Towards the Design of a Collaborative Cybersecurity Networked Organisation: Identification and Prioritisation of Governance Needs and Objectives
Abstract
1. Introduction
- the effective contribution of private persons to formal computer emergency response arrangements, e.g., crowdsourcing, requires recognition and division based on the roles and individual needs and can encourage ‘netizens’ to co-produce cybersecurity [24];
- trust is key for sharing cyber intelligence and motivating partners to join a cybersecurity alliance [25];
- the timely identification, management and resolution of conflicts among partner organisations is key for successful collaboration [26];
- traditional assessments of security risks often focus on tangible assets, while intangibles such as tacit knowledge are in some cases more important than physical assets [27];
- knowledge sharing is a fundamental factor for strategic decision making, particularly in relation to innovation management and sustainability of collaborative organisations [28];
- Interoperability is a must for cybersecurity information sharing and timely threat intelligence [29].
2. Materials and Methods
- Ninety-two existing network organisations of four kinds: networks dedicated to information/cybersecurity research and services; cybersecurity incubators/accelerators/tech parks/ecosystems; other research-intensive networks; and networked organisations providing (among others) information services related to cybersecurity (for the full list of the analysed network organisations see Supplementary S1);
- Fourteen regulations and other normative documents, related to the governance of networked organisations in the field of cybersecurity, including relevant EU norms and available governance documents of the four pilot projects;
- Sixty academic articles, books, book chapters and conference papers. In the identification of sources, an initial list of 543 publications was generated by a Scopus search for “networked organizations”/“networked organisations” AND “collaborative”. A subset was selected by reviewing abstracts to identify sources discussing governance issues. In addition, preference was given to more recent and open-access publications, adding also books presenting comparative analyses and benchmarking studies of collaborative networked organisations (for the full list of the analysed academic sources see Supplementary S2).
3. Results
3.1. Analysis of Interviews
- (1)
- Geographical Representation or Exclusion
- (2)
- Supply Chain Security
- (3)
- Involvement of External Stakeholders
- (4)
- Standards and Methodologies
- (5)
- Representation on Senior Governance body/Ies
- (6)
- Decision Making
- (7)
- Auditing
- (8)
- Dispute/Conflict Management Arrangements
- (9)
- Confidentiality
- (10)
- Intellectual Property Management Arrangements
- (11)
- Ethics Code
- (12)
- Specific Ethical Issues
- (13)
- ‘Green’ Policies
- (14)
- Gender Policies and Representation
- (15)
- Transparency
- (16)
- Accountability
- (17)
- Anti-Corruption/Integrity Policies
- the importance of achieving and maintaining trust between the partners and to the network as a whole;
- network’s cohesion;
- knowledge sharing;
- the need to introduce results-oriented management, supported by appropriate instruments for performance monitoring and measurement, e-Procurement, and provision of information and targeted training opportunities;
- quality control;
- resiliency and sustainability of the network;
- the role of strategic communication and engagement.
3.2. Network Governance Issues in Academic Sources
- (18)
- Innovation
- (19)
- Adaptiveness
- CNOs’ adaptability to changing environment (markets, technologies), the need to cope with external change through an adequate rate of adaptation, and evolutionary development, aiming at continuous improvement;
- flexibility and the need to swiftly adjust to market challenges and adapt to turbulent contexts;
- change management; redesign, reengineering, renewal and restructuring; process reengineering and having flexible business processes;
- agility and the capabilities “to sense and respond to predictable and unpredictable events [45];
- the capacity to self-organise, self-adapt, and exhibit emergent behaviour [16];
- (20)
- Cohesion
- balancing interests;
- complementarity and subdivision of successes and risks;
- developing social capital;
- alignment and integration across an increasingly complex network of multiple partners and collaborators;
- exploiting creative synergies.
- (21)
- Trust
- (22)
- Sustainability
- (23)
- Resilience
- (24)
- Communication and Engagement
- (25)
- Knowledge Management
- knowledge acquisition and the organisation’s capacity to transform information gathered from a vast array of diverse sources into useful knowledge;
- knowledge exchange or knowledge sharing;
- knowledge enrichment and the creation of transdisciplinary knowledge;
- knowledge representation;
- the use of knowledge (enterprise knowledge resources), e.g., for making effective decisions;
- knowledge retention or minimising knowledge loss in changes in the networked organisation.
- the importance of aligning knowledge management with structured business processes [53];
- the need for systematic efforts to increase the absorptive capacity of the networked organisation, i.e., its “ability to acquire, assimilate, transform and exploit new knowledge” [54];
- the conditions of performance, creativity and collaboration of knowledge workers, seen as central to an organisation’s success [53];
- information and knowledge brokering and the roles a knowledge broker may play in a networked organisation [55];
- the use of active knowledge models [56].
- (26)
- Long-Term Perspective on Collaboration
- (27)
- Interoperability
- (28)
- Leadership
- (29)
- Organisational Culture
- (30)
- Competences
- understanding of and developing the CNO expertise potential, seeking to build the network mass and also multidisciplinary competences;
- building CNO competences by sharing knowledge and exchanging skills [42];
- developing individual and organisational capabilities for intuitive thinking, complex data analysis and communication [46].
