. Color-avoiding percolation. Phys. Rev. E 2017, 96, 022313. [Google Scholar] [CrossRef] [Green Version]
- Kadović, A.; Krause, S.M.; Caldarelli, G.; Zlatic, V. Bond and site color-avoiding percolation in scale-free networks. Phys. Rev. E 2018, 98, 062308. [Google Scholar] [CrossRef] [Green Version]
- Giusfredi, M.; Bagnoli, F. A Self-organized Criticality Method for the Study of Color-Avoiding Percolation. In Proceedings of the Internet Science: 6th International Conference (INSCI 2019), Perpignan, France, 2–5 December 2019; p. 217. [Google Scholar] [CrossRef]
- Bagnoli, F.; Palmerini, P.; Rechtman, R. Algorithmic mapping from criticality to self-organized criticality. Phys. Rev. E 1997, 55, 3970–3976. [Google Scholar] [CrossRef]
- Kinzel, W. Directed Percolation. In Percolation Structures and Processes; Deutscher, G., Zallen, R., Adler, J., Eds.; Adam Hilger: Bristol, UK, 1983; Volume 5. [Google Scholar]
- Kinzel, W. Phase transitions of cellular automata. Z. für Phys. B Condens. Matter 1985, 58, 229–244. [Google Scholar] [CrossRef]
- Domany, E.; Kinzel, W. Equivalence of Cellular Automata to Ising Models and Directed Percolation. Phys. Rev. Lett. 1984, 53, 311–314. [Google Scholar] [CrossRef]
- Hinrichsen, H. Non-equilibrium critical phenomena and phase transitions into absorbing states. Adv. Phys. 2000, 49, 815–958. [Google Scholar] [CrossRef]
- Martins, M.L.; Verona de Resende, H.F.; Tsallis, C.; de Magalhes, A.C.N. Evidence for a new phase in the Domany-Kinzel cellular automaton. Phys. Rev. Lett. 1991, 66, 2045–2047. [Google Scholar] [CrossRef] [Green Version]
- Bagnoli, F.; Rechtman, R. Phase Transitions of Cellular Automata. In Probabilistic Cellular Automata: Theory, Applications and Future Perspectives; Louis, P.Y., Nardi, F.R., Eds.; Springer International Publishing: Cham, Switzerland, 2018; pp. 215–236. [Google Scholar] [CrossRef] [Green Version]
- Bagnoli, F.; Lio, P.; Sguanci, L. Risk perception in epidemic modeling. Phys. Rev. E 2007, 76, 061904. [Google Scholar] [CrossRef] [Green Version]
- Bagnoli, F.; Bellini, E.; Massaro, E. Risk Perception and Epidemics in Complex Computer Networks. In Proceedings of the 2018 IEEE Workshop on Complexity in Engineering (COMPENG), Florence, Italy, 10–12 October 2018; pp. 1–5. [Google Scholar]
- Bak, P.; Tang, C.; Wiesenfeld, K. Self-organized criticality: An explanation of the 1/f noise. Phys. Rev. Lett. 1987, 59, 381–384. [Google Scholar] [CrossRef]
- Bak, P.; Sneppen, K. Punctuated equilibrium and criticality in a simple model of evolution. Phys. Rev. Lett. 1993, 71, 4083–4086. [Google Scholar] [CrossRef]
- Wilkinson, D.; Willemsen, J.F. Invasion percolation: A new form of percolation theory. J. Phys. Math. Gen. 1983, 16, 3365–3376. [Google Scholar] [CrossRef]
- Grassberger, P.; Zhang, Y.C. Self-organized formulation of standard percolation phenomena. Phys. Stat. Mech. Its Appl. 1996, 224, 169–179. [Google Scholar] [CrossRef]
- Aharony, A.; Harris, A.B. Absence of self-averaging and universal fluctuations in random systems near critical points. Phys. Rev. Lett. 1996, 77, 3700. [Google Scholar] [CrossRef] [PubMed] [Green Version]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).