Cybersecurity and Safety Co-Engineering of Cyberphysical Systems—A Comprehensive Survey
Abstract
1. Introduction
- Conditional dependencies: Safe operations may be conditioned by cybersecurity, for example, malicious modifications of sensor data or control programs may prevent safety systems from protecting an installation in accidental conditions. Conversely, safety may be a condition for cybersecurity, for example, when unmanaged catastrophic conditions weaken the security posture of a system or an organization, and lead to opportunistic malicious acts.
- Reinforcement: Safety and cybersecurity measures can be complementary, for example, event and activity logging may be used both for attack detection and accident anticipation, as well as post-event analysis.
- Conflict: If safety and cybersecurity are considered separately for the same system, it is possible that conflicting requirements or measures may be identified, for example, a safety requirement for an automatic door shutting system, would be to leave the door open, whereas a security requirement would be to leave the door locked in case of failure.
- Security-informed safety approaches: Approaches that extend the scope of safety engineering by adapting cybersecurity-related techniques.
- Safety-informed security approaches: Approaches that extend the scope of security engineering by adapting safety-related techniques.
- Combined safety and security approaches: Combined approaches for safety and cybersecurity co-engineering.
- A comprehensive review of sixty eight methods for cybersecurity and safety co-engineering, of which nine have not been reviewed before.
- The development of a multi-attribute taxonomy of cybersecurity and safety co-engineering methods, encompassing inter alia all attributes used in previous surveys.
- A discussion on open issues, not fully addressed by existing approaches for cybersecurity and safety co-engineering, that give rise to research challenges.
2. Related Work
2.1. Previous Reviews
2.2. Methods not Included in Previous Reviews
2.2.1. Search Method
- The article must be explicitly related to a cybersecurity and safety co-engineering methodology.
- The article must not be included in previously published reviews.
2.2.2. Methods
3. Analysis
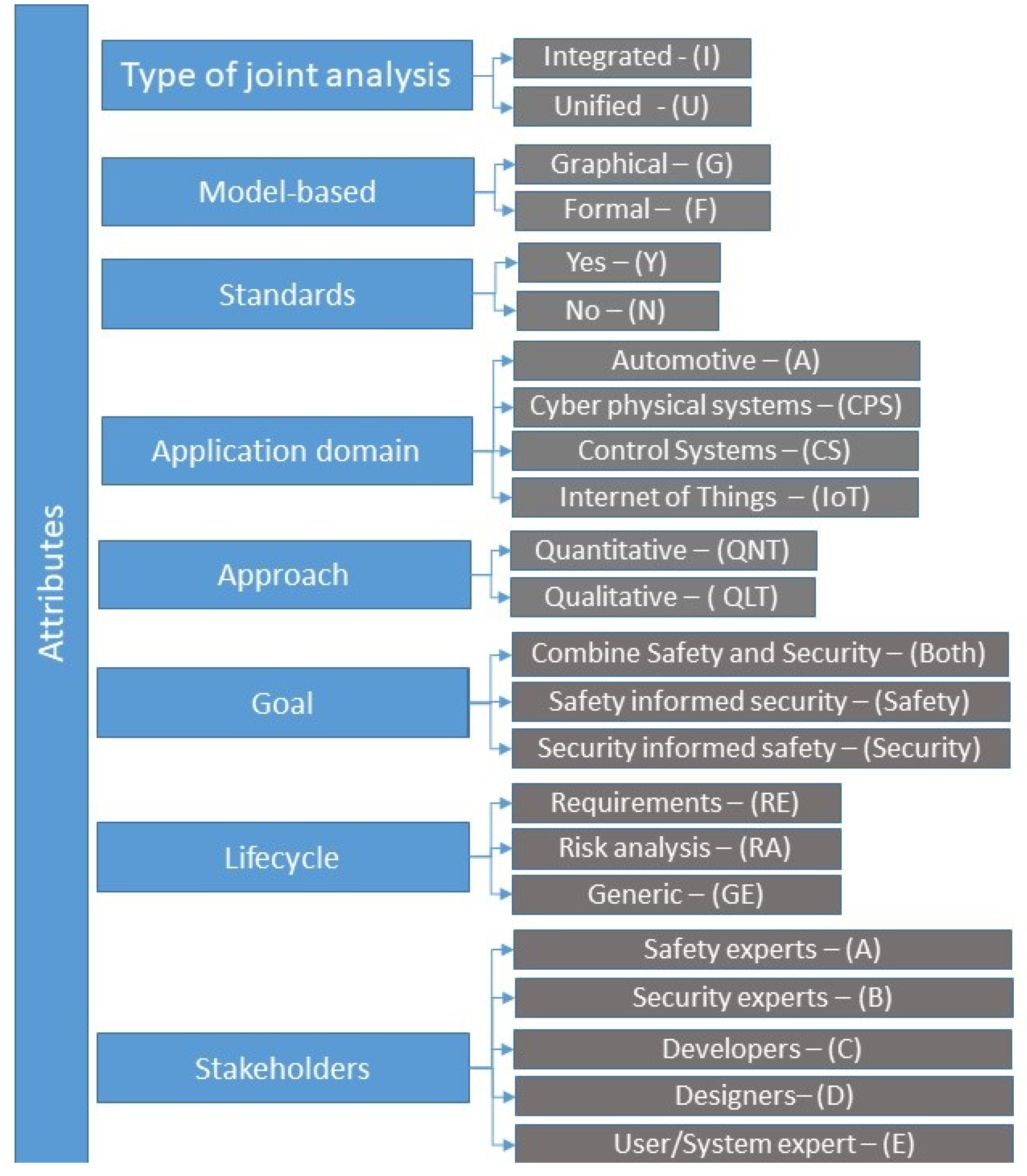
- Type of joint analysis (Type): This attribute may assume either the value “Integrated (I)” or the value “Unified (U)”. In the former case the analysis is done in two separate, yet interrelated processes, whereas in the latter the analysis is performed following a single, unified process. The attribute was originally used in References [4,7].
- Model type (Model): Describes the model that the analysis is based on. Possible values are “Graphical (G)”, “Formal (F)” and “Both graphical and formal (Both)”. In graphical methods the analysis is carried out by leveraging graphical models, whilst in formal methods the analysis is based on formulas, equations, and modelling languages. This attribute was originally used in References [4,8].
- Standards: The method is informed by and leverages safety/security standards. Possible values are “Yes (Y)” and “No (N)”. This attribute was originally used in Reference [7].
- Goal of the analysis (Goal): Describes the overall goal of the analysis and whether the approach aims to ensure safety, security, or both. Possible values are “Security”, “Safety” and “Both”. This attribute was originally used in Reference [7].
- Lifecycle: Describes in which phase of the system lifecycle the method is applied. Possible values are “Requirements (RE)”, “Risk Analysis (RA)”, “Any phase - Generic (GE)”. This attribute was originally used in Reference [4].