- (31)
- Risk Management
- Identifying and quantifying existing or potential hazards, for example at the level of communication, management and sharing of knowledge [67];
- major concerns related to the use of shared assets and risks of intellectual property infringement [15];
- reducing uncertainty [68];
- risk mitigation [48]; and
- sharing risks among network partners [52].
- (32)
- Evidenceence-based Decision-Making
- (33)
- Competitiveness
- effectiveness;
- involving the most suitable partners with complementary competencies and providing access to new markets;
- customer-focus;
- reduced time to market;
- lower costs;
- delivery of services and products of higher quality;
- larger service and product portfolio;
- enhanced enterprise assets value;
- faster delivery;
- reliability;
- efficiency; etc.
3.3. Normative Requirements to Networks’ Governance
3.4. Governance Issues in Statutory Documents of Existing Networks
3.5. Summary on Governance Objectives and Requirements
- Those that can be designated as “objectives” which can be achieved by devising and effectively implementing sets of normative, organisational, procedural, technical and training measures (included in the second column of Table 2);
- Those that depend on various intangibles and the interplay of numerous factors and contexts, and can be addressed only partially by norms, procedures, training and technical measures. These governance issues are designated as “features of CNOs” and included in the third column of Table 2.
4. Conclusions
Supplementary Materials
Funding
Acknowledgments
Conflicts of Interest
References
- Goel, S. National Cyber Security Strategy and the Emergence of Strong Digital Borders. Connect. Quart. J. 2020, 19. [Google Scholar] [CrossRef]
- Spremić, M.; Šimunic, A. Cyber Security Challenges in Digital Economy. In Proceedings of the World Congress on Engineering WCE 2018, London, UK, 4–6 July 2018; pp. 341–346. [Google Scholar]
- Singh, J.; Millard, C.; Reed, C.; Cobbe, J.; Crowcroft, J. Accountability in the IoT: Systems, Law, and Ways Forward. Computer 2018, 51, 54–65. [Google Scholar] [CrossRef]
- Boeke, S. National cyber crisis management: Different European approaches. Governance 2018, 31, 449–464. [Google Scholar] [CrossRef]
- Rondelez, R. Governing Cyber Security through Networks: An Analysis of Cyber Security Coordination in Belgium. Int. J. Cyber Criminol. 2018, 12, 300–315. [Google Scholar] [CrossRef]
- Sharkov, G. From Cybersecurity to Collaborative Resiliency. In Proceedings of the 2016 ACM Workshop on Automated Decision Making for Active Cyber Defense SafeConfig, Vienna, Austria, 24 October 2016; pp. 3–9. [Google Scholar] [CrossRef]
- Proposal for a Regulation of the European Parliament and of the Council establishing a European Cybersecurity Industrial, Technology and Research Competence Centre and a Network of National Coordination Centres (COM(2018) 630 Final). Available online: https://ec.europa.eu/commission/sites/beta-political/files/soteu2018-cybersecurity-centres-regulation-630_en.pdf (accessed on 9 March 2020).
- Establishing and Operating a Pilot for a Cybersecurity Competence Network to Develop and Implement a Common Cybersecurity Research & Innovation Roadmap. ID: SU-ICT-03-2018. 27 October 2017. Available online: https://ec.europa.eu/info/funding-tenders/opportunities/portal/screen/opportunities/topic-details/su-ict-03-2018 (accessed on 9 March 2020).
- Camarinha-Matos, L.M.; Afsarmanesh, H.; Galeano, N.; Molina, A. Collaborative Networked Organizations—Concepts and Practice in Manufacturing Enterprises. Comput. Ind. Eng. 2009, 57, 46–60. [Google Scholar] [CrossRef]
- Ouyang, L.; Yuan, Y.; Wang, F.-Y. A Blockchain-based Framework for Collaborative Production in Distributed and Social Manufacturing. In Proceedings of the IEEE International Conference on Service Operations and Logistics, and Informatics 2019, SOLI 2019, Zhengzhou, China, 6–8 November 2019; pp. 76–81. [Google Scholar] [CrossRef]
- Ziolkowski, R.; Miscione, G.; Schwabe, G. Consensus through Blockchains: Exploring Governance across Inter-organizational Settings. In Proceedings of the International Conference on Information Systems 2018, ICIS 2018, San Francisco, CA, USA, 13–16 December 2018. [Google Scholar]
- Buchanan, W.; Thuemmler, C.; Spyra, G.; Smales, A.; Prajapati, B. Towards Trust and Governance in Integrated Health and Social Care Platforms. In Health 4.0: How Virtualization and Big Data Are Revolutionizing Healthcare; Thuemmler, C., Bai, C., Eds.; Springer: Cham, Switzerland, 2017; pp. 219–231. [Google Scholar] [CrossRef]
- Kumar, B. The (In) Security of Smart Cities: Vulnerabilities, Risks, Mitigation and Prevention. Int. J. Eng. Adv. Technol. 2019, 8, 464–470. [Google Scholar] [CrossRef]
- Radanliev, P.; De Roure, D.; Nurse, J.R.C.; Nicolescu, R.; Huth, M.; Cannady, S.; Montalvo, R.M. Integration of Cyber Security Frameworks, Models and Approaches for Building Design Principles for the Internet-of-Things in Industry 4.0. In Proceedings of the Living in the Internet of Things: Cybersecurity of the IoT, London, UK, 28–29 March 2018. CP740. [Google Scholar] [CrossRef]
- Su, Z.; Biennier, F.; Ouedraogo, W.F. A Governance Framework for Mitigating Risks and Uncertainty in Collaborative Business Processes. In Collaborative Networks in the Internet of Services; Camarinha-Matos, L.M., Xu, L., Afsarmanesh, H., Eds.; Springer: Heidelberg, Germany, 2012; pp. 667–674. [Google Scholar]
- Bilal, M.; Daclin, N.; Chapurlat, V. Collaborative Networked Organizations as System of Systems: A Model-Based Engineering Approach. In Collaborative Systems for Smart Networked Environments, IFIP Advances in Information and Communication Technology; Camarinha-Matos, L.M., Afsarmanesh, H., Eds.; Springer: Berlin/Heidelberg, Germany, 2014; Volume 434, pp. 227–234. [Google Scholar]
- Dotsenko, S.; Illiashenko, O.; Kamenskyi, S.; Kharchenko, V. Integrated Security Management System for Enterprises in Industry 4.0. Inf. Secur. Int. J. 2019, 43, 294–304. [Google Scholar] [CrossRef][Green Version]
- Hütten, M. The Soft Spot of Hard Code: Blockchain Technology, Network Governance and Pitfalls of Technological Utopianism. Glob. Netw. 2019, 19, 329–348. [Google Scholar] [CrossRef]
- Saleem, J.; Hammoudeh, M.; Raza, U.; Adebisi, B.; Ande, R. IoT Standardisation: Challenges, Perspectives and Solution. In Proceedings of the 2nd International Conference on Future Networks and Distributed Systems, Amman, Jordan, 26–27 June 2018. [Google Scholar] [CrossRef]
- Eichensehr, K.E. Public-Private Cybersecurity. Tex. Law Rev. 2017, 95, 467–538. [Google Scholar]
- Newlove-Eriksson, L.; Giacomello, G.; Eriksson, J. The Invisible Hand? Critical Information Infrastructures, Commercialisation and National Security. Int. Spect. 2018, 53, 124–140. [Google Scholar] [CrossRef]
- Skierka, I.M. The Governance of Safety and Security Risks in Connected Healthcare. In Proceedings of the Living in the Internet of Things: Cybersecurity of the IoT, London, UK, 28–29 March 2018. CP740. [Google Scholar] [CrossRef]
- Radanliev, P.; De Roure, D.C.; Nurse, J.R.C.; Montalvo, R.M.; Cannady, S.; Santos, O.; Maddox, L.T.; Burnap, P.; Maple, C. Future Developments in Standardisation of Cyber Risk in the Internet of Things (IoT). SN Appl. Sci. 2020, 2, 169. [Google Scholar] [CrossRef]
- Leppänen, A.; Kankaanranta, T. Co-production of Cybersecurity: A Case of Reported Data System Break-ins. Police Pract. Res. Int. J. 2020, 21, 78–94. [Google Scholar] [CrossRef]
- Deljoo, A.; Van Engers, T.; Koning, R.; Gommans, L.; De Laat, C. Towards Trustworthy Information Sharing by Creating Cyber Security Alliances. In Proceedings of the 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications and 12th IEEE International Conference on Big Data Science and Engineering, Trustcom/BigDataSE 2018, New York, NY, USA, 1–3 August 2018; pp. 1506–1510. [Google Scholar] [CrossRef]
- Narendra, N.C.; Norta, A.; Mahunnah, M.; Ma, L.; Maggi, F.M. Sound Conflict Management and Resolution for Virtual-Enterprise Collaborations. Serv. Oriented Comput. Appl. 2016, 10, 233–251. [Google Scholar] [CrossRef]
- Nurse, J.R.C.; Radanliev, P.; Creese, S.; De Roure, D. If You Can’t Understand It, You Can’t Properly Assess It! The Reality of Assessing Security Risks in Internet of Things Systems. In Proceedings of the Living in the Internet of Things: Cybersecurity of the IoT, London, UK, 28–29 March 2018. [Google Scholar] [CrossRef]
- Wulf, A.; Butel, L. Knowledge Sharing and Collaborative Relationships in Business Ecosystems and Networks: A Definition and a Demarcation. Ind. Manag. Data Syst. 2017, 117, 1407–1425. [Google Scholar] [CrossRef]
- Rantos, K.; Spyros, A.; Papanikolaou, A.; Kritsas, A.; Ilioudis, C.A.; Katos, A. Interoperability Challenges in the Cybersecurity Information Sharing Ecosystem. Computers 2020, 9, 18. [Google Scholar] [CrossRef]
- Scala, N.M.; Reilly, A.C.; Goethals, P.L.; Cukier, M. Risk and the Five Hard Problems of Cybersecurity. Risk Anal. 2019, 39, 2119–2126. [Google Scholar] [CrossRef]
- European Network of Cybersecurity Centres and Competence Hub for Innovation and Operations (ECHO). Available online: https://echonetwork.eu/ (accessed on 10 March 2020).