- Stakeholders: Describes which stakeholders are involved, either by applying it (users) or by giving input (participants); when applying the method. Possible values are “Safety experts (A)”, “Security experts (B)”, “Developers (C)”, “Designers (D)”, and “Users or system experts (E)”. This attribute was originally used in Reference [27].
- Process: Is the method supported by a systematic and structured process?
- Scalability: Does the method scale well with the size and complexity of the system under assessment?
- Creativity: Does the method include mechanisms to stimulate creativity among the stakeholders? Examples of such mechanisms are guide-words, checklists and questionnaires.
- Communication: Is the method offering features to facilitate communication between different stakeholders during its application? Examples of such features are guidelines, diagrams, schematics, and so forth.
- Conflict resolution (Conflict): Does the method facilitate the identification and study of potential conflicts between safety and security aspects?
- Software tool (Tool): Does a software tool or toolkit that supports the application of the method exist?
4. Discussion
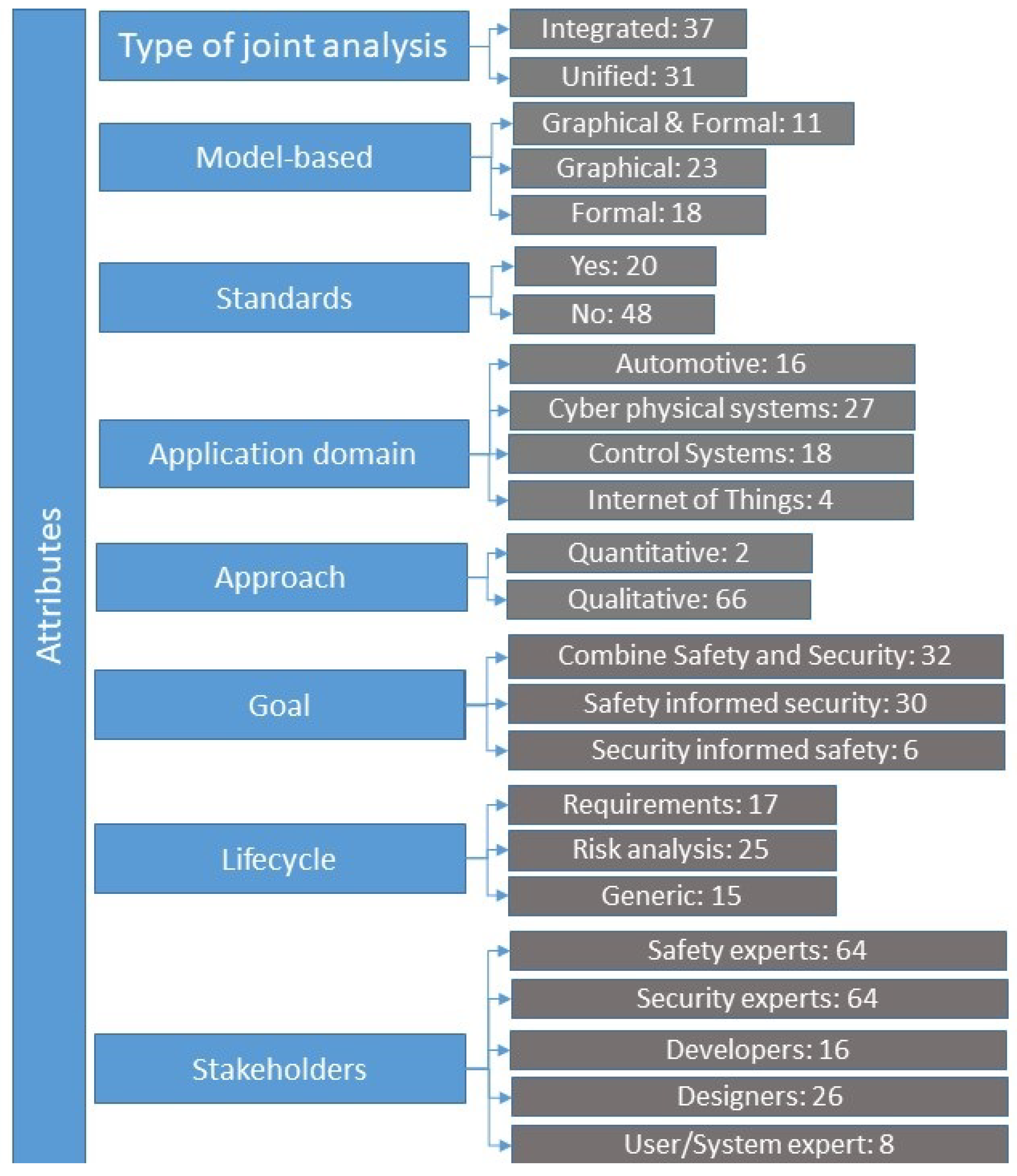
- A total of sixty eight methods have been reviewed. These span a time period of approximately 20 years, with most having been proposed after 2013, and with a steady increase in the past 5 years. This is an indication of the timeliness of the subject, which can be attributed to the increased proliferation of cyber physical systems and the integration of Information Technology with Operational Technology.
- The number of integrated methods (37) is slightly larger than that of unified ones (31). According to Reference [62], approaches that attempt to unify safety and security analysis techniques reduce the developer’s understanding of the system being analyzed and prevent a thorough analysis of either property; this leads to an incomplete analysis with subsequent safety and security risks going unobserved. On the other hand, integrated methods extract more rigorous results and facilitate the identification of potential conflicts.
- Model-based methods prevail (52 out of 68). Of these, 18 methods employ formal models, 23 methods employ graphical models, and 11 methods employ both formal and graphical models. Model-based approaches are more practical for modeling a system’s components and functionalities for existing and operational systems, by virtue of their qualitative and quantitative capabilities [4]. They are generally able to scale up to complex systems and represent different aspects related to safety and security with different viewpoints and levels of detail. On the other hand, such approaches require the analyst to have a thorough knowledge of the system; engaging all stakeholders in the process my facilitate the fulfillment of this requirement.
- Less than half of the reviewed methods (20) are informed by safety and security standards. Cyberphysical systems often operate in domains and environments highly regulated by safety and security standards. Therefore, they must be engineered to conform to these standards. It follows that safety-security co-engineering methods needs to be informed by standards. This need is more often than not satisfied if the method has been designed for use in a specific application domain. Including a validation phase in the workflow of the method, in which conformance to relevant standards is performed, is a viable alternative that may lead to the development of generic methods informed by standards. A related issue, discussed in the next section, is the need for integrated safety-security standards in several application domains.
- Most (45) of the reviewed methods have been used to analyze general CPS architectures and industrial control systems in various application domains, with the transportation domain prevailing. However, the applicability of the generic methods to different application domains is usually not demonstrated. Developing a method applicable to a broad spectrum of domains and at the same time ensuring compliance with relevant standards appears as a very challenging task.