- Kalkman, J.P.; Wieskamp, L. Cyber Intelligence Networks: A Typology. Int. J. Intell. Secur. Public Aff. 2019, 21, 4–24. [Google Scholar] [CrossRef][Green Version]
- Tapia, R.S. Converging on Business-IT Alignment Best Practices: Lessons Learned from a Dutch Cross-Governmental Partnership. In Proceedings of the 2009 IEEE International Technology Management Conference (ICE), Leiden, The Netherlands, 22–24 June 2009. [Google Scholar] [CrossRef][Green Version]
- Rabelo, R.J.; Costa, S.N.; Romero, D. A Governance Reference Model for Virtual Enterprises. In Collaborative Systems for Smart Networked Environments, IFIP Advances in Information and Communication Technology; Luis, M., Camarinha-Matos, L.M., Afsarmanesh, H., Eds.; Springer: Berlin/Heidelberg, Germany, 2014; Volume 434, pp. 60–70. [Google Scholar]
- Slayton, R. Governing Uncertainty or Uncertain Governance? Information Security and the Challenge of Cutting Ties. Sci. Technol. Hum. Values 2020. [Google Scholar] [CrossRef]
- Pohle, J. Multistakeholder Governance Processes as Production Sites: Enhanced Cooperation in the Making. Internet Policy Rev. 2016, 5. [Google Scholar] [CrossRef]
- Feenberg, A. The Internet as Network, World, Co-construction, and Mode of Governance. Inf. Soc. 2019, 35, 229–243. [Google Scholar] [CrossRef]
- Sterlini, P.; Massacci, F.; Kadenko, N.; Fiebig, T.; Van Eeten, M. Governance Challenges for European Cybersecurity Policies: Stakeholder Views. IEEE Secur. Priv. 2020, 18, 46–54. [Google Scholar] [CrossRef]
- Kvale, S.; Brinkmann, S. InterViews: Learning the Craft of Qualitative Research Interviewing, 2nd ed.; SAGE: Los Angeles, CA, USA, 2009. [Google Scholar]
- Brymann, A. Social Research Methods, 4th ed.; Oxford University Press: Oxford, UK, 2012. [Google Scholar]
- Tagarev, T. Governance of Collaborative Networked Organisations: Stakeholder Requirements. In Proceedings of the 11th IEEE International Conference on Dependable Systems, Services and Technologies DESSERT 2020, Kyiv, Ukraine, 14–18 May 2020. [Google Scholar]
- Mortati, M. Systemic Aspects of Innovation and Design: The Perspective of Collaborative Networks; Springer: Cham, Switzerland, 2013. [Google Scholar]
- Grippa, F.; Leitão, J.; Gluesing, J.; Riopelle, K.; Gloor, P. Collaborative Innovation Networks: Building Adaptive and Resilient Organizations; Springer: Cham, Switzerland, 2018. [Google Scholar] [CrossRef]
- Kandjani, H.; Bernus, P. Towards a Cybernetic Theory and Reference Model of Self-designing Complex Collaborative Networks. In Collaborative Net-Works in the Internet of Services; Camarinha-Matos, L.M., Xu, L., Afsarmanesh, H., Eds.; Springer: Berlin/Heidelberg, Germany, 2012; pp. 485–493. [Google Scholar]
- Hovorka, D.S.; Larsen, K.R. Enabling Agile Adoption Practices through Network Organizations. Eur. J. Inf. Syst. 2006, 15, 159–168. [Google Scholar] [CrossRef]
- Crawford, K.; Hasan, H.M.; Warne, L.; Linger, H. From Traditional Knowledge Management in Hierarchical Organizations to a Network Centric Paradigm for a Changing World. Emerg. Complex. Organ. 2009, 11, 1–8. [Google Scholar]
- Jackson, P.; Cardoni, A. Organizational Design and Collaborative Networked Organizations in a Data-Rich World: A Cybernetics Perspective. In Collaboration in a Data-Rich World, IFIP Advances in Information and Communication Technology; Camarinha-Matos, L.M., Afsarmanesh, H., Fornasiero, R., Eds.; Springer: Cham, Switzerland, 2017; Volume 506, pp. 185–193. [Google Scholar] [CrossRef]
- Durugbo, C. Collaborative Networks: A Systematic Review and Multi-level Framework. Int. J. Prod. Res. 2016, 54, 3749–3776. [Google Scholar] [CrossRef]
- Noran, O. Towards a Meta-Methodology for Collaborative Networked Organisations. In Virtual Enterprises and Collaborative Networks, IFIP International Federation for Information Processing; Camarinha-Matos, L.M., Ed.; Springer: Boston, MA, USA, 2004; Volume 149, pp. 71–78. [Google Scholar]
- Jung, K. Sources of Organizational Resilience for Sustainable Communities: An Institutional Collective Action Perspective. Sustainability 2017, 9, 1141. [Google Scholar] [CrossRef]
- Krčo SVan Kranenburg, R.; Lončar, M.; Ziouvelou, X.; McGroarty, F. Digitization of Value Chains and Ecosystems. In Digital Business Models: Driving Transformation and Innovation; Aagaard, A., Ed.; Palgrave MacMillan: Cham, Switzerland, 2019; pp. 81–116. [Google Scholar] [CrossRef]
- Romero, D.; Molina, A. Collaborative Networked Organisations and Customer Communities: Value Co-Creation and Co-Innovation in the Networking Era. J. Prod. Plan. Control 2011, 22, 447–472. [Google Scholar] [CrossRef]