- The vast majority of the reviewed methods (66) follow -at least partially- a qualitative approach; only two methods are fully quantitative. This is not surprising, because even though quantitative approaches prevail for safety engineering, the opposite is true for security engineering, where quantitative approaches are very rarely used, as they require the existence of a formal model describing the system under study. Attempting to analyze security, particularly security risk, has been shown quantitatively to be either infeasible or inadvisable in most real-world situations. Hence, a reasonable compromise is to opt for a combination of quantitative and qualitative approaches for safety-security co-engineering.
- The number of methods whose goal is to ensure both safety and security (32) is slightly larger than the number of those aiming to ensure safety (30), whilst only six methods have as their primary goal to ensure security. The appropriateness of each of these approaches depends largely on the system’s safety/security criticality. When the system under study is safety critical, a method whose goal is to ensure that security will not adversely influence safety is appropriate; the opposite is true when the system is security critical. But if the intention is to also have a secure system beyond the safety relevant security issues, and a safe system beyond the security relevant issues, then neither of these approaches is appropriate. In systems where both safety and security are equally important, an approach aiming to ensure both safety and security would be more appropriate.
- The number of reviewed methods that are applied to both the requirements elicitation and risk analysis phases of the system lifecycle (26) is almost equal to that of methods applied to the risk analysis phase (25), and only slightly exceeds that of methods applied to the requirements elicitation phase (17); only fifteen methods are frameworks, hence applicable to any phase of the lifecycle. This nearly uniform distribution reflects the emphasis given into co-engineering safety and security as early as possible in the development lifecycle, while allowing for revisiting the results of the analysis when the system under study has been developed or is even operational.
- The application of most of the reviewed methods involves safety and security experts; only few methods require the engagement of developers, designers and systems users. It is important to note that stakeholders, particularly designers and users, may engage with the analysis in two distinct but complementary ways: they provide input to the analysis in the form of domain expert knowledge, and they are the targets of the process of communicating the results; both are equally important. Acknowledging the fact that complex issues such as those of safety and security cannot be effectively analysed by the corresponding experts, it follows that successful methods will seek to involve engaged stakeholders.
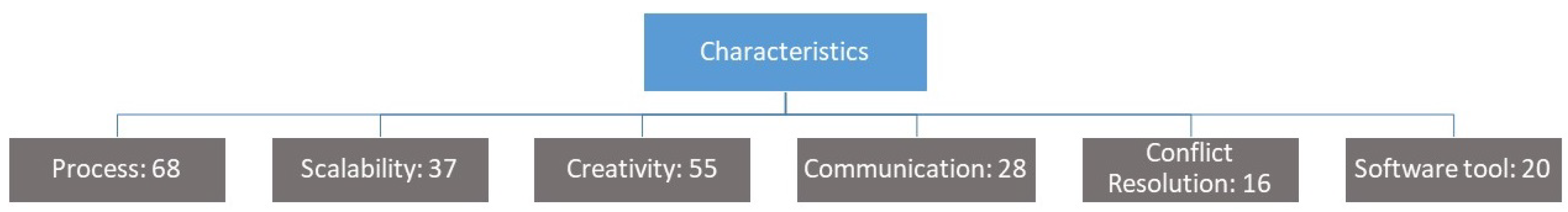
- Scalability issues have been discussed in the vast majority (61) of the papers proposing methods, in 24 of which these issues have only briefly been considered. Thirty seven methods are scalable, whereas 7 do not scale well. It should be noted that scalability refers to both the ability of the method to handle complex systems and to the level of abstraction at which the system under study is represented. The two are correlated, as high level abstraction allows for more complex systems to be analyzed. The challenge, therefore, is to develop methods that can strike an appropriate balance between those two aspects of scalability, so that the analysis results in an appropriate and practically useful level of detail.
- The majority (55) of the reviewed methods provide mechanisms to stimulate creativity among the analysts and other relevant stakeholders. As many methods rely, at least to some extent, on scenario development, creativity is an important characteristic. This is even more so when the application of the method calls for a multi-disciplinary, multi-stakeholder team.
- Less than half (28) of the reviewed methods include techniques to communicate their results to the relevant stakeholders. Another 28 methods only briefly address the issue, whilst 10 methods do not address it at all. As already implied above, this characteristic is intertwined with the involvement of stakeholders attribute.
- All methods are process-based; the structure and the steps of the process do vary, however. As pointed out in the sequel, developing a methodology to encompass different process structures is still a challenge.
- The majority (49) of the reviewed methods do not address the conflict resolution issue. Sixteen methods do address it, and a further 3 address it only partially. The implications of this central issue is elaborated upon in the sequel.
- The majority (41) of the reviewed methods are not supported by any software tool or toolkit. Only 20 methods are fully supported, and another 7 are partially supported by such tools. This has been a rather surprising finding, as the purpose of a safety-security co-engineering method is to be applied in real-world application scenarios. The complexity of such methods requires software support for their usage.
- Resolving conflicting safety/security results: The problem of conflicting results when studying safety and security jointly has been known for some time. There are two approaches to address this problem: either allow conflicting results to be derived and then resolve these conflicts, or avoid the occurrence of such conflicts by design. Unified safety and security co-engineering methods tend to generate less conflicts than integrated methods do. However, integrated methods tend to allow more comprehensive analyses of both domains. Therefore, integrated methods that would by design prevent the occurrence of conflicting results would address this issue effectively. This could perhaps be achieved if goal oriented integrated methods were developed. Further, the analysis is best performed in the early stages (requirements elicitation phase), as this makes the problem of conflict resolution much easier to solve, and leads to the development of safe-and-secure CPSs by design.
- Standard methodology: Despite the sizable extent of the literature on safety and security co-engineering methods, a generic, application-domain-independent methodology, instances of which would be existing methods and those to be developed in the future, is yet to be developed. An example of such a methodology in the security domain is the risk analysis methodology defined in the ISO 27005 standard.
- Validation: Not many of the reviewed papers include information on the validation/evaluation of the method they propose. More research is needed to evaluate the correctness, completeness, effectiveness, efficiency, scalability and so forth, of proposed methods, in a manner that will facilitate comparative assessments.
- Safety and security standards: Some standards addressing safety and security for industrial control systems exist. Examples of such standards are ISA99/IEC 6443, IEC 62645, IEC TR63609, ISO 26262 to name a few; cross-references with other standards (e.g., IEC 61508) also exist. However, the applicability of such standards to effectively address both safety and security, particularly in an industry 4.0 context, is still to be firmly established. Hence, a need for revisiting existing standards with an eye towards facilitating their use in industry, by means of reducing ambiguity, arises. Additionally, the adoption of standards specific for industry sectors, along the lines of the practice followed in the nuclear plant domain will guide the development of safe-and-secure by design industrial control systems.
- Application domains: As noted before, the transportation domain prevails among application domains addressed by the reviewed methods. Notwithstanding the fact that several methods have been claimed to have been designed to be applicable to any domain, their applicability has not been demonstrated. As several emerging application domains are both safety and security critical (e.g., autonomous vessels, drones), the development of methods addressing specifically systems in such domains remains an issue.