- Barchetti, U.; Capodieci, A.; Guido, A.L.; Mainetti, L. Collaborative Process Management for the Networked Enterprise: A Case Study. In Proceedings of the 26th IEEE International Conference on Advanced Information Networking and Applications Workshops, Fukuoka, Japan, 26–29 March 2012; pp. 1343–1348. [Google Scholar] [CrossRef]
- Hovorka, D.S.; Larsen, K.R. Increasing Absorptive Capacity through Strategic use of Network Organizations. In Proceedings of the 11th Americas Conference on Information Systems AMCIS 2005, Omaha, NE, USA, 11–14 August 2005; p. 270. [Google Scholar]
- Rostek, K. Benchmarking Collaborative Networks: A Key to SME Competitiveness; Springer: Cham, Switzerland, 2015. [Google Scholar]
- Pawlak, A.; Jørgensen, H.D. Holistic Design of Collaborative Net-works of Design Engineering Organizations. In Risks and Resilience of Collaborative Networks, IFIP Advances in Information and Communication Technology; Camarinha-Matos, L.M., Bénaben, F., Picard, W., Eds.; Springer: Cham, Switzerland, 2015; Volume 463, pp. 612–621. [Google Scholar]
- Serrier, S.B.; Ducq, Y.; Vallespir, B. Networked Companies and a Typology of Collaborations. In Enterprise Interoperability: INTEROP-PGSO Vision; Archimède, B., Vallespir, B., Eds.; Wiley-ISTE: London, UK, 2017; Volume 1, pp. 19–42. [Google Scholar] [CrossRef]
- Ulbrich, S.; Troitzsch, H.; Van den Anker, F.; Plüss, A.; Huber, C. How Teams in Networked Organisations Develop Collaborative Capability: Processes, Critical Incidents and Success Factors. Prod. Plan. Control Manag. Oper. 2011, 22, 488–500. [Google Scholar] [CrossRef]
- Cardoni, A.; Saetta, S.; Tiacci, L. Evaluating How Potential Pool of Partners Can Join Together in Different Types of Long Term Collaborative Networked Organizations. In Collaborative Networks for a Sustainable World, IFIP Advances in Information and Communication Technology; Camarinha-Matos, L.M., Boucher, X., Afsarmanesh, H., Eds.; Springer: Berlin/Heidelberg, Germany, 2010; Volume 336, pp. 312–321. [Google Scholar]
- Saetta, S.; Tiacci, L.; Cagnazzo, L. The Innovative Model of the Virtual Development Office for Collaborative Networked Enterprises: The GPT Network Case Study. Int. J. Comput. Integr. Manuf. 2013, 26, 41–54. [Google Scholar] [CrossRef]
- Andres, B.; Poler, B.; Sanchis, R. Collaborative Strategies Alignment to Enhance the Collaborative Network Agility and Resilience. In Risks and Resilience of Collaborative Networks, IFIP Advances in Information and Communication Technology; Camarinha-Matos, L.M., Bénaben, F., Picard, W., Eds.; Springer: Cham, Switzerland, 2015; Volume 463, pp. 88–99. [Google Scholar]
- Durugbo, C.; Riedel, L.C.K.H. Readiness Assessment of Collaborative Networked Organisations for Integrated Product and Service Delivery. Int. J. Prod. Res. 2013, 51, 598–613. [Google Scholar] [CrossRef]
- Mabey, C.; Wong, A.L.Y.; Hsieh, L. Knowledge Exchange in Networked Organizations: Does Place Matter? R D Manag. 2014, 45, 487–500. [Google Scholar] [CrossRef]
- Song, Y.; Grippa, F.; Gloor, P.A.; Leitão, J. (Eds.) Collaborative Innovation Networks: Latest Insights from Social Innovation, Education, and Emerging Technologies Research; Springer: Cham, Switzerland, 2019. [Google Scholar]
- Enquist, H.; Nilsson, A.; Magnusson, J. Change Management Implications for Network Organizations. In Proceedings of the 37th Annual Hawaii International Conference on System Sciences, Big Island, HI, USA, 5–8 January 2004. [Google Scholar] [CrossRef]
- Arrais-Castro, A.; Varela, M.L.R.; Putnik, G.D.; Ribeiro, R.A.; Machado, J.; Ferreira, L. Collaborative Framework for Virtual Organization Synthesis Based on a Dynamic Multi-criteria Decision Model. Int. J. Comput. Integr. Manuf. 2018, 31, 857–868. [Google Scholar] [CrossRef]
- Abreu, A.; Calado, J.M.F. Risk Model to Support the Governance of Collaborative Ecosystems. IFAC PapersOnLine 2017, 50, 10544–10549. [Google Scholar] [CrossRef]
- Komanda, M. Foundations of Network Organizations Ontology. Int. J. Bus. Manag. Stud. 2012, 1, 565–569. [Google Scholar]
- Pierce, P.; Ricciardi, F.; Zardini, A. Smart Cities as Organizational Fields: A Framework for Mapping Sustainability-Enabling Configurations. Sustainability 2017, 9, 1506. [Google Scholar] [CrossRef]
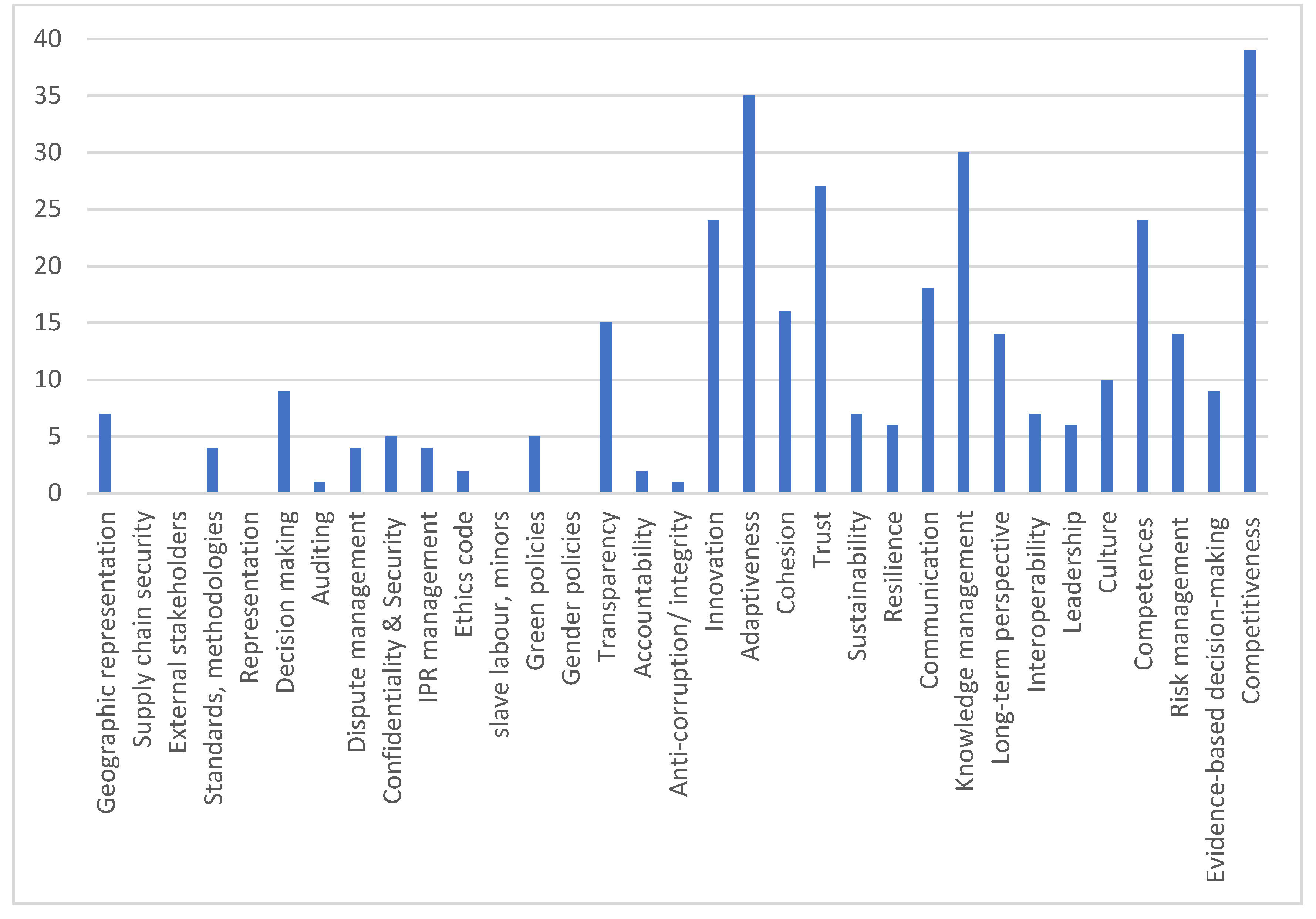
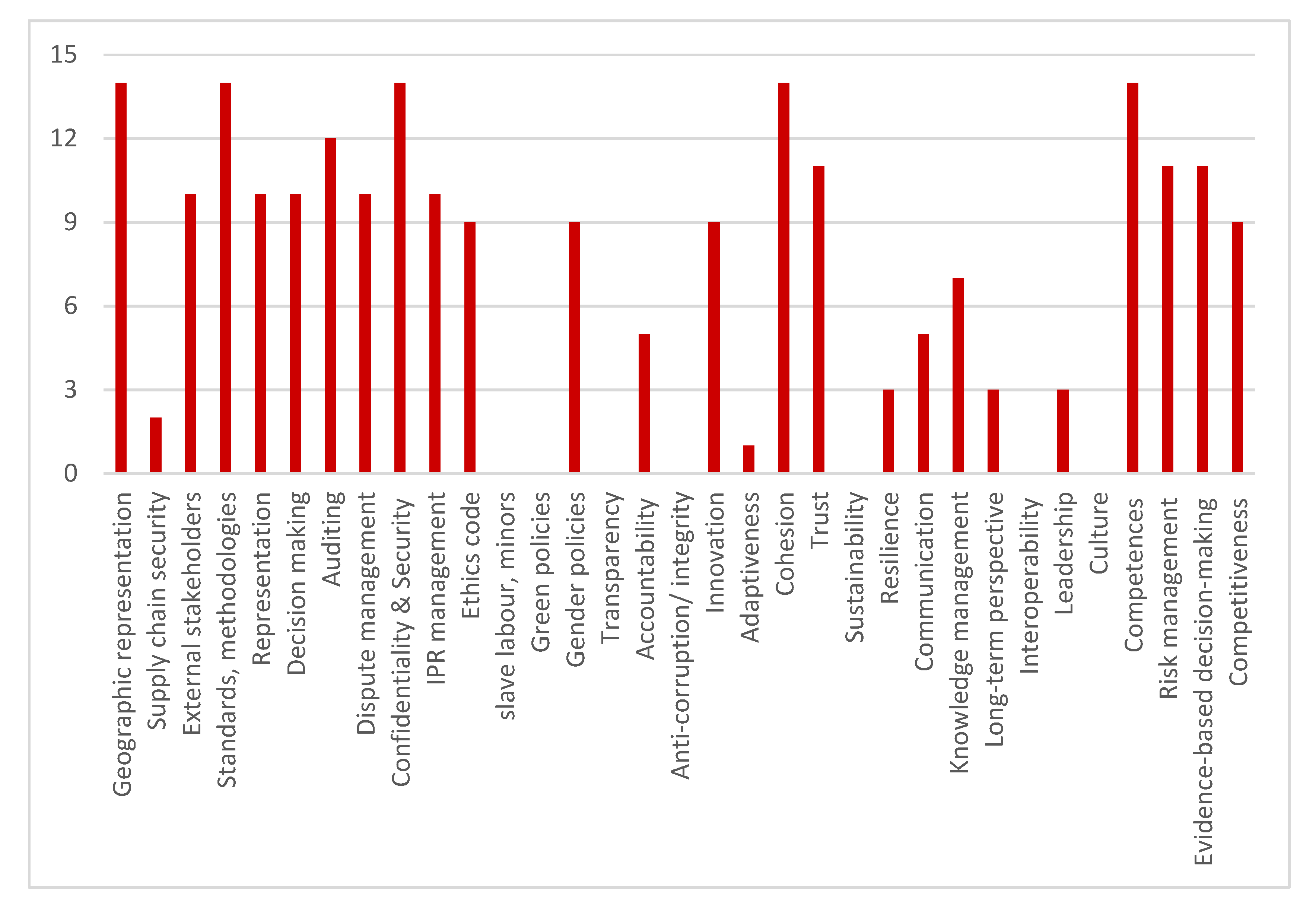
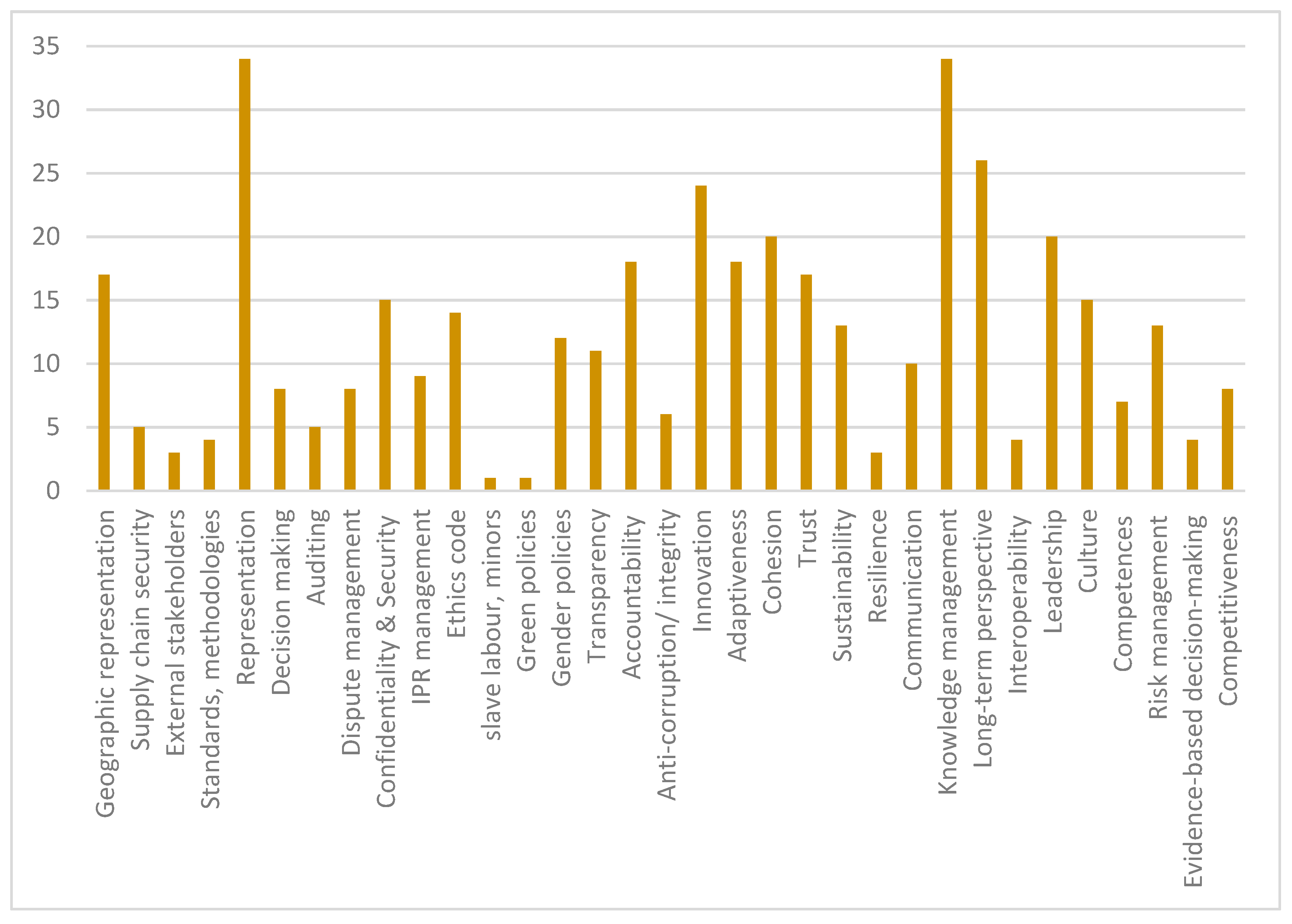
| Tier | Governance Categories |