- Dynamic character of CPS: CPSs are dynamic by nature. Methods able to model and cope with this characteristic of CPSs are yet to be developed. Existing work on dynamic security and dynamic safety risk assessment can be leveraged to this end.
- Model type: Most of the safety analysis approaches are based on formal models. Security techniques on the other hand tend to focus on qualitative analysis. Therefore, an approach able to handle the complexity of CPS by leveraging both graphical models and systematic perspectives would allow the consolidation of advantages of both worlds.
- Holistic approach: The human factor in relation with CPSs is often overlooked. In fact, CPSs, particularly safety/security critical ones need to be considered and studied as socio-technical systems. This calls for a holistic approach towards safety and security co-engineering, that would encompass the whole ecosystem into which the CPS under study is expected to operate, and would involve all the relevant stakeholders in the process. To this end, future methods should enjoy previously mentioned attributes such as scalability, communication, and model type, in order to facilitate the analysis of CPSs when both technical and human aspects are considered. Particularly, such methods should be able to handle the complexity (scalability) derived from the human-machine interaction; communicate the results by providing reports and leveraging software tools (communication); and provide graphical models of the system under study (model type) to facilitate the analysis and the validation of the results.
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Piètre-Cambacédès, L.; Bouissou, M. Modeling safety and security interdependencies with BDMP (Boolean logic Driven Markov Processes). In Proceedings of the 2010 IEEE International Conference on Systems, Man and Cybernetics, Istanbul, Turkey, 10–13 October 2010; pp. 2852–2861. [Google Scholar]
- Paul, S.; Rioux, L. Over 20 Years of Research into Cybersecurity and Safety Engineering: A Short Bibliography; WIT Press: Ashurst Lodge, UK, 2015; pp. 335–349. [Google Scholar]
- Piètre-Cambacédès, L.; Bouissou, M. Cross-fertilization between safety and security engineering. Reliab. Eng. Syst. Saf. 2013, 110, 110–126. [Google Scholar] [CrossRef]
- Kriaa, S.; Pietre-Cambacedes, L.; Bouissou, M.; Halgand, Y. A survey of approaches combining safety and security for industrial control systems. Reliab. Eng. Syst. Saf. 2015, 139, 156–178. [Google Scholar] [CrossRef]
- Chockalingam, S.; Hadžiosmanović, D.; Pieters, W.; Teixeira, A.; van Gelder, P. Integrated safety and security risk assessment methods: a survey of key characteristics and applications. In Proceedings of the International Conference on Critical Information Infrastructures Security, Paris, France, 10–12 October 2016; pp. 50–62. [Google Scholar]
- Abulamddi, M.F. A Survey on techniques requirements for integrating safety and security engineering for cyber-physical systems. J. Comput. Commun. 2017, 5, 94–100. [Google Scholar] [CrossRef][Green Version]
- Lisova, E.; Sljivo, I.; Causevic, A. Safety and Security Co-Analyses: A Systematic Literature Review. IEEE Syst. J. 2018, 13, 2189–2200. [Google Scholar] [CrossRef]
- Lyu, X.; Ding, Y.; Yang, S.H. Safety and security risk assessment in cyber-physical systems. IET Cyber-Physical Syst. Theory Appl. 2019, 4, 221–232. [Google Scholar] [CrossRef]
- Hart, C. Doing a Literature Review: Releasing the Research Imagination; SAGE Publications Ltd.: Southend Oaks, CA, USA, 2018. [Google Scholar]
- Cui, J.; Sabaliauskaite, G. US 2: An Unified Safety and Security Analysis Method for Autonomous Vehicles. In Proceedings of the Future of Information and Communication Conference, Singapore, 5–6 April 2018; pp. 600–611. [Google Scholar]
- Sabaliauskaite, G.; Liew, L.S.; Cui, J. Integrating autonomous vehicle safety and security analysis using stpa method and the six-step model. Int. J. Adv. Secur. 2018, 11, 160–169. [Google Scholar]
- Sabaliauskaite, G.; Adepu, S.; Mathur, A. A six-step model for safety and security analysis of cyber-physical systems. In Proceedings of the International Conference on Critical Information Infrastructures Security, Paris, France, 10–12 October 2016; pp. 189–200. [Google Scholar]
- Leveson, N.G.; Thomas, J.P. STPA Handbook. 2018. Available online: https://psas.scripts.mit.edu/home/get_file.php?name=STPA_handbook.pdf (accessed on 18 October 2019).
- International Organization for Standardization (ISO). Road Vehicles—Functional Safety; Technical Report ISO 26262-1:2018; ISO: Geneva, Switzerland, 2018. [Google Scholar]
- SAE, J. 3061: Cybersecurity Guidebook for Cyber-Physical Vehicle Systems. 2016. Available online: https://www.sae.org/standards/content/j3061/ (accessed on 18 October 2019).
- Sabaliauskaite, G.; Mathur, A.P. Aligning Cyber-Physical System Safety and Security. 2015. Available online: http://www.2014.csdm-asia.net/IMG/pdf/Aligning_Cyber-Physical_System_Safety_and_Security-2.pdf (accessed on 20 November 2019).
- Cui, J.; Sabaliauskaite, G. On the alignment of safety and security for autonomous vehicles. In Proceedings of the CYBER 2017: The Second International Conference on Cyber-Technologies and Cyber-Systems, IARIA CYBER, Barcelona, Spain, 12–16 November 2017. [Google Scholar]
- International Society of Automation—ISA. Technical report, ANSI/ISA 84.00.01-2004, Application of Safety Instrumented Systems for the Process Industries; ISA: Isa, Japan, 2004. [Google Scholar]
- International Society of Automation—ISA. Technical report, ANSI/ISA-99-00-01-2007. Security for Industrial Automation and Control Systems Part 1: Terminology, Concepts, and Models; ISA: Isa, Japan, 2007. [Google Scholar]
- Asplund, F.; McDermid, J.; Oates, R.; Roberts, J. Rapid Integration of CPS Security and Safety. IEEE Embed. Syst. Lett. 2018, 11, 111–114. [Google Scholar] [CrossRef]
- Guzman, N.H.C.; Kufoalor, D.K.M.; Kozin, I.; Lundteigen, M.A. Combined safety and security risk analysis using the UFoI-E method: A case study of an autonomous surface vessel. In Proceedings of the 29th European Safety and Reliability Conference, Hannover, Germany, 22–26 September 2019; pp. 4099–4106. [Google Scholar]
- Sabaliauskaite, G.; Liew, L.S.; Zhou, F. AVES–Automated Vehicle Safety and Security Analysis Framework. In Proceedings of the CSCS ’19: ACM Computer Science in Cars Symposium, Kaiserslautern, Germany, 8 October 2019; pp. 1–8. [Google Scholar]
- Guzman, N.H.C.; Wied, M.; Kozine, I.; Lundteigen, M.A. Conceptualizing the key features of cyber-physical systems in a multi-layered representation for safety and security analysis. Syst. Eng. 2019, 23, 189–210. [Google Scholar] [CrossRef]
- Carreras Guzman, N.H.; Mezovari, A.G. Design of IoT-based Cyber–Physical Systems: A Driverless Bulldozer Prototype. Information 2019, 10, 343. [Google Scholar] [CrossRef]
- Hayakawa, T.; Sasaki, R.; Hayashi, H.; Takahashi, Y.; Kaneko, T.; Okubo, T. Proposal and Application of Security/Safety Evaluation Method for Medical Device System that Includes IoT. In Proceedings of the 2018 VII International Conference on Network, Communication and Computing, Taipei, Taiwan, 14–16 December 2018; pp. 157–164. [Google Scholar]
- Monteuuis, J.P.; Boudguiga, A.; Zhang, J.; Labiod, H.; Servel, A.; Urien, P. Sara: Security automotive risk analysis method. In Proceedings of the 4th ACM Workshop on Cyber-Physical System, Incheon, Korea, 4 June 2018; pp. 3–14. [Google Scholar]
- Raspotnig, C.; Opdahl, A. Comparing risk identification techniques for safety and security requirements. J. Syst. Softw. 2013, 86, 1124–1151. [Google Scholar] [CrossRef]
- Raspotnig, C.; Karpati, P.; Katta, V. A combined process for elicitation and analysis of safety and security requirements. Enterprise, Business-Process and Information Systems Modeling; Springer: Berlin/Heidelberg, Germany, 2012; pp. 347–361. [Google Scholar]
- Reichenbach, F.; Endresen, J.; Chowdhury, M.M.; Rossebø, J. A pragmatic approach on combined safety and security risk analysis. In Proceedings of the 2012 IEEE 23rd International Symposium on Software Reliability Engineering Workshops, Dallas, TX, USA, 27–30 November 2012; pp. 239–244. [Google Scholar]
- Silva, N.; Lopes, R. Practical Experiences with real-world systems: Security in the World of Reliable and Safe Systems. In Proceedings of the 2013 43rd Annual IEEE/IFIP Conference on Dependable Systems and Networks Workshop (DSN-W), Budapest, Hungary, 24–27 June 2013; pp. 1–5. [Google Scholar]
- Young, W.; Leveson, N. Systems thinking for safety and security. In Proceedings of the 29th Annual Computer Security Applications Conference, New Orleans, LA, USA, 9–13 December 2013; pp. 1–8. [Google Scholar]
- Chen, Y.R.; Chen, S.J.; Hsiung, P.A.; Chou, I.H. Unified security and safety risk assessment-a case study on nuclear power plant. In Proceedings of the 2014 International Conference on Trustworthy Systems and Their Applications, Taichung, Taiwan, 9–10 June 2014; pp. 22–28. [Google Scholar]
- Ito, M. Finding threats with hazards in the concept phase of product development. European Conference on Software Process Improvement, Luxembourg, 25–27 June 2014; pp. 277–284. [Google Scholar]
- Kriaa, S.; Bouissou, M.; Colin, F.; Halgand, Y.; Pietre-Cambacedes, L. Safety and security interactions modeling using the BDMP formalism: case study of a pipeline. In Proceedings of the International Conference on Computer Safety, Reliability, and Security, SAFECOMP 2014, Florence, Italy, September 2014; pp. 326–341. [Google Scholar]
- Schmittner, C.; Gruber, T.; Puschner, P.; Schoitsch, E. Security application of failure mode and effect analysis (FMEA). In Proceedings of the International Conference on Computer Safety, Reliability, and Security, Florence, Italy, September 2014; pp. 310–325. [Google Scholar]
- Apvrille, L.; Roudier, Y. Designing safe and secure embedded and cyber-physical systems with SysML-Sec. In Proceedings of the International Conference on Model-Driven Engineering and Software Development, Angers, France, 9–11 February 2015; pp. 293–308. [Google Scholar]
- Gu, T.; Lu, M.; Li, L. Extracting interdependent requirements and resolving conflicted requirements of safety and security for industrial control systems. In Proceedings of the 2015 First International Conference on Reliability Systems Engineering (ICRSE), Beijing, China, 21–23 October 2015; pp. 1–8. [Google Scholar]
- Kriaa, S.; Bouissou, M.; Laarouchi, Y. A model based approach for SCADA safety and security joint modelling: S-Cube. In Proceedings of the 10th IET System Safety and Cyber-Security Conference 2015, Bristol, UK, 21–22 October 2015. [Google Scholar]
- Macher, G.; Höller, A.; Sporer, H.; Armengaud, E.; Kreiner, C. A combined safety-hazards and security-threat analysis method for automotive systems. In Proceedings of the International Conference on Computer Safety, Reliability, and Security, Delft, The Netherlands, 22–25 September 2014; pp. 237–250. [Google Scholar]
- Popov, P.T. Stochastic Modeling of Safety and Security of the e-Motor, an ASIL-D Device. In Computer Safety, Reliability, and Security; Koornneef, F., van Gulijk, C., Eds.; Springer International Publishing: Cham, Switzerland, 2015; pp. 385–399. [Google Scholar]
- Steiner, M.; Liggesmeyer, P. Qualitative and quantitative analysis of CFTs taking security causes into account. In Proceedings of the International Conference on Computer Safety, Reliability, and Security, Delft, The Netherlands, 22–25 September 2014; pp. 109–120. [Google Scholar]
- Wei, J.; Matsubara, Y.; Takada, H. HAZOP-Based Security Analysis for Embedded Systems: Case Study of Open Source Immobilizer Protocol Stack. In Recent Advances in Systems Safety and Security; Springer International Publishing: Cham, Switzerland, 2016; pp. 79–96. [Google Scholar]
- Islam, M.M.; Lautenbach, A.; Sandberg, C.; Olovsson, T. A risk assessment framework for automotive embedded systems. In Proceedings of the 2nd ACM International Workshop on Cyber-Physical System Security, Xi’an, China, 30 May 2016; pp. 3–14. [Google Scholar]
- Nicklas, J.P.; Mamrot, M.; Winzer, P.; Lichte, D.; Marchlewitz, S.; Wolf, K.D. Use case based approach for an integrated consideration of safety and security aspects for smart home applications. In Proceedings of the 2016 11th System of Systems Engineering Conference (SoSE), Kongsberg, Norway, 12–16 June 2016. [Google Scholar]