|---|---|
| 1 | Geographic representation; involvement of external stakeholders; decision-making arrangements; confidentiality |
| 2 | Supply chain security; representation on the senior governance bodies; auditing; dispute and IPR management; Ethics code; gender policy; transparency, accountability and integrity |
| 3 | Standards and methodologies |
| 4 | Use of slave labour or labour of minors; ‘green’ policies |
| Tier | Governance Objectives | Features of CNOs |
|---|---|---|
| 1 | Geographical representation or exclusion; Involving external stakeholders; Representation; Decision making; Auditing; Confidentiality and Security; Knowledge management; Standards and methodologies; Long-term perspective on collaboration; Competences; Risk management; Evidence-based decision-making | Adaptiveness; Cohesion; Trust; Competitiveness |
| 2 | Supply chain security; Dispute/conflict management arrangements; Intellectual Property management; Ethics code; Gender policies and representation; Transparency; Accountability; Integrity/anti-corruption policy | Innovation; Leadership |
| 3 | Communication and engagement | Organisational culture; Sustainability |
| 4 | ‘Green’ policies; Slave labour, labour of minors; Interoperability | Resilience |
© 2020 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tagarev, T. Towards the Design of a Collaborative Cybersecurity Networked Organisation: Identification and Prioritisation of Governance Needs and Objectives. Future Internet 2020, 12, 62. https://doi.org/10.3390/fi12040062
Tagarev T. Towards the Design of a Collaborative Cybersecurity Networked Organisation: Identification and Prioritisation of Governance Needs and Objectives. Future Internet. 2020; 12(4):62. https://doi.org/10.3390/fi12040062
Chicago/Turabian StyleTagarev, Todor. 2020. "Towards the Design of a Collaborative Cybersecurity Networked Organisation: Identification and Prioritisation of Governance Needs and Objectives" Future Internet 12, no. 4: 62. https://doi.org/10.3390/fi12040062
APA StyleTagarev, T. (2020). Towards the Design of a Collaborative Cybersecurity Networked Organisation: Identification and Prioritisation of Governance Needs and Objectives. Future Internet, 12(4), 62. https://doi.org/10.3390/fi12040062