- Ponsard, C.; Dallons, G.; Massonet, P. Goal-oriented co-engineering of security and safety requirements in cyber-physical systems. In Proceedings of the International Conference on Computer Safety, Reliability, and Security, Trondheim, Norway, 20–23 September 2016; pp. 334–345. [Google Scholar]
- Schmittner, C.; Ma, Z.; Puschner, P. Limitation and improvement of STPA-Sec for safety and security co-analysis. In Proceedings of the International Conference on Computer Safety, Reliability, and Security, Trondheim, Norway, 20–23 September 2016; pp. 195–209. [Google Scholar]
- Troubitsyna, E. An integrated approach to deriving safety and security requirements from safety cases. In Proceedings of the 2016 IEEE 40th Annual Computer Software and Applications Conference (COMPSAC), Atlanta, GA, USA, 10–14 June 2016; pp. 614–615. [Google Scholar]
- Dürrwang, J.; Beckers, K.; Kriesten, R. A lightweight threat analysis approach intertwining safety and security for the automotive domain. In Proceedings of the International Conference on Computer Safety, Reliability, and Security, Trento, Italy, 12–15 September 2017; pp. 305–319. [Google Scholar]
- Friedberg, I.; McLaughlin, K.; Smith, P.; Laverty, D.; Sezer, S. STPA-SafeSec: Safety and security analysis for cyber-physical systems. J. Inf. Secur. Appl. 2017, 34, 183–196. [Google Scholar] [CrossRef]
- Howard, G.; Butler, M.; Colley, J.; Sassone, V. Formal analysis of safety and security requirements of critical systems supported by an extended STPA methodology. In Proceedings of the 2017 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), Paris, France, 26–28 April 2017; pp. 174–180. [Google Scholar]
- Kumar, R.; Stoelinga, M. Quantitative security and safety analysis with attack-fault trees. In Proceedings of the 2017 IEEE 18th International Symposium on High Assurance Systems Engineering (HASE), Singapore, 12–14 January 2017; pp. 25–32. [Google Scholar]
- Pereira, D.; Hirata, C.; Pagliares, R.; Nadjm-Tehrani, S. Towards combined safety and security constraints analysis. In Proceedings of the International Conference on Computer Safety, Reliability, and Security, Trento, Italy, 12–15 September 2017; pp. 70–80. [Google Scholar]
- Plósz, S.; Schmittner, C.; Varga, P. Combining safety and security analysis for industrial collaborative automation systems. In Proceedings of the International Conference on Computer Safety, Reliability, and Security, Trento, Italy, 12–15 September 2017; pp. 187–198. [Google Scholar]
- Procter, S.; Vasserman, E.Y.; Hatcliff, J. SAFE and secure: Deeply integrating security in a new hazard analysis. In Proceedings of the 12th International Conference on Availability, Reliability and Security, Reggio Calabria, Italy, 29 August–1 September 2017; p. 66. [Google Scholar]
- Sabaliauskaite, G.; Adepu, S. Integrating six-step model with information flow diagrams for comprehensive analysis of cyber-physical system safety and security. In Proceedings of the 2017 IEEE 18th International Symposium on High Assurance Systems Engineering (HASE), Singapore, 12–14 January 2017; pp. 41–48. [Google Scholar]
- Temple, W.G.; Wu, Y.; Chen, B.; Kalbarczyk, Z. Systems-theoretic likelihood and severity analysis for safety and security co-engineering. In Proceedings of the International Conference on Reliability, Safety and Security of Railway Systems, Trento, Italy, 12–15 September 2017; pp. 51–67. [Google Scholar]
- Vistbakka, I.; Troubitsyna, E.; Kuismin, T.; Latvala, T. Co-engineering safety and security in industrial control systems: a formal outlook. In Proceedings of the International Workshop on Software Engineering for Resilient Systems, Geneva, Switzerland, 4–5 September 2017; pp. 96–114. [Google Scholar]
- Stoneburner, G. Toward a unified security-safety model. Computer 2006, 39, 96–97. [Google Scholar] [CrossRef]
- Aven, T. A unified framework for risk and vulnerability analysis covering both safety and security. Reliab. Eng. Syst. Saf. 2007, 92, 745–754. [Google Scholar] [CrossRef]
- Derock, A.; Hebrard, P.; Vallée, F. Convergence of the Latest Standards Addressing Safety and Security for Information Technology. 2010. Available online: https://hal.archives-ouvertes.fr/hal-02267717/ (accessed on 15 October 2019).
- Woskowski, C. A pragmatic approach towards safe and secure medical device integration. In Proceedings of the International Conference on Computer Safety, Reliability, and Security, Florence, Italy, 10–12 September 2014; pp. 342–353. [Google Scholar]
- Eames, D.P.; Moffett, J. The integration of safety and security requirements. In Proceedings of the International Conference on Computer Safety, Reliability, and Security, Toulouse, France, 27–29 September 1999; pp. 468–480. [Google Scholar]
- Kornecki, A.J.; Zalewski, J. Safety and security in industrial control. In Proceedings of the Sixth Annual Workshop on Cyber Security and Information Intelligence Research, Oak Ridge, TN, USA, 21–23 April 2010; p. 77. [Google Scholar]
- Novak, T.; Gerstinger, A. Safety-and security-critical services in building automation and control systems. IEEE Trans. Ind. Electron. 2009, 57, 3614–3621. [Google Scholar] [CrossRef]
- Subramanian, N.; Zalewski, J. Assessment of safety and security of system architectures for cyberphysical systems. In Proceedings of the 2013 IEEE International Systems Conference (SysCon), Orlando, FL, USA, 15–18 April 2013; pp. 634–641. [Google Scholar]
- Fovino, I.N.; Masera, M.; De Cian, A. Integrating cyber attacks within fault trees. Reliab. Eng. Syst. Saf. 2009, 94, 1394–1402. [Google Scholar] [CrossRef]
- Bezzateev, S.; Voloshina, N.; Sankin, P. Joint safety and security analysis for complex systems. In Proceedings of the 2013 13th Conference of Open Innovations Association (FRUCT), Petrozavodsk, Russia, 22–26 April 2013; pp. 3–13. [Google Scholar]
- Kornecki, A.; Liu, M. Fault tree analysis for safety/security verification in aviation software. Electronics 2013, 2, 41–56. [Google Scholar] [CrossRef]
- Steiner, M.; Liggesmeyer, P. Combination of Safety and Security Analysis-Finding Security Problems that Threaten the Safety of a System. 2013. Available online: https://hal.archives-ouvertes.fr/hal-00848604 (accessed on 4 November 2019).
- Piètre-Cambacédès, L.; Deflesselle, Y.; Bouissou, M. Security modeling with BDMP: from theory to implementation. In Proceedings of the 2011 Conference on Network and Information Systems Security, La Rochelle, France, 18–21 May 2011. [Google Scholar]
- Kornecki, A.J.; Subramanian, N.; Zalewski, J. Studying interrelationships of safety and security for software assurance in cyber-physical systems: Approach based on bayesian belief networks. In Proceedings of the 2013 Federated Conference on Computer Science and Information Systems, Krakow, Poland, 8–11 September 2013; pp. 1393–1399. [Google Scholar]
- Sindre, G. A Look at Misuse Cases for Safety Concerns. Situational Method Engineering: Fundamentals and Experiences; Ralyté, J., Brinkkemper, S., Henderson-Sellers, B., Eds.; Springer US: Boston, MA, USA, 2007; pp. 252–266. [Google Scholar]
- Jürjens, J. Developing Safety-and Security-Critical Systems with UML; DARP Workshop: Loughborough, UK, 2003. [Google Scholar]
- Apvrille, L.; Roudier, Y. Towards the model-driven engineering of secure yet safe embedded systems. arXiv 2014, arXiv:1404.1985. Available online: https://arxiv.org/abs/1404.1985 (accessed on 8 November 2019). [CrossRef]
- Roth, M.; Liggesmeyer, P. Modeling and Analysis of Safety-Critical Cyber Physical Systems Using State/Event Fault Trees. Available online: https://hal.archives-ouvertes.fr/SAFECOMP2013-DECS/hal-00848640 (accessed on 18 October 2019).
- Brunel, J.; Chemouil, D.; Rioux, L.; Bakkali, M.; Vallée, F. A Viewpoint-Based Approach for Formal Safety & Security Assessment of System Architectures. Available online: https://hal.archives-ouvertes.fr/hal-01070960 (accessed on 22 October 2019).
- Zafar, S.; Dromey, R.G. Integrating safety and security requirements into design of an embedded system. In Proceedings of the 12th Asia-Pacific Software Engineering Conference (APSEC’05), Taipei, Taiwan, 15–17 December 2005; p. 8. [Google Scholar]
- Pieters, W.; Lukszo, Z.; Hadziosmanovic, D.; van den Berg, J. Reconciling Malicious and Accidental Risk in Cyber Security. J. Internet Serv. Inf. Secur. 2014, 4, 4–26. [Google Scholar]
- Sun, M.; Mohan, S.; Sha, L.; Gunter, C. Addressing safety and security contradictions in cyber-physical systems. In Proceedings of the 1st Workshop on Future Directions in Cyber-Physical Systems Security (CPSSW’09), Newark, NJ, USA, 22–24 July 2009. [Google Scholar]
- Simpson, A.; Woodcock, J.; Davies, J. Safety through security. In Proceedings of the Ninth International Workshop on Software Specification and Design; Available online: https://www.computer.org/csdl/proceedings-article/iwssd/1998/00667912/12OmNx4gUlw (accessed on 22 October 2019).
- Delange, J.; Pautet, L.; Feiler, P. Validating safety and security requirements for partitioned architectures. In Proceedings of the International Conference on Reliable Software Technologies, Brest, France, 8–12 June 2009; pp. 30–43. [Google Scholar]
- Young, W.; Leveson, N.G. An integrated approach to safety and security based on systems theory. Commun. ACM 2014, 57, 31–35. [Google Scholar] [CrossRef]
- Schmittner, C.; Ma, Z.; Schoitsch, E.; Gruber, T. A case study of fmvea and chassis as safety and security co-analysis method for automotive cyber-physical systems. In Proceedings of the 1st ACM Workshop on Cyber-Physical System Security, Singapore, 14 April 2015; pp. 69–80. [Google Scholar]
- Schmittner, C.; Ma, Z.; Smith, P. FMVEA for safety and security analysis of intelligent and cooperative vehicles. In Proceedings of the International Conference on Computer Safety, Reliability, and Security, Florence, Italy, 10–12 September 2014; pp. 282–288. [Google Scholar]
- Chung, L.; Nixon, B.A.; Yu, E.; Mylopoulos, J. Non-functional Requirements in Software Engineering; Springer US: Cham, Switzerland, 2012. [Google Scholar]
- Subramanian, N.; Zalewski, J. Quantitative assessment of safety and security of system architectures for cyberphysical systems using the NFR approach. IEEE Syst. J. 2014, 10, 397–409. [Google Scholar] [CrossRef]
- Winther, R.; Johnsen, O.A.; Gran, B.A. Security assessments of safety critical systems using HAZOPs. In Proceedings of the International Conference on Computer Safety, Reliability, and Security, Budapest, Hungary, 26–28 September 2001; pp. 14–24. [Google Scholar]
| Method | Type | Model | Standards | Domain | Approach | Goal | Lifecycle | Stakeholders | Scalability | Creativity | Communication | Process | Conflict | Software |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| [10] | U | F | No | A | QLT | Both | RE | A/B | Y | Y | P | Y | N | N |
| [11] | I | G | Yes | A | QLT | Both | RA/RE | A/B/D | Y | Y | Y | Y | P | N |
| [16,17] | U | G | Yes | CS | QLT | Both | RA/RE | A/B/D | Y | Y | P | Y | Y | N |
| [20] | I | N/A | No | CPS | QLT | Security | RE/RA | A/C/E | P | P | Y | Y | Y | N |
| [21] | I | G | Yes | A | QLT | Safety | RA | A/B/C/E | Y | P | Y | Y | P | N |
| [22] | I | G | No | CPS | QLT | Both | RA/RE | A/B/C/D | P | Y | Y | Y | Y | N |
| [23] | I | G | No | CPS | QLT | Both | RA | A/B/D/E | Y | Y | Y | Y | N | N |
| [25] | I | G | No | CPS | QLT | Safety | RA/RE | A/B/D | Y | Y | Y | Y | N | Y |
| [26] | I | N/A | No | CPS/A | QLT | Both | RA | A/B | N | P | N | Y | N | N |
| [28] | U | G | No | CPS | QLT | Safety | RE | A/B/C | N | Y | Y | Y | Y | N |
| [29] | I | N/A | Yes | CS | QLT/QNT | Safety | RA | A/B | P | Y | P | Y | N | N |
| [30] | U | G | Yes | CPS | QLT | Safety | RA | A/B | P | Y | P | Y | N | N |
| [31] | U | G | No | CPS | QLT | Both | RA/RE | A/B/D/E | Y | N | Y | Y | P | P |
| [32] | U | F | Yes | CPS | QLT/QNT | Both | RA | A/B | P | Y | N | Y | N | N |
| [33] | U | G | Yes | A | QLT | Both | RA | A/B | N | Y | Y | Y | N | N |
| [34] | U | F | No | CS | QLT/QNT | Both | RA/RE | A/B | P | P | P | Y | Y | Y |
| [35] | U | Both | Yes | CS | QLT | Safety | GE/RA | A/B | Y | Y | Y | Y | N | N |
| [36] | U | Both | No | A | QLT/QNT | Safety | RE | A/B/C | P | Y | Y | Y | N | Y |
| [37] | I | F | No | CS | QLT/QNT | Both | RE | A/B/D | P | P | N | Y | Y | N |
| [38] | U | F | No | CS | QLT/QNT | Both | RA | A/B/E | Y | P | P | Y | N | Y |
| [39] | U | F | Yes | A | QNT | Safety | RE | A/B | P | P | Y | Y | N | N |
| [40] | U | F | Yes | A | QNT | Safety | RA | A/B/D/E | Y | Y | Y | Y | N | N |
| [41] | U | F | Yes | CPS | QLT/QNT | Safety | RA | A/B | N | Y | N | Y | N | N |
| [42] | U | G | No | A | QLT | Safety | RA | A/B/D | N | Y | Y | Y | N | N |
| [43] | I | Both | Yes | A | QLT | Both | GE/RE/RA | A/B/C/D/E | P | Y | Y | Y | N | Y |
| [44] | I | G | No | IoT | QLT/QNT | Safety | RA | A/B/C/D | Y | Y | Y | Y | Y | N |
| [45] | U | G | Yes | A | QLT | Both | RE | A/B | N | Y | P | Y | Y | X |
| [46] | U | G | Yes | A | QLT | Safety | RA/RE | A/B/C/D | Y | Y | P | Y | N | P |
| [47] | I | G | No | CPS | QLT | Safety | RE | A/B/D | P | Y | N | Y | N | N |
| [48] | U | N/A | Yes | A | QLT | Safety | GE/RA/RE | A/B/E | Y | Y | N | Y | N | N |
| [49] | U | G | No | CPS | QLT | Both | RA | A/B/C/D | Y | Y | Y | Y | N | P |
| [50] | U | F | No | CPS | QLT/QNT | Both | RA/RE | A/B/C | Y | Y | Y | Y | N | Y |
| [51] | U | Both | No | CPS | QLT/QNT | Both | RA | A/B | Y | N | P | Y | N | Y |
| [52] | I | N/A | Yes | CPS | QLT | Both | GE/RA/RE | A/B/D | Y | Y | Y | Y | Y | P |
| [53] | U | N/A | No | CPS | QLT | Both | GE/RA | A/B/D | Y | Y | Y | Y | N | P |
| [54] | U | N/A | No | IoT | QLT | Safety | GE/RA | A/B | Y | Y | Y | Y | N | P |
| [55] | I | G | Yes | CPS | QLT | Both | RA | A/B | Y | Y | Y | Y | Y | N |
| [56] | U | G | Yes | CPS | QLT/QNT | Safety | RA | A/B | Y | Y | Y | Y | N | N |
| [57] | U | F | No | CS | QLT | Both | RE | A/B | Y | Y | Y | Y | N | P |
| [58] | U | N/A | No | N/A | QLT/QNT | Both | GE/RA | A/B | Y | N | N | Y | N | N |
| [59] | U | F | No | N/A | QLT/QNT | Both | GE/RE/RA | A/B | Y | Y | N | Y | N | N |
| [60] | U | N/A | Yes | CPS | QLT | Both | GE/RE/RA | A/B | Y | Y | P | Y | N | N |
| [61] | U | N/A | Yes | IoT | QLT | Safety | GE/RA/RE | A/B/C/D | Y | N | N | Y | N | N |
| [62] | I | N/A | No | CS | QLT | Both | GE/RA | A/B/C | N | P | P | Y | Y | N |
| [63] | I | N/A | No | CS | QLT | Safety | GE/RE | A/B/C/D | Y | Y | Y | Y | N | N |
| [64] | I | N/A | No | CS | QLT | Both | GE/RE | A/B | Y | Y | P | Y | Y | N |
| [65] | I | G | No | CS | QLT | Safety | RE/RA | A/B | Y | Y | N | Y | Y | N |
| [66] | I | Both | No | CS | QLT/QNT | Safety | RA | A/B | P | Y | N | Y | N | N |
| [67] | I | Both | No | CPS | QLT/QNT | Safety | RE | A/B | Y | Y | P | Y | N | N |
| [68] | I | Both | No | CPS | QLT/QNT | Safety | RE/RA | A/B | P | Y | Y | Y | N | Y |
| [69] | I | Both | No | CS | QLT/QNT | Safety | RA | A/B | P | Y | P | Y | N | N |
| [70] | U | F | No | N/A | QLT/QNT | Security | RA/RE | A/B/E | P | Y | P | Y | N | Y |
| [71] | I | Both | No | CS | QLT/QNT | Both | RA | A/B | P | Y | P | Y | N | Y |
| [72] | I | G | No | CPS | QLT | Security | RE/RA | A/C/D | Y | Y | P | Y | N | N |
| [73] | I | Both | No | CS | QLT/QNT | Safety | RE | A/B | P | Y | Y | Y | N | Y |
| [74] | I | F | No | A | QLT/QNT | Security | RE/RA | B/D | Y | Y | N | Y | N | Y |
| [75] | U | Both | No | CS | QLT/QNT | Safety | RE/RA | B | P | Y | P | Y | N | Y |
| [76] | I | F | No | CPS | QLT/QNT | Both | RE/RA | A/B/D | Y | P | P | Y | N | Y |
| [77] | I | Both | No | IoT | QLT | Both | RE | A/B | P | Y | P | Y | Y | Y |
| [78] | I | F | No | CPS | QLT/QNT | Security | GE/RE/RA | A/B | Y | Y | P | Y | N | N |
| [79] | I | F | No | CPS | QLT/QNT | Both | GE/RE | A/B | P | Y | P | Y | Y | N |
| [80] | I | F | No | A | QLT | Security | RE | B | P | Y | P | Y | N | Y |
| [81] | I | F | No | CPS | QLT | Both | RE | A/B/D | Y | Y | P | Y | N | Y |
| [82] | I | G | No | CPS | QLT | Safety | RE/RA | A/B/C/D | Y | Y | Y | Y | N | Y |
| [83] | I | G | No | A | QLT | Safety | RA/RE | A/B | Y | Y | P | Y | N | N |
| [84] | I | N/A | No | A | QLT | Safety | RA | A/B | P | Y | P | Y | N | N |
| [85,86] | I | G | No | CS | QLT | Both | RE | A/B/C/D | P | Y | P | Y | Y | Y |
| [87] | I | N/A | No | CS | QLT | Safety | RA/RE | A | P | Y | P | Y | N | N |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kavallieratos, G.; Katsikas, S.; Gkioulos, V. Cybersecurity and Safety Co-Engineering of Cyberphysical Systems—A Comprehensive Survey. Future Internet 2020, 12, 65. https://doi.org/10.3390/fi12040065
Kavallieratos G, Katsikas S, Gkioulos V. Cybersecurity and Safety Co-Engineering of Cyberphysical Systems—A Comprehensive Survey. Future Internet. 2020; 12(4):65. https://doi.org/10.3390/fi12040065
Chicago/Turabian StyleKavallieratos, Georgios, Sokratis Katsikas, and Vasileios Gkioulos. 2020. "Cybersecurity and Safety Co-Engineering of Cyberphysical Systems—A Comprehensive Survey" Future Internet 12, no. 4: 65. https://doi.org/10.3390/fi12040065
APA StyleKavallieratos, G., Katsikas, S., & Gkioulos, V. (2020). Cybersecurity and Safety Co-Engineering of Cyberphysical Systems—A Comprehensive Survey. Future Internet, 12(4), 65. https://doi.org/10.3390/fi12040065







